CO4512 Risk Assessment: Information Security Management for CONVXYZ
VerifiedAdded on 2023/01/18
|11
|3202
|65
Report
AI Summary
This report presents a comprehensive risk assessment for CONVXYZ, a real estate and conveyancing service, focusing on its information security management. The assessment utilizes the ISO 31000:2018 standard to identify and mitigate risks within CONVXYZ's network. The report details owner specifications, analyzes primary and secondary assets, and discusses associated threats and vulnerabilities, including brute force attacks, DDoS attacks, data leakage, and malware. A likelihood level computation is performed using the Boston grid framework, and an impact table is provided. The report concludes with the identification of various network security risks and their levels, offering insights into potential mitigation strategies and security enhancements for CONVXYZ. This report aims to provide an overview of the information security risks faced by CONVXYZ and the methods used to assess and manage those risks.

Running head: INFORMATION SECURITY MANAGEMENT
Information Security Management
(CONVXYZ)
Name of the student:
Name of the university:
Author Note
Information Security Management
(CONVXYZ)
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY MANAGEMENT 1
Executive summary
The CONVXYZ provides various real estate services and conveyancing operations from their lawyers. Here,
the ISO 31000:2018 standard is chosen as the risk mitigation technique for the network of CONVXYZ. The
report demonstrates various owner specifications along with the analysis of secondary and primary assets.
Then the vulnerabilities and threats are discussed. After that, the likelihood of particular computation is
demonstrated in the study with the help of Boston grid framework. At last, various risks of CONVXYZ’s
network security risks are identified.
Executive summary
The CONVXYZ provides various real estate services and conveyancing operations from their lawyers. Here,
the ISO 31000:2018 standard is chosen as the risk mitigation technique for the network of CONVXYZ. The
report demonstrates various owner specifications along with the analysis of secondary and primary assets.
Then the vulnerabilities and threats are discussed. After that, the likelihood of particular computation is
demonstrated in the study with the help of Boston grid framework. At last, various risks of CONVXYZ’s
network security risks are identified.

INFORMATION SECURITY MANAGEMENT 2
Table of Contents
1. Introduction:..................................................................................................................................................3
2. Understanding the owner specification:........................................................................................................3
3. Understanding the assets:.............................................................................................................................3
4. Discussion on threats:....................................................................................................................................4
5. Understanding the Likelihood level computation:.........................................................................................7
6. Impact table specification:.............................................................................................................................7
7. Risk identification:..........................................................................................................................................8
8. Conclusion:.....................................................................................................................................................9
9. References:..................................................................................................................................................10
Table of Contents
1. Introduction:..................................................................................................................................................3
2. Understanding the owner specification:........................................................................................................3
3. Understanding the assets:.............................................................................................................................3
4. Discussion on threats:....................................................................................................................................4
5. Understanding the Likelihood level computation:.........................................................................................7
6. Impact table specification:.............................................................................................................................7
7. Risk identification:..........................................................................................................................................8
8. Conclusion:.....................................................................................................................................................9
9. References:..................................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INFORMATION SECURITY MANAGEMENT 3
1. Introduction:
The CONVXYZ is an estate and conveyancing service located in the United Kingdom. They are
intended to provide various real estate services. Further, they have been conveyancing services from the side
of their employed lawyers. Here, their security system aims to minimise or secure the loss of their businesses.
To mitigate the various risks, for this case the ISO 31000:2018 standard is deployed. The main benefit
of the standard lies in the fact that it can provide various guides to manage risks at CONVXYZ. Further, these
applications can be customized to the business and its context. Moreover, it has been providing the common
measure in controlling any risk and this has not been sector or industry specific. Apart from this, it is usable
across the whole life of CONVXYZ and applies to any activity. This involves decision making at every level.
In the following study, the owner specifications are demonstrated. Next, the secondary and primary
assets are discussed. Then one threat and vulnerability is analyzed for every resource. Besides, a likelihood
level of computation is discussed through the help of Boston grid along with impact level specifications.
Lastly, risks are determined with its level through the Boston grid risk matrix.
2. Understanding the owner specification:
It is vital that the personnel of project management gains particular training for managing the risk.
These owners here might lack particular specific experience and expertise to determine the risk of the project
without any assistances. Hence, the real identification of the risks might be carried out by the representatives
of the owners through contractors (Singhal and Ou 2017). This can be done through external and internal
advisors and consultants. Further, the function of the risk identification must not be left with any scope that
should be covered explicitly in various documents of the project.
The aim behind the risk determination has been to avoid the omissions. Besides, this also involves
the avoiding of adverse pitfalls to get distracted through various factors that are never the core reasons.
These are just the symptoms. Thus, through treating the symptoms, instead of the root causes, the
appearance of the activity can be provided and this will never solve the issue. However, it must be kept in
mind that determinations of symptoms are far simpler that finding the root causes behind that. Hence, the
project owners must specify that the process of risk identification moves beyond the actual symptoms. The
disinterested owners, while outside at many times can perform the tasks (Liu and Liu 2016).
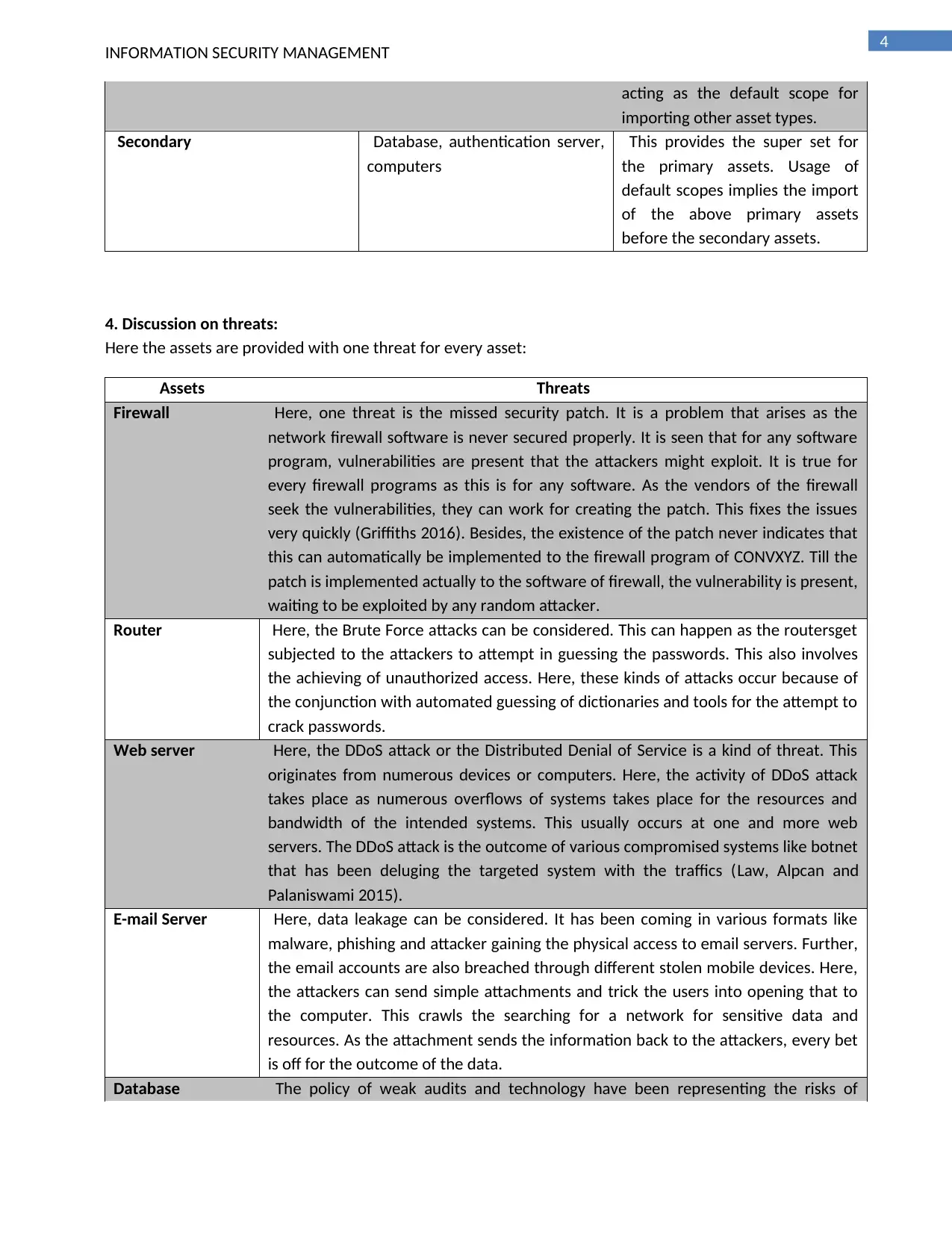
3. Understanding the assets:
The assets to be considered for the risk identification of CONVXYZ are highlighted below. Besides,
there types are also mentioned.
Type Resources Justification of their types
Primary Firewall, router, web-server,
email server
These primary assets are
imported in the first place for
importing particular type of
external assets. They have been
1. Introduction:
The CONVXYZ is an estate and conveyancing service located in the United Kingdom. They are
intended to provide various real estate services. Further, they have been conveyancing services from the side
of their employed lawyers. Here, their security system aims to minimise or secure the loss of their businesses.
To mitigate the various risks, for this case the ISO 31000:2018 standard is deployed. The main benefit
of the standard lies in the fact that it can provide various guides to manage risks at CONVXYZ. Further, these
applications can be customized to the business and its context. Moreover, it has been providing the common
measure in controlling any risk and this has not been sector or industry specific. Apart from this, it is usable
across the whole life of CONVXYZ and applies to any activity. This involves decision making at every level.
In the following study, the owner specifications are demonstrated. Next, the secondary and primary
assets are discussed. Then one threat and vulnerability is analyzed for every resource. Besides, a likelihood
level of computation is discussed through the help of Boston grid along with impact level specifications.
Lastly, risks are determined with its level through the Boston grid risk matrix.
2. Understanding the owner specification:
It is vital that the personnel of project management gains particular training for managing the risk.
These owners here might lack particular specific experience and expertise to determine the risk of the project
without any assistances. Hence, the real identification of the risks might be carried out by the representatives
of the owners through contractors (Singhal and Ou 2017). This can be done through external and internal
advisors and consultants. Further, the function of the risk identification must not be left with any scope that
should be covered explicitly in various documents of the project.
The aim behind the risk determination has been to avoid the omissions. Besides, this also involves
the avoiding of adverse pitfalls to get distracted through various factors that are never the core reasons.
These are just the symptoms. Thus, through treating the symptoms, instead of the root causes, the
appearance of the activity can be provided and this will never solve the issue. However, it must be kept in
mind that determinations of symptoms are far simpler that finding the root causes behind that. Hence, the
project owners must specify that the process of risk identification moves beyond the actual symptoms. The
disinterested owners, while outside at many times can perform the tasks (Liu and Liu 2016).
3. Understanding the assets:
The assets to be considered for the risk identification of CONVXYZ are highlighted below. Besides,
there types are also mentioned.
Type Resources Justification of their types
Primary Firewall, router, web-server,
email server
These primary assets are
imported in the first place for
importing particular type of
external assets. They have been
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SECURITY MANAGEMENT 4
acting as the default scope for
importing other asset types.
Secondary Database, authentication server,
computers
This provides the super set for
the primary assets. Usage of
default scopes implies the import
of the above primary assets
before the secondary assets.
4. Discussion on threats:
Here the assets are provided with one threat for every asset:
Assets Threats
Firewall Here, one threat is the missed security patch. It is a problem that arises as the
network firewall software is never secured properly. It is seen that for any software
program, vulnerabilities are present that the attackers might exploit. It is true for
every firewall programs as this is for any software. As the vendors of the firewall
seek the vulnerabilities, they can work for creating the patch. This fixes the issues
very quickly (Griffiths 2016). Besides, the existence of the patch never indicates that
this can automatically be implemented to the firewall program of CONVXYZ. Till the
patch is implemented actually to the software of firewall, the vulnerability is present,
waiting to be exploited by any random attacker.
Router Here, the Brute Force attacks can be considered. This can happen as the routersget
subjected to the attackers to attempt in guessing the passwords. This also involves
the achieving of unauthorized access. Here, these kinds of attacks occur because of
the conjunction with automated guessing of dictionaries and tools for the attempt to
crack passwords.
Web server Here, the DDoS attack or the Distributed Denial of Service is a kind of threat. This
originates from numerous devices or computers. Here, the activity of DDoS attack
takes place as numerous overflows of systems takes place for the resources and
bandwidth of the intended systems. This usually occurs at one and more web
servers. The DDoS attack is the outcome of various compromised systems like botnet
that has been deluging the targeted system with the traffics (Law, Alpcan and
Palaniswami 2015).
E-mail Server Here, data leakage can be considered. It has been coming in various formats like
malware, phishing and attacker gaining the physical access to email servers. Further,
the email accounts are also breached through different stolen mobile devices. Here,
the attackers can send simple attachments and trick the users into opening that to
the computer. This crawls the searching for a network for sensitive data and
resources. As the attachment sends the information back to the attackers, every bet
is off for the outcome of the data.
Database The policy of weak audits and technology have been representing the risks of
acting as the default scope for
importing other asset types.
Secondary Database, authentication server,
computers
This provides the super set for
the primary assets. Usage of
default scopes implies the import
of the above primary assets
before the secondary assets.
4. Discussion on threats:
Here the assets are provided with one threat for every asset:
Assets Threats
Firewall Here, one threat is the missed security patch. It is a problem that arises as the
network firewall software is never secured properly. It is seen that for any software
program, vulnerabilities are present that the attackers might exploit. It is true for
every firewall programs as this is for any software. As the vendors of the firewall
seek the vulnerabilities, they can work for creating the patch. This fixes the issues
very quickly (Griffiths 2016). Besides, the existence of the patch never indicates that
this can automatically be implemented to the firewall program of CONVXYZ. Till the
patch is implemented actually to the software of firewall, the vulnerability is present,
waiting to be exploited by any random attacker.
Router Here, the Brute Force attacks can be considered. This can happen as the routersget
subjected to the attackers to attempt in guessing the passwords. This also involves
the achieving of unauthorized access. Here, these kinds of attacks occur because of
the conjunction with automated guessing of dictionaries and tools for the attempt to
crack passwords.
Web server Here, the DDoS attack or the Distributed Denial of Service is a kind of threat. This
originates from numerous devices or computers. Here, the activity of DDoS attack
takes place as numerous overflows of systems takes place for the resources and
bandwidth of the intended systems. This usually occurs at one and more web
servers. The DDoS attack is the outcome of various compromised systems like botnet
that has been deluging the targeted system with the traffics (Law, Alpcan and
Palaniswami 2015).
E-mail Server Here, data leakage can be considered. It has been coming in various formats like
malware, phishing and attacker gaining the physical access to email servers. Further,
the email accounts are also breached through different stolen mobile devices. Here,
the attackers can send simple attachments and trick the users into opening that to
the computer. This crawls the searching for a network for sensitive data and
resources. As the attachment sends the information back to the attackers, every bet
is off for the outcome of the data.
Database The policy of weak audits and technology have been representing the risks of

INFORMATION SECURITY MANAGEMENT 5
CONVXYZ. This happens in terms of recoveries, forensics, detection, deterrence and
compliances. However, it is seen that the native DBMS or Database Management
System audit abilities have been resulting in the degradation of unacceptable
performances. They are vulnerable to the attacks that are privilege related. This
indicates that DBs or the developers can stop the auditing (Yu, Hu and Wang 2018).
Apart from this, CONVXYZ’s audit solutions have been lacking important
granularities. Here, for instance, the products of DBMS haverarely been logging what
application must be used. This is helpful to access the database, the sources of IP
addresses and various failed queries.
Further, the audit appliances of network-based audits are a great solution for
CONVXYZ. These do not affect the performance of databases. It has been operating
independently for every user and providing the collection of granular data (White,
Fisch and Pooch 2017).
Authentication
Server
Here, the hackers have been bypassing the security. Thus, the authentication is of
no exception to this case. The root causes of the bypass of authentication have been
the failure of software systems for imposing access policies. This is the weakly
designed architecture of authentication systems. Here, for instance, it is seen that
the web code performing the activity of authentication has been utilizing user
credentials. They have been enforcing the strong policies of passwords. This is
through simply failing to disallow the blank passwords (Xu and Lin 2016). In this way,
it generates a serious loophole. Again, as the developers of CONVXYZ make any
mistake to put variously unprotected and secured file in a similar folder, this makes
the web code vulnerable and visible. It can be said that these bypass attacks are
tried against the CONVXYZ’s customized authentication systems, instead of robust
industry standard ones.
Computers Here adware and spywares can be considered. This is the software designed for
tracking information about the habits of browsing. This highlights the pop-ups and
advertisements. The adware collects the information with the consent and is a
legitimate source of revenues for CONVXYZ. It is helpful for the users to try the
software for free. The clause of adware is hidden in the relevant document of user
agreements (Hou et al. 2018). It can be checked carefullyby reading the terms for
accepting the process to install the software. Adware’s presence over the computer
can only be seen as the pop-ups. It can also slow down the processor of the
computer and the speed of the Internet connection. Again, the spyware can be
installed in the machine without the user’s knowledge. This consists of keyloggers
recording personal data. This involves the passwords, email addresses, credit card
numbers. This turns to be dangerous due to the greater risk of theft of identification
(Hong et al. 2018).
5. Analyzing the vulnerabilities:
CONVXYZ. This happens in terms of recoveries, forensics, detection, deterrence and
compliances. However, it is seen that the native DBMS or Database Management
System audit abilities have been resulting in the degradation of unacceptable
performances. They are vulnerable to the attacks that are privilege related. This
indicates that DBs or the developers can stop the auditing (Yu, Hu and Wang 2018).
Apart from this, CONVXYZ’s audit solutions have been lacking important
granularities. Here, for instance, the products of DBMS haverarely been logging what
application must be used. This is helpful to access the database, the sources of IP
addresses and various failed queries.
Further, the audit appliances of network-based audits are a great solution for
CONVXYZ. These do not affect the performance of databases. It has been operating
independently for every user and providing the collection of granular data (White,
Fisch and Pooch 2017).
Authentication
Server
Here, the hackers have been bypassing the security. Thus, the authentication is of
no exception to this case. The root causes of the bypass of authentication have been
the failure of software systems for imposing access policies. This is the weakly
designed architecture of authentication systems. Here, for instance, it is seen that
the web code performing the activity of authentication has been utilizing user
credentials. They have been enforcing the strong policies of passwords. This is
through simply failing to disallow the blank passwords (Xu and Lin 2016). In this way,
it generates a serious loophole. Again, as the developers of CONVXYZ make any
mistake to put variously unprotected and secured file in a similar folder, this makes
the web code vulnerable and visible. It can be said that these bypass attacks are
tried against the CONVXYZ’s customized authentication systems, instead of robust
industry standard ones.
Computers Here adware and spywares can be considered. This is the software designed for
tracking information about the habits of browsing. This highlights the pop-ups and
advertisements. The adware collects the information with the consent and is a
legitimate source of revenues for CONVXYZ. It is helpful for the users to try the
software for free. The clause of adware is hidden in the relevant document of user
agreements (Hou et al. 2018). It can be checked carefullyby reading the terms for
accepting the process to install the software. Adware’s presence over the computer
can only be seen as the pop-ups. It can also slow down the processor of the
computer and the speed of the Internet connection. Again, the spyware can be
installed in the machine without the user’s knowledge. This consists of keyloggers
recording personal data. This involves the passwords, email addresses, credit card
numbers. This turns to be dangerous due to the greater risk of theft of identification
(Hong et al. 2018).
5. Analyzing the vulnerabilities:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
INFORMATION SECURITY MANAGEMENT 6
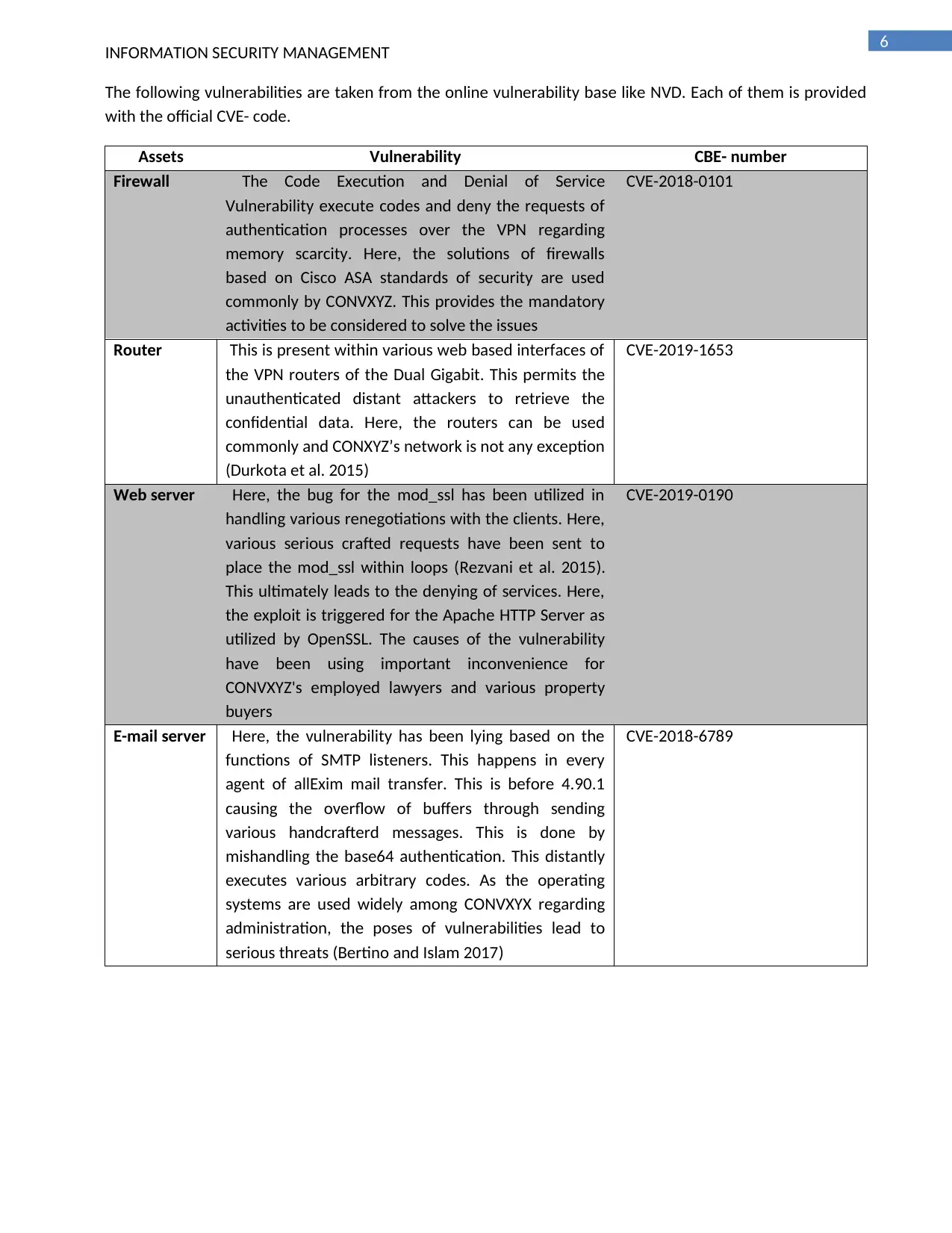
The following vulnerabilities are taken from the online vulnerability base like NVD. Each of them is provided
with the official CVE- code.
Assets Vulnerability CBE- number
Firewall The Code Execution and Denial of Service
Vulnerability execute codes and deny the requests of
authentication processes over the VPN regarding
memory scarcity. Here, the solutions of firewalls
based on Cisco ASA standards of security are used
commonly by CONVXYZ. This provides the mandatory
activities to be considered to solve the issues
CVE-2018-0101
Router This is present within various web based interfaces of
the VPN routers of the Dual Gigabit. This permits the
unauthenticated distant attackers to retrieve the
confidential data. Here, the routers can be used
commonly and CONXYZ’s network is not any exception
(Durkota et al. 2015)
CVE-2019-1653
Web server Here, the bug for the mod_ssl has been utilized in
handling various renegotiations with the clients. Here,
various serious crafted requests have been sent to
place the mod_ssl within loops (Rezvani et al. 2015).
This ultimately leads to the denying of services. Here,
the exploit is triggered for the Apache HTTP Server as
utilized by OpenSSL. The causes of the vulnerability
have been using important inconvenience for
CONVXYZ's employed lawyers and various property
buyers
CVE-2019-0190
E-mail server Here, the vulnerability has been lying based on the
functions of SMTP listeners. This happens in every
agent of allExim mail transfer. This is before 4.90.1
causing the overflow of buffers through sending
various handcrafterd messages. This is done by
mishandling the base64 authentication. This distantly
executes various arbitrary codes. As the operating
systems are used widely among CONVXYX regarding
administration, the poses of vulnerabilities lead to
serious threats (Bertino and Islam 2017)
CVE-2018-6789
The following vulnerabilities are taken from the online vulnerability base like NVD. Each of them is provided
with the official CVE- code.
Assets Vulnerability CBE- number
Firewall The Code Execution and Denial of Service
Vulnerability execute codes and deny the requests of
authentication processes over the VPN regarding
memory scarcity. Here, the solutions of firewalls
based on Cisco ASA standards of security are used
commonly by CONVXYZ. This provides the mandatory
activities to be considered to solve the issues
CVE-2018-0101
Router This is present within various web based interfaces of
the VPN routers of the Dual Gigabit. This permits the
unauthenticated distant attackers to retrieve the
confidential data. Here, the routers can be used
commonly and CONXYZ’s network is not any exception
(Durkota et al. 2015)
CVE-2019-1653
Web server Here, the bug for the mod_ssl has been utilized in
handling various renegotiations with the clients. Here,
various serious crafted requests have been sent to
place the mod_ssl within loops (Rezvani et al. 2015).
This ultimately leads to the denying of services. Here,
the exploit is triggered for the Apache HTTP Server as
utilized by OpenSSL. The causes of the vulnerability
have been using important inconvenience for
CONVXYZ's employed lawyers and various property
buyers
CVE-2019-0190
E-mail server Here, the vulnerability has been lying based on the
functions of SMTP listeners. This happens in every
agent of allExim mail transfer. This is before 4.90.1
causing the overflow of buffers through sending
various handcrafterd messages. This is done by
mishandling the base64 authentication. This distantly
executes various arbitrary codes. As the operating
systems are used widely among CONVXYX regarding
administration, the poses of vulnerabilities lead to
serious threats (Bertino and Islam 2017)
CVE-2018-6789
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
INFORMATION SECURITY MANAGEMENT 7
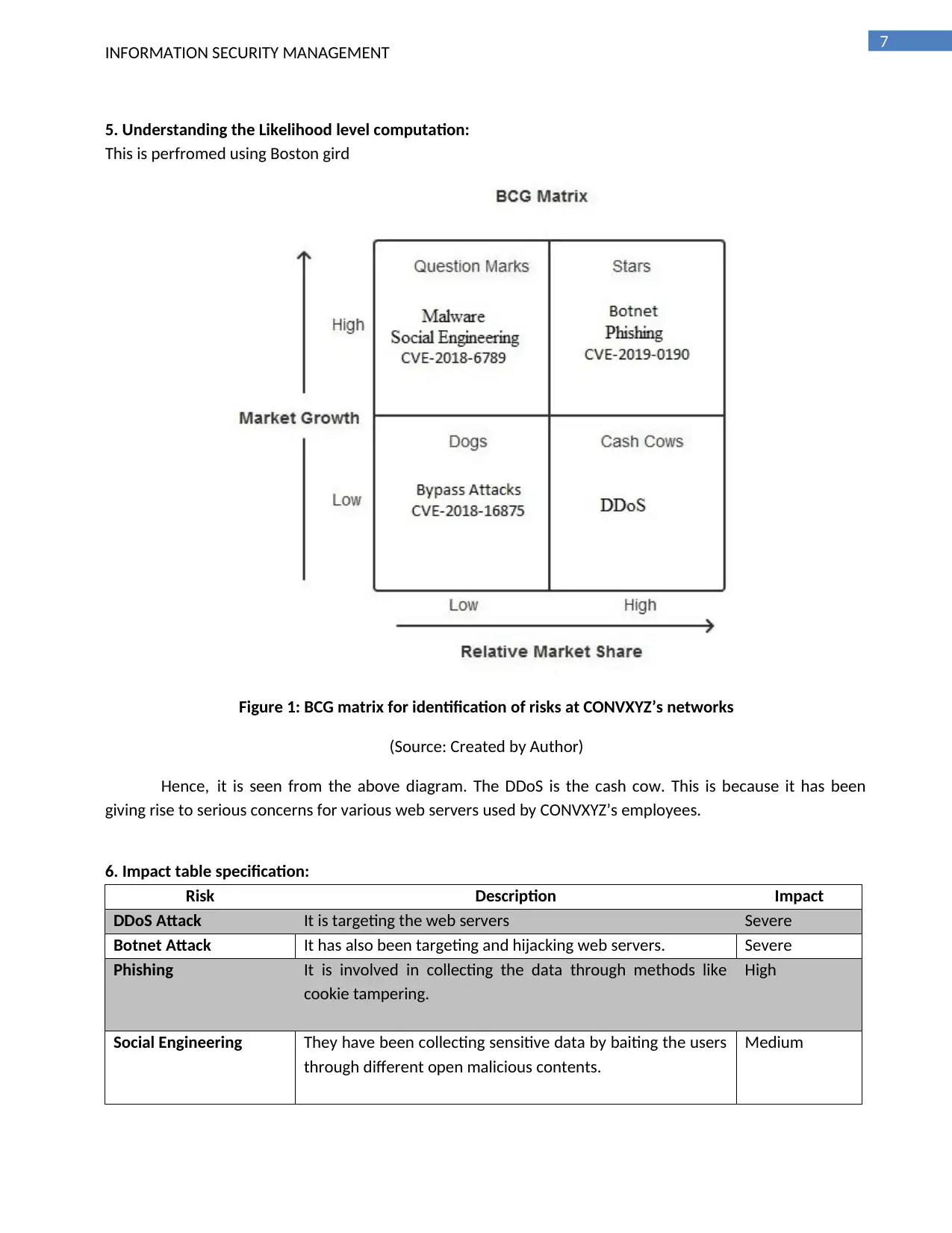
5. Understanding the Likelihood level computation:
This is perfromed using Boston gird
Figure 1: BCG matrix for identification of risks at CONVXYZ’s networks
(Source: Created by Author)
Hence, it is seen from the above diagram. The DDoS is the cash cow. This is because it has been
giving rise to serious concerns for various web servers used by CONVXYZ’s employees.
6. Impact table specification:
Risk Description Impact
DDoS Attack It is targeting the web servers Severe
Botnet Attack It has also been targeting and hijacking web servers. Severe
Phishing It is involved in collecting the data through methods like
cookie tampering.
High
Social Engineering They have been collecting sensitive data by baiting the users
through different open malicious contents.
Medium
5. Understanding the Likelihood level computation:
This is perfromed using Boston gird
Figure 1: BCG matrix for identification of risks at CONVXYZ’s networks
(Source: Created by Author)
Hence, it is seen from the above diagram. The DDoS is the cash cow. This is because it has been
giving rise to serious concerns for various web servers used by CONVXYZ’s employees.
6. Impact table specification:
Risk Description Impact
DDoS Attack It is targeting the web servers Severe
Botnet Attack It has also been targeting and hijacking web servers. Severe
Phishing It is involved in collecting the data through methods like
cookie tampering.
High
Social Engineering They have been collecting sensitive data by baiting the users
through different open malicious contents.
Medium
INFORMATION SECURITY MANAGEMENT 8
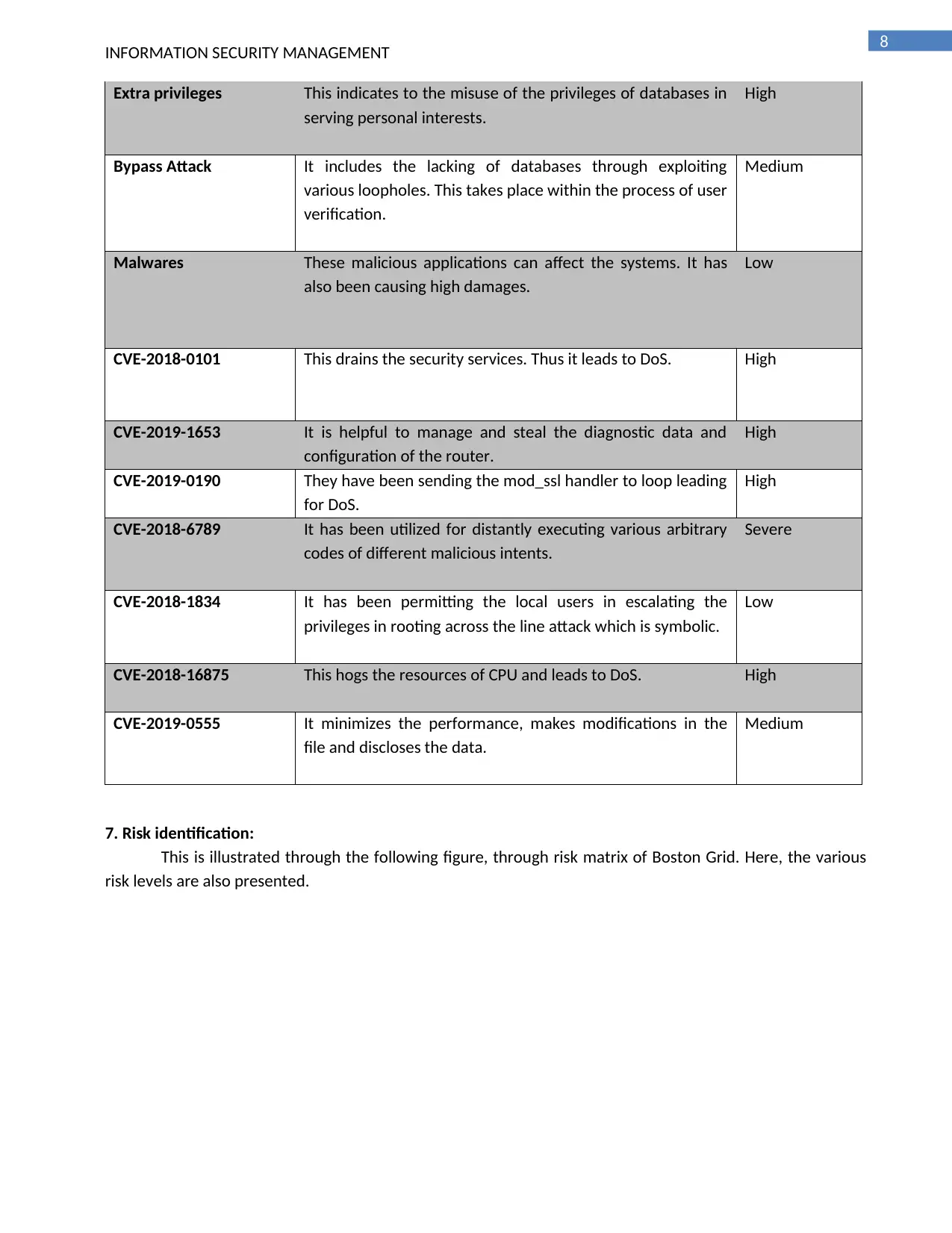
Extra privileges This indicates to the misuse of the privileges of databases in
serving personal interests.
High
Bypass Attack It includes the lacking of databases through exploiting
various loopholes. This takes place within the process of user
verification.
Medium
Malwares These malicious applications can affect the systems. It has
also been causing high damages.
Low
CVE-2018-0101 This drains the security services. Thus it leads to DoS. High
CVE-2019-1653 It is helpful to manage and steal the diagnostic data and
configuration of the router.
High
CVE-2019-0190 They have been sending the mod_ssl handler to loop leading
for DoS.
High
CVE-2018-6789 It has been utilized for distantly executing various arbitrary
codes of different malicious intents.
Severe
CVE-2018-1834 It has been permitting the local users in escalating the
privileges in rooting across the line attack which is symbolic.
Low
CVE-2018-16875 This hogs the resources of CPU and leads to DoS. High
CVE-2019-0555 It minimizes the performance, makes modifications in the
file and discloses the data.
Medium
7. Risk identification:
This is illustrated through the following figure, through risk matrix of Boston Grid. Here, the various
risk levels are also presented.
Extra privileges This indicates to the misuse of the privileges of databases in
serving personal interests.
High
Bypass Attack It includes the lacking of databases through exploiting
various loopholes. This takes place within the process of user
verification.
Medium
Malwares These malicious applications can affect the systems. It has
also been causing high damages.
Low
CVE-2018-0101 This drains the security services. Thus it leads to DoS. High
CVE-2019-1653 It is helpful to manage and steal the diagnostic data and
configuration of the router.
High
CVE-2019-0190 They have been sending the mod_ssl handler to loop leading
for DoS.
High
CVE-2018-6789 It has been utilized for distantly executing various arbitrary
codes of different malicious intents.
Severe
CVE-2018-1834 It has been permitting the local users in escalating the
privileges in rooting across the line attack which is symbolic.
Low
CVE-2018-16875 This hogs the resources of CPU and leads to DoS. High
CVE-2019-0555 It minimizes the performance, makes modifications in the
file and discloses the data.
Medium
7. Risk identification:
This is illustrated through the following figure, through risk matrix of Boston Grid. Here, the various
risk levels are also presented.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
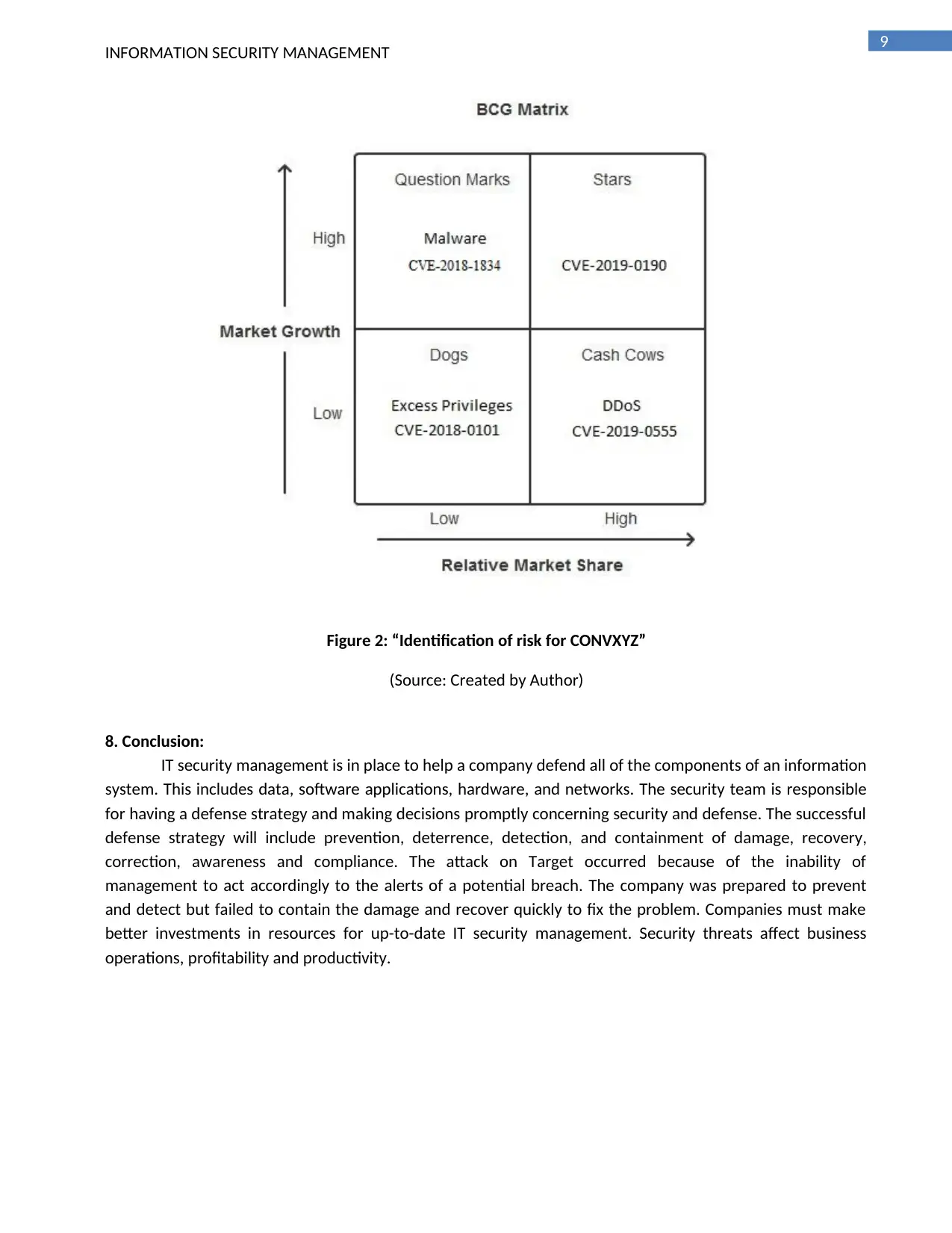
INFORMATION SECURITY MANAGEMENT 9
Figure 2: “Identification of risk for CONVXYZ”
(Source: Created by Author)
8. Conclusion:
IT security management is in place to help a company defend all of the components of an information
system. This includes data, software applications, hardware, and networks. The security team is responsible
for having a defense strategy and making decisions promptly concerning security and defense. The successful
defense strategy will include prevention, deterrence, detection, and containment of damage, recovery,
correction, awareness and compliance. The attack on Target occurred because of the inability of
management to act accordingly to the alerts of a potential breach. The company was prepared to prevent
and detect but failed to contain the damage and recover quickly to fix the problem. Companies must make
better investments in resources for up-to-date IT security management. Security threats affect business
operations, profitability and productivity.
Figure 2: “Identification of risk for CONVXYZ”
(Source: Created by Author)
8. Conclusion:
IT security management is in place to help a company defend all of the components of an information
system. This includes data, software applications, hardware, and networks. The security team is responsible
for having a defense strategy and making decisions promptly concerning security and defense. The successful
defense strategy will include prevention, deterrence, detection, and containment of damage, recovery,
correction, awareness and compliance. The attack on Target occurred because of the inability of
management to act accordingly to the alerts of a potential breach. The company was prepared to prevent
and detect but failed to contain the damage and recover quickly to fix the problem. Companies must make
better investments in resources for up-to-date IT security management. Security threats affect business
operations, profitability and productivity.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INFORMATION SECURITY MANAGEMENT 10
9. References:
Singhal, A. and Ou, X., 2017. Security risk analysis of enterprise networks using probabilistic attack graphs. In
Network Security Metrics (pp. 53-73). Springer, Cham.
Griffiths, P., 2016. Risk-based auditing. Routledge.
Law, Y.W., Alpcan, T. and Palaniswami, M., 2015. Security games for risk minimization in automatic
generation control. IEEE Transactions on Power Systems, 30(1), pp.223-232.
Yu, J., Hu, M. and Wang, P., 2018. Evaluation and reliability analysis of network security risk factors based on
DS evidence theory. Journal of Intelligent & Fuzzy Systems, 34(2), pp.861-869.
White, G.B., Fisch, E.A. and Pooch, U.W., 2017. Computer system and network security. CRC press.
Xu, H. and Lin, R., 2016. Resource allocation for network security risk assessment: A non-cooperative
differential game based approach. China Communications, 13(4), pp.131-135.
Durkota, K., Lisý, V., Bošanský, B. and Kiekintveld, C., 2015, June. Optimal network security hardening using
attack graph games. In Twenty-Fourth International Joint Conference on Artificial Intelligence.
Bertino, E. and Islam, N., 2017. Botnets and internet of things security. Computer, (2), pp.76-79.
Rezvani, M., Sekulic, V., Ignjatovic, A., Bertino, E. and Jha, S., 2015. Interdependent security risk analysis of
hosts and flows. IEEE Transactions on Information Forensics and Security, 10(11), pp.2325-2339.
Jia, Y., Xu, Z., Lai, L.L. and Wong, K.P., 2016. Risk-based power system security analysis considering cascading
outages. IEEE Transactions on Industrial Informatics, 12(2), pp.872-882.
Noel, S., 2018. A Review of Graph Approaches to Network Security Analytics. In From Database to Cyber
Security (pp. 300-323). Springer, Cham.
Munoz Gonzalez, L. and Lupu, E., 2016. Bayesian attack graphs for security risk assessment.
Li, F., Huang, Q., Zhu, J. and Peng, Z., 2015, May. Network security risk assessment based on item response
theory. In Proceedings of the 8th International Conference on Mobile Multimedia Communications (pp. 117-
122). ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering).
Liu, S.C. and Liu, Y., 2016, May. Network security risk assessment method based on HMM and attack graph
model. In 2016 17th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence,
Networking and Parallel/Distributed Computing (SNPD) (pp. 517-522). IEEE.
Hong, J.B., Yusuf, S.E., Kim, D.S. and Khan, K.M., 2018, June. Stateless Security Risk Assessment for Dynamic
Networks. In 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks
Workshops (DSN-W) (pp. 65-66). IEEE.
Hou, W., Ning, Z., Guo, L., Chen, Z. and Obaidat, M.S., 2018. Novel framework of risk-aware virtual network
embedding in optical data center networks. IEEE Systems Journal, 12(3), pp.2473-2482.
9. References:
Singhal, A. and Ou, X., 2017. Security risk analysis of enterprise networks using probabilistic attack graphs. In
Network Security Metrics (pp. 53-73). Springer, Cham.
Griffiths, P., 2016. Risk-based auditing. Routledge.
Law, Y.W., Alpcan, T. and Palaniswami, M., 2015. Security games for risk minimization in automatic
generation control. IEEE Transactions on Power Systems, 30(1), pp.223-232.
Yu, J., Hu, M. and Wang, P., 2018. Evaluation and reliability analysis of network security risk factors based on
DS evidence theory. Journal of Intelligent & Fuzzy Systems, 34(2), pp.861-869.
White, G.B., Fisch, E.A. and Pooch, U.W., 2017. Computer system and network security. CRC press.
Xu, H. and Lin, R., 2016. Resource allocation for network security risk assessment: A non-cooperative
differential game based approach. China Communications, 13(4), pp.131-135.
Durkota, K., Lisý, V., Bošanský, B. and Kiekintveld, C., 2015, June. Optimal network security hardening using
attack graph games. In Twenty-Fourth International Joint Conference on Artificial Intelligence.
Bertino, E. and Islam, N., 2017. Botnets and internet of things security. Computer, (2), pp.76-79.
Rezvani, M., Sekulic, V., Ignjatovic, A., Bertino, E. and Jha, S., 2015. Interdependent security risk analysis of
hosts and flows. IEEE Transactions on Information Forensics and Security, 10(11), pp.2325-2339.
Jia, Y., Xu, Z., Lai, L.L. and Wong, K.P., 2016. Risk-based power system security analysis considering cascading
outages. IEEE Transactions on Industrial Informatics, 12(2), pp.872-882.
Noel, S., 2018. A Review of Graph Approaches to Network Security Analytics. In From Database to Cyber
Security (pp. 300-323). Springer, Cham.
Munoz Gonzalez, L. and Lupu, E., 2016. Bayesian attack graphs for security risk assessment.
Li, F., Huang, Q., Zhu, J. and Peng, Z., 2015, May. Network security risk assessment based on item response
theory. In Proceedings of the 8th International Conference on Mobile Multimedia Communications (pp. 117-
122). ICST (Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering).
Liu, S.C. and Liu, Y., 2016, May. Network security risk assessment method based on HMM and attack graph
model. In 2016 17th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence,
Networking and Parallel/Distributed Computing (SNPD) (pp. 517-522). IEEE.
Hong, J.B., Yusuf, S.E., Kim, D.S. and Khan, K.M., 2018, June. Stateless Security Risk Assessment for Dynamic
Networks. In 2018 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks
Workshops (DSN-W) (pp. 65-66). IEEE.
Hou, W., Ning, Z., Guo, L., Chen, Z. and Obaidat, M.S., 2018. Novel framework of risk-aware virtual network
embedding in optical data center networks. IEEE Systems Journal, 12(3), pp.2473-2482.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





