Self-Service Kiosks: Analyzing the Checkout Process for Libraries
VerifiedAdded on 2022/08/11
|7
|837
|15
Report
AI Summary
This report analyzes the implementation of self-service kiosks in libraries, focusing on the checkout process and adherence to rules such as limiting checked-out items and managing fines. It includes an activity diagram illustrating the checkout process and discusses the pros and cons of in-house versus off-the-shelf software development, recommending in-house development for customization. The report also addresses ethical, legal, and cultural issues, such as job displacement and accessibility for all users, suggesting solutions like providing guidance for kiosk usage. It concludes that libraries should consider these factors to ensure a smooth and ethical transition to automated systems.

Running head: SELF-SERVICE KIOSK
SELF-SERVICE KIOSK
Name of student
Name of university
Author’s note:
SELF-SERVICE KIOSK
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
SELF-SERVICE KIOSK
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................3
Activity diagram.........................................................................................................3
In house and off-the-shelf software development......................................................4
Ethical, legal and cultural issues................................................................................4
Conclusion......................................................................................................................5
Reference........................................................................................................................6
SELF-SERVICE KIOSK
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................3
Activity diagram.........................................................................................................3
In house and off-the-shelf software development......................................................4
Ethical, legal and cultural issues................................................................................4
Conclusion......................................................................................................................5
Reference........................................................................................................................6

2
SELF-SERVICE KIOSK
Introduction
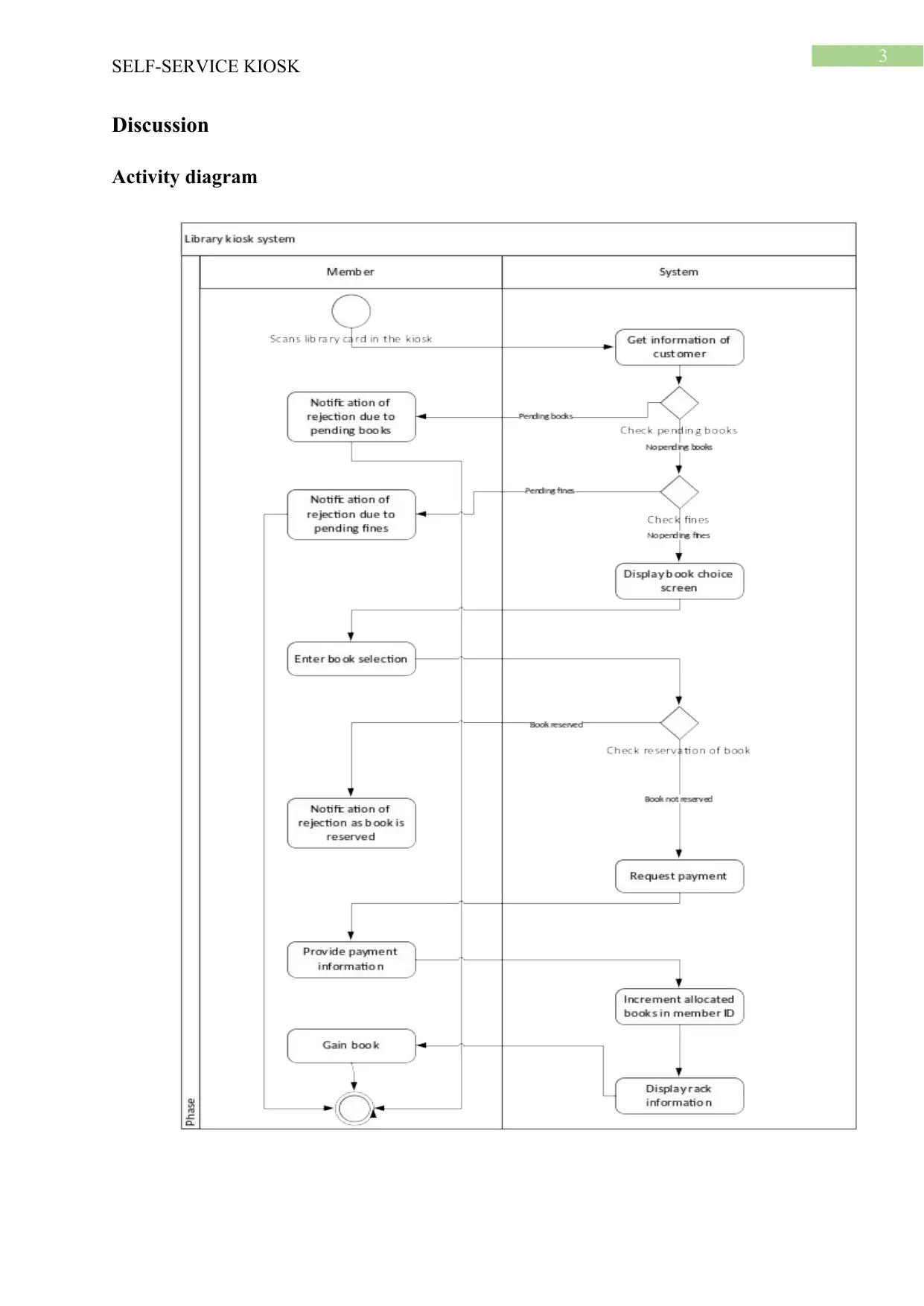
The technological developments in the various sectors of the modern world has led to
the introduction of automation that could be helpful for eliminating the manual processes.
The kiosk checkout process helps the libraries in introducing automation is allowing the
member to gain books. The members could enter their choice of books in the kiosk and then
make the payment in the kiosk. If all the details of the member is valid and the people have
no outstanding balance against their name then the kiosk would direct the member to the
appropriate rack where the book has been placed.
SELF-SERVICE KIOSK
Introduction
The technological developments in the various sectors of the modern world has led to
the introduction of automation that could be helpful for eliminating the manual processes.
The kiosk checkout process helps the libraries in introducing automation is allowing the
member to gain books. The members could enter their choice of books in the kiosk and then
make the payment in the kiosk. If all the details of the member is valid and the people have
no outstanding balance against their name then the kiosk would direct the member to the
appropriate rack where the book has been placed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
SELF-SERVICE KIOSK
Discussion
Activity diagram
SELF-SERVICE KIOSK
Discussion
Activity diagram
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
SELF-SERVICE KIOSK
In house and off-the-shelf software development
The library could build their software product in-house with the help of the internal
development team. It entails the procedure of sourcing, attracting, as well as recruiting the
software developers (Abrahamsson, Pekka, et al 1). The in-house software development
provides the opportunity of quickly changing the features of the product, add some new
features, and appropriate assess the technical background. The errors and bugs would be dealt
with the internal teams faster and easily.
The main disadvantage of developing the application in-house is the significantly high
costs, difficulty in searching the skilled IT experts, and the increased staff turnover
(Lindsjørn, Yngve, et al. 275).
Off-the-shelf software could be described as the software that is ready for using right
from beginning. Off the shelf software is primarily significantly cheaper than the in-house
developed software. The support for the Off the shelf software is easily available and the
employees of the organisation could be properly guided in using the software easily (Hoda,
Rashina, et al. 62).
The main disadvantage of using the Off the shelf software is that is does not provide
the facility of modifying the software according to the current needs. The organisation needs
to use the software just as developed and purchased.
Ethical, legal and cultural issues
The main ethical issue with the kiosk in the present times is that is leads to the loss of
jobs in the organisation where it has been placed. The automation of the checkout process
would allow the company to sack significantly huge number of employees and employ
people for maintenance of kiosks (He, Danping, et al 503). If the kiosk placed in the library
does not follow the proper license and the legal boundaries of using the automation systems,
SELF-SERVICE KIOSK
In house and off-the-shelf software development
The library could build their software product in-house with the help of the internal
development team. It entails the procedure of sourcing, attracting, as well as recruiting the
software developers (Abrahamsson, Pekka, et al 1). The in-house software development
provides the opportunity of quickly changing the features of the product, add some new
features, and appropriate assess the technical background. The errors and bugs would be dealt
with the internal teams faster and easily.
The main disadvantage of developing the application in-house is the significantly high
costs, difficulty in searching the skilled IT experts, and the increased staff turnover
(Lindsjørn, Yngve, et al. 275).
Off-the-shelf software could be described as the software that is ready for using right
from beginning. Off the shelf software is primarily significantly cheaper than the in-house
developed software. The support for the Off the shelf software is easily available and the
employees of the organisation could be properly guided in using the software easily (Hoda,
Rashina, et al. 62).
The main disadvantage of using the Off the shelf software is that is does not provide
the facility of modifying the software according to the current needs. The organisation needs
to use the software just as developed and purchased.
Ethical, legal and cultural issues
The main ethical issue with the kiosk in the present times is that is leads to the loss of
jobs in the organisation where it has been placed. The automation of the checkout process
would allow the company to sack significantly huge number of employees and employ
people for maintenance of kiosks (He, Danping, et al 503). If the kiosk placed in the library
does not follow the proper license and the legal boundaries of using the automation systems,

5
SELF-SERVICE KIOSK
it could rise in legal issues (Luse, Andrew W., et al 1). The main cultural issues associated
with the kiosk in the library is that there might be some individuals who might not be able to
use the kiosk properly, for instance any senior citizen might not be able to use the system
appropriately and would not be able get their desired book without proper assistance (Tüzün
et al 74).
Conclusion
Therefore, it could be concluded from above discussion that the introduction of the
kiosk in the library should be done by developing the software in-house. It would allow the
company to make any required modifications in the system. The ethical issues should be
considered by the library and proper guidance of using the kiosk should be placed near the
kiosk so that any individual facing any difficulty in using the system should take required
guidance.
SELF-SERVICE KIOSK
it could rise in legal issues (Luse, Andrew W., et al 1). The main cultural issues associated
with the kiosk in the library is that there might be some individuals who might not be able to
use the kiosk properly, for instance any senior citizen might not be able to use the system
appropriately and would not be able get their desired book without proper assistance (Tüzün
et al 74).
Conclusion
Therefore, it could be concluded from above discussion that the introduction of the
kiosk in the library should be done by developing the software in-house. It would allow the
company to make any required modifications in the system. The ethical issues should be
considered by the library and proper guidance of using the kiosk should be placed near the
kiosk so that any individual facing any difficulty in using the system should take required
guidance.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
SELF-SERVICE KIOSK
Reference
Abrahamsson, Pekka, et al. "Agile software development methods: Review and
analysis." arXiv preprint arXiv:1709.08439 (2017).
He, Danping, et al. "Stochastic channel modeling for kiosk applications in the terahertz
band." IEEE Transactions on Terahertz Science and Technology 7.5 (2017): 502-513.
Hoda, Rashina, et al. "Systematic literature reviews in agile software development: A tertiary
study." Information and Software Technology 85 (2017): 60-70.
Lindsjørn, Yngve, et al. "Teamwork quality and project success in software development: A
survey of agile development teams." Journal of Systems and Software 122 (2016): 274-286.
Luse, Andrew W., et al. "A Location-based Approach for Distributed Kiosk Design." arXiv
preprint arXiv:1803.05993 (2018).
Tüzün, Hakan, Esra Telli, and Arman Alır. "Usability testing of a 3D touch screen kiosk
system for way-finding." computers in human behavior 61 (2016): 73-79.
SELF-SERVICE KIOSK
Reference
Abrahamsson, Pekka, et al. "Agile software development methods: Review and
analysis." arXiv preprint arXiv:1709.08439 (2017).
He, Danping, et al. "Stochastic channel modeling for kiosk applications in the terahertz
band." IEEE Transactions on Terahertz Science and Technology 7.5 (2017): 502-513.
Hoda, Rashina, et al. "Systematic literature reviews in agile software development: A tertiary
study." Information and Software Technology 85 (2017): 60-70.
Lindsjørn, Yngve, et al. "Teamwork quality and project success in software development: A
survey of agile development teams." Journal of Systems and Software 122 (2016): 274-286.
Luse, Andrew W., et al. "A Location-based Approach for Distributed Kiosk Design." arXiv
preprint arXiv:1803.05993 (2018).
Tüzün, Hakan, Esra Telli, and Arman Alır. "Usability testing of a 3D touch screen kiosk
system for way-finding." computers in human behavior 61 (2016): 73-79.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




