Information Governance for Fresh Air.
VerifiedAdded on 2022/09/06
|19
|5287
|16
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INFORMATION GOVERNANCE FOR FRESH AIR
Information Governance for Fresh Air
Name of the Student
Name of the University
Author note
Information Governance for Fresh Air
Name of the Student
Name of the University
Author note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1INFORMATION GOVERNANCE FOR FRESH AIR
Table of Contents
1. Risk Assessment Analysis in relation to Data Security and IT Services.....................................2
2. Summary of ethical, social, legal and regulatory compliance issues related to Fresh Air..........5
3. Poster undertaking Disaster Recovery Steps.............................................................................12
4. Reflection on Portfolio..............................................................................................................14
References......................................................................................................................................17
Table of Contents
1. Risk Assessment Analysis in relation to Data Security and IT Services.....................................2
2. Summary of ethical, social, legal and regulatory compliance issues related to Fresh Air..........5
3. Poster undertaking Disaster Recovery Steps.............................................................................12
4. Reflection on Portfolio..............................................................................................................14
References......................................................................................................................................17
2INFORMATION GOVERNANCE FOR FRESH AIR
1. Risk Assessment Analysis in relation to Data Security and IT Services
In order to develop a unified desktop solution and deploy a solution that employs the use of cloud computing, Fresh Air would
need to think over including a proprietary cloud-based software solution. However, in order to determine the solution, a risk
assessment needs to be conducted in relation to the data security and IT services, which would also include solutions for mitigating
them accordingly.
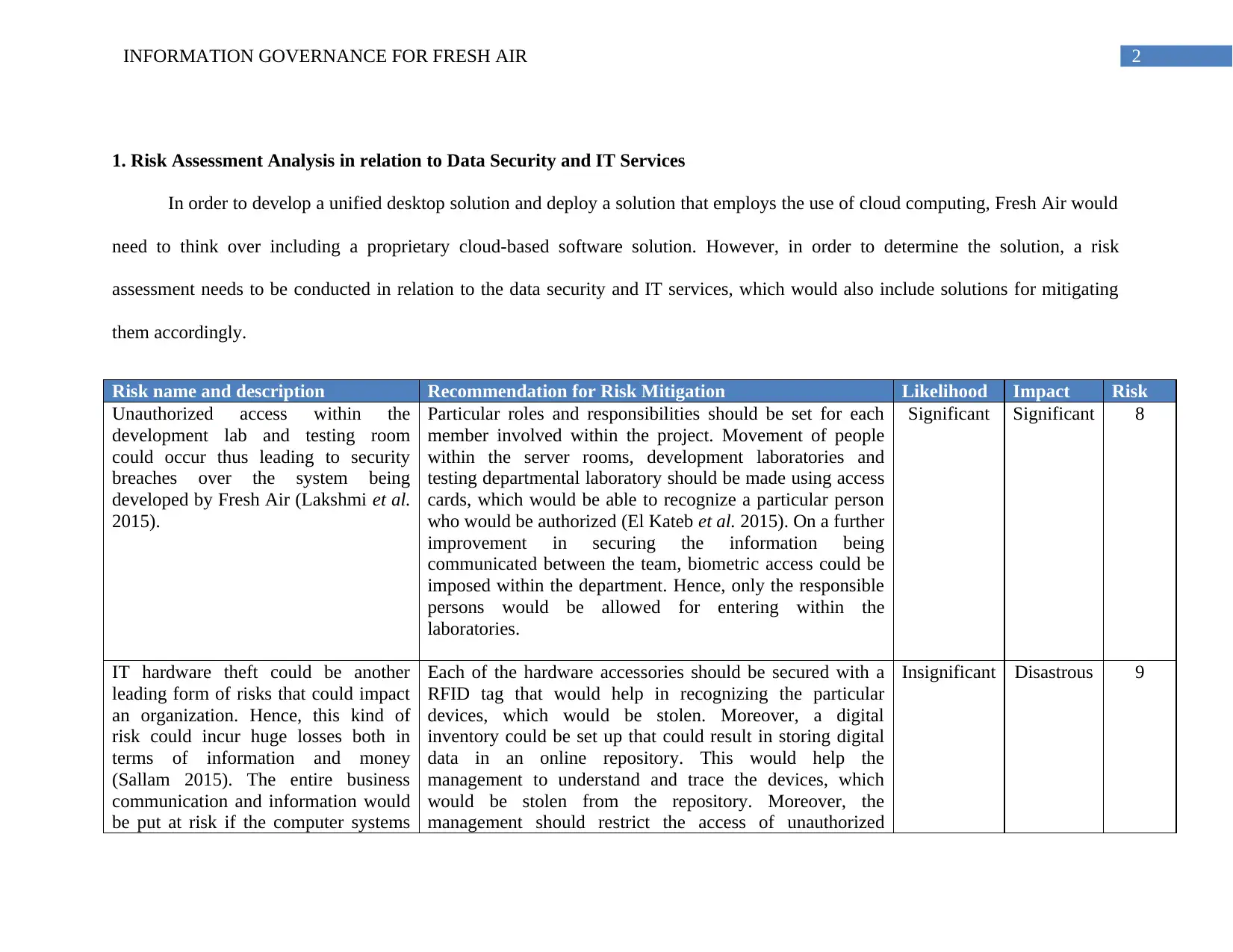
Risk name and description Recommendation for Risk Mitigation Likelihood Impact Risk
Unauthorized access within the
development lab and testing room
could occur thus leading to security
breaches over the system being
developed by Fresh Air (Lakshmi et al.
2015).
Particular roles and responsibilities should be set for each
member involved within the project. Movement of people
within the server rooms, development laboratories and
testing departmental laboratory should be made using access
cards, which would be able to recognize a particular person
who would be authorized (El Kateb et al. 2015). On a further
improvement in securing the information being
communicated between the team, biometric access could be
imposed within the department. Hence, only the responsible
persons would be allowed for entering within the
laboratories.
Significant Significant 8
IT hardware theft could be another
leading form of risks that could impact
an organization. Hence, this kind of
risk could incur huge losses both in
terms of information and money
(Sallam 2015). The entire business
communication and information would
be put at risk if the computer systems
Each of the hardware accessories should be secured with a
RFID tag that would help in recognizing the particular
devices, which would be stolen. Moreover, a digital
inventory could be set up that could result in storing digital
data in an online repository. This would help the
management to understand and trace the devices, which
would be stolen from the repository. Moreover, the
management should restrict the access of unauthorized
Insignificant Disastrous 9
1. Risk Assessment Analysis in relation to Data Security and IT Services
In order to develop a unified desktop solution and deploy a solution that employs the use of cloud computing, Fresh Air would
need to think over including a proprietary cloud-based software solution. However, in order to determine the solution, a risk
assessment needs to be conducted in relation to the data security and IT services, which would also include solutions for mitigating
them accordingly.
Risk name and description Recommendation for Risk Mitigation Likelihood Impact Risk
Unauthorized access within the
development lab and testing room
could occur thus leading to security
breaches over the system being
developed by Fresh Air (Lakshmi et al.
2015).
Particular roles and responsibilities should be set for each
member involved within the project. Movement of people
within the server rooms, development laboratories and
testing departmental laboratory should be made using access
cards, which would be able to recognize a particular person
who would be authorized (El Kateb et al. 2015). On a further
improvement in securing the information being
communicated between the team, biometric access could be
imposed within the department. Hence, only the responsible
persons would be allowed for entering within the
laboratories.
Significant Significant 8
IT hardware theft could be another
leading form of risks that could impact
an organization. Hence, this kind of
risk could incur huge losses both in
terms of information and money
(Sallam 2015). The entire business
communication and information would
be put at risk if the computer systems
Each of the hardware accessories should be secured with a
RFID tag that would help in recognizing the particular
devices, which would be stolen. Moreover, a digital
inventory could be set up that could result in storing digital
data in an online repository. This would help the
management to understand and trace the devices, which
would be stolen from the repository. Moreover, the
management should restrict the access of unauthorized
Insignificant Disastrous 9
3INFORMATION GOVERNANCE FOR FRESH AIR
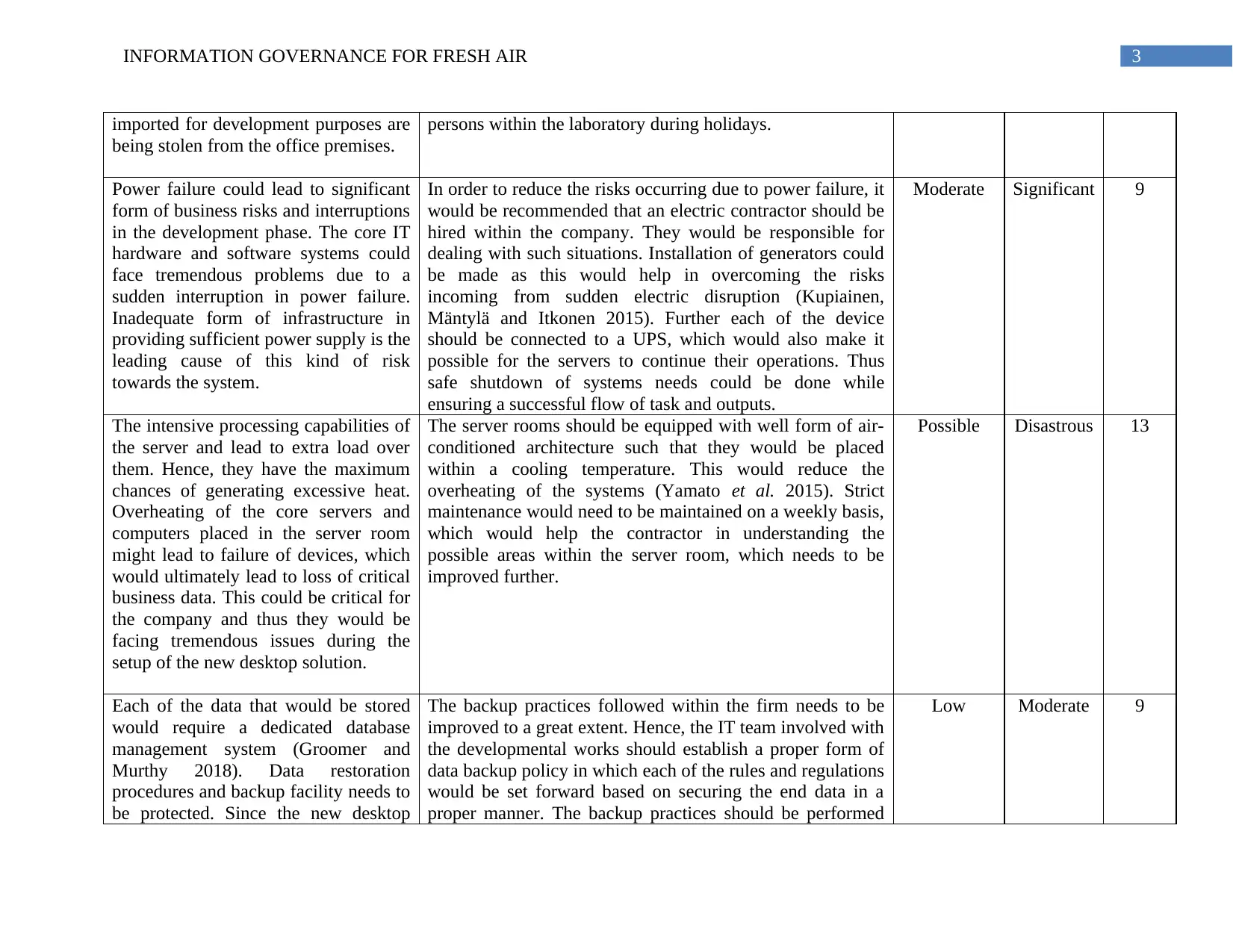
imported for development purposes are
being stolen from the office premises.
persons within the laboratory during holidays.
Power failure could lead to significant
form of business risks and interruptions
in the development phase. The core IT
hardware and software systems could
face tremendous problems due to a
sudden interruption in power failure.
Inadequate form of infrastructure in
providing sufficient power supply is the
leading cause of this kind of risk
towards the system.
In order to reduce the risks occurring due to power failure, it
would be recommended that an electric contractor should be
hired within the company. They would be responsible for
dealing with such situations. Installation of generators could
be made as this would help in overcoming the risks
incoming from sudden electric disruption (Kupiainen,
Mäntylä and Itkonen 2015). Further each of the device
should be connected to a UPS, which would also make it
possible for the servers to continue their operations. Thus
safe shutdown of systems needs could be done while
ensuring a successful flow of task and outputs.
Moderate Significant 9
The intensive processing capabilities of
the server and lead to extra load over
them. Hence, they have the maximum
chances of generating excessive heat.
Overheating of the core servers and
computers placed in the server room
might lead to failure of devices, which
would ultimately lead to loss of critical
business data. This could be critical for
the company and thus they would be
facing tremendous issues during the
setup of the new desktop solution.
The server rooms should be equipped with well form of air-
conditioned architecture such that they would be placed
within a cooling temperature. This would reduce the
overheating of the systems (Yamato et al. 2015). Strict
maintenance would need to be maintained on a weekly basis,
which would help the contractor in understanding the
possible areas within the server room, which needs to be
improved further.
Possible Disastrous 13
Each of the data that would be stored
would require a dedicated database
management system (Groomer and
Murthy 2018). Data restoration
procedures and backup facility needs to
be protected. Since the new desktop
The backup practices followed within the firm needs to be
improved to a great extent. Hence, the IT team involved with
the developmental works should establish a proper form of
data backup policy in which each of the rules and regulations
would be set forward based on securing the end data in a
proper manner. The backup practices should be performed
Low Moderate 9
imported for development purposes are
being stolen from the office premises.
persons within the laboratory during holidays.
Power failure could lead to significant
form of business risks and interruptions
in the development phase. The core IT
hardware and software systems could
face tremendous problems due to a
sudden interruption in power failure.
Inadequate form of infrastructure in
providing sufficient power supply is the
leading cause of this kind of risk
towards the system.
In order to reduce the risks occurring due to power failure, it
would be recommended that an electric contractor should be
hired within the company. They would be responsible for
dealing with such situations. Installation of generators could
be made as this would help in overcoming the risks
incoming from sudden electric disruption (Kupiainen,
Mäntylä and Itkonen 2015). Further each of the device
should be connected to a UPS, which would also make it
possible for the servers to continue their operations. Thus
safe shutdown of systems needs could be done while
ensuring a successful flow of task and outputs.
Moderate Significant 9
The intensive processing capabilities of
the server and lead to extra load over
them. Hence, they have the maximum
chances of generating excessive heat.
Overheating of the core servers and
computers placed in the server room
might lead to failure of devices, which
would ultimately lead to loss of critical
business data. This could be critical for
the company and thus they would be
facing tremendous issues during the
setup of the new desktop solution.
The server rooms should be equipped with well form of air-
conditioned architecture such that they would be placed
within a cooling temperature. This would reduce the
overheating of the systems (Yamato et al. 2015). Strict
maintenance would need to be maintained on a weekly basis,
which would help the contractor in understanding the
possible areas within the server room, which needs to be
improved further.
Possible Disastrous 13
Each of the data that would be stored
would require a dedicated database
management system (Groomer and
Murthy 2018). Data restoration
procedures and backup facility needs to
be protected. Since the new desktop
The backup practices followed within the firm needs to be
improved to a great extent. Hence, the IT team involved with
the developmental works should establish a proper form of
data backup policy in which each of the rules and regulations
would be set forward based on securing the end data in a
proper manner. The backup practices should be performed
Low Moderate 9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4INFORMATION GOVERNANCE FOR FRESH AIR
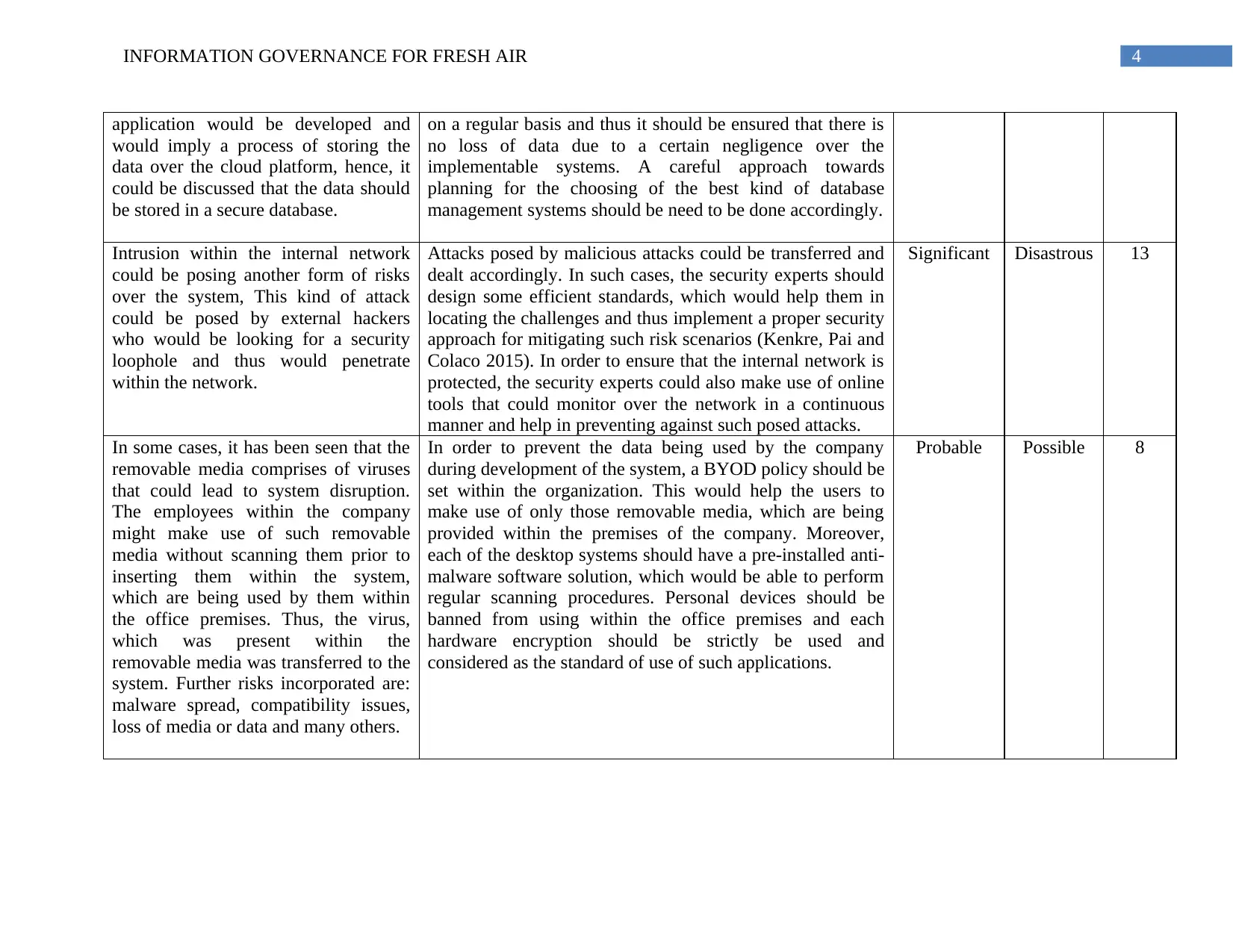
application would be developed and
would imply a process of storing the
data over the cloud platform, hence, it
could be discussed that the data should
be stored in a secure database.
on a regular basis and thus it should be ensured that there is
no loss of data due to a certain negligence over the
implementable systems. A careful approach towards
planning for the choosing of the best kind of database
management systems should be need to be done accordingly.
Intrusion within the internal network
could be posing another form of risks
over the system, This kind of attack
could be posed by external hackers
who would be looking for a security
loophole and thus would penetrate
within the network.
Attacks posed by malicious attacks could be transferred and
dealt accordingly. In such cases, the security experts should
design some efficient standards, which would help them in
locating the challenges and thus implement a proper security
approach for mitigating such risk scenarios (Kenkre, Pai and
Colaco 2015). In order to ensure that the internal network is
protected, the security experts could also make use of online
tools that could monitor over the network in a continuous
manner and help in preventing against such posed attacks.
Significant Disastrous 13
In some cases, it has been seen that the
removable media comprises of viruses
that could lead to system disruption.
The employees within the company
might make use of such removable
media without scanning them prior to
inserting them within the system,
which are being used by them within
the office premises. Thus, the virus,
which was present within the
removable media was transferred to the
system. Further risks incorporated are:
malware spread, compatibility issues,
loss of media or data and many others.
In order to prevent the data being used by the company
during development of the system, a BYOD policy should be
set within the organization. This would help the users to
make use of only those removable media, which are being
provided within the premises of the company. Moreover,
each of the desktop systems should have a pre-installed anti-
malware software solution, which would be able to perform
regular scanning procedures. Personal devices should be
banned from using within the office premises and each
hardware encryption should be strictly be used and
considered as the standard of use of such applications.
Probable Possible 8
application would be developed and
would imply a process of storing the
data over the cloud platform, hence, it
could be discussed that the data should
be stored in a secure database.
on a regular basis and thus it should be ensured that there is
no loss of data due to a certain negligence over the
implementable systems. A careful approach towards
planning for the choosing of the best kind of database
management systems should be need to be done accordingly.
Intrusion within the internal network
could be posing another form of risks
over the system, This kind of attack
could be posed by external hackers
who would be looking for a security
loophole and thus would penetrate
within the network.
Attacks posed by malicious attacks could be transferred and
dealt accordingly. In such cases, the security experts should
design some efficient standards, which would help them in
locating the challenges and thus implement a proper security
approach for mitigating such risk scenarios (Kenkre, Pai and
Colaco 2015). In order to ensure that the internal network is
protected, the security experts could also make use of online
tools that could monitor over the network in a continuous
manner and help in preventing against such posed attacks.
Significant Disastrous 13
In some cases, it has been seen that the
removable media comprises of viruses
that could lead to system disruption.
The employees within the company
might make use of such removable
media without scanning them prior to
inserting them within the system,
which are being used by them within
the office premises. Thus, the virus,
which was present within the
removable media was transferred to the
system. Further risks incorporated are:
malware spread, compatibility issues,
loss of media or data and many others.
In order to prevent the data being used by the company
during development of the system, a BYOD policy should be
set within the organization. This would help the users to
make use of only those removable media, which are being
provided within the premises of the company. Moreover,
each of the desktop systems should have a pre-installed anti-
malware software solution, which would be able to perform
regular scanning procedures. Personal devices should be
banned from using within the office premises and each
hardware encryption should be strictly be used and
considered as the standard of use of such applications.
Probable Possible 8

5INFORMATION GOVERNANCE FOR FRESH AIR
In the above table, ratings are followed as: (1-5 = Low or Insignificant; 5-7 Medium or
Moderate; 7 or above = Significant or Disastrous)
2. Summary of ethical, social, legal and regulatory compliance issues related to Fresh Air
In relation to the case study, it has been discussed that Fresh Air has been planning to
implement and deploy for a unified desktop solution that would employ the use of cloud
computing solutions for storing every day data. The different employees within the IT team
would form a collaboration and develop the software in the in-house department (Khan and Khan
2017). The IT team will also be responsible for performing in-house support to all staff and
services, which would be occurring within the firm. After the deployment of the software
solution for the business, a comprehensive training would be provided to all employees and
existing staff.
However, during the development of the unified desktop software solution, there might
be some issues, which could arise from ethical, regulatory, legal and social compliance factors. A
discussion would be put forward on the various issues that could occur and then a proper
application of the best industrial practices and laws would be included henceforth.
Ethical Compliance Issues with Fresh Air – The issues based on maintaining
compliance based on the ethical grounds are discussed as follows:
1. Since the unified desktop solution would be designed for the staff, hence it would need
to be designed in such a manner that it would help the staff to manage customer data within the
helpdesk. These staff would also perform telephonic conversations, offer walk-in, chat and email
support. The total range of services would be based on managing the requests placed by
customers by performing an analysis over the market and providing them with better solutions.
In the above table, ratings are followed as: (1-5 = Low or Insignificant; 5-7 Medium or
Moderate; 7 or above = Significant or Disastrous)
2. Summary of ethical, social, legal and regulatory compliance issues related to Fresh Air
In relation to the case study, it has been discussed that Fresh Air has been planning to
implement and deploy for a unified desktop solution that would employ the use of cloud
computing solutions for storing every day data. The different employees within the IT team
would form a collaboration and develop the software in the in-house department (Khan and Khan
2017). The IT team will also be responsible for performing in-house support to all staff and
services, which would be occurring within the firm. After the deployment of the software
solution for the business, a comprehensive training would be provided to all employees and
existing staff.
However, during the development of the unified desktop software solution, there might
be some issues, which could arise from ethical, regulatory, legal and social compliance factors. A
discussion would be put forward on the various issues that could occur and then a proper
application of the best industrial practices and laws would be included henceforth.
Ethical Compliance Issues with Fresh Air – The issues based on maintaining
compliance based on the ethical grounds are discussed as follows:
1. Since the unified desktop solution would be designed for the staff, hence it would need
to be designed in such a manner that it would help the staff to manage customer data within the
helpdesk. These staff would also perform telephonic conversations, offer walk-in, chat and email
support. The total range of services would be based on managing the requests placed by
customers by performing an analysis over the market and providing them with better solutions.

6INFORMATION GOVERNANCE FOR FRESH AIR
The customer data might be breached by hackers monitoring the internal network of the
company. In order to secure the data of customers, the IT team at Fresh Air should abide by the
Data Protection Act 2018 (DPA) set within the UK data protection legislation and General Data
Protection Regulation (GDPR) (Act 2018). Based on these, the ethical ways of data governance
would remain compliant accordingly.
2. The software solution that is being developed by the IT team at Fresh Air would face
some form of interrelated issues comprising of patent, trademark, competitive advantages law
and copyright. Hence, the IT team should be aware of such form of ethical issues arising within
the system and thus develop strategies that could be effective for proper development of
software.
3. After the deployment of the product, copyright issues could arise within the system.
Hence, the source code should be protected with the help of proper copyright, which would be
beneficial for the company and thus help in the securing of intellectual property. The Copyright,
Design and Patent Act (1998) would help in forming a copyright law for each kind of
technological work used within the smartphones, tablets and other mobile devices (Grant 2016).
Regulatory Compliance Issues with Fresh Air – During the defining of the unified
desktop solution for Fresh Air, it can be discussed that some issues could be faced with
compliance with the regulatory aspects of software development. Improper form of coordinated
efforts in relation to development of software by the multiple integrated teams could lead to
issues (Sadiq and Governatori 2015). Improper skills within the employees in relation to
governance, inter-dependent capabilities and risk management strategies could lead to high
issues in the development phase. Low experience within the people and improper processes
The customer data might be breached by hackers monitoring the internal network of the
company. In order to secure the data of customers, the IT team at Fresh Air should abide by the
Data Protection Act 2018 (DPA) set within the UK data protection legislation and General Data
Protection Regulation (GDPR) (Act 2018). Based on these, the ethical ways of data governance
would remain compliant accordingly.
2. The software solution that is being developed by the IT team at Fresh Air would face
some form of interrelated issues comprising of patent, trademark, competitive advantages law
and copyright. Hence, the IT team should be aware of such form of ethical issues arising within
the system and thus develop strategies that could be effective for proper development of
software.
3. After the deployment of the product, copyright issues could arise within the system.
Hence, the source code should be protected with the help of proper copyright, which would be
beneficial for the company and thus help in the securing of intellectual property. The Copyright,
Design and Patent Act (1998) would help in forming a copyright law for each kind of
technological work used within the smartphones, tablets and other mobile devices (Grant 2016).
Regulatory Compliance Issues with Fresh Air – During the defining of the unified
desktop solution for Fresh Air, it can be discussed that some issues could be faced with
compliance with the regulatory aspects of software development. Improper form of coordinated
efforts in relation to development of software by the multiple integrated teams could lead to
issues (Sadiq and Governatori 2015). Improper skills within the employees in relation to
governance, inter-dependent capabilities and risk management strategies could lead to high
issues in the development phase. Low experience within the people and improper processes
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION GOVERNANCE FOR FRESH AIR
could also lead to various issues in the progress work over the software. New form of regulatory
environment could lead to issues in adjusting to the scenario and thus lead to improper form of
software development aspects.
Hence, in order to incur the best results over the solving of regulatory compliance issues,
it would be discussed as appropriate for developing accurate kind of compliance requirements.
Special kind of governance facilities should also be provided and hence the risk management
aspects should be properly be improved. Moreover, experienced team members should be
responsible for designing the work over the development of a unified business solution.
Legal Compliance Issues with Fresh Air – Since, Fresh Air primarily deal with
customers from all across the world, hence, the factor of compliance with the legal factors would
be considered as highly helpful. However, in the present times, when the company has been
deciding over the process of developing a solution for the staff in order to include all kind of
functionalities and help them in solving the queries raised in the helpdesk, hence the company
would have to focus on the legal aspects. In order to design the desktop software solution in a
legal form, the Freedom of Information Act (2000) should be the guiding light towards this
factor. This would lead to transparency within the data governed for the public sector. Based on
this law, customer data cannot be requested without prior permission and thus be used for any
unethical means (Noto La Diega 2018). Information stored within the software would be
confidential in nature and would be under restricted access from the data archive.
Some of the issues that are faced in this aspect are being discussed as follows:
1. There might be some situations in which the involved IT teams would ignore the
compliance issues and thus they would not follow certain legal standards. However, ignoring the
could also lead to various issues in the progress work over the software. New form of regulatory
environment could lead to issues in adjusting to the scenario and thus lead to improper form of
software development aspects.
Hence, in order to incur the best results over the solving of regulatory compliance issues,
it would be discussed as appropriate for developing accurate kind of compliance requirements.
Special kind of governance facilities should also be provided and hence the risk management
aspects should be properly be improved. Moreover, experienced team members should be
responsible for designing the work over the development of a unified business solution.
Legal Compliance Issues with Fresh Air – Since, Fresh Air primarily deal with
customers from all across the world, hence, the factor of compliance with the legal factors would
be considered as highly helpful. However, in the present times, when the company has been
deciding over the process of developing a solution for the staff in order to include all kind of
functionalities and help them in solving the queries raised in the helpdesk, hence the company
would have to focus on the legal aspects. In order to design the desktop software solution in a
legal form, the Freedom of Information Act (2000) should be the guiding light towards this
factor. This would lead to transparency within the data governed for the public sector. Based on
this law, customer data cannot be requested without prior permission and thus be used for any
unethical means (Noto La Diega 2018). Information stored within the software would be
confidential in nature and would be under restricted access from the data archive.
Some of the issues that are faced in this aspect are being discussed as follows:
1. There might be some situations in which the involved IT teams would ignore the
compliance issues and thus they would not follow certain legal standards. However, ignoring the

8INFORMATION GOVERNANCE FOR FRESH AIR
compliance issues based on legal grounds and not following the standards would thus lead to
sever rise in costs at later phases.
2. There are many software, which are not purchased through license. Hence, this could
lead future complications in dealing with lawsuits and thus lead to certain disruption in the
software design phases. With the rise in such form of issues, it could be discussed that the factor
of legal compliance would need to be strictly followed by developers and assurance should be
provided to them that the software that is being used by them should be made in proper
compliance with the legal standards.
3. Taking proper actions at a later stage during the lifecycle of the project could take the
certain form of internal or external auditing. This could further lead to tremendous negative
impacts towards the final stages of product testing and also lead to delay within the process of
quality assurance. The given option could lead to incurring of higher costs based on the
professional services. The cost incurred over the necessary changes to be made would also incur
the stages of re-auditing and re-testing. Although the discussed option would be yielding some
kind of results, it does not impact towards the overall workflow. It could also impact the
rendering process and thus could ensure a cost effective process (Barabanov et al. 2015). Thus, a
prolonged testing process could lead to prolonged time of the completion of the project lifecycle.
This would further lead to delays in the delivering the final outcome of the product.
4. Improper form of periodic auditing could lead to improper outcomes during the
delivery phase of the software. Improper delays within the software development phase could
lead to serious implications over the company. Certain lease of software usage might be need to
extended, which would incur a high cost at the end of the software development process. Hence,
compliance issues based on legal grounds and not following the standards would thus lead to
sever rise in costs at later phases.
2. There are many software, which are not purchased through license. Hence, this could
lead future complications in dealing with lawsuits and thus lead to certain disruption in the
software design phases. With the rise in such form of issues, it could be discussed that the factor
of legal compliance would need to be strictly followed by developers and assurance should be
provided to them that the software that is being used by them should be made in proper
compliance with the legal standards.
3. Taking proper actions at a later stage during the lifecycle of the project could take the
certain form of internal or external auditing. This could further lead to tremendous negative
impacts towards the final stages of product testing and also lead to delay within the process of
quality assurance. The given option could lead to incurring of higher costs based on the
professional services. The cost incurred over the necessary changes to be made would also incur
the stages of re-auditing and re-testing. Although the discussed option would be yielding some
kind of results, it does not impact towards the overall workflow. It could also impact the
rendering process and thus could ensure a cost effective process (Barabanov et al. 2015). Thus, a
prolonged testing process could lead to prolonged time of the completion of the project lifecycle.
This would further lead to delays in the delivering the final outcome of the product.
4. Improper form of periodic auditing could lead to improper outcomes during the
delivery phase of the software. Improper delays within the software development phase could
lead to serious implications over the company. Certain lease of software usage might be need to
extended, which would incur a high cost at the end of the software development process. Hence,

9INFORMATION GOVERNANCE FOR FRESH AIR
issues that would be discovered should be dealt carefully and re-testing should also be done in
proper time. Policy violations could be made, which could ultimately lead to several kind of
delays in delivering the software outcomes.
5. Violations made in the area of software licenses should be detected in proper time and
thus should be reported at the earliest. Based on performing this action, it would be greatly
helpful for determining the cost of correcting those errors. Moreover, replacement in the code
sections could also be done immediately and in proper timing. Necessary corrections in the areas
of software development include replacement or code changes, justification made for the
selection of the appropriate code and re-testing of the individual components would need to be
done accordingly (Mesquida and Mas 2015). However, this proper could also be designed with
the help of automated tools to determine the proper license setup of the software, which are
being used in the development rooms. Detection of possible kind of violations in the real-time
scenarios would be considered as highly cost-efficient for the company and also lead to lowest
form of risk options during the long term business prospects.
Social Compliance Issues with Fresh Air – The proper handling of issues raised while
maintaining of social compliance would be considered as highly important. Safeguarding the
reputation of the brand would be considered as highly important while delivering the integral
communications that would need to be considered. Hence, in order to address the issues arising
due to social compliance within the software development phase there should be a proper
development of strategy that needs to be focused on greatly by the IT development team.
1. Issues arising in the aspect of social compliance might be highly great in nature. The
software that is been developed should be developed in such a manner that it would match
issues that would be discovered should be dealt carefully and re-testing should also be done in
proper time. Policy violations could be made, which could ultimately lead to several kind of
delays in delivering the software outcomes.
5. Violations made in the area of software licenses should be detected in proper time and
thus should be reported at the earliest. Based on performing this action, it would be greatly
helpful for determining the cost of correcting those errors. Moreover, replacement in the code
sections could also be done immediately and in proper timing. Necessary corrections in the areas
of software development include replacement or code changes, justification made for the
selection of the appropriate code and re-testing of the individual components would need to be
done accordingly (Mesquida and Mas 2015). However, this proper could also be designed with
the help of automated tools to determine the proper license setup of the software, which are
being used in the development rooms. Detection of possible kind of violations in the real-time
scenarios would be considered as highly cost-efficient for the company and also lead to lowest
form of risk options during the long term business prospects.
Social Compliance Issues with Fresh Air – The proper handling of issues raised while
maintaining of social compliance would be considered as highly important. Safeguarding the
reputation of the brand would be considered as highly important while delivering the integral
communications that would need to be considered. Hence, in order to address the issues arising
due to social compliance within the software development phase there should be a proper
development of strategy that needs to be focused on greatly by the IT development team.
1. Issues arising in the aspect of social compliance might be highly great in nature. The
software that is been developed should be developed in such a manner that it would match
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10INFORMATION GOVERNANCE FOR FRESH AIR
properly with the requirements of the social media environments. This could be performed by
using secure login mechanisms, maintaining content validation and establishing a proper
workflow mechanism. It should also be able to perform flexible levels of permission. The
software might be linked to social media platforms as customers might contact the Fresh Air
Company via the social media platforms that are meant for the company. Hence, the social media
content that would be applicable should be meant with regulatory requirements. It should also
support the facility automated form of email alerts and social media archiving.
2. Securing the reputation of the brand while delivering the software solution would also
be considered as highly appropriate. Modification within the content delivered should be
manageable to a great extent. The developers responsible for developing the desktop software
solution should be incorporated with keyword dictionaries based on both outbound and inbound
messages that would help in providing of immediate alerts in case some abusive or sensitive
phases would be detected. Upon detection, these phrases should be either hidden or completely
be deleted.
3. Crisis control mechanisms should be installed within the system. This would help in
instant locking down of scheduled messages, revoking or giving certain form of user access.
Handling of large volumes of messages through the social media during the crisis situations
would be considered as appropriate. Responding to such messages in proper time would also be
considered as highly necessary. This would help in maintaining of proper record over the activity
being performed within the system. Every activity or communication that would be maintained
within the system and processes should be tracked in order to detect any form of violation within
the system. This would also help in resolving such issues based on a proper analysis over the
business processes accordingly.
properly with the requirements of the social media environments. This could be performed by
using secure login mechanisms, maintaining content validation and establishing a proper
workflow mechanism. It should also be able to perform flexible levels of permission. The
software might be linked to social media platforms as customers might contact the Fresh Air
Company via the social media platforms that are meant for the company. Hence, the social media
content that would be applicable should be meant with regulatory requirements. It should also
support the facility automated form of email alerts and social media archiving.
2. Securing the reputation of the brand while delivering the software solution would also
be considered as highly appropriate. Modification within the content delivered should be
manageable to a great extent. The developers responsible for developing the desktop software
solution should be incorporated with keyword dictionaries based on both outbound and inbound
messages that would help in providing of immediate alerts in case some abusive or sensitive
phases would be detected. Upon detection, these phrases should be either hidden or completely
be deleted.
3. Crisis control mechanisms should be installed within the system. This would help in
instant locking down of scheduled messages, revoking or giving certain form of user access.
Handling of large volumes of messages through the social media during the crisis situations
would be considered as appropriate. Responding to such messages in proper time would also be
considered as highly necessary. This would help in maintaining of proper record over the activity
being performed within the system. Every activity or communication that would be maintained
within the system and processes should be tracked in order to detect any form of violation within
the system. This would also help in resolving such issues based on a proper analysis over the
business processes accordingly.

11INFORMATION GOVERNANCE FOR FRESH AIR
4. The accounts of the staff needs to be protected based on secure encryption techniques.
Individual kind of user login operations and tiered access levels would be helpful towards
assuring that only authorized staff would be able to perform login operations within the system.
They would thus be able to access the corporate profiles of social media. There are different kind
of permission levels when the development of the software would be performed. Access rights
would also be need to be provided based on performing the high form of user management and
control operations for the purpose of handling the large or dispersed teams based on the users of
social media. The IT teams should be able to perform rigorous form of penetration testing for the
purpose of ensuring that the highest standards of IT governance should be maintained. The
penetration testing should be compliant with the PCI DSS Requirement 11.3.4, which would be
used for validation of segmented controls (Information Supplement: Penetration Testing
Guidance 2020). They would also support methods, which would be effective, isolate each form
of out-of-scope activities and operational in nature.
The above discussion thus focuses on the different areas from which issues could arise
due to non-compliance. In order to compliant with the compliance factors based within the
software development industry, the IT team at Fresh Air should also specify the use of the
software with ISO 27001. This is considered as one of the best international standard, which
would propose a specification for the Information Security Management System (ISMS). The
use of this approach would help Fresh Air to manage their information and data while securing
them with the alignment of the best and standard industry practices.
4. The accounts of the staff needs to be protected based on secure encryption techniques.
Individual kind of user login operations and tiered access levels would be helpful towards
assuring that only authorized staff would be able to perform login operations within the system.
They would thus be able to access the corporate profiles of social media. There are different kind
of permission levels when the development of the software would be performed. Access rights
would also be need to be provided based on performing the high form of user management and
control operations for the purpose of handling the large or dispersed teams based on the users of
social media. The IT teams should be able to perform rigorous form of penetration testing for the
purpose of ensuring that the highest standards of IT governance should be maintained. The
penetration testing should be compliant with the PCI DSS Requirement 11.3.4, which would be
used for validation of segmented controls (Information Supplement: Penetration Testing
Guidance 2020). They would also support methods, which would be effective, isolate each form
of out-of-scope activities and operational in nature.
The above discussion thus focuses on the different areas from which issues could arise
due to non-compliance. In order to compliant with the compliance factors based within the
software development industry, the IT team at Fresh Air should also specify the use of the
software with ISO 27001. This is considered as one of the best international standard, which
would propose a specification for the Information Security Management System (ISMS). The
use of this approach would help Fresh Air to manage their information and data while securing
them with the alignment of the best and standard industry practices.

12INFORMATION GOVERNANCE FOR FRESH AIR
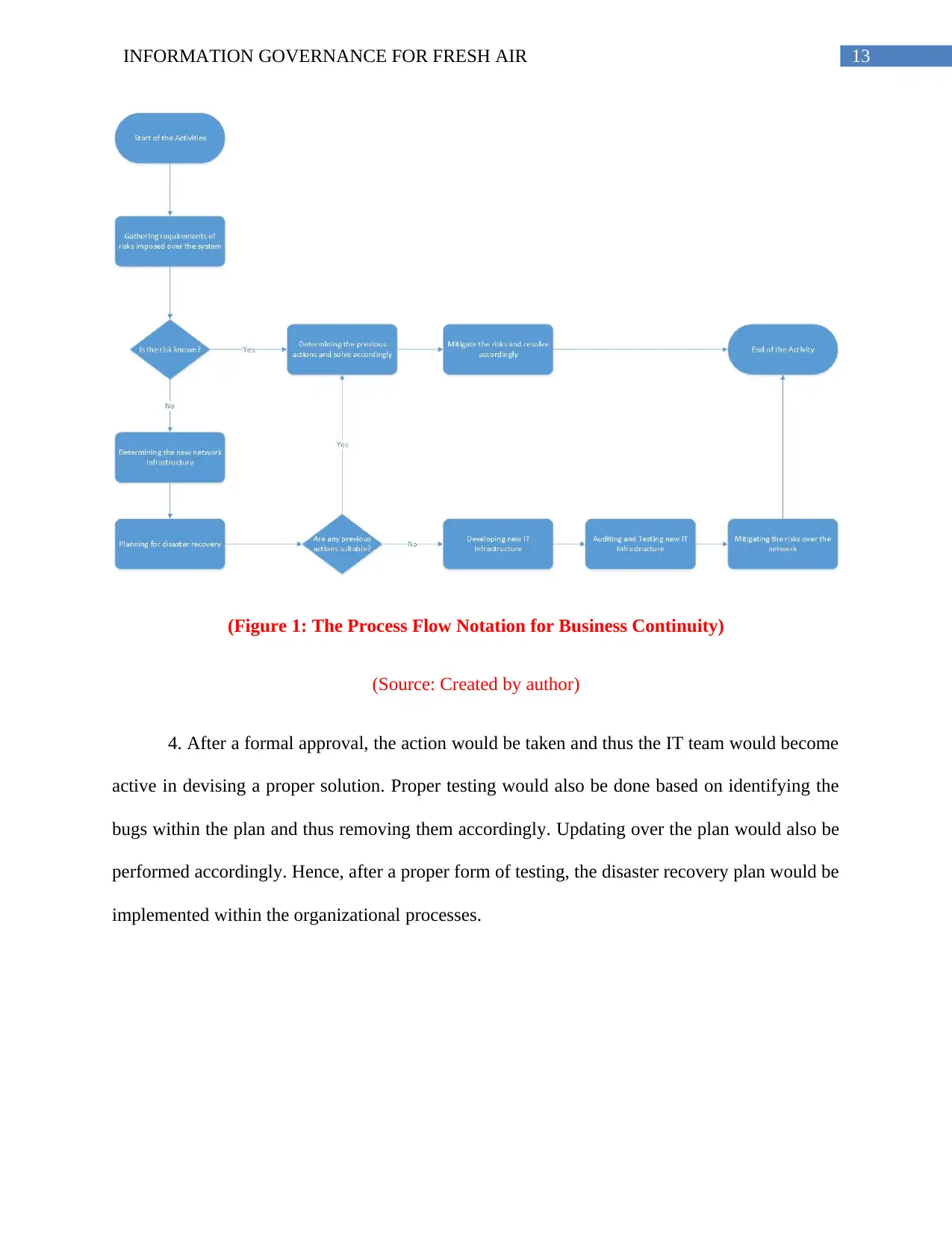
3. Poster undertaking Disaster Recovery Steps
The different disaster recovery steps that could be approached during the development of
the unified software solution for the firm have been discussed as follows:
1. Based on using the process flow notation, the most important and primary step within
the disaster recovery plan would be based on gathering requirements properly. Different kind of
network infrastructure documents would need to be provided, which would help in proper
estimation of business risks and determination of critical assets in relation to the organization.
2. In the secondary step, the IT team should conduct a brief form of disaster recovery
analysis over the collected documents. This would help the team in planning for the outages and
incidents that would have happened previously within the company. This analysis would also
lead the IT team to understand about the possible actions that might have been taken previously.
3. After analyzing the scenario, a detailed analysis would also be need to be made over
the future course of actions that would need to be determined. Identification of the proper team,
which would be able to handle every situation in a proper manner have also been discussed.
After devising the strategic plan, the management at Fresh Air would decide over approving the
disaster recovery plan.
3. Poster undertaking Disaster Recovery Steps
The different disaster recovery steps that could be approached during the development of
the unified software solution for the firm have been discussed as follows:
1. Based on using the process flow notation, the most important and primary step within
the disaster recovery plan would be based on gathering requirements properly. Different kind of
network infrastructure documents would need to be provided, which would help in proper
estimation of business risks and determination of critical assets in relation to the organization.
2. In the secondary step, the IT team should conduct a brief form of disaster recovery
analysis over the collected documents. This would help the team in planning for the outages and
incidents that would have happened previously within the company. This analysis would also
lead the IT team to understand about the possible actions that might have been taken previously.
3. After analyzing the scenario, a detailed analysis would also be need to be made over
the future course of actions that would need to be determined. Identification of the proper team,
which would be able to handle every situation in a proper manner have also been discussed.
After devising the strategic plan, the management at Fresh Air would decide over approving the
disaster recovery plan.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13INFORMATION GOVERNANCE FOR FRESH AIR
(Figure 1: The Process Flow Notation for Business Continuity)
(Source: Created by author)
4. After a formal approval, the action would be taken and thus the IT team would become
active in devising a proper solution. Proper testing would also be done based on identifying the
bugs within the plan and thus removing them accordingly. Updating over the plan would also be
performed accordingly. Hence, after a proper form of testing, the disaster recovery plan would be
implemented within the organizational processes.
(Figure 1: The Process Flow Notation for Business Continuity)
(Source: Created by author)
4. After a formal approval, the action would be taken and thus the IT team would become
active in devising a proper solution. Proper testing would also be done based on identifying the
bugs within the plan and thus removing them accordingly. Updating over the plan would also be
performed accordingly. Hence, after a proper form of testing, the disaster recovery plan would be
implemented within the organizational processes.

14INFORMATION GOVERNANCE FOR FRESH AIR
Continuity Plan
The Business Continuity Plan (BCP) have been developed in relevance to the Disaster
Recovery Plan. An overview over the BCP including some major sections are described below:
Section Content
1.0 Staffing Details
1.0.1 Contact Details of staff
1.0.2 Responsibilities of staff
1.0.3 Useful contact number and details
2.0 Planning over Business Procedures
2.0.1 Defining the activation process
2.0.2 Managing workspace loss
2.0.3 Managing network loss
2.0.4 Managing business downtime
2.0.5 Managing other resources
3.0 Other supportable information
3.0.1 Managing staff welfare
3.0.2 Managing communication
3.0.3 Presenting information towards clients
4. Reflection on Portfolio
Based on the discussed scenario, it can be discussed that the portfolio have been planned
properly to include each form of discussions that could be in relation to the development of
software. The discussion in the portfolio primarily puts emphasis over the development of the
software solution as proposed and planned by Fresh Air. The company helps in supporting their
customers with a diverse range of business solutions to their customers. In the above discussion,
it has been focused that Fresh Air focuses on the development of a unified software solution that
would be implemented within the helpdesk and thus would be able to support the staff.
In the initial discussion of the portfolio, an analysis over the risk assessment process in
relation to the IT services have been discussed. Data security is also a major concern in relation
to the securing the internal data in relation the customers. Hence, in this aspect it can be
Continuity Plan
The Business Continuity Plan (BCP) have been developed in relevance to the Disaster
Recovery Plan. An overview over the BCP including some major sections are described below:
Section Content
1.0 Staffing Details
1.0.1 Contact Details of staff
1.0.2 Responsibilities of staff
1.0.3 Useful contact number and details
2.0 Planning over Business Procedures
2.0.1 Defining the activation process
2.0.2 Managing workspace loss
2.0.3 Managing network loss
2.0.4 Managing business downtime
2.0.5 Managing other resources
3.0 Other supportable information
3.0.1 Managing staff welfare
3.0.2 Managing communication
3.0.3 Presenting information towards clients
4. Reflection on Portfolio
Based on the discussed scenario, it can be discussed that the portfolio have been planned
properly to include each form of discussions that could be in relation to the development of
software. The discussion in the portfolio primarily puts emphasis over the development of the
software solution as proposed and planned by Fresh Air. The company helps in supporting their
customers with a diverse range of business solutions to their customers. In the above discussion,
it has been focused that Fresh Air focuses on the development of a unified software solution that
would be implemented within the helpdesk and thus would be able to support the staff.
In the initial discussion of the portfolio, an analysis over the risk assessment process in
relation to the IT services have been discussed. Data security is also a major concern in relation
to the securing the internal data in relation the customers. Hence, in this aspect it can be

15INFORMATION GOVERNANCE FOR FRESH AIR
discussed that the discussion primarily focused on the different risks that could approach towards
the systems. Different risks that have been discussed could lead to tremendous issues over the
business processes. The risk mitigation steps and approaches have also been discussed, which
could lead to proper form of management of the internal processes. Hence, this can be
considered as the major strength of the portfolio in which the defined risks have been discussed
properly and proper risk mitigation steps have also been discussed properly.
The next part of the discussion focuses on the determining a summary of legal, ethical,
social, regulatory compliance issues during the software development lifecycle. Different issues
that could arise on non-compliance with the aspects have also been discussed and thus proper
measures have also been discussed properly. An indication of consequences towards the
organization when non-compliance would be made towards the system. Hence, suggested
controls based on following and taking necessary actions for performing proper compliance with
the issues have also been discussed properly.
The third part of the discussion also focuses on taking of necessary steps that would need
to be taken during performing disaster recovery. During performing or taking actions during
disaster recovery, responsibilities should be taken by individuals responsible for work within the
IT team and hence a proper action have been focused based on performing recovery over the
disaster being made. The target audience have also been clearly described and the process have
also been discussed, which could be taken in order to recover from the disaster that could be
made from external or internal processes.
Based on the discussion over such aspects, it can be discussed that in the future learning
from the case, certain actions could be presented in a well-formed manner. The future learning
discussed that the discussion primarily focused on the different risks that could approach towards
the systems. Different risks that have been discussed could lead to tremendous issues over the
business processes. The risk mitigation steps and approaches have also been discussed, which
could lead to proper form of management of the internal processes. Hence, this can be
considered as the major strength of the portfolio in which the defined risks have been discussed
properly and proper risk mitigation steps have also been discussed properly.
The next part of the discussion focuses on the determining a summary of legal, ethical,
social, regulatory compliance issues during the software development lifecycle. Different issues
that could arise on non-compliance with the aspects have also been discussed and thus proper
measures have also been discussed properly. An indication of consequences towards the
organization when non-compliance would be made towards the system. Hence, suggested
controls based on following and taking necessary actions for performing proper compliance with
the issues have also been discussed properly.
The third part of the discussion also focuses on taking of necessary steps that would need
to be taken during performing disaster recovery. During performing or taking actions during
disaster recovery, responsibilities should be taken by individuals responsible for work within the
IT team and hence a proper action have been focused based on performing recovery over the
disaster being made. The target audience have also been clearly described and the process have
also been discussed, which could be taken in order to recover from the disaster that could be
made from external or internal processes.
Based on the discussion over such aspects, it can be discussed that in the future learning
from the case, certain actions could be presented in a well-formed manner. The future learning
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16INFORMATION GOVERNANCE FOR FRESH AIR
should be primarily be focused on the discussions based on understanding the exact risks that
could pose harm during the software development phase and also during deployment process.
Moreover, the processes in which the software solution could be presented could be designed
based on determining aspects of a project. A well-planned project would be able to discuss each
of the steps that would be incurred during the process of development of the unified desktop
software to be installed at the helpdesk for the staff. Hence, the development of project
management skills would also be enhanced and thus it would be helpful for learners to develop
future skills and would be able to undertake the project in a well-planned manner. Knowledge in
terms of cost allocation and allocating of resources to particular activities within the project
would also be discussed and learnt properly that would help in developing the software
accordingly and make it as a success for the company.
should be primarily be focused on the discussions based on understanding the exact risks that
could pose harm during the software development phase and also during deployment process.
Moreover, the processes in which the software solution could be presented could be designed
based on determining aspects of a project. A well-planned project would be able to discuss each
of the steps that would be incurred during the process of development of the unified desktop
software to be installed at the helpdesk for the staff. Hence, the development of project
management skills would also be enhanced and thus it would be helpful for learners to develop
future skills and would be able to undertake the project in a well-planned manner. Knowledge in
terms of cost allocation and allocating of resources to particular activities within the project
would also be discussed and learnt properly that would help in developing the software
accordingly and make it as a success for the company.

17INFORMATION GOVERNANCE FOR FRESH AIR
References
Act, D.P., 2018. Policy: DATA PROTECTION POLICY. Policy.
Barabanov, A., Markov, A., Fadin, A., Tsirlov, V. and Shakhalov, I., 2015, September. Synthesis
of secure software development controls. In Proceedings of the 8th International Conference on
Security of Information and Networks (pp. 93-97).
El Kateb, D., Zannone, N., Moawad, A., Caire, P., Nain, G., Mouelhi, T. and Le Traon, Y., 2015.
Conviviality-driven access control policy. Requirements Engineering, 20(4), pp.363-382.
Grant, R.M., 2016. Contemporary strategy analysis: Text and cases edition. John Wiley & Sons.
Groomer, S.M. and Murthy, U.S., 2018. Continuous auditing of database applications: An
embedded audit module approach. Continuous Auditing, pp.105-124.
Kenkre, P.S., Pai, A. and Colaco, L., 2015. Real time intrusion detection and prevention system.
In Proceedings of the 3rd International Conference on Frontiers of Intelligent Computing:
Theory and Applications (FICTA) 2014 (pp. 405-411). Springer, Cham.
Khan, S.U. and Khan, A.W., 2017. Critical challenges in managing offshore software
development outsourcing contract from vendors' perspectives. IET software, 11(1), pp.1-11.
Kupiainen, E., Mäntylä, M.V. and Itkonen, J., 2015. Using metrics in Agile and Lean Software
Development–A systematic literature review of industrial studies. Information and Software
Technology, 62, pp.143-163.
References
Act, D.P., 2018. Policy: DATA PROTECTION POLICY. Policy.
Barabanov, A., Markov, A., Fadin, A., Tsirlov, V. and Shakhalov, I., 2015, September. Synthesis
of secure software development controls. In Proceedings of the 8th International Conference on
Security of Information and Networks (pp. 93-97).
El Kateb, D., Zannone, N., Moawad, A., Caire, P., Nain, G., Mouelhi, T. and Le Traon, Y., 2015.
Conviviality-driven access control policy. Requirements Engineering, 20(4), pp.363-382.
Grant, R.M., 2016. Contemporary strategy analysis: Text and cases edition. John Wiley & Sons.
Groomer, S.M. and Murthy, U.S., 2018. Continuous auditing of database applications: An
embedded audit module approach. Continuous Auditing, pp.105-124.
Kenkre, P.S., Pai, A. and Colaco, L., 2015. Real time intrusion detection and prevention system.
In Proceedings of the 3rd International Conference on Frontiers of Intelligent Computing:
Theory and Applications (FICTA) 2014 (pp. 405-411). Springer, Cham.
Khan, S.U. and Khan, A.W., 2017. Critical challenges in managing offshore software
development outsourcing contract from vendors' perspectives. IET software, 11(1), pp.1-11.
Kupiainen, E., Mäntylä, M.V. and Itkonen, J., 2015. Using metrics in Agile and Lean Software
Development–A systematic literature review of industrial studies. Information and Software
Technology, 62, pp.143-163.

18INFORMATION GOVERNANCE FOR FRESH AIR
Lakshmi, H., Namitha, S., Gopalan, S., Sanjay, H.A., Chandrashekaran, K. and Bhaskar, A.,
2015, October. Risk based access control in cloud computing. In 2015 International Conference
on Green Computing and Internet of Things (ICGCIoT) (pp. 1502-1505). IEEE.
Mesquida, A.L. and Mas, A., 2015. Implementing information security best practices on
software lifecycle processes: The ISO/IEC 15504 Security Extension. Computers & Security, 48,
pp.19-34.
Noto La Diega, G., 2018. Against the dehumanisation of decision-making–algorithmic decisions
at the crossroads of intellectual property, data protection, and freedom of information. Against
the Dehumanisation of Decision-Making–Algorithmic Decisions at the Crossroads of Intellectual
Property, Data Protection, and Freedom of Information (May 31, 2018), 9.
Pcisecuritystandards.org. 2020. [online] Available at:
<https://www.pcisecuritystandards.org/documents/Penetration_Testing_Guidance_March_2015.
pdf> [Accessed 10 April 2020].
Sadiq, S. and Governatori, G., 2015. Managing regulatory compliance in business processes.
In Handbook on Business Process Management 2 (pp. 265-288). Springer, Berlin, Heidelberg.
Sallam, H., 2015. Cyber security risk assessment using multi fuzzy inference system. IJEIT, 4(8),
pp.13-19.
Yamato, Y., Nishizawa, Y., Muroi, M. and Tanaka, K., 2015. Development of resource
management server for production IaaS services based on OpenStack. Journal of Information
Processing, 23(1), pp.58-66.
Lakshmi, H., Namitha, S., Gopalan, S., Sanjay, H.A., Chandrashekaran, K. and Bhaskar, A.,
2015, October. Risk based access control in cloud computing. In 2015 International Conference
on Green Computing and Internet of Things (ICGCIoT) (pp. 1502-1505). IEEE.
Mesquida, A.L. and Mas, A., 2015. Implementing information security best practices on
software lifecycle processes: The ISO/IEC 15504 Security Extension. Computers & Security, 48,
pp.19-34.
Noto La Diega, G., 2018. Against the dehumanisation of decision-making–algorithmic decisions
at the crossroads of intellectual property, data protection, and freedom of information. Against
the Dehumanisation of Decision-Making–Algorithmic Decisions at the Crossroads of Intellectual
Property, Data Protection, and Freedom of Information (May 31, 2018), 9.
Pcisecuritystandards.org. 2020. [online] Available at:
<https://www.pcisecuritystandards.org/documents/Penetration_Testing_Guidance_March_2015.
pdf> [Accessed 10 April 2020].
Sadiq, S. and Governatori, G., 2015. Managing regulatory compliance in business processes.
In Handbook on Business Process Management 2 (pp. 265-288). Springer, Berlin, Heidelberg.
Sallam, H., 2015. Cyber security risk assessment using multi fuzzy inference system. IJEIT, 4(8),
pp.13-19.
Yamato, Y., Nishizawa, Y., Muroi, M. and Tanaka, K., 2015. Development of resource
management server for production IaaS services based on OpenStack. Journal of Information
Processing, 23(1), pp.58-66.
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





