Information Security: ATM Confidentiality, Integrity and Availability
VerifiedAdded on 2023/06/13
|11
|3557
|353
AI Summary
This article covers the confidentiality, integrity and availability requirements of ATM machines. It also discusses biometric authentication, transposition cipher and Caesar cipher. The article also highlights the advantages and disadvantages of biometric authentication.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Author’s Note:
Information Security
Name of the Student
Name of the University
Author’s Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
INFORMATION SECURITY
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................3
Question 3..................................................................................................................................4
Question 4..................................................................................................................................5
Question 5..................................................................................................................................6
References..................................................................................................................................8
INFORMATION SECURITY
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................3
Question 3..................................................................................................................................4
Question 4..................................................................................................................................5
Question 5..................................................................................................................................6
References..................................................................................................................................8

2
INFORMATION SECURITY
Question 1
ATM or Automated Teller Machines are so designed that there should be no issues
with information security and the users could easily get a particular personal identification
number or PIN for accessing their accounts in banks (Peltier, 2013). The detailed descriptions
of these three requirements with examples are given below:
i) Confidentiality: Confidentiality can be roughly stated as privacy. The various
measures that are undertaken for ensuring confidentiality in ATM are designed for the
prevention of sensitive information from reaching to the wrong people (Von Solms & Van
Niekerk, 2013). The access of these ATM cards and PIN numbers should be absolutely
restricted and limited to only those who are authorized. There are several examples of
confidentiality associated in these systems. These examples are as follows:
a) The first example for ensuring confidentiality is the account number or any routing
number when internet banking is executed. Data encryption is the most common method to
ensure confidentiality. The unique username as well as passwords help to differentiate the
authorized user.
b) The second example of confidentiality in ATM machines is that the particular card
should be present and without it, no transaction is done (Siponen, Mahmood & Pahnila,
2014).
c) Two distinct kinds of breaching of confidentiality are possible in ATM. One of
them is while the credentials of the authorized user are being stolen and the second is while
the employee detail of any organization is being breached.
ii) Integrity: The second requirement that is solely associated with the ATM system is
integrity. It helps to maintain the accuracy, consistency as well as trustworthiness of any
specific data (De Gramatica et al., 2015).
The examples of integrity requirement are given below:
a) The data should not be changed without the permission of the authorized user.
b) The sudden or accidental deletion of data of ATM also affects the data integrity.
c) The particular people who maintain the data should search for some measures to
implement data integrity.
iii) Availability: The third significant requirement in ATM is the availability. It
roughly refers to maintenance of the hardware or information that is being involved while
doing any transaction (Andress, 2014). This hardware is the most important factor in the
ATM machine. It is connected with software and thus, this hardware is checked with proper
system up gradation.
The examples of availability in an ATM machine are given below:
a) The systems that are being utilized while executing any transaction.
b) DoS attacks should be prevented while maintaining availability.
INFORMATION SECURITY
Question 1
ATM or Automated Teller Machines are so designed that there should be no issues
with information security and the users could easily get a particular personal identification
number or PIN for accessing their accounts in banks (Peltier, 2013). The detailed descriptions
of these three requirements with examples are given below:
i) Confidentiality: Confidentiality can be roughly stated as privacy. The various
measures that are undertaken for ensuring confidentiality in ATM are designed for the
prevention of sensitive information from reaching to the wrong people (Von Solms & Van
Niekerk, 2013). The access of these ATM cards and PIN numbers should be absolutely
restricted and limited to only those who are authorized. There are several examples of
confidentiality associated in these systems. These examples are as follows:
a) The first example for ensuring confidentiality is the account number or any routing
number when internet banking is executed. Data encryption is the most common method to
ensure confidentiality. The unique username as well as passwords help to differentiate the
authorized user.
b) The second example of confidentiality in ATM machines is that the particular card
should be present and without it, no transaction is done (Siponen, Mahmood & Pahnila,
2014).
c) Two distinct kinds of breaching of confidentiality are possible in ATM. One of
them is while the credentials of the authorized user are being stolen and the second is while
the employee detail of any organization is being breached.
ii) Integrity: The second requirement that is solely associated with the ATM system is
integrity. It helps to maintain the accuracy, consistency as well as trustworthiness of any
specific data (De Gramatica et al., 2015).
The examples of integrity requirement are given below:
a) The data should not be changed without the permission of the authorized user.
b) The sudden or accidental deletion of data of ATM also affects the data integrity.
c) The particular people who maintain the data should search for some measures to
implement data integrity.
iii) Availability: The third significant requirement in ATM is the availability. It
roughly refers to maintenance of the hardware or information that is being involved while
doing any transaction (Andress, 2014). This hardware is the most important factor in the
ATM machine. It is connected with software and thus, this hardware is checked with proper
system up gradation.
The examples of availability in an ATM machine are given below:
a) The systems that are being utilized while executing any transaction.
b) DoS attacks should be prevented while maintaining availability.

3
INFORMATION SECURITY
c) The information availability refers to the information required while making a
transaction.
Question 2
A thief has broken into an ATM or an Automated Teller Machine by utilizing a
screwdriver and thus was successful in jamming the ATM card reader. He even broke the five
distinct keys from keypad. He was extremely confident regarding his approach towards
stealing the money from that Automated Teller Machine or ATM.
Although, this particular thief had to stop his entire process of ATM machine
breaking off. A customer came in between to withdraw some cash. For this purpose, the thief
had to hide. The customer was not able to spot the thief.
He came inside the Automated Teller Machine or ATM and entered his ATM card
within the machine. This customer then, entered his respective four digits PIN within the
machine and was also successful in withdrawing out some cash from his bank account. Next,
he tried to take out the ATM card from the machine. As the card reader of the Automated
Teller Machine was jammed beforehand, he was unable to complete this procedure. His ATM
card was jammed within the machine and he went out to call someone for help.
During this period, the thief came out. He took the decision to find out the unique PIN
of the customer for the purpose of stealing money from that account. He tried many times and
there is a specific procedure to find out the PIN number of the customer.
The following steps clearly depict the maximum number of PINs or personal
identification numbers, this particular thief is required to enter, before successfully
discovering the correct PIN of that customer.
There are four keys in any PIN number. Therefore, these four keys could be utilized
with the combination of probabilities.
The total number of probabilities or possibilities, which the particular thief present
within the Automated Teller Machine or ATM could enter, is given below:
5P4 = 5!/(5 - 4)! = 5!/4! = 120.
Thus, the thief can enter 120 ways or possibilities for detecting the ATM PIN of the
customer.
Various security measures are present in all Automated Teller Machines and each of
them is unique in nature. The most significant limitation or restriction within an ATM card is
that the user is allowed to enter only 3 times. After those three times, if the user is
unsuccessful in giving the correct card number, the specific card would be blocked.
INFORMATION SECURITY
c) The information availability refers to the information required while making a
transaction.
Question 2
A thief has broken into an ATM or an Automated Teller Machine by utilizing a
screwdriver and thus was successful in jamming the ATM card reader. He even broke the five
distinct keys from keypad. He was extremely confident regarding his approach towards
stealing the money from that Automated Teller Machine or ATM.
Although, this particular thief had to stop his entire process of ATM machine
breaking off. A customer came in between to withdraw some cash. For this purpose, the thief
had to hide. The customer was not able to spot the thief.
He came inside the Automated Teller Machine or ATM and entered his ATM card
within the machine. This customer then, entered his respective four digits PIN within the
machine and was also successful in withdrawing out some cash from his bank account. Next,
he tried to take out the ATM card from the machine. As the card reader of the Automated
Teller Machine was jammed beforehand, he was unable to complete this procedure. His ATM
card was jammed within the machine and he went out to call someone for help.
During this period, the thief came out. He took the decision to find out the unique PIN
of the customer for the purpose of stealing money from that account. He tried many times and
there is a specific procedure to find out the PIN number of the customer.
The following steps clearly depict the maximum number of PINs or personal
identification numbers, this particular thief is required to enter, before successfully
discovering the correct PIN of that customer.
There are four keys in any PIN number. Therefore, these four keys could be utilized
with the combination of probabilities.
The total number of probabilities or possibilities, which the particular thief present
within the Automated Teller Machine or ATM could enter, is given below:
5P4 = 5!/(5 - 4)! = 5!/4! = 120.
Thus, the thief can enter 120 ways or possibilities for detecting the ATM PIN of the
customer.
Various security measures are present in all Automated Teller Machines and each of
them is unique in nature. The most significant limitation or restriction within an ATM card is
that the user is allowed to enter only 3 times. After those three times, if the user is
unsuccessful in giving the correct card number, the specific card would be blocked.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
INFORMATION SECURITY
Question 3
Bio-metric authentication can be defined as the security process, which solely relies
on the specific or unique characteristics that are biological of any person or individual. It is
considered as one of the safest modes of verification of all persons (Grama, 2014). The
systems for bio-metric authentication are utilized for comparing any biometric data or
information that is already being captured within the system.
A database is present within the system and this database stores or captures the
biometric data of that particular individual (Sayed et al., 2013). As soon as the authorized
person enters his biological characteristic within the system, the database matches that data
with the existing database. If that data is matched, then only, the person is allowed to enter or
the bio-metric authentication is confirmed. Eventually, this bio-metric authentication is
utilized for the successful management of access to any type of physical devices or digital
resources like computing systems or buildings. Several, offices, schools and colleges have
implemented this particular type of authentication for allowing or identifying their employees
or students (Bhagavatula et al., 2015). The most significant and popular examples of
biometric authentication systems are the fingerprint recognition, retina scans, face
recognition, voice recognition and many more.
However, in spite of having such vast and beneficial advantages, there are few
reasons that people do not want to utilize this system. Following are the three important and
significant reasons that why people are still reluctant to utilize bio-metric system with the
methods of countering these problems.
i) Cannot Be Reset: This is the first and the foremost reason, why people are always
reluctant to use the bio-metric authentication for their devices or buildings. Once, the bio-
metric data is being entered within the system, it is very difficult to change or compromise
with that data. Hence, the users do not want to use this system (Frank et al., 2013). This is
more relevant when the users have bio-metric authentication in their computing devices or
phones. For any reason, if the phone or the laptop cannot recognize the biometric feature of
the user, they will not be able to open them.
For solving this particular problem, the way out is to keep another trustworthy person
for identifying or unlocking the devices. Moreover, there is an additional option of resetting
the password without much complexity. They could simply reset their passwords with the
help of PCI-DDS, HIPAA and Sarbanes-Oxley regulations.
ii) Need of Additional Hardware: This type of problem is faced in offices or
buildings. The system for biometric authentication is to be installed within the office for
successfully executing the biometric authentication (He & Wang, 2015). People are reluctant
as they feel that this is an extra cost for them.
For removing this type of objection, cost effective hardware could be implemented.
Many of them are available in the market and thus could be used by the users.
iii) Lack of Accuracy: Bio-metric systems are not always 100% accurate and thus
they are not being used by the users.
For solving this problem, FAR or FRR metrics could be utilized. False Acceptance
Rate and False Rejection Rate are probabilities that help in determining the accuracy.
INFORMATION SECURITY
Question 3
Bio-metric authentication can be defined as the security process, which solely relies
on the specific or unique characteristics that are biological of any person or individual. It is
considered as one of the safest modes of verification of all persons (Grama, 2014). The
systems for bio-metric authentication are utilized for comparing any biometric data or
information that is already being captured within the system.
A database is present within the system and this database stores or captures the
biometric data of that particular individual (Sayed et al., 2013). As soon as the authorized
person enters his biological characteristic within the system, the database matches that data
with the existing database. If that data is matched, then only, the person is allowed to enter or
the bio-metric authentication is confirmed. Eventually, this bio-metric authentication is
utilized for the successful management of access to any type of physical devices or digital
resources like computing systems or buildings. Several, offices, schools and colleges have
implemented this particular type of authentication for allowing or identifying their employees
or students (Bhagavatula et al., 2015). The most significant and popular examples of
biometric authentication systems are the fingerprint recognition, retina scans, face
recognition, voice recognition and many more.
However, in spite of having such vast and beneficial advantages, there are few
reasons that people do not want to utilize this system. Following are the three important and
significant reasons that why people are still reluctant to utilize bio-metric system with the
methods of countering these problems.
i) Cannot Be Reset: This is the first and the foremost reason, why people are always
reluctant to use the bio-metric authentication for their devices or buildings. Once, the bio-
metric data is being entered within the system, it is very difficult to change or compromise
with that data. Hence, the users do not want to use this system (Frank et al., 2013). This is
more relevant when the users have bio-metric authentication in their computing devices or
phones. For any reason, if the phone or the laptop cannot recognize the biometric feature of
the user, they will not be able to open them.
For solving this particular problem, the way out is to keep another trustworthy person
for identifying or unlocking the devices. Moreover, there is an additional option of resetting
the password without much complexity. They could simply reset their passwords with the
help of PCI-DDS, HIPAA and Sarbanes-Oxley regulations.
ii) Need of Additional Hardware: This type of problem is faced in offices or
buildings. The system for biometric authentication is to be installed within the office for
successfully executing the biometric authentication (He & Wang, 2015). People are reluctant
as they feel that this is an extra cost for them.
For removing this type of objection, cost effective hardware could be implemented.
Many of them are available in the market and thus could be used by the users.
iii) Lack of Accuracy: Bio-metric systems are not always 100% accurate and thus
they are not being used by the users.
For solving this problem, FAR or FRR metrics could be utilized. False Acceptance
Rate and False Rejection Rate are probabilities that help in determining the accuracy.

5
INFORMATION SECURITY
Question 4
Biometric authentication is the technical term for identifying any particular or specific
person in terms of their biological characteristics. This type of authentication system is
utilized in any type of offices, buildings, schools and colleges (Chaudhry et al., 2015).
Biometric authentication is also utilized for the purpose of locking or unlocking any
computing device of any particular individual or person.
The identifiers of biometric are the distinctive and measurable features that are
utilized for labelling as well as describing the individuals. These identifiers of biometric are
solely categorized as the behavioural and physiological features or characteristics. The most
significant examples of physiological characteristics are explicitly related to the body shape
of any specific person (Lu et al., 2015). The most significant examples of these physiological
characteristics of a person mainly include face recognition, voice recognition, DNA
identification, fingerprint recognition, retina scan, palm scan, iris recognition, hand geometry
and many more. The behavioural characteristics of that of an individual mainly include the
pattern of how a person behaves, gait, voice, typing rhythm and many more.
Although, biometric authentication comprises of various advantages, there are few
disadvantages of this particular system. The false positive rates and the false negative rates
could be substantially tuned as per the given requirement. These false positive rates and the
false negative rates are most of the times complementary to each other, which means it
lowers one another (Xu, Zhou & Lyu, 2014). There can be various such situations, where the
false negative rates have turned down to false positive rates and thus are termed as extremely
serious and dangerous. The false negative rates occur when the biometric systems eventually
fail in recognizing the authorized and authenticated users.
Following are the two such circumstances, where the false negative rates have been
more serious as well as dangerous than the false positive rates.
i) Access to Own Possession: The first circumstance occurs when the owner of an
expensive object could be prevented from being accessed to his own object and thus leading
him or her to such a situation that he is not being able to access his own possession. This type
of situation is extremely dangerous as the person might need his possession effective
immediately and thus it could be termed as false negative rate (Andress, 2014). This
particular of problem occurs when the biometric authentication system does not respond
perfectly and thus is termed as the most significant problem in terms of security. The way to
get out from this type of situation is very problematic and thus often users are reluctant to use
this system.
ii) Failing to Recognize Patients: This is the second important circumstance where
the false negative rates are extremely dangerous than the false positive rates. Suppose, a
patient has suffered a cardiac arrest and the doors of his house are locked with biometric
authentication (Bhagavatula et al., 2015). He is unable to visit to the doctors or the doctors
are unable to reach him since they could not open up the doors. This is an extremely
dangerous situation and thus the false negative rates are more dangerous in this type of
situation.
INFORMATION SECURITY
Question 4
Biometric authentication is the technical term for identifying any particular or specific
person in terms of their biological characteristics. This type of authentication system is
utilized in any type of offices, buildings, schools and colleges (Chaudhry et al., 2015).
Biometric authentication is also utilized for the purpose of locking or unlocking any
computing device of any particular individual or person.
The identifiers of biometric are the distinctive and measurable features that are
utilized for labelling as well as describing the individuals. These identifiers of biometric are
solely categorized as the behavioural and physiological features or characteristics. The most
significant examples of physiological characteristics are explicitly related to the body shape
of any specific person (Lu et al., 2015). The most significant examples of these physiological
characteristics of a person mainly include face recognition, voice recognition, DNA
identification, fingerprint recognition, retina scan, palm scan, iris recognition, hand geometry
and many more. The behavioural characteristics of that of an individual mainly include the
pattern of how a person behaves, gait, voice, typing rhythm and many more.
Although, biometric authentication comprises of various advantages, there are few
disadvantages of this particular system. The false positive rates and the false negative rates
could be substantially tuned as per the given requirement. These false positive rates and the
false negative rates are most of the times complementary to each other, which means it
lowers one another (Xu, Zhou & Lyu, 2014). There can be various such situations, where the
false negative rates have turned down to false positive rates and thus are termed as extremely
serious and dangerous. The false negative rates occur when the biometric systems eventually
fail in recognizing the authorized and authenticated users.
Following are the two such circumstances, where the false negative rates have been
more serious as well as dangerous than the false positive rates.
i) Access to Own Possession: The first circumstance occurs when the owner of an
expensive object could be prevented from being accessed to his own object and thus leading
him or her to such a situation that he is not being able to access his own possession. This type
of situation is extremely dangerous as the person might need his possession effective
immediately and thus it could be termed as false negative rate (Andress, 2014). This
particular of problem occurs when the biometric authentication system does not respond
perfectly and thus is termed as the most significant problem in terms of security. The way to
get out from this type of situation is very problematic and thus often users are reluctant to use
this system.
ii) Failing to Recognize Patients: This is the second important circumstance where
the false negative rates are extremely dangerous than the false positive rates. Suppose, a
patient has suffered a cardiac arrest and the doors of his house are locked with biometric
authentication (Bhagavatula et al., 2015). He is unable to visit to the doctors or the doctors
are unable to reach him since they could not open up the doors. This is an extremely
dangerous situation and thus the false negative rates are more dangerous in this type of
situation.
6
INFORMATION SECURITY
Question 5
1st part
Transposition is the best method for encrypting any text. In cryptography, the
transposition cipher is the procedure through which the specific positions that are being held
by the units of the plaintext are being moved as per any specific regular system (Rewagad &
Pawar, 2013). The plaintext refers to all the common characters or the collection of
characters. The cipher text comprises of the permutation of a plaintext. One of the best forms
of transposition cipher is the rail fence cipher. The name itself suggests how the cipher
method works or does its job. The most significant benefit of the columnar transposition over
the substitution encryption methodology is that all the algorithms required here could be
utilized as many times required. In case of the substitution method, this particular feature is
absent. For example, the decryption of the cipher text with the columnar transposition could
be utilized twice on any plain text (Singh, 2013). There is a distinct procedure or deciphering
any encrypted text. Following are the two steps for decrypting a cipher.
i) At first, the user has to look at the column length by simply sub dividing this length
with the help of key length.
ii) The second step is that the message is next written within the columns once again
and finally the key becomes successful in retransforming the columns (Xu, Zhou & Lyu,
2014).
Thus, with the help of columnar transposition, any cipher text could be easily as well
as quickly determined.
2nd part
George’s company for preventing the leakage of any type of information while
transmission, George decided to send the instructions completely encrypted under Caesar
cipher by following one after another.
The substitution key is 234 and the cipher text is NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE.
After utilizing the algorithm of Caesar cipher and substitution, the given encrypted
text could be decrypted as:
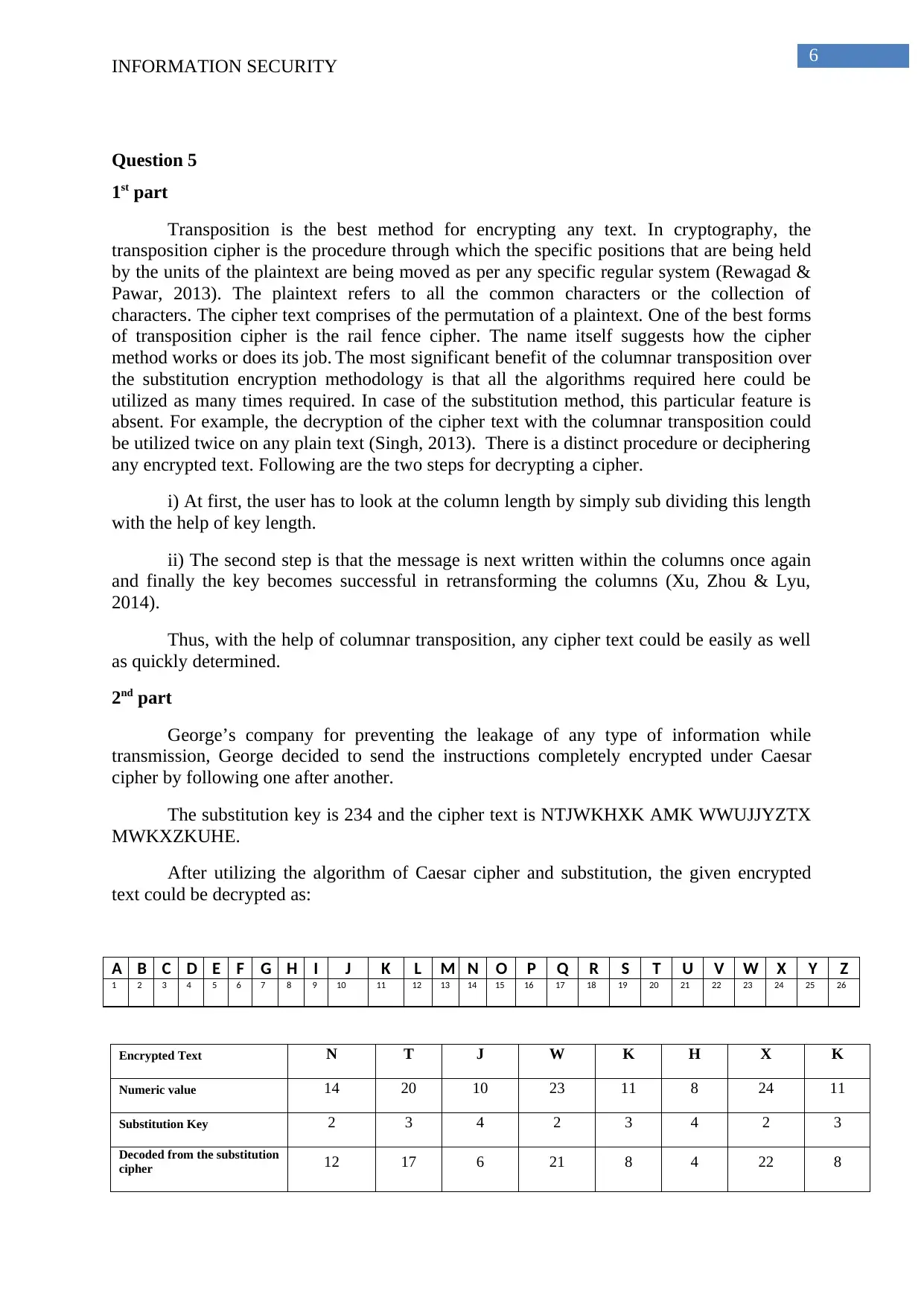
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 21 8 4 22 8
INFORMATION SECURITY
Question 5
1st part
Transposition is the best method for encrypting any text. In cryptography, the
transposition cipher is the procedure through which the specific positions that are being held
by the units of the plaintext are being moved as per any specific regular system (Rewagad &
Pawar, 2013). The plaintext refers to all the common characters or the collection of
characters. The cipher text comprises of the permutation of a plaintext. One of the best forms
of transposition cipher is the rail fence cipher. The name itself suggests how the cipher
method works or does its job. The most significant benefit of the columnar transposition over
the substitution encryption methodology is that all the algorithms required here could be
utilized as many times required. In case of the substitution method, this particular feature is
absent. For example, the decryption of the cipher text with the columnar transposition could
be utilized twice on any plain text (Singh, 2013). There is a distinct procedure or deciphering
any encrypted text. Following are the two steps for decrypting a cipher.
i) At first, the user has to look at the column length by simply sub dividing this length
with the help of key length.
ii) The second step is that the message is next written within the columns once again
and finally the key becomes successful in retransforming the columns (Xu, Zhou & Lyu,
2014).
Thus, with the help of columnar transposition, any cipher text could be easily as well
as quickly determined.
2nd part
George’s company for preventing the leakage of any type of information while
transmission, George decided to send the instructions completely encrypted under Caesar
cipher by following one after another.
The substitution key is 234 and the cipher text is NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE.
After utilizing the algorithm of Caesar cipher and substitution, the given encrypted
text could be decrypted as:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 21 8 4 22 8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INFORMATION SECURITY
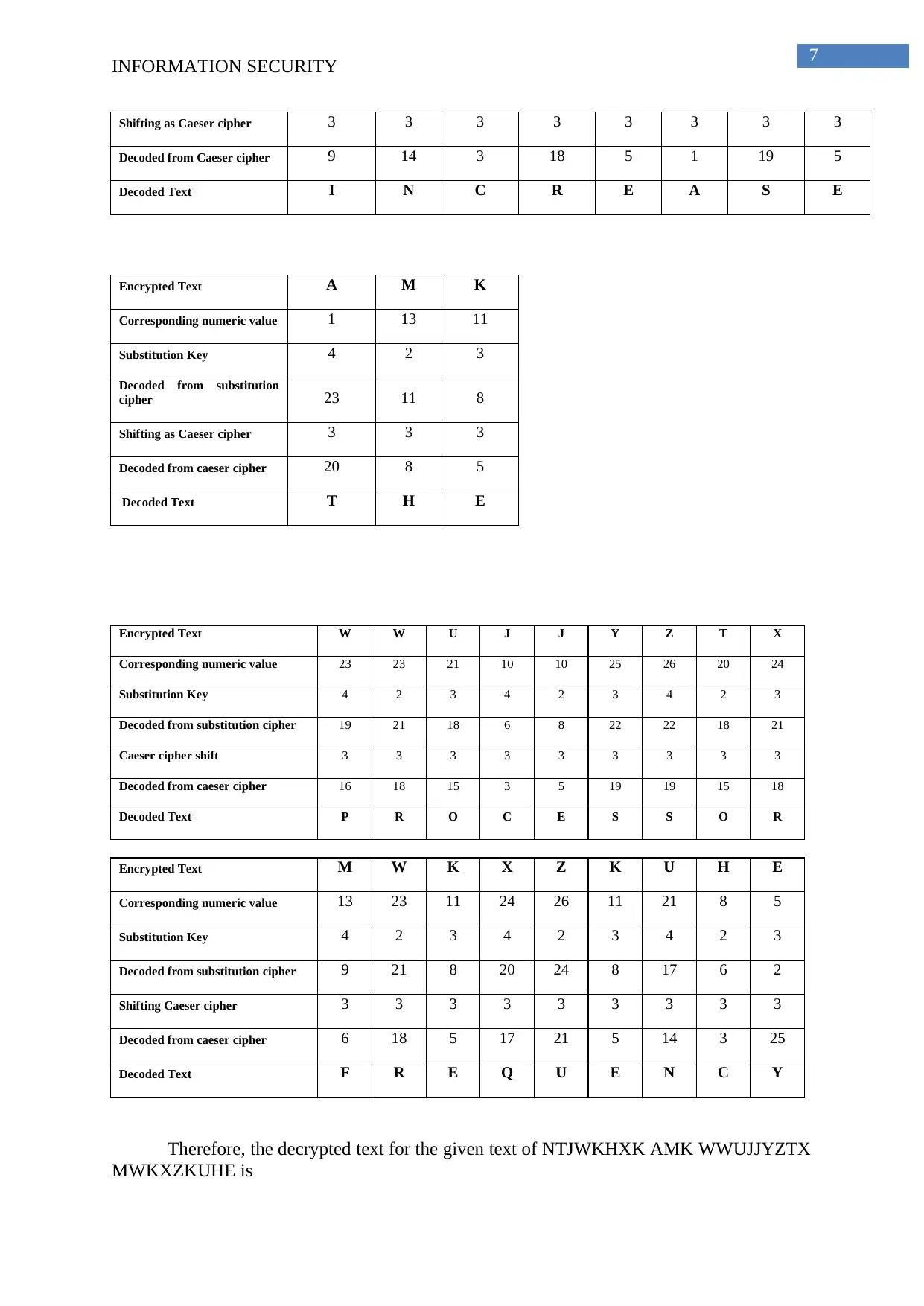
Shifting as Caeser cipher 3 3 3 3 3 3 3 3
Decoded from Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Substitution Key 4 2 3
Decoded from substitution
cipher 23 11 8
Shifting as Caeser cipher 3 3 3
Decoded from caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decrypted text for the given text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
INFORMATION SECURITY
Shifting as Caeser cipher 3 3 3 3 3 3 3 3
Decoded from Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Substitution Key 4 2 3
Decoded from substitution
cipher 23 11 8
Shifting as Caeser cipher 3 3 3
Decoded from caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decrypted text for the given text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is

8
INFORMATION SECURITY
INCREASE THE PROCESSOR FREQUENCY.
INFORMATION SECURITY
INCREASE THE PROCESSOR FREQUENCY.

9
INFORMATION SECURITY
References
Andress, J. (2014). The basics of information security: understanding the fundamentals of
InfoSec in theory and practice. Syngress.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and
influences on adoption. Proc. USEC, 1-2.
Chaudhry, S. A., Mahmood, K., Naqvi, H., & Khan, M. K. (2015). An improved and secure
biometric authentication scheme for telecare medicine information systems based on
elliptic curve cryptography. Journal of Medical Systems, 39(11), 175.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The
role of catalogues of threats and security controls in security risk assessment: an
empirical study with ATM professionals. In International Working Conference on
Requirements Engineering: Foundation for Software Quality (pp. 98-114). Springer,
Cham.
Frank, M., Biedert, R., Ma, E., Martinovic, I., & Song, D. (2013). Touchalytics: On the
applicability of touchscreen input as a behavioral biometric for continuous
authentication. IEEE transactions on information forensics and security, 8(1), 136-
148.
Grama, J. L. (2014). Legal issues in information security. Jones & Bartlett Publishers.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). An enhanced biometric-based authentication
scheme for telecare medicine information systems using elliptic curve
cryptosystem. Journal of medical systems, 39(3), 32.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. CRC Press.
Rewagad, P., & Pawar, Y. (2013, April). Use of digital signature with diffie hellman key
exchange and AES encryption algorithm to enhance data security in cloud computing.
In Communication Systems and Network Technologies (CSNT), 2013 International
Conference on (pp. 437-439). IEEE.
Sayed, B., Traoré, I., Woungang, I., & Obaidat, M. S. (2013). Biometric authentication using
mouse gesture dynamics. IEEE Systems Journal, 7(2), 262-274.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for
information security. International Journal of Computer Applications, 67(19).
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
INFORMATION SECURITY
References
Andress, J. (2014). The basics of information security: understanding the fundamentals of
InfoSec in theory and practice. Syngress.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and
influences on adoption. Proc. USEC, 1-2.
Chaudhry, S. A., Mahmood, K., Naqvi, H., & Khan, M. K. (2015). An improved and secure
biometric authentication scheme for telecare medicine information systems based on
elliptic curve cryptography. Journal of Medical Systems, 39(11), 175.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The
role of catalogues of threats and security controls in security risk assessment: an
empirical study with ATM professionals. In International Working Conference on
Requirements Engineering: Foundation for Software Quality (pp. 98-114). Springer,
Cham.
Frank, M., Biedert, R., Ma, E., Martinovic, I., & Song, D. (2013). Touchalytics: On the
applicability of touchscreen input as a behavioral biometric for continuous
authentication. IEEE transactions on information forensics and security, 8(1), 136-
148.
Grama, J. L. (2014). Legal issues in information security. Jones & Bartlett Publishers.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). An enhanced biometric-based authentication
scheme for telecare medicine information systems using elliptic curve
cryptosystem. Journal of medical systems, 39(3), 32.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. CRC Press.
Rewagad, P., & Pawar, Y. (2013, April). Use of digital signature with diffie hellman key
exchange and AES encryption algorithm to enhance data security in cloud computing.
In Communication Systems and Network Technologies (CSNT), 2013 International
Conference on (pp. 437-439). IEEE.
Sayed, B., Traoré, I., Woungang, I., & Obaidat, M. S. (2013). Biometric authentication using
mouse gesture dynamics. IEEE Systems Journal, 7(2), 262-274.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for
information security. International Journal of Computer Applications, 67(19).
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10
INFORMATION SECURITY
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Xu, H., Zhou, Y., & Lyu, M. R. (2014, July). Towards continuous and passive authentication
via touch biometrics: An experimental study on smartphones. In Symposium On
Usable Privacy and Security, SOUPS (Vol. 14, pp. 187-198).
INFORMATION SECURITY
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Xu, H., Zhou, Y., & Lyu, M. R. (2014, July). Towards continuous and passive authentication
via touch biometrics: An experimental study on smartphones. In Symposium On
Usable Privacy and Security, SOUPS (Vol. 14, pp. 187-198).
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



