Server Monitoring for Optimal Performance
VerifiedAdded on 2023/01/19
|7
|1882
|80
AI Summary
This document discusses the importance of server monitoring for optimal performance and provides insights into various tools available for IT infrastructure monitoring. It also highlights the top IT infrastructure monitoring tools in 2019.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

INFORMATION TECHNOLOGY INFRASTRACTURE
Student Name
College
Student Name
College
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Introduction
The idea driving server checking is straight-forward: server observing is the customary
accumulation and investigation of information to guarantee that servers are performing ideally
and giving their planned capacity. So as to serve the clients and organizations acceptably, flaw
happening in data centres and servers must be identified and anticipated effectively so as to
dispatch systems to endure the disappointments happened [1]. Disappointment in one of the
facilitated datacenters may proliferate to different datacenters and exacerbate things. So as to
avoid such circumstances, one can foresee a disappointment multiplying all through the
distributed computing framework and dispatch components to manage it proactively. The
information utilized for server observing envelops key execution markers (KPIs), organize
network, and application accessibility. For instance, checking a Windows document server
would analyze [2]:
Server working framework KPIs (CPU, memory, system and plate execution
measurements)
System Share accessibility
Log File Monitoring
Occasion Log Monitoring
Question a)
Tool Disk
usage
CPU
monitoring
Process
Monitoring
Bandwidth
Monitoring
Resource
Measuring
Overall
availability
Nagios
Core,
High Good Good Good Good Good
Ganglia, Medium Relatively
good
Relatively
good
Relatively
good
Relatively
good
Relatively
good
CollectD, Medium good good good good fair
Spiceworks, good good good good Good
Cacti, Low good good good good Relatively
good
Zabbix, Medium good good good good good
Icinga, High Relatively Relatively Relatively Relatively Relatively
The idea driving server checking is straight-forward: server observing is the customary
accumulation and investigation of information to guarantee that servers are performing ideally
and giving their planned capacity. So as to serve the clients and organizations acceptably, flaw
happening in data centres and servers must be identified and anticipated effectively so as to
dispatch systems to endure the disappointments happened [1]. Disappointment in one of the
facilitated datacenters may proliferate to different datacenters and exacerbate things. So as to
avoid such circumstances, one can foresee a disappointment multiplying all through the
distributed computing framework and dispatch components to manage it proactively. The
information utilized for server observing envelops key execution markers (KPIs), organize
network, and application accessibility. For instance, checking a Windows document server
would analyze [2]:
Server working framework KPIs (CPU, memory, system and plate execution
measurements)
System Share accessibility
Log File Monitoring
Occasion Log Monitoring
Question a)
Tool Disk
usage
CPU
monitoring
Process
Monitoring
Bandwidth
Monitoring
Resource
Measuring
Overall
availability
Nagios
Core,
High Good Good Good Good Good
Ganglia, Medium Relatively
good
Relatively
good
Relatively
good
Relatively
good
Relatively
good
CollectD, Medium good good good good fair
Spiceworks, good good good good Good
Cacti, Low good good good good Relatively
good
Zabbix, Medium good good good good good
Icinga, High Relatively Relatively Relatively Relatively Relatively
good good good good good
OpenNMS, Medium good good good good fair
WhatsUp
Gold,
Medium Relatively
good
Relatively
good
Relatively
good
Relatively
good
Relatively
good
In terms of the following server availability tools, Cacti remains the top because of its wide
application in measuring almost all the parameters of the server and also in matters of being able
to use low space in the disk. Configuration process in it is fair and not tedious as in Nagios Core
which has been in the market for long
Question b)
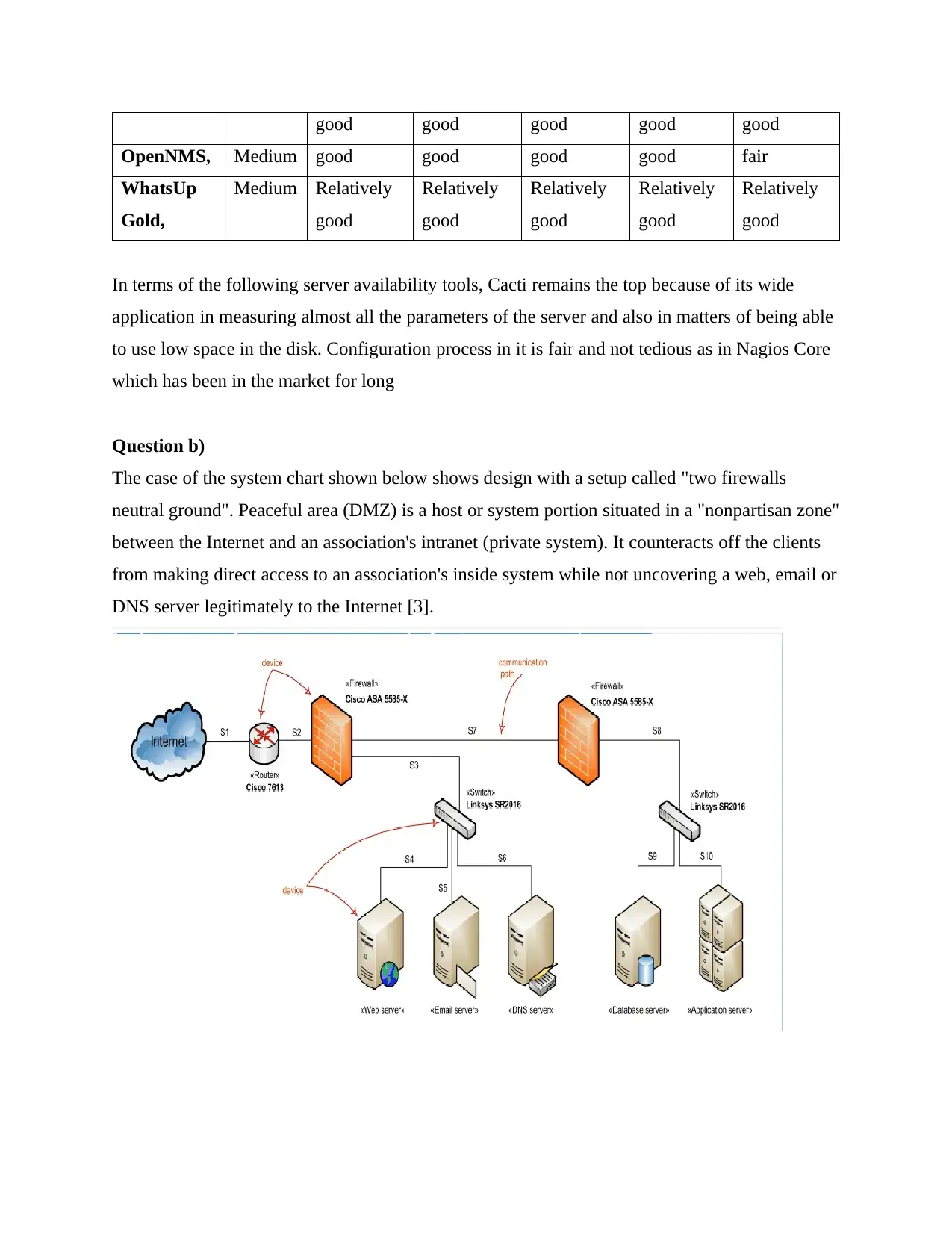
The case of the system chart shown below shows design with a setup called "two firewalls
neutral ground". Peaceful area (DMZ) is a host or system portion situated in a "nonpartisan zone"
between the Internet and an association's intranet (private system). It counteracts off the clients
from making direct access to an association's inside system while not uncovering a web, email or
DNS server legitimately to the Internet [3].
OpenNMS, Medium good good good good fair
WhatsUp
Gold,
Medium Relatively
good
Relatively
good
Relatively
good
Relatively
good
Relatively
good
In terms of the following server availability tools, Cacti remains the top because of its wide
application in measuring almost all the parameters of the server and also in matters of being able
to use low space in the disk. Configuration process in it is fair and not tedious as in Nagios Core
which has been in the market for long
Question b)
The case of the system chart shown below shows design with a setup called "two firewalls
neutral ground". Peaceful area (DMZ) is a host or system portion situated in a "nonpartisan zone"
between the Internet and an association's intranet (private system). It counteracts off the clients
from making direct access to an association's inside system while not uncovering a web, email or
DNS server legitimately to the Internet [3].

Question c)
Whenever an IT expert or an organization thinks to set up systems or applications, their main
aim and hope are that all those installations will work well without interference in the process of
running. They are all installed in the very heart of the servers. It is very important for constant
monitoring of the servers in order to establish their performance and how they are working out
[5]. Failure to be keen on this aspect can lead to devastating effects when the vulnerabilities
within hits circles are exploited by the malicious intruders. The main solution towards sealing all
these loops holes is to have a careful eye on all the operations and logs that are happing from the
server. This solution is categorized into several specific aspects which are foundation towards
protecting the servers in the face of many possible failures. These are just a few among many
others which can be put in place to ensure that security is a priority [4].
i) Cryptographic Keys
This is a very modern technology towards the protection of the servers and it involves two major
keys which are used instead of passwords. These keys are to make access to the server on two
independent grounds. The primary key is supposed to be used by the insider or rather the system
administration and must not be shared to other people while the other secondary key towards the
server is public to be used by other normal users. The main tragedy of using passwords is that
they can be easily be cracked down by the attackers, so the modern use of keys ensures no such a
fault is left aside it would take a hacker a hell of a time to bypass the authentication set aside.
ii) The use of firewalls
In any network environment, there is so much traffic towards the server. Each and every ICT
department must be very alert towards this since, when these packets are coming some of them
come along with Trojan horses which are loaded with viruses. This software ensures that all the
incoming requests have been filtered and checked before they can be allowed to enter into the
server. The suspected ones are blocked and this ensures the security of the servers [6].
iii) Use of Virtual Private Network
This is a technology in computer networks that masks the real server and provides an IP address
which helps it to be identified from the network without having to be exposed therein. This
provides security to the servers in place.
Question d)
Whenever an IT expert or an organization thinks to set up systems or applications, their main
aim and hope are that all those installations will work well without interference in the process of
running. They are all installed in the very heart of the servers. It is very important for constant
monitoring of the servers in order to establish their performance and how they are working out
[5]. Failure to be keen on this aspect can lead to devastating effects when the vulnerabilities
within hits circles are exploited by the malicious intruders. The main solution towards sealing all
these loops holes is to have a careful eye on all the operations and logs that are happing from the
server. This solution is categorized into several specific aspects which are foundation towards
protecting the servers in the face of many possible failures. These are just a few among many
others which can be put in place to ensure that security is a priority [4].
i) Cryptographic Keys
This is a very modern technology towards the protection of the servers and it involves two major
keys which are used instead of passwords. These keys are to make access to the server on two
independent grounds. The primary key is supposed to be used by the insider or rather the system
administration and must not be shared to other people while the other secondary key towards the
server is public to be used by other normal users. The main tragedy of using passwords is that
they can be easily be cracked down by the attackers, so the modern use of keys ensures no such a
fault is left aside it would take a hacker a hell of a time to bypass the authentication set aside.
ii) The use of firewalls
In any network environment, there is so much traffic towards the server. Each and every ICT
department must be very alert towards this since, when these packets are coming some of them
come along with Trojan horses which are loaded with viruses. This software ensures that all the
incoming requests have been filtered and checked before they can be allowed to enter into the
server. The suspected ones are blocked and this ensures the security of the servers [6].
iii) Use of Virtual Private Network
This is a technology in computer networks that masks the real server and provides an IP address
which helps it to be identified from the network without having to be exposed therein. This
provides security to the servers in place.
Question d)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Distributed computing is a novel innovation in the field of dispersed registering. Use of Cloud
registering is expanding quickly step by step. So as to serve the clients and organizations
acceptably, flaw happening in data centres and servers must be identified and anticipated
effectively so as to dispatch systems to endure the disappointments happened [10].
Disappointment in one of the facilitated datacenters may proliferate to different datacenters and
exacerbate things. So as to avoid such circumstances, one can foresee a disappointment
multiplying all through the distributed computing framework and dispatch components to
manage it proactively. One of the approaches to anticipate disappointments is to prepare a
machine to foresee disappointment based on messages or logs go between different parts of the
cloud [7].
In the instructional meeting, the machine can recognize certain message designs identifying with
the disappointment of information focuses. Later on, the machine can be utilized to check
whether a specific gathering of message logs pursue such examples or not. In addition, each
cloud server can be characterized by a state which demonstrates whether the cloud is running
legitimately or is confronting a few disappointment. Parameters, for example, CPU use, memory
utilization and so forth can be kept up for every one of the servers. Utilizing these parameters,
we can include a layer of the location wherein we build up a choice tree dependent on these
parameters which can order whether the gone in parameters to the choice tree demonstrate
disappointment state or legitimate state [8].
The following are the impacts of such negligence on specific parts of the server monitoring
system
Site server
No site organization is conceivable. You can't interface the reassure to the site.
The administration point gathers customer data and reserves it until the website server is back on
the web.
Clients can run existing organizations, and customers can download content from conveyance
focuses.
Site database
o No site organization is conceivable.
o On the off chance that the Configuration Manager customer as of now has an approaching task
with new strategies, and if the administration point has reserved the arrangement body, the
registering is expanding quickly step by step. So as to serve the clients and organizations
acceptably, flaw happening in data centres and servers must be identified and anticipated
effectively so as to dispatch systems to endure the disappointments happened [10].
Disappointment in one of the facilitated datacenters may proliferate to different datacenters and
exacerbate things. So as to avoid such circumstances, one can foresee a disappointment
multiplying all through the distributed computing framework and dispatch components to
manage it proactively. One of the approaches to anticipate disappointments is to prepare a
machine to foresee disappointment based on messages or logs go between different parts of the
cloud [7].
In the instructional meeting, the machine can recognize certain message designs identifying with
the disappointment of information focuses. Later on, the machine can be utilized to check
whether a specific gathering of message logs pursue such examples or not. In addition, each
cloud server can be characterized by a state which demonstrates whether the cloud is running
legitimately or is confronting a few disappointment. Parameters, for example, CPU use, memory
utilization and so forth can be kept up for every one of the servers. Utilizing these parameters,
we can include a layer of the location wherein we build up a choice tree dependent on these
parameters which can order whether the gone in parameters to the choice tree demonstrate
disappointment state or legitimate state [8].
The following are the impacts of such negligence on specific parts of the server monitoring
system
Site server
No site organization is conceivable. You can't interface the reassure to the site.
The administration point gathers customer data and reserves it until the website server is back on
the web.
Clients can run existing organizations, and customers can download content from conveyance
focuses.
Site database
o No site organization is conceivable.
o On the off chance that the Configuration Manager customer as of now has an approaching task
with new strategies, and if the administration point has reserved the arrangement body, the

customer can make a strategy body demand and get the approach body answer. Be that as it may,
the site can't support any new arrangement task demands [9].
o Customers can run organizations, just in the event that they've effectively gotten the strategy, and
the related source records are as of now stored locally at the customer.
The Management point
In spite of the fact that you can make new arrangements, customers don't get them until an
administration point is on the web.
Customers still gather stock, programming metering, and status data. They store this information
locally until the administration point is accessible.
Customers can run arrangements, just on the off chance that they've effectively gotten the
approach, and the related source records are as of now reserved locally at the customer.
Conclusion
It is a key thing for any technological organization to be careful about the security of their data
centres so that they can evade most of the losses that they are likely to incur. There must be a
very stringent mechanism put in place to tackle all the issue that may be connected with all the
threats so that the servers can be secure. Server continuous monitoring is another key aspect to
consider.
References
[1]R. Rashedi and T. Hegazy, "Capital renewal optimisation for large-scale infrastructure
networks: genetic algorithms versus advanced mathematical tools", Structure and Infrastructure
Engineering, vol. 11, no. 3, pp. 253-262, 2014. Available: 10.1080/15732479.2013.866968.
[2]H. Jui, "Monitoring fog with cellular network infrastructure", Physics Today, vol. 67, no. 6, p.
453, 2015. Available: 10.1063/pt.5.7138.
[3]S. Thöns, "On the Value of Monitoring Information for the Structural Integrity and Risk
Management", Computer-Aided Civil and Infrastructure Engineering, vol. 33, no. 1, pp. 79-94,
2017. Available: 10.1111/mice.12332.
the site can't support any new arrangement task demands [9].
o Customers can run organizations, just in the event that they've effectively gotten the strategy, and
the related source records are as of now stored locally at the customer.
The Management point
In spite of the fact that you can make new arrangements, customers don't get them until an
administration point is on the web.
Customers still gather stock, programming metering, and status data. They store this information
locally until the administration point is accessible.
Customers can run arrangements, just on the off chance that they've effectively gotten the
approach, and the related source records are as of now reserved locally at the customer.
Conclusion
It is a key thing for any technological organization to be careful about the security of their data
centres so that they can evade most of the losses that they are likely to incur. There must be a
very stringent mechanism put in place to tackle all the issue that may be connected with all the
threats so that the servers can be secure. Server continuous monitoring is another key aspect to
consider.
References
[1]R. Rashedi and T. Hegazy, "Capital renewal optimisation for large-scale infrastructure
networks: genetic algorithms versus advanced mathematical tools", Structure and Infrastructure
Engineering, vol. 11, no. 3, pp. 253-262, 2014. Available: 10.1080/15732479.2013.866968.
[2]H. Jui, "Monitoring fog with cellular network infrastructure", Physics Today, vol. 67, no. 6, p.
453, 2015. Available: 10.1063/pt.5.7138.
[3]S. Thöns, "On the Value of Monitoring Information for the Structural Integrity and Risk
Management", Computer-Aided Civil and Infrastructure Engineering, vol. 33, no. 1, pp. 79-94,
2017. Available: 10.1111/mice.12332.

[4]A. Alowayr and A. Badii, "Review of Monitoring Tools for E-Learning Platforms",
International Journal of Computer Science and Information Technology, vol. 6, no. 3, pp. 79-86,
2014. Available: 10.5121/ijcsit.2014.6306.
[5]N. Johnson, "Information Infrastructure as Rhetoric: Tools for Analysis", Poroi, vol. 8, no. 1,
2012. Available: 10.13008/2151-2957.1113.
[6]"Top IT Infrastructure Monitoring Tools in 2019 | TrustRadius". [Online]. Available:
https://www.trustradius.com/it-infrastructure-monitoring. [Accessed: 2019].
[7]"Best IT Infrastructure Monitoring Tools & Software 2019 ...". [Online]. Available:
https://www.pcwdld.com/best-infrastructure-monitoring-tools-and-software. [Accessed: 2019].
[8]"IT Infrastructure Monitoring Tools Reviews - gartner.com". [Online]. Available:
https://www.gartner.com/reviews/market/it-infrastructure-monitoring-tools/vendors. [Accessed:
2019].
[9]"Best IT Infrastructure Monitoring Tools and Software ...". [Online]. Available:
https://www.addictivetips.com/net-admin/it-infrastructure-monitoring/. [Accessed: 2019].
[10] J. Hernantes, G. Gallardo and N. Serrano, "IT Infrastructure-Monitoring Tools" in IEEE Software,
vol. 32, no. 04, pp. 88-93, 2015.doi: 10.1109/MS.2015.96
International Journal of Computer Science and Information Technology, vol. 6, no. 3, pp. 79-86,
2014. Available: 10.5121/ijcsit.2014.6306.
[5]N. Johnson, "Information Infrastructure as Rhetoric: Tools for Analysis", Poroi, vol. 8, no. 1,
2012. Available: 10.13008/2151-2957.1113.
[6]"Top IT Infrastructure Monitoring Tools in 2019 | TrustRadius". [Online]. Available:
https://www.trustradius.com/it-infrastructure-monitoring. [Accessed: 2019].
[7]"Best IT Infrastructure Monitoring Tools & Software 2019 ...". [Online]. Available:
https://www.pcwdld.com/best-infrastructure-monitoring-tools-and-software. [Accessed: 2019].
[8]"IT Infrastructure Monitoring Tools Reviews - gartner.com". [Online]. Available:
https://www.gartner.com/reviews/market/it-infrastructure-monitoring-tools/vendors. [Accessed:
2019].
[9]"Best IT Infrastructure Monitoring Tools and Software ...". [Online]. Available:
https://www.addictivetips.com/net-admin/it-infrastructure-monitoring/. [Accessed: 2019].
[10] J. Hernantes, G. Gallardo and N. Serrano, "IT Infrastructure-Monitoring Tools" in IEEE Software,
vol. 32, no. 04, pp. 88-93, 2015.doi: 10.1109/MS.2015.96
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




