Report on IoT based Smart Home
Added on 2020-05-16
9 Pages8918 Words66 Views
IoT in Smart Home
Name of the Student
Name of the University
Student Number
Course ID
Email Address of Student
Abstract— the report reflects the development of the network
level security to the IoT based smart home. The IoT is the
abbreviation of internet of things. Five methodologies of
developing the security in the smart home has been discussed in
the report Based on the flexibility and impact the network level
security implementation through the SMP (security management
provider) has been selected.
Keywords— IoT; cloud; SMP; smart home; nerwork; device
management; network architecture; synthetic packet; ISP; Sensor
1. INTRODUCTION
The Internet of Things were developed with the purpose of
connecting various electronic components to the internet and
gathering data or condoling electronic device from remote
locations. The IoT is capable of supporting various day-to-
applications. Various organizations are putting effort in making
new IoT technologies that can be used for facilitating the
business process or selling. One of the most popular method of
using the IoT is the application in the smart homes. In the smart
home concept, various IoT devices (electronic devices) are
connected with each other through wire or wireless
communication medium. These devices can also communicate
with each other to execute a process. The homes are becoming
extensively smart due to use of the IoT devices. These smart
homes are often connected to a cloud environment computing
system so that the owner of the house can control it from remote
location. As the data from the smart home IoT network travels
to the server wirelessly, the device becomes extremely
vulnerable to cyber-attacks.
At the beginning of the report, the main considerations has
been the security issues and smart home network related
solutions. Then various arguments will be proposed in the
context of security implementations. In the literature review
part, the security issues of the smart home has been discussed.
Based on the major issues or the issues that is relevantly new
will be focused upon. After proper analysis of the circumstances
and available IoT technology, the solution to the security issue
will be provided.
The main problem of the project is to identify the security
issues that is most harmful and providing an utmost solution to
it which can be implemented irrespective of the IoT technology
platform. The report is focused upon a project with the
deliverable of developing a network level security for the
security. In the recent years it has been seen that various attacks
has been executed on the smart homes successfully. The report
provides details of the future works that can be don later on this
project outcome.
2. BACKGROUND/LITERATURE REVIEW
In order to discuss bout the smart home security issues, the
details of the architecture, network, components used and
much more things need to be considered. All the entities that
make up the IoT based smart home system can be exploited by
the cybercriminals to hack into the smart home. At the
beginning of the literature review, the idea of a typical smart
home architecture will be provided.
2.1 Architecture of Smart Home Based on IoT
The smart homes are the combination of different
electronic components and a network. The electronic
components are sensors, controllers, circuits and many more.
The applications are developed for the user mobile device
(smart phones) so the users can control the operations of the
IoT based smart home from distance. The connection is a
significant part of the homes as this makes the smart home a
really advanced technology. These entities are utilized for
designing and developing a dynamic heterogeneous
architecture [6]. These architecture remains the source of smart
home operations. The quality and advancement in the
architecture defines the amount of operations that the smart
home will be performing. The IoT devices is not equipped with
interoperability standards and that is why the connected IoT
devices in a smart home architecture can be controlled directly
via a smartphone or other device. The sensors that are used
within the smart home environment does not have the feature
of connecting to the internet directly [11]. In reality, the
sensors does not have any direct connection with the internet,
the microcontroller provides them all the instruction through
the output ports of it.
Fig 1 Architecture of a typical Smart Home [1]
The internet connection is established in the hub of the
network. The hub works as the local workstation in the smart
home architecture. Basically wireless communication mediums
Name of the Student
Name of the University
Student Number
Course ID
Email Address of Student
Abstract— the report reflects the development of the network
level security to the IoT based smart home. The IoT is the
abbreviation of internet of things. Five methodologies of
developing the security in the smart home has been discussed in
the report Based on the flexibility and impact the network level
security implementation through the SMP (security management
provider) has been selected.
Keywords— IoT; cloud; SMP; smart home; nerwork; device
management; network architecture; synthetic packet; ISP; Sensor
1. INTRODUCTION
The Internet of Things were developed with the purpose of
connecting various electronic components to the internet and
gathering data or condoling electronic device from remote
locations. The IoT is capable of supporting various day-to-
applications. Various organizations are putting effort in making
new IoT technologies that can be used for facilitating the
business process or selling. One of the most popular method of
using the IoT is the application in the smart homes. In the smart
home concept, various IoT devices (electronic devices) are
connected with each other through wire or wireless
communication medium. These devices can also communicate
with each other to execute a process. The homes are becoming
extensively smart due to use of the IoT devices. These smart
homes are often connected to a cloud environment computing
system so that the owner of the house can control it from remote
location. As the data from the smart home IoT network travels
to the server wirelessly, the device becomes extremely
vulnerable to cyber-attacks.
At the beginning of the report, the main considerations has
been the security issues and smart home network related
solutions. Then various arguments will be proposed in the
context of security implementations. In the literature review
part, the security issues of the smart home has been discussed.
Based on the major issues or the issues that is relevantly new
will be focused upon. After proper analysis of the circumstances
and available IoT technology, the solution to the security issue
will be provided.
The main problem of the project is to identify the security
issues that is most harmful and providing an utmost solution to
it which can be implemented irrespective of the IoT technology
platform. The report is focused upon a project with the
deliverable of developing a network level security for the
security. In the recent years it has been seen that various attacks
has been executed on the smart homes successfully. The report
provides details of the future works that can be don later on this
project outcome.
2. BACKGROUND/LITERATURE REVIEW
In order to discuss bout the smart home security issues, the
details of the architecture, network, components used and
much more things need to be considered. All the entities that
make up the IoT based smart home system can be exploited by
the cybercriminals to hack into the smart home. At the
beginning of the literature review, the idea of a typical smart
home architecture will be provided.
2.1 Architecture of Smart Home Based on IoT
The smart homes are the combination of different
electronic components and a network. The electronic
components are sensors, controllers, circuits and many more.
The applications are developed for the user mobile device
(smart phones) so the users can control the operations of the
IoT based smart home from distance. The connection is a
significant part of the homes as this makes the smart home a
really advanced technology. These entities are utilized for
designing and developing a dynamic heterogeneous
architecture [6]. These architecture remains the source of smart
home operations. The quality and advancement in the
architecture defines the amount of operations that the smart
home will be performing. The IoT devices is not equipped with
interoperability standards and that is why the connected IoT
devices in a smart home architecture can be controlled directly
via a smartphone or other device. The sensors that are used
within the smart home environment does not have the feature
of connecting to the internet directly [11]. In reality, the
sensors does not have any direct connection with the internet,
the microcontroller provides them all the instruction through
the output ports of it.
Fig 1 Architecture of a typical Smart Home [1]
The internet connection is established in the hub of the
network. The hub works as the local workstation in the smart
home architecture. Basically wireless communication mediums

are selected for establishing the communication between the
hubs and the IoT devices installed in the home. Different
manufacturers of the IoT devices develop their devices based
on different protocols. These protocols are followed by the
architecture while developing the sensor-hub connection. The
hub is connected to the internet connection available at home
via Wi-Fi interface or the Ethernet connection. This decision
depends upon the capabilities of the IoT architecture’s in order
to communicate with the outside world. The quality of
interaction will be judged based on two phenomenon such as
access to internet cloud services that act together with the hub
and properly connected to the IoT elements [1]. The second
phenomenon is direct interaction with the hub through the
internet through the use of the connectivity and services that
hub offers.
The remote interaction with the IoT devices are often done
by considering the above two options. These two phenomenon
must be considered simultaneously while developing the IoT
architecture best remote interaction experience can be provided
to user. There are basically two modes defined in the
architecture to forward instructions from the user device to the
hub [24]. The first one is through the cloud service while the
user is sending instruction from remote location outside the
range of the local network. The second is directly to the hub
through the hub while the user is within the local network. In
the later, no internet access is required as the network (Ethernet
or Wi-Fi) sends the instructions sends the information using
local connection.
2.2 Components of IoT smart home
This device is considered as a lovely alarm clock that is
technologically advanced from the conventional ones. This
device remains close to the bed and analyze the environment in
the room during and before sleep [3]. In order to analyze the
environment, the device uses the state-of-art sensors.
Monitoring devices are used for total monitoring of the
home based IoT system. These devices are connected to the
hub or often used as the hub in case of small scale IoT
implementation. Smart thermostats are used for automation in
the temperature of the home. Wireless speaker systems are a
favorite IoT technology of various smart home owners. This
speakers can be connected from anywhere at the home and
play music wirelessly. Smart lights are used for controlling the
lights of the rooms wirelessly through mobile device or
automatically switch off or on the bulbs [22]. The hub is the
key of connecting the devices to the user device. Various other
IoT devices are used in the smart home that has not been
discussed in this report.
2.3 Privacy Vulnerability
The patterns, contents and metadata of the network traffic
is consisting of various sensitive information of the user of the
smart home. If these entities are hacked by the cybercriminals,
then all the sensitive data will be revealed to the attacker. The
websites were the only way of communicating with the internet
based resources, but with the emerging of cloud and IoT the
usage of the internet has become a vast concept [3]. The IoT
smart home is also connected to the user mobile device, so it
the network of smart home is hacked, the cybercriminals will
get a way to the mobile device in an unauthorized way. The
mobile devices can be hacked for getting personal data of the
user.
2.3.1 IoT traffic analysis strategy
It has been a great way of securing the traffic from the user
device to the IoT hub. In this traffic strategy, the packets will
be considered as the main part to examine. The IP address
adversary can be prevented using the division of traffic packets
as per device strategy are being used. In this methodology, the
network traffic is divided into streams of meaningful data. The
home gateway routers are basically used as the NAT or
network address translator. The purpose of the NAT is to
overwrite the IP address of various IoT connected devices a
sole IP address that has been provided by the ISP [3]. There is
an issues in this method as the counting of the various clients
of the NAT is difficult.
After the distinct streams are separated, the identification of
the IoT device that is responsible for individual streams are
done. It is then possible to map the queries of the DNS to the
associated device. The devices that are manufactured by the
same organization, can communicate using the same IP
address.
2.3.2 A Case of sense sleep monitor
As the domains only holds the sense and hello,
identification of traffic to and fro sense sleep monitor is an
easy task.
Fig 2 Sense sleep monitor network traffic send/receive rates [3]
The study has been conducted for a 12 hour period starting
form 10.40 pm to 10.40 am. The user activity is reason of the
send and receive of the packets. The peak between the 5.20 am
to 7 am shows that the user was out of bed temporarily. This
figure shows a general idea regarding how the IoT device
operates automatically on the basis of the user activities. If the
intruders are able to get hand to these kinds of data then they
can identify the daily activities of the user. This will allow the
intruders to target the home easily as they will know when the
home remains empty. Various other circumstances can be
imagined based on the security flaws of the IoT smart home
technology.
2.4 NDOMUS Framework
The NDN or named data networking is the basis of the
Named Data netwOrking for sMart home aUtomation Systems.
The whole architecture is consisting of three layers such as
thing-layer, NDOMUS and application layer. In the thing layer,
the IoT devices are installed in the home [15]. NDOMUS is
consisting of the operations such as routing of packets, security
protocols, caching of data packets, naming strategy,
hubs and the IoT devices installed in the home. Different
manufacturers of the IoT devices develop their devices based
on different protocols. These protocols are followed by the
architecture while developing the sensor-hub connection. The
hub is connected to the internet connection available at home
via Wi-Fi interface or the Ethernet connection. This decision
depends upon the capabilities of the IoT architecture’s in order
to communicate with the outside world. The quality of
interaction will be judged based on two phenomenon such as
access to internet cloud services that act together with the hub
and properly connected to the IoT elements [1]. The second
phenomenon is direct interaction with the hub through the
internet through the use of the connectivity and services that
hub offers.
The remote interaction with the IoT devices are often done
by considering the above two options. These two phenomenon
must be considered simultaneously while developing the IoT
architecture best remote interaction experience can be provided
to user. There are basically two modes defined in the
architecture to forward instructions from the user device to the
hub [24]. The first one is through the cloud service while the
user is sending instruction from remote location outside the
range of the local network. The second is directly to the hub
through the hub while the user is within the local network. In
the later, no internet access is required as the network (Ethernet
or Wi-Fi) sends the instructions sends the information using
local connection.
2.2 Components of IoT smart home
This device is considered as a lovely alarm clock that is
technologically advanced from the conventional ones. This
device remains close to the bed and analyze the environment in
the room during and before sleep [3]. In order to analyze the
environment, the device uses the state-of-art sensors.
Monitoring devices are used for total monitoring of the
home based IoT system. These devices are connected to the
hub or often used as the hub in case of small scale IoT
implementation. Smart thermostats are used for automation in
the temperature of the home. Wireless speaker systems are a
favorite IoT technology of various smart home owners. This
speakers can be connected from anywhere at the home and
play music wirelessly. Smart lights are used for controlling the
lights of the rooms wirelessly through mobile device or
automatically switch off or on the bulbs [22]. The hub is the
key of connecting the devices to the user device. Various other
IoT devices are used in the smart home that has not been
discussed in this report.
2.3 Privacy Vulnerability
The patterns, contents and metadata of the network traffic
is consisting of various sensitive information of the user of the
smart home. If these entities are hacked by the cybercriminals,
then all the sensitive data will be revealed to the attacker. The
websites were the only way of communicating with the internet
based resources, but with the emerging of cloud and IoT the
usage of the internet has become a vast concept [3]. The IoT
smart home is also connected to the user mobile device, so it
the network of smart home is hacked, the cybercriminals will
get a way to the mobile device in an unauthorized way. The
mobile devices can be hacked for getting personal data of the
user.
2.3.1 IoT traffic analysis strategy
It has been a great way of securing the traffic from the user
device to the IoT hub. In this traffic strategy, the packets will
be considered as the main part to examine. The IP address
adversary can be prevented using the division of traffic packets
as per device strategy are being used. In this methodology, the
network traffic is divided into streams of meaningful data. The
home gateway routers are basically used as the NAT or
network address translator. The purpose of the NAT is to
overwrite the IP address of various IoT connected devices a
sole IP address that has been provided by the ISP [3]. There is
an issues in this method as the counting of the various clients
of the NAT is difficult.
After the distinct streams are separated, the identification of
the IoT device that is responsible for individual streams are
done. It is then possible to map the queries of the DNS to the
associated device. The devices that are manufactured by the
same organization, can communicate using the same IP
address.
2.3.2 A Case of sense sleep monitor
As the domains only holds the sense and hello,
identification of traffic to and fro sense sleep monitor is an
easy task.
Fig 2 Sense sleep monitor network traffic send/receive rates [3]
The study has been conducted for a 12 hour period starting
form 10.40 pm to 10.40 am. The user activity is reason of the
send and receive of the packets. The peak between the 5.20 am
to 7 am shows that the user was out of bed temporarily. This
figure shows a general idea regarding how the IoT device
operates automatically on the basis of the user activities. If the
intruders are able to get hand to these kinds of data then they
can identify the daily activities of the user. This will allow the
intruders to target the home easily as they will know when the
home remains empty. Various other circumstances can be
imagined based on the security flaws of the IoT smart home
technology.
2.4 NDOMUS Framework
The NDN or named data networking is the basis of the
Named Data netwOrking for sMart home aUtomation Systems.
The whole architecture is consisting of three layers such as
thing-layer, NDOMUS and application layer. In the thing layer,
the IoT devices are installed in the home [15]. NDOMUS is
consisting of the operations such as routing of packets, security
protocols, caching of data packets, naming strategy,

configuration of the network and the service model. The
NDOMUS is then connected to the application layer which is
the larger picture of the IoT smart home like home automation
system.
Fig 3 The NDOMUS framework [15]
This methodology is consisted with the naming scheme in
which management and configuration of namespace is done
and task namespace is defined. A prefix to the device is
provided during the initialization of the home network through
which management and configuration of the operations done
by the device are done. The task name space is generally used
for tracking and controlling purpose.
The service model divides the home applications into three
parts called as pull, event-triggered push and periodic push.
The NDOMUS model that has been considered in this
methodology is capable of supporting all the three strategies
[34]. This is a strong point in the favor of this methodology.
The NDN generally supports this pull service model. Periodic
pushing provides the benefit of periodically measuring the
reading for each of the sensors. Event-triggered pushing is
referred to the process of taking measurements triggered by
predefined events.
Smart home applications uses the 1C:1S communication
along with the multiparty communication. The NDN natively
support the multi-consumer communication via data catching
and interest aggregation [15]. As a single data in the NDOMUS
framework of Multi-source communication is related to only
one pending request multi differentiated interests are used for
retrieving data.
2.5 Device management
Deice management is consisted of five parts such as the
proxy layer, device management layer and service enablement
layer. Different protocols and communication technologies are
used for developing the proxy layer. This layer is essential in
the Smart Home network as the IoT devices or the hub is
connected to each other through the BLE module, Wi-Fi or any
other device [28]. In order to establish the interaction of the
devices with the network, the proxy layer configured with
various communication technologies and protocols. The legacy
devices ate setup using the CoRE Link Format so that it can be
ensured that the smart home is consisting with legacy and
smart IoT devices.
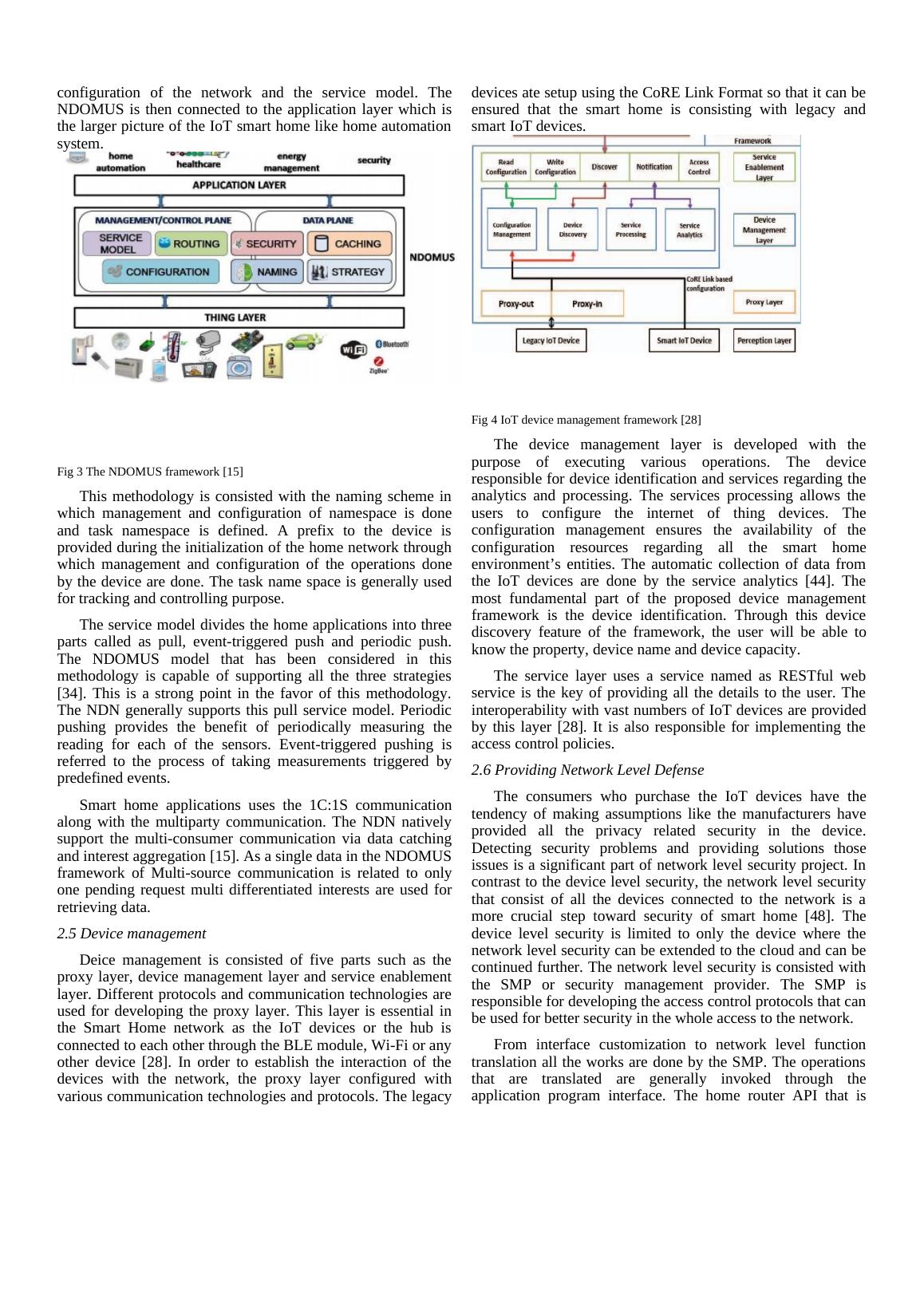
Fig 4 IoT device management framework [28]
The device management layer is developed with the
purpose of executing various operations. The device
responsible for device identification and services regarding the
analytics and processing. The services processing allows the
users to configure the internet of thing devices. The
configuration management ensures the availability of the
configuration resources regarding all the smart home
environment’s entities. The automatic collection of data from
the IoT devices are done by the service analytics [44]. The
most fundamental part of the proposed device management
framework is the device identification. Through this device
discovery feature of the framework, the user will be able to
know the property, device name and device capacity.
The service layer uses a service named as RESTful web
service is the key of providing all the details to the user. The
interoperability with vast numbers of IoT devices are provided
by this layer [28]. It is also responsible for implementing the
access control policies.
2.6 Providing Network Level Defense
The consumers who purchase the IoT devices have the
tendency of making assumptions like the manufacturers have
provided all the privacy related security in the device.
Detecting security problems and providing solutions those
issues is a significant part of network level security project. In
contrast to the device level security, the network level security
that consist of all the devices connected to the network is a
more crucial step toward security of smart home [48]. The
device level security is limited to only the device where the
network level security can be extended to the cloud and can be
continued further. The network level security is consisted with
the SMP or security management provider. The SMP is
responsible for developing the access control protocols that can
be used for better security in the whole access to the network.
From interface customization to network level function
translation all the works are done by the SMP. The operations
that are translated are generally invoked through the
application program interface. The home router API that is
NDOMUS is then connected to the application layer which is
the larger picture of the IoT smart home like home automation
system.
Fig 3 The NDOMUS framework [15]
This methodology is consisted with the naming scheme in
which management and configuration of namespace is done
and task namespace is defined. A prefix to the device is
provided during the initialization of the home network through
which management and configuration of the operations done
by the device are done. The task name space is generally used
for tracking and controlling purpose.
The service model divides the home applications into three
parts called as pull, event-triggered push and periodic push.
The NDOMUS model that has been considered in this
methodology is capable of supporting all the three strategies
[34]. This is a strong point in the favor of this methodology.
The NDN generally supports this pull service model. Periodic
pushing provides the benefit of periodically measuring the
reading for each of the sensors. Event-triggered pushing is
referred to the process of taking measurements triggered by
predefined events.
Smart home applications uses the 1C:1S communication
along with the multiparty communication. The NDN natively
support the multi-consumer communication via data catching
and interest aggregation [15]. As a single data in the NDOMUS
framework of Multi-source communication is related to only
one pending request multi differentiated interests are used for
retrieving data.
2.5 Device management
Deice management is consisted of five parts such as the
proxy layer, device management layer and service enablement
layer. Different protocols and communication technologies are
used for developing the proxy layer. This layer is essential in
the Smart Home network as the IoT devices or the hub is
connected to each other through the BLE module, Wi-Fi or any
other device [28]. In order to establish the interaction of the
devices with the network, the proxy layer configured with
various communication technologies and protocols. The legacy
devices ate setup using the CoRE Link Format so that it can be
ensured that the smart home is consisting with legacy and
smart IoT devices.
Fig 4 IoT device management framework [28]
The device management layer is developed with the
purpose of executing various operations. The device
responsible for device identification and services regarding the
analytics and processing. The services processing allows the
users to configure the internet of thing devices. The
configuration management ensures the availability of the
configuration resources regarding all the smart home
environment’s entities. The automatic collection of data from
the IoT devices are done by the service analytics [44]. The
most fundamental part of the proposed device management
framework is the device identification. Through this device
discovery feature of the framework, the user will be able to
know the property, device name and device capacity.
The service layer uses a service named as RESTful web
service is the key of providing all the details to the user. The
interoperability with vast numbers of IoT devices are provided
by this layer [28]. It is also responsible for implementing the
access control policies.
2.6 Providing Network Level Defense
The consumers who purchase the IoT devices have the
tendency of making assumptions like the manufacturers have
provided all the privacy related security in the device.
Detecting security problems and providing solutions those
issues is a significant part of network level security project. In
contrast to the device level security, the network level security
that consist of all the devices connected to the network is a
more crucial step toward security of smart home [48]. The
device level security is limited to only the device where the
network level security can be extended to the cloud and can be
continued further. The network level security is consisted with
the SMP or security management provider. The SMP is
responsible for developing the access control protocols that can
be used for better security in the whole access to the network.
From interface customization to network level function
translation all the works are done by the SMP. The operations
that are translated are generally invoked through the
application program interface. The home router API that is
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Applications of IoT in Connected Cars, Connected Cars and Connected Carslg...
|13
|2938
|189
Internet of Things & Cyber Securitylg...
|19
|5950
|53
Literature Review on Internet of Thingslg...
|9
|2313
|74
IoT for Smart Homelg...
|15
|5166
|57
Smart Home Systems underlined with IoT technologylg...
|24
|6566
|31
Security Issues and Countermeasures in Internet of Things (IoT)lg...
|9
|2591
|194
