A Detailed Report on IoT in Communication, Big Data, and Security
VerifiedAdded on 2023/06/05
|11
|3013
|282
Report
AI Summary
This report examines the role of the Internet of Things (IoT) in modern communication systems, highlighting the increasing adoption of IoT devices and their impact on data transmission. It emphasizes the significance of big data and cloud computing in managing and processing the vast amounts of data generated by IoT devices. The report also addresses the critical security challenges associated with IoT, including data breaches and denial-of-service attacks, and explores various security measures such as firewalls, pattern recognition, and encryption. It reviews existing literature on IoT and big data, discussing the advantages and disadvantages of these technologies, and identifies key components of IoT systems, including sensors, routers, and cloud computing. Furthermore, the report outlines various applications of IoT in areas such as smart homes, connected cars, and industrial internet, concluding that while IoT offers numerous benefits, robust security measures are essential to mitigate potential risks. Desklib offers a range of solved assignments and past papers for students.

Executive Summary
IoT refers to network technology which
is used to interconnect various
computing devices like smartphones,
tablets, and other peripheral devices.
Home automation is the very best
example of the internet of thing and
numbers of people adopt this
innovation to reduce efforts and
improve the efficiency of their systems.
This report is explaining the significance
of IoT in communication system and
importance of Big data and cloud
computing. It is investigated that in the
year 2017 the rate of the internet of
thing is increased by 33% and many
users use wireless technologies for
communication purpose. Security is the
very big problem for any organization
and information technology developed
many security plans to avoid threats and
risk of IoT. Firewall is the very common
step to block unauthentic signals and
traffic into commuter networks and
users can adopt pattern recognition,
cryptography, and encryption
technologies.
IoT refers to network technology which
is used to interconnect various
computing devices like smartphones,
tablets, and other peripheral devices.
Home automation is the very best
example of the internet of thing and
numbers of people adopt this
innovation to reduce efforts and
improve the efficiency of their systems.
This report is explaining the significance
of IoT in communication system and
importance of Big data and cloud
computing. It is investigated that in the
year 2017 the rate of the internet of
thing is increased by 33% and many
users use wireless technologies for
communication purpose. Security is the
very big problem for any organization
and information technology developed
many security plans to avoid threats and
risk of IoT. Firewall is the very common
step to block unauthentic signals and
traffic into commuter networks and
users can adopt pattern recognition,
cryptography, and encryption
technologies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction...........................................................................................................................................3
Internet of thing....................................................................................................................................3
Literature Review..................................................................................................................................3
Components of IoT................................................................................................................................8
Application of IoT..................................................................................................................................9
Conclusion.............................................................................................................................................9
References...........................................................................................................................................11
Introduction...........................................................................................................................................3
Internet of thing....................................................................................................................................3
Literature Review..................................................................................................................................3
Components of IoT................................................................................................................................8
Application of IoT..................................................................................................................................9
Conclusion.............................................................................................................................................9
References...........................................................................................................................................11

Introduction
Internet of thing is one advanced
technology in the field of wireless
communication and it is observed that it
is a more flexible network process.
There are many organizations use this
technology because it can be used for
long distance communication and
security is a very common issue for IoT
(Al-Fuqaha, et al., 2015). The main
purpose of this report is to recognize
the fundamental concept of the internet
of things and their security issues. In
this process, two or more peripheral
devices are connected to each other
with the help of internet and it provides
wireless connectivity between
transmitter and receiver (Cai, Xu, Jiang,
& Vasilakos, 2017). There are various
problems faced by the big data on the
internet of thing and cloud computing
such as data storage issues,
transmission issue, data breach, the
problem of data processing, security of
data, privacy challenges, and Denial of
services attack.
Internet of thing
It is defined as a network for physical
equipment’s and devices and it has the
ability to interconnect two or more
computing devices with the help of
internet access (Chandrakanth, et al.,
2014). From the last five years, the rate
of IoT is increasing very fast and around
8.4 million people are using this
technology for the daily purpose. It
includes various devices, for example, a
computer system, network devices,
smartphones, and other peripheral
devices (Da, He, & Li, 2014). The main
advantage of this innovation is that it is
very flexible and reliable that reduces
the issue of security.
Literature Review
1. Hashem, I. A. T., Yaqoob, I.,
Anuar, N. B., Mokhtar, S., Gani,
A., & Khan, S. U. (2015). The
rise of “big data” on cloud
computing: Review and open
research issues. Information
Systems, 47, 98-115.
In this journal paper, the author
describes the working mechanism of big
data and the role of IoT in cloud
computing. According to the writer, the
internet of thing is very popular
technology by which users can share
their personal information with other
like social media (Hashem, et al., 2015).
This paper is completely based on the
big data encounters and the concept of
Internet of thing is one advanced
technology in the field of wireless
communication and it is observed that it
is a more flexible network process.
There are many organizations use this
technology because it can be used for
long distance communication and
security is a very common issue for IoT
(Al-Fuqaha, et al., 2015). The main
purpose of this report is to recognize
the fundamental concept of the internet
of things and their security issues. In
this process, two or more peripheral
devices are connected to each other
with the help of internet and it provides
wireless connectivity between
transmitter and receiver (Cai, Xu, Jiang,
& Vasilakos, 2017). There are various
problems faced by the big data on the
internet of thing and cloud computing
such as data storage issues,
transmission issue, data breach, the
problem of data processing, security of
data, privacy challenges, and Denial of
services attack.
Internet of thing
It is defined as a network for physical
equipment’s and devices and it has the
ability to interconnect two or more
computing devices with the help of
internet access (Chandrakanth, et al.,
2014). From the last five years, the rate
of IoT is increasing very fast and around
8.4 million people are using this
technology for the daily purpose. It
includes various devices, for example, a
computer system, network devices,
smartphones, and other peripheral
devices (Da, He, & Li, 2014). The main
advantage of this innovation is that it is
very flexible and reliable that reduces
the issue of security.
Literature Review
1. Hashem, I. A. T., Yaqoob, I.,
Anuar, N. B., Mokhtar, S., Gani,
A., & Khan, S. U. (2015). The
rise of “big data” on cloud
computing: Review and open
research issues. Information
Systems, 47, 98-115.
In this journal paper, the author
describes the working mechanism of big
data and the role of IoT in cloud
computing. According to the writer, the
internet of thing is very popular
technology by which users can share
their personal information with other
like social media (Hashem, et al., 2015).
This paper is completely based on the
big data encounters and the concept of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
cloud computing. There are four main
parts of big data which are also called as
four Vs and author identified security
issue occurs with IoT and big data. It is
observed that big data can be used to
analyse different types of data and many
organizations are using this technology
to control and monitor a large amount
of data. It uses various networks devices
such as routers, hubs, bridges and other
peripheral devices to communicate with
computer devices (Hashem, et al., 2015).
Big data and IoT is completely based on
wireless technology because it provides
a platform to send or receive data from
one location to another.
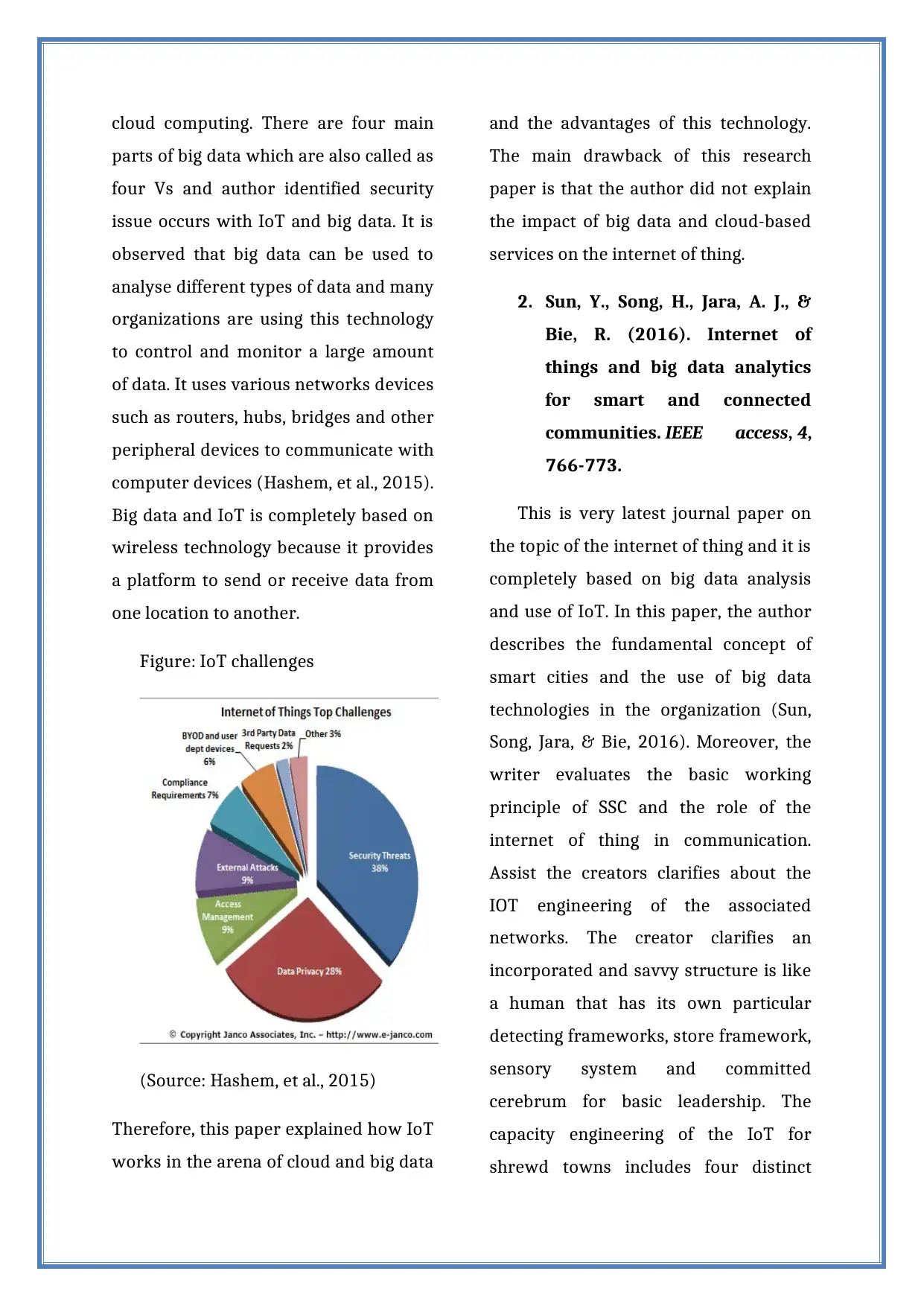
Figure: IoT challenges
(Source: Hashem, et al., 2015)
Therefore, this paper explained how IoT
works in the arena of cloud and big data
and the advantages of this technology.
The main drawback of this research
paper is that the author did not explain
the impact of big data and cloud-based
services on the internet of thing.
2. Sun, Y., Song, H., Jara, A. J., &
Bie, R. (2016). Internet of
things and big data analytics
for smart and connected
communities. IEEE access, 4,
766-773.
This is very latest journal paper on
the topic of the internet of thing and it is
completely based on big data analysis
and use of IoT. In this paper, the author
describes the fundamental concept of
smart cities and the use of big data
technologies in the organization (Sun,
Song, Jara, & Bie, 2016). Moreover, the
writer evaluates the basic working
principle of SSC and the role of the
internet of thing in communication.
Assist the creators clarifies about the
IOT engineering of the associated
networks. The creator clarifies an
incorporated and savvy structure is like
a human that has its own particular
detecting frameworks, store framework,
sensory system and committed
cerebrum for basic leadership. The
capacity engineering of the IoT for
shrewd towns includes four distinct
parts of big data which are also called as
four Vs and author identified security
issue occurs with IoT and big data. It is
observed that big data can be used to
analyse different types of data and many
organizations are using this technology
to control and monitor a large amount
of data. It uses various networks devices
such as routers, hubs, bridges and other
peripheral devices to communicate with
computer devices (Hashem, et al., 2015).
Big data and IoT is completely based on
wireless technology because it provides
a platform to send or receive data from
one location to another.
Figure: IoT challenges
(Source: Hashem, et al., 2015)
Therefore, this paper explained how IoT
works in the arena of cloud and big data
and the advantages of this technology.
The main drawback of this research
paper is that the author did not explain
the impact of big data and cloud-based
services on the internet of thing.
2. Sun, Y., Song, H., Jara, A. J., &
Bie, R. (2016). Internet of
things and big data analytics
for smart and connected
communities. IEEE access, 4,
766-773.
This is very latest journal paper on
the topic of the internet of thing and it is
completely based on big data analysis
and use of IoT. In this paper, the author
describes the fundamental concept of
smart cities and the use of big data
technologies in the organization (Sun,
Song, Jara, & Bie, 2016). Moreover, the
writer evaluates the basic working
principle of SSC and the role of the
internet of thing in communication.
Assist the creators clarifies about the
IOT engineering of the associated
networks. The creator clarifies an
incorporated and savvy structure is like
a human that has its own particular
detecting frameworks, store framework,
sensory system and committed
cerebrum for basic leadership. The
capacity engineering of the IoT for
shrewd towns includes four distinct
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

layers: detecting or reacting, layer, the
information layer, interconnecting layer,
and administrations layer (Liu et al.,
2015). Assist in this paper the
specialists clarifies in points of interest
of advances that will be essential for the
empowering the IOT in associating the
network (Jin, Wah, Cheng, & Wang,
2015). The analysts clarify that the huge
information is one of the real things that
will be valuable at the costs of
examination of subtle elements. This
must be guaranteed that the huge
information investigation is one of the
significant things in the procedure of
legitimate usage of the associated
innovations. At the point when there
will be a colossal measure of the
information that will be produced and
these frameworks will be immense and
there would be a need of assessing this
information in an appropriate way
(Stankovic, 2014). Encourage the
finishing up the subject the analysts
clarify about the issues that may come
up in issuing these innovations in an
associated network. The main
disadvantage of this article is that it
does not describe different types of the
security issue and threats of big data
and internet of thing.
3. Cai, H., Xu, B., Jiang, L., &
Vasilakos, A. V. (2017). IoT-
based big data storage systems
in cloud computing:
Perspectives and
challenges. IEEE Internet of
Things Journal, 4(1), 75-87.
The title of this paper is IoT based big
data storage system in the field of the
cloud: perspectives and their challenges.
The main determination of this research
article is to provide basic knowledge
about the internet of thing in terms of
data storage (Cai, Xu, Jiang, & Vasilakos,
2017). The author provides a platform
where users of IoT and cloud computing
can understand the challenges and
issues faced by these techniques. Cloud
computing can be used as a backup plan
and it has the ability to reduce cyber-
attacks. It is identified that lack of
security and issue of data storage both
are a very common problem of big data
and IoT and various organizations are
suffering from these problems (Lee, &
Lee, 2015). The writer clarifies the
billow of things as cloud servers are
associated with every one of the gadgets
and servers are associated with a
solitary server. Further clarifying the
connection with the enormous
information the analysts clarifies the
information administration processes
that are fundamental for the way
toward breaking down of the distinctive
information layer, interconnecting layer,
and administrations layer (Liu et al.,
2015). Assist in this paper the
specialists clarifies in points of interest
of advances that will be essential for the
empowering the IOT in associating the
network (Jin, Wah, Cheng, & Wang,
2015). The analysts clarify that the huge
information is one of the real things that
will be valuable at the costs of
examination of subtle elements. This
must be guaranteed that the huge
information investigation is one of the
significant things in the procedure of
legitimate usage of the associated
innovations. At the point when there
will be a colossal measure of the
information that will be produced and
these frameworks will be immense and
there would be a need of assessing this
information in an appropriate way
(Stankovic, 2014). Encourage the
finishing up the subject the analysts
clarify about the issues that may come
up in issuing these innovations in an
associated network. The main
disadvantage of this article is that it
does not describe different types of the
security issue and threats of big data
and internet of thing.
3. Cai, H., Xu, B., Jiang, L., &
Vasilakos, A. V. (2017). IoT-
based big data storage systems
in cloud computing:
Perspectives and
challenges. IEEE Internet of
Things Journal, 4(1), 75-87.
The title of this paper is IoT based big
data storage system in the field of the
cloud: perspectives and their challenges.
The main determination of this research
article is to provide basic knowledge
about the internet of thing in terms of
data storage (Cai, Xu, Jiang, & Vasilakos,
2017). The author provides a platform
where users of IoT and cloud computing
can understand the challenges and
issues faced by these techniques. Cloud
computing can be used as a backup plan
and it has the ability to reduce cyber-
attacks. It is identified that lack of
security and issue of data storage both
are a very common problem of big data
and IoT and various organizations are
suffering from these problems (Lee, &
Lee, 2015). The writer clarifies the
billow of things as cloud servers are
associated with every one of the gadgets
and servers are associated with a
solitary server. Further clarifying the
connection with the enormous
information the analysts clarifies the
information administration processes
that are fundamental for the way
toward breaking down of the distinctive

types of the information that might be
helpful to analyse the information in an
appropriate way (Wortmann, &
Flüchter, 2015). The information mining
forms are additionally all around
clarified in the paper. Therefore
consumers can use these innovations by
improving flexibility and security of
their data.
4. Jin, X., Wah, B. W., Cheng, X., &
Wang, Y. (2015). Significance
and challenges of big data
research. Big Data
Research, 2(2), 59-64.
This paper is completely based on the
security issues faced in big data
technologies and author use qualitative
data analysis process to understand the
threats and risks of this process.
According to this paper, the use of
wireless networks and cloud computing
is growing very fast by which various
security issues also associated with IoT
for example data breach, and DOS
attack. The main objective of the author
is to explain the importance of big data
in communication and impact of this
innovation on the life of consumers.
Author evaluate major problems occur
with the internet of thing in the last five
years and prevention methods to reduce
challenges and issues. Fabulous
difficulties of the enormous information
that are very much clarified in the paper
are the information unpredictability,
computational many-sided quality and
the framework intricacy (Sun, Song,
Jara, & Bie, 2016). The scientists clarify
these there as the significant issue in the
improvement of the IOT and how these
can hamper the idea. Finishing up the
theme the scientist sums up the
guarantee mapper and examines the
achievement focuses that can help in the
advancement of the big information in
IOT.
5. Lee, I., & Lee, K. (2015). The
Internet of Things (IoT):
Applications, investments, and
challenges for
enterprises. Business
Horizons, 58(4), 431-440.
This article was written by Lee and it
provides the concept of the internet of
thing in terms of business. There are
many applications of IoT but many
organizations use this for
communication purpose because it
enhances the performance of networks.
In which author first describe the
history of the internet of thing and the
implementation process of this
technology. There are main four
technologies are used in IoT for
helpful to analyse the information in an
appropriate way (Wortmann, &
Flüchter, 2015). The information mining
forms are additionally all around
clarified in the paper. Therefore
consumers can use these innovations by
improving flexibility and security of
their data.
4. Jin, X., Wah, B. W., Cheng, X., &
Wang, Y. (2015). Significance
and challenges of big data
research. Big Data
Research, 2(2), 59-64.
This paper is completely based on the
security issues faced in big data
technologies and author use qualitative
data analysis process to understand the
threats and risks of this process.
According to this paper, the use of
wireless networks and cloud computing
is growing very fast by which various
security issues also associated with IoT
for example data breach, and DOS
attack. The main objective of the author
is to explain the importance of big data
in communication and impact of this
innovation on the life of consumers.
Author evaluate major problems occur
with the internet of thing in the last five
years and prevention methods to reduce
challenges and issues. Fabulous
difficulties of the enormous information
that are very much clarified in the paper
are the information unpredictability,
computational many-sided quality and
the framework intricacy (Sun, Song,
Jara, & Bie, 2016). The scientists clarify
these there as the significant issue in the
improvement of the IOT and how these
can hamper the idea. Finishing up the
theme the scientist sums up the
guarantee mapper and examines the
achievement focuses that can help in the
advancement of the big information in
IOT.
5. Lee, I., & Lee, K. (2015). The
Internet of Things (IoT):
Applications, investments, and
challenges for
enterprises. Business
Horizons, 58(4), 431-440.
This article was written by Lee and it
provides the concept of the internet of
thing in terms of business. There are
many applications of IoT but many
organizations use this for
communication purpose because it
enhances the performance of networks.
In which author first describe the
history of the internet of thing and the
implementation process of this
technology. There are main four
technologies are used in IoT for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

example, wireless sensor network,
middleware, cloud computing, RFID
technology, and network devices. This
article provides an overview of the
application of IoT and their security
risks and author also provide mitigation
tools to avoid the issue of security
(Whitmore, Agarwal, & Da, 2015).
Figure: IoT smart cities
(Source: Whitmore, Agarwal, & Da,
2015)
Hacker produces malicious and flooding
process due to which they can share
unwanted signals to computer networks
and encrypt all personal information. It
is estimated that many users and
organization use simple passwords and
they do not adopt authentic servers by
which hackers can easily target their
private accounts and reduce the privacy
of human personal information (Sicari,
Rizzardi, Grieco, & Coen, 2015). In this
article, the writer uses qualitative data
analysis and it provides a proper
explanation of the Internet of thing but
the main problem of this paper is that it
does not provide steps to avoid security
risks.
Components of IoT
It is a very best method to communicate
with computer devices and the
following main components are used on
the internet of thing:
Smart and digital devices
Sensors
Routers, Gateway, and Hubs
Cloud computing
DSL modem
Firewall and NAT
Internet connection sharing
Wireless sensor networks
Data links
Access points
RFID and proximity technology
User interface systems (Perera,
Zaslavsky, Christen, &
Georgakopoulos, 2014).
Figure: IoT components
middleware, cloud computing, RFID
technology, and network devices. This
article provides an overview of the
application of IoT and their security
risks and author also provide mitigation
tools to avoid the issue of security
(Whitmore, Agarwal, & Da, 2015).
Figure: IoT smart cities
(Source: Whitmore, Agarwal, & Da,
2015)
Hacker produces malicious and flooding
process due to which they can share
unwanted signals to computer networks
and encrypt all personal information. It
is estimated that many users and
organization use simple passwords and
they do not adopt authentic servers by
which hackers can easily target their
private accounts and reduce the privacy
of human personal information (Sicari,
Rizzardi, Grieco, & Coen, 2015). In this
article, the writer uses qualitative data
analysis and it provides a proper
explanation of the Internet of thing but
the main problem of this paper is that it
does not provide steps to avoid security
risks.
Components of IoT
It is a very best method to communicate
with computer devices and the
following main components are used on
the internet of thing:
Smart and digital devices
Sensors
Routers, Gateway, and Hubs
Cloud computing
DSL modem
Firewall and NAT
Internet connection sharing
Wireless sensor networks
Data links
Access points
RFID and proximity technology
User interface systems (Perera,
Zaslavsky, Christen, &
Georgakopoulos, 2014).
Figure: IoT components
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

(Source: Perera, Zaslavsky, Christen, &
Georgakopoulos, 2014)
Application of IoT
The main role of the internet of thing in
real word is that users can communicate
and share their private data from one
location to another (Li, Da, & Zhao,
2015). It uses internet process to
interconnect two or mobile devices and
it has the capability to improve the
efficiency of the transmission system.
There are many applications of this
technology which are described below:
Figure: IoT application
(Source: Li, Da, & Zhao, 2015)
Smart home
Wearable’s
Connected cars
Industrial internet
Smart cities
IoT in agriculture
Smart Retail
Energy Engagement
In healthcare
IoT in farming and poultry
(Osseiran, Elloumi, Song, &
Monserrat, 2017).
Conclusion
Internet of thing is a type of computer
system which explains the idea of
physical objects that connected to the
internet. It uses radio frequency
identification process for
communication purpose and it involves
different kinds of sensor, wireless
networks, and QR codes. In this
technology, any object can be
Georgakopoulos, 2014)
Application of IoT
The main role of the internet of thing in
real word is that users can communicate
and share their private data from one
location to another (Li, Da, & Zhao,
2015). It uses internet process to
interconnect two or mobile devices and
it has the capability to improve the
efficiency of the transmission system.
There are many applications of this
technology which are described below:
Figure: IoT application
(Source: Li, Da, & Zhao, 2015)
Smart home
Wearable’s
Connected cars
Industrial internet
Smart cities
IoT in agriculture
Smart Retail
Energy Engagement
In healthcare
IoT in farming and poultry
(Osseiran, Elloumi, Song, &
Monserrat, 2017).
Conclusion
Internet of thing is a type of computer
system which explains the idea of
physical objects that connected to the
internet. It uses radio frequency
identification process for
communication purpose and it involves
different kinds of sensor, wireless
networks, and QR codes. In this
technology, any object can be

represented in the form of digital which
is connected to database systems. This
report explained the role of IoT in daily
life and different types of challenges
faced by big data and cloud computing.
Therefore users can adopt a firewall and
encryption technique to reduce security
threats of IoT.
is connected to database systems. This
report explained the role of IoT in daily
life and different types of challenges
faced by big data and cloud computing.
Therefore users can adopt a firewall and
encryption technique to reduce security
threats of IoT.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Al-Fuqaha, A., Guizani, M., Mohammadi,
M., Aledhari, M., & Ayyash, M. (2015).
Internet of things: A survey on enabling
technologies, protocols, and
applications. IEEE Communications
Surveys & Tutorials, 17(4), 2347-2376.
Cai, H., Xu, B., Jiang, L., & Vasilakos, A. V.
(2017). IoT-based big data storage
systems in cloud computing:
Perspectives and challenges. IEEE
Internet of Things Journal, 4(1), 75-87.
Chandrakanth, S., Venkatesh, K., Uma
Mahesh, J., & Naganjaneyulu, K. V.
(2014). Internet of things. International
Journal of Innovations & Advancement in
Computer Science, 3(8), 16-20.
Da Xu, L., He, W., & Li, S. (2014). Internet
of things in industries: A survey. IEEE
Transactions on industrial
informatics, 10(4), 2233-2243.
Hashem, I. A. T., Yaqoob, I., Anuar, N. B.,
Mokhtar, S., Gani, A., & Khan, S. U.
(2015). The rise of “big data” on cloud
computing: Review and open research
issues. Information Systems, 47, 98-115.
Jin, X., Wah, B. W., Cheng, X., & Wang, Y.
(2015). Significance and challenges of
big data research. Big Data
Research, 2(2), 59-64.
Lee, I., & Lee, K. (2015). The Internet of
Things (IoT): Applications, investments,
and challenges for enterprises. Business
Horizons, 58(4), 431-440.
Li, S., Da Xu, L., & Zhao, S. (2015). The
internet of things: a survey. Information
Systems Frontiers, 17(2), 243-259.
Osseiran, A., Elloumi, O., Song, J., &
Monserrat, J. F. (2017). Internet of
Things. IEEE Communications Standards
Magazine, 1(2), 84-84.
Perera, C., Zaslavsky, A., Christen, P., &
Georgakopoulos, D. (2014). Context-
aware computing for the internet of
things: A survey. IEEE communications
surveys & tutorials, 16(1), 414-454.
Sicari, S., Rizzardi, A., Grieco, L. A., &
Coen-Porisini, A. (2015). Security,
privacy and trust in the Internet of
Things: The road ahead. Computer
networks, 76, 146-164.
Stankovic, J. A. (2014). Research
directions for the internet of
things. IEEE Internet of Things
Journal, 1(1), 3-9.
Sun, Y., Song, H., Jara, A. J., & Bie, R.
(2016). Internet of things and big data
Al-Fuqaha, A., Guizani, M., Mohammadi,
M., Aledhari, M., & Ayyash, M. (2015).
Internet of things: A survey on enabling
technologies, protocols, and
applications. IEEE Communications
Surveys & Tutorials, 17(4), 2347-2376.
Cai, H., Xu, B., Jiang, L., & Vasilakos, A. V.
(2017). IoT-based big data storage
systems in cloud computing:
Perspectives and challenges. IEEE
Internet of Things Journal, 4(1), 75-87.
Chandrakanth, S., Venkatesh, K., Uma
Mahesh, J., & Naganjaneyulu, K. V.
(2014). Internet of things. International
Journal of Innovations & Advancement in
Computer Science, 3(8), 16-20.
Da Xu, L., He, W., & Li, S. (2014). Internet
of things in industries: A survey. IEEE
Transactions on industrial
informatics, 10(4), 2233-2243.
Hashem, I. A. T., Yaqoob, I., Anuar, N. B.,
Mokhtar, S., Gani, A., & Khan, S. U.
(2015). The rise of “big data” on cloud
computing: Review and open research
issues. Information Systems, 47, 98-115.
Jin, X., Wah, B. W., Cheng, X., & Wang, Y.
(2015). Significance and challenges of
big data research. Big Data
Research, 2(2), 59-64.
Lee, I., & Lee, K. (2015). The Internet of
Things (IoT): Applications, investments,
and challenges for enterprises. Business
Horizons, 58(4), 431-440.
Li, S., Da Xu, L., & Zhao, S. (2015). The
internet of things: a survey. Information
Systems Frontiers, 17(2), 243-259.
Osseiran, A., Elloumi, O., Song, J., &
Monserrat, J. F. (2017). Internet of
Things. IEEE Communications Standards
Magazine, 1(2), 84-84.
Perera, C., Zaslavsky, A., Christen, P., &
Georgakopoulos, D. (2014). Context-
aware computing for the internet of
things: A survey. IEEE communications
surveys & tutorials, 16(1), 414-454.
Sicari, S., Rizzardi, A., Grieco, L. A., &
Coen-Porisini, A. (2015). Security,
privacy and trust in the Internet of
Things: The road ahead. Computer
networks, 76, 146-164.
Stankovic, J. A. (2014). Research
directions for the internet of
things. IEEE Internet of Things
Journal, 1(1), 3-9.
Sun, Y., Song, H., Jara, A. J., & Bie, R.
(2016). Internet of things and big data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

analytics for smart and connected
communities. IEEE access, 4, 766-773.
Whitmore, A., Agarwal, A., & Da Xu, L.
(2015). The Internet of Things—A
survey of topics and trends. Information
Systems Frontiers, 17(2), 261-274.
Wortmann, F., & Flüchter, K. (2015).
Internet of things. Business &
Information Systems Engineering, 57(3),
221-224.
communities. IEEE access, 4, 766-773.
Whitmore, A., Agarwal, A., & Da Xu, L.
(2015). The Internet of Things—A
survey of topics and trends. Information
Systems Frontiers, 17(2), 261-274.
Wortmann, F., & Flüchter, K. (2015).
Internet of things. Business &
Information Systems Engineering, 57(3),
221-224.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





