An Analysis of Ethical Issues within the Internet of Things
VerifiedAdded on 2020/03/16
|11
|2668
|43
Report
AI Summary
This report delves into the ethical dimensions of the Internet of Things (IoT), a rapidly evolving technology with significant implications for modern society. It begins with an overview of IoT, defining its characteristics, and then explores its architecture, outlining the various layers and components involved in data flow and processing. The core of the report focuses on the ethical issues arising from the widespread adoption of IoT, including data privacy, security concerns, data management challenges, and issues related to equal access and heavy reliance on these technologies. A detailed case study of the CloudPets data breach is presented, illustrating the real-world consequences of these ethical lapses. The report concludes by summarizing the key ethical challenges and the need for robust policies and security measures to mitigate the risks associated with IoT.

Internet Of Things
Ethical issues
Ethical issues
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The Internet of things is the most significant technology of current era. It is revolving around the
Internet and other networks (wired or wireless). It is considered as the most promising technology for
research work in universities. The invention of smart devices has increased this research focus in recent
years. Although IoT provides a very efficient and smart life to consumers but it has various security
concerns as well. In this report we are going to discuss the concept of IoT, its characteristics,
architecture and the ethical issues. We will also discuss one case study of Teddy bear leaked ethical
issue in the upcoming sector of report.
Table of Contents
Abstract.......................................................................................................................................................1
Introduction.................................................................................................................................................1
Topic description.........................................................................................................................................2
IOT Architecture..........................................................................................................................................2
Ethical Issues...............................................................................................................................................4
Ethical challenges in IoT..............................................................................................................................6
Case study: Teddy Bear Leaked 2................................................................................................................6
Conclusion...................................................................................................................................................8
Introduction
Internet of things is the network or combination of physical devices, or any other machines
those are co-related with software, sensors, electronic devices, actuators etc. that enables the
systems involved to combine the data all together and share it all along for a better functioning.
IOT permits the objects to be controlled with the help of sensors across existing network
system that enables it to create the base for more integration of the computer-based
integrated world, and this all results in effective efficiency, accuracy along with a major
reduction of human involvement. When IOT is linked with the use of actuators and sensors, this
all becomes a form for more general class of cyber physical systems that also initiates the
technologies as like smart grids, smart phones or power plants (Song, 2013). Each of these
1
The Internet of things is the most significant technology of current era. It is revolving around the
Internet and other networks (wired or wireless). It is considered as the most promising technology for
research work in universities. The invention of smart devices has increased this research focus in recent
years. Although IoT provides a very efficient and smart life to consumers but it has various security
concerns as well. In this report we are going to discuss the concept of IoT, its characteristics,
architecture and the ethical issues. We will also discuss one case study of Teddy bear leaked ethical
issue in the upcoming sector of report.
Table of Contents
Abstract.......................................................................................................................................................1
Introduction.................................................................................................................................................1
Topic description.........................................................................................................................................2
IOT Architecture..........................................................................................................................................2
Ethical Issues...............................................................................................................................................4
Ethical challenges in IoT..............................................................................................................................6
Case study: Teddy Bear Leaked 2................................................................................................................6
Conclusion...................................................................................................................................................8
Introduction
Internet of things is the network or combination of physical devices, or any other machines
those are co-related with software, sensors, electronic devices, actuators etc. that enables the
systems involved to combine the data all together and share it all along for a better functioning.
IOT permits the objects to be controlled with the help of sensors across existing network
system that enables it to create the base for more integration of the computer-based
integrated world, and this all results in effective efficiency, accuracy along with a major
reduction of human involvement. When IOT is linked with the use of actuators and sensors, this
all becomes a form for more general class of cyber physical systems that also initiates the
technologies as like smart grids, smart phones or power plants (Song, 2013). Each of these
1

things can be identified with a unique perception with the help of the whole computer
embedded network but it is able to operate internally with in the present internet network. It is
being estimated that IOT may consist of 30 billion objects by 2020.
IOT is expected to provide advanced connectivity of systems and services that will be
beyond the communication network of machine to machine, and most probably will cover a
large variety of domains. The internal communication of these devices is much more expected
to move towards automation in nearly all the sectors of network system, as they also provides
the base for advanced networks and applications like smart grids and smart cities (Saied, 2013).
In IOT sense, most of the “things” can be defined to a variety of devices such as implants for
monitoring, biochips on animals for the need of farming and also their tracing, advanced
automobiles with in-built sensors. So, the “things” can also be defined as the incredible mixture
of hardware, data services along with the perfect use of accurate software.
These devices combine the useful informations or data with the help of various advanced
systems and technologies so as to make the data flow among the devices, with an ease.
Topic description
IoT is the most revolutionary technology in which the most important thing is its data. To
establish the fundamental layout of its infrastructure in real life, it is important to plan the
architecture of IoT. The architecture can be considered as the blueprint or layout which
represents the flow of data and processing in various stages at different layers of IoT.
IOT Architecture
Sooner or later every organization must need the planning about architecture of IOT (Sarangi,
2017). The four stages of IOT architecture consists of following 4 major layers or stages:
Stage 1: consists of all the devices, sensors and actuators which are involved in the IOT.
These devices may be wired or wireless. Sensors collect data from surroundings and
convert it into useful information.
2
embedded network but it is able to operate internally with in the present internet network. It is
being estimated that IOT may consist of 30 billion objects by 2020.
IOT is expected to provide advanced connectivity of systems and services that will be
beyond the communication network of machine to machine, and most probably will cover a
large variety of domains. The internal communication of these devices is much more expected
to move towards automation in nearly all the sectors of network system, as they also provides
the base for advanced networks and applications like smart grids and smart cities (Saied, 2013).
In IOT sense, most of the “things” can be defined to a variety of devices such as implants for
monitoring, biochips on animals for the need of farming and also their tracing, advanced
automobiles with in-built sensors. So, the “things” can also be defined as the incredible mixture
of hardware, data services along with the perfect use of accurate software.
These devices combine the useful informations or data with the help of various advanced
systems and technologies so as to make the data flow among the devices, with an ease.
Topic description
IoT is the most revolutionary technology in which the most important thing is its data. To
establish the fundamental layout of its infrastructure in real life, it is important to plan the
architecture of IoT. The architecture can be considered as the blueprint or layout which
represents the flow of data and processing in various stages at different layers of IoT.
IOT Architecture
Sooner or later every organization must need the planning about architecture of IOT (Sarangi,
2017). The four stages of IOT architecture consists of following 4 major layers or stages:
Stage 1: consists of all the devices, sensors and actuators which are involved in the IOT.
These devices may be wired or wireless. Sensors collect data from surroundings and
convert it into useful information.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
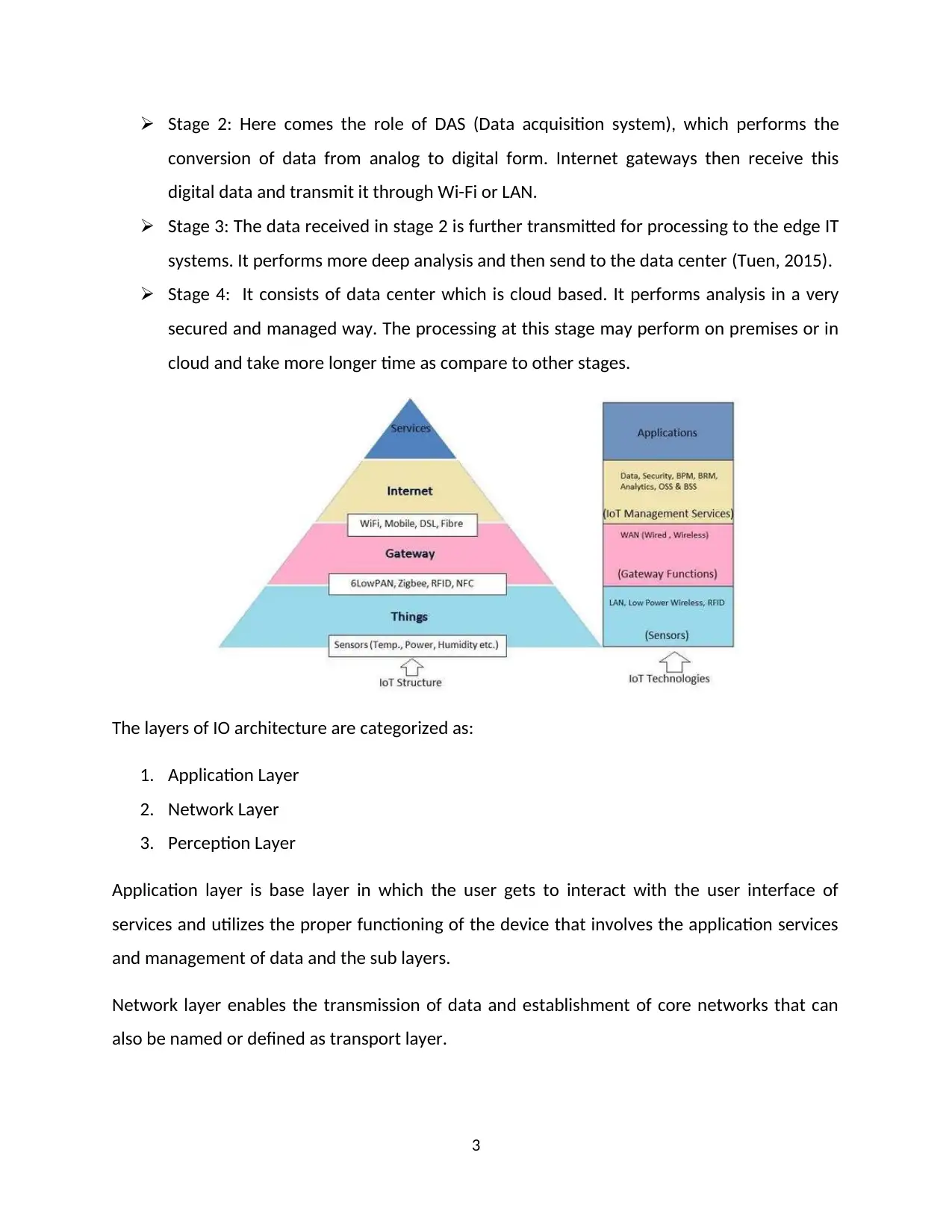
Stage 2: Here comes the role of DAS (Data acquisition system), which performs the
conversion of data from analog to digital form. Internet gateways then receive this
digital data and transmit it through Wi-Fi or LAN.
Stage 3: The data received in stage 2 is further transmitted for processing to the edge IT
systems. It performs more deep analysis and then send to the data center (Tuen, 2015).
Stage 4: It consists of data center which is cloud based. It performs analysis in a very
secured and managed way. The processing at this stage may perform on premises or in
cloud and take more longer time as compare to other stages.
The layers of IO architecture are categorized as:
1. Application Layer
2. Network Layer
3. Perception Layer
Application layer is base layer in which the user gets to interact with the user interface of
services and utilizes the proper functioning of the device that involves the application services
and management of data and the sub layers.
Network layer enables the transmission of data and establishment of core networks that can
also be named or defined as transport layer.
3
conversion of data from analog to digital form. Internet gateways then receive this
digital data and transmit it through Wi-Fi or LAN.
Stage 3: The data received in stage 2 is further transmitted for processing to the edge IT
systems. It performs more deep analysis and then send to the data center (Tuen, 2015).
Stage 4: It consists of data center which is cloud based. It performs analysis in a very
secured and managed way. The processing at this stage may perform on premises or in
cloud and take more longer time as compare to other stages.
The layers of IO architecture are categorized as:
1. Application Layer
2. Network Layer
3. Perception Layer
Application layer is base layer in which the user gets to interact with the user interface of
services and utilizes the proper functioning of the device that involves the application services
and management of data and the sub layers.
Network layer enables the transmission of data and establishment of core networks that can
also be named or defined as transport layer.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Perception layer provides the base for the gathering or collection of data in which the camera,
RFID and sensors together gets to operate along the physical environment.
Ethical Issues
The most innovative technology of current era is Internet of things, which we can see in form of
remarkable advancement in communication over the internet. If we analyze the present scenario, we
can say that without this concept we cannot use the information technology to continue our daily
routines works also. Using IoT we can use our physical devices merged with digital information. From
the door locks, home appliances, cameras, medical devices, network based hardware and transportation
to smart toys, we can see the impact of Internet of things in almost every sphere of our life (Covert,
2014). The data generated by using the IoT concepts are increasing day by day and can be accessible
across a wide range of people and applications. Most of the organizations are now moving to adopt IoT
technique for better decision making capability, allocation of resources and providing services 24x7
hours of a day. In this way the IoT became the part of our life nowadays.
The enormous use of IoT has created a new channel for hackers. The possibilities of data breaches is
expanding day by day. According to Maneesha Mithal (Federal trade commission associate director),
“ubiquitous data collection” at the user side is creating new privacy issues and data breaches and the
peta bytes of data is creating treasure for hackers.
In the opinion of Naomi Lefkowitz (privacy policy advisor at National institute of standards and
technology), “There is no perfect privacy” in the world of IoT. Right now there are no specific privacy
policy standards designed which can be implemented world-wide uniformly. The security concerns are
decided as per the companies and also resolved as per their legislations (Gunter, 2017).
Data Management
As many sensors are being attached in the system or installed to allow the smart and
better environment for user or for customer service, there also arise some of the issues
related to the management of high amount of data.
Communication
4
RFID and sensors together gets to operate along the physical environment.
Ethical Issues
The most innovative technology of current era is Internet of things, which we can see in form of
remarkable advancement in communication over the internet. If we analyze the present scenario, we
can say that without this concept we cannot use the information technology to continue our daily
routines works also. Using IoT we can use our physical devices merged with digital information. From
the door locks, home appliances, cameras, medical devices, network based hardware and transportation
to smart toys, we can see the impact of Internet of things in almost every sphere of our life (Covert,
2014). The data generated by using the IoT concepts are increasing day by day and can be accessible
across a wide range of people and applications. Most of the organizations are now moving to adopt IoT
technique for better decision making capability, allocation of resources and providing services 24x7
hours of a day. In this way the IoT became the part of our life nowadays.
The enormous use of IoT has created a new channel for hackers. The possibilities of data breaches is
expanding day by day. According to Maneesha Mithal (Federal trade commission associate director),
“ubiquitous data collection” at the user side is creating new privacy issues and data breaches and the
peta bytes of data is creating treasure for hackers.
In the opinion of Naomi Lefkowitz (privacy policy advisor at National institute of standards and
technology), “There is no perfect privacy” in the world of IoT. Right now there are no specific privacy
policy standards designed which can be implemented world-wide uniformly. The security concerns are
decided as per the companies and also resolved as per their legislations (Gunter, 2017).
Data Management
As many sensors are being attached in the system or installed to allow the smart and
better environment for user or for customer service, there also arise some of the issues
related to the management of high amount of data.
Communication
4

In IoT the devices may communicate to alert people about their surroundings. The data
to be transmitted would be in form of signals and must be converted into
understandable format so that it can be analysed. This data while traversed can be on
high risk, it can be captured and manipulated by unauthorized persons in transit.
Data Breach
Breaching of data is a very common problem in the IT sector, as the huge amount of
physical data, sensor nodes are installed into the whole network system, it increases the
concern of data safety on a large scale.
Security Issues
In the increasing IT age, we are having all our best to obtain the best and everything in a
much smart way. Sensors of different kinds are being setup on electronic devices. This
whole new era of digitalization needs a similar level of security to safeguard the
informations being used in the whole network according to the different intentions that
they would play.
Equal Access Issues
The major code in IT sector of ethics is to treat all equally, without any discrimination,
but the reality is that there are various sectors that can’t access the internet, and also
do not mention to connect all types of physical devices. We can easily note that the
developed countries are ethical enough, but the ones who are unethical in this sector
are not able to share the same kind of resources.
Heavy Reliance Issue
With the growth, the electronic devices have become a significant part of our lives. The
trend of IOT seems to be unavoidable, many of the organizations and working systems
also implement the trend of IOT to have a perfect decision making environment.
Government is also analyzing the data collection from the means of wireless sensors and
smart devices to allocate and manage their resources in a much perfect manner.
This shows that how much we are dependent on the base of internet of things, in a way we can
also say that we have taken a very big step to become a part of IOT network and make
ourselves a part of a new era of modernization and digitalization.
5
to be transmitted would be in form of signals and must be converted into
understandable format so that it can be analysed. This data while traversed can be on
high risk, it can be captured and manipulated by unauthorized persons in transit.
Data Breach
Breaching of data is a very common problem in the IT sector, as the huge amount of
physical data, sensor nodes are installed into the whole network system, it increases the
concern of data safety on a large scale.
Security Issues
In the increasing IT age, we are having all our best to obtain the best and everything in a
much smart way. Sensors of different kinds are being setup on electronic devices. This
whole new era of digitalization needs a similar level of security to safeguard the
informations being used in the whole network according to the different intentions that
they would play.
Equal Access Issues
The major code in IT sector of ethics is to treat all equally, without any discrimination,
but the reality is that there are various sectors that can’t access the internet, and also
do not mention to connect all types of physical devices. We can easily note that the
developed countries are ethical enough, but the ones who are unethical in this sector
are not able to share the same kind of resources.
Heavy Reliance Issue
With the growth, the electronic devices have become a significant part of our lives. The
trend of IOT seems to be unavoidable, many of the organizations and working systems
also implement the trend of IOT to have a perfect decision making environment.
Government is also analyzing the data collection from the means of wireless sensors and
smart devices to allocate and manage their resources in a much perfect manner.
This shows that how much we are dependent on the base of internet of things, in a way we can
also say that we have taken a very big step to become a part of IOT network and make
ourselves a part of a new era of modernization and digitalization.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ethical challenges in IoT
According to Valacich and Schneider, the ethical issues in Internet of things can be
classified on the basis of their accessibility, privacy and accuracy of data. It may be of
following types:
The issues related with right of information
Issues related with the integrity of information
Issues related with personal information
Issues related with the accessibility of information
Ethical issues in IoT
Case study: Teddy Bear Leaked 2
There are so many examples available of ethical issues in Internet of things. One of the event
was of Teddy Bear issue, in which a smart teddy bear selling company involved in the sending of
emotional messages among kids and their parents, hacked near about 800,000 accounts of
users. This ethical attack locked the user accounts and demanded for ransom (Franceschi-
Bicchierai, 2017). The users were also sending the messages in form of recording to express
their emotional feelings. In this attack the messages of users were exposed publically so that
everyone was able to view and listen these messages. This breach was called as CloudPets data
breach (Forrest, 2017). This ethical event was firstly reported by Troy Hunt, who was specialist
of security and cloud at Microsoft. CloudPets was using MongoDB as backend. The main
problem with this database was that it is publically open and there is no requirement of
authentication credentials.
6
According to Valacich and Schneider, the ethical issues in Internet of things can be
classified on the basis of their accessibility, privacy and accuracy of data. It may be of
following types:
The issues related with right of information
Issues related with the integrity of information
Issues related with personal information
Issues related with the accessibility of information
Ethical issues in IoT
Case study: Teddy Bear Leaked 2
There are so many examples available of ethical issues in Internet of things. One of the event
was of Teddy Bear issue, in which a smart teddy bear selling company involved in the sending of
emotional messages among kids and their parents, hacked near about 800,000 accounts of
users. This ethical attack locked the user accounts and demanded for ransom (Franceschi-
Bicchierai, 2017). The users were also sending the messages in form of recording to express
their emotional feelings. In this attack the messages of users were exposed publically so that
everyone was able to view and listen these messages. This breach was called as CloudPets data
breach (Forrest, 2017). This ethical event was firstly reported by Troy Hunt, who was specialist
of security and cloud at Microsoft. CloudPets was using MongoDB as backend. The main
problem with this database was that it is publically open and there is no requirement of
authentication credentials.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
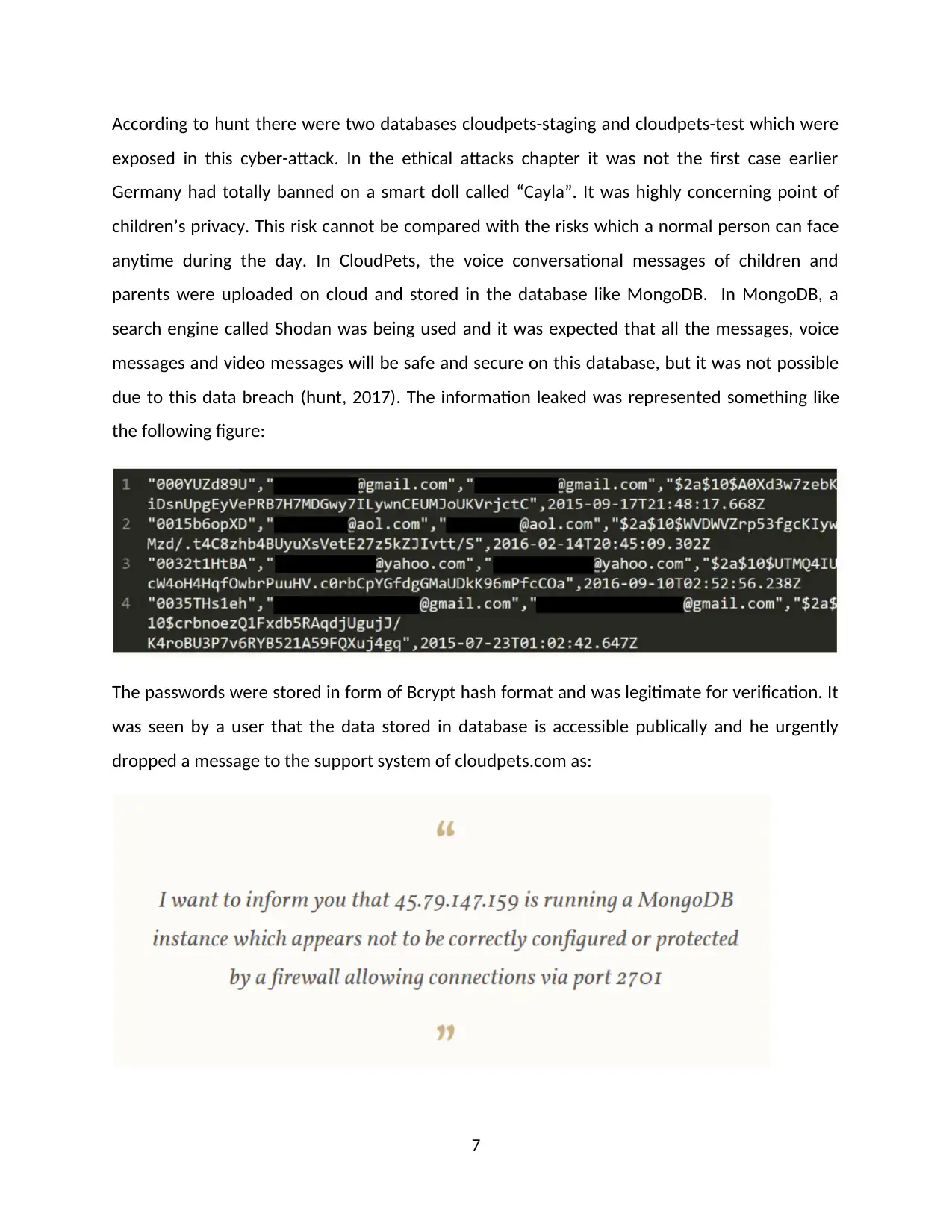
According to hunt there were two databases cloudpets-staging and cloudpets-test which were
exposed in this cyber-attack. In the ethical attacks chapter it was not the first case earlier
Germany had totally banned on a smart doll called “Cayla”. It was highly concerning point of
children’s privacy. This risk cannot be compared with the risks which a normal person can face
anytime during the day. In CloudPets, the voice conversational messages of children and
parents were uploaded on cloud and stored in the database like MongoDB. In MongoDB, a
search engine called Shodan was being used and it was expected that all the messages, voice
messages and video messages will be safe and secure on this database, but it was not possible
due to this data breach (hunt, 2017). The information leaked was represented something like
the following figure:
The passwords were stored in form of Bcrypt hash format and was legitimate for verification. It
was seen by a user that the data stored in database is accessible publically and he urgently
dropped a message to the support system of cloudpets.com as:
7
exposed in this cyber-attack. In the ethical attacks chapter it was not the first case earlier
Germany had totally banned on a smart doll called “Cayla”. It was highly concerning point of
children’s privacy. This risk cannot be compared with the risks which a normal person can face
anytime during the day. In CloudPets, the voice conversational messages of children and
parents were uploaded on cloud and stored in the database like MongoDB. In MongoDB, a
search engine called Shodan was being used and it was expected that all the messages, voice
messages and video messages will be safe and secure on this database, but it was not possible
due to this data breach (hunt, 2017). The information leaked was represented something like
the following figure:
The passwords were stored in form of Bcrypt hash format and was legitimate for verification. It
was seen by a user that the data stored in database is accessible publically and he urgently
dropped a message to the support system of cloudpets.com as:
7
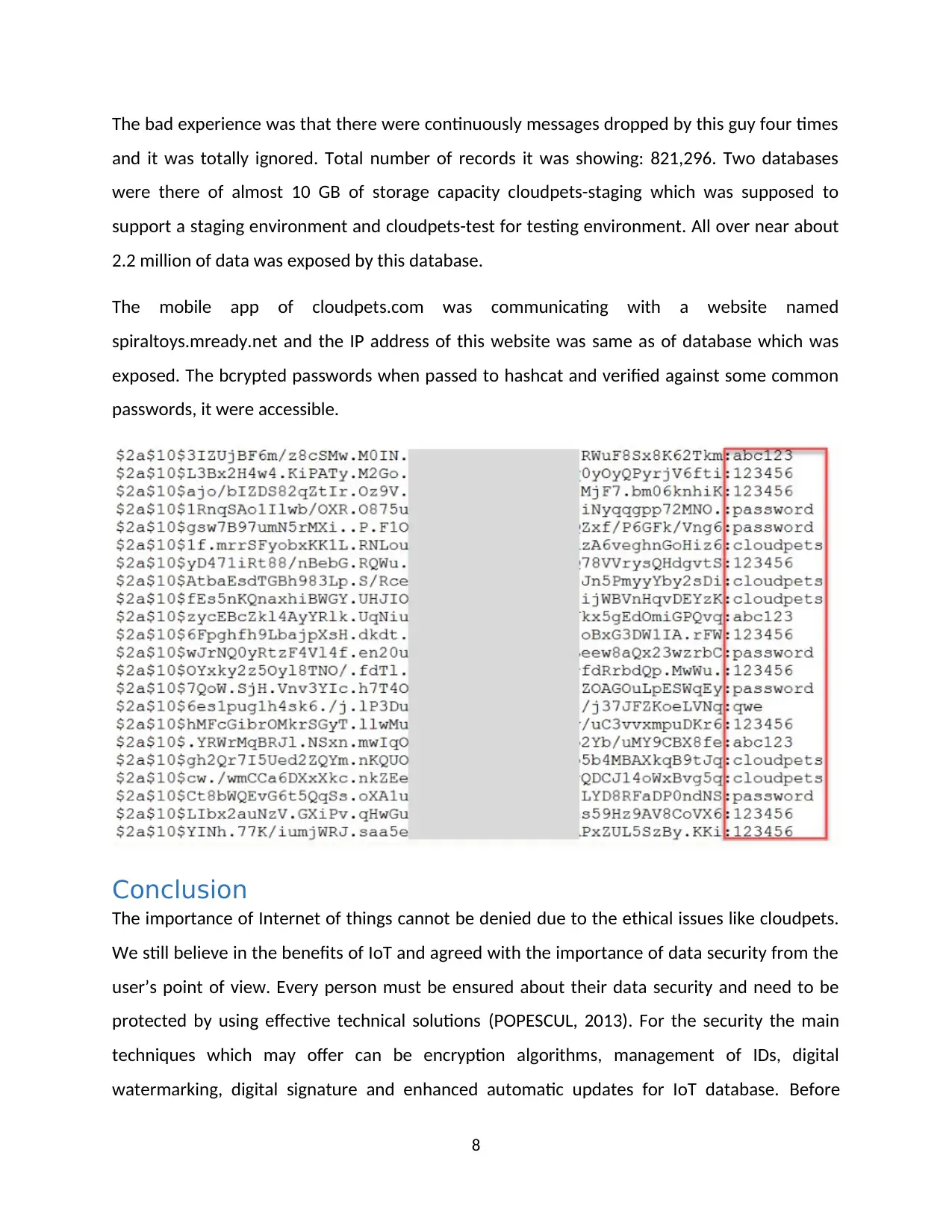
The bad experience was that there were continuously messages dropped by this guy four times
and it was totally ignored. Total number of records it was showing: 821,296. Two databases
were there of almost 10 GB of storage capacity cloudpets-staging which was supposed to
support a staging environment and cloudpets-test for testing environment. All over near about
2.2 million of data was exposed by this database.
The mobile app of cloudpets.com was communicating with a website named
spiraltoys.mready.net and the IP address of this website was same as of database which was
exposed. The bcrypted passwords when passed to hashcat and verified against some common
passwords, it were accessible.
Conclusion
The importance of Internet of things cannot be denied due to the ethical issues like cloudpets.
We still believe in the benefits of IoT and agreed with the importance of data security from the
user’s point of view. Every person must be ensured about their data security and need to be
protected by using effective technical solutions (POPESCUL, 2013). For the security the main
techniques which may offer can be encryption algorithms, management of IDs, digital
watermarking, digital signature and enhanced automatic updates for IoT database. Before
8
and it was totally ignored. Total number of records it was showing: 821,296. Two databases
were there of almost 10 GB of storage capacity cloudpets-staging which was supposed to
support a staging environment and cloudpets-test for testing environment. All over near about
2.2 million of data was exposed by this database.
The mobile app of cloudpets.com was communicating with a website named
spiraltoys.mready.net and the IP address of this website was same as of database which was
exposed. The bcrypted passwords when passed to hashcat and verified against some common
passwords, it were accessible.
Conclusion
The importance of Internet of things cannot be denied due to the ethical issues like cloudpets.
We still believe in the benefits of IoT and agreed with the importance of data security from the
user’s point of view. Every person must be ensured about their data security and need to be
protected by using effective technical solutions (POPESCUL, 2013). For the security the main
techniques which may offer can be encryption algorithms, management of IDs, digital
watermarking, digital signature and enhanced automatic updates for IoT database. Before
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

installing any app regarding IoT, both parties must accept some pre-defined legal terms, the
accessibility scope of information, code of conduct and economic measures. By following these
steps of awareness, the issues in IoT can be easily resolved in future.
References
Covert, E., 2014. ethical-challenges-of-the-internet-of-things. [Online]
Available at: https://www.scmagazine.com/ethical-challenges-of-the-internet-of-things/article/538993/
[Accessed 12 October 2017].
Forrest, C., 2017. iot-connected-teddy-bear-leaks-millions-of-kids-conversations-exposed-database-to-
blame. [Online]
Available at: http://www.techrepublic.com/article/iot-connected-teddy-bear-leaks-millions-of-kids-
conversations-exposed-database-to-blame/
[Accessed 11 October 2017].
Franceschi-Bicchierai, L., 2017. internet-of-things-teddy-bear-leaked-2-million-parent-and-kids-message-
recordings. [Online]
Available at: https://motherboard.vice.com/en_us/article/pgwean/internet-of-things-teddy-bear-
leaked-2-million-parent-and-kids-message-recordings
[Accessed 11 October 2017].
Gunter, C., 2017. iot-security-data-gunter. [Online]
Available at: https://fcw.com/articles/2017/05/11/iot-security-data-gunter.aspx
[Accessed 12 october 2017].
hunt, T., 2017. data-from-connected-cloudpets-teddy-bears-leaked-and-ransomed-exposing-kids-voice-
messages. [Online]
Available at: https://www.troyhunt.com/data-from-connected-cloudpets-teddy-bears-leaked-and-
ransomed-exposing-kids-voice-messages/
[Accessed 12 October 2017].
POPESCUL, D., 2013. INTERNET OF THINGS – SOME ETHICAL ISSUES. The USV Annals, 13(2(18)), p. 7.
Saied, Y. B., 2013. halshs.archives-ouvertes.fr. [Online]
Available at: https://halshs.archives-ouvertes.fr/tel-00879790/document
[Accessed 12 October 2017].
Sarangi, P. S. a. S. R., 2017. Internet of Things: Architectures, Protocols, and Applications. Journal of
Electrical and Computer Engineering, 2017(150), p. 25.
Song, Y., 2013. metalab.uniten.edu.my. [Online]
Available at: http://metalab.uniten.edu.my/~azie/AllArt/13010%20-%202014%20-%20Yuanjun%20Song
%20-%20Security%20in%20Internet%20of%20Things%20(MASTER%20Thesis).pdf
[Accessed 12 october 2017].
9
accessibility scope of information, code of conduct and economic measures. By following these
steps of awareness, the issues in IoT can be easily resolved in future.
References
Covert, E., 2014. ethical-challenges-of-the-internet-of-things. [Online]
Available at: https://www.scmagazine.com/ethical-challenges-of-the-internet-of-things/article/538993/
[Accessed 12 October 2017].
Forrest, C., 2017. iot-connected-teddy-bear-leaks-millions-of-kids-conversations-exposed-database-to-
blame. [Online]
Available at: http://www.techrepublic.com/article/iot-connected-teddy-bear-leaks-millions-of-kids-
conversations-exposed-database-to-blame/
[Accessed 11 October 2017].
Franceschi-Bicchierai, L., 2017. internet-of-things-teddy-bear-leaked-2-million-parent-and-kids-message-
recordings. [Online]
Available at: https://motherboard.vice.com/en_us/article/pgwean/internet-of-things-teddy-bear-
leaked-2-million-parent-and-kids-message-recordings
[Accessed 11 October 2017].
Gunter, C., 2017. iot-security-data-gunter. [Online]
Available at: https://fcw.com/articles/2017/05/11/iot-security-data-gunter.aspx
[Accessed 12 october 2017].
hunt, T., 2017. data-from-connected-cloudpets-teddy-bears-leaked-and-ransomed-exposing-kids-voice-
messages. [Online]
Available at: https://www.troyhunt.com/data-from-connected-cloudpets-teddy-bears-leaked-and-
ransomed-exposing-kids-voice-messages/
[Accessed 12 October 2017].
POPESCUL, D., 2013. INTERNET OF THINGS – SOME ETHICAL ISSUES. The USV Annals, 13(2(18)), p. 7.
Saied, Y. B., 2013. halshs.archives-ouvertes.fr. [Online]
Available at: https://halshs.archives-ouvertes.fr/tel-00879790/document
[Accessed 12 October 2017].
Sarangi, P. S. a. S. R., 2017. Internet of Things: Architectures, Protocols, and Applications. Journal of
Electrical and Computer Engineering, 2017(150), p. 25.
Song, Y., 2013. metalab.uniten.edu.my. [Online]
Available at: http://metalab.uniten.edu.my/~azie/AllArt/13010%20-%202014%20-%20Yuanjun%20Song
%20-%20Security%20in%20Internet%20of%20Things%20(MASTER%20Thesis).pdf
[Accessed 12 october 2017].
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Tuen, C. D., 2015. brage.bibsys.no. [Online]
Available at: https://brage.bibsys.no/xmlui/bitstream/handle/11250/2352738/12892_FULLTEXT.pdf?
sequence=1&isAllowed=y
[Accessed 12 october 2017].
10
Available at: https://brage.bibsys.no/xmlui/bitstream/handle/11250/2352738/12892_FULLTEXT.pdf?
sequence=1&isAllowed=y
[Accessed 12 october 2017].
10
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





