Security Fundamentals: ATM Security, Biometrics & Cryptography
VerifiedAdded on 2023/06/14
|10
|1864
|148
Homework Assignment
AI Summary
This assignment delves into fundamental security concepts, beginning with an analysis of Automated Teller Machine (ATM) security. It identifies confidentiality, integrity, and availability as key requirements for ATM systems, providing examples for each. The assignment then calculates the probability of a thief discovering an ATM PIN. It also addresses the advantages and disadvantages of biometric authentication systems, offering solutions to common problems like high hardware costs and data accuracy. Furthermore, it explores situations where false negative rates in biometric systems can be problematic. Finally, the assignment demonstrates the decryption of a Caesar cipher, revealing the original message related to mobile phone processor frequency. Desklib offers a wealth of similar solved assignments and past papers to aid students in their studies.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Author’s Note:
Information Security
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................4
Question 3..................................................................................................................................5
Question 4..................................................................................................................................6
Question 5..................................................................................................................................7
References..................................................................................................................................9
INFORMATION SECURITY
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................4
Question 3..................................................................................................................................5
Question 4..................................................................................................................................6
Question 5..................................................................................................................................7
References..................................................................................................................................9

2
INFORMATION SECURITY
Question 1
Automated Teller Machine or an ATM is used for the purpose of withdrawing cash
without even visiting to the bank or without interacting with the bank staff members. Three
important requirements are present for the ATM card and the PIN. They are as follows:
i) Confidentiality: It is the other name for privacy and it helps to maintain the privacy
of the ATM card. Under no circumstances, the confidentiality of the card should be lost. The
user would major losses if this type of situation arrives (Peltier, 2013).
The degree of importance of confidentiality is high since, unsecured PIN during the
transactions can lead to the compromise of the bank account and therefore, encryption must
be present.
The examples of confidentiality in ATM system are as follows:
a) The details of the ATM card and PIN are extremely confidential and should not be
lost.
b) Presence of the ATM card while making a transaction is mandatory.
ii) Integrity: The data integrity is the next important requirement in ATM. The PIN
could be changed by the hackers and the users should ensure that this type of situation does
not arrive.
The degree of importance of integrity is high as if any hacker or thief gets hold of the
ATM card or PIN; they might change the data for the purpose of withdrawing money. Hence,
data integrity should be maintained properly.
The examples are as follows:
INFORMATION SECURITY
Question 1
Automated Teller Machine or an ATM is used for the purpose of withdrawing cash
without even visiting to the bank or without interacting with the bank staff members. Three
important requirements are present for the ATM card and the PIN. They are as follows:
i) Confidentiality: It is the other name for privacy and it helps to maintain the privacy
of the ATM card. Under no circumstances, the confidentiality of the card should be lost. The
user would major losses if this type of situation arrives (Peltier, 2013).
The degree of importance of confidentiality is high since, unsecured PIN during the
transactions can lead to the compromise of the bank account and therefore, encryption must
be present.
The examples of confidentiality in ATM system are as follows:
a) The details of the ATM card and PIN are extremely confidential and should not be
lost.
b) Presence of the ATM card while making a transaction is mandatory.
ii) Integrity: The data integrity is the next important requirement in ATM. The PIN
could be changed by the hackers and the users should ensure that this type of situation does
not arrive.
The degree of importance of integrity is high as if any hacker or thief gets hold of the
ATM card or PIN; they might change the data for the purpose of withdrawing money. Hence,
data integrity should be maintained properly.
The examples are as follows:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY
a) Altering of data without taking permission from the user.
b) Unintentional data deletion is again an important example (Siponen, Mahmood &
Pahnila, 2014).
iii) Availability: The next requirement is the availability of valid information and
hardware. If these would be absent, it is impossible to execute any transaction.
The degree of importance of availability of information and hardware is extremely
high as without the information of PIN, ATM card and the ATM, it is impossible to use them.
The examples are as follows:
a) Availability of valid information related to ATM card and PIN.
b) Availability of hardware for making the transaction.
INFORMATION SECURITY
a) Altering of data without taking permission from the user.
b) Unintentional data deletion is again an important example (Siponen, Mahmood &
Pahnila, 2014).
iii) Availability: The next requirement is the availability of valid information and
hardware. If these would be absent, it is impossible to execute any transaction.
The degree of importance of availability of information and hardware is extremely
high as without the information of PIN, ATM card and the ATM, it is impossible to use them.
The examples are as follows:
a) Availability of valid information related to ATM card and PIN.
b) Availability of hardware for making the transaction.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY
Question 2
According to the given scenario, the thief wants to discover the PIN of the customer.
There is a process to find out the PIN of the customer. There are four keys in a PIN
and for discovering the accurate PIN of the customer; the thief should undergo a series of
permutations.
The series of the PIN of the customer can be from 0 to 9.
Available keys = 4.
Keys broken in the keypad= 5.
Hence, the total no of probabilities for detecting the PIN is
5P4 = 5!/(5 - 4)! = 5!/4! = 120.
Therefore, the thief can detect the correct PIN up to 120 ways.
However, only 3 times the PIN could be given. After the third wrong attempt, the
ATM card would be automatically blocked.
INFORMATION SECURITY
Question 2
According to the given scenario, the thief wants to discover the PIN of the customer.
There is a process to find out the PIN of the customer. There are four keys in a PIN
and for discovering the accurate PIN of the customer; the thief should undergo a series of
permutations.
The series of the PIN of the customer can be from 0 to 9.
Available keys = 4.
Keys broken in the keypad= 5.
Hence, the total no of probabilities for detecting the PIN is
5P4 = 5!/(5 - 4)! = 5!/4! = 120.
Therefore, the thief can detect the correct PIN up to 120 ways.
However, only 3 times the PIN could be given. After the third wrong attempt, the
ATM card would be automatically blocked.

5
INFORMATION SECURITY
Question 3
Biometric authentication system is utilized for identifying any particular individual
with the help of his or her biological traits and attributes. A database is maintained in this
purpose, where the data is matched with the previously existing data. When the data is
matched, the person is termed as authorized, else unauthorized (Bhagavatula et al., 2015).
The most significant examples of biometric authentication system are the fingerprint
recognition, face or voice recognition, retina scan and iris scan.
However, in spite of all these advantages, biometric authentication system is still not
used by few people. The main reasons with their solutions for this are given below:
i) Extra Hardware is Required: When biometric authentication system is
implemented in any office or school, the hardware for it is also installed. This often exceeds
the budget of the office or school. Hence, people are still reluctant in utilizing this system.
To solve this problem, cheap machines are available in the market that does not incur
huge cost and does not exceed the budget limit (De Gramatica et al., 2015).
ii) Lack of Data Accuracy: Biometric authentication system should not provide data
accuracy and thus the data is not always 100% correct.
To solve this problem, metrics like False Acceptance Rate and False Rejection Rate
are utilized that determine the accuracy.
iii) Password Resetting: The third problem is password resetting. It is extremely
difficult to reset the password.
To solve this problem, regulations like PCI-DDS and HIPAA can be used.
INFORMATION SECURITY
Question 3
Biometric authentication system is utilized for identifying any particular individual
with the help of his or her biological traits and attributes. A database is maintained in this
purpose, where the data is matched with the previously existing data. When the data is
matched, the person is termed as authorized, else unauthorized (Bhagavatula et al., 2015).
The most significant examples of biometric authentication system are the fingerprint
recognition, face or voice recognition, retina scan and iris scan.
However, in spite of all these advantages, biometric authentication system is still not
used by few people. The main reasons with their solutions for this are given below:
i) Extra Hardware is Required: When biometric authentication system is
implemented in any office or school, the hardware for it is also installed. This often exceeds
the budget of the office or school. Hence, people are still reluctant in utilizing this system.
To solve this problem, cheap machines are available in the market that does not incur
huge cost and does not exceed the budget limit (De Gramatica et al., 2015).
ii) Lack of Data Accuracy: Biometric authentication system should not provide data
accuracy and thus the data is not always 100% correct.
To solve this problem, metrics like False Acceptance Rate and False Rejection Rate
are utilized that determine the accuracy.
iii) Password Resetting: The third problem is password resetting. It is extremely
difficult to reset the password.
To solve this problem, regulations like PCI-DDS and HIPAA can be used.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INFORMATION SECURITY
Question 4
Biometric authentication system is the procedure of recognition of any specific
individual with the help of his or her biological traits and attributes. These are exclusively
utilized for uniquely identifying the person. This type of authentication is also used to lock or
unlock any phone, laptop or any other computing device.
The biometric identification is done either by physiological or by behavioural
features. The physiological features include the body parts like fingerprint recognition, face
or voice recognition, retina scan and iris scan (De Gramatica et al., 2015). The behavioural
attributes include the behaviour, voice and gait of the person.
Many times, there are certain situations, where the false negative rates get higher and
serious than the false positive rates. The examples of two such situations are as follows:
i) Accessing Own Objects: Often due to minor problem in the information system
within the biometric machine, the owner of the object is unable to get hold of it as the
biometric machine cannot take the password or the biological trait of the user.
ii) Failure in Recognition of Patients: The patients often cannot give the biometric
password properly either due to their cardiac arrest, or burnt fingers (Bhagavatula et al.,
2015). This can lead to major problems as they would not be able to access their own
possessions because of the problem in giving the passwords.
INFORMATION SECURITY
Question 4
Biometric authentication system is the procedure of recognition of any specific
individual with the help of his or her biological traits and attributes. These are exclusively
utilized for uniquely identifying the person. This type of authentication is also used to lock or
unlock any phone, laptop or any other computing device.
The biometric identification is done either by physiological or by behavioural
features. The physiological features include the body parts like fingerprint recognition, face
or voice recognition, retina scan and iris scan (De Gramatica et al., 2015). The behavioural
attributes include the behaviour, voice and gait of the person.
Many times, there are certain situations, where the false negative rates get higher and
serious than the false positive rates. The examples of two such situations are as follows:
i) Accessing Own Objects: Often due to minor problem in the information system
within the biometric machine, the owner of the object is unable to get hold of it as the
biometric machine cannot take the password or the biological trait of the user.
ii) Failure in Recognition of Patients: The patients often cannot give the biometric
password properly either due to their cardiac arrest, or burnt fingers (Bhagavatula et al.,
2015). This can lead to major problems as they would not be able to access their own
possessions because of the problem in giving the passwords.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INFORMATION SECURITY
Question 5
In cryptography, transposition is the best method for encryption. Rail fence cipher is
the best form of the transposition cipher that is used for decrypting the encrypted cipher in a
proper sequence (Singh, 2013). It is extremely effective and could be executed quickly.
George decided to send the instructions completely encrypted under Caesar cipher by
following one after another.
The substitution key is 234 and the cipher text is NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE.
After using the algorithms of Caesar cipher and substitution, the given encrypted text
could be decrypted as:
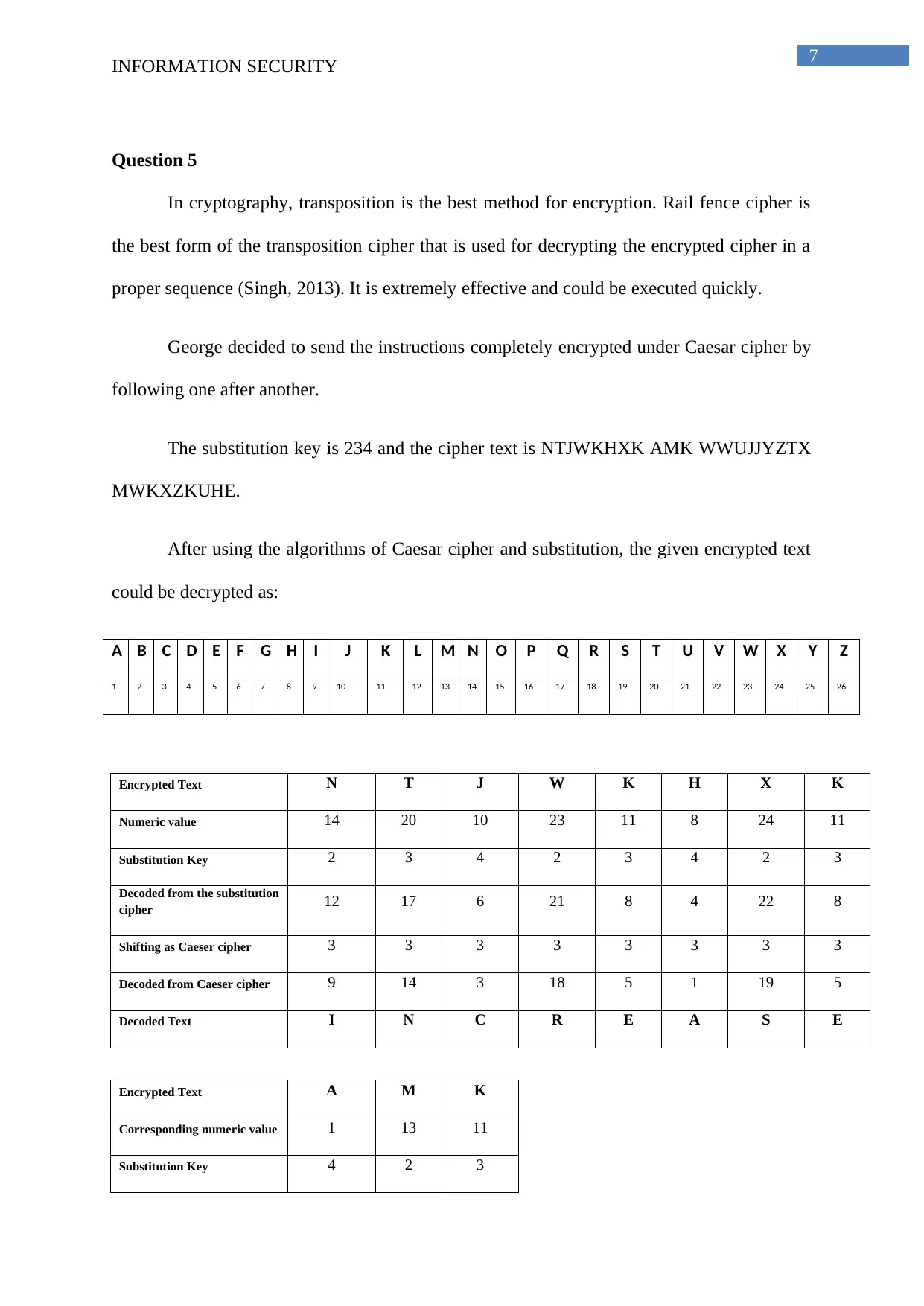
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 21 8 4 22 8
Shifting as Caeser cipher 3 3 3 3 3 3 3 3
Decoded from Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Substitution Key 4 2 3
INFORMATION SECURITY
Question 5
In cryptography, transposition is the best method for encryption. Rail fence cipher is
the best form of the transposition cipher that is used for decrypting the encrypted cipher in a
proper sequence (Singh, 2013). It is extremely effective and could be executed quickly.
George decided to send the instructions completely encrypted under Caesar cipher by
following one after another.
The substitution key is 234 and the cipher text is NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE.
After using the algorithms of Caesar cipher and substitution, the given encrypted text
could be decrypted as:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 21 8 4 22 8
Shifting as Caeser cipher 3 3 3 3 3 3 3 3
Decoded from Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Substitution Key 4 2 3
8
INFORMATION SECURITY
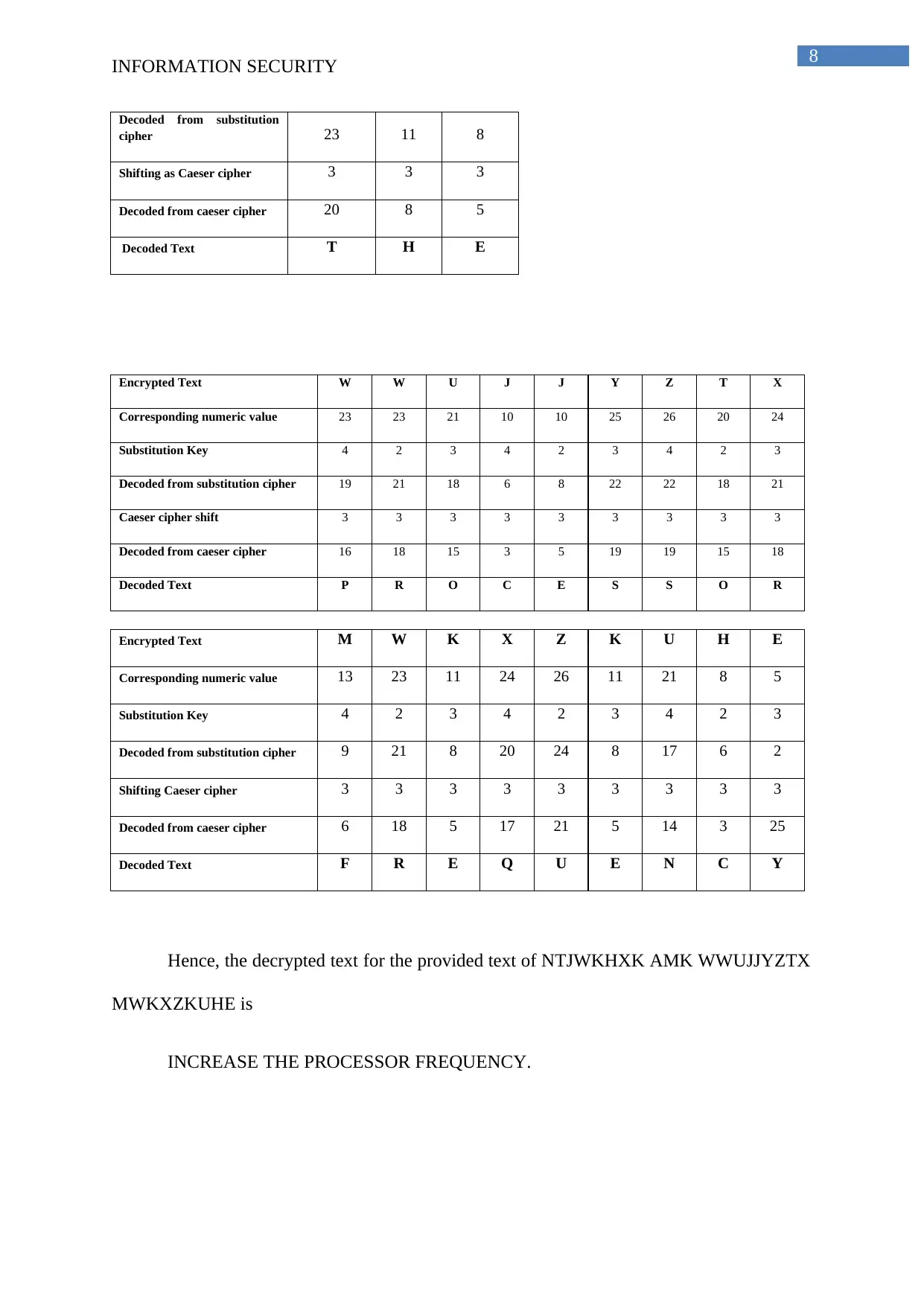
Decoded from substitution
cipher 23 11 8
Shifting as Caeser cipher 3 3 3
Decoded from caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Hence, the decrypted text for the provided text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
INCREASE THE PROCESSOR FREQUENCY.
INFORMATION SECURITY
Decoded from substitution
cipher 23 11 8
Shifting as Caeser cipher 3 3 3
Decoded from caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Hence, the decrypted text for the provided text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
INCREASE THE PROCESSOR FREQUENCY.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INFORMATION SECURITY
References
Andress, J. (2014). The basics of information security: understanding the fundamentals of
InfoSec in theory and practice. Syngress.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and
influences on adoption. Proc. USEC, 1-2.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The
role of catalogues of threats and security controls in security risk assessment: an
empirical study with ATM professionals. In International Working Conference on
Requirements Engineering: Foundation for Software Quality (pp. 98-114). Springer,
Cham.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for
information security. International Journal of Computer Applications, 67(19).
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
INFORMATION SECURITY
References
Andress, J. (2014). The basics of information security: understanding the fundamentals of
InfoSec in theory and practice. Syngress.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and
influences on adoption. Proc. USEC, 1-2.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The
role of catalogues of threats and security controls in security risk assessment: an
empirical study with ATM professionals. In International Working Conference on
Requirements Engineering: Foundation for Software Quality (pp. 98-114). Springer,
Cham.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for
information security. International Journal of Computer Applications, 67(19).
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




