Smart Home Security and Privacy in IoT
VerifiedAdded on 2020/05/16
|9
|8918
|66
AI Summary
This assignment delves into the security and privacy concerns associated with smart home technologies within the Internet of Things (IoT) landscape. Students are tasked with examining relevant research papers, focusing on the vulnerabilities and potential risks inherent in interconnected smart devices within a home setting. The analysis should encompass various aspects such as data breaches, unauthorized access, and the misuse of personal information gathered by smart home systems. Additionally, students are expected to evaluate proposed solutions and strategies aimed at mitigating these security and privacy threats, ultimately contributing to a safer and more secure connected living environment.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

IoT in Smart Home
Name of the Student
Name of the University
Student Number
Course ID
Email Address of Student
Abstract— the report reflects the development of the network
level security to the IoT based smart home. The IoT is the
abbreviation of internet of things. Five methodologies of
developing the security in the smart home has been discussed in
the report Based on the flexibility and impact the network level
security implementation through the SMP (security management
provider) has been selected.
Keywords— IoT; cloud; SMP; smart home; nerwork; device
management; network architecture; synthetic packet; ISP; Sensor
1. INTRODUCTION
The Internet of Things were developed with the purpose of
connecting various electronic components to the internet and
gathering data or condoling electronic device from remote
locations. The IoT is capable of supporting various day-to-
applications. Various organizations are putting effort in making
new IoT technologies that can be used for facilitating the
business process or selling. One of the most popular method of
using the IoT is the application in the smart homes. In the smart
home concept, various IoT devices (electronic devices) are
connected with each other through wire or wireless
communication medium. These devices can also communicate
with each other to execute a process. The homes are becoming
extensively smart due to use of the IoT devices. These smart
homes are often connected to a cloud environment computing
system so that the owner of the house can control it from remote
location. As the data from the smart home IoT network travels
to the server wirelessly, the device becomes extremely
vulnerable to cyber-attacks.
At the beginning of the report, the main considerations has
been the security issues and smart home network related
solutions. Then various arguments will be proposed in the
context of security implementations. In the literature review
part, the security issues of the smart home has been discussed.
Based on the major issues or the issues that is relevantly new
will be focused upon. After proper analysis of the circumstances
and available IoT technology, the solution to the security issue
will be provided.
The main problem of the project is to identify the security
issues that is most harmful and providing an utmost solution to
it which can be implemented irrespective of the IoT technology
platform. The report is focused upon a project with the
deliverable of developing a network level security for the
security. In the recent years it has been seen that various attacks
has been executed on the smart homes successfully. The report
provides details of the future works that can be don later on this
project outcome.
2. BACKGROUND/LITERATURE REVIEW
In order to discuss bout the smart home security issues, the
details of the architecture, network, components used and
much more things need to be considered. All the entities that
make up the IoT based smart home system can be exploited by
the cybercriminals to hack into the smart home. At the
beginning of the literature review, the idea of a typical smart
home architecture will be provided.
2.1 Architecture of Smart Home Based on IoT
The smart homes are the combination of different
electronic components and a network. The electronic
components are sensors, controllers, circuits and many more.
The applications are developed for the user mobile device
(smart phones) so the users can control the operations of the
IoT based smart home from distance. The connection is a
significant part of the homes as this makes the smart home a
really advanced technology. These entities are utilized for
designing and developing a dynamic heterogeneous
architecture [6]. These architecture remains the source of smart
home operations. The quality and advancement in the
architecture defines the amount of operations that the smart
home will be performing. The IoT devices is not equipped with
interoperability standards and that is why the connected IoT
devices in a smart home architecture can be controlled directly
via a smartphone or other device. The sensors that are used
within the smart home environment does not have the feature
of connecting to the internet directly [11]. In reality, the
sensors does not have any direct connection with the internet,
the microcontroller provides them all the instruction through
the output ports of it.
Fig 1 Architecture of a typical Smart Home [1]
The internet connection is established in the hub of the
network. The hub works as the local workstation in the smart
home architecture. Basically wireless communication mediums
Name of the Student
Name of the University
Student Number
Course ID
Email Address of Student
Abstract— the report reflects the development of the network
level security to the IoT based smart home. The IoT is the
abbreviation of internet of things. Five methodologies of
developing the security in the smart home has been discussed in
the report Based on the flexibility and impact the network level
security implementation through the SMP (security management
provider) has been selected.
Keywords— IoT; cloud; SMP; smart home; nerwork; device
management; network architecture; synthetic packet; ISP; Sensor
1. INTRODUCTION
The Internet of Things were developed with the purpose of
connecting various electronic components to the internet and
gathering data or condoling electronic device from remote
locations. The IoT is capable of supporting various day-to-
applications. Various organizations are putting effort in making
new IoT technologies that can be used for facilitating the
business process or selling. One of the most popular method of
using the IoT is the application in the smart homes. In the smart
home concept, various IoT devices (electronic devices) are
connected with each other through wire or wireless
communication medium. These devices can also communicate
with each other to execute a process. The homes are becoming
extensively smart due to use of the IoT devices. These smart
homes are often connected to a cloud environment computing
system so that the owner of the house can control it from remote
location. As the data from the smart home IoT network travels
to the server wirelessly, the device becomes extremely
vulnerable to cyber-attacks.
At the beginning of the report, the main considerations has
been the security issues and smart home network related
solutions. Then various arguments will be proposed in the
context of security implementations. In the literature review
part, the security issues of the smart home has been discussed.
Based on the major issues or the issues that is relevantly new
will be focused upon. After proper analysis of the circumstances
and available IoT technology, the solution to the security issue
will be provided.
The main problem of the project is to identify the security
issues that is most harmful and providing an utmost solution to
it which can be implemented irrespective of the IoT technology
platform. The report is focused upon a project with the
deliverable of developing a network level security for the
security. In the recent years it has been seen that various attacks
has been executed on the smart homes successfully. The report
provides details of the future works that can be don later on this
project outcome.
2. BACKGROUND/LITERATURE REVIEW
In order to discuss bout the smart home security issues, the
details of the architecture, network, components used and
much more things need to be considered. All the entities that
make up the IoT based smart home system can be exploited by
the cybercriminals to hack into the smart home. At the
beginning of the literature review, the idea of a typical smart
home architecture will be provided.
2.1 Architecture of Smart Home Based on IoT
The smart homes are the combination of different
electronic components and a network. The electronic
components are sensors, controllers, circuits and many more.
The applications are developed for the user mobile device
(smart phones) so the users can control the operations of the
IoT based smart home from distance. The connection is a
significant part of the homes as this makes the smart home a
really advanced technology. These entities are utilized for
designing and developing a dynamic heterogeneous
architecture [6]. These architecture remains the source of smart
home operations. The quality and advancement in the
architecture defines the amount of operations that the smart
home will be performing. The IoT devices is not equipped with
interoperability standards and that is why the connected IoT
devices in a smart home architecture can be controlled directly
via a smartphone or other device. The sensors that are used
within the smart home environment does not have the feature
of connecting to the internet directly [11]. In reality, the
sensors does not have any direct connection with the internet,
the microcontroller provides them all the instruction through
the output ports of it.
Fig 1 Architecture of a typical Smart Home [1]
The internet connection is established in the hub of the
network. The hub works as the local workstation in the smart
home architecture. Basically wireless communication mediums
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

are selected for establishing the communication between the
hubs and the IoT devices installed in the home. Different
manufacturers of the IoT devices develop their devices based
on different protocols. These protocols are followed by the
architecture while developing the sensor-hub connection. The
hub is connected to the internet connection available at home
via Wi-Fi interface or the Ethernet connection. This decision
depends upon the capabilities of the IoT architecture’s in order
to communicate with the outside world. The quality of
interaction will be judged based on two phenomenon such as
access to internet cloud services that act together with the hub
and properly connected to the IoT elements [1]. The second
phenomenon is direct interaction with the hub through the
internet through the use of the connectivity and services that
hub offers.
The remote interaction with the IoT devices are often done
by considering the above two options. These two phenomenon
must be considered simultaneously while developing the IoT
architecture best remote interaction experience can be provided
to user. There are basically two modes defined in the
architecture to forward instructions from the user device to the
hub [24]. The first one is through the cloud service while the
user is sending instruction from remote location outside the
range of the local network. The second is directly to the hub
through the hub while the user is within the local network. In
the later, no internet access is required as the network (Ethernet
or Wi-Fi) sends the instructions sends the information using
local connection.
2.2 Components of IoT smart home
This device is considered as a lovely alarm clock that is
technologically advanced from the conventional ones. This
device remains close to the bed and analyze the environment in
the room during and before sleep [3]. In order to analyze the
environment, the device uses the state-of-art sensors.
Monitoring devices are used for total monitoring of the
home based IoT system. These devices are connected to the
hub or often used as the hub in case of small scale IoT
implementation. Smart thermostats are used for automation in
the temperature of the home. Wireless speaker systems are a
favorite IoT technology of various smart home owners. This
speakers can be connected from anywhere at the home and
play music wirelessly. Smart lights are used for controlling the
lights of the rooms wirelessly through mobile device or
automatically switch off or on the bulbs [22]. The hub is the
key of connecting the devices to the user device. Various other
IoT devices are used in the smart home that has not been
discussed in this report.
2.3 Privacy Vulnerability
The patterns, contents and metadata of the network traffic
is consisting of various sensitive information of the user of the
smart home. If these entities are hacked by the cybercriminals,
then all the sensitive data will be revealed to the attacker. The
websites were the only way of communicating with the internet
based resources, but with the emerging of cloud and IoT the
usage of the internet has become a vast concept [3]. The IoT
smart home is also connected to the user mobile device, so it
the network of smart home is hacked, the cybercriminals will
get a way to the mobile device in an unauthorized way. The
mobile devices can be hacked for getting personal data of the
user.
2.3.1 IoT traffic analysis strategy
It has been a great way of securing the traffic from the user
device to the IoT hub. In this traffic strategy, the packets will
be considered as the main part to examine. The IP address
adversary can be prevented using the division of traffic packets
as per device strategy are being used. In this methodology, the
network traffic is divided into streams of meaningful data. The
home gateway routers are basically used as the NAT or
network address translator. The purpose of the NAT is to
overwrite the IP address of various IoT connected devices a
sole IP address that has been provided by the ISP [3]. There is
an issues in this method as the counting of the various clients
of the NAT is difficult.
After the distinct streams are separated, the identification of
the IoT device that is responsible for individual streams are
done. It is then possible to map the queries of the DNS to the
associated device. The devices that are manufactured by the
same organization, can communicate using the same IP
address.
2.3.2 A Case of sense sleep monitor
As the domains only holds the sense and hello,
identification of traffic to and fro sense sleep monitor is an
easy task.
Fig 2 Sense sleep monitor network traffic send/receive rates [3]
The study has been conducted for a 12 hour period starting
form 10.40 pm to 10.40 am. The user activity is reason of the
send and receive of the packets. The peak between the 5.20 am
to 7 am shows that the user was out of bed temporarily. This
figure shows a general idea regarding how the IoT device
operates automatically on the basis of the user activities. If the
intruders are able to get hand to these kinds of data then they
can identify the daily activities of the user. This will allow the
intruders to target the home easily as they will know when the
home remains empty. Various other circumstances can be
imagined based on the security flaws of the IoT smart home
technology.
2.4 NDOMUS Framework
The NDN or named data networking is the basis of the
Named Data netwOrking for sMart home aUtomation Systems.
The whole architecture is consisting of three layers such as
thing-layer, NDOMUS and application layer. In the thing layer,
the IoT devices are installed in the home [15]. NDOMUS is
consisting of the operations such as routing of packets, security
protocols, caching of data packets, naming strategy,
hubs and the IoT devices installed in the home. Different
manufacturers of the IoT devices develop their devices based
on different protocols. These protocols are followed by the
architecture while developing the sensor-hub connection. The
hub is connected to the internet connection available at home
via Wi-Fi interface or the Ethernet connection. This decision
depends upon the capabilities of the IoT architecture’s in order
to communicate with the outside world. The quality of
interaction will be judged based on two phenomenon such as
access to internet cloud services that act together with the hub
and properly connected to the IoT elements [1]. The second
phenomenon is direct interaction with the hub through the
internet through the use of the connectivity and services that
hub offers.
The remote interaction with the IoT devices are often done
by considering the above two options. These two phenomenon
must be considered simultaneously while developing the IoT
architecture best remote interaction experience can be provided
to user. There are basically two modes defined in the
architecture to forward instructions from the user device to the
hub [24]. The first one is through the cloud service while the
user is sending instruction from remote location outside the
range of the local network. The second is directly to the hub
through the hub while the user is within the local network. In
the later, no internet access is required as the network (Ethernet
or Wi-Fi) sends the instructions sends the information using
local connection.
2.2 Components of IoT smart home
This device is considered as a lovely alarm clock that is
technologically advanced from the conventional ones. This
device remains close to the bed and analyze the environment in
the room during and before sleep [3]. In order to analyze the
environment, the device uses the state-of-art sensors.
Monitoring devices are used for total monitoring of the
home based IoT system. These devices are connected to the
hub or often used as the hub in case of small scale IoT
implementation. Smart thermostats are used for automation in
the temperature of the home. Wireless speaker systems are a
favorite IoT technology of various smart home owners. This
speakers can be connected from anywhere at the home and
play music wirelessly. Smart lights are used for controlling the
lights of the rooms wirelessly through mobile device or
automatically switch off or on the bulbs [22]. The hub is the
key of connecting the devices to the user device. Various other
IoT devices are used in the smart home that has not been
discussed in this report.
2.3 Privacy Vulnerability
The patterns, contents and metadata of the network traffic
is consisting of various sensitive information of the user of the
smart home. If these entities are hacked by the cybercriminals,
then all the sensitive data will be revealed to the attacker. The
websites were the only way of communicating with the internet
based resources, but with the emerging of cloud and IoT the
usage of the internet has become a vast concept [3]. The IoT
smart home is also connected to the user mobile device, so it
the network of smart home is hacked, the cybercriminals will
get a way to the mobile device in an unauthorized way. The
mobile devices can be hacked for getting personal data of the
user.
2.3.1 IoT traffic analysis strategy
It has been a great way of securing the traffic from the user
device to the IoT hub. In this traffic strategy, the packets will
be considered as the main part to examine. The IP address
adversary can be prevented using the division of traffic packets
as per device strategy are being used. In this methodology, the
network traffic is divided into streams of meaningful data. The
home gateway routers are basically used as the NAT or
network address translator. The purpose of the NAT is to
overwrite the IP address of various IoT connected devices a
sole IP address that has been provided by the ISP [3]. There is
an issues in this method as the counting of the various clients
of the NAT is difficult.
After the distinct streams are separated, the identification of
the IoT device that is responsible for individual streams are
done. It is then possible to map the queries of the DNS to the
associated device. The devices that are manufactured by the
same organization, can communicate using the same IP
address.
2.3.2 A Case of sense sleep monitor
As the domains only holds the sense and hello,
identification of traffic to and fro sense sleep monitor is an
easy task.
Fig 2 Sense sleep monitor network traffic send/receive rates [3]
The study has been conducted for a 12 hour period starting
form 10.40 pm to 10.40 am. The user activity is reason of the
send and receive of the packets. The peak between the 5.20 am
to 7 am shows that the user was out of bed temporarily. This
figure shows a general idea regarding how the IoT device
operates automatically on the basis of the user activities. If the
intruders are able to get hand to these kinds of data then they
can identify the daily activities of the user. This will allow the
intruders to target the home easily as they will know when the
home remains empty. Various other circumstances can be
imagined based on the security flaws of the IoT smart home
technology.
2.4 NDOMUS Framework
The NDN or named data networking is the basis of the
Named Data netwOrking for sMart home aUtomation Systems.
The whole architecture is consisting of three layers such as
thing-layer, NDOMUS and application layer. In the thing layer,
the IoT devices are installed in the home [15]. NDOMUS is
consisting of the operations such as routing of packets, security
protocols, caching of data packets, naming strategy,
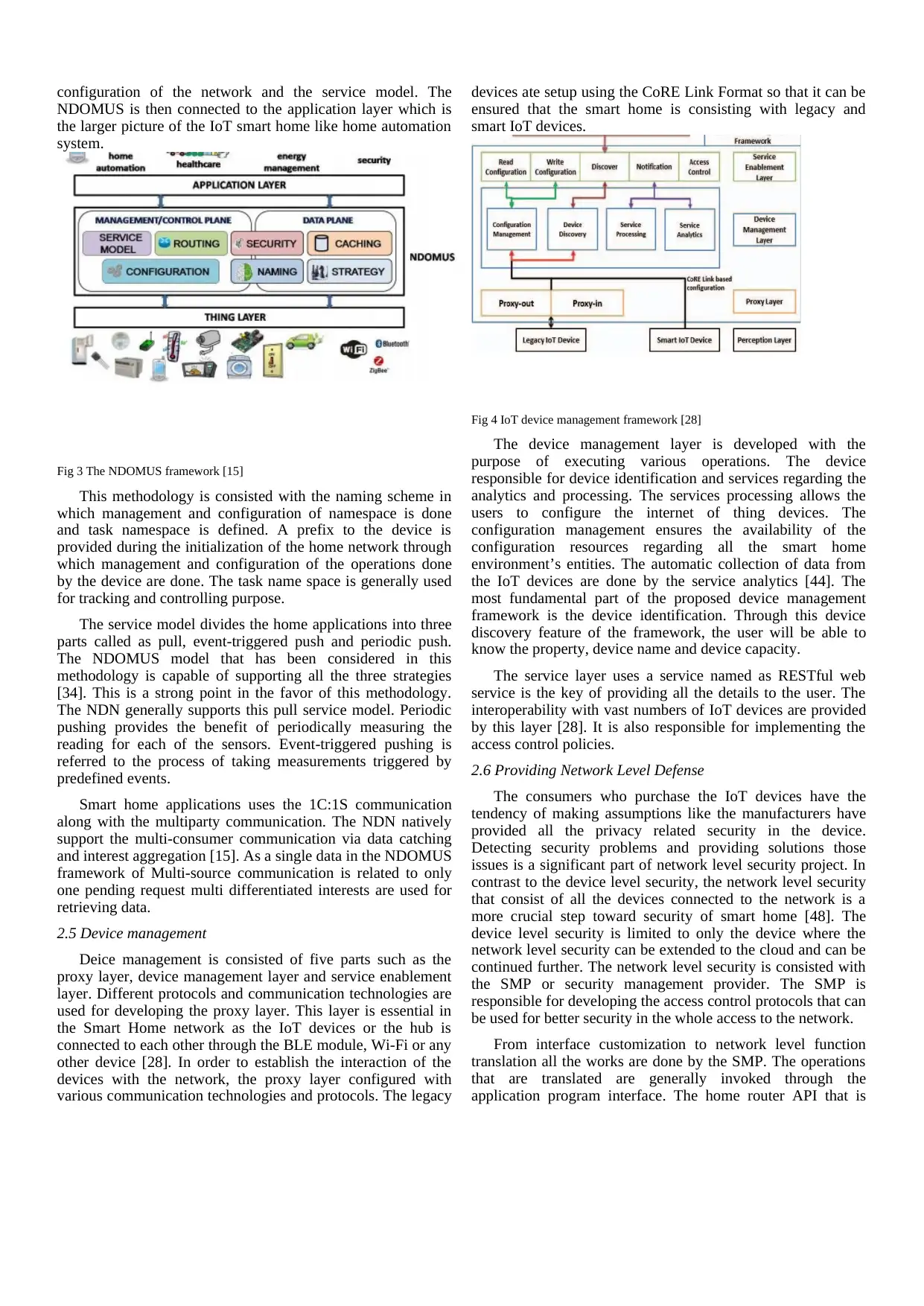
configuration of the network and the service model. The
NDOMUS is then connected to the application layer which is
the larger picture of the IoT smart home like home automation
system.
Fig 3 The NDOMUS framework [15]
This methodology is consisted with the naming scheme in
which management and configuration of namespace is done
and task namespace is defined. A prefix to the device is
provided during the initialization of the home network through
which management and configuration of the operations done
by the device are done. The task name space is generally used
for tracking and controlling purpose.
The service model divides the home applications into three
parts called as pull, event-triggered push and periodic push.
The NDOMUS model that has been considered in this
methodology is capable of supporting all the three strategies
[34]. This is a strong point in the favor of this methodology.
The NDN generally supports this pull service model. Periodic
pushing provides the benefit of periodically measuring the
reading for each of the sensors. Event-triggered pushing is
referred to the process of taking measurements triggered by
predefined events.
Smart home applications uses the 1C:1S communication
along with the multiparty communication. The NDN natively
support the multi-consumer communication via data catching
and interest aggregation [15]. As a single data in the NDOMUS
framework of Multi-source communication is related to only
one pending request multi differentiated interests are used for
retrieving data.
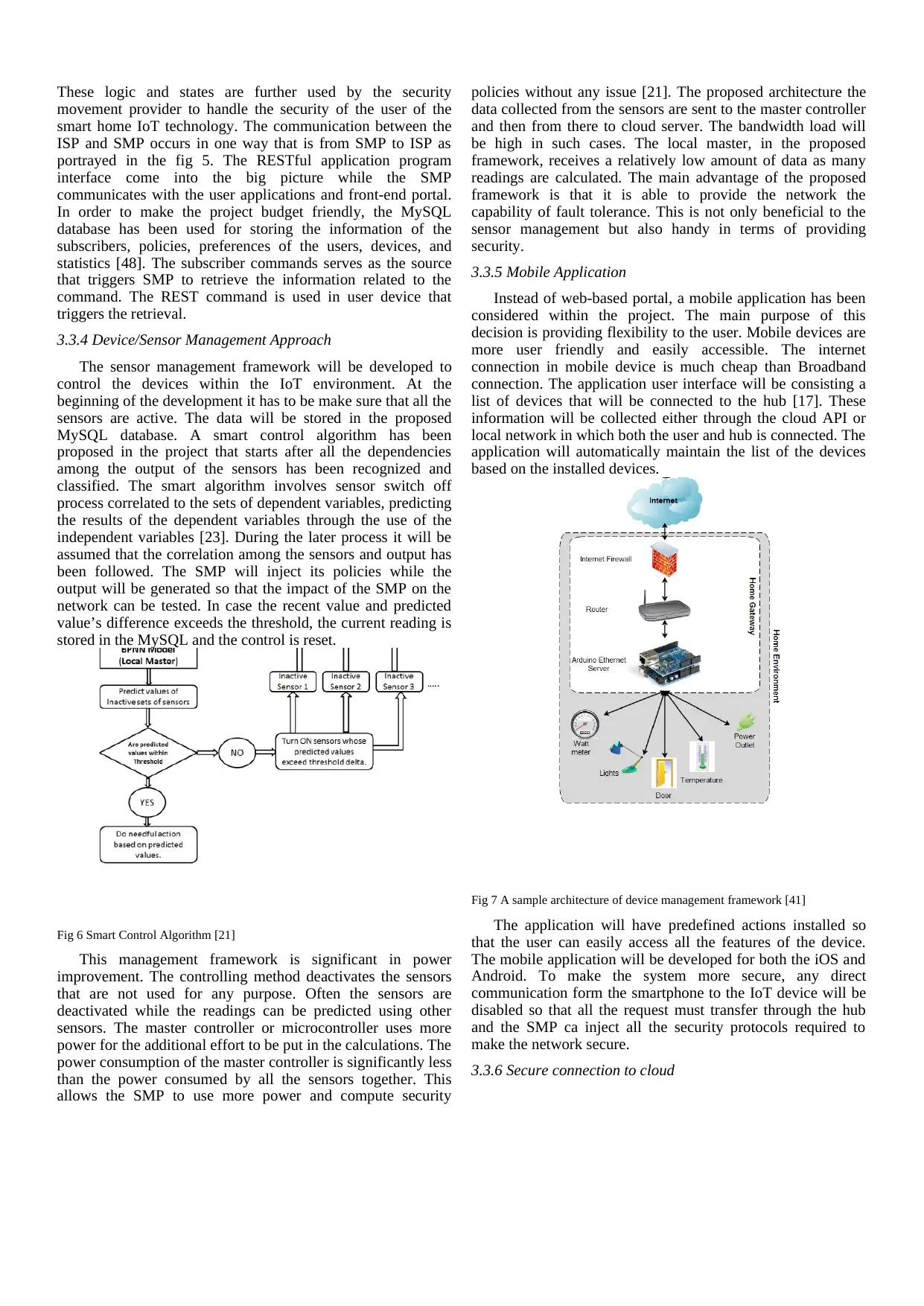
2.5 Device management
Deice management is consisted of five parts such as the
proxy layer, device management layer and service enablement
layer. Different protocols and communication technologies are
used for developing the proxy layer. This layer is essential in
the Smart Home network as the IoT devices or the hub is
connected to each other through the BLE module, Wi-Fi or any
other device [28]. In order to establish the interaction of the
devices with the network, the proxy layer configured with
various communication technologies and protocols. The legacy
devices ate setup using the CoRE Link Format so that it can be
ensured that the smart home is consisting with legacy and
smart IoT devices.
Fig 4 IoT device management framework [28]
The device management layer is developed with the
purpose of executing various operations. The device
responsible for device identification and services regarding the
analytics and processing. The services processing allows the
users to configure the internet of thing devices. The
configuration management ensures the availability of the
configuration resources regarding all the smart home
environment’s entities. The automatic collection of data from
the IoT devices are done by the service analytics [44]. The
most fundamental part of the proposed device management
framework is the device identification. Through this device
discovery feature of the framework, the user will be able to
know the property, device name and device capacity.
The service layer uses a service named as RESTful web
service is the key of providing all the details to the user. The
interoperability with vast numbers of IoT devices are provided
by this layer [28]. It is also responsible for implementing the
access control policies.
2.6 Providing Network Level Defense
The consumers who purchase the IoT devices have the
tendency of making assumptions like the manufacturers have
provided all the privacy related security in the device.
Detecting security problems and providing solutions those
issues is a significant part of network level security project. In
contrast to the device level security, the network level security
that consist of all the devices connected to the network is a
more crucial step toward security of smart home [48]. The
device level security is limited to only the device where the
network level security can be extended to the cloud and can be
continued further. The network level security is consisted with
the SMP or security management provider. The SMP is
responsible for developing the access control protocols that can
be used for better security in the whole access to the network.
From interface customization to network level function
translation all the works are done by the SMP. The operations
that are translated are generally invoked through the
application program interface. The home router API that is
NDOMUS is then connected to the application layer which is
the larger picture of the IoT smart home like home automation
system.
Fig 3 The NDOMUS framework [15]
This methodology is consisted with the naming scheme in
which management and configuration of namespace is done
and task namespace is defined. A prefix to the device is
provided during the initialization of the home network through
which management and configuration of the operations done
by the device are done. The task name space is generally used
for tracking and controlling purpose.
The service model divides the home applications into three
parts called as pull, event-triggered push and periodic push.
The NDOMUS model that has been considered in this
methodology is capable of supporting all the three strategies
[34]. This is a strong point in the favor of this methodology.
The NDN generally supports this pull service model. Periodic
pushing provides the benefit of periodically measuring the
reading for each of the sensors. Event-triggered pushing is
referred to the process of taking measurements triggered by
predefined events.
Smart home applications uses the 1C:1S communication
along with the multiparty communication. The NDN natively
support the multi-consumer communication via data catching
and interest aggregation [15]. As a single data in the NDOMUS
framework of Multi-source communication is related to only
one pending request multi differentiated interests are used for
retrieving data.
2.5 Device management
Deice management is consisted of five parts such as the
proxy layer, device management layer and service enablement
layer. Different protocols and communication technologies are
used for developing the proxy layer. This layer is essential in
the Smart Home network as the IoT devices or the hub is
connected to each other through the BLE module, Wi-Fi or any
other device [28]. In order to establish the interaction of the
devices with the network, the proxy layer configured with
various communication technologies and protocols. The legacy
devices ate setup using the CoRE Link Format so that it can be
ensured that the smart home is consisting with legacy and
smart IoT devices.
Fig 4 IoT device management framework [28]
The device management layer is developed with the
purpose of executing various operations. The device
responsible for device identification and services regarding the
analytics and processing. The services processing allows the
users to configure the internet of thing devices. The
configuration management ensures the availability of the
configuration resources regarding all the smart home
environment’s entities. The automatic collection of data from
the IoT devices are done by the service analytics [44]. The
most fundamental part of the proposed device management
framework is the device identification. Through this device
discovery feature of the framework, the user will be able to
know the property, device name and device capacity.
The service layer uses a service named as RESTful web
service is the key of providing all the details to the user. The
interoperability with vast numbers of IoT devices are provided
by this layer [28]. It is also responsible for implementing the
access control policies.
2.6 Providing Network Level Defense
The consumers who purchase the IoT devices have the
tendency of making assumptions like the manufacturers have
provided all the privacy related security in the device.
Detecting security problems and providing solutions those
issues is a significant part of network level security project. In
contrast to the device level security, the network level security
that consist of all the devices connected to the network is a
more crucial step toward security of smart home [48]. The
device level security is limited to only the device where the
network level security can be extended to the cloud and can be
continued further. The network level security is consisted with
the SMP or security management provider. The SMP is
responsible for developing the access control protocols that can
be used for better security in the whole access to the network.
From interface customization to network level function
translation all the works are done by the SMP. The operations
that are translated are generally invoked through the
application program interface. The home router API that is

capable of supporting an external SMP entity is need to be
considered in this methodology.
2.7 Synthetic packet injection
The main purpose of this methodology is to reduce the
chance of hacking into the IoT based smart home environment
while the messages are transferred between IoT hub and cloud
API. It ensures that traffic analysis is complex enough that no
hacker can attack this system. Though the network uses the
encryption technology, it is not always possible to protect the
data [8]. The passive listening can be used by the hackers to
capture the sequences of initialization vectors that are used in
the protected communication medium. Proper traffic analysis
techniques will be used for establishing the connection
between the servers and the hub. Synthetic packet injection is
particularly designed based on software application. In real
world, injection of the synthetic packet will have the same
impact on the network security as in the simulation. The VPN
serves as a crucial part of this methodology as it is used for
encrypting the packets in the network traffic. The synthetic
packet can be used in the application service and virtual private
network.
3. ISSUES/SOLUTIONS
3.1 Requirement of the project
From the above literature review it has been understood
that providing control and security to the IoT based smart
home is a crucial factor. Various methodologies can be used
for providing the security. It can be done through offering
uninterrupted and secure control over the sensors and devices,
or it can be done through creating a safe and secure network
level security. Inn case of the synthetic packet injection, the
use of the VPN can be a solution to prevent capturing of
packets. Though the attackers cannot monitor the packet
transfer in the network, the main purpose of smart IoT based
home is the real issue in security. The mobile device of the user
can be used for hacking into the system and get access to the
personal data. No matter how much the device is secured from
being hacked, the threat of traffic analysis always remain on
the IoT devices. If the whole network can be secured then it
will be very effective in securing the whole smart home
architecture.
The requirements of the project is an IoT device or sensor,
hub, home router, cloud service API. The cloud service will be
connected to the mobile device. The concept of the device
management framework can be seen in this project. However,
the main focus remains on the network security. The SMP or
security management provider will be developed to secure the
network additionally. The home router must be chosen that can
support the SMP. The project prototype will be developed for
providing various customization options to the users.
3.2 modified problem Statement
Thus the main problem statement is developing the
prototype that will be used for developing the network that can
support security from the device level to cloud level.
Configuration the router to support the security management
provider is another problem of the project.
3.3 Proposed Project and Method of Network-Level Security
3.3.1 Security Management Provider
The project has been developed using a prototype that will
be done considering a three part architecture and application
program interface for providing various advanced options. The
users of the IoT architecture will be able to control the devices
through the cloud service API [48]. Project also proposed the
advancement in the access switch and controlling of the ISP
network modules. The SMP will be responsible for operating a
web based graphical user interface. The Amazon cloud has
been selected for running the SMP and the ISP will in a safe
data-center (not been identified still). Two settings has been
considered while testing the project outcome. The first one is
testing it in campus network that is SDN-enabled and consist
of over than three thousand Wi-Fi access points. The second is
the small amount of houses where the network will be
operating as the OTTor over the top legacy ISP network [37].
Fig 5 Proposed network prototype in the project [48]
3.3.2 Securing Local Network
The figure 5 shows the prototype of the proposed network.
In the project it has been assumed that SDN enabled internet
service providers’ access switches will be used within the
network. The layer 2 protocols of the solution network will be
more secure due to the use of the SDN controllers. It is
considered that the ISP will be able to see the household IoT
entities. The MAC address are the unique and static identifier
for identifying the devices in the network. The ISP access
switches will be running Open vSwitch 1.9.0 (OVS). In
addition to that, it will be exposing showing the OpenFlow
APIs. The ISP network controller will be controlled through
the Floodlight OpenFlow controller. The version of the
Floodlight is 0.09 [48]. The API calls that are successful is
resulted into the proper flow of table protocol. These flows are
then added or removed from the OVS Bridge, respectively,
based on which OVS bridge is serving the user. In order to
have a access control, the fresh Floodlight module has been
used for developing the Application Program Interface [23].
This access point provides the wrapper to the firewall module
of the flood light in order to activate the SMP to push the
access control policies into the network into the smart home
IoT device.
3.3.3 Further network security setup
The Ruby-on-Rails programming environment has been
selected in the project to develop the security orchestrator. This
orchestrator will be responsible for holding the logic and state.
considered in this methodology.
2.7 Synthetic packet injection
The main purpose of this methodology is to reduce the
chance of hacking into the IoT based smart home environment
while the messages are transferred between IoT hub and cloud
API. It ensures that traffic analysis is complex enough that no
hacker can attack this system. Though the network uses the
encryption technology, it is not always possible to protect the
data [8]. The passive listening can be used by the hackers to
capture the sequences of initialization vectors that are used in
the protected communication medium. Proper traffic analysis
techniques will be used for establishing the connection
between the servers and the hub. Synthetic packet injection is
particularly designed based on software application. In real
world, injection of the synthetic packet will have the same
impact on the network security as in the simulation. The VPN
serves as a crucial part of this methodology as it is used for
encrypting the packets in the network traffic. The synthetic
packet can be used in the application service and virtual private
network.
3. ISSUES/SOLUTIONS
3.1 Requirement of the project
From the above literature review it has been understood
that providing control and security to the IoT based smart
home is a crucial factor. Various methodologies can be used
for providing the security. It can be done through offering
uninterrupted and secure control over the sensors and devices,
or it can be done through creating a safe and secure network
level security. Inn case of the synthetic packet injection, the
use of the VPN can be a solution to prevent capturing of
packets. Though the attackers cannot monitor the packet
transfer in the network, the main purpose of smart IoT based
home is the real issue in security. The mobile device of the user
can be used for hacking into the system and get access to the
personal data. No matter how much the device is secured from
being hacked, the threat of traffic analysis always remain on
the IoT devices. If the whole network can be secured then it
will be very effective in securing the whole smart home
architecture.
The requirements of the project is an IoT device or sensor,
hub, home router, cloud service API. The cloud service will be
connected to the mobile device. The concept of the device
management framework can be seen in this project. However,
the main focus remains on the network security. The SMP or
security management provider will be developed to secure the
network additionally. The home router must be chosen that can
support the SMP. The project prototype will be developed for
providing various customization options to the users.
3.2 modified problem Statement
Thus the main problem statement is developing the
prototype that will be used for developing the network that can
support security from the device level to cloud level.
Configuration the router to support the security management
provider is another problem of the project.
3.3 Proposed Project and Method of Network-Level Security
3.3.1 Security Management Provider
The project has been developed using a prototype that will
be done considering a three part architecture and application
program interface for providing various advanced options. The
users of the IoT architecture will be able to control the devices
through the cloud service API [48]. Project also proposed the
advancement in the access switch and controlling of the ISP
network modules. The SMP will be responsible for operating a
web based graphical user interface. The Amazon cloud has
been selected for running the SMP and the ISP will in a safe
data-center (not been identified still). Two settings has been
considered while testing the project outcome. The first one is
testing it in campus network that is SDN-enabled and consist
of over than three thousand Wi-Fi access points. The second is
the small amount of houses where the network will be
operating as the OTTor over the top legacy ISP network [37].
Fig 5 Proposed network prototype in the project [48]
3.3.2 Securing Local Network
The figure 5 shows the prototype of the proposed network.
In the project it has been assumed that SDN enabled internet
service providers’ access switches will be used within the
network. The layer 2 protocols of the solution network will be
more secure due to the use of the SDN controllers. It is
considered that the ISP will be able to see the household IoT
entities. The MAC address are the unique and static identifier
for identifying the devices in the network. The ISP access
switches will be running Open vSwitch 1.9.0 (OVS). In
addition to that, it will be exposing showing the OpenFlow
APIs. The ISP network controller will be controlled through
the Floodlight OpenFlow controller. The version of the
Floodlight is 0.09 [48]. The API calls that are successful is
resulted into the proper flow of table protocol. These flows are
then added or removed from the OVS Bridge, respectively,
based on which OVS bridge is serving the user. In order to
have a access control, the fresh Floodlight module has been
used for developing the Application Program Interface [23].
This access point provides the wrapper to the firewall module
of the flood light in order to activate the SMP to push the
access control policies into the network into the smart home
IoT device.
3.3.3 Further network security setup
The Ruby-on-Rails programming environment has been
selected in the project to develop the security orchestrator. This
orchestrator will be responsible for holding the logic and state.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
These logic and states are further used by the security
movement provider to handle the security of the user of the
smart home IoT technology. The communication between the
ISP and SMP occurs in one way that is from SMP to ISP as
portrayed in the fig 5. The RESTful application program
interface come into the big picture while the SMP
communicates with the user applications and front-end portal.
In order to make the project budget friendly, the MySQL
database has been used for storing the information of the
subscribers, policies, preferences of the users, devices, and
statistics [48]. The subscriber commands serves as the source
that triggers SMP to retrieve the information related to the
command. The REST command is used in user device that
triggers the retrieval.
3.3.4 Device/Sensor Management Approach
The sensor management framework will be developed to
control the devices within the IoT environment. At the
beginning of the development it has to be make sure that all the
sensors are active. The data will be stored in the proposed
MySQL database. A smart control algorithm has been
proposed in the project that starts after all the dependencies
among the output of the sensors has been recognized and
classified. The smart algorithm involves sensor switch off
process correlated to the sets of dependent variables, predicting
the results of the dependent variables through the use of the
independent variables [23]. During the later process it will be
assumed that the correlation among the sensors and output has
been followed. The SMP will inject its policies while the
output will be generated so that the impact of the SMP on the
network can be tested. In case the recent value and predicted
value’s difference exceeds the threshold, the current reading is
stored in the MySQL and the control is reset.
Fig 6 Smart Control Algorithm [21]
This management framework is significant in power
improvement. The controlling method deactivates the sensors
that are not used for any purpose. Often the sensors are
deactivated while the readings can be predicted using other
sensors. The master controller or microcontroller uses more
power for the additional effort to be put in the calculations. The
power consumption of the master controller is significantly less
than the power consumed by all the sensors together. This
allows the SMP to use more power and compute security
policies without any issue [21]. The proposed architecture the
data collected from the sensors are sent to the master controller
and then from there to cloud server. The bandwidth load will
be high in such cases. The local master, in the proposed
framework, receives a relatively low amount of data as many
readings are calculated. The main advantage of the proposed
framework is that it is able to provide the network the
capability of fault tolerance. This is not only beneficial to the
sensor management but also handy in terms of providing
security.
3.3.5 Mobile Application
Instead of web-based portal, a mobile application has been
considered within the project. The main purpose of this
decision is providing flexibility to the user. Mobile devices are
more user friendly and easily accessible. The internet
connection in mobile device is much cheap than Broadband
connection. The application user interface will be consisting a
list of devices that will be connected to the hub [17]. These
information will be collected either through the cloud API or
local network in which both the user and hub is connected. The
application will automatically maintain the list of the devices
based on the installed devices.
Fig 7 A sample architecture of device management framework [41]
The application will have predefined actions installed so
that the user can easily access all the features of the device.
The mobile application will be developed for both the iOS and
Android. To make the system more secure, any direct
communication form the smartphone to the IoT device will be
disabled so that all the request must transfer through the hub
and the SMP ca inject all the security protocols required to
make the network secure.
3.3.6 Secure connection to cloud
movement provider to handle the security of the user of the
smart home IoT technology. The communication between the
ISP and SMP occurs in one way that is from SMP to ISP as
portrayed in the fig 5. The RESTful application program
interface come into the big picture while the SMP
communicates with the user applications and front-end portal.
In order to make the project budget friendly, the MySQL
database has been used for storing the information of the
subscribers, policies, preferences of the users, devices, and
statistics [48]. The subscriber commands serves as the source
that triggers SMP to retrieve the information related to the
command. The REST command is used in user device that
triggers the retrieval.
3.3.4 Device/Sensor Management Approach
The sensor management framework will be developed to
control the devices within the IoT environment. At the
beginning of the development it has to be make sure that all the
sensors are active. The data will be stored in the proposed
MySQL database. A smart control algorithm has been
proposed in the project that starts after all the dependencies
among the output of the sensors has been recognized and
classified. The smart algorithm involves sensor switch off
process correlated to the sets of dependent variables, predicting
the results of the dependent variables through the use of the
independent variables [23]. During the later process it will be
assumed that the correlation among the sensors and output has
been followed. The SMP will inject its policies while the
output will be generated so that the impact of the SMP on the
network can be tested. In case the recent value and predicted
value’s difference exceeds the threshold, the current reading is
stored in the MySQL and the control is reset.
Fig 6 Smart Control Algorithm [21]
This management framework is significant in power
improvement. The controlling method deactivates the sensors
that are not used for any purpose. Often the sensors are
deactivated while the readings can be predicted using other
sensors. The master controller or microcontroller uses more
power for the additional effort to be put in the calculations. The
power consumption of the master controller is significantly less
than the power consumed by all the sensors together. This
allows the SMP to use more power and compute security
policies without any issue [21]. The proposed architecture the
data collected from the sensors are sent to the master controller
and then from there to cloud server. The bandwidth load will
be high in such cases. The local master, in the proposed
framework, receives a relatively low amount of data as many
readings are calculated. The main advantage of the proposed
framework is that it is able to provide the network the
capability of fault tolerance. This is not only beneficial to the
sensor management but also handy in terms of providing
security.
3.3.5 Mobile Application
Instead of web-based portal, a mobile application has been
considered within the project. The main purpose of this
decision is providing flexibility to the user. Mobile devices are
more user friendly and easily accessible. The internet
connection in mobile device is much cheap than Broadband
connection. The application user interface will be consisting a
list of devices that will be connected to the hub [17]. These
information will be collected either through the cloud API or
local network in which both the user and hub is connected. The
application will automatically maintain the list of the devices
based on the installed devices.
Fig 7 A sample architecture of device management framework [41]
The application will have predefined actions installed so
that the user can easily access all the features of the device.
The mobile application will be developed for both the iOS and
Android. To make the system more secure, any direct
communication form the smartphone to the IoT device will be
disabled so that all the request must transfer through the hub
and the SMP ca inject all the security protocols required to
make the network secure.
3.3.6 Secure connection to cloud

In this section the application of VPN in this project has
been discussed in broad. An open VPN tunnel will be
established so that remote service to the cloud can be provide
to the users with proper security. At the time of establishing
VPN tunnel through the use of the VPN client private network,
no restriction to the communication is imposed. This way the
endpoints become able to communicate endlessly. As the cloud
server is not as safe as the VPN, proper rules are deployed to
secure the communication. This will make sure that even if the
cloud server is hacked, the hub or local network will be
secured.
4. FUTURE RESEARCH
In the future research, the IPsec tunnel can be considered
instead of the VPN tunnel. This tunnel will be using the IP
protocol based mechanism to establish compunction in the
network. Various changes can be done in the microcontroller
that acts as the hub. The connection method of device and
smartphone can be more secured. The changes can be done in
the application interface. The network will be modified to
analyze the traffic coming from the IoT devices so the device
status can be checked. Research into security and privacy of
IoT is still in its infancy, and much of the prior work has
focused on understanding and identifying potential threats and
adapting existing security techniques to the IoT environment –
see a recent survey article. A majority of the work advocates
embedding security architectures within the IoT device,
including securing the communication protocols. For example,
proposes optimizing the DLTS communication protocol for
securing IoT data exchange, avises implementation of IEEE
802.15.4 compliant link layer security procedures, and presents
a lightweight encryption/decryption method for ID
authentication among sensor nodes. Concepts from Artificial
Immune System (AIS) have been imported to detect attacks on
IoT, and an IoT intrusion detection system with dynamic
defense was developed in. VIRTUS, a middleware solution for
management of applications in IoT environments adopts open
standards such as XMPP and OSGi. Accesscontrol
mechanisms based on an optimized implementation of elliptic-
curve digital signatures (ECDSA) and token-based access to
CoAP resources have been developed in.
5. ADVANTAGES AND DISADVANTAGES
5.1 Advantages
The main advantage of the project is the control over the
network from remote location. Taken as an example, no matter
where the user is, he/she can access the hub if proper internet
connection is available. The user can access and see the videos
from the other cities through the application installed in the
mobile device. The system will be collecting all the data from
the device and send the data to the mobile device through the
cloud API. The hub will allow the user to access the data only
after it is verified as authorized [5]. This verification process
increases the security as the user device requesting the data
will only access after successfully very to the system in both
the cloud and the hub. The cloud is protected through the
different user id and password and the hub uses a unique
identifier.
The MAC address of the device is not used as the identifier as
it will restrict the user access. Taken as an example, the user
will be able to access the network using a different mobile
device even if the previous mobile is stolen or sold [30]. The
user will only need to remember the unique identification
number that has been given to him. Making the whole
authorization technique based on the software based has made
the network more flexible and user friendly.
The application graphical user interface will be consisting
of only the required data like the buttons and device name. No
additional and unnecessary data will be shown to the user. This
not only makes the syste more user friendly but also allow the
user to be faster during controlling the devices. Only the
options of the devices that are connected to the hub will be
shown so that the users can be accessing the application
without having any knowledge of the configuration.
Using the SMP or security management provider has
proved to be a great advantage. This not only allows the
developers to inject protocols that are best suited for the
network but custom made configurations are highly adaptable
to the changes. The SMP will be monitoring all the packets that
will transfer through the hub. Taken as an example, if an
intruder wants to access the system, the SMP will verify the
access based on the predefined network protocols and reject the
access [16]. The only way to access the devices are only by
hacking them physically. The communication between the
device and cloud is done through the VPN. The VPN allows
the packets to be encrypted so that even if the information is
stolen it cannot be read.
There are various advantages of using the amazon cloud
services. The amazon are one of the leading cloud service
providers in the whole world and choosing the amazon service
has provided the opportunity to neglect the security concerns of
cloud storage. The amazon cloud can be purchased as per the
usage requirements and investment can be done as various
ways. The payment can be done based on resource usage or per
month basis [28]. The services that amazon cloud provides are
capable of supporting high performance application. Taken as
example, if the number of users are exceeded to more than
thousands then the number of devices connected to the cloud
through the hub will be more than ten thousand. Now the data
flow and processing of data will be much immense and without
proper high performance support, the network will go down.
The amazon cloud is maintained by several experienced staff.
These staff can take care of user request. In addition to that,
the organization is capable of providing unique solutions to the
cloud related issues in the network level security planning.
5.2 Disadvantages
The biggest disadvanatge of the project is its complexity.
Developing an application that consist of all the features of the
device is a critical task. The possibility of occuring any issue is
high. The application reuests are sent to the hub through a open
internet connection [45]. The hackers can get access to the user
reuest to the hub even if they do not have access to the cloud
serice API.
The cloud is a seroius consideration while security is the
topic. The cloud services are always vulnerable to the cyber
been discussed in broad. An open VPN tunnel will be
established so that remote service to the cloud can be provide
to the users with proper security. At the time of establishing
VPN tunnel through the use of the VPN client private network,
no restriction to the communication is imposed. This way the
endpoints become able to communicate endlessly. As the cloud
server is not as safe as the VPN, proper rules are deployed to
secure the communication. This will make sure that even if the
cloud server is hacked, the hub or local network will be
secured.
4. FUTURE RESEARCH
In the future research, the IPsec tunnel can be considered
instead of the VPN tunnel. This tunnel will be using the IP
protocol based mechanism to establish compunction in the
network. Various changes can be done in the microcontroller
that acts as the hub. The connection method of device and
smartphone can be more secured. The changes can be done in
the application interface. The network will be modified to
analyze the traffic coming from the IoT devices so the device
status can be checked. Research into security and privacy of
IoT is still in its infancy, and much of the prior work has
focused on understanding and identifying potential threats and
adapting existing security techniques to the IoT environment –
see a recent survey article. A majority of the work advocates
embedding security architectures within the IoT device,
including securing the communication protocols. For example,
proposes optimizing the DLTS communication protocol for
securing IoT data exchange, avises implementation of IEEE
802.15.4 compliant link layer security procedures, and presents
a lightweight encryption/decryption method for ID
authentication among sensor nodes. Concepts from Artificial
Immune System (AIS) have been imported to detect attacks on
IoT, and an IoT intrusion detection system with dynamic
defense was developed in. VIRTUS, a middleware solution for
management of applications in IoT environments adopts open
standards such as XMPP and OSGi. Accesscontrol
mechanisms based on an optimized implementation of elliptic-
curve digital signatures (ECDSA) and token-based access to
CoAP resources have been developed in.
5. ADVANTAGES AND DISADVANTAGES
5.1 Advantages
The main advantage of the project is the control over the
network from remote location. Taken as an example, no matter
where the user is, he/she can access the hub if proper internet
connection is available. The user can access and see the videos
from the other cities through the application installed in the
mobile device. The system will be collecting all the data from
the device and send the data to the mobile device through the
cloud API. The hub will allow the user to access the data only
after it is verified as authorized [5]. This verification process
increases the security as the user device requesting the data
will only access after successfully very to the system in both
the cloud and the hub. The cloud is protected through the
different user id and password and the hub uses a unique
identifier.
The MAC address of the device is not used as the identifier as
it will restrict the user access. Taken as an example, the user
will be able to access the network using a different mobile
device even if the previous mobile is stolen or sold [30]. The
user will only need to remember the unique identification
number that has been given to him. Making the whole
authorization technique based on the software based has made
the network more flexible and user friendly.
The application graphical user interface will be consisting
of only the required data like the buttons and device name. No
additional and unnecessary data will be shown to the user. This
not only makes the syste more user friendly but also allow the
user to be faster during controlling the devices. Only the
options of the devices that are connected to the hub will be
shown so that the users can be accessing the application
without having any knowledge of the configuration.
Using the SMP or security management provider has
proved to be a great advantage. This not only allows the
developers to inject protocols that are best suited for the
network but custom made configurations are highly adaptable
to the changes. The SMP will be monitoring all the packets that
will transfer through the hub. Taken as an example, if an
intruder wants to access the system, the SMP will verify the
access based on the predefined network protocols and reject the
access [16]. The only way to access the devices are only by
hacking them physically. The communication between the
device and cloud is done through the VPN. The VPN allows
the packets to be encrypted so that even if the information is
stolen it cannot be read.
There are various advantages of using the amazon cloud
services. The amazon are one of the leading cloud service
providers in the whole world and choosing the amazon service
has provided the opportunity to neglect the security concerns of
cloud storage. The amazon cloud can be purchased as per the
usage requirements and investment can be done as various
ways. The payment can be done based on resource usage or per
month basis [28]. The services that amazon cloud provides are
capable of supporting high performance application. Taken as
example, if the number of users are exceeded to more than
thousands then the number of devices connected to the cloud
through the hub will be more than ten thousand. Now the data
flow and processing of data will be much immense and without
proper high performance support, the network will go down.
The amazon cloud is maintained by several experienced staff.
These staff can take care of user request. In addition to that,
the organization is capable of providing unique solutions to the
cloud related issues in the network level security planning.
5.2 Disadvantages
The biggest disadvanatge of the project is its complexity.
Developing an application that consist of all the features of the
device is a critical task. The possibility of occuring any issue is
high. The application reuests are sent to the hub through a open
internet connection [45]. The hackers can get access to the user
reuest to the hub even if they do not have access to the cloud
serice API.
The cloud is a seroius consideration while security is the
topic. The cloud services are always vulnerable to the cyber

attacks. The cloud service providers can sell the sensitve data
to other organzations without giving warning to the clients.
The user will not have authority of controlling the cloud
services. Though this is not a seriuos conern for a signle user
but for a organiztion that is providing services to thousands of
users is a signficnat matter. The cloud services are not also
dependable. Taken as an example, the user is in diferne town
and wants to control the curtains of the window [37]. If the
cloud service is down, there is no way the user will be able to
get access to those curtains.
The devices are not provided any security by the network.
If the attacker able to hack into a IoT device seperately then the
attack will not be detected by the network. It is because the
network does not employ any protocol to check the device
configuration. This happens because the project has been
developed without collaborating the manufacturing
organization [21]. Taken as an example, the attackers has
hacked into the ssecueity camera and providing the hub only
the inframtion that the attacker wants to send. In this case, the
user will be able to access the camera but will not be seeing the
original infroamtion taken by the camrea. The user will be
seeeing the images that the hacker wants to make them see.
Another disadvantage is with the SMP. Proper
configuration of the SMP is not possible in a signle go. There
are various threats that can be used for hacking into system or
making it go down. The DDoS attack in the cloud can be done
to prevent the hub to send or receive any information to the
cloud. The SMP will not be able to handle any intrision attack
in this case as the cloud will not be able to assist the SMP.
The hub will store any specific device as the controller. In
case the user-id is theft then the intruder can authorizely
control all the devices form a remote location. No matter how
much the user tries to prevent this issue, there no way than
trunfing off the hub and cllaing the experts to solve the issues.
Taken as an example, the user sells the mmobile in which the
application is stored it will have the id of the user in it. Then
the buyer can use this device to access the hub [47]. There
other numerarous security and computation related issues that
the project should have been considered.
6. CONCLUSION
The report has presented a network level security solution
and IoT device management framework. As per the project has
been discussed in the report, device security is essential but the
security in the network-level. The privacy concern of the
network security is the biggest disadvantage of the IoT based
smart home security. The attackers are tend to get into the
home system through the local routers or cloud services.
Attacking the cloud or local routers are competitively easy for
the attackers. The attackers then either remain in the system for
a longtime or get all the required data and leave the system. In
both cases the privacy security concern is very high. The
attackers can also get access to various IoT devices and control
it. The report has represented a security management provider
that implies protocols and policies to the incoming requests and
verify the user. The VPN approach of securing the
communication between the cloud and the hub is a good
approach. Proper protocols must be implied to the network.
The network must be monitored for a long period (say about
three months) so that proper testing of the network can be
done.
The security of the IoT smart home system is related to the
control framework over the IoT devices. The project will be
using a unique algorithm to get control over the devices. In
order to have a universal controller which will signal the
devices, installing a microcontroller is essential. In this case,
raspberry-pi is a suitable microcontroller which is able to
handle all the computation functions. The report has
successfully proposed the methodologies of securing an IoT
based smart home network but lacks in describing the threats
that can be used for attacking the system. The project will be
consisting of devices/sensors that will gather data periodically
and as well triggered by an event. These devices will need to
be configured to cope with the scope of the project. The system
may be monitored even after the deployment so that required
changes can be done in the system. No matter how much a
network is secured, there always a flaw in it. In case of the
proposed network, the security flaw is in the cloud level. The
project did not consider making any assumptions on securing
the solution. It is completely depended upon the security
provide by Amazon. In case an organization is going for its
hybrid cloud infrastructure there is no solution for that part.
The proposed network solution is able to provide the security
to all the devices that are connected to the network. The
network will identify all the request by the user device and
send it to the desired device. The project has considered the
device management system that is able to provide the user all
the freedom. The user will be able to access all the features of
the device through a single application. Various IoT device
manufacturers have their own applications. In the future project
modifications can be done by collaborating with them. This
will reduce the effort of application development and
microcontroller configuration.
ACKNOWLEDGEMENT
This report has been developed with the help of <Your teacher name>. The university <your university> has provided all the
resources that were required to develop the report.
REFERENCES
[1] Geneiatakis, D., Kounelis, I., Neisse, R., Nai-Fovino, I., Steri, G., & Baldini, G. (2017). Security and privacy issues for an IoT based smart home. In
Information and Communication Technology, Electronics and Microelectronics (MIPRO), 2017 40th International Convention on (pp. 1292-1297). IEEE.
[2] Apthorpe, N., Reisman, D., & Feamster, N. (2017). A Smart Home is No Castle: Privacy Vulnerabilities of Encrypted IoT Traffic. arXiv preprint
arXiv:1705.06805.
to other organzations without giving warning to the clients.
The user will not have authority of controlling the cloud
services. Though this is not a seriuos conern for a signle user
but for a organiztion that is providing services to thousands of
users is a signficnat matter. The cloud services are not also
dependable. Taken as an example, the user is in diferne town
and wants to control the curtains of the window [37]. If the
cloud service is down, there is no way the user will be able to
get access to those curtains.
The devices are not provided any security by the network.
If the attacker able to hack into a IoT device seperately then the
attack will not be detected by the network. It is because the
network does not employ any protocol to check the device
configuration. This happens because the project has been
developed without collaborating the manufacturing
organization [21]. Taken as an example, the attackers has
hacked into the ssecueity camera and providing the hub only
the inframtion that the attacker wants to send. In this case, the
user will be able to access the camera but will not be seeing the
original infroamtion taken by the camrea. The user will be
seeeing the images that the hacker wants to make them see.
Another disadvantage is with the SMP. Proper
configuration of the SMP is not possible in a signle go. There
are various threats that can be used for hacking into system or
making it go down. The DDoS attack in the cloud can be done
to prevent the hub to send or receive any information to the
cloud. The SMP will not be able to handle any intrision attack
in this case as the cloud will not be able to assist the SMP.
The hub will store any specific device as the controller. In
case the user-id is theft then the intruder can authorizely
control all the devices form a remote location. No matter how
much the user tries to prevent this issue, there no way than
trunfing off the hub and cllaing the experts to solve the issues.
Taken as an example, the user sells the mmobile in which the
application is stored it will have the id of the user in it. Then
the buyer can use this device to access the hub [47]. There
other numerarous security and computation related issues that
the project should have been considered.
6. CONCLUSION
The report has presented a network level security solution
and IoT device management framework. As per the project has
been discussed in the report, device security is essential but the
security in the network-level. The privacy concern of the
network security is the biggest disadvantage of the IoT based
smart home security. The attackers are tend to get into the
home system through the local routers or cloud services.
Attacking the cloud or local routers are competitively easy for
the attackers. The attackers then either remain in the system for
a longtime or get all the required data and leave the system. In
both cases the privacy security concern is very high. The
attackers can also get access to various IoT devices and control
it. The report has represented a security management provider
that implies protocols and policies to the incoming requests and
verify the user. The VPN approach of securing the
communication between the cloud and the hub is a good
approach. Proper protocols must be implied to the network.
The network must be monitored for a long period (say about
three months) so that proper testing of the network can be
done.
The security of the IoT smart home system is related to the
control framework over the IoT devices. The project will be
using a unique algorithm to get control over the devices. In
order to have a universal controller which will signal the
devices, installing a microcontroller is essential. In this case,
raspberry-pi is a suitable microcontroller which is able to
handle all the computation functions. The report has
successfully proposed the methodologies of securing an IoT
based smart home network but lacks in describing the threats
that can be used for attacking the system. The project will be
consisting of devices/sensors that will gather data periodically
and as well triggered by an event. These devices will need to
be configured to cope with the scope of the project. The system
may be monitored even after the deployment so that required
changes can be done in the system. No matter how much a
network is secured, there always a flaw in it. In case of the
proposed network, the security flaw is in the cloud level. The
project did not consider making any assumptions on securing
the solution. It is completely depended upon the security
provide by Amazon. In case an organization is going for its
hybrid cloud infrastructure there is no solution for that part.
The proposed network solution is able to provide the security
to all the devices that are connected to the network. The
network will identify all the request by the user device and
send it to the desired device. The project has considered the
device management system that is able to provide the user all
the freedom. The user will be able to access all the features of
the device through a single application. Various IoT device
manufacturers have their own applications. In the future project
modifications can be done by collaborating with them. This
will reduce the effort of application development and
microcontroller configuration.
ACKNOWLEDGEMENT
This report has been developed with the help of <Your teacher name>. The university <your university> has provided all the
resources that were required to develop the report.
REFERENCES
[1] Geneiatakis, D., Kounelis, I., Neisse, R., Nai-Fovino, I., Steri, G., & Baldini, G. (2017). Security and privacy issues for an IoT based smart home. In
Information and Communication Technology, Electronics and Microelectronics (MIPRO), 2017 40th International Convention on (pp. 1292-1297). IEEE.
[2] Apthorpe, N., Reisman, D., & Feamster, N. (2017). A Smart Home is No Castle: Privacy Vulnerabilities of Encrypted IoT Traffic. arXiv preprint
arXiv:1705.06805.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

[3] Patel, S. M., & Kanawade, S. Y. (2017). Internet of Things Based Smart Home with Intel Edison. In Proceedings of International Conference on
Communication and Networks (pp. 385-392). Springer, Singapore.
[4] Pirbhulal, S., Zhang, H., E Alahi, M. E., Ghayvat, H., Mukhopadhyay, S. C., Zhang, Y. T., & Wu, W. (2016). A novel secure IoT-based smart home
automation system using a wireless sensor network. Sensors, 17(1), 69.
[5] Yoon, S., Park, H., & Yoo, H. S. (2015). Security issues on smarthome in IoT environment. In Computer Science and its Applications (pp. 691-696).
Springer, Berlin, Heidelberg.
[6] Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future vision, architecture, challenges and services. In Internet of things
(WF-IoT), 2014 IEEE world forum on (pp. 287-292). IEEE.
[7] Jian, M. S., Wu, J. Y., Chen, J. Y., Li, Y. J., Wang, Y. C., & Xu, H. Y. (2017, February). IOT base smart home appliances by using Cloud Intelligent Tetris
Switch. In Advanced Communication Technology (ICACT), 2017 19th International Conference on (pp. 589-592). IEEE.
[8] Yoshigoe, K., Dai, W., Abramson, M., & Jacobs, A. (2015, December). Overcoming invasion of privacy in smart home environment with synthetic packet
injection. In TRON Symposium (TRONSHOW), 2015 (pp. 1-7). IEEE.
[9] Stojkoska, B. L. R., & Trivodaliev, K. V. (2017). A review of Internet of Things for smart home: Challenges and solutions. Journal of Cleaner Production,
140, 1454-1464.
[10] Al-Ali, A. R., & Aburukba, R. (2015). Role of internet of things in the smart grid technology. Journal of Computer and Communications, 3(05), 229.
[11] Pandikumar, S., & Vetrivel, R. S. (2014, March). Internet of things based architecture of web and smart home interface using GSM. In International Journal
of Innovative Research in Science, Engineering and Technology (Vol. 3, No. 3, pp. 1721-1727).
[12] Jacobsson, A., Boldt, M., & Carlsson, B. (2016). A risk analysis of a smart home automation system. Future Generation Computer Systems, 56, 719-733.
[13] Adhya, S., Saha, D., Das, A., Jana, J., & Saha, H. (2016, January). An IoT based smart solar photovoltaic remote monitoring and control unit. In Control,
Instrumentation, Energy & Communication (CIEC), 2016 2nd International Conference on (pp. 432-436). IEEE.
[14] Chen, M., Yang, J., Zhu, X., Wang, X., Liu, M., & Song, J. (2017). Smart Home 2.0: Innovative Smart Home System Powered by Botanical IoT and Emotion
Detection. Mobile Networks and Applications, 1-11.
[15] Amadeo, M., Campolo, C., Iera, A., & Molinaro, A. (2015, June). Information Centric Networking in IoT scenarios: The case of a smart home. In
Communications (ICC), 2015 IEEE International Conference on (pp. 648-653). IEEE.
[16] Shingala, K., & Patel, J. (2017). Automatic Home Appliances and Security of Smart Home with RFID, SMS, Email and Real Time Algorithm Based on IOT.
[17] Alletto, S., Cucchiara, R., Del Fiore, G., Mainetti, L., Mighali, V., Patrono, L., & Serra, G. (2016). An indoor location-aware system for an IoT-based smart
museum. IEEE Internet of Things Journal, 3(2), 244-253.
[18] Apthorpe, N., Reisman, D., Sundaresan, S., Narayanan, A., & Feamster, N. (2017). Spying on the smart home: Privacy attacks and defenses on encrypted iot
traffic. arXiv preprint arXiv:1708.05044.
[19] Dorri, A., Kanhere, S. S., Jurdak, R., & Gauravaram, P. (2017, March). Blockchain for IoT security and privacy: The case study of a smart home. In
Pervasive Computing and Communications Workshops (PerCom Workshops), 2017 IEEE International Conference on (pp. 618-623). IEEE.
[20] Lin, H., & Bergmann, N. W. (2016). IoT privacy and security challenges for smart home environments. Information, 7(3), 44.
[21] Choubey, P. K., Pateria, S., Saxena, A., SB, V. P. C., Jha, K. K., & PM, S. B. (2015, June). Power efficient, bandwidth optimized and fault tolerant sensor
management for IOT in Smart Home. In Advance Computing Conference (IACC), 2015 IEEE International (pp. 366-370). IEEE.
[22] Strohbach, M., Ziekow, H., Gazis, V., & Akiva, N. (2015). Towards a big data analytics framework for IoT and smart city applications. In Modeling and
processing for next-generation big-data technologies (pp. 257-282). Springer International Publishing.
[23] Pradeep, S., Kousalya, T., Suresh, K. A., & Edwin, J. (2016). Iot and its connectivity challenges in smart home.
[24] Whitmore, A., Agarwal, A., & Da Xu, L. (2015). The Internet of Things—A survey of topics and trends. Information Systems Frontiers, 17(2), 261-274.
[25] Lee, I., & Lee, K. (2015). The Internet of Things (IoT): Applications, investments, and challenges for enterprises. Business Horizons, 58(4), 431-440.
[26] Xu, K., Wang, X., Wei, W., Song, H., & Mao, B. (2016). Toward software defined smart home. IEEE Communications Magazine, 54(5), 116-122.
[27] Cho, J. Y., Lee, H. S., & Lee, B. G. (2015, February). Connectivity issues on IoT business-the Korean case of smart home network. In The Second
International Conference on Electrical, Electronics, Computer Engineering and their Applications (EECEA2015) (p. 120).
[28] Perumal, T., Datta, S. K., & Bonnet, C. (2015). IoT device management framework for smart home scenarios. In Consumer Electronics (GCCE), 2015 IEEE
4th Global Conference on (pp. 54-55). IEEE.
[29] Bugeja, J., Jacobsson, A., & Davidsson, P. (2016, August). On Privacy and Security Challenges in Smart Connected Homes. In Intelligence and Security
Informatics Conference (EISIC), 2016 European (pp. 172-175). IEEE.
[30] Chang, C. Y., Kuo, C. H., Chen, J. C., & Wang, T. C. (2015). Design and implementation of an IoT access point for smart home. Applied Sciences, 5(4),
1882-1903.
[31] Pandikumar, S., & Vetrivel, R. S. (2014, March). Internet of things based architecture of web and smart home interface using GSM. In International Journal
of Innovative Research in Science, Engineering and Technology (Vol. 3, No. 3, pp. 1721-1727).
[32] Kumar, P., & Pati, U. C. (2016, May). IoT based monitoring and control of appliances for smart home. In Recent Trends in Electronics, Information &
Communication Technology (RTEICT), IEEE International Conference on (pp. 1145-1150). IEEE.
[33] Ghayvat, H., Mukhopadhyay, S., Liu, J., Babu, A., Alahi, M. E. E., & Gui, X. (2015). Internet of things for smart homes and buildings. Australian Journal of
Telecommunications and the Digital Economy, 3(4).
[34] Meddeb, M., Dhraief, A., Belghith, A., Monteil, T., & Drira, K. (2017). Named Data Networking: A promising architecture for the Internet of things (IoT).
Communication and Networks (pp. 385-392). Springer, Singapore.
[4] Pirbhulal, S., Zhang, H., E Alahi, M. E., Ghayvat, H., Mukhopadhyay, S. C., Zhang, Y. T., & Wu, W. (2016). A novel secure IoT-based smart home
automation system using a wireless sensor network. Sensors, 17(1), 69.
[5] Yoon, S., Park, H., & Yoo, H. S. (2015). Security issues on smarthome in IoT environment. In Computer Science and its Applications (pp. 691-696).
Springer, Berlin, Heidelberg.
[6] Singh, D., Tripathi, G., & Jara, A. J. (2014, March). A survey of Internet-of-Things: Future vision, architecture, challenges and services. In Internet of things
(WF-IoT), 2014 IEEE world forum on (pp. 287-292). IEEE.
[7] Jian, M. S., Wu, J. Y., Chen, J. Y., Li, Y. J., Wang, Y. C., & Xu, H. Y. (2017, February). IOT base smart home appliances by using Cloud Intelligent Tetris
Switch. In Advanced Communication Technology (ICACT), 2017 19th International Conference on (pp. 589-592). IEEE.
[8] Yoshigoe, K., Dai, W., Abramson, M., & Jacobs, A. (2015, December). Overcoming invasion of privacy in smart home environment with synthetic packet
injection. In TRON Symposium (TRONSHOW), 2015 (pp. 1-7). IEEE.
[9] Stojkoska, B. L. R., & Trivodaliev, K. V. (2017). A review of Internet of Things for smart home: Challenges and solutions. Journal of Cleaner Production,
140, 1454-1464.
[10] Al-Ali, A. R., & Aburukba, R. (2015). Role of internet of things in the smart grid technology. Journal of Computer and Communications, 3(05), 229.
[11] Pandikumar, S., & Vetrivel, R. S. (2014, March). Internet of things based architecture of web and smart home interface using GSM. In International Journal
of Innovative Research in Science, Engineering and Technology (Vol. 3, No. 3, pp. 1721-1727).
[12] Jacobsson, A., Boldt, M., & Carlsson, B. (2016). A risk analysis of a smart home automation system. Future Generation Computer Systems, 56, 719-733.
[13] Adhya, S., Saha, D., Das, A., Jana, J., & Saha, H. (2016, January). An IoT based smart solar photovoltaic remote monitoring and control unit. In Control,
Instrumentation, Energy & Communication (CIEC), 2016 2nd International Conference on (pp. 432-436). IEEE.
[14] Chen, M., Yang, J., Zhu, X., Wang, X., Liu, M., & Song, J. (2017). Smart Home 2.0: Innovative Smart Home System Powered by Botanical IoT and Emotion
Detection. Mobile Networks and Applications, 1-11.
[15] Amadeo, M., Campolo, C., Iera, A., & Molinaro, A. (2015, June). Information Centric Networking in IoT scenarios: The case of a smart home. In
Communications (ICC), 2015 IEEE International Conference on (pp. 648-653). IEEE.
[16] Shingala, K., & Patel, J. (2017). Automatic Home Appliances and Security of Smart Home with RFID, SMS, Email and Real Time Algorithm Based on IOT.
[17] Alletto, S., Cucchiara, R., Del Fiore, G., Mainetti, L., Mighali, V., Patrono, L., & Serra, G. (2016). An indoor location-aware system for an IoT-based smart
museum. IEEE Internet of Things Journal, 3(2), 244-253.
[18] Apthorpe, N., Reisman, D., Sundaresan, S., Narayanan, A., & Feamster, N. (2017). Spying on the smart home: Privacy attacks and defenses on encrypted iot
traffic. arXiv preprint arXiv:1708.05044.
[19] Dorri, A., Kanhere, S. S., Jurdak, R., & Gauravaram, P. (2017, March). Blockchain for IoT security and privacy: The case study of a smart home. In
Pervasive Computing and Communications Workshops (PerCom Workshops), 2017 IEEE International Conference on (pp. 618-623). IEEE.
[20] Lin, H., & Bergmann, N. W. (2016). IoT privacy and security challenges for smart home environments. Information, 7(3), 44.
[21] Choubey, P. K., Pateria, S., Saxena, A., SB, V. P. C., Jha, K. K., & PM, S. B. (2015, June). Power efficient, bandwidth optimized and fault tolerant sensor
management for IOT in Smart Home. In Advance Computing Conference (IACC), 2015 IEEE International (pp. 366-370). IEEE.
[22] Strohbach, M., Ziekow, H., Gazis, V., & Akiva, N. (2015). Towards a big data analytics framework for IoT and smart city applications. In Modeling and
processing for next-generation big-data technologies (pp. 257-282). Springer International Publishing.
[23] Pradeep, S., Kousalya, T., Suresh, K. A., & Edwin, J. (2016). Iot and its connectivity challenges in smart home.
[24] Whitmore, A., Agarwal, A., & Da Xu, L. (2015). The Internet of Things—A survey of topics and trends. Information Systems Frontiers, 17(2), 261-274.
[25] Lee, I., & Lee, K. (2015). The Internet of Things (IoT): Applications, investments, and challenges for enterprises. Business Horizons, 58(4), 431-440.
[26] Xu, K., Wang, X., Wei, W., Song, H., & Mao, B. (2016). Toward software defined smart home. IEEE Communications Magazine, 54(5), 116-122.
[27] Cho, J. Y., Lee, H. S., & Lee, B. G. (2015, February). Connectivity issues on IoT business-the Korean case of smart home network. In The Second
International Conference on Electrical, Electronics, Computer Engineering and their Applications (EECEA2015) (p. 120).
[28] Perumal, T., Datta, S. K., & Bonnet, C. (2015). IoT device management framework for smart home scenarios. In Consumer Electronics (GCCE), 2015 IEEE
4th Global Conference on (pp. 54-55). IEEE.
[29] Bugeja, J., Jacobsson, A., & Davidsson, P. (2016, August). On Privacy and Security Challenges in Smart Connected Homes. In Intelligence and Security
Informatics Conference (EISIC), 2016 European (pp. 172-175). IEEE.
[30] Chang, C. Y., Kuo, C. H., Chen, J. C., & Wang, T. C. (2015). Design and implementation of an IoT access point for smart home. Applied Sciences, 5(4),
1882-1903.
[31] Pandikumar, S., & Vetrivel, R. S. (2014, March). Internet of things based architecture of web and smart home interface using GSM. In International Journal
of Innovative Research in Science, Engineering and Technology (Vol. 3, No. 3, pp. 1721-1727).
[32] Kumar, P., & Pati, U. C. (2016, May). IoT based monitoring and control of appliances for smart home. In Recent Trends in Electronics, Information &
Communication Technology (RTEICT), IEEE International Conference on (pp. 1145-1150). IEEE.
[33] Ghayvat, H., Mukhopadhyay, S., Liu, J., Babu, A., Alahi, M. E. E., & Gui, X. (2015). Internet of things for smart homes and buildings. Australian Journal of
Telecommunications and the Digital Economy, 3(4).
[34] Meddeb, M., Dhraief, A., Belghith, A., Monteil, T., & Drira, K. (2017). Named Data Networking: A promising architecture for the Internet of things (IoT).

[35] Kim, J. (2016). HEMS (Home Energy Management System) base on the IoT smart home. Contemporary Engineering Sciences, 9(1), 21-28.
[36] Karmakar, G., Roy, S., Chattopadhyay, G., & Xiao, Z. (2017, February). Dynamically controlling exterior and interior window coverings through IoT for
environmental friendly smart homes. In Mechatronics (ICM), 2017 IEEE International Conference on (pp. 487-491). IEEE.
[37] Wallis, K., & Reich, C. (2016). Secure Zero Configuration of IoT Devices-A Survey. BW-CAR| SINCOM, 59.
[38] La Marra, A., Martinelli, F., Mori, P., & Saracino, A. (2017, August). Implementing usage control in internet of things: a smart home use case. In
Trustcom/BigDataSE/ICESS, 2017 IEEE (pp. 1056-1063). IEEE.
[39] Cui, X. (2016). The internet of things. In Ethical Ripples of Creativity and Innovation (pp. 61-68). Palgrave Macmillan, London.
[40] Elkhodr, M., Shahrestani, S., & Cheung, H. (2015, December). A smart home application based on the Internet of Things management platform. In Data
Science and Data Intensive Systems (DSDIS), 2015 IEEE International Conference on (pp. 491-496). IEEE.
[41] Chen, H., Xie, X., Shu, W., & Xiong, N. (2016). An Efficient Recommendation Filter Model on Smart Home Big Data Analytics for Enhanced Living
Environments. Sensors, 16(10), 1706.
[42] Mano, L. Y., Faiçal, B. S., Nakamura, L. H., Gomes, P. H., Libralon, G. L., Meneguete, R. I., ... & Ueyama, J. (2016). Exploiting IoT technologies for
enhancing Health Smart Homes through patient identification and emotion recognition. Computer Communications, 89, 178-190.
[43] Li, M., & Lin, H. J. (2015). Design and implementation of smart home control systems based on wireless sensor networks and power line communications.
IEEE Transactions on Industrial Electronics, 62(7), 4430-4442.
[44] Sicari, S., Rizzardi, A., Grieco, L. A., & Coen-Porisini, A. (2015). Security, privacy and trust in Internet of Things: The road ahead. Computer Networks, 76,
146-164.
[45] Lee, Y. T., Hsiao, W. H., Huang, C. M., & Seng-cho, T. C. (2016). An integrated cloud-based smart home management system with community hierarchy.
IEEE Transactions on Consumer Electronics, 62(1), 1-9.
[46] Hoffman, D. L., & Novak, T. P. (2015). Emergent experience and the connected consumer in the smart home assemblage and the internet of things.
[47] Kang, D. H., Park, M. S., Kim, H. S., Kim, D. Y., Kim, S. H., Son, H. J., & Lee, S. G. (2017, February). Room Temperature Control and Fire
Alarm/Suppression IoT Service Using MQTT on AWS. In Platform Technology and Service (PlatCon), 2017 International Conference on (pp. 1-5). IEEE.
[48] Sivaraman, V., Gharakheili, H. H., Vishwanath, A., Boreli, R., & Mehani, O. (2015, October). Network-level security and privacy control for smart-home IoT
devices. In Wireless and Mobile Computing, Networking and Communications (WiMob), 2015 IEEE 11th International Conference on (pp. 163-167). IEEE.
[36] Karmakar, G., Roy, S., Chattopadhyay, G., & Xiao, Z. (2017, February). Dynamically controlling exterior and interior window coverings through IoT for
environmental friendly smart homes. In Mechatronics (ICM), 2017 IEEE International Conference on (pp. 487-491). IEEE.
[37] Wallis, K., & Reich, C. (2016). Secure Zero Configuration of IoT Devices-A Survey. BW-CAR| SINCOM, 59.
[38] La Marra, A., Martinelli, F., Mori, P., & Saracino, A. (2017, August). Implementing usage control in internet of things: a smart home use case. In
Trustcom/BigDataSE/ICESS, 2017 IEEE (pp. 1056-1063). IEEE.
[39] Cui, X. (2016). The internet of things. In Ethical Ripples of Creativity and Innovation (pp. 61-68). Palgrave Macmillan, London.
[40] Elkhodr, M., Shahrestani, S., & Cheung, H. (2015, December). A smart home application based on the Internet of Things management platform. In Data
Science and Data Intensive Systems (DSDIS), 2015 IEEE International Conference on (pp. 491-496). IEEE.
[41] Chen, H., Xie, X., Shu, W., & Xiong, N. (2016). An Efficient Recommendation Filter Model on Smart Home Big Data Analytics for Enhanced Living
Environments. Sensors, 16(10), 1706.
[42] Mano, L. Y., Faiçal, B. S., Nakamura, L. H., Gomes, P. H., Libralon, G. L., Meneguete, R. I., ... & Ueyama, J. (2016). Exploiting IoT technologies for
enhancing Health Smart Homes through patient identification and emotion recognition. Computer Communications, 89, 178-190.
[43] Li, M., & Lin, H. J. (2015). Design and implementation of smart home control systems based on wireless sensor networks and power line communications.
IEEE Transactions on Industrial Electronics, 62(7), 4430-4442.
[44] Sicari, S., Rizzardi, A., Grieco, L. A., & Coen-Porisini, A. (2015). Security, privacy and trust in Internet of Things: The road ahead. Computer Networks, 76,
146-164.
[45] Lee, Y. T., Hsiao, W. H., Huang, C. M., & Seng-cho, T. C. (2016). An integrated cloud-based smart home management system with community hierarchy.
IEEE Transactions on Consumer Electronics, 62(1), 1-9.
[46] Hoffman, D. L., & Novak, T. P. (2015). Emergent experience and the connected consumer in the smart home assemblage and the internet of things.
[47] Kang, D. H., Park, M. S., Kim, H. S., Kim, D. Y., Kim, S. H., Son, H. J., & Lee, S. G. (2017, February). Room Temperature Control and Fire
Alarm/Suppression IoT Service Using MQTT on AWS. In Platform Technology and Service (PlatCon), 2017 International Conference on (pp. 1-5). IEEE.
[48] Sivaraman, V., Gharakheili, H. H., Vishwanath, A., Boreli, R., & Mehani, O. (2015, October). Network-level security and privacy control for smart-home IoT
devices. In Wireless and Mobile Computing, Networking and Communications (WiMob), 2015 IEEE 11th International Conference on (pp. 163-167). IEEE.
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





