CIS4019-N IoT Security PDF
VerifiedAdded on 2021/09/09
|11
|2849
|120
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

IoT 1
INTERNET OF THINGS (IoT)
By (Student Name)
(Course)
(Tutor)
(University)
(City)
(Date)
INTERNET OF THINGS (IoT)
By (Student Name)
(Course)
(Tutor)
(University)
(City)
(Date)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IoT 2
Introduction
Airport management is mandated in handling baggage of the passengers. The current system is
said to have many issues with baggage, they are lots of complaints due to the increasing loss of baggage.
To sort out this problem, this paper will propose an IoT sensor system. First, the paper will give a detailed
design of the IoT system. Second, the paper will give a clear description of all the security aspects of the
IoT system and protection mechanism. Lastly, the paper will simulate the scenario
An outline of the IoT system
Internet of Things (IoT) is a system which has brought up a lot of benefits. The system has
employed the use of sensors which in turn has greatly improved speed and quality of the production
process. To be able to monitor the movement of a baggage, the IoT needs to be integrated with the cloud
platform so as to send a short message to the owner of baggage about the movement of their baggage.
IoT system lets people to attain a deeper automation, integration, and analysis within the system. The
system utilizes emerging and existing technology for robotics, sensing, and networking. Some of the key
features of IoT include connectivity, active management, small device use, and artificial intelligence.
With IoT, an organization is able to increase efficiency other advantages are improved customer
engagement, reduced waste, and enhanced data collection (Benabdellah, 2017).
A design of the IoT system
Hardware platform
To start with IoT hardware has four building blocks which as shown by figure one below
Introduction
Airport management is mandated in handling baggage of the passengers. The current system is
said to have many issues with baggage, they are lots of complaints due to the increasing loss of baggage.
To sort out this problem, this paper will propose an IoT sensor system. First, the paper will give a detailed
design of the IoT system. Second, the paper will give a clear description of all the security aspects of the
IoT system and protection mechanism. Lastly, the paper will simulate the scenario
An outline of the IoT system
Internet of Things (IoT) is a system which has brought up a lot of benefits. The system has
employed the use of sensors which in turn has greatly improved speed and quality of the production
process. To be able to monitor the movement of a baggage, the IoT needs to be integrated with the cloud
platform so as to send a short message to the owner of baggage about the movement of their baggage.
IoT system lets people to attain a deeper automation, integration, and analysis within the system. The
system utilizes emerging and existing technology for robotics, sensing, and networking. Some of the key
features of IoT include connectivity, active management, small device use, and artificial intelligence.
With IoT, an organization is able to increase efficiency other advantages are improved customer
engagement, reduced waste, and enhanced data collection (Benabdellah, 2017).
A design of the IoT system
Hardware platform
To start with IoT hardware has four building blocks which as shown by figure one below

IoT 3
Figure 1: Hardware building blocks (Welton, 2017)
The first building block which is thing is a set of an asset which that one desire to control. The
thing building block is integrated with a smart device. The second building block is the data acquisition
module, this focuses on converting the physical signal into digital signals which can then be handled by
the computer. This is the hardware part of the IoT system which include all the sensors which are
mandated in acquiring the real-world signals like motion and vibration. For this IoT, monitoring system
include 3 sensors. In addition to this, some of the considerations to make when coming up with this type
of IoT monitoring system are the signals that one need to measure, the number of sensors, how fast one
ought to measure the real-world signals, and the accuracy one need in the measurement (Gilchrist, 2016).
Third hardware building block as shown by figure one is the data processing module, this is the CPU part
which processes the data. It also performs native analytics. It also stores data and at the same time
performs any other computing operations. When coming up with IoT monitoring system it is very
important to consider the processing power and the amount of local data storage. The last module is the
communication module. This is the last device hardware module which enables communication with a
cloud platform. This module includes ports like a serial (232/485), USB, Modbus. It also include radio
technology for all wireless communications like WiFi, ZigBee, and LoRA.
For this case, the Airport ought to have 802.15.4 mote modules. This is a hardware platform
which will provide a broad portfolio for wireless modules. The reason as to why the gadget is best suited
for this case is that it provides a portfolio for all the wireless modules which enable the organization to
Figure 1: Hardware building blocks (Welton, 2017)
The first building block which is thing is a set of an asset which that one desire to control. The
thing building block is integrated with a smart device. The second building block is the data acquisition
module, this focuses on converting the physical signal into digital signals which can then be handled by
the computer. This is the hardware part of the IoT system which include all the sensors which are
mandated in acquiring the real-world signals like motion and vibration. For this IoT, monitoring system
include 3 sensors. In addition to this, some of the considerations to make when coming up with this type
of IoT monitoring system are the signals that one need to measure, the number of sensors, how fast one
ought to measure the real-world signals, and the accuracy one need in the measurement (Gilchrist, 2016).
Third hardware building block as shown by figure one is the data processing module, this is the CPU part
which processes the data. It also performs native analytics. It also stores data and at the same time
performs any other computing operations. When coming up with IoT monitoring system it is very
important to consider the processing power and the amount of local data storage. The last module is the
communication module. This is the last device hardware module which enables communication with a
cloud platform. This module includes ports like a serial (232/485), USB, Modbus. It also include radio
technology for all wireless communications like WiFi, ZigBee, and LoRA.
For this case, the Airport ought to have 802.15.4 mote modules. This is a hardware platform
which will provide a broad portfolio for wireless modules. The reason as to why the gadget is best suited
for this case is that it provides a portfolio for all the wireless modules which enable the organization to

IoT 4
meet the needs of the organization. The sensor board ought to be of Ds1000 which offers both direct
sensing connectivity and all the IoT sensor capabilities. In addition, the organization ought to go for
802.15.14 network infrastructure of type SG1100 which is able to provide gateway services and is able to
deal with the deployment of wireless sensor networks. The processor for this case ought to be Intel X86;
this type of processor is able to handle all the IoT monitoring system commands (Yarali, 2016).
Operating system
IoT operating system ought to perform better within constraints of IoT devices which includes
size, power, the processing capacity, and memory. There are various IoT OS which includes, Ubuntu
Core, Fuchsia OS, Linux based OS, and RIOT. Ubuntu core is a transactional version which made
specifically for IoT devices. Fuchsia OS; this type of IoT OS which is Google based. On the other hand,
RIOT is one of the open source OS which is specialized for all IoT devices.
For this case, this paper will go for Fuchsia type of operating System which is a cross-device
open source OS. It is an OS from Google which is able to run IoT equipment. The OS also has the ability
to run across the various platforms meaning that it cannot only run only on smartphones but it can also
run on tablets, digital monitors, Airport controls, desktops, and notebooks. One of the major reason this
paper has gone for Fuchsia OS is that it is integrated with Google assistant and the Google cloud
environment (Kurose & Ross, 2017).
Sensors and actuators
When making a decision on the types of sensors; one of the major considerations is the sensor
signal conditioning. It is either the sensor signal conditioning is integrated with micro-controllers or with
the sensor module package. Another consideration to make is power management. So as to select the best
component four major specifications that this scenario ought to consider which the needed intelligence is
that is required by the sensor node; this ought to dictate either to use a 32 or 16 bit type of processor but
for this as indicated earlier a 32-bit processor is to be used. The second specification is the
meet the needs of the organization. The sensor board ought to be of Ds1000 which offers both direct
sensing connectivity and all the IoT sensor capabilities. In addition, the organization ought to go for
802.15.14 network infrastructure of type SG1100 which is able to provide gateway services and is able to
deal with the deployment of wireless sensor networks. The processor for this case ought to be Intel X86;
this type of processor is able to handle all the IoT monitoring system commands (Yarali, 2016).
Operating system
IoT operating system ought to perform better within constraints of IoT devices which includes
size, power, the processing capacity, and memory. There are various IoT OS which includes, Ubuntu
Core, Fuchsia OS, Linux based OS, and RIOT. Ubuntu core is a transactional version which made
specifically for IoT devices. Fuchsia OS; this type of IoT OS which is Google based. On the other hand,
RIOT is one of the open source OS which is specialized for all IoT devices.
For this case, this paper will go for Fuchsia type of operating System which is a cross-device
open source OS. It is an OS from Google which is able to run IoT equipment. The OS also has the ability
to run across the various platforms meaning that it cannot only run only on smartphones but it can also
run on tablets, digital monitors, Airport controls, desktops, and notebooks. One of the major reason this
paper has gone for Fuchsia OS is that it is integrated with Google assistant and the Google cloud
environment (Kurose & Ross, 2017).
Sensors and actuators
When making a decision on the types of sensors; one of the major considerations is the sensor
signal conditioning. It is either the sensor signal conditioning is integrated with micro-controllers or with
the sensor module package. Another consideration to make is power management. So as to select the best
component four major specifications that this scenario ought to consider which the needed intelligence is
that is required by the sensor node; this ought to dictate either to use a 32 or 16 bit type of processor but
for this as indicated earlier a 32-bit processor is to be used. The second specification is the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IoT 5
communication technologies. Third, the sampling rate which is required for the sensor signal conditioning
and the power source.
To accommodate the requirements of the airport management system, they ought to go for the
DS1000 type of sensor with CMXX00 series which have 51 pins connector. This type of sensor has very
low power consumption rate, low response time, and broad measuring range. Other specifications of this
type of sensor is that it is resistive-based technology (Watts, 2015)
Physical channel
For this case, this paper will go for the ZigBee protocol. ZigBee communication protocol is best
suited for this case. This type of protocol which is specifically created for the wireless sensor network.
The protocol includes both software and hardware which is highly reliable, low, power, data rate, and
cost. In addition the protocol is scalable. The reason as to why this paper goes for ZigBee protocol is that
it is inexpensive and has the capability pf processing and collecting physical environmental information.
It also has the capability of communicating with the neigbouri9ng sensors. The airport management can
also use it as an air conditioning detection system (Blanc & Cotton, 2014).
The reason as to why this paper goes for ZigBee is that it offers Bluetooth services of upto 2.4 GHZ with
a data rate of 1Mbps. In addition it has a power consumption rate of 40 to 100MW. ZigBee also ranges
from 30 to 75 meters which is a good range for this case.
Logical channel
This project will go for hypertext transfer Protocol; this a type of protocol which allows fetching
of resources like HTML documents. It also permits users of WWW to exchange data and information
which is found on the internet. The Hyper Text Transfer Protocol uses port 443 so as to transfer
information. One of the reasons this paper has opted for HTTP is because it is simple as it is able to
encapsulate HTTP messages into frames. The protocol is designed to be simple and it easily understood
by users. Second, the protocol is extensible; i.e. it is very easy to extend HTTP protocol. Third, HTTP
protocol is stateless and session less; i.e. it allows the use of stateful sessions (Matthews, 2007)
communication technologies. Third, the sampling rate which is required for the sensor signal conditioning
and the power source.
To accommodate the requirements of the airport management system, they ought to go for the
DS1000 type of sensor with CMXX00 series which have 51 pins connector. This type of sensor has very
low power consumption rate, low response time, and broad measuring range. Other specifications of this
type of sensor is that it is resistive-based technology (Watts, 2015)
Physical channel
For this case, this paper will go for the ZigBee protocol. ZigBee communication protocol is best
suited for this case. This type of protocol which is specifically created for the wireless sensor network.
The protocol includes both software and hardware which is highly reliable, low, power, data rate, and
cost. In addition the protocol is scalable. The reason as to why this paper goes for ZigBee protocol is that
it is inexpensive and has the capability pf processing and collecting physical environmental information.
It also has the capability of communicating with the neigbouri9ng sensors. The airport management can
also use it as an air conditioning detection system (Blanc & Cotton, 2014).
The reason as to why this paper goes for ZigBee is that it offers Bluetooth services of upto 2.4 GHZ with
a data rate of 1Mbps. In addition it has a power consumption rate of 40 to 100MW. ZigBee also ranges
from 30 to 75 meters which is a good range for this case.
Logical channel
This project will go for hypertext transfer Protocol; this a type of protocol which allows fetching
of resources like HTML documents. It also permits users of WWW to exchange data and information
which is found on the internet. The Hyper Text Transfer Protocol uses port 443 so as to transfer
information. One of the reasons this paper has opted for HTTP is because it is simple as it is able to
encapsulate HTTP messages into frames. The protocol is designed to be simple and it easily understood
by users. Second, the protocol is extensible; i.e. it is very easy to extend HTTP protocol. Third, HTTP
protocol is stateless and session less; i.e. it allows the use of stateful sessions (Matthews, 2007)

IoT 6
Network topology
When choosing the best network topology few consideration has to be met first. First, is latency;
this is the time taken for a certain packet of data or information to move from one sensor node via an
organization network to a gateway node. Generally, this consideration imitates the speed of the
organization network. They say that the faster the organization network then the lower the latency. On the
other hand throughput, this is the amount of information or data which can pass via network in one
second. Third, consideration is the fault resiliency, this is that degree to which a network will recover in
case it is interrupted. Scalability is the total number of organization devices or gadgets which can be
included in the organization network.
For this case, this paper will go for mesh network topology. This is a type of topology which
consists of 3 types of nodes which are simple sensor nodes, router nodes, and a gateway node. Router
nodes which are used for routing, the gateway node are provided so as that data can reach to the outside
world.
One of the reasons as to why the organization goes for this type of topology is that the sensor
nodes able to capture and at the same time disseminate their own information or data. In addition, mesh
type of topology is able to serve as relays for the other nodes. Also it have that capability of collaborating
with the neighboring nodes so as to propagating data via a network (Kurose & Ross, 2017).
Second, mesh topology is positioned such that each and every node which is within the
transmission range for all the router nodes. In addition, data packets pass via multiple routers and sensors
so as to reach to the gateway noide. In addition, mesh type of topology is able to cover broad range; it is
able to scale up thousands of nodes and at the same time provide a high density of coverage. Other
advantages related to mesh type of topology is that data can be transmitted over various devices
simultaneously and at the same time the to0pology can withstand high traffic. Also, if one of the
component or device fails or cannot withstand high traffic, there is always an alternative component.
Lastly, modification and expansion can be done without having to disrupt other services.
Network topology
When choosing the best network topology few consideration has to be met first. First, is latency;
this is the time taken for a certain packet of data or information to move from one sensor node via an
organization network to a gateway node. Generally, this consideration imitates the speed of the
organization network. They say that the faster the organization network then the lower the latency. On the
other hand throughput, this is the amount of information or data which can pass via network in one
second. Third, consideration is the fault resiliency, this is that degree to which a network will recover in
case it is interrupted. Scalability is the total number of organization devices or gadgets which can be
included in the organization network.
For this case, this paper will go for mesh network topology. This is a type of topology which
consists of 3 types of nodes which are simple sensor nodes, router nodes, and a gateway node. Router
nodes which are used for routing, the gateway node are provided so as that data can reach to the outside
world.
One of the reasons as to why the organization goes for this type of topology is that the sensor
nodes able to capture and at the same time disseminate their own information or data. In addition, mesh
type of topology is able to serve as relays for the other nodes. Also it have that capability of collaborating
with the neighboring nodes so as to propagating data via a network (Kurose & Ross, 2017).
Second, mesh topology is positioned such that each and every node which is within the
transmission range for all the router nodes. In addition, data packets pass via multiple routers and sensors
so as to reach to the gateway noide. In addition, mesh type of topology is able to cover broad range; it is
able to scale up thousands of nodes and at the same time provide a high density of coverage. Other
advantages related to mesh type of topology is that data can be transmitted over various devices
simultaneously and at the same time the to0pology can withstand high traffic. Also, if one of the
component or device fails or cannot withstand high traffic, there is always an alternative component.
Lastly, modification and expansion can be done without having to disrupt other services.

IoT 7
Maintenance
This paper will propose a predictive type of maintenance. This is a type of maintenance which is
used to determine the conditions of all the in-service equipment so as to predict when a maintenance
ought to be performed. One of the reasons this project goes for this type of maintenance is that it allows
convenient scheduling of corrective maintenance. It also prevents what one would refer to as unexpected
equipment failures (Huang, 2015).
Data storage
For this scenario, this paper will go for cloud type of data storage. This is because data cloud is
ubiquitous and elastic. In addition, cloud has analytical tools which can help in discovering some of the
secrets which are hidden in a broad pool of data. In addition, cloud data storage can be designed such that
the IoT system is able to perform real-time analytics.
Data Access
There two types of data access which are random access and sequential type of data access. For
this scenario, this paper will go for a random type of data access. Random data access is also referred to
as direct access. With this type of data access, the IoT system has the ability to access an arbitrary data
element, no matter the number of data elements which may be set; The IoT system has the ability to
access any data set in constant time.
Cost
To come with this IoT monitoring system more weight has been put on hardware. The maximum
cost for this system is $20,000. The cost is like that of an environmental monitoring system. The
hardware takes 75 percent of the cost while the software part takes 25 percent of the cost (Amazon,
2016).
The security aspect of the IoT system
IoT system makes use of lots of security aspects. To start with all the security aspects, rely
heavily on the encryption. Example, this IoT system should make use of the many layers of defense, an
Maintenance
This paper will propose a predictive type of maintenance. This is a type of maintenance which is
used to determine the conditions of all the in-service equipment so as to predict when a maintenance
ought to be performed. One of the reasons this project goes for this type of maintenance is that it allows
convenient scheduling of corrective maintenance. It also prevents what one would refer to as unexpected
equipment failures (Huang, 2015).
Data storage
For this scenario, this paper will go for cloud type of data storage. This is because data cloud is
ubiquitous and elastic. In addition, cloud has analytical tools which can help in discovering some of the
secrets which are hidden in a broad pool of data. In addition, cloud data storage can be designed such that
the IoT system is able to perform real-time analytics.
Data Access
There two types of data access which are random access and sequential type of data access. For
this scenario, this paper will go for a random type of data access. Random data access is also referred to
as direct access. With this type of data access, the IoT system has the ability to access an arbitrary data
element, no matter the number of data elements which may be set; The IoT system has the ability to
access any data set in constant time.
Cost
To come with this IoT monitoring system more weight has been put on hardware. The maximum
cost for this system is $20,000. The cost is like that of an environmental monitoring system. The
hardware takes 75 percent of the cost while the software part takes 25 percent of the cost (Amazon,
2016).
The security aspect of the IoT system
IoT system makes use of lots of security aspects. To start with all the security aspects, rely
heavily on the encryption. Example, this IoT system should make use of the many layers of defense, an
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IoT 8
example is segregating devices onto separate networks. Another aspect of IoT system security is device
authorization and authentication. All the devices ought to establish their own identity before accessing
upstream apps and services. Third, it is important to manage device updates which include security
patches. All the devices must be up to date. The fourth aspect is that the system must ensure data integrity
and privacy. Lastly, the IoT system must detect weaknesses and security breaches (Gilchrist, 2016).
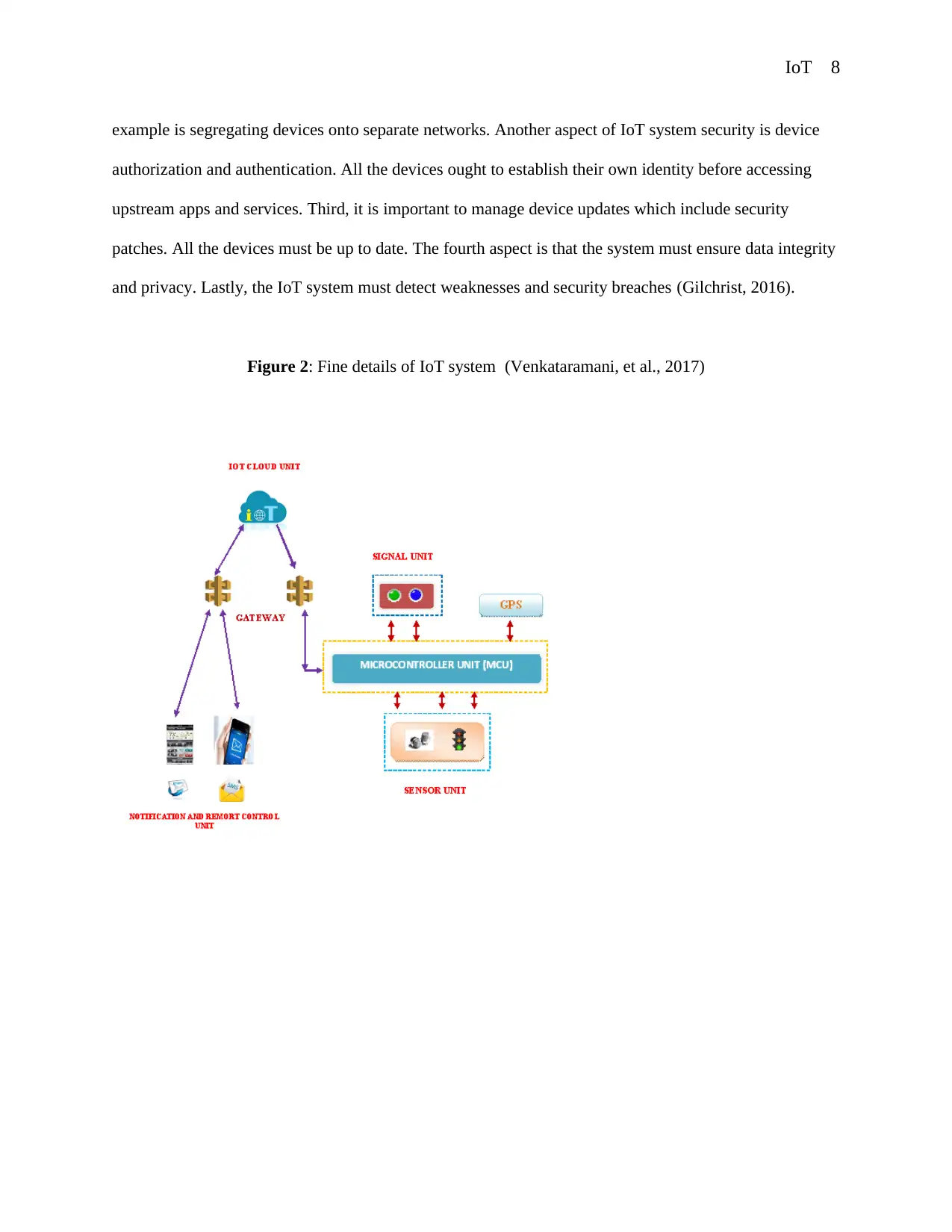
Figure 2: Fine details of IoT system (Venkataramani, et al., 2017)
example is segregating devices onto separate networks. Another aspect of IoT system security is device
authorization and authentication. All the devices ought to establish their own identity before accessing
upstream apps and services. Third, it is important to manage device updates which include security
patches. All the devices must be up to date. The fourth aspect is that the system must ensure data integrity
and privacy. Lastly, the IoT system must detect weaknesses and security breaches (Gilchrist, 2016).
Figure 2: Fine details of IoT system (Venkataramani, et al., 2017)

IoT 9
Simulation codes of the scenario
Simulating connected baggage
{
var path = Baggage({start:' Airportarrival',end:'customerpick',accuracy:5});
return JSON.stringify(path);
}
Simulating found baggage
{
var found = Baggage ( { start: ‘customerbaggage’, end ‘givecustomer’, accuracy: 4});
return JSON.stringify(Baggage);
Conclusion
From this paper, it is evident that IoT system will sort the problem in the airport. In addition, the
system enhances connectivity of baggage after they arrive at the airport at any-place or any-time that they
are required. The proposed IoT system has the ability to transfer data over the organization network
without the requirement of human to computer or what one may refer to as human-computer interaction.
References
Simulation codes of the scenario
Simulating connected baggage
{
var path = Baggage({start:' Airportarrival',end:'customerpick',accuracy:5});
return JSON.stringify(path);
}
Simulating found baggage
{
var found = Baggage ( { start: ‘customerbaggage’, end ‘givecustomer’, accuracy: 4});
return JSON.stringify(Baggage);
Conclusion
From this paper, it is evident that IoT system will sort the problem in the airport. In addition, the
system enhances connectivity of baggage after they arrive at the airport at any-place or any-time that they
are required. The proposed IoT system has the ability to transfer data over the organization network
without the requirement of human to computer or what one may refer to as human-computer interaction.
References

IoT 10
Amazon, 2016. AMAZON. [Online]
Available at: https://www.amazon.com
[Accessed 5th November 2018].
Benabdellah, 2017. Internet of things security. Wireless Technologies, Embedded and Intelligent
Systems, I(1), pp. 1-6.
Blanc, R. P. & Cotton, I. W., 2014. Computer networking by Robert P Blanc. s.l.:s.n.
Gilchrist, A., 2016. IoT security issues by Alasdair Gilchrist. 3rd ed. New York: Boston Press.
Gilchrist, A., 2016. Internet of things security analysis. Internet Technology and Applications
(iTAP, 2(1), pp. 1-4.
Huang, Z., 2015. Progression and Edge Intelligence Framework for IoT Systems. 2nd ed.
Chicago: John & Wiley Sons Press.
Kurose, J. F. & Ross, K. W., 2017. Networking. Computer security, II(2), pp. 27-78.
Matthews, J., 2007. Computer networking : Internet protocols in action. 1st ed. New York:
Springer .
Venkataramani, G. P. et al., 2017. Smart secure systems - IoT and analytics perspective : second
International Conference on Intelligent Information Technologies, ICIIT 2017, Chennai, India,
December 20-22, 2017, proceedings. 3rd ed. Singapore : Springer.
Watts, S., 2015. The Internet of Things (IoT) : applications, technology,... by Silvia Watts. 1st ed.
Chicago: Springer.
Amazon, 2016. AMAZON. [Online]
Available at: https://www.amazon.com
[Accessed 5th November 2018].
Benabdellah, 2017. Internet of things security. Wireless Technologies, Embedded and Intelligent
Systems, I(1), pp. 1-6.
Blanc, R. P. & Cotton, I. W., 2014. Computer networking by Robert P Blanc. s.l.:s.n.
Gilchrist, A., 2016. IoT security issues by Alasdair Gilchrist. 3rd ed. New York: Boston Press.
Gilchrist, A., 2016. Internet of things security analysis. Internet Technology and Applications
(iTAP, 2(1), pp. 1-4.
Huang, Z., 2015. Progression and Edge Intelligence Framework for IoT Systems. 2nd ed.
Chicago: John & Wiley Sons Press.
Kurose, J. F. & Ross, K. W., 2017. Networking. Computer security, II(2), pp. 27-78.
Matthews, J., 2007. Computer networking : Internet protocols in action. 1st ed. New York:
Springer .
Venkataramani, G. P. et al., 2017. Smart secure systems - IoT and analytics perspective : second
International Conference on Intelligent Information Technologies, ICIIT 2017, Chennai, India,
December 20-22, 2017, proceedings. 3rd ed. Singapore : Springer.
Watts, S., 2015. The Internet of Things (IoT) : applications, technology,... by Silvia Watts. 1st ed.
Chicago: Springer.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IoT 11
Welton, T., 2017. Internet of Things : Characteristics of IoT Systems by Travis Welton. 1st ed.
London: New Hampshire Press.
Yarali, A., 2016. IoT. 4th ed. New York: Nova Science Publishers.
Welton, T., 2017. Internet of Things : Characteristics of IoT Systems by Travis Welton. 1st ed.
London: New Hampshire Press.
Yarali, A., 2016. IoT. 4th ed. New York: Nova Science Publishers.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





