Information Security Assignment: Firewall Implementation and Analysis
VerifiedAdded on 2023/03/17
|9
|1040
|63
Report
AI Summary
This assignment report focuses on securing a system using an IPTable firewall. It includes practical configuration steps such as rejecting SSH packets, allowing SSH remote connections, denying ping, rejecting traffic to port 80, blocking incoming traffic, and allowing inbound but rejecting outbound traffic through port 80. The report then discusses the advantages and disadvantages of using firewalls, specifically with IPTable, and suggests ways to overcome the disadvantages. Finally, it examines the role and significance of a circuit relay firewall in securing communication, emphasizing its function in validating connections and enforcing real-time packet screening. The assignment demonstrates a comprehensive understanding of firewall implementation and network security principles.

Running head: INFORMATION SECURITY 1
Information Security
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
INTRODUCTION
Information Security
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
INTRODUCTION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: INFORMATION SECURITY 2
The assignment in this document is on securing system for the IP enabled firewall. In this
assignment, deliverable include the configuration and the testing of our firewall. The assignment
uses IP tables to deliver the task. The second section of the assignment focuses on discussing the
various advantages and disadvantages that normal firewall has over the IP Tables
implementation. The last section provides an overview of a circuit relay firewall, the various
roles it play and the significance it has in overall securing of communication
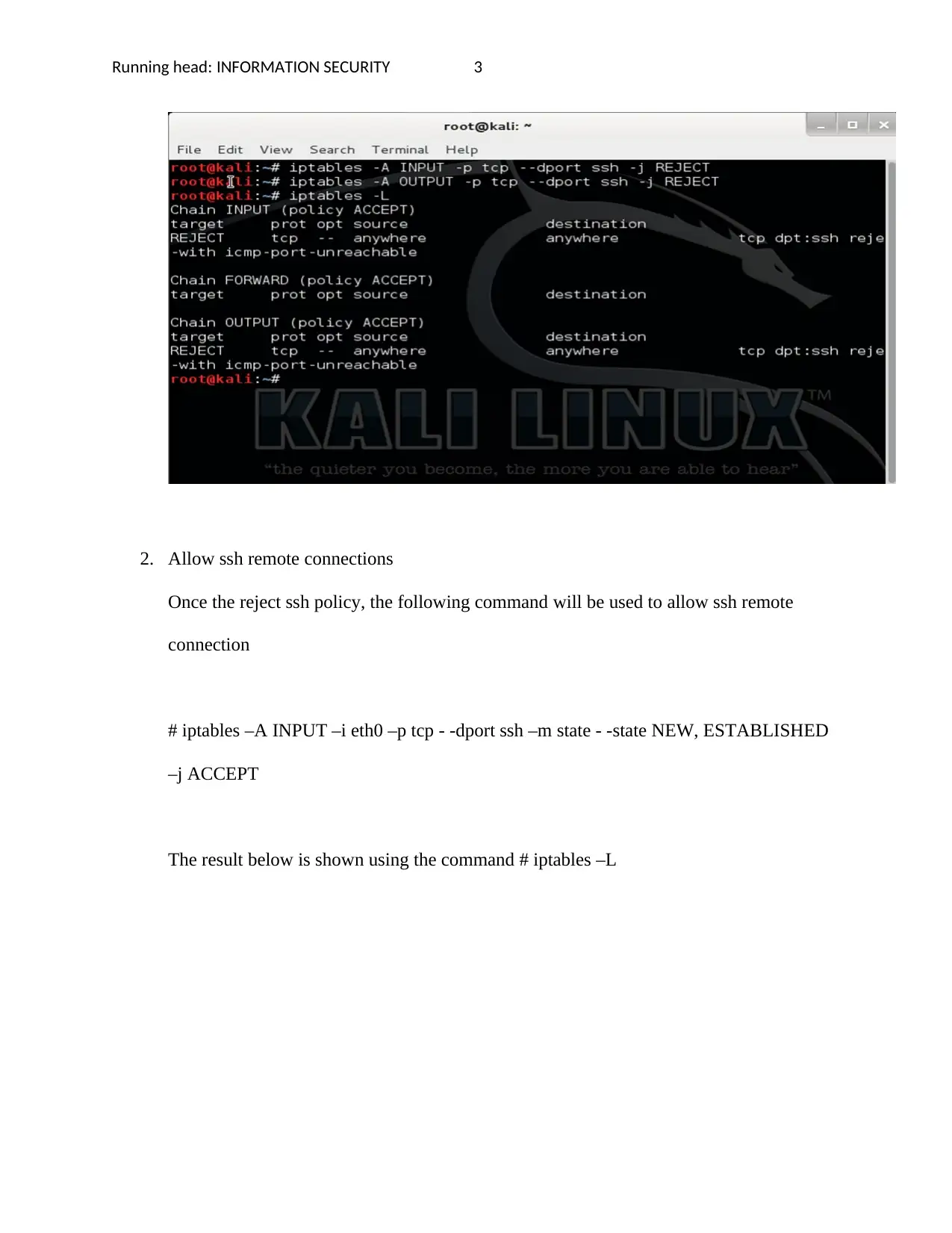
1. Reject all ssh packages
The command below is used
# iptables –A INPUT –p tcp - -dport ssh –j REJECT
# iptables –A INPUT –p tcp - -dport ssh –j REJECT will reject all ssh packages
Here, two policies get applied, the INPUT and the OUTPUT, the REJECT option will
reject the above policy applied.
# iptables –L is used to show the results as shown in the screenshot below
The assignment in this document is on securing system for the IP enabled firewall. In this
assignment, deliverable include the configuration and the testing of our firewall. The assignment
uses IP tables to deliver the task. The second section of the assignment focuses on discussing the
various advantages and disadvantages that normal firewall has over the IP Tables
implementation. The last section provides an overview of a circuit relay firewall, the various
roles it play and the significance it has in overall securing of communication
1. Reject all ssh packages
The command below is used
# iptables –A INPUT –p tcp - -dport ssh –j REJECT
# iptables –A INPUT –p tcp - -dport ssh –j REJECT will reject all ssh packages
Here, two policies get applied, the INPUT and the OUTPUT, the REJECT option will
reject the above policy applied.
# iptables –L is used to show the results as shown in the screenshot below
Running head: INFORMATION SECURITY 3
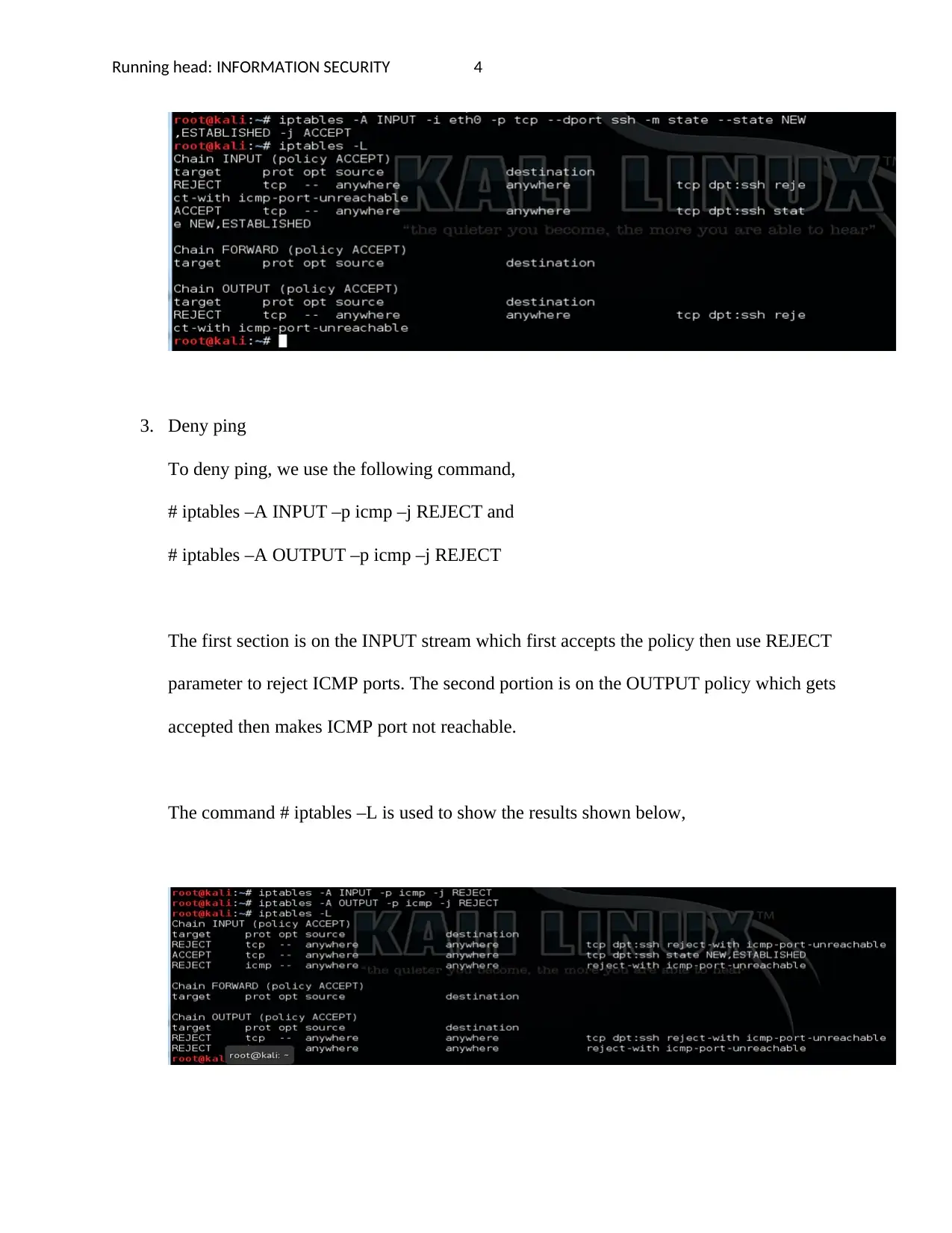
2. Allow ssh remote connections
Once the reject ssh policy, the following command will be used to allow ssh remote
connection
# iptables –A INPUT –i eth0 –p tcp - -dport ssh –m state - -state NEW, ESTABLISHED
–j ACCEPT
The result below is shown using the command # iptables –L
2. Allow ssh remote connections
Once the reject ssh policy, the following command will be used to allow ssh remote
connection
# iptables –A INPUT –i eth0 –p tcp - -dport ssh –m state - -state NEW, ESTABLISHED
–j ACCEPT
The result below is shown using the command # iptables –L
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: INFORMATION SECURITY 4
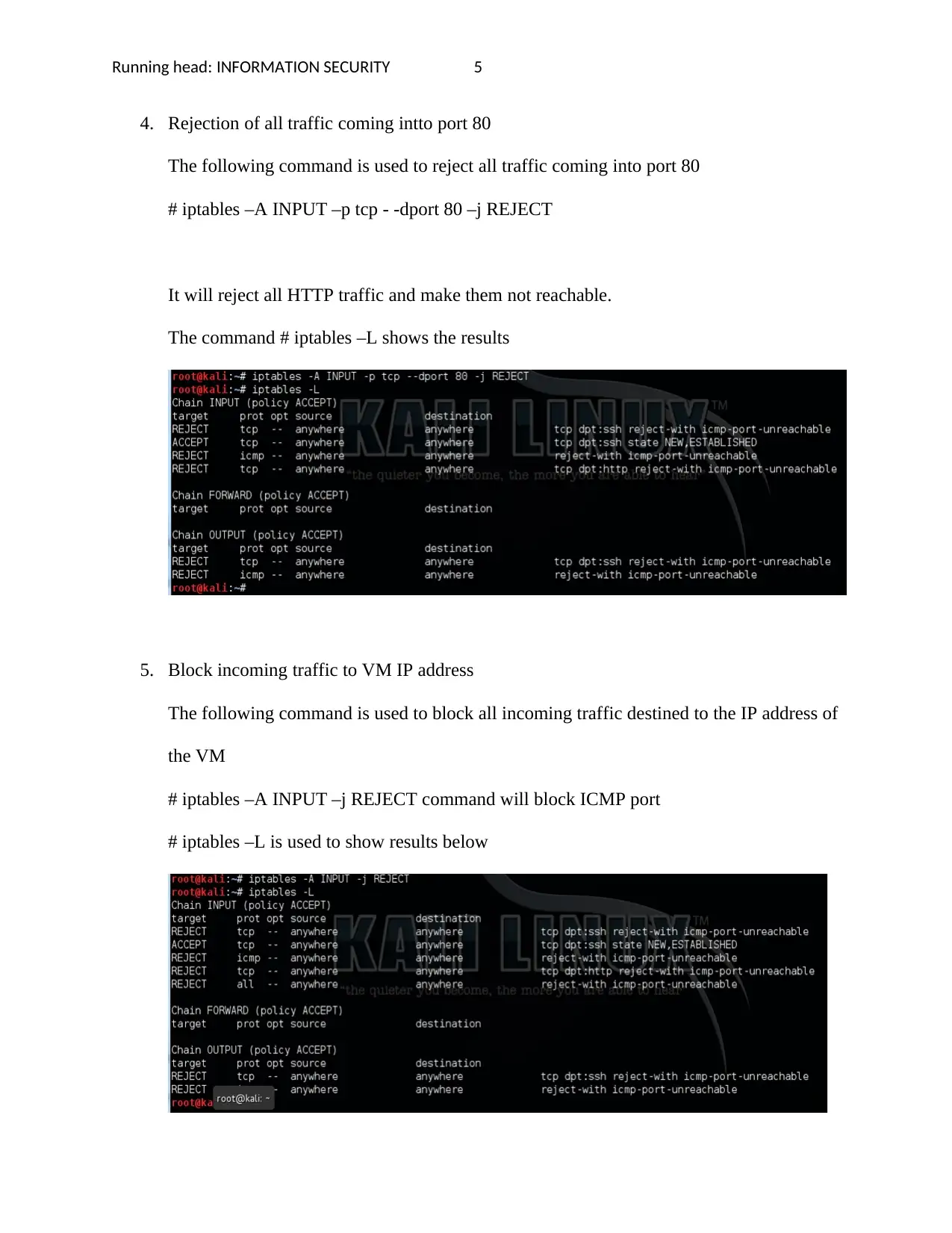
3. Deny ping
To deny ping, we use the following command,
# iptables –A INPUT –p icmp –j REJECT and
# iptables –A OUTPUT –p icmp –j REJECT
The first section is on the INPUT stream which first accepts the policy then use REJECT
parameter to reject ICMP ports. The second portion is on the OUTPUT policy which gets
accepted then makes ICMP port not reachable.
The command # iptables –L is used to show the results shown below,
3. Deny ping
To deny ping, we use the following command,
# iptables –A INPUT –p icmp –j REJECT and
# iptables –A OUTPUT –p icmp –j REJECT
The first section is on the INPUT stream which first accepts the policy then use REJECT
parameter to reject ICMP ports. The second portion is on the OUTPUT policy which gets
accepted then makes ICMP port not reachable.
The command # iptables –L is used to show the results shown below,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: INFORMATION SECURITY 5
4. Rejection of all traffic coming intto port 80
The following command is used to reject all traffic coming into port 80
# iptables –A INPUT –p tcp - -dport 80 –j REJECT
It will reject all HTTP traffic and make them not reachable.
The command # iptables –L shows the results
5. Block incoming traffic to VM IP address
The following command is used to block all incoming traffic destined to the IP address of
the VM
# iptables –A INPUT –j REJECT command will block ICMP port
# iptables –L is used to show results below
4. Rejection of all traffic coming intto port 80
The following command is used to reject all traffic coming into port 80
# iptables –A INPUT –p tcp - -dport 80 –j REJECT
It will reject all HTTP traffic and make them not reachable.
The command # iptables –L shows the results
5. Block incoming traffic to VM IP address
The following command is used to block all incoming traffic destined to the IP address of
the VM
# iptables –A INPUT –j REJECT command will block ICMP port
# iptables –L is used to show results below

Running head: INFORMATION SECURITY 6
6. Allow inbound traffic through port 80 but reject outbound traffic through port 80
The following command gets utilized
# iptables –A INPUT –p tcp - -dport 80 –j ACCEPT
# iptables –A OUTPUT –p tcp - -dport 80 –j REJECT
To show results, # iptables –L gives output as shown below
b. Discuss the advantages and disadvantages of firewall, with iptables and make
suggestions to overcome disadvantages in your report
Advantages
i. Implementable directly to the various individual hosts
ii. Provide a mechanism to restrict user access to and from the ports
iii. There is no need to handle any combinations of firewall filtering rules
iv. More flexible to use especially with the iptable front end services
6. Allow inbound traffic through port 80 but reject outbound traffic through port 80
The following command gets utilized
# iptables –A INPUT –p tcp - -dport 80 –j ACCEPT
# iptables –A OUTPUT –p tcp - -dport 80 –j REJECT
To show results, # iptables –L gives output as shown below
b. Discuss the advantages and disadvantages of firewall, with iptables and make
suggestions to overcome disadvantages in your report
Advantages
i. Implementable directly to the various individual hosts
ii. Provide a mechanism to restrict user access to and from the ports
iii. There is no need to handle any combinations of firewall filtering rules
iv. More flexible to use especially with the iptable front end services
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: INFORMATION SECURITY 7
v. No need for any customization at the customer side. All the system functions all
get done at the switch instead of at the application level
vi. Execution of system functions is quicker since no proxy is used between the client
and remote hosts
Disadvantages
i. Difficulty in filtering proxy based contents especially the proxy firewalls
ii. Complex to define and filter rules
iii. No advanced means to authenticate users
iv. Can be used to process packets at the application layer
Overcome the disadvantages
The above disadvantages can be overcome by
i. Use the following command /sbin/service iptables save to save the
rules for future use after reboot
ii. The administrator can utilize private IP addresses in their networking
devices so that each has legal inward and outward network facing
sides
c. Discuss the role and significance o, circuit relay firewall in securing communication
Circuit relay firewall is those that validate the connection before it allows traffic
through them. It does not simply look the rules to allow or reject the traffic but also
ascertains whether the connection is valid. Normally, this type of firewall works at the
v. No need for any customization at the customer side. All the system functions all
get done at the switch instead of at the application level
vi. Execution of system functions is quicker since no proxy is used between the client
and remote hosts
Disadvantages
i. Difficulty in filtering proxy based contents especially the proxy firewalls
ii. Complex to define and filter rules
iii. No advanced means to authenticate users
iv. Can be used to process packets at the application layer
Overcome the disadvantages
The above disadvantages can be overcome by
i. Use the following command /sbin/service iptables save to save the
rules for future use after reboot
ii. The administrator can utilize private IP addresses in their networking
devices so that each has legal inward and outward network facing
sides
c. Discuss the role and significance o, circuit relay firewall in securing communication
Circuit relay firewall is those that validate the connection before it allows traffic
through them. It does not simply look the rules to allow or reject the traffic but also
ascertains whether the connection is valid. Normally, this type of firewall works at the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: INFORMATION SECURITY 8
session layer of the OSI model. It uses the following matrix to gaude the validity of a
connection; destination IP, source IP, time, proto , username and password (Gurevich,
2014). The fireall will analyse eadh packet in depth to check for validity before it is
permitted based on rules. This types of firewall is thus very important in securing
communications (Modi & Acha, 2017)
Significance
The passages for the circuit are sent to the session layer of OSI where they
gets screen like most TCP three way handshake to check for validty of the
connection
It enforced realtime screening of packets before a connection get
established
It is significan in achieving private communications since the data is
always contained within the circutit
References
Gurevich, V. (2014). Susceptibility of Modern Relay Protection: Will Protection From Cyber
Attacks Help? Serbian Journal of Electrical Engineering, 11(2), 233.
Modi, C., & Acha, K. (2017). Virtualization layer security challenges and intrusion
detection/prevention systems in cloud computing: a comprehensive review. Journal of
Supercomputing, 73(3), 1192–1234. https://doi.org/10.1007/s11227-016-1805-9
session layer of the OSI model. It uses the following matrix to gaude the validity of a
connection; destination IP, source IP, time, proto , username and password (Gurevich,
2014). The fireall will analyse eadh packet in depth to check for validity before it is
permitted based on rules. This types of firewall is thus very important in securing
communications (Modi & Acha, 2017)
Significance
The passages for the circuit are sent to the session layer of OSI where they
gets screen like most TCP three way handshake to check for validty of the
connection
It enforced realtime screening of packets before a connection get
established
It is significan in achieving private communications since the data is
always contained within the circutit
References
Gurevich, V. (2014). Susceptibility of Modern Relay Protection: Will Protection From Cyber
Attacks Help? Serbian Journal of Electrical Engineering, 11(2), 233.
Modi, C., & Acha, K. (2017). Virtualization layer security challenges and intrusion
detection/prevention systems in cloud computing: a comprehensive review. Journal of
Supercomputing, 73(3), 1192–1234. https://doi.org/10.1007/s11227-016-1805-9

Running head: INFORMATION SECURITY 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




