Importance of HTTPS in Website Security
VerifiedAdded on 2022/11/28
|37
|6568
|166
AI Summary
This article discusses the importance of HTTPS in website security and how it protects sensitive information from hackers. It explains the difference between HTTP and HTTPS and highlights why businesses should use HTTPS for secure communication.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Author Note
INFORMATION SECURITY
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INFORMATION SECURITY 1
Question 1:
Bring Your Own Device (BYOD) Policy:
The Bring Your Own Device policy is important for organizations and corporation as
it help the corporation control the usage of this mobile device which when left uncontrolled
can be used by attacker to launch malwares and serious data breaches at the corporation if no
formal policy is established (Wilkins, 2014) . It is therefore vital for organization to have
some formal Bring Your Own Device policy in place. This report discuss the Bring Your
Own Device policy of Sydney University and Victoria university focusing on the components
of their individual policy which shall inform the report to formulate a bring your own device
policy for the organisation. The Sydney University deals with a large number of students and
stand who have access to the university network using their own devices. It is therefore vital
for the university to have clear formal policy on the BYOD policy. The policy has the
following components:
Security of the university data on this device was a key component of the policy. In
this component, the university has defined what is considers as sensitive data through their
data classification schemes and use the scheme to define what each entity in the university
domain can access what regardless of their device they using.
The second component to the policy defines what the IT department is mandated to
do. It is clear the university has not completely abandon control of the employees and
students devices. The policy has defined the minimum software recommended for the mobile
devices to have in order to access some of the university critical systems and data. The role of
IT in event of a cyber-security incident is again outlined in the policy document. This
includes active incident response plans and disaster recovery mechanism in case of a cyber-
Question 1:
Bring Your Own Device (BYOD) Policy:
The Bring Your Own Device policy is important for organizations and corporation as
it help the corporation control the usage of this mobile device which when left uncontrolled
can be used by attacker to launch malwares and serious data breaches at the corporation if no
formal policy is established (Wilkins, 2014) . It is therefore vital for organization to have
some formal Bring Your Own Device policy in place. This report discuss the Bring Your
Own Device policy of Sydney University and Victoria university focusing on the components
of their individual policy which shall inform the report to formulate a bring your own device
policy for the organisation. The Sydney University deals with a large number of students and
stand who have access to the university network using their own devices. It is therefore vital
for the university to have clear formal policy on the BYOD policy. The policy has the
following components:
Security of the university data on this device was a key component of the policy. In
this component, the university has defined what is considers as sensitive data through their
data classification schemes and use the scheme to define what each entity in the university
domain can access what regardless of their device they using.
The second component to the policy defines what the IT department is mandated to
do. It is clear the university has not completely abandon control of the employees and
students devices. The policy has defined the minimum software recommended for the mobile
devices to have in order to access some of the university critical systems and data. The role of
IT in event of a cyber-security incident is again outlined in the policy document. This
includes active incident response plans and disaster recovery mechanism in case of a cyber-

2INFORMATION SECURITY
attack on the university’s network that can emancipate from a breach through the mobile
devices usage on the university network.
The third most critical component of the policy outlines the acceptable usage of the
university’s network using the mobile device. This includes the acceptable usage of the
university’s network infrastructure, data and systems. This has been strategically been put in
place to avoid the university being liable in case its resources is used by rogue student’s to
commit a cyber-attack or data breaches on other system which is not uncommon in most of
the universities.
The fourth part of the policy outlines the university due diligence in terms of
providing education and creation of awareness to ensure the students are aware of the dangers
the devices which are not properly controlled can wreak havoc not only to the student’s own
data but also to the university as a whole. The same applies to the staff of the university.
Victoria University, which was the second case study of the report, had more less the
same outline in terms of the key components of the BYOD policy. The university has
included a policy clause on monitoring of the user devices in terms of traffic exchanges
between the user devices and the university systems and application.
The personal cloud used by students and staff is again added to the policy where the
policy has outline to take no liability for the user data in their own personal clouds
From the above case study, the following policy can be adopted by the university to
properly managed the user devices
Policy audience and purpose: This policy addresses all the staff and the students’ personal
devices which includes but not limited to smartphones, tablets and laptops hereinafter
referred to as BYOD
attack on the university’s network that can emancipate from a breach through the mobile
devices usage on the university network.
The third most critical component of the policy outlines the acceptable usage of the
university’s network using the mobile device. This includes the acceptable usage of the
university’s network infrastructure, data and systems. This has been strategically been put in
place to avoid the university being liable in case its resources is used by rogue student’s to
commit a cyber-attack or data breaches on other system which is not uncommon in most of
the universities.
The fourth part of the policy outlines the university due diligence in terms of
providing education and creation of awareness to ensure the students are aware of the dangers
the devices which are not properly controlled can wreak havoc not only to the student’s own
data but also to the university as a whole. The same applies to the staff of the university.
Victoria University, which was the second case study of the report, had more less the
same outline in terms of the key components of the BYOD policy. The university has
included a policy clause on monitoring of the user devices in terms of traffic exchanges
between the user devices and the university systems and application.
The personal cloud used by students and staff is again added to the policy where the
policy has outline to take no liability for the user data in their own personal clouds
From the above case study, the following policy can be adopted by the university to
properly managed the user devices
Policy audience and purpose: This policy addresses all the staff and the students’ personal
devices which includes but not limited to smartphones, tablets and laptops hereinafter
referred to as BYOD

3INFORMATION SECURITY
General principle: Ensure the device your own is properly protected to safeguard its data
Policy statements:
Users must set up passwords or passphrases for devices used in the university network
Users must ensure their devices’ software’s are up to date
Users must ensure the university data are backup in some way to ensure recovery in
case of theft
Users must securely delete user and university data when no longer using the devices
Users must configure their devices to be able to remote wipe in case of theft
Users must ensure their devices have up to date antivirus on their devices
Users must always disable wireless and the Bluetooth survives when not in use
Compliance:
Failure to follow the policy can be used against the user when such devices is used to
cause data breached, which has legal implication. This can attract a fine of not less than
$500,000. The user may be subjected to disciplinary hearings, which may lead to dismal from
the university
Question 2
Zero-Day Attacks:
Zero data attacks according to security experts are deemed as the most dangerous
security attacks in the cyber security domain (Zhou & Pezaros, 2019). A survey by (Vishal
Sharma et al., 2017) indicates that nearly a third of corporations have been compromised by
the zero day attacks in the past one year. These attacks are extremely costly as on average $7
million is spent on mitigating such attacks. This reports focused on some highly reported zero
General principle: Ensure the device your own is properly protected to safeguard its data
Policy statements:
Users must set up passwords or passphrases for devices used in the university network
Users must ensure their devices’ software’s are up to date
Users must ensure the university data are backup in some way to ensure recovery in
case of theft
Users must securely delete user and university data when no longer using the devices
Users must configure their devices to be able to remote wipe in case of theft
Users must ensure their devices have up to date antivirus on their devices
Users must always disable wireless and the Bluetooth survives when not in use
Compliance:
Failure to follow the policy can be used against the user when such devices is used to
cause data breached, which has legal implication. This can attract a fine of not less than
$500,000. The user may be subjected to disciplinary hearings, which may lead to dismal from
the university
Question 2
Zero-Day Attacks:
Zero data attacks according to security experts are deemed as the most dangerous
security attacks in the cyber security domain (Zhou & Pezaros, 2019). A survey by (Vishal
Sharma et al., 2017) indicates that nearly a third of corporations have been compromised by
the zero day attacks in the past one year. These attacks are extremely costly as on average $7
million is spent on mitigating such attacks. This reports focused on some highly reported zero
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4INFORMATION SECURITY
day attacks, how the zero day vulnerabilities are discovered and some mitigation strategies
recommended by the report (Shaer, 2014).
A zero day vulnerability is a security flaw in software that may be known to the
vendor of the but currently has no patch to it hence is risky since cyber criminals can exploit
that vulnerability by writing zero day attack exploits. The terms zero day is used to refer to
the newly learnt vulnerability in software. Since the developers has just learnt about the flaw,
no proper patches or fixes has been developed, making it easily exploited by the attackers
(Pierre et al, 2018).
The zero day vulnerabilities can be discovered by several means. First, security
researcher can use their systems and application to discover the vulnerabilities. The
researchers always try to seal the information on such vulnerability to avoid the bad people
from knowing about it hence giving the developers time to write patches on the vulnerability.
They may even go ahead and inform the developers of such discovered vulnerabilities
(Nakao et al., 2009). Secondly, the developers themselves when doing the rotational patches
onto their systems and applications can discovered a vulnerability, which currently they have
not figured a fix for. This again is less threat to the users as the developers will try to keep the
information a secret and try out some patches to fix the vulnerability. However, if the hackers
use their tools to discover the vulnerability, they normally make such vulnerable public
causing the rush between the developers and hackers (Huang, Siegel, & Madnick, 2018). The
hackers will rush to exploit the vulnerability before it is fixed while the developers are trying
to write patches and fixes for the same security flaws before a potential zero day exploits is
exposed to the users. Such kind of zero day attacks have been reported widely onto the
internet. The mostly publicly exposed was the stunt worm attack. The attackers behind the
stunt worm used up to four zero day’s vulnerabilities in the windows operating system. The
worm was targeted at Siemen’s PLC used by the Iran nuclear program (Radziwill, 2018). The
day attacks, how the zero day vulnerabilities are discovered and some mitigation strategies
recommended by the report (Shaer, 2014).
A zero day vulnerability is a security flaw in software that may be known to the
vendor of the but currently has no patch to it hence is risky since cyber criminals can exploit
that vulnerability by writing zero day attack exploits. The terms zero day is used to refer to
the newly learnt vulnerability in software. Since the developers has just learnt about the flaw,
no proper patches or fixes has been developed, making it easily exploited by the attackers
(Pierre et al, 2018).
The zero day vulnerabilities can be discovered by several means. First, security
researcher can use their systems and application to discover the vulnerabilities. The
researchers always try to seal the information on such vulnerability to avoid the bad people
from knowing about it hence giving the developers time to write patches on the vulnerability.
They may even go ahead and inform the developers of such discovered vulnerabilities
(Nakao et al., 2009). Secondly, the developers themselves when doing the rotational patches
onto their systems and applications can discovered a vulnerability, which currently they have
not figured a fix for. This again is less threat to the users as the developers will try to keep the
information a secret and try out some patches to fix the vulnerability. However, if the hackers
use their tools to discover the vulnerability, they normally make such vulnerable public
causing the rush between the developers and hackers (Huang, Siegel, & Madnick, 2018). The
hackers will rush to exploit the vulnerability before it is fixed while the developers are trying
to write patches and fixes for the same security flaws before a potential zero day exploits is
exposed to the users. Such kind of zero day attacks have been reported widely onto the
internet. The mostly publicly exposed was the stunt worm attack. The attackers behind the
stunt worm used up to four zero day’s vulnerabilities in the windows operating system. The
worm was targeted at Siemen’s PLC used by the Iran nuclear program (Radziwill, 2018). The

5INFORMATION SECURITY
worm exploited the four zero day vulnerabilities in Microsoft to breach the PLC of Siemens
and make them function abnormally thereby not able to enrich Uranium for the Nuclear
program of Iran. This zero day attack spread across the Internet and was discovered by the
Kaspersky antivirus group who made their research public. It took Microsoft up to four years
to fix the zero days making numerous computer system using the Microsoft OS susceptible to
the stunt worm (Kerner, 2015).
The second zero day was attack on the Swift banking network where reportedly
millions of dollar was stolen. This was first reported by central bank of Bangladesh where
attackers taken advantage of zero day in Microsoft windows OS to launch attack from
unpatched end points in the Bangladesh central bank systems as easily got into the swift
network (Wojcik, 2014). This caused loss of millions of dollars due to the failure of the
patching of the systems at the Bangladesh central bank system.
From the literature, it is critical for organization to organized mitigation strategies for
zero day attacks, the report recommends the following strategies. First, the company should
put limits on the type of email attachments that can be sent or received in the network.
Second, install firewall to carefully scan the inbound and outbound traffic through the
organization for any abnormally. Third, that should be well-established disaster recovery
procedure in place in case a zero day exploit materialize.
Question 3:
Diffie-Helman Research:
The diffie helman algorithm is utilized for establishing one secret key which can be
used for the communication that remain secret at the time of exchanging data over the public
network by utilizing the elliptic curve for generating the points as well as for getting the
private key by utilizing the parameters. The diffie-helman key exchange algorithm can solve
worm exploited the four zero day vulnerabilities in Microsoft to breach the PLC of Siemens
and make them function abnormally thereby not able to enrich Uranium for the Nuclear
program of Iran. This zero day attack spread across the Internet and was discovered by the
Kaspersky antivirus group who made their research public. It took Microsoft up to four years
to fix the zero days making numerous computer system using the Microsoft OS susceptible to
the stunt worm (Kerner, 2015).
The second zero day was attack on the Swift banking network where reportedly
millions of dollar was stolen. This was first reported by central bank of Bangladesh where
attackers taken advantage of zero day in Microsoft windows OS to launch attack from
unpatched end points in the Bangladesh central bank systems as easily got into the swift
network (Wojcik, 2014). This caused loss of millions of dollars due to the failure of the
patching of the systems at the Bangladesh central bank system.
From the literature, it is critical for organization to organized mitigation strategies for
zero day attacks, the report recommends the following strategies. First, the company should
put limits on the type of email attachments that can be sent or received in the network.
Second, install firewall to carefully scan the inbound and outbound traffic through the
organization for any abnormally. Third, that should be well-established disaster recovery
procedure in place in case a zero day exploit materialize.
Question 3:
Diffie-Helman Research:
The diffie helman algorithm is utilized for establishing one secret key which can be
used for the communication that remain secret at the time of exchanging data over the public
network by utilizing the elliptic curve for generating the points as well as for getting the
private key by utilizing the parameters. The diffie-helman key exchange algorithm can solve

6INFORMATION SECURITY
the following dilemma. Bob and Alice agree for sharing a secret key to utilize in a symmetric
cipher. However, the only means of their communication is not so secure. Each of the pieces
of the information that are exchanged within them has been countered by their adversary
EVE. How this is possible for Bob and Alice to share the key without informing EVE. For
the first time this appears that, Bob and Alice this is appearing that the issues that are
associated with the discrete logarithm problem for Fp gives a possible solution for the
problem. The protocol is not in any used in exchanging the data in public key encryption but
it is however used in exchanging the cryptographic keys which shall be later be used in
securing the data being exchanges by the parties involved in the communication via the
unsecure channel. This mechanism is particularly useful in case the two parties are using non
secure channel like the Internet to exchange information hence needs a way to ensure even if
the attacker gains access to the traffic, which they can easily sniff, the protocol shall ensure
the attacker will have difficult time figuring out the keys used in the data encryption hence
will not be able to breach the data on transit.
In this protocol, the two parties creates private and public key pairs where the private key is
only known to the party while the public key is published and communicated to the other
parties involved in the communication. The protocol uses the concept of elliptic curves to
ensure the keys i.e. private and public keys are different but mathematically related to each
other in a sense that that the same unique private key can be calculated on both sides of the
communication using the ones private key and the other side’s public key. The complexity of
the algorithm relies on exponential modulo of the prime numbers sets.
The primary step for both Bob and Alice is to agree on huge prime p as well as one non-zero
integer g modulo p. Bob and Alice create the values that are associated with g and p public
knowledge; as example Bob and Alice may post the values on the web sites of them.
the following dilemma. Bob and Alice agree for sharing a secret key to utilize in a symmetric
cipher. However, the only means of their communication is not so secure. Each of the pieces
of the information that are exchanged within them has been countered by their adversary
EVE. How this is possible for Bob and Alice to share the key without informing EVE. For
the first time this appears that, Bob and Alice this is appearing that the issues that are
associated with the discrete logarithm problem for Fp gives a possible solution for the
problem. The protocol is not in any used in exchanging the data in public key encryption but
it is however used in exchanging the cryptographic keys which shall be later be used in
securing the data being exchanges by the parties involved in the communication via the
unsecure channel. This mechanism is particularly useful in case the two parties are using non
secure channel like the Internet to exchange information hence needs a way to ensure even if
the attacker gains access to the traffic, which they can easily sniff, the protocol shall ensure
the attacker will have difficult time figuring out the keys used in the data encryption hence
will not be able to breach the data on transit.
In this protocol, the two parties creates private and public key pairs where the private key is
only known to the party while the public key is published and communicated to the other
parties involved in the communication. The protocol uses the concept of elliptic curves to
ensure the keys i.e. private and public keys are different but mathematically related to each
other in a sense that that the same unique private key can be calculated on both sides of the
communication using the ones private key and the other side’s public key. The complexity of
the algorithm relies on exponential modulo of the prime numbers sets.
The primary step for both Bob and Alice is to agree on huge prime p as well as one non-zero
integer g modulo p. Bob and Alice create the values that are associated with g and p public
knowledge; as example Bob and Alice may post the values on the web sites of them.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
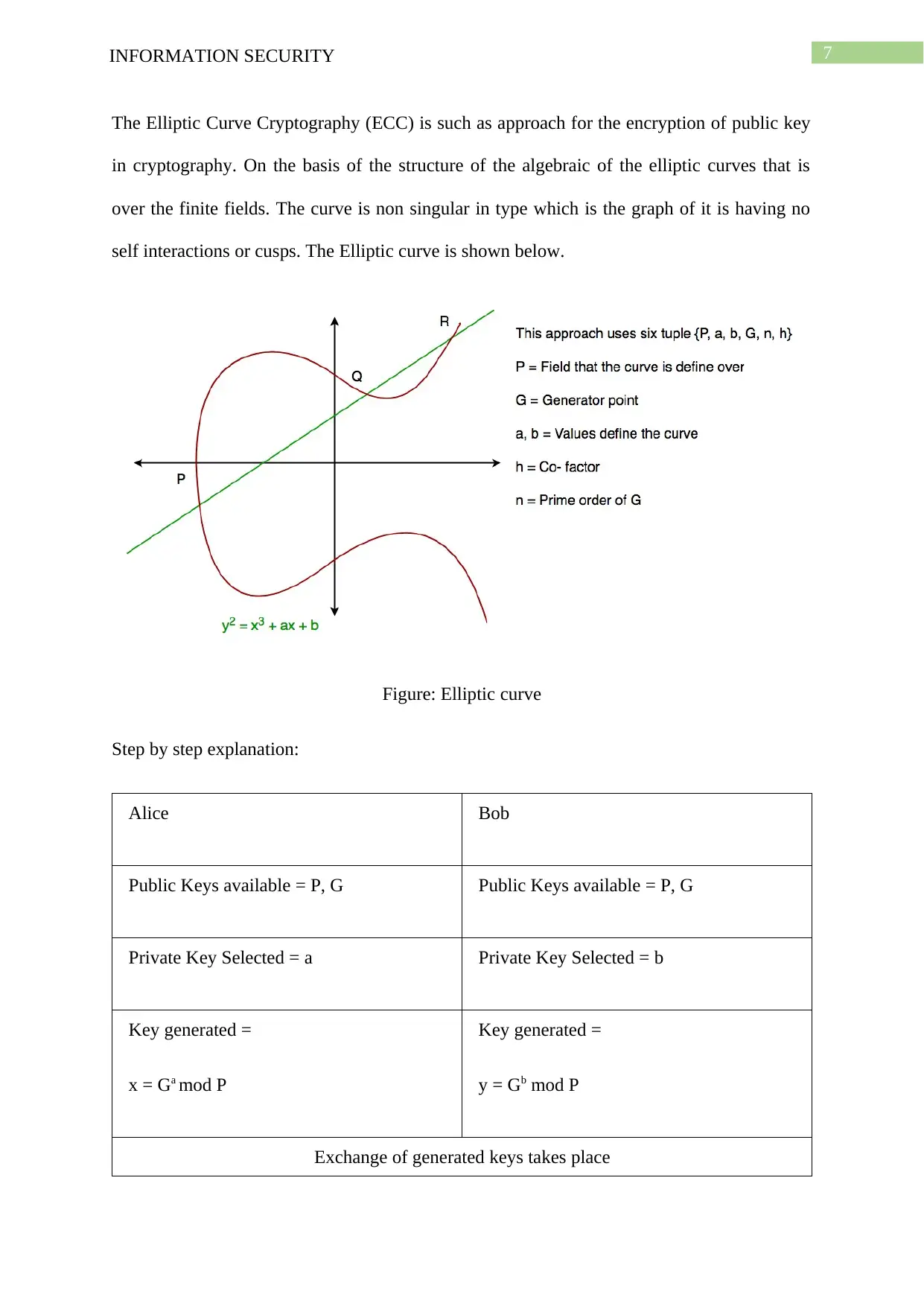
7INFORMATION SECURITY
The Elliptic Curve Cryptography (ECC) is such as approach for the encryption of public key
in cryptography. On the basis of the structure of the algebraic of the elliptic curves that is
over the finite fields. The curve is non singular in type which is the graph of it is having no
self interactions or cusps. The Elliptic curve is shown below.
Figure: Elliptic curve
Step by step explanation:
Alice Bob
Public Keys available = P, G Public Keys available = P, G
Private Key Selected = a Private Key Selected = b
Key generated =
x = Ga mod P
Key generated =
y = Gb mod P
Exchange of generated keys takes place
The Elliptic Curve Cryptography (ECC) is such as approach for the encryption of public key
in cryptography. On the basis of the structure of the algebraic of the elliptic curves that is
over the finite fields. The curve is non singular in type which is the graph of it is having no
self interactions or cusps. The Elliptic curve is shown below.
Figure: Elliptic curve
Step by step explanation:
Alice Bob
Public Keys available = P, G Public Keys available = P, G
Private Key Selected = a Private Key Selected = b
Key generated =
x = Ga mod P
Key generated =
y = Gb mod P
Exchange of generated keys takes place

8INFORMATION SECURITY
Key received = y key received = x
Generated Secret Key =
ka = ya mod P
Generated Secret Key =
kb = xb mod P
Algebraically it can be shown that ka = kb
Users now have a symmetric secret key to encrypt
Example:
Step 1:
Alice and Bob get the public numbers P = 23, G = 9
Step 2: Alice selected a private key a = 4 and
Bob selected a private key b = 3
Step 3: Alice & Bob compute public values
Alice: x =(9^4 mod 23) = (6561 mod 23) = 6
Bob: y = (9^3 mod 23) = (729 mod 23) = 16
Step 4: Alice & Bob exchange public numbers
Step 5: Alice receives public key y =16 and
Bob receives public key x = 6
Key received = y key received = x
Generated Secret Key =
ka = ya mod P
Generated Secret Key =
kb = xb mod P
Algebraically it can be shown that ka = kb
Users now have a symmetric secret key to encrypt
Example:
Step 1:
Alice and Bob get the public numbers P = 23, G = 9
Step 2: Alice selected a private key a = 4 and
Bob selected a private key b = 3
Step 3: Alice & Bob compute public values
Alice: x =(9^4 mod 23) = (6561 mod 23) = 6
Bob: y = (9^3 mod 23) = (729 mod 23) = 16
Step 4: Alice & Bob exchange public numbers
Step 5: Alice receives public key y =16 and
Bob receives public key x = 6

9INFORMATION SECURITY
Step 6: The symmetric keys are computed by Bob and Alice
Alice: ka = y^a mod p = 65536 mod 23 = 9
Bob: kb = x^b mod p = 216 mod 23 = 9
Step 7: The secret key is 9
Question 4:
The term HTTPS is an abbreviation for hypertext exchange convention secure. The
abbreviation goes before the URL in a site address. Barely any individuals know about its
importance. The HTTPS is just about a precise of the ordinary hypertext exchange
convention, this variant of this is distinctive in light of the fact that the "S" toward the end
recognizes this as it is having a protected HTTP association. A HTTPS association is utilized
every now and again in organizations where touchy data, for example, government disability
numbers and Mastercard numbers that have been passed with the purpose of procurement
destinations or the payment of bills locales. The hypertext exchange convention secure gives
confirmation that programmers are not ready to block the message that contain touchy
information as it heads towards the server. To comprehend the HTTPS convention,
comprehend that HTTPS is certainly not a different convention from HTTP. It is just a safe
variety. Sending messages by means of a scrambled Secure Sockets Layer (SSL) or Transport
Layer Security (TLS) association gives clients a sensible measure of assurance from meddlers
and go-between assaults that have the ability to siphon significant data or access specific
servers that are private.
It is a down to earth path for individuals who are new to the risks of programmers and
different issues to know which are utilizing a protected informing framework. It is likewise
every now and again suggested, even on site pages, that individuals who don't see HTTPS
toward the start of the URL in the location bar ought not to enter any delicate data, not
Step 6: The symmetric keys are computed by Bob and Alice
Alice: ka = y^a mod p = 65536 mod 23 = 9
Bob: kb = x^b mod p = 216 mod 23 = 9
Step 7: The secret key is 9
Question 4:
The term HTTPS is an abbreviation for hypertext exchange convention secure. The
abbreviation goes before the URL in a site address. Barely any individuals know about its
importance. The HTTPS is just about a precise of the ordinary hypertext exchange
convention, this variant of this is distinctive in light of the fact that the "S" toward the end
recognizes this as it is having a protected HTTP association. A HTTPS association is utilized
every now and again in organizations where touchy data, for example, government disability
numbers and Mastercard numbers that have been passed with the purpose of procurement
destinations or the payment of bills locales. The hypertext exchange convention secure gives
confirmation that programmers are not ready to block the message that contain touchy
information as it heads towards the server. To comprehend the HTTPS convention,
comprehend that HTTPS is certainly not a different convention from HTTP. It is just a safe
variety. Sending messages by means of a scrambled Secure Sockets Layer (SSL) or Transport
Layer Security (TLS) association gives clients a sensible measure of assurance from meddlers
and go-between assaults that have the ability to siphon significant data or access specific
servers that are private.
It is a down to earth path for individuals who are new to the risks of programmers and
different issues to know which are utilizing a protected informing framework. It is likewise
every now and again suggested, even on site pages, that individuals who don't see HTTPS
toward the start of the URL in the location bar ought not to enter any delicate data, not
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10INFORMATION SECURITY
exclusively to ensure the guest to the site, however to secure the site's notoriety for being
admirably.
HTTP: No Data Encryption Implemented
Each URL interface that starts with HTTP utilizes a fundamental sort of "hypertext exchange
convention". Made by Tim Berners-Lee back in the mid 1990's, the point at which the web
was still in the early stages, this system convention standard is the thing that permits internet
servers and the browsers to impart through the trading of information.
HTTPS: Encrypted Connections
HTTPS is not something contrary to HTTP; however, it is more youthful cousin. The two are
the equivalent, in that the two allude to the equivalent "hypertext exchange convention" that
empowers mentioned web information to be exhibited on the screen. However, HTTPS is still
marginally unique, further developed, and significantly more secure. It is a down to earth
path for individuals who are new to the risks of programmers and different issues to know
which are utilizing a protected informing framework. It is likewise every now and again
suggested, even on site pages, that individuals who don't see HTTPS toward the start of the
URL in the location bar ought not to enter any delicate data, not exclusively to ensure the
guest to the site, however to secure the site's notoriety for being admirably. HTTPS
convention is an augmentation of HTTP. That "S" in the shortened form originates from the
word Secure and it is controlled by Transport Layer Security (TLS) [the successor to Secure
Sockets Layer (SSL)], the security that is standard innovation that builds up an encoded
association between a program and web server.
The Advantages and Disadvantages of HTTPS
As talked about above, HTTPS guarantees digital wellbeing. It is, undoubtedly, a superior
system convention arrangement than its more established cousin, HTTP.
exclusively to ensure the guest to the site, however to secure the site's notoriety for being
admirably.
HTTP: No Data Encryption Implemented
Each URL interface that starts with HTTP utilizes a fundamental sort of "hypertext exchange
convention". Made by Tim Berners-Lee back in the mid 1990's, the point at which the web
was still in the early stages, this system convention standard is the thing that permits internet
servers and the browsers to impart through the trading of information.
HTTPS: Encrypted Connections
HTTPS is not something contrary to HTTP; however, it is more youthful cousin. The two are
the equivalent, in that the two allude to the equivalent "hypertext exchange convention" that
empowers mentioned web information to be exhibited on the screen. However, HTTPS is still
marginally unique, further developed, and significantly more secure. It is a down to earth
path for individuals who are new to the risks of programmers and different issues to know
which are utilizing a protected informing framework. It is likewise every now and again
suggested, even on site pages, that individuals who don't see HTTPS toward the start of the
URL in the location bar ought not to enter any delicate data, not exclusively to ensure the
guest to the site, however to secure the site's notoriety for being admirably. HTTPS
convention is an augmentation of HTTP. That "S" in the shortened form originates from the
word Secure and it is controlled by Transport Layer Security (TLS) [the successor to Secure
Sockets Layer (SSL)], the security that is standard innovation that builds up an encoded
association between a program and web server.
The Advantages and Disadvantages of HTTPS
As talked about above, HTTPS guarantees digital wellbeing. It is, undoubtedly, a superior
system convention arrangement than its more established cousin, HTTP.

11INFORMATION SECURITY
Nevertheless, is HTTPS about the focal points? Maybe there is a disadvantage to everything?
We should discover.
The Advantages of Using HTTPS
The security related benefits referenced above - validating the server, encoding information
transmission, and shielding the trades from altering - are the undeniable fundamental
favourable circumstances to utilizing HTTPS. Site administrators need and need to ensure
their guests information (HTTPS is really a prerequisite for any destinations gathering
instalment data as per the PCI Data Security Standard) and site guests need to realize that
their information is being transmitted safely.
The developing interest for information protection as well as the security that is from the
overall population is another bit of leeway to utilizing HTTPS. Truth be told, agreeing to
Make the Websites, 13% of entire truck surrender is because of instalment concerns of the
security. Site guests need to realize that they are able to confide in your site, particularly in
the event that they have been entering budgetary subtleties, and utilizing HTTPS is one of the
approaches to do that (for example it's single direction to demonstrate your guests that any
data that is entered by them will be scrambled).
Question 5:
Task 1:
Cipher text:
ij ticvs ij rat zgzra fthrxcs e.f. rat jwicrihj tjrievgjatm rat zgcjr jsjrtb qz bgvgrics
fcswrqnciwas. fcswrqnciwas gh grj ticvs sticj ctjtbevtm ltcs bxfa jtfctr dcgrghn. rat dtvv
uhqdh fitjic fgwatc, dagfa dij xjtm rq thfcswr bgvgrics qcmtcj, gj ih tkibwvt qz ragj
nthtcirgqh. gh ragj jsjrtb faicifrtcj dtct rcihjzqcbtm xjghn i ltcs jgbwvt jxejrgrxrgqh.
Nevertheless, is HTTPS about the focal points? Maybe there is a disadvantage to everything?
We should discover.
The Advantages of Using HTTPS
The security related benefits referenced above - validating the server, encoding information
transmission, and shielding the trades from altering - are the undeniable fundamental
favourable circumstances to utilizing HTTPS. Site administrators need and need to ensure
their guests information (HTTPS is really a prerequisite for any destinations gathering
instalment data as per the PCI Data Security Standard) and site guests need to realize that
their information is being transmitted safely.
The developing interest for information protection as well as the security that is from the
overall population is another bit of leeway to utilizing HTTPS. Truth be told, agreeing to
Make the Websites, 13% of entire truck surrender is because of instalment concerns of the
security. Site guests need to realize that they are able to confide in your site, particularly in
the event that they have been entering budgetary subtleties, and utilizing HTTPS is one of the
approaches to do that (for example it's single direction to demonstrate your guests that any
data that is entered by them will be scrambled).
Question 5:
Task 1:
Cipher text:
ij ticvs ij rat zgzra fthrxcs e.f. rat jwicrihj tjrievgjatm rat zgcjr jsjrtb qz bgvgrics
fcswrqnciwas. fcswrqnciwas gh grj ticvs sticj ctjtbevtm ltcs bxfa jtfctr dcgrghn. rat dtvv
uhqdh fitjic fgwatc, dagfa dij xjtm rq thfcswr bgvgrics qcmtcj, gj ih tkibwvt qz ragj
nthtcirgqh. gh ragj jsjrtb faicifrtcj dtct rcihjzqcbtm xjghn i ltcs jgbwvt jxejrgrxrgqh.
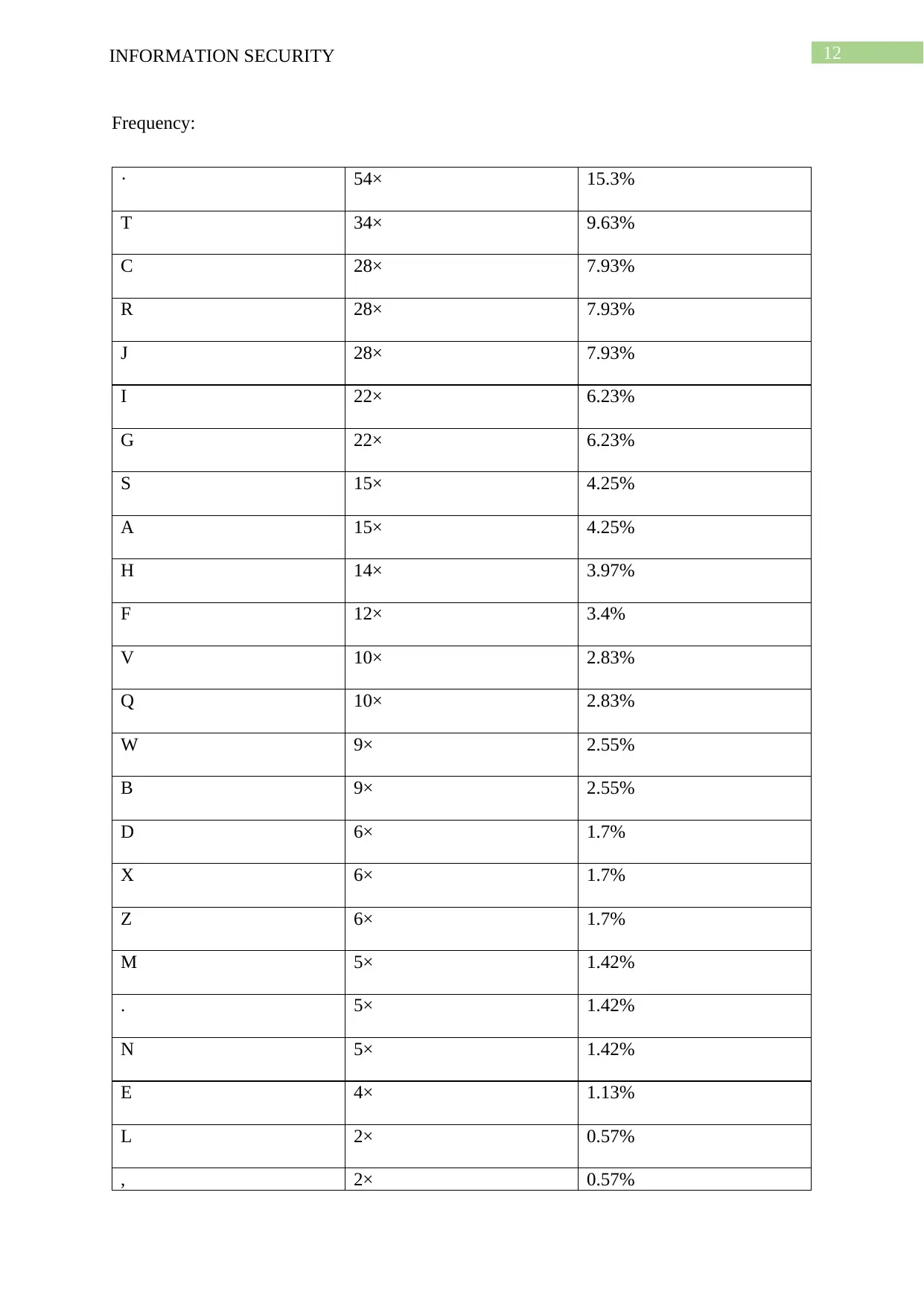
12INFORMATION SECURITY
Frequency:
· 54× 15.3%
T 34× 9.63%
C 28× 7.93%
R 28× 7.93%
J 28× 7.93%
I 22× 6.23%
G 22× 6.23%
S 15× 4.25%
A 15× 4.25%
H 14× 3.97%
F 12× 3.4%
V 10× 2.83%
Q 10× 2.83%
W 9× 2.55%
B 9× 2.55%
D 6× 1.7%
X 6× 1.7%
Z 6× 1.7%
M 5× 1.42%
. 5× 1.42%
N 5× 1.42%
E 4× 1.13%
L 2× 0.57%
, 2× 0.57%
Frequency:
· 54× 15.3%
T 34× 9.63%
C 28× 7.93%
R 28× 7.93%
J 28× 7.93%
I 22× 6.23%
G 22× 6.23%
S 15× 4.25%
A 15× 4.25%
H 14× 3.97%
F 12× 3.4%
V 10× 2.83%
Q 10× 2.83%
W 9× 2.55%
B 9× 2.55%
D 6× 1.7%
X 6× 1.7%
Z 6× 1.7%
M 5× 1.42%
. 5× 1.42%
N 5× 1.42%
E 4× 1.13%
L 2× 0.57%
, 2× 0.57%
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
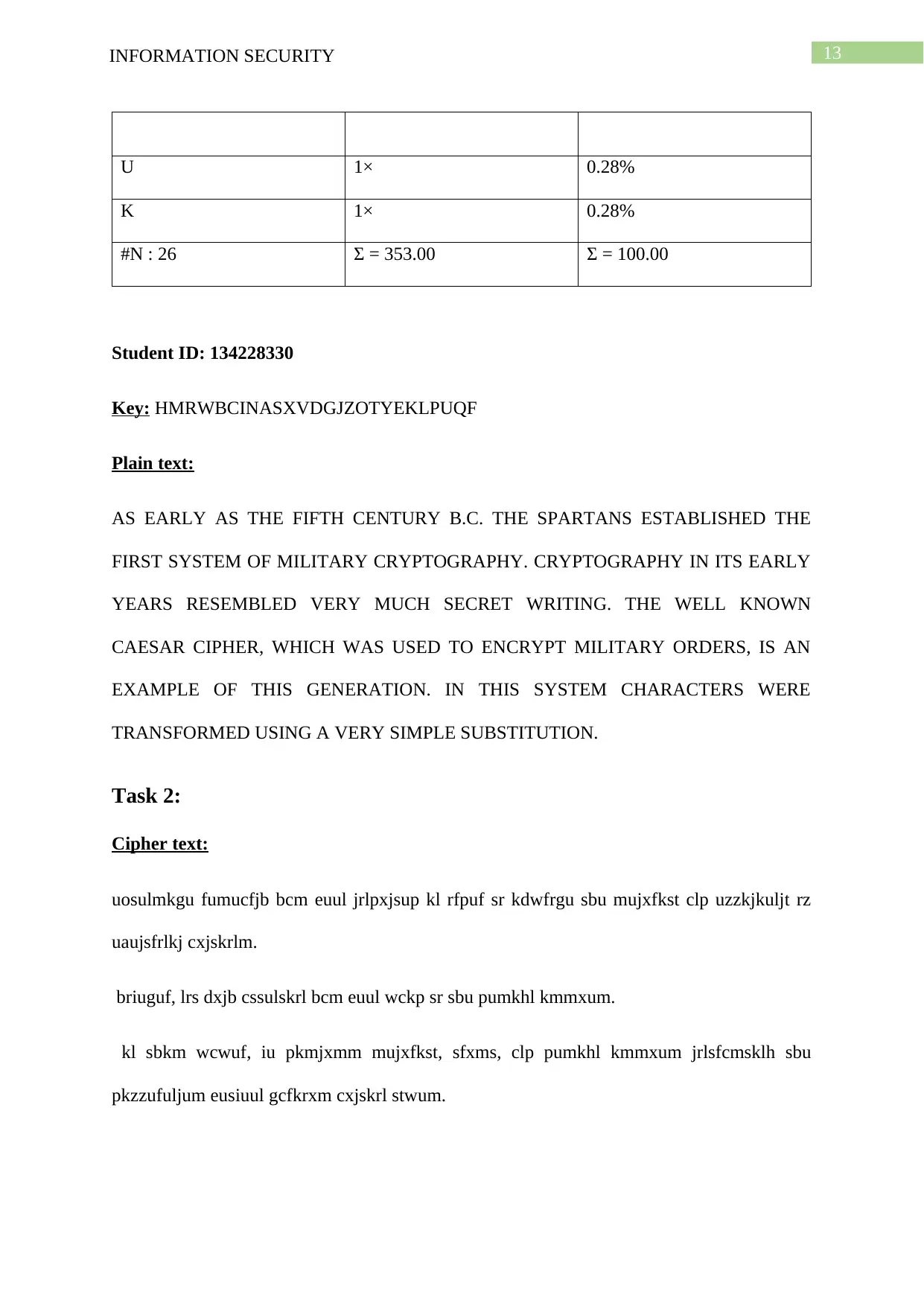
13INFORMATION SECURITY
U 1× 0.28%
K 1× 0.28%
#N : 26 Σ = 353.00 Σ = 100.00
Student ID: 134228330
Key: HMRWBCINASXVDGJZOTYEKLPUQF
Plain text:
AS EARLY AS THE FIFTH CENTURY B.C. THE SPARTANS ESTABLISHED THE
FIRST SYSTEM OF MILITARY CRYPTOGRAPHY. CRYPTOGRAPHY IN ITS EARLY
YEARS RESEMBLED VERY MUCH SECRET WRITING. THE WELL KNOWN
CAESAR CIPHER, WHICH WAS USED TO ENCRYPT MILITARY ORDERS, IS AN
EXAMPLE OF THIS GENERATION. IN THIS SYSTEM CHARACTERS WERE
TRANSFORMED USING A VERY SIMPLE SUBSTITUTION.
Task 2:
Cipher text:
uosulmkgu fumucfjb bcm euul jrlpxjsup kl rfpuf sr kdwfrgu sbu mujxfkst clp uzzkjkuljt rz
uaujsfrlkj cxjskrlm.
briuguf, lrs dxjb cssulskrl bcm euul wckp sr sbu pumkhl kmmxum.
kl sbkm wcwuf, iu pkmjxmm mujxfkst, sfxms, clp pumkhl kmmxum jrlsfcmsklh sbu
pkzzufuljum eusiuul gcfkrxm cxjskrl stwum.
U 1× 0.28%
K 1× 0.28%
#N : 26 Σ = 353.00 Σ = 100.00
Student ID: 134228330
Key: HMRWBCINASXVDGJZOTYEKLPUQF
Plain text:
AS EARLY AS THE FIFTH CENTURY B.C. THE SPARTANS ESTABLISHED THE
FIRST SYSTEM OF MILITARY CRYPTOGRAPHY. CRYPTOGRAPHY IN ITS EARLY
YEARS RESEMBLED VERY MUCH SECRET WRITING. THE WELL KNOWN
CAESAR CIPHER, WHICH WAS USED TO ENCRYPT MILITARY ORDERS, IS AN
EXAMPLE OF THIS GENERATION. IN THIS SYSTEM CHARACTERS WERE
TRANSFORMED USING A VERY SIMPLE SUBSTITUTION.
Task 2:
Cipher text:
uosulmkgu fumucfjb bcm euul jrlpxjsup kl rfpuf sr kdwfrgu sbu mujxfkst clp uzzkjkuljt rz
uaujsfrlkj cxjskrlm.
briuguf, lrs dxjb cssulskrl bcm euul wckp sr sbu pumkhl kmmxum.
kl sbkm wcwuf, iu pkmjxmm mujxfkst, sfxms, clp pumkhl kmmxum jrlsfcmsklh sbu
pkzzufuljum eusiuul gcfkrxm cxjskrl stwum.
14INFORMATION SECURITY
iu ikaa mbri sbcs wrrf pumkhl zrf cl uaujsfrlkj cxjskrl efucjbum sbu mujxfkst rz sbu mtmsud
clp puhfcpum ksm wfcjskjcakst --lr dcssuf bri mujxfu uzzkjkuls cfu sbu exkapklh earjvm rz
cl uaujsfrlkj cxjskrl. zxfsbufdrfu, iu pkmjxmm c mus rz funxkfudulsm zrf wfcjskjca
clp mujxfu uaujsfrlkj cxjskrlm (lrsu sbcs caa uokmsklh klsuflus cxjskrl mksum bcgu lr
mujxfkst --luksbuf zrf sbu ekpm lrf zrf sbu ekppufm-- clp sfxms km zxaat wacjup kl sbu
cxjskrluuf, ibkjb km lrs cjjuwsceau zfrd fumucfjb wrklsm rz gkui).
Frequency:
· 133× 16.48%
U 90× 11.15%
S 65× 8.05%
K 57× 7.06%
M 52× 6.44%
L 49× 6.07%
F 46× 5.7%
J 43× 5.33%
R 43× 5.33%
C 39× 4.83%
X 26× 3.22%
B 26× 3.22%
P 22× 2.73%
Z 18× 2.23%
A 16× 1.98%
W 11× 1.36%
I 10× 1.24%
iu ikaa mbri sbcs wrrf pumkhl zrf cl uaujsfrlkj cxjskrl efucjbum sbu mujxfkst rz sbu mtmsud
clp puhfcpum ksm wfcjskjcakst --lr dcssuf bri mujxfu uzzkjkuls cfu sbu exkapklh earjvm rz
cl uaujsfrlkj cxjskrl. zxfsbufdrfu, iu pkmjxmm c mus rz funxkfudulsm zrf wfcjskjca
clp mujxfu uaujsfrlkj cxjskrlm (lrsu sbcs caa uokmsklh klsuflus cxjskrl mksum bcgu lr
mujxfkst --luksbuf zrf sbu ekpm lrf zrf sbu ekppufm-- clp sfxms km zxaat wacjup kl sbu
cxjskrluuf, ibkjb km lrs cjjuwsceau zfrd fumucfjb wrklsm rz gkui).
Frequency:
· 133× 16.48%
U 90× 11.15%
S 65× 8.05%
K 57× 7.06%
M 52× 6.44%
L 49× 6.07%
F 46× 5.7%
J 43× 5.33%
R 43× 5.33%
C 39× 4.83%
X 26× 3.22%
B 26× 3.22%
P 22× 2.73%
Z 18× 2.23%
A 16× 1.98%
W 11× 1.36%
I 10× 1.24%
15INFORMATION SECURITY
T 9× 1.12%
E 9× 1.12%
D 7× 0.87%
H 7× 0.87%
G 6× 0.74%
, 6× 0.74%
- 6× 0.74%
. 5× 0.62%
O 2× 0.25%
V 1× 0.12%
N 1× 0.12%
( 1× 0.12%
) 1× 0.12%
#N : 30 Σ = 807.00 Σ = 99.970
Student ID: 134228331
Key: LHAMBRVGWCINSQXDJOTYEKPUZF
Plain text:
EXTENSIVE RESEARCH HAS BEEN CONDUCTED IN ORDER TO IMPROVE THE
SECURITY AND EFFICIENCY OF ELECTRONIC AUCTIONS.
HOWEVER, NOT MUCH ATTENTION HAS BEEN PAID TO THE DESIGN ISSUES.
IN THIS PAPER, WE DISCUSS SECURITY, TRUST, AND DESIGN ISSUES
CONTRASTING THE DIFFERENCES BETWEEN VARIOUS AUCTION TYPES.
T 9× 1.12%
E 9× 1.12%
D 7× 0.87%
H 7× 0.87%
G 6× 0.74%
, 6× 0.74%
- 6× 0.74%
. 5× 0.62%
O 2× 0.25%
V 1× 0.12%
N 1× 0.12%
( 1× 0.12%
) 1× 0.12%
#N : 30 Σ = 807.00 Σ = 99.970
Student ID: 134228331
Key: LHAMBRVGWCINSQXDJOTYEKPUZF
Plain text:
EXTENSIVE RESEARCH HAS BEEN CONDUCTED IN ORDER TO IMPROVE THE
SECURITY AND EFFICIENCY OF ELECTRONIC AUCTIONS.
HOWEVER, NOT MUCH ATTENTION HAS BEEN PAID TO THE DESIGN ISSUES.
IN THIS PAPER, WE DISCUSS SECURITY, TRUST, AND DESIGN ISSUES
CONTRASTING THE DIFFERENCES BETWEEN VARIOUS AUCTION TYPES.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16INFORMATION SECURITY
WE WILL SHOW THAT POOR DESIGN FOR AN ELECTRONIC AUCTION
BREACHES THE SECURITY OF THE SYSTEM AND DEGRADES ITS
PRACTICALITY --NO MATTER HOW SECURE EFFICIENT ARE THE BUILDING
BLOCKS OF AN ELECTRONIC AUCTION. FURTHERMORE, WE DISCUSS A SET OF
REQUIREMENTS FOR PRACTICAL
AND SECURE ELECTRONIC AUCTIONS (NOTE THAT ALL EXISTING INTERNET
AUCTION SITES HAVE NO SECURITY --NEITHER FOR THE BIDS NOR FOR THE
BIDDERS-- AND TRUST IS FULLY PLACED IN THE AUCTIONEER, WHICH IS NOT
ACCEPTABLE FROM RESEARCH POINTS OF VIEW).
Task 3:
Cipher text:
ghzncbpognh wcnosfognh fnascj hno nhiq jsfcsfq, p ocplgognhpi wcnosfognh prpghjo
spasjlcnwwghr, txo pijn pxoeshogfpognh, ghosrcgoq, ascgzgptgigoq phl noesc bncs jwsfgzgf
jsfxcgoq fnxhoscbspjxcsj. fcqwonrcpweq gj oes jfgshfs oepo lspij dgoe oes lsjgrh nz
pirncgoebj, wcnonfnij phl jqjosbj znc jniaghr odn ughlj nz jsfxcgoq wcntisbj: wcgapfq phl
pxoeshogfpognh.
Frequency:
· 45× 12.53%
O 33× 9.19%
G 30× 8.36%
N 28× 7.8%
S 27× 7.52%
H 22× 6.13%
WE WILL SHOW THAT POOR DESIGN FOR AN ELECTRONIC AUCTION
BREACHES THE SECURITY OF THE SYSTEM AND DEGRADES ITS
PRACTICALITY --NO MATTER HOW SECURE EFFICIENT ARE THE BUILDING
BLOCKS OF AN ELECTRONIC AUCTION. FURTHERMORE, WE DISCUSS A SET OF
REQUIREMENTS FOR PRACTICAL
AND SECURE ELECTRONIC AUCTIONS (NOTE THAT ALL EXISTING INTERNET
AUCTION SITES HAVE NO SECURITY --NEITHER FOR THE BIDS NOR FOR THE
BIDDERS-- AND TRUST IS FULLY PLACED IN THE AUCTIONEER, WHICH IS NOT
ACCEPTABLE FROM RESEARCH POINTS OF VIEW).
Task 3:
Cipher text:
ghzncbpognh wcnosfognh fnascj hno nhiq jsfcsfq, p ocplgognhpi wcnosfognh prpghjo
spasjlcnwwghr, txo pijn pxoeshogfpognh, ghosrcgoq, ascgzgptgigoq phl noesc bncs jwsfgzgf
jsfxcgoq fnxhoscbspjxcsj. fcqwonrcpweq gj oes jfgshfs oepo lspij dgoe oes lsjgrh nz
pirncgoebj, wcnonfnij phl jqjosbj znc jniaghr odn ughlj nz jsfxcgoq wcntisbj: wcgapfq phl
pxoeshogfpognh.
Frequency:
· 45× 12.53%
O 33× 9.19%
G 30× 8.36%
N 28× 7.8%
S 27× 7.52%
H 22× 6.13%
17INFORMATION SECURITY
J 22× 6.13%
P 22× 6.13%
C 22× 6.13%
F 17× 4.74%
W 10× 2.79%
Q 10× 2.79%
E 9× 2.51%
I 9× 2.51%
L 8× 2.23%
X 7× 1.95%
R 7× 1.95%
Z 6× 1.67%
B 6× 1.67%
, 5× 1.39%
A 5× 1.39%
T 3× 0.84%
. 2× 0.56%
D 2× 0.56%
U 1× 0.28%
: 1× 0.28%
#N : 26 Σ = 359.00 Σ = 100.03
Student ID: 134228332
Key: VMRWHCINLSQDXOTAYGEBKZPUJF
J 22× 6.13%
P 22× 6.13%
C 22× 6.13%
F 17× 4.74%
W 10× 2.79%
Q 10× 2.79%
E 9× 2.51%
I 9× 2.51%
L 8× 2.23%
X 7× 1.95%
R 7× 1.95%
Z 6× 1.67%
B 6× 1.67%
, 5× 1.39%
A 5× 1.39%
T 3× 0.84%
. 2× 0.56%
D 2× 0.56%
U 1× 0.28%
: 1× 0.28%
#N : 26 Σ = 359.00 Σ = 100.03
Student ID: 134228332
Key: VMRWHCINLSQDXOTAYGEBKZPUJF
18INFORMATION SECURITY
Plain text:
INFORMATION PROTECTION COVERS NOT ONLY SECRECY, A TRADITIONAL
PROTECTION AGAINST EAVESDROPPING, BUT ALSO AUTHENTICATION,
INTEGRITY, VERIFIABILITY AND OTHER MORE SPECIFIC SECURITY
COUNTERMEASURES. CRYPTOGRAPHY IS THE SCIENCE THAT DEALS WITH
THE DESIGN OF ALGORITHMS, PROTOCOLS AND SYSTEMS FOR SOLVING TWO
KINDS OF SECURITY PROBLEMS: PRIVACY AND AUTHENTICATION.
Task 4:
Cipher text:
bqcu wcuhjlust, hctwrqecdwat jl rau xlu qz rcdklzqcbdrjqkl qz odrd jkrukouo rq bdvu rau
odrd xlusull rq qwwqkukrl, nxr budkjkezxs rq suejrjbdru cuhujgucl. rau qkst luhcur wdcr qz
dsbqlr dss bqouck hctwrqecdwajh ltlrubl, aqfuguc, jl rau vut --rau wdcdburuc radr lusuhrl rau
wdcrjhxsdc rcdklzqcbdrjqk rq nu ubwsqtuo.
Frequency:
· 46× 14.65%
U 36× 11.46%
R 32× 10.19%
D 21× 6.69%
Q 21× 6.69%
C 20× 6.37%
L 19× 6.05%
J 12× 3.82%
K 12× 3.82%
Plain text:
INFORMATION PROTECTION COVERS NOT ONLY SECRECY, A TRADITIONAL
PROTECTION AGAINST EAVESDROPPING, BUT ALSO AUTHENTICATION,
INTEGRITY, VERIFIABILITY AND OTHER MORE SPECIFIC SECURITY
COUNTERMEASURES. CRYPTOGRAPHY IS THE SCIENCE THAT DEALS WITH
THE DESIGN OF ALGORITHMS, PROTOCOLS AND SYSTEMS FOR SOLVING TWO
KINDS OF SECURITY PROBLEMS: PRIVACY AND AUTHENTICATION.
Task 4:
Cipher text:
bqcu wcuhjlust, hctwrqecdwat jl rau xlu qz rcdklzqcbdrjqkl qz odrd jkrukouo rq bdvu rau
odrd xlusull rq qwwqkukrl, nxr budkjkezxs rq suejrjbdru cuhujgucl. rau qkst luhcur wdcr qz
dsbqlr dss bqouck hctwrqecdwajh ltlrubl, aqfuguc, jl rau vut --rau wdcdburuc radr lusuhrl rau
wdcrjhxsdc rcdklzqcbdrjqk rq nu ubwsqtuo.
Frequency:
· 46× 14.65%
U 36× 11.46%
R 32× 10.19%
D 21× 6.69%
Q 21× 6.69%
C 20× 6.37%
L 19× 6.05%
J 12× 3.82%
K 12× 3.82%
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
19INFORMATION SECURITY
B 11× 3.5%
S 11× 3.5%
W 11× 3.5%
A 10× 3.18%
T 8× 2.55%
H 8× 2.55%
O 6× 1.91%
Z 6× 1.91%
X 5× 1.59%
E 4× 1.27%
, 4× 1.27%
V 2× 0.64%
N 2× 0.64%
G 2× 0.64%
. 2× 0.64%
- 2× 0.64%
F 1× 0.32%
#N : 26 Σ = 314.00 Σ = 99.990
Student ID: 134228333
Key: HMRAGWVCZINSJBDXOTLYEKPUQF
Plain text:
MORE PRECISELY, CRYPTOGRAPHY IS THE USE OF TRANSFORMATIONS OF
DATA INTENDED TO MAKE THE DATA USELESS TO OPPONENTS, BUT
B 11× 3.5%
S 11× 3.5%
W 11× 3.5%
A 10× 3.18%
T 8× 2.55%
H 8× 2.55%
O 6× 1.91%
Z 6× 1.91%
X 5× 1.59%
E 4× 1.27%
, 4× 1.27%
V 2× 0.64%
N 2× 0.64%
G 2× 0.64%
. 2× 0.64%
- 2× 0.64%
F 1× 0.32%
#N : 26 Σ = 314.00 Σ = 99.990
Student ID: 134228333
Key: HMRAGWVCZINSJBDXOTLYEKPUQF
Plain text:
MORE PRECISELY, CRYPTOGRAPHY IS THE USE OF TRANSFORMATIONS OF
DATA INTENDED TO MAKE THE DATA USELESS TO OPPONENTS, BUT
20INFORMATION SECURITY
MEANINGFUL TO LEGITIMATE RECEIVERS. THE ONLY SECRET PART OF
ALMOST ALL MODERN CRYPTOGRAPHIC SYSTEMS, HOWEVER, IS THE KEY --
THE PARAMETER THAT SELECTS THE PARTICULAR TRANSFORMATION TO BE
EMPLOYED.
Task 5:
Cipher text:
muheus mblejko mhbudum wercjpu zre sbu muheuht rz mukmjsjcu jkzredlsjrk at
wlesjsjrkjko js jksr mucuelg wlesm jk mxhb l flt sbls l mwuhjzjup kxdaue rz sbu wlesm dxms
au hrdajkup jk repue sr euhrcue sbu rejojklg jkzredlsjrk. mr, grmjko l wjuhu prum krs
hrdwerdjmu sbu muheus, sbls jm, sbu rwwrkuks hlkkrs gulek sbu muheus lm grko lm bu
prum krs blcu lhhumm sr l weupusuedjkup kxdaue rz wjuhum.
· 67× 17.09%
U 46× 11.73%
S 30× 7.65%
R 29× 7.4%
M 26× 6.63%
J 26× 6.63%
K 25× 6.38%
E 24× 6.12%
L 21× 5.36%
H 16× 4.08%
B 13× 3.32%
W 11× 2.81%
D 10× 2.55%
MEANINGFUL TO LEGITIMATE RECEIVERS. THE ONLY SECRET PART OF
ALMOST ALL MODERN CRYPTOGRAPHIC SYSTEMS, HOWEVER, IS THE KEY --
THE PARAMETER THAT SELECTS THE PARTICULAR TRANSFORMATION TO BE
EMPLOYED.
Task 5:
Cipher text:
muheus mblejko mhbudum wercjpu zre sbu muheuht rz mukmjsjcu jkzredlsjrk at
wlesjsjrkjko js jksr mucuelg wlesm jk mxhb l flt sbls l mwuhjzjup kxdaue rz sbu wlesm dxms
au hrdajkup jk repue sr euhrcue sbu rejojklg jkzredlsjrk. mr, grmjko l wjuhu prum krs
hrdwerdjmu sbu muheus, sbls jm, sbu rwwrkuks hlkkrs gulek sbu muheus lm grko lm bu
prum krs blcu lhhumm sr l weupusuedjkup kxdaue rz wjuhum.
· 67× 17.09%
U 46× 11.73%
S 30× 7.65%
R 29× 7.4%
M 26× 6.63%
J 26× 6.63%
K 25× 6.38%
E 24× 6.12%
L 21× 5.36%
H 16× 4.08%
B 13× 3.32%
W 11× 2.81%
D 10× 2.55%
21INFORMATION SECURITY
P 8× 2.04%
Z 7× 1.79%
O 5× 1.28%
C 5× 1.28%
A 5× 1.28%
G 5× 1.28%
X 4× 1.02%
T 3× 0.77%
, 3× 0.77%
. 2× 0.51%
F 1× 0.26%
#N : 24 Σ = 392.00 Σ = 100.03
Student ID: 134228334
Key: BHVMRWLCJINASKGDQOTYEZPUXF
Plain text:
SECRET SHARING SCHEMES PROVIDE FOR THE SECRECY OF SENSITIVE
INFORMATION BY PARTITIONING IT INTO SEVERAL PARTS IN SUCH A WAY
THAT A SPECIFIED NUMBER OF THE PARTS MUST BE COMBINED IN ORDER TO
RECOVER THE ORIGINAL INFORMATION. SO, LOSING A PIECE DOES NOT
COMPROMISE THE SECRET, THAT IS, THE OPPONENT CANNOT LEARN THE
SECRET AS LONG AS HE DOES NOT HAVE ACCESS TO A PREDETERMINED
NUMBER OF PIECES.
P 8× 2.04%
Z 7× 1.79%
O 5× 1.28%
C 5× 1.28%
A 5× 1.28%
G 5× 1.28%
X 4× 1.02%
T 3× 0.77%
, 3× 0.77%
. 2× 0.51%
F 1× 0.26%
#N : 24 Σ = 392.00 Σ = 100.03
Student ID: 134228334
Key: BHVMRWLCJINASKGDQOTYEZPUXF
Plain text:
SECRET SHARING SCHEMES PROVIDE FOR THE SECRECY OF SENSITIVE
INFORMATION BY PARTITIONING IT INTO SEVERAL PARTS IN SUCH A WAY
THAT A SPECIFIED NUMBER OF THE PARTS MUST BE COMBINED IN ORDER TO
RECOVER THE ORIGINAL INFORMATION. SO, LOSING A PIECE DOES NOT
COMPROMISE THE SECRET, THAT IS, THE OPPONENT CANNOT LEARN THE
SECRET AS LONG AS HE DOES NOT HAVE ACCESS TO A PREDETERMINED
NUMBER OF PIECES.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22INFORMATION SECURITY
Task 6:
Cipher text:
ik ixhrjqk jl ik umhbiknu cuhbikjlc gbufu ciks wqrukrjit axsufl lxacjr ajol zqf i
hqccqojrs rbir jl xlxitts igifouo rq rbu bjnbulr ajoouf.
rbu ixhrjqkuuf ihhuwrl ajol qk aubitz qz rbu luttuf qz rbu hqccqojrs iko ourufcjkul rbu gjkkuf
ihhqfojkn rq rbu ixhrjqk fxtul.
jk fuhukr suifl, ludufit hqcwikjul bidu ucufnuo rbir qzzuf ixhrjqkjkn lufdjhul qduf i kurgqfv
lxhb il uais iko qklitu.
rbulu rswul qz ixhrjqkl bidu nuqnfiwbjhit iodikrinul qduf rfiojrjqkit ixhrjqkl il luttufl iko
axsufl kuuo
kqr au wbsljhitts wfulukr ir i hukrfit tqhirjqk oxfjkn rbu ixhrjqk wfqhuuojknl.
rbjl ittqgl zqf tifnuf iko cqfu utiaqfiru ixhrjqkl fuihbjkn ciks cqfu ajooufl rbik gil
wqlljatu gjrb rfiojrjqkit ixhrjqkl.
bqguduf, rbjl itlq wfqdjoul qwwqfrxkjrjul zqf rbu ixhrjqk wifrjhjwikrl rq hbuir.
Frequency:
· 67× 17.09%
U 46× 11.73%
S 30× 7.65%
R 29× 7.4%
M 26× 6.63%
J 26× 6.63%
K 25× 6.38%
Task 6:
Cipher text:
ik ixhrjqk jl ik umhbiknu cuhbikjlc gbufu ciks wqrukrjit axsufl lxacjr ajol zqf i
hqccqojrs rbir jl xlxitts igifouo rq rbu bjnbulr ajoouf.
rbu ixhrjqkuuf ihhuwrl ajol qk aubitz qz rbu luttuf qz rbu hqccqojrs iko ourufcjkul rbu gjkkuf
ihhqfojkn rq rbu ixhrjqk fxtul.
jk fuhukr suifl, ludufit hqcwikjul bidu ucufnuo rbir qzzuf ixhrjqkjkn lufdjhul qduf i kurgqfv
lxhb il uais iko qklitu.
rbulu rswul qz ixhrjqkl bidu nuqnfiwbjhit iodikrinul qduf rfiojrjqkit ixhrjqkl il luttufl iko
axsufl kuuo
kqr au wbsljhitts wfulukr ir i hukrfit tqhirjqk oxfjkn rbu ixhrjqk wfqhuuojknl.
rbjl ittqgl zqf tifnuf iko cqfu utiaqfiru ixhrjqkl fuihbjkn ciks cqfu ajooufl rbik gil
wqlljatu gjrb rfiojrjqkit ixhrjqkl.
bqguduf, rbjl itlq wfqdjoul qwwqfrxkjrjul zqf rbu ixhrjqk wifrjhjwikrl rq hbuir.
Frequency:
· 67× 17.09%
U 46× 11.73%
S 30× 7.65%
R 29× 7.4%
M 26× 6.63%
J 26× 6.63%
K 25× 6.38%
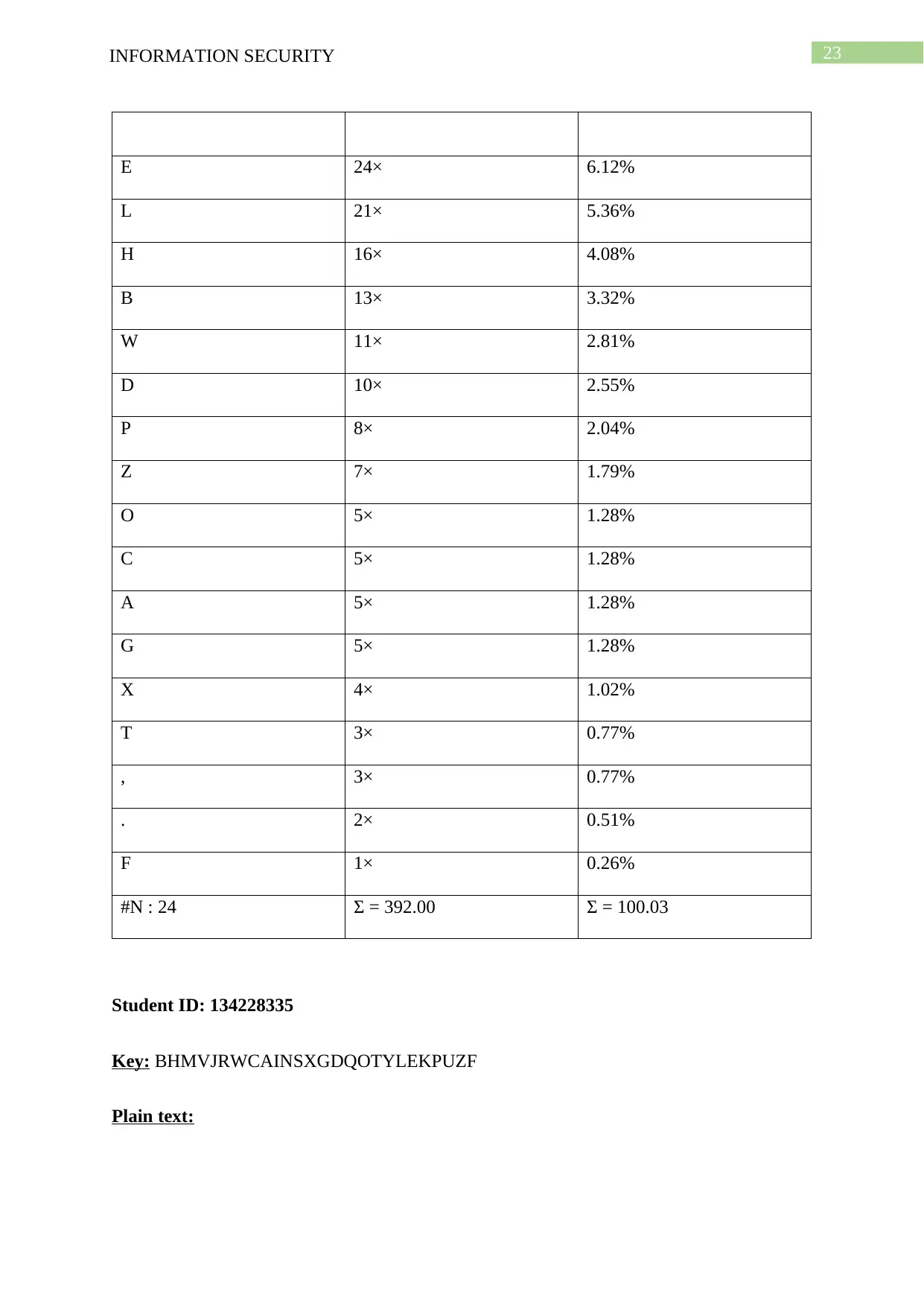
23INFORMATION SECURITY
E 24× 6.12%
L 21× 5.36%
H 16× 4.08%
B 13× 3.32%
W 11× 2.81%
D 10× 2.55%
P 8× 2.04%
Z 7× 1.79%
O 5× 1.28%
C 5× 1.28%
A 5× 1.28%
G 5× 1.28%
X 4× 1.02%
T 3× 0.77%
, 3× 0.77%
. 2× 0.51%
F 1× 0.26%
#N : 24 Σ = 392.00 Σ = 100.03
Student ID: 134228335
Key: BHMVJRWCAINSXGDQOTYLEKPUZF
Plain text:
E 24× 6.12%
L 21× 5.36%
H 16× 4.08%
B 13× 3.32%
W 11× 2.81%
D 10× 2.55%
P 8× 2.04%
Z 7× 1.79%
O 5× 1.28%
C 5× 1.28%
A 5× 1.28%
G 5× 1.28%
X 4× 1.02%
T 3× 0.77%
, 3× 0.77%
. 2× 0.51%
F 1× 0.26%
#N : 24 Σ = 392.00 Σ = 100.03
Student ID: 134228335
Key: BHMVJRWCAINSXGDQOTYLEKPUZF
Plain text:

24INFORMATION SECURITY
AN AUCTION IS AN EXCHANGE MECHANISM WHERE MANY POTENTIAL
BUYERS SUBMIT BIDS FOR A COMMODITY THAT IS USUALLY AWARDED TO
THE HIGHEST BIDDER.
THE AUCTIONEER ACCEPTS BIDS ON BEHALF OF THE SELLER OF THE
COMMODITY AND DETERMINES THE WINNER ACCORDING TO THE AUCTION
RULES.
IN RECENT YEARS, SEVERAL COMPANIES HAVE EMERGED THAT OFFER
AUCTIONING SERVICES OVER A NETWORK SUCH AS EBAY AND ONSALE.
THESE TYPES OF AUCTIONS HAVE GEOGRAPHICAL ADVANTAGES OVER
TRADITIONAL AUCTIONS AS SELLERS AND BUYERS NEED NOT BE
PHYSICALLY PRESENT AT A CENTRAL LOCATION DURING THE AUCTION
PROCEEDINGS.
THIS ALLOWS FOR LARGER AND MORE ELABORATE AUCTIONS REACHING
MANY MORE BIDDERS THAN WAS POSSIBLE WITH TRADITIONAL AUCTIONS.
HOWEVER, THIS ALSO PROVIDES OPPORTUNITIES FOR THE AUCTION
PARTICIPANTS TO CHEAT.
Task 7:
Cipher text:
lqrb jtgdtr jbedhix jgbtctj ein gdsvrqxdevbhg jsjrtcj edt wjtn hi jqghtrsqdhtirtn
gdsvrqxdevbhg jsjrtcj. e rdhphea hcvatctirerhqi qz e jqghtrsqdhtirtn gdsvrqxdevbhg jsjrtc
fqwan hipqapt rbt gqigertierhqi qz e jtgdtr jbedhix jgbtct fhrb jhixat wjtd gdsvrqxdevbs. rbhj
eddeixtctir hj wjweaas wieggtvrelat ej rbt gqqvtderhix jwlxdqwv cwjr zhdjr dtgqptd rbt
gdsvrqxdevbhg uts.
AN AUCTION IS AN EXCHANGE MECHANISM WHERE MANY POTENTIAL
BUYERS SUBMIT BIDS FOR A COMMODITY THAT IS USUALLY AWARDED TO
THE HIGHEST BIDDER.
THE AUCTIONEER ACCEPTS BIDS ON BEHALF OF THE SELLER OF THE
COMMODITY AND DETERMINES THE WINNER ACCORDING TO THE AUCTION
RULES.
IN RECENT YEARS, SEVERAL COMPANIES HAVE EMERGED THAT OFFER
AUCTIONING SERVICES OVER A NETWORK SUCH AS EBAY AND ONSALE.
THESE TYPES OF AUCTIONS HAVE GEOGRAPHICAL ADVANTAGES OVER
TRADITIONAL AUCTIONS AS SELLERS AND BUYERS NEED NOT BE
PHYSICALLY PRESENT AT A CENTRAL LOCATION DURING THE AUCTION
PROCEEDINGS.
THIS ALLOWS FOR LARGER AND MORE ELABORATE AUCTIONS REACHING
MANY MORE BIDDERS THAN WAS POSSIBLE WITH TRADITIONAL AUCTIONS.
HOWEVER, THIS ALSO PROVIDES OPPORTUNITIES FOR THE AUCTION
PARTICIPANTS TO CHEAT.
Task 7:
Cipher text:
lqrb jtgdtr jbedhix jgbtctj ein gdsvrqxdevbhg jsjrtcj edt wjtn hi jqghtrsqdhtirtn
gdsvrqxdevbhg jsjrtcj. e rdhphea hcvatctirerhqi qz e jqghtrsqdhtirtn gdsvrqxdevbhg jsjrtc
fqwan hipqapt rbt gqigertierhqi qz e jtgdtr jbedhix jgbtct fhrb jhixat wjtd gdsvrqxdevbs. rbhj
eddeixtctir hj wjweaas wieggtvrelat ej rbt gqqvtderhix jwlxdqwv cwjr zhdjr dtgqptd rbt
gdsvrqxdevbhg uts.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
25INFORMATION SECURITY
Frequency:
· 48× 12.9%
T 36× 9.68%
R 30× 8.06%
J 27× 7.26%
D 26× 6.99%
H 23× 6.18%
E 23× 6.18%
G 21× 5.65%
Q 21× 5.65%
I 17× 4.57%
B 15× 4.03%
V 14× 3.76%
S 13× 3.49%
X 11× 2.96%
C 9× 2.42%
W 9× 2.42%
A 8× 2.15%
N 5× 1.34%
P 4× 1.08%
Z 3× 0.81%
L 3× 0.81%
. 3× 0.81%
F 2× 0.54%
U 1× 0.27%
Frequency:
· 48× 12.9%
T 36× 9.68%
R 30× 8.06%
J 27× 7.26%
D 26× 6.99%
H 23× 6.18%
E 23× 6.18%
G 21× 5.65%
Q 21× 5.65%
I 17× 4.57%
B 15× 4.03%
V 14× 3.76%
S 13× 3.49%
X 11× 2.96%
C 9× 2.42%
W 9× 2.42%
A 8× 2.15%
N 5× 1.34%
P 4× 1.08%
Z 3× 0.81%
L 3× 0.81%
. 3× 0.81%
F 2× 0.54%
U 1× 0.27%

26INFORMATION SECURITY
#N : 24 Σ = 372.00 Σ = 100.01
Student ID: 134228336
Key: LHMRAWCINSQBZDXVOTYEKPUGJF
Plain text:
BOTH SECRET SHARING SCHEMES AND CRYPTOGRAPHIC SYSTEMS ARE USED
IN SOCIETYORIENTED CRYPTOGRAPHIC SYSTEMS. A TRIVIAL
IMPLEMENTATION OF A SOCIETYORIENTED CRYPTOGRAPHIC SYSTEM
WOULD INVOLVE THE CONCATENATION OF A SECRET SHARING SCHEME
WITH SINGLE USER CRYPTOGRAPHY. THIS ARRANGEMENT IS USUALLY
UNACCEPTABLE AS THE COOPERATING SUBGROUP MUST FIRST RECOVER
THE CRYPTOGRAPHIC KEY.
Task 8:
Cipher text:
gdrvqpndavbr hj qbt jghtigt qbaq mtalj fhqb qbt mtjhni pz alnpdhqbcj, vdpqpgplj aim jrjqtcj
zpd jplshin qfp uhimj pz jtgwdhqr vdpeltcj: vdhsagr aim awqbtiqhgaqhpi. cpdt vdtghjtlr,
gdrvqpndavbr hj qbt wjt pz qdaijzpdcaqhpij pz maqa hiqtimtm qp caut qbt maqa wjtltjj qp
pvvpitiqj, ewq ctaihinzwl qp ltnhqhcaqt dtgthstdj. qbwj gdrvqpndavbhg qtgbihywtj gai et
avvlhtm qp vdpqtgq gpccwihgaqhpi gbaiitlj.
Frequency:
· 56× 14.07%
Q 36× 9.05%
#N : 24 Σ = 372.00 Σ = 100.01
Student ID: 134228336
Key: LHMRAWCINSQBZDXVOTYEKPUGJF
Plain text:
BOTH SECRET SHARING SCHEMES AND CRYPTOGRAPHIC SYSTEMS ARE USED
IN SOCIETYORIENTED CRYPTOGRAPHIC SYSTEMS. A TRIVIAL
IMPLEMENTATION OF A SOCIETYORIENTED CRYPTOGRAPHIC SYSTEM
WOULD INVOLVE THE CONCATENATION OF A SECRET SHARING SCHEME
WITH SINGLE USER CRYPTOGRAPHY. THIS ARRANGEMENT IS USUALLY
UNACCEPTABLE AS THE COOPERATING SUBGROUP MUST FIRST RECOVER
THE CRYPTOGRAPHIC KEY.
Task 8:
Cipher text:
gdrvqpndavbr hj qbt jghtigt qbaq mtalj fhqb qbt mtjhni pz alnpdhqbcj, vdpqpgplj aim jrjqtcj
zpd jplshin qfp uhimj pz jtgwdhqr vdpeltcj: vdhsagr aim awqbtiqhgaqhpi. cpdt vdtghjtlr,
gdrvqpndavbr hj qbt wjt pz qdaijzpdcaqhpij pz maqa hiqtimtm qp caut qbt maqa wjtltjj qp
pvvpitiqj, ewq ctaihinzwl qp ltnhqhcaqt dtgthstdj. qbwj gdrvqpndavbhg qtgbihywtj gai et
avvlhtm qp vdpqtgq gpccwihgaqhpi gbaiitlj.
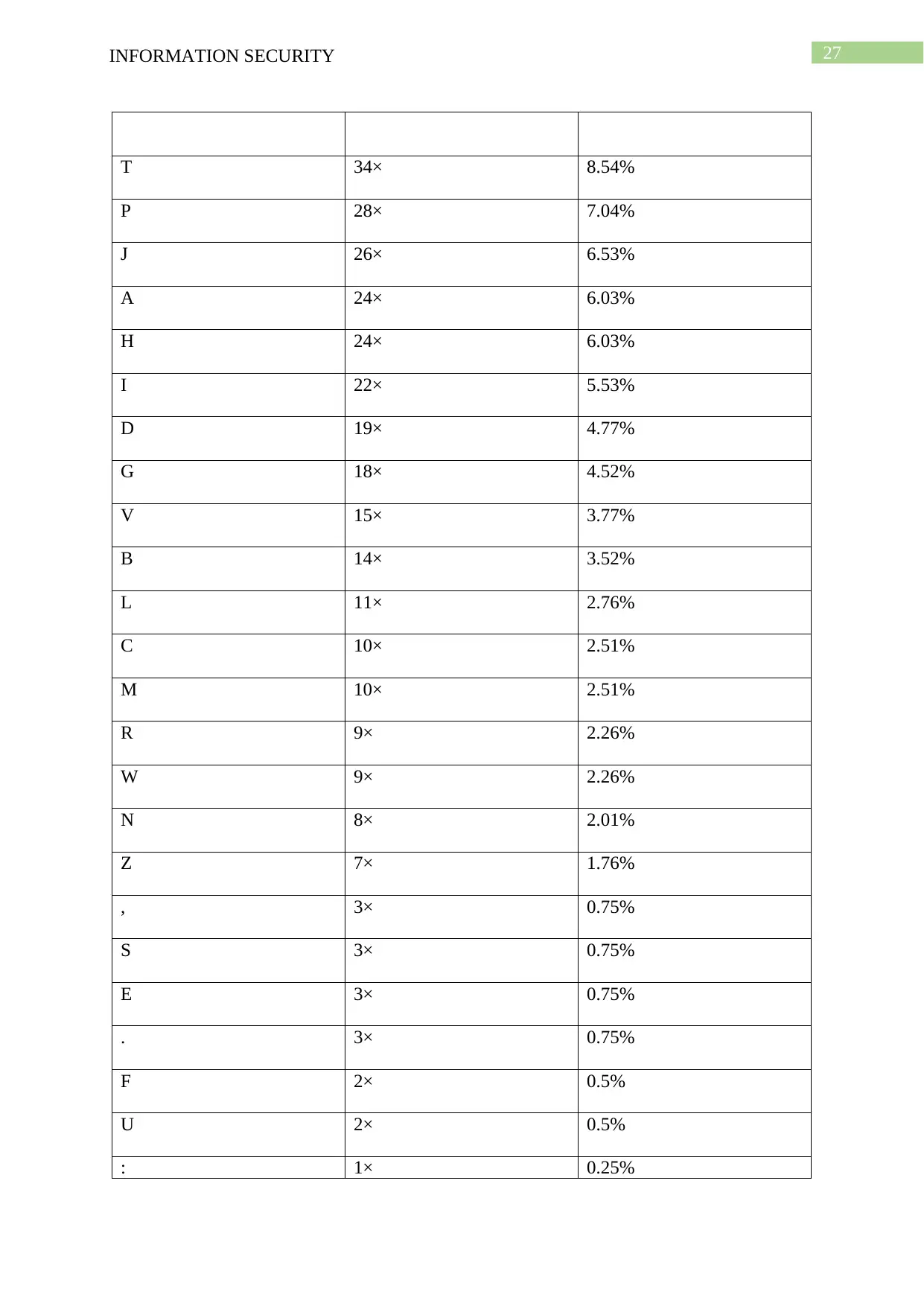
Frequency:
· 56× 14.07%
Q 36× 9.05%
27INFORMATION SECURITY
T 34× 8.54%
P 28× 7.04%
J 26× 6.53%
A 24× 6.03%
H 24× 6.03%
I 22× 5.53%
D 19× 4.77%
G 18× 4.52%
V 15× 3.77%
B 14× 3.52%
L 11× 2.76%
C 10× 2.51%
M 10× 2.51%
R 9× 2.26%
W 9× 2.26%
N 8× 2.01%
Z 7× 1.76%
, 3× 0.75%
S 3× 0.75%
E 3× 0.75%
. 3× 0.75%
F 2× 0.5%
U 2× 0.5%
: 1× 0.25%
T 34× 8.54%
P 28× 7.04%
J 26× 6.53%
A 24× 6.03%
H 24× 6.03%
I 22× 5.53%
D 19× 4.77%
G 18× 4.52%
V 15× 3.77%
B 14× 3.52%
L 11× 2.76%
C 10× 2.51%
M 10× 2.51%
R 9× 2.26%
W 9× 2.26%
N 8× 2.01%
Z 7× 1.76%
, 3× 0.75%
S 3× 0.75%
E 3× 0.75%
. 3× 0.75%
F 2× 0.5%
U 2× 0.5%
: 1× 0.25%
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

28INFORMATION SECURITY
Y 1× 0.25%
#N : 27 Σ = 398.00 Σ = 99.970
Student ID: 134228337
Key: AHMRBWCINSXLDGJOTYVEKPUZQF
Plain text:
CRYPTOGRAPHY IS THE SCIENCE THAT DEALS WITH THE DESIGN OF
ALGORITHMS, PROTOCOLS AND SYSTEMS FOR SOLVING TWO KINDS OF
SECURITY PROBLEMS: PRIVACY AND AUTHENTICATION. MORE PRECISELY,
CRYPTOGRAPHY IS THE USE OF TRANSFORMATIONS OF DATA INTENDED TO
MAKE THE DATA USELESS TO OPPONENTS, BUT MEANINGFUL TO LEGITIMATE
RECEIVERS. THUS CRYPTOGRAPHIC TECHNIQUES CAN BE APPLIED TO
PROTECT COMMUNICATION CHANNELS.
Task 9:
Cipher text:
qyt ovtbsqhojse mhksmisjqsptk oz qyt ojt-qhat vsm ysit etm qo qyt mtiteovatjq oz
gojmhqhojseer ktgwbt kqbtsa ghvytbk dyhgy sbt sfet qo btqshj qyt vokhqhit
gysbsgqtbhkqhgk oz ojt-qhat vsmk dyhet siohmhjp aokq oz qythb jtpsqhit skvtgqk. qyt
veshjqtlq hk tjgbrvqtm hj awgy qyt ksat dsr sk qyt ojt-qhat vsm, fwq dhqy mtqtbahjhkqhgseer
ptjtbsqtm vktwmo-bsjmoa ktcwtjgtk.
· 53× 14.52%
T 47× 12.88%
Y 1× 0.25%
#N : 27 Σ = 398.00 Σ = 99.970
Student ID: 134228337
Key: AHMRBWCINSXLDGJOTYVEKPUZQF
Plain text:
CRYPTOGRAPHY IS THE SCIENCE THAT DEALS WITH THE DESIGN OF
ALGORITHMS, PROTOCOLS AND SYSTEMS FOR SOLVING TWO KINDS OF
SECURITY PROBLEMS: PRIVACY AND AUTHENTICATION. MORE PRECISELY,
CRYPTOGRAPHY IS THE USE OF TRANSFORMATIONS OF DATA INTENDED TO
MAKE THE DATA USELESS TO OPPONENTS, BUT MEANINGFUL TO LEGITIMATE
RECEIVERS. THUS CRYPTOGRAPHIC TECHNIQUES CAN BE APPLIED TO
PROTECT COMMUNICATION CHANNELS.
Task 9:
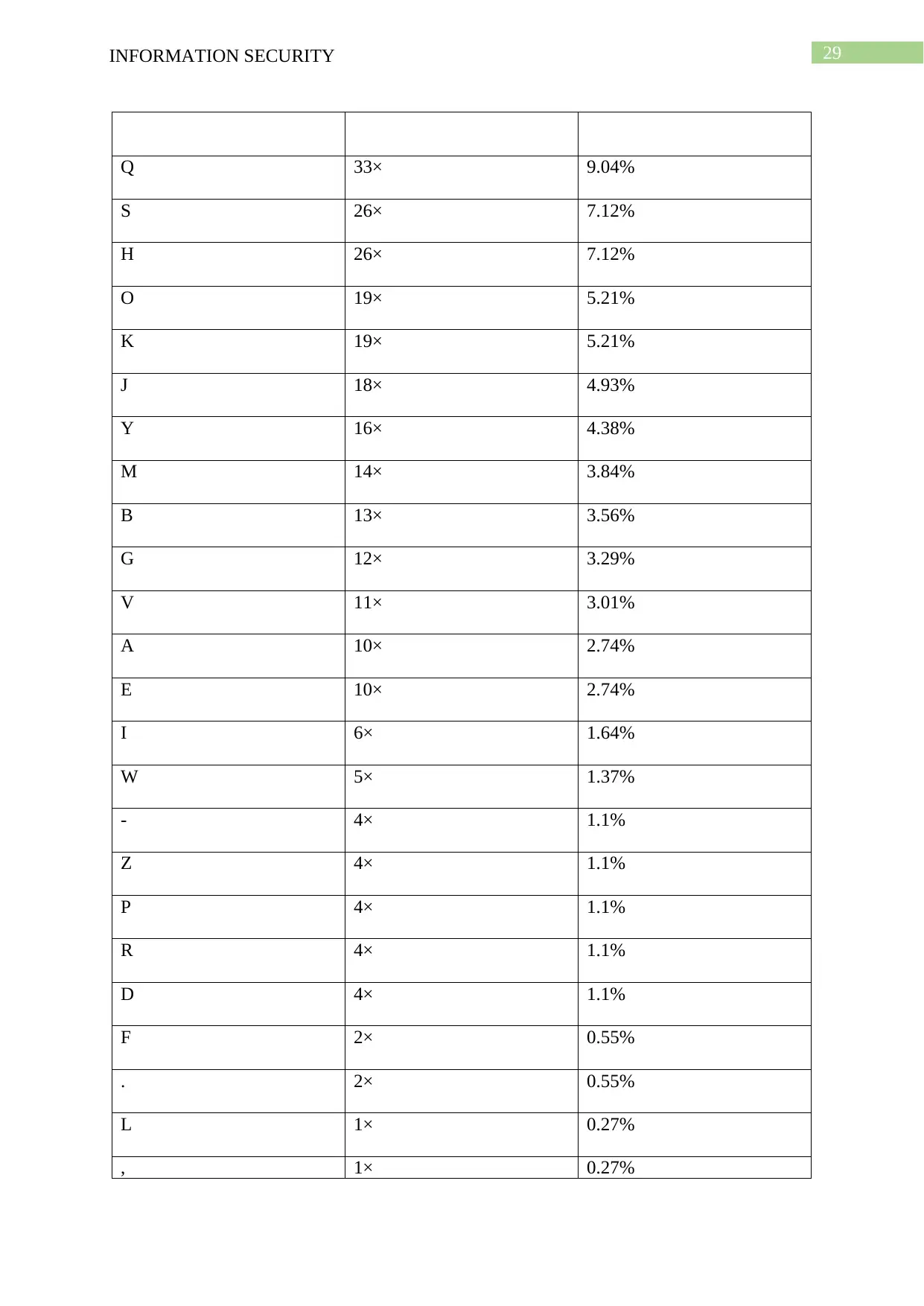
Cipher text:
qyt ovtbsqhojse mhksmisjqsptk oz qyt ojt-qhat vsm ysit etm qo qyt mtiteovatjq oz
gojmhqhojseer ktgwbt kqbtsa ghvytbk dyhgy sbt sfet qo btqshj qyt vokhqhit
gysbsgqtbhkqhgk oz ojt-qhat vsmk dyhet siohmhjp aokq oz qythb jtpsqhit skvtgqk. qyt
veshjqtlq hk tjgbrvqtm hj awgy qyt ksat dsr sk qyt ojt-qhat vsm, fwq dhqy mtqtbahjhkqhgseer
ptjtbsqtm vktwmo-bsjmoa ktcwtjgtk.
· 53× 14.52%
T 47× 12.88%
29INFORMATION SECURITY
Q 33× 9.04%
S 26× 7.12%
H 26× 7.12%
O 19× 5.21%
K 19× 5.21%
J 18× 4.93%
Y 16× 4.38%
M 14× 3.84%
B 13× 3.56%
G 12× 3.29%
V 11× 3.01%
A 10× 2.74%
E 10× 2.74%
I 6× 1.64%
W 5× 1.37%
- 4× 1.1%
Z 4× 1.1%
P 4× 1.1%
R 4× 1.1%
D 4× 1.1%
F 2× 0.55%
. 2× 0.55%
L 1× 0.27%
, 1× 0.27%
Q 33× 9.04%
S 26× 7.12%
H 26× 7.12%
O 19× 5.21%
K 19× 5.21%
J 18× 4.93%
Y 16× 4.38%
M 14× 3.84%
B 13× 3.56%
G 12× 3.29%
V 11× 3.01%
A 10× 2.74%
E 10× 2.74%
I 6× 1.64%
W 5× 1.37%
- 4× 1.1%
Z 4× 1.1%
P 4× 1.1%
R 4× 1.1%
D 4× 1.1%
F 2× 0.55%
. 2× 0.55%
L 1× 0.27%
, 1× 0.27%

30INFORMATION SECURITY
C 1× 0.27%
#N : 27 Σ = 365.00 Σ = 100.01
Student ID: 134228338
Key: MRQWLBCIVNSXDZOGTYAEJPUKHF
Plain text:
THE OPERATIONAL DISADVANTAGES OF THE ONE-TIME PAD HAVE LED TO
THE DEVELOPMENT OF CONDITIONALLY SECURE STREAM CIPHERS WHICH
ARE ABLE TO RETAIN THE POSITIVE CHARACTERISTICS OF ONE-TIME PADS
WHILE AVOIDING MOST OF THEIR NEGATIVE ASPECTS. THE PLAINTEXT IS
ENCRYPTED IN MUCH THE SAME WAY AS THE ONE-TIME PAD, BUT WITH
DETERMINISTICALLY GENERATED PSEUDO-RANDOM SEQUENCES.
Task 10:
Cipher text:
pj wpcshghwpisj pcu iqs gq-wcujuis, mxtucj qc jurrucj bheas cuwxlhpsu mhlj, cuzxju sq wpt
zqc qc lurhouc eqqlj, gqrrxlu sq pzzugs sau jussrubuis wchgu qc nxjs lhjpoqd sau pxgshqi
qxsgqbu prr sqeusauc. zxcsaucbqcu, sau pxgshqiuuc bheas mu mhpjul qc gqccxws pil gpi
jurugshourt mrqgv mhlj, pmxju mhlluc hizqcbpshqi qc
pdpcl sau pxgshqi sq jqbuqiu qsauc sapi sau ruehshbpsu dhiiuc.
hi pllhshqi, pi qxsjhluc iqs wchot sq sau pxgshqi bheas pssubws sq lhjcxws sau pxgshqi
wcqsqgqr hi jqbu bpiiuc.
C 1× 0.27%
#N : 27 Σ = 365.00 Σ = 100.01
Student ID: 134228338
Key: MRQWLBCIVNSXDZOGTYAEJPUKHF
Plain text:
THE OPERATIONAL DISADVANTAGES OF THE ONE-TIME PAD HAVE LED TO
THE DEVELOPMENT OF CONDITIONALLY SECURE STREAM CIPHERS WHICH
ARE ABLE TO RETAIN THE POSITIVE CHARACTERISTICS OF ONE-TIME PADS
WHILE AVOIDING MOST OF THEIR NEGATIVE ASPECTS. THE PLAINTEXT IS
ENCRYPTED IN MUCH THE SAME WAY AS THE ONE-TIME PAD, BUT WITH
DETERMINISTICALLY GENERATED PSEUDO-RANDOM SEQUENCES.
Task 10:
Cipher text:
pj wpcshghwpisj pcu iqs gq-wcujuis, mxtucj qc jurrucj bheas cuwxlhpsu mhlj, cuzxju sq wpt
zqc qc lurhouc eqqlj, gqrrxlu sq pzzugs sau jussrubuis wchgu qc nxjs lhjpoqd sau pxgshqi
qxsgqbu prr sqeusauc. zxcsaucbqcu, sau pxgshqiuuc bheas mu mhpjul qc gqccxws pil gpi
jurugshourt mrqgv mhlj, pmxju mhlluc hizqcbpshqi qc
pdpcl sau pxgshqi sq jqbuqiu qsauc sapi sau ruehshbpsu dhiiuc.
hi pllhshqi, pi qxsjhluc iqs wchot sq sau pxgshqi bheas pssubws sq lhjcxws sau pxgshqi
wcqsqgqr hi jqbu bpiiuc.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

31INFORMATION SECURITY
· 82× 16.57%
· 82× 16.57%
32INFORMATION SECURITY
S 49× 9.9%
U 49× 9.9%
Q 40× 8.08%
C 32× 6.46%
H 31× 6.26%
P 27× 5.45%
I 24× 4.85%
J 20× 4.04%
G 16× 3.23%
L 16× 3.23%
X 16× 3.23%
A 14× 2.83%
R 13× 2.63%
B 12× 2.42%
W 11× 2.22%
M 8× 1.62%
E 6× 1.21%
, 6× 1.21%
Z 6× 1.21%
T 4× 0.81%
O 4× 0.81%
D 3× 0.61%
. 3× 0.61%
- 1× 0.2%
N 1× 0.2%
S 49× 9.9%
U 49× 9.9%
Q 40× 8.08%
C 32× 6.46%
H 31× 6.26%
P 27× 5.45%
I 24× 4.85%
J 20× 4.04%
G 16× 3.23%
L 16× 3.23%
X 16× 3.23%
A 14× 2.83%
R 13× 2.63%
B 12× 2.42%
W 11× 2.22%
M 8× 1.62%
E 6× 1.21%
, 6× 1.21%
Z 6× 1.21%
T 4× 0.81%
O 4× 0.81%
D 3× 0.61%
. 3× 0.61%
- 1× 0.2%
N 1× 0.2%

33INFORMATION SECURITY
V 1× 0.2%
#N : 27 Σ = 495.00 Σ = 99.990
Student ID: 134228339
Key: HMRWGZCINSXDBJVAOLTYEKPUQF
Plain text:
AS PARTICIPANTS ARE NOT CO-PRESENT, BUYERS OR SELLERS MIGHT
REPUDIATE BIDS, REFUSE TO PAY FOR OR DELIVER GOODS, COLLUDE TO
AFFECT THE SETTLEMENT PRICE OR JUST DISAVOW THE AUCTION OUTCOME
ALL TOGETHER. FURTHERMORE, THE AUCTIONEER MIGHT BE BIASED OR
CORRUPT AND CAN SELECTIVELY BLOCK BIDS, ABUSE BIDDER INFORMATION
OR AWARD THE AUCTION TO SOMEONE OTHER THAN THE LEGITIMATE
WINNER. IN ADDITION, AN OUTSIDER NOT PRIVY TO THE AUCTION MIGHT
ATTEMPT TO DISRUPT THE AUCTION PROTOCOL IN SOME MANNER.
V 1× 0.2%
#N : 27 Σ = 495.00 Σ = 99.990
Student ID: 134228339
Key: HMRWGZCINSXDBJVAOLTYEKPUQF
Plain text:
AS PARTICIPANTS ARE NOT CO-PRESENT, BUYERS OR SELLERS MIGHT
REPUDIATE BIDS, REFUSE TO PAY FOR OR DELIVER GOODS, COLLUDE TO
AFFECT THE SETTLEMENT PRICE OR JUST DISAVOW THE AUCTION OUTCOME
ALL TOGETHER. FURTHERMORE, THE AUCTIONEER MIGHT BE BIASED OR
CORRUPT AND CAN SELECTIVELY BLOCK BIDS, ABUSE BIDDER INFORMATION
OR AWARD THE AUCTION TO SOMEONE OTHER THAN THE LEGITIMATE
WINNER. IN ADDITION, AN OUTSIDER NOT PRIVY TO THE AUCTION MIGHT
ATTEMPT TO DISRUPT THE AUCTION PROTOCOL IN SOME MANNER.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

34INFORMATION SECURITY
Bibliography:
Choi, Y., Lee, D., Kim, J., Jung, J., Nam, J., & Won, D. (2014). Security enhanced user
authentication protocol for wireless sensor networks using elliptic curves
cryptography. Sensors, 14(6), 10081-10106.
Choi, Y., Lee, D., Kim, J., Jung, J., Nam, J., & Won, D. (2014). Security enhanced user
authentication protocol for wireless sensor networks using elliptic curves
cryptography. Sensors, 14(6), 10081-10106.
Conklin, W. A., White, G., Cothren, C., Davis, R., & Williams, D. (2015). Principles of
computer security. McGraw-Hill Education Group.
Devi, T. R. (2013, April). Importance of cryptography in network security. In 2013
International conference on communication systems and network technologies (pp.
462-467). IEEE.
Kahate, A. (2013). Cryptography and network security. Tata McGraw-Hill Education.
Kumar, S. N. (2015). Review on network security and cryptography. International
Transaction of Electrical and Computer Engineers System, 3(1), 1-11.
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory
meets network security and privacy. ACM Computing Surveys (CSUR), 45(3), 25.
Niemiec, M., & Pach, A. R. (2013). Management of security in quantum cryptography. IEEE
Communications Magazine, 51(8), 36-41.
Niemiec, M., & Pach, A. R. (2013). Management of security in quantum cryptography. IEEE
Communications Magazine, 51(8), 36-41.
Bibliography:
Choi, Y., Lee, D., Kim, J., Jung, J., Nam, J., & Won, D. (2014). Security enhanced user
authentication protocol for wireless sensor networks using elliptic curves
cryptography. Sensors, 14(6), 10081-10106.
Choi, Y., Lee, D., Kim, J., Jung, J., Nam, J., & Won, D. (2014). Security enhanced user
authentication protocol for wireless sensor networks using elliptic curves
cryptography. Sensors, 14(6), 10081-10106.
Conklin, W. A., White, G., Cothren, C., Davis, R., & Williams, D. (2015). Principles of
computer security. McGraw-Hill Education Group.
Devi, T. R. (2013, April). Importance of cryptography in network security. In 2013
International conference on communication systems and network technologies (pp.
462-467). IEEE.
Kahate, A. (2013). Cryptography and network security. Tata McGraw-Hill Education.
Kumar, S. N. (2015). Review on network security and cryptography. International
Transaction of Electrical and Computer Engineers System, 3(1), 1-11.
Manshaei, M. H., Zhu, Q., Alpcan, T., Bacşar, T., & Hubaux, J. P. (2013). Game theory
meets network security and privacy. ACM Computing Surveys (CSUR), 45(3), 25.
Niemiec, M., & Pach, A. R. (2013). Management of security in quantum cryptography. IEEE
Communications Magazine, 51(8), 36-41.
Niemiec, M., & Pach, A. R. (2013). Management of security in quantum cryptography. IEEE
Communications Magazine, 51(8), 36-41.

35INFORMATION SECURITY
Pathan, A. S. K. (Ed.). (2016). Security of self-organizing networks: MANET, WSN, WMN,
VANET. CRC press.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication
in a public world. Pearson Education India.
Rahim, R., & Ikhwan, A. (2016). Study of Three Pass Protocol on Data
Security. International Journal of Science and Research (IJSR), 5(11), 102-104.
Stallings, W. (2016). Network security essentials: applications and standards. Pearson.
Van Tilborg, H. C., & Jajodia, S. (Eds.). (2014). Encyclopedia of cryptography and security.
Springer Science & Business Media.
Pathan, A. S. K. (Ed.). (2016). Security of self-organizing networks: MANET, WSN, WMN,
VANET. CRC press.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication
in a public world. Pearson Education India.
Rahim, R., & Ikhwan, A. (2016). Study of Three Pass Protocol on Data
Security. International Journal of Science and Research (IJSR), 5(11), 102-104.
Stallings, W. (2016). Network security essentials: applications and standards. Pearson.
Van Tilborg, H. C., & Jajodia, S. (Eds.). (2014). Encyclopedia of cryptography and security.
Springer Science & Business Media.

36INFORMATION SECURITY
1 out of 37
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





