IoT Design and Simulation
VerifiedAdded on 2023/04/22
|12
|2822
|77
AI Summary
This paper presents the software and hardware tools for the development of an IoT system and its security analysis tools. It discusses the hardware platform, physical and logical channels, network topology, maintenance, data storage, data access, and cost. The paper also highlights the security aspects of the IoT system.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IoT Design and Simulation 1
IoT Design and Simulation
Student Name
Institution
Professor’s Name
Date
IoT Design and Simulation
Student Name
Institution
Professor’s Name
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IoT Design and Simulation 2
Abstract
Sorting system installed in every airport makes easy the work for every passenger.
Manual loading of the bags is carried out at the end of the system to the aircraft. Even though
this is done, there is a risk of losing the bags since most of the operations involve over 85% of
human labor. This paper presents the software and the hardware tools for the development of an
IoT system and its security analysis tools. This enables the visualization of the IoT systems.
Abstract
Sorting system installed in every airport makes easy the work for every passenger.
Manual loading of the bags is carried out at the end of the system to the aircraft. Even though
this is done, there is a risk of losing the bags since most of the operations involve over 85% of
human labor. This paper presents the software and the hardware tools for the development of an
IoT system and its security analysis tools. This enables the visualization of the IoT systems.

IoT Design and Simulation 3
Table of Contents
Abstract............................................................................................................................................2
1 Introduction...................................................................................................................................4
1.1 Hardware Platform............................................................................................................4
1.2 Physical channel................................................................................................................5
1.3 Logical channel.................................................................................................................6
1.4 Network topology.............................................................................................................6
1.5 Maintenance......................................................................................................................6
1.6 Data storage.......................................................................................................................7
1.7 Data Access.......................................................................................................................7
1.8 Cost...................................................................................................................................8
2 Security Aspects...........................................................................................................................8
3 Conclusion....................................................................................................................................9
References......................................................................................................................................11
Table of Contents
Abstract............................................................................................................................................2
1 Introduction...................................................................................................................................4
1.1 Hardware Platform............................................................................................................4
1.2 Physical channel................................................................................................................5
1.3 Logical channel.................................................................................................................6
1.4 Network topology.............................................................................................................6
1.5 Maintenance......................................................................................................................6
1.6 Data storage.......................................................................................................................7
1.7 Data Access.......................................................................................................................7
1.8 Cost...................................................................................................................................8
2 Security Aspects...........................................................................................................................8
3 Conclusion....................................................................................................................................9
References......................................................................................................................................11

IoT Design and Simulation 4
IoT Design and Simulation
1 Introduction
Every system that employs the Internet of Things (IoT) is made up of a thousand
interconnections of related objects, these are human beings, the devices and to some extent the
cloud-based services which need to be analyzed critically by the engineers so as to carry out the
real duty of analysis as per the magnitude, Lee I & Lee K (2015). Due to the rising complaints
about the loss of the baggage in the port, there arises a need to deploy an IoT system where the
bags could be monitored from the time the passenger arrives until the moment when they will be
leaving for their various destinations.
The system basically aims at passenger satisfaction at the airport since it ensures less time is
consumed, economically fit for all and above all, it ensures adequate security to the baggage with
the real-time tracking via the use of the cloud service, Dawson, DiLuoffo, Kendzierski &
Seaman (2015). This system incorporates four components that ensure overall functionality;
these are the internet connection, the sensors and the actuators for the data transfer in a real-time
manner over the designed network¸ the network protocols with well-established gateways for the
translation of the protocols and finally the Back-end for the storage of the data.
1.1 Hardware Platform
The system under development is basically meant to target the use of the “Real-Time
Operating System” RTOS with the benefit of multitasking, task prioritization, and resource
sharing. The RTOS processes data without any delay with the buffering process, Dietrich,
Hoffmann & Lohmann (2017). The airport system will involve a number of sensors and
actuators, this will help in keeping track of all the movement of the bags before it reaches the
IoT Design and Simulation
1 Introduction
Every system that employs the Internet of Things (IoT) is made up of a thousand
interconnections of related objects, these are human beings, the devices and to some extent the
cloud-based services which need to be analyzed critically by the engineers so as to carry out the
real duty of analysis as per the magnitude, Lee I & Lee K (2015). Due to the rising complaints
about the loss of the baggage in the port, there arises a need to deploy an IoT system where the
bags could be monitored from the time the passenger arrives until the moment when they will be
leaving for their various destinations.
The system basically aims at passenger satisfaction at the airport since it ensures less time is
consumed, economically fit for all and above all, it ensures adequate security to the baggage with
the real-time tracking via the use of the cloud service, Dawson, DiLuoffo, Kendzierski &
Seaman (2015). This system incorporates four components that ensure overall functionality;
these are the internet connection, the sensors and the actuators for the data transfer in a real-time
manner over the designed network¸ the network protocols with well-established gateways for the
translation of the protocols and finally the Back-end for the storage of the data.
1.1 Hardware Platform
The system under development is basically meant to target the use of the “Real-Time
Operating System” RTOS with the benefit of multitasking, task prioritization, and resource
sharing. The RTOS processes data without any delay with the buffering process, Dietrich,
Hoffmann & Lohmann (2017). The airport system will involve a number of sensors and
actuators, this will help in keeping track of all the movement of the bags before it reaches the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IoT Design and Simulation 5
final owner-passenger. The most important sensor to be used is the image sensor whereby it will
be responsible for capturing the movement of the baggage and the passengers through the
already set IoT network infrastructure. Together with this, the system will incorporate the motion
sensors to monitor all the movements of the staff members and the passengers within the airport.
RFID tags will also be applied in this system to track the location and movement of the RFID the
luggage’s of each specific individual.
1.2 Physical channel
Given the fact that the system targets a small range, the IoT system will mainly use the
Bluetooth and the Zigbee as the main channels for communication. These provide an avenue
where communication can take place easily without the interference by other systems within the
organization. The Bluetooth Low Energy (BLE) provides a channel in which the system can run
on even with a low power supply, Andersen, Fierro & Culler (2016). The Baggage system uses
this personal area network (PAN) to connect the sensors and the other infrastructure for the
overall process. On the other hand, a meshed network can be used to automate the sensors within
the airport. Through this medium distance, the Zigbee carries some amounts of data from one
device to the other, for instance from a one sensor node directly to the other nodes to the final
gateway.
Since most of the operations in the airport are run on a full-time basis (24 hours system), this
requires devices with low power consumption. To utilize this, the Baggage system uses the
Zigbee channel to connect with several devices while economizing on the input power. With the
laid standards on the use of the Bluetooth technology, the Airport system will be easily adaptable
and replaceable given that fact that this employed technology focuses much on the outcome of
data transfer without compromising the user battery and the power supply. Given that the airport
final owner-passenger. The most important sensor to be used is the image sensor whereby it will
be responsible for capturing the movement of the baggage and the passengers through the
already set IoT network infrastructure. Together with this, the system will incorporate the motion
sensors to monitor all the movements of the staff members and the passengers within the airport.
RFID tags will also be applied in this system to track the location and movement of the RFID the
luggage’s of each specific individual.
1.2 Physical channel
Given the fact that the system targets a small range, the IoT system will mainly use the
Bluetooth and the Zigbee as the main channels for communication. These provide an avenue
where communication can take place easily without the interference by other systems within the
organization. The Bluetooth Low Energy (BLE) provides a channel in which the system can run
on even with a low power supply, Andersen, Fierro & Culler (2016). The Baggage system uses
this personal area network (PAN) to connect the sensors and the other infrastructure for the
overall process. On the other hand, a meshed network can be used to automate the sensors within
the airport. Through this medium distance, the Zigbee carries some amounts of data from one
device to the other, for instance from a one sensor node directly to the other nodes to the final
gateway.
Since most of the operations in the airport are run on a full-time basis (24 hours system), this
requires devices with low power consumption. To utilize this, the Baggage system uses the
Zigbee channel to connect with several devices while economizing on the input power. With the
laid standards on the use of the Bluetooth technology, the Airport system will be easily adaptable
and replaceable given that fact that this employed technology focuses much on the outcome of
data transfer without compromising the user battery and the power supply. Given that the airport
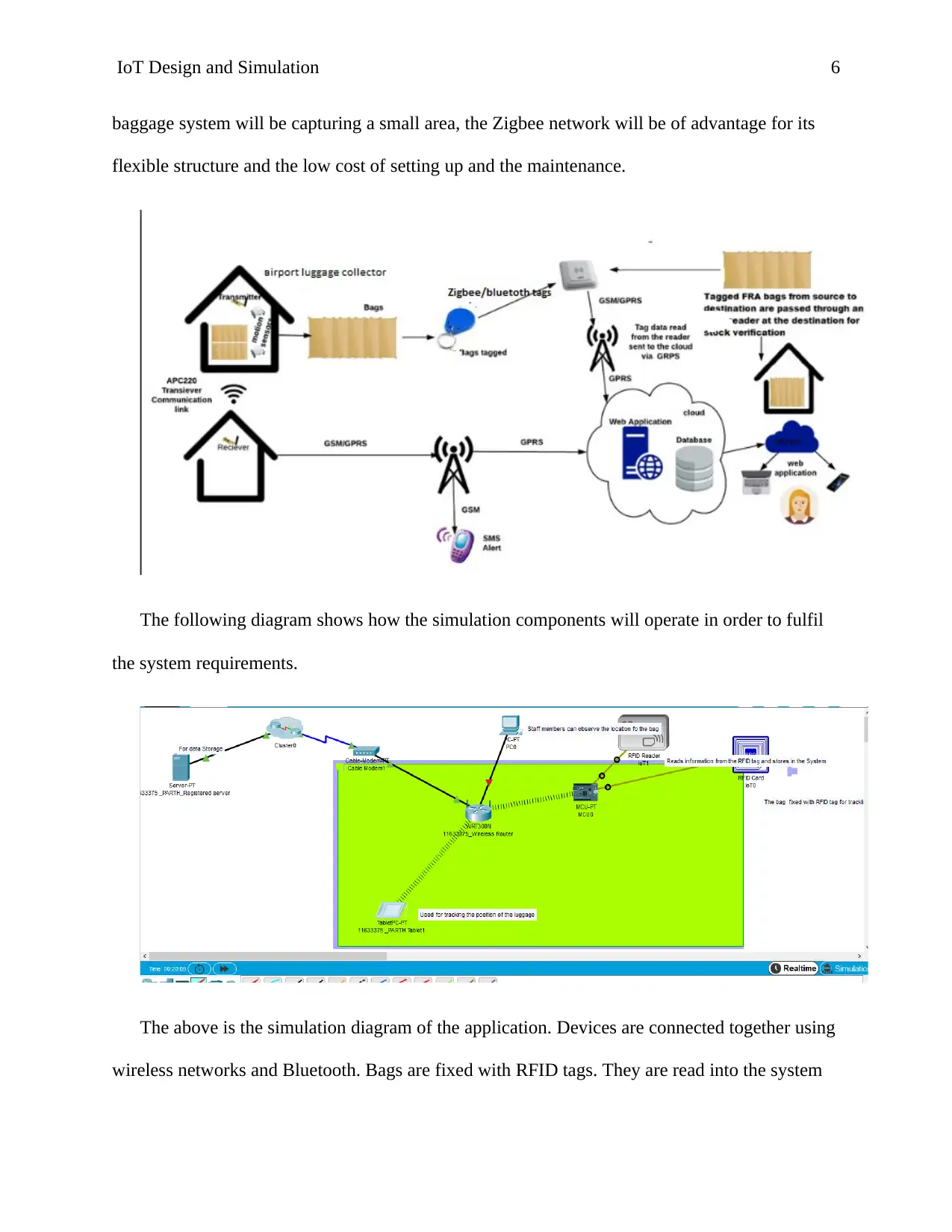
IoT Design and Simulation 6
baggage system will be capturing a small area, the Zigbee network will be of advantage for its
flexible structure and the low cost of setting up and the maintenance.
The following diagram shows how the simulation components will operate in order to fulfil
the system requirements.
The above is the simulation diagram of the application. Devices are connected together using
wireless networks and Bluetooth. Bags are fixed with RFID tags. They are read into the system
baggage system will be capturing a small area, the Zigbee network will be of advantage for its
flexible structure and the low cost of setting up and the maintenance.
The following diagram shows how the simulation components will operate in order to fulfil
the system requirements.
The above is the simulation diagram of the application. Devices are connected together using
wireless networks and Bluetooth. Bags are fixed with RFID tags. They are read into the system

IoT Design and Simulation 7
using RFID readers. This information is then used for locating the location of the devices. The
information is then stored in the IOT server in cloud. This information is then accessed using
mobile applications. Thus, reducing the loss cases of luggage in the airports.
1.3 Logical channel
Communication within the network infrastructure eases the overall functioning of the airport
system. Every information that needs to be relayed to the other device needs to be packed in
form of a packet over the Internet Protocol (IP). The Airport baggage system utilizes the
Message Queuing Telemetry Transport protocol (MQTT) in which the messages are sent and
commands sent for controlling the output devices, reading of information and the publication of
the data from any sensor at a given node. Together with the ZigBee channel, a connection
between several devices can be made easier hence faster communication. On the other hand,
since the system will be a kind of distributed system, then the Hypertext Transfer Protocol
(HTTP) can be utilized for the object management within the infrastructure. With no connection,
the protocol allows being used widely since it involves little or no disturbance.
1.4 Network topology
Having discussed the physical and the logical channels in details, the system has it
predefined network topology through which the nodes and the line of connection will be
arranged together in the overall structure. Mesh topology matches with the channels discussed
above since there is a connection to every node and the devices. The Routing type topology
provides a platform where the data reaches the endpoint within a very short distance and allows
for robust connection while ensuring a flexible connection. The connected nodes facilitate the
data transfer among every other node in a manner in which the data flow without any
using RFID readers. This information is then used for locating the location of the devices. The
information is then stored in the IOT server in cloud. This information is then accessed using
mobile applications. Thus, reducing the loss cases of luggage in the airports.
1.3 Logical channel
Communication within the network infrastructure eases the overall functioning of the airport
system. Every information that needs to be relayed to the other device needs to be packed in
form of a packet over the Internet Protocol (IP). The Airport baggage system utilizes the
Message Queuing Telemetry Transport protocol (MQTT) in which the messages are sent and
commands sent for controlling the output devices, reading of information and the publication of
the data from any sensor at a given node. Together with the ZigBee channel, a connection
between several devices can be made easier hence faster communication. On the other hand,
since the system will be a kind of distributed system, then the Hypertext Transfer Protocol
(HTTP) can be utilized for the object management within the infrastructure. With no connection,
the protocol allows being used widely since it involves little or no disturbance.
1.4 Network topology
Having discussed the physical and the logical channels in details, the system has it
predefined network topology through which the nodes and the line of connection will be
arranged together in the overall structure. Mesh topology matches with the channels discussed
above since there is a connection to every node and the devices. The Routing type topology
provides a platform where the data reaches the endpoint within a very short distance and allows
for robust connection while ensuring a flexible connection. The connected nodes facilitate the
data transfer among every other node in a manner in which the data flow without any
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IoT Design and Simulation 8
interruption. Through this connection, routers can be connected along for the efficiency of the
data being relayed.
The topology Implemented is as shown.
1.5 Maintenance
With the Internet of Things, equipment is monitored for any failure and a notification sent to
the concerned personnel for replacement of any part as required. Through this, effective
maintenance can only be done at the instance when required hence minimizing other costs that
are associated with replacing the whole infrastructure, Sánchez-Silva, Frangopol, Padgett &
Soliman (2016). With the real-time data analysis aspect, the airport staff is able to predict any
associated failure from the system since the sensors in use report the condition of any operation.
Through this, the managers will only incur little maintenance costs compared to the manual
checkup and the overall replacement when the system is used until the point of total failure.
1.6 Data storage
Elastic cloud storage is practically applicable in the airport baggage system since it provides
the analytical tools for manipulating the data. The gateways provide endpoints from where the
interruption. Through this connection, routers can be connected along for the efficiency of the
data being relayed.
The topology Implemented is as shown.
1.5 Maintenance
With the Internet of Things, equipment is monitored for any failure and a notification sent to
the concerned personnel for replacement of any part as required. Through this, effective
maintenance can only be done at the instance when required hence minimizing other costs that
are associated with replacing the whole infrastructure, Sánchez-Silva, Frangopol, Padgett &
Soliman (2016). With the real-time data analysis aspect, the airport staff is able to predict any
associated failure from the system since the sensors in use report the condition of any operation.
Through this, the managers will only incur little maintenance costs compared to the manual
checkup and the overall replacement when the system is used until the point of total failure.
1.6 Data storage
Elastic cloud storage is practically applicable in the airport baggage system since it provides
the analytical tools for manipulating the data. The gateways provide endpoints from where the

IoT Design and Simulation 9
information could be obtained in a real-time case. In case of an alert, it will be very simple to
relay the information by the sensors to the designed devices easily both for a situational or an
emotional alert. Most of the information collected is in the heterogeneous mode, Bosworth, Alla,
Splaine, Shivampet, & Gaynor (2018). While the protocols used and the channels mainly use the
low bandwidth, during times when the data coverage is higher, the data could be easily pushed to
the cloud in a real-time manner. Utilizing the cloud storage service for the airport baggage
system will ensure a continuous flow of data from the sensor edge all the way to the deepest
cloud section. Most of the sensors are meant to locally store the data. For the Internet of Things
to take over, the collected data by the sensor is further pushed to the cloud for storage.
1.7 Data Access
The data sensors have the data access component integrated within them for the coordination
of the manipulation of all the data within the airport baggage system. The internet connection
should be very reliable so as to allow the sensors to capture the most needed data with a lot of
ease. Security is a paramount factor of concern, the data from the cloud is encrypted first before
they are being accessed back by the user. Each and every sensor installed collects the
information needed and relays through the network infrastructure, for this data to be accessed,
the endpoint connected to the internet picks the most important in terms of the baggage handling
scenario and encrypts it. This increases the security aspect for the data hence will determine the
access level when it comes to retrieval of the same information. Cloud data easily access unlike
when stored locally. With the analytical tools in place, each authorized staff member is able to
visualize the data and explore more and more in the cloud. This data can then be accessed using
mobile phones.
information could be obtained in a real-time case. In case of an alert, it will be very simple to
relay the information by the sensors to the designed devices easily both for a situational or an
emotional alert. Most of the information collected is in the heterogeneous mode, Bosworth, Alla,
Splaine, Shivampet, & Gaynor (2018). While the protocols used and the channels mainly use the
low bandwidth, during times when the data coverage is higher, the data could be easily pushed to
the cloud in a real-time manner. Utilizing the cloud storage service for the airport baggage
system will ensure a continuous flow of data from the sensor edge all the way to the deepest
cloud section. Most of the sensors are meant to locally store the data. For the Internet of Things
to take over, the collected data by the sensor is further pushed to the cloud for storage.
1.7 Data Access
The data sensors have the data access component integrated within them for the coordination
of the manipulation of all the data within the airport baggage system. The internet connection
should be very reliable so as to allow the sensors to capture the most needed data with a lot of
ease. Security is a paramount factor of concern, the data from the cloud is encrypted first before
they are being accessed back by the user. Each and every sensor installed collects the
information needed and relays through the network infrastructure, for this data to be accessed,
the endpoint connected to the internet picks the most important in terms of the baggage handling
scenario and encrypts it. This increases the security aspect for the data hence will determine the
access level when it comes to retrieval of the same information. Cloud data easily access unlike
when stored locally. With the analytical tools in place, each authorized staff member is able to
visualize the data and explore more and more in the cloud. This data can then be accessed using
mobile phones.

IoT Design and Simulation 10
1.8 Cost
Human labor is becoming more unreliable in modern airports, this is due to the fact that most
of the baggage fails to reach their destination. The use of the IoT system saves much on the cost
since nearly all the sensors used for the IoT system and the data storage facilities are falling
tremendously. This propagates the adoption of the IoT application easily. The implementation of
this IoT based airport baggage system focuses on cutting the cost of the manpower used in the
management of baggage. Even though the initial capital for setting up the system may seem to be
higher, having deployed the system will be of much importance since most of the work done is
just some little maintenance which is less costly compared to the manual labor that could have
otherwise been used. Through this, the airport will minimize the cost while maximizing profits.
2 Security Aspects
The developed system brings security as a factor to be considered. It’s one of the
paramount requirements for the design. The system uses the Wi-Fi, the NFC tags for the
regulation of the staff members within the airport while on the other hand emphasizes on the
streamlines the checkpoint with the biometrics for instance the facial recognition so as to reduce
the loss of bags and the regulation of the passenger traffic, Evans, Marcel, Ross & Teoh (2015).
With the cloud storage in use, data security becomes a major problem that should be well taken
care of. Data security transfer becomes the first option to consider. Before any data is transferred
from one sensor to the other node in the system, there should be a security feature to ensure no
information is lost to the outsiders.
The airport baggage system ensures security through the use of proper user interfaces to
the staff members. Through this well-designed interface, the data integrity is preserved and all
the truthful information of a given data set perseveres. Cryptography can be applied to ensure all
1.8 Cost
Human labor is becoming more unreliable in modern airports, this is due to the fact that most
of the baggage fails to reach their destination. The use of the IoT system saves much on the cost
since nearly all the sensors used for the IoT system and the data storage facilities are falling
tremendously. This propagates the adoption of the IoT application easily. The implementation of
this IoT based airport baggage system focuses on cutting the cost of the manpower used in the
management of baggage. Even though the initial capital for setting up the system may seem to be
higher, having deployed the system will be of much importance since most of the work done is
just some little maintenance which is less costly compared to the manual labor that could have
otherwise been used. Through this, the airport will minimize the cost while maximizing profits.
2 Security Aspects
The developed system brings security as a factor to be considered. It’s one of the
paramount requirements for the design. The system uses the Wi-Fi, the NFC tags for the
regulation of the staff members within the airport while on the other hand emphasizes on the
streamlines the checkpoint with the biometrics for instance the facial recognition so as to reduce
the loss of bags and the regulation of the passenger traffic, Evans, Marcel, Ross & Teoh (2015).
With the cloud storage in use, data security becomes a major problem that should be well taken
care of. Data security transfer becomes the first option to consider. Before any data is transferred
from one sensor to the other node in the system, there should be a security feature to ensure no
information is lost to the outsiders.
The airport baggage system ensures security through the use of proper user interfaces to
the staff members. Through this well-designed interface, the data integrity is preserved and all
the truthful information of a given data set perseveres. Cryptography can be applied to ensure all
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IoT Design and Simulation 11
the data privacy rights are maintained. Access to information should be considered through the
various user levels, not all the staff members have the same privilege when it comes to accessing
the information. As a security feature, access to the information in the Internet of Things (IoT)
system should be specified via the use of the access controls to ensure protection to the system
and its resources, Fontijn, Talstra, Newton & Holtman (2015). The main method of protection in
use here is the cryptography technique from where the system ensures maximum security over
all the IoT information in the cloud storage.
3 Conclusion
In this paper, we compare the manual bags handling and the new IoT-based system for
bag handling in the airports and conclude that none of the human methods can fully satisfy the
passenger needs while the security factor is concerned. With the diverse requirements of the IoT
system, the generic development becomes a challenge in curbing the overall safety of the
passenger bags. Data security is considered to be the most essential factor in ensuring the privacy
of any information being relayed over the network. As a closing remark, the development of the
IoT based baggage system will not only ensure data security but also ensure customer
satisfaction within the airport hence building trust among the passengers resulting to more
operations within the airport.
the data privacy rights are maintained. Access to information should be considered through the
various user levels, not all the staff members have the same privilege when it comes to accessing
the information. As a security feature, access to the information in the Internet of Things (IoT)
system should be specified via the use of the access controls to ensure protection to the system
and its resources, Fontijn, Talstra, Newton & Holtman (2015). The main method of protection in
use here is the cryptography technique from where the system ensures maximum security over
all the IoT information in the cloud storage.
3 Conclusion
In this paper, we compare the manual bags handling and the new IoT-based system for
bag handling in the airports and conclude that none of the human methods can fully satisfy the
passenger needs while the security factor is concerned. With the diverse requirements of the IoT
system, the generic development becomes a challenge in curbing the overall safety of the
passenger bags. Data security is considered to be the most essential factor in ensuring the privacy
of any information being relayed over the network. As a closing remark, the development of the
IoT based baggage system will not only ensure data security but also ensure customer
satisfaction within the airport hence building trust among the passengers resulting to more
operations within the airport.

IoT Design and Simulation 12
References
Andersen, M. P., Fierro, G., & Culler, D. E. (2016, April). System design for a synergistic, low
power mote/BLE embedded platform. In Information Processing in Sensor Networks
(IPSN), 2016 15th ACM/IEEE International Conference on (pp. 1-12). IEEE.
Bosworth, A. N., Alla, M. R., Splaine, S. J., Shivampet, B. R., & Gaynor, K. K. (2018). U.S.
Patent No. 9,979,544. Washington, DC: U.S. Patent and Trademark Office.
Dawson, C. J., DiLuoffo, V. V., Kendzierski, M. D., & Seaman, J. W. (2015). U.S. Patent No.
9,009,294. Washington, DC: U.S. Patent and Trademark Office.
Dietrich, C., Hoffmann, M., & Lohmann, D. (2017). Global optimization of fixed-priority real-
time systems by RTOS-aware control-flow analysis. ACM Transactions on Embedded
Computing Systems (TECS), 16(2), 35.
Evans, N., Marcel, S., Ross, A., & Teoh, A. B. J. (2015). Biometrics security and privacy
protection [from the guest editors]. IEEE Signal Processing Magazine, 32(5), 17-18.
Fontijn, W. F. J., Talstra, J. C., Newton, P. S., & Holtman, K. J. G. (2015). U.S. Patent No.
9,202,045. Washington, DC: U.S. Patent and Trademark Office.
Lee, I., & Lee, K. (2015). The Internet of Things (IoT): Applications, investments, and
challenges for enterprises. Business Horizons, 58(4), 431-440.
Sánchez-Silva, M., Frangopol, D. M., Padgett, J., & Soliman, M. (2016). Maintenance and
operation of infrastructure systems. Journal of Structural Engineering, 142(9),
F4016004.
References
Andersen, M. P., Fierro, G., & Culler, D. E. (2016, April). System design for a synergistic, low
power mote/BLE embedded platform. In Information Processing in Sensor Networks
(IPSN), 2016 15th ACM/IEEE International Conference on (pp. 1-12). IEEE.
Bosworth, A. N., Alla, M. R., Splaine, S. J., Shivampet, B. R., & Gaynor, K. K. (2018). U.S.
Patent No. 9,979,544. Washington, DC: U.S. Patent and Trademark Office.
Dawson, C. J., DiLuoffo, V. V., Kendzierski, M. D., & Seaman, J. W. (2015). U.S. Patent No.
9,009,294. Washington, DC: U.S. Patent and Trademark Office.
Dietrich, C., Hoffmann, M., & Lohmann, D. (2017). Global optimization of fixed-priority real-
time systems by RTOS-aware control-flow analysis. ACM Transactions on Embedded
Computing Systems (TECS), 16(2), 35.
Evans, N., Marcel, S., Ross, A., & Teoh, A. B. J. (2015). Biometrics security and privacy
protection [from the guest editors]. IEEE Signal Processing Magazine, 32(5), 17-18.
Fontijn, W. F. J., Talstra, J. C., Newton, P. S., & Holtman, K. J. G. (2015). U.S. Patent No.
9,202,045. Washington, DC: U.S. Patent and Trademark Office.
Lee, I., & Lee, K. (2015). The Internet of Things (IoT): Applications, investments, and
challenges for enterprises. Business Horizons, 58(4), 431-440.
Sánchez-Silva, M., Frangopol, D. M., Padgett, J., & Soliman, M. (2016). Maintenance and
operation of infrastructure systems. Journal of Structural Engineering, 142(9),
F4016004.
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





