Information Technology Security and Cryptography Assignment
VerifiedAdded on 2021/04/24
|5
|1474
|167
Homework Assignment
AI Summary
This Information Technology assignment delves into critical aspects of IT security. It begins by defining and explaining the principles of confidentiality, integrity, and availability within the context of ATM card security, emphasizing the importance of data encryption and protection against unauthorized access or modification. The assignment then addresses the potential vulnerabilities of ATM PIN security, outlining the limited attempts allowed to prevent unauthorized access. Furthermore, the assignment explores the advantages of biometric authentication, highlighting its benefits over traditional username and password methods. The discussion extends to the concepts of false positive and false negative authentication rates in biometric systems. Finally, the assignment concludes with a practical example of decrypting a text encrypted using a transposition cipher, demonstrating the columnar transposition method. The assignment draws upon several academic sources to support its claims and provide a comprehensive understanding of the subject matter.

Running head: INFORMATION TECHNOLOGY
INFORMATION TECHNOLOGY
Name of Student-
Name of University-
Author’s Note-
INFORMATION TECHNOLOGY
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION TECHNOLOGY
Question 1:
Confidentiality:
Confidentiality involves keeping the information secure and protected from some unauthorized person.
The information involved in ATM cards has some important values and are to be kept confidential.
The users of ATM must keep the credentials of their cards secret so that the information on the card and the security of their
bank details are kept safe (Tchernykh et al., 2016).
The confidentiality of data can be done by applying encryption method on the information that is to be kept secured.
The process of encryption ensures the right person to read the right information.
Confidentiality ensures proper encryption and is used in every part of the security where the data is to be kept secured.
The credentials of the ATM are to be kept secured so that any third person cannot get the details of the ATM pin.
Integrity:
From the term integrity, it can be ensured that the information of the ATM card is to be protected from being changed or
altered by some unauthorized parties.
The information or the data that is in the ATM has values if the information stored in the system is correct.
The information transmitting from one network to another should not be tampered (Sumra, Hasbullah & AbManan, 2015).
With the encryption process, the data integrity is also kept secured.
The methods that helps to keep the integrity of the data includes the hashing function.
Availability:
The data that are available includes that the information that is involved in the ATM transaction process should be available
only with the authorized parties and the authenticate users can only access the data.
If the right person accesses the information at right time, then only the information is considered to be valid.
The availability of the data can also be hampered includes natural disasters and power outages.
To ensure availability of data, the information is to be kept as a backup to keep secure from any type of security breach that
may occur.
Question 2:
Several ways are there by which the thief can identify the pin of the ATM from the remaining pin that are good. The maximum
number of possibility that the thief can attempt to get the pin is 5! / (5 - 4)! that is 120 set of pins. The thief can enter all total of 120
times the secret pin.
But keeping the security of the ATM, the system of ATM does not allow a user to enter the pin several times. The number of
time the pins that can be entered by a user is maximum of three times. After entering the wrong pin three times, the card will be
blocked and the thief will not be able to withdraw money from the ATM machine.
Question 3:
Three advantages of biometric authentication because of which the users use them for security purpose are:
Question 1:
Confidentiality:
Confidentiality involves keeping the information secure and protected from some unauthorized person.
The information involved in ATM cards has some important values and are to be kept confidential.
The users of ATM must keep the credentials of their cards secret so that the information on the card and the security of their
bank details are kept safe (Tchernykh et al., 2016).
The confidentiality of data can be done by applying encryption method on the information that is to be kept secured.
The process of encryption ensures the right person to read the right information.
Confidentiality ensures proper encryption and is used in every part of the security where the data is to be kept secured.
The credentials of the ATM are to be kept secured so that any third person cannot get the details of the ATM pin.
Integrity:
From the term integrity, it can be ensured that the information of the ATM card is to be protected from being changed or
altered by some unauthorized parties.
The information or the data that is in the ATM has values if the information stored in the system is correct.
The information transmitting from one network to another should not be tampered (Sumra, Hasbullah & AbManan, 2015).
With the encryption process, the data integrity is also kept secured.
The methods that helps to keep the integrity of the data includes the hashing function.
Availability:
The data that are available includes that the information that is involved in the ATM transaction process should be available
only with the authorized parties and the authenticate users can only access the data.
If the right person accesses the information at right time, then only the information is considered to be valid.
The availability of the data can also be hampered includes natural disasters and power outages.
To ensure availability of data, the information is to be kept as a backup to keep secure from any type of security breach that
may occur.
Question 2:
Several ways are there by which the thief can identify the pin of the ATM from the remaining pin that are good. The maximum
number of possibility that the thief can attempt to get the pin is 5! / (5 - 4)! that is 120 set of pins. The thief can enter all total of 120
times the secret pin.
But keeping the security of the ATM, the system of ATM does not allow a user to enter the pin several times. The number of
time the pins that can be entered by a user is maximum of three times. After entering the wrong pin three times, the card will be
blocked and the thief will not be able to withdraw money from the ATM machine.
Question 3:
Three advantages of biometric authentication because of which the users use them for security purpose are:
2INFORMATION TECHNOLOGY
1. While using the biometric authentication, the user does not have to enter their usernames and passwords multiple times to login
their account (Bhagavatula et al., 2015). The biometric helps to replace the password and the user name and is considered to be an
alternative to enter the password many times.
2. The second advantage that biometric authentication can provide is the advantage of not remembering the password all the time the
user have to login. Biometric systems use physical parts to keep the system secure. So, using the biometric system is the user can login
with the body part whose data is stored in the database (He & Wang, 2015). The user do not have to remember the password and enter
the forgot password page many times that may hamper the security of the system.
3. The third advantage that the biometric authentication provide is accountability to the users.
Question 4:
False positive authentication for biometric is basically a technique in which the system accepts a user who is unauthorized as a
authorized person (Pinto et al., 2014). The false positive case arise when the system rematches the data of an authorized one similar to
that of the unauthorized person. According to many surveys, the rate of false positive is more than the rate of false negative. The rate
of false negative is a technique in which the system rejects an authorized person even when its data is present in the database (Hadid et
al., 2015). The system cannot match the data of the authorized person with that which is stored in the database. Generally, the
percentage of false positive starts from zero whereas the percentage of false negative starts from 0.00066%.
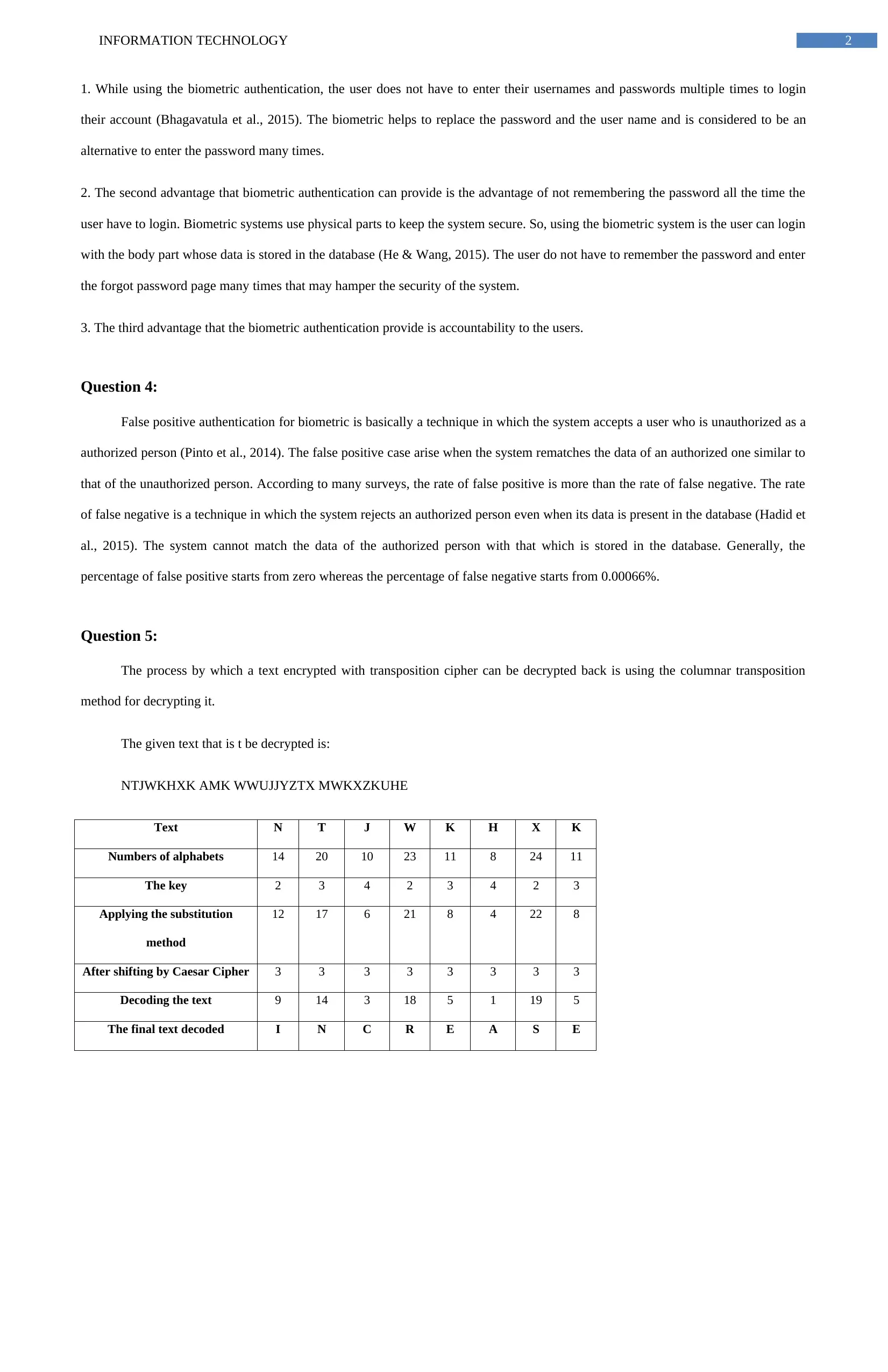
Question 5:
The process by which a text encrypted with transposition cipher can be decrypted back is using the columnar transposition
method for decrypting it.
The given text that is t be decrypted is:
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Text N T J W K H X K
Numbers of alphabets 14 20 10 23 11 8 24 11
The key 2 3 4 2 3 4 2 3
Applying the substitution
method
12 17 6 21 8 4 22 8
After shifting by Caesar Cipher 3 3 3 3 3 3 3 3
Decoding the text 9 14 3 18 5 1 19 5
The final text decoded I N C R E A S E
1. While using the biometric authentication, the user does not have to enter their usernames and passwords multiple times to login
their account (Bhagavatula et al., 2015). The biometric helps to replace the password and the user name and is considered to be an
alternative to enter the password many times.
2. The second advantage that biometric authentication can provide is the advantage of not remembering the password all the time the
user have to login. Biometric systems use physical parts to keep the system secure. So, using the biometric system is the user can login
with the body part whose data is stored in the database (He & Wang, 2015). The user do not have to remember the password and enter
the forgot password page many times that may hamper the security of the system.
3. The third advantage that the biometric authentication provide is accountability to the users.
Question 4:
False positive authentication for biometric is basically a technique in which the system accepts a user who is unauthorized as a
authorized person (Pinto et al., 2014). The false positive case arise when the system rematches the data of an authorized one similar to
that of the unauthorized person. According to many surveys, the rate of false positive is more than the rate of false negative. The rate
of false negative is a technique in which the system rejects an authorized person even when its data is present in the database (Hadid et
al., 2015). The system cannot match the data of the authorized person with that which is stored in the database. Generally, the
percentage of false positive starts from zero whereas the percentage of false negative starts from 0.00066%.
Question 5:
The process by which a text encrypted with transposition cipher can be decrypted back is using the columnar transposition
method for decrypting it.
The given text that is t be decrypted is:
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Text N T J W K H X K
Numbers of alphabets 14 20 10 23 11 8 24 11
The key 2 3 4 2 3 4 2 3
Applying the substitution
method
12 17 6 21 8 4 22 8
After shifting by Caesar Cipher 3 3 3 3 3 3 3 3
Decoding the text 9 14 3 18 5 1 19 5
The final text decoded I N C R E A S E
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
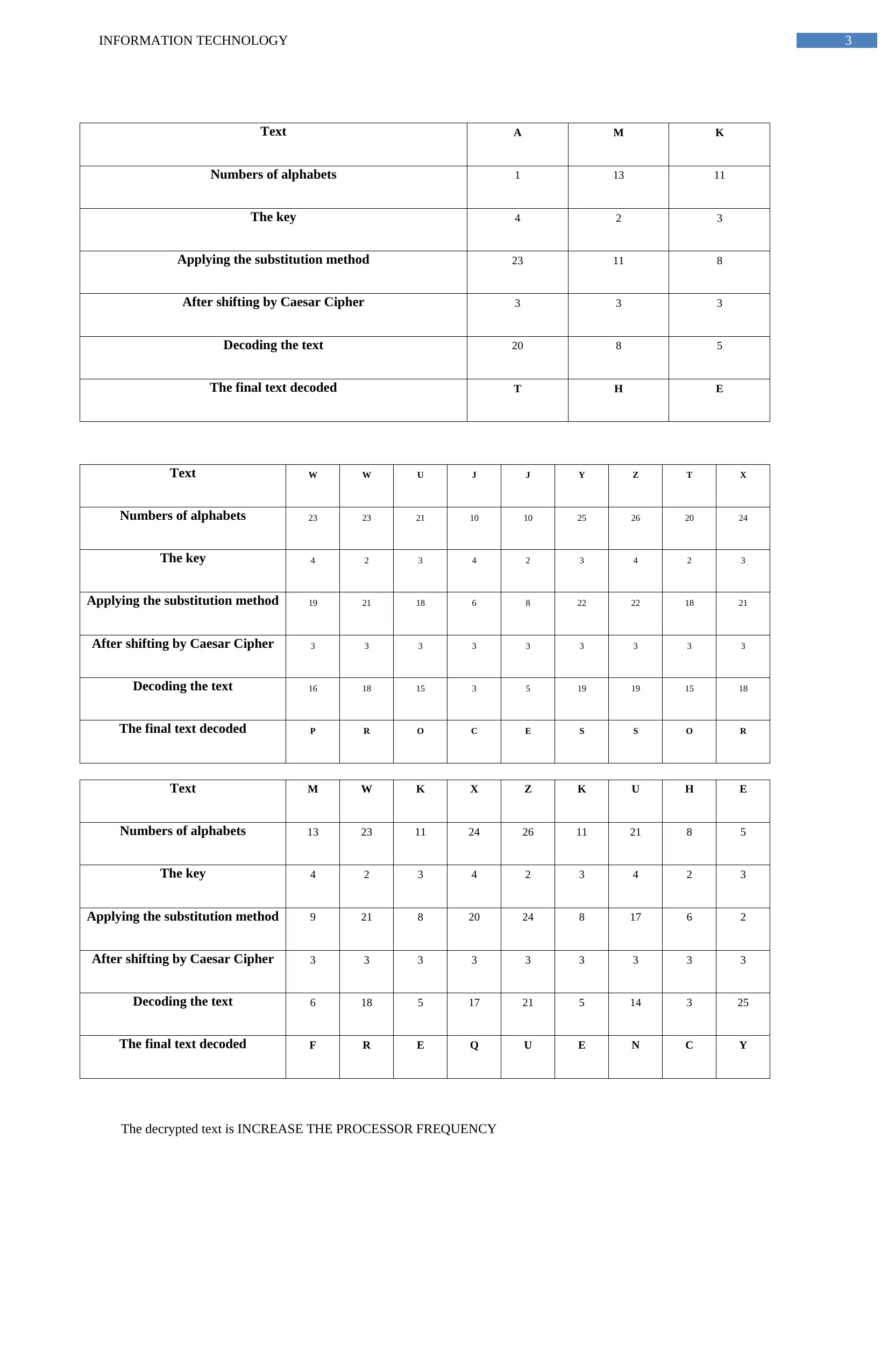
3INFORMATION TECHNOLOGY
Text A M K
Numbers of alphabets 1 13 11
The key 4 2 3
Applying the substitution method 23 11 8
After shifting by Caesar Cipher 3 3 3
Decoding the text 20 8 5
The final text decoded T H E
Text W W U J J Y Z T X
Numbers of alphabets 23 23 21 10 10 25 26 20 24
The key 4 2 3 4 2 3 4 2 3
Applying the substitution method 19 21 18 6 8 22 22 18 21
After shifting by Caesar Cipher 3 3 3 3 3 3 3 3 3
Decoding the text 16 18 15 3 5 19 19 15 18
The final text decoded P R O C E S S O R
Text M W K X Z K U H E
Numbers of alphabets 13 23 11 24 26 11 21 8 5
The key 4 2 3 4 2 3 4 2 3
Applying the substitution method 9 21 8 20 24 8 17 6 2
After shifting by Caesar Cipher 3 3 3 3 3 3 3 3 3
Decoding the text 6 18 5 17 21 5 14 3 25
The final text decoded F R E Q U E N C Y
The decrypted text is INCREASE THE PROCESSOR FREQUENCY
Text A M K
Numbers of alphabets 1 13 11
The key 4 2 3
Applying the substitution method 23 11 8
After shifting by Caesar Cipher 3 3 3
Decoding the text 20 8 5
The final text decoded T H E
Text W W U J J Y Z T X
Numbers of alphabets 23 23 21 10 10 25 26 20 24
The key 4 2 3 4 2 3 4 2 3
Applying the substitution method 19 21 18 6 8 22 22 18 21
After shifting by Caesar Cipher 3 3 3 3 3 3 3 3 3
Decoding the text 16 18 15 3 5 19 19 15 18
The final text decoded P R O C E S S O R
Text M W K X Z K U H E
Numbers of alphabets 13 23 11 24 26 11 21 8 5
The key 4 2 3 4 2 3 4 2 3
Applying the substitution method 9 21 8 20 24 8 17 6 2
After shifting by Caesar Cipher 3 3 3 3 3 3 3 3 3
Decoding the text 6 18 5 17 21 5 14 3 25
The final text decoded F R E Q U E N C Y
The decrypted text is INCREASE THE PROCESSOR FREQUENCY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION TECHNOLOGY
REFERENCES
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015). Biometric authentication on iphone and
android: Usability, perceptions, and influences on adoption. Proc. USEC, 1-2.
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack: an evaluation methodology and
lessons learned. IEEE Signal Processing Magazine, 32(5), 20-30.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver environment. IEEE Systems Journal, 9(3),
816-823.
Pinto, J. R., Cardoso, J. S., Lourenço, A., & Carreiras, C. (2017). Towards a Continuous Biometric System Based on ECG Signals
Acquired on the Steering Wheel. Sensors, 17(10), 2228.
Sumra, I. A., Hasbullah, H. B., & AbManan, J. L. B. (2015). Attacks on security goals (confidentiality, integrity, availability) in
VANET: a survey. In Vehicular Ad-Hoc Networks for Smart Cities (pp. 51-61). Springer, Singapore.
Tchernykh, A., Schwiegelsohn, U., Talbi, E. G., & Babenko, M. (2016). Towards understanding uncertainty in cloud computing with
risks of confidentiality, integrity, and availability. Journal of Computational Science.
REFERENCES
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015). Biometric authentication on iphone and
android: Usability, perceptions, and influences on adoption. Proc. USEC, 1-2.
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack: an evaluation methodology and
lessons learned. IEEE Signal Processing Magazine, 32(5), 20-30.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver environment. IEEE Systems Journal, 9(3),
816-823.
Pinto, J. R., Cardoso, J. S., Lourenço, A., & Carreiras, C. (2017). Towards a Continuous Biometric System Based on ECG Signals
Acquired on the Steering Wheel. Sensors, 17(10), 2228.
Sumra, I. A., Hasbullah, H. B., & AbManan, J. L. B. (2015). Attacks on security goals (confidentiality, integrity, availability) in
VANET: a survey. In Vehicular Ad-Hoc Networks for Smart Cities (pp. 51-61). Springer, Singapore.
Tchernykh, A., Schwiegelsohn, U., Talbi, E. G., & Babenko, M. (2016). Towards understanding uncertainty in cloud computing with
risks of confidentiality, integrity, and availability. Journal of Computational Science.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




