Network Infrastructure Design and Cloud Proposal for CompName
VerifiedAdded on 2023/06/13
|18
|2850
|452
Report
AI Summary
This report provides a detailed analysis and proposed IT infrastructure solution for CompName.org.Au, a software development company with 900 hosts across three floors. It includes a discussion of required IT infrastructure components, a three-layer hierarchical network model, and an analysis of current IT infrastructure requirements. The report features a geographical diagram of the network, considerations for scaling the network, identification of necessary services and servers (DHCP, WEB, DNS), a logical network diagram with justification, and an IP addressing plan. Furthermore, the report proposes a cloud-based design, identifying potential cloud service organizations like AWS, and discusses dynamic application scaling using virtualization. Network simulation diagrams, including access layer diagrams, DHCP, DNS, and web server configurations, are included. The goal is to improve network security, scalability, and efficiency for CompName.org.Au.

Running head: IT INFRASTRUCTURE
IT Infrastructure
Name of the Student
Name of the University
Author’s Note
IT Infrastructure
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT INFRASTRUCTURE
Table of Contents
Introduction......................................................................................................................................3
Discussion of the IT infrastructure Components Required.............................................................4
Three layer hierarchical Model........................................................................................................5
Introduction..................................................................................................................................5
Analysis of the current IT Infrastructure Requirements..............................................................5
Geographical Diagram of the network........................................................................................5
Possibility of scaling of the organization network......................................................................6
Identification of service and servers required..............................................................................6
Logical Network Diagram and Justification................................................................................7
List of IP address and Network Mask for all the network...........................................................7
Cloud Based design proposal...........................................................................................................8
Identification of two cloud service organization.........................................................................8
List of service provided by the organization...............................................................................8
Dynamic Application Scaling using virtualization....................................................................10
Network Simulation.......................................................................................................................10
Access Layer Diagram...............................................................................................................10
DHCP Configuration.................................................................................................................11
DNS and Web Server Configuration.........................................................................................12
Demonstration and Explanation................................................................................................13
IT INFRASTRUCTURE
Table of Contents
Introduction......................................................................................................................................3
Discussion of the IT infrastructure Components Required.............................................................4
Three layer hierarchical Model........................................................................................................5
Introduction..................................................................................................................................5
Analysis of the current IT Infrastructure Requirements..............................................................5
Geographical Diagram of the network........................................................................................5
Possibility of scaling of the organization network......................................................................6
Identification of service and servers required..............................................................................6
Logical Network Diagram and Justification................................................................................7
List of IP address and Network Mask for all the network...........................................................7
Cloud Based design proposal...........................................................................................................8
Identification of two cloud service organization.........................................................................8
List of service provided by the organization...............................................................................8
Dynamic Application Scaling using virtualization....................................................................10
Network Simulation.......................................................................................................................10
Access Layer Diagram...............................................................................................................10
DHCP Configuration.................................................................................................................11
DNS and Web Server Configuration.........................................................................................12
Demonstration and Explanation................................................................................................13

2
IT INFRASTRUCTURE
Conclusion and Recommendations................................................................................................14
References......................................................................................................................................15
IT INFRASTRUCTURE
Conclusion and Recommendations................................................................................................14
References......................................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT INFRASTRUCTURE
Introduction
Aims and Objectives
The following are aims for the development of the network framework for CompName.org.Au.
An analysis should be performed on the current framework of the organization and
identification of the requirement of the project for aligning the business with the network
framework.
An analysis should be made on the number of hosts required to be connected to the
network and the address plan should be created according to it.
There must be scope of expansion of the current network and it should be expanded for
the accommodation of the future growth of the company.
A secure zone must be created for installing the DNS, WEB and DHCP servers for
serving the different needs of the users connected with the network framework.
Proper authorization should be used for connecting with the service and access the
resources of the organization.
There are different objectives that are identified for the development of the network
infrastructure are listed below:
To configure the networking devices according to the network plan and secure it from
illegal access
To isolate the server from the employees for reducing the risk of data steal and malware
injection via USB or other sources.
To use an appropriate domain name for the web server and configure the firewall for
denying the unknown users to access the servers installed in the dmz zone.
IT INFRASTRUCTURE
Introduction
Aims and Objectives
The following are aims for the development of the network framework for CompName.org.Au.
An analysis should be performed on the current framework of the organization and
identification of the requirement of the project for aligning the business with the network
framework.
An analysis should be made on the number of hosts required to be connected to the
network and the address plan should be created according to it.
There must be scope of expansion of the current network and it should be expanded for
the accommodation of the future growth of the company.
A secure zone must be created for installing the DNS, WEB and DHCP servers for
serving the different needs of the users connected with the network framework.
Proper authorization should be used for connecting with the service and access the
resources of the organization.
There are different objectives that are identified for the development of the network
infrastructure are listed below:
To configure the networking devices according to the network plan and secure it from
illegal access
To isolate the server from the employees for reducing the risk of data steal and malware
injection via USB or other sources.
To use an appropriate domain name for the web server and configure the firewall for
denying the unknown users to access the servers installed in the dmz zone.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT INFRASTRUCTURE
The report is created for CompName.org.Au where two network solutions are proposed
according to the needs of the organization. A local area network is designed for connecting the
different areas of the building and cisco packet tracer is used for the development of the network
solution. For the development of the network the requirement of the organization is analyzed. A
cloud solution is proposed for DR management and increasing the flexibility of the network. The
benefits for the adoption of the cloud platform is discussed in the report with the details of the
configuration of the server and the addressing plan followed for the development of the network.
The organization CompName.org.au has its network connected with 900 hosts located in
different floors of its building. It is a software development company and it building has three
adjacent floors. The company have the requirement to implement new technologies for the
management of the network and increase its security such that the intruders cannot access the
core resources such as the DNS, Web and the DHCP servers.
Discussion of the IT infrastructure Components Required
A dedicated server design architecture is applied for developing the network solution and
thus a dmz zone is created for the installing the servers and isolate them form the internal users
to access them. The creation of the demilitarized zone helps in improvement the security of the
network and protect the network from internal risks. A wall mounted rack should be used for the
installation of the switch and the router. Proper cooling should be provided to the network
devices such that they does not get overheated and their performance level does not drops
because overheating can drop the performance and thus causing congestion and loss of data
packets in the network. A cisco 5505 ASA firewall should be installed for securing the entry and
the exit point of the network and block the unknown request. The integration of the cloud service
IT INFRASTRUCTURE
The report is created for CompName.org.Au where two network solutions are proposed
according to the needs of the organization. A local area network is designed for connecting the
different areas of the building and cisco packet tracer is used for the development of the network
solution. For the development of the network the requirement of the organization is analyzed. A
cloud solution is proposed for DR management and increasing the flexibility of the network. The
benefits for the adoption of the cloud platform is discussed in the report with the details of the
configuration of the server and the addressing plan followed for the development of the network.
The organization CompName.org.au has its network connected with 900 hosts located in
different floors of its building. It is a software development company and it building has three
adjacent floors. The company have the requirement to implement new technologies for the
management of the network and increase its security such that the intruders cannot access the
core resources such as the DNS, Web and the DHCP servers.
Discussion of the IT infrastructure Components Required
A dedicated server design architecture is applied for developing the network solution and
thus a dmz zone is created for the installing the servers and isolate them form the internal users
to access them. The creation of the demilitarized zone helps in improvement the security of the
network and protect the network from internal risks. A wall mounted rack should be used for the
installation of the switch and the router. Proper cooling should be provided to the network
devices such that they does not get overheated and their performance level does not drops
because overheating can drop the performance and thus causing congestion and loss of data
packets in the network. A cisco 5505 ASA firewall should be installed for securing the entry and
the exit point of the network and block the unknown request. The integration of the cloud service

5
IT INFRASTRUCTURE
with the in-house servers can increase the efficiency of the network and reduce the cost of
management of the network.
Three layer hierarchical Model
Introduction
The network proposed for CompName.org.au is divided into three layers such as the core
layer, access layer and distribution layer for reducing the effort of management. The core layer
consist of the central router and the servers and it acts as the heart of the network because all the
data packets in the network are transferred through the core layer. The access layer consists of
the switch that acts as the mediator or link between the distribution layer and the core layer of the
network. In the distribution layer the hosts are present that connects with the server via the
access layer switch.
Analysis of the current IT Infrastructure Requirements
The current requirement of the organization is to create an in-house database
administrative framework such that the employees in the organization can use it to
communication and increase their efficiency. The files are required to be stored in the central
database and accessed by the other employees working in the organization. A DHCP server is
required to be configured following the addressing scheme for allocation of the IP address to the
hosts connected in different subnets. A web server should also be configured with the domain
name “CompName.org.Au” for accessing the resources.
Geographical Diagram of the network
All the floors of the building are needed to be covered and a similar type of topology is
used for connecting all the hosts in different floors of the building. The network device should be
IT INFRASTRUCTURE
with the in-house servers can increase the efficiency of the network and reduce the cost of
management of the network.
Three layer hierarchical Model
Introduction
The network proposed for CompName.org.au is divided into three layers such as the core
layer, access layer and distribution layer for reducing the effort of management. The core layer
consist of the central router and the servers and it acts as the heart of the network because all the
data packets in the network are transferred through the core layer. The access layer consists of
the switch that acts as the mediator or link between the distribution layer and the core layer of the
network. In the distribution layer the hosts are present that connects with the server via the
access layer switch.
Analysis of the current IT Infrastructure Requirements
The current requirement of the organization is to create an in-house database
administrative framework such that the employees in the organization can use it to
communication and increase their efficiency. The files are required to be stored in the central
database and accessed by the other employees working in the organization. A DHCP server is
required to be configured following the addressing scheme for allocation of the IP address to the
hosts connected in different subnets. A web server should also be configured with the domain
name “CompName.org.Au” for accessing the resources.
Geographical Diagram of the network
All the floors of the building are needed to be covered and a similar type of topology is
used for connecting all the hosts in different floors of the building. The network device should be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT INFRASTRUCTURE
connected with serial fiber optics cable for getting larger bandwidth and reducing the congestion
in the network. The flow of the data should be monitored for enforcing traffic management and
preventing loss of data packets in the network. The branch office located in different
geographical location is required to be connected by the implementation of VPN connection and
securing the transaction between the remote site and the local site.
Possibility of scaling of the organization network
The current network is designed such that it can be expanded according to the growth of
the organization for the accommodation of the new hosts per subnet. The subnet plan is created
with extra address for meeting the future needs. The network solution should accommodate the
growth upto five years and thus latest technology are applied for designing the network solution.
Identification of service and servers required
The following services and the servers are required for the development of the network solution
such as:
DHCP service – use for automatically assigning IP address to the host connected with the
network and thus the DHCP server is configured according to the created IP addressing plan.
WEB & DNS Service –Used for hosting a web page or portal used by the employees for
management of the information and reach the other users connected in the network.
IT INFRASTRUCTURE
connected with serial fiber optics cable for getting larger bandwidth and reducing the congestion
in the network. The flow of the data should be monitored for enforcing traffic management and
preventing loss of data packets in the network. The branch office located in different
geographical location is required to be connected by the implementation of VPN connection and
securing the transaction between the remote site and the local site.
Possibility of scaling of the organization network
The current network is designed such that it can be expanded according to the growth of
the organization for the accommodation of the new hosts per subnet. The subnet plan is created
with extra address for meeting the future needs. The network solution should accommodate the
growth upto five years and thus latest technology are applied for designing the network solution.
Identification of service and servers required
The following services and the servers are required for the development of the network solution
such as:
DHCP service – use for automatically assigning IP address to the host connected with the
network and thus the DHCP server is configured according to the created IP addressing plan.
WEB & DNS Service –Used for hosting a web page or portal used by the employees for
management of the information and reach the other users connected in the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT INFRASTRUCTURE
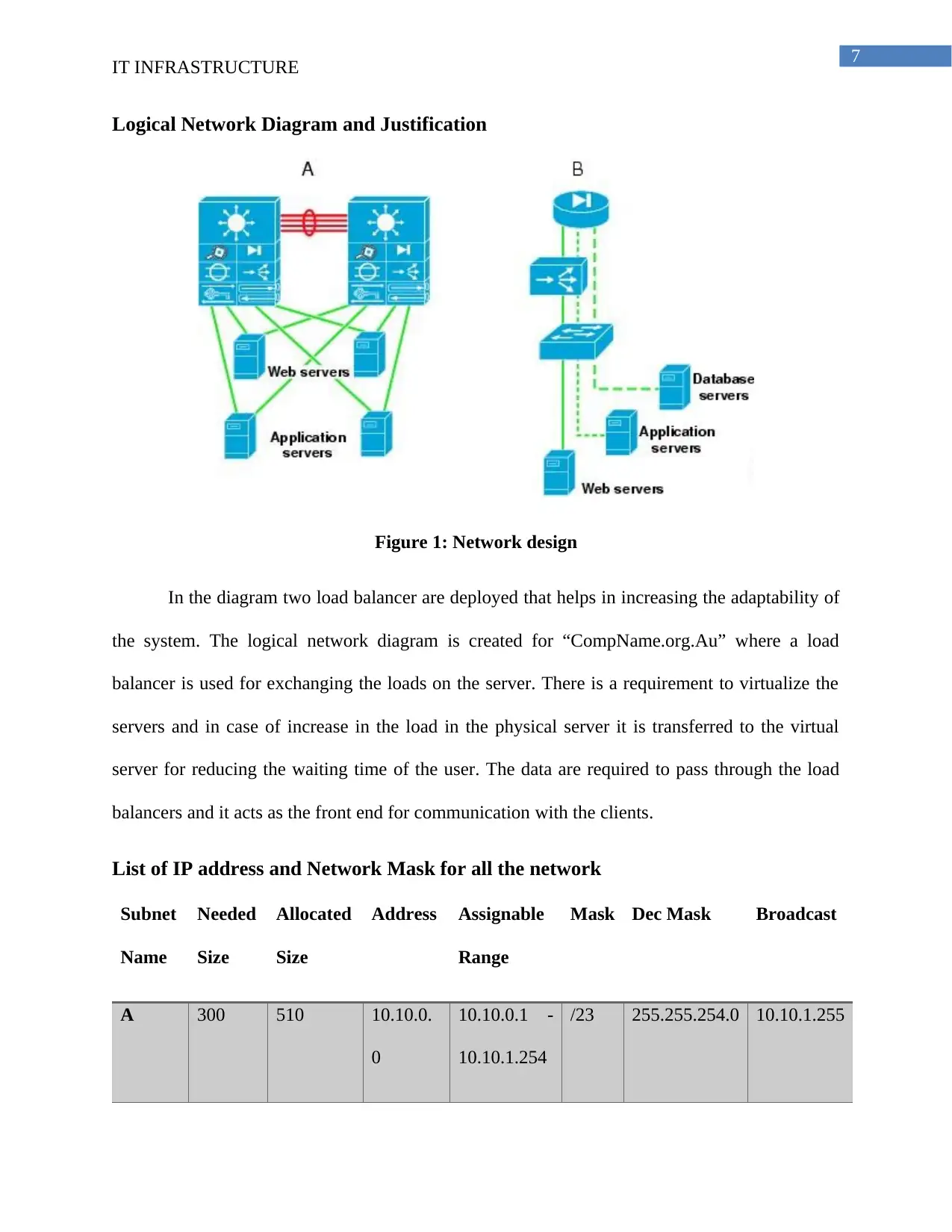
Logical Network Diagram and Justification
Figure 1: Network design
In the diagram two load balancer are deployed that helps in increasing the adaptability of
the system. The logical network diagram is created for “CompName.org.Au” where a load
balancer is used for exchanging the loads on the server. There is a requirement to virtualize the
servers and in case of increase in the load in the physical server it is transferred to the virtual
server for reducing the waiting time of the user. The data are required to pass through the load
balancers and it acts as the front end for communication with the clients.
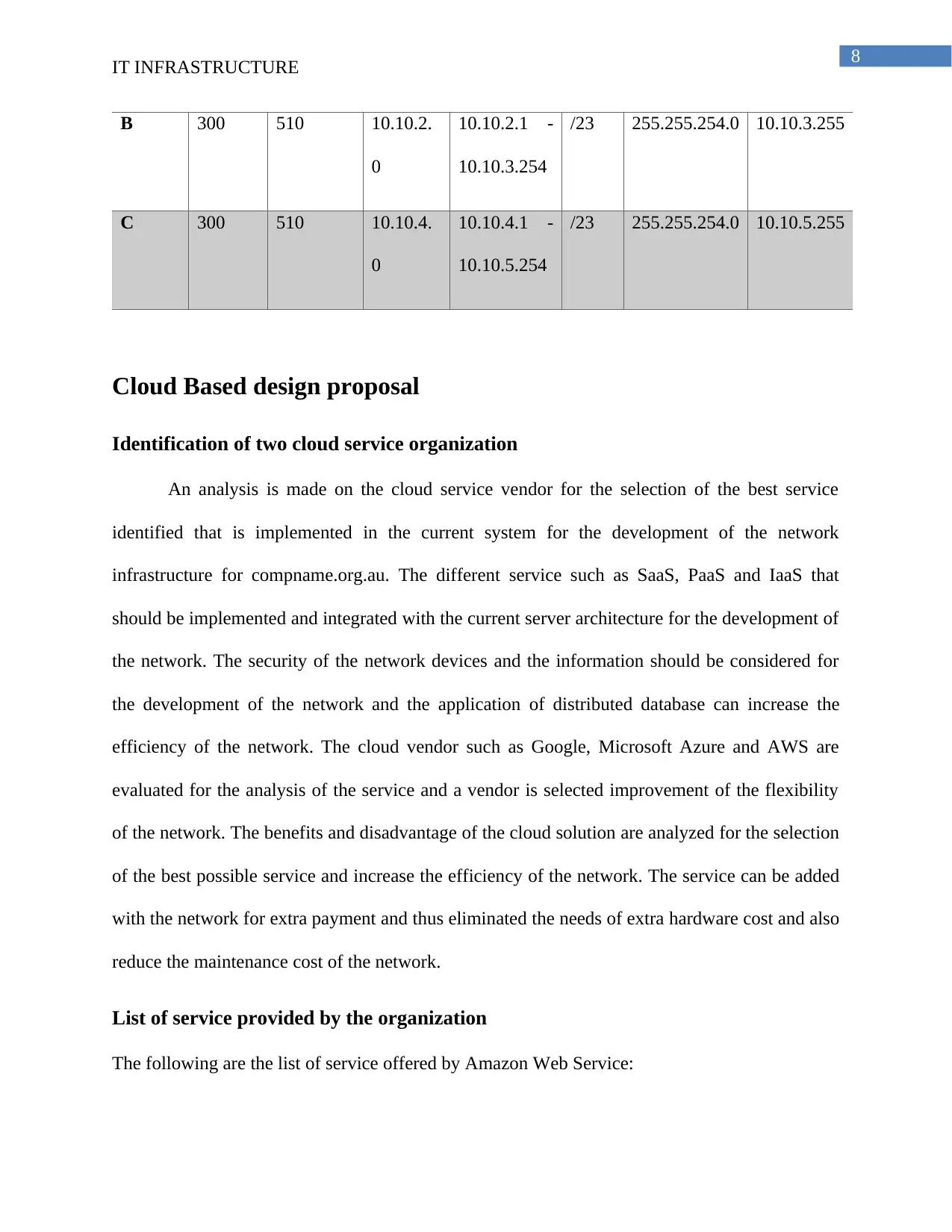
List of IP address and Network Mask for all the network
Subnet
Name
Needed
Size
Allocated
Size
Address Assignable
Range
Mask Dec Mask Broadcast
A 300 510 10.10.0.
0
10.10.0.1 -
10.10.1.254
/23 255.255.254.0 10.10.1.255
IT INFRASTRUCTURE
Logical Network Diagram and Justification
Figure 1: Network design
In the diagram two load balancer are deployed that helps in increasing the adaptability of
the system. The logical network diagram is created for “CompName.org.Au” where a load
balancer is used for exchanging the loads on the server. There is a requirement to virtualize the
servers and in case of increase in the load in the physical server it is transferred to the virtual
server for reducing the waiting time of the user. The data are required to pass through the load
balancers and it acts as the front end for communication with the clients.
List of IP address and Network Mask for all the network
Subnet
Name
Needed
Size
Allocated
Size
Address Assignable
Range
Mask Dec Mask Broadcast
A 300 510 10.10.0.
0
10.10.0.1 -
10.10.1.254
/23 255.255.254.0 10.10.1.255
8
IT INFRASTRUCTURE
B 300 510 10.10.2.
0
10.10.2.1 -
10.10.3.254
/23 255.255.254.0 10.10.3.255
C 300 510 10.10.4.
0
10.10.4.1 -
10.10.5.254
/23 255.255.254.0 10.10.5.255
Cloud Based design proposal
Identification of two cloud service organization
An analysis is made on the cloud service vendor for the selection of the best service
identified that is implemented in the current system for the development of the network
infrastructure for compname.org.au. The different service such as SaaS, PaaS and IaaS that
should be implemented and integrated with the current server architecture for the development of
the network. The security of the network devices and the information should be considered for
the development of the network and the application of distributed database can increase the
efficiency of the network. The cloud vendor such as Google, Microsoft Azure and AWS are
evaluated for the analysis of the service and a vendor is selected improvement of the flexibility
of the network. The benefits and disadvantage of the cloud solution are analyzed for the selection
of the best possible service and increase the efficiency of the network. The service can be added
with the network for extra payment and thus eliminated the needs of extra hardware cost and also
reduce the maintenance cost of the network.
List of service provided by the organization
The following are the list of service offered by Amazon Web Service:
IT INFRASTRUCTURE
B 300 510 10.10.2.
0
10.10.2.1 -
10.10.3.254
/23 255.255.254.0 10.10.3.255
C 300 510 10.10.4.
0
10.10.4.1 -
10.10.5.254
/23 255.255.254.0 10.10.5.255
Cloud Based design proposal
Identification of two cloud service organization
An analysis is made on the cloud service vendor for the selection of the best service
identified that is implemented in the current system for the development of the network
infrastructure for compname.org.au. The different service such as SaaS, PaaS and IaaS that
should be implemented and integrated with the current server architecture for the development of
the network. The security of the network devices and the information should be considered for
the development of the network and the application of distributed database can increase the
efficiency of the network. The cloud vendor such as Google, Microsoft Azure and AWS are
evaluated for the analysis of the service and a vendor is selected improvement of the flexibility
of the network. The benefits and disadvantage of the cloud solution are analyzed for the selection
of the best possible service and increase the efficiency of the network. The service can be added
with the network for extra payment and thus eliminated the needs of extra hardware cost and also
reduce the maintenance cost of the network.
List of service provided by the organization
The following are the list of service offered by Amazon Web Service:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT INFRASTRUCTURE
Computation – It can be used for increasing the computation power and without adding
more hardware in the in-house arrangement and serve more customers at a time.
Storage – It can be used for getting more storage for storing more files and documents in
the cloud storage.
Migration – It is used as a commercial platform to move the current resources and
increase the proficiency of the system.
Database – It is used for management of the unstructured data generated from different
sources of the network and record the details of the employees working in the
organization.
Substance and Network Delivery – It is used for enforcing authorization and reduce the
congestion and better management of the different components of the network.
Developer Tools – It is used for testing the codes developed by the software development
team working in the organization and minimizes the cost for purchasing new applications
for testing.
Management Instruments – It is used for the management of the assets of the organization
and improvement of the cloud service framework and secure it from external agents.
Security – Different security options are provided such as private clouds that can be used
for storing the sensitive data and information about the organization in the cloud
platform.
Mobile benefits – It can be used for testing mobile applications and building mobile apps
for fifferent platforms.
IT INFRASTRUCTURE
Computation – It can be used for increasing the computation power and without adding
more hardware in the in-house arrangement and serve more customers at a time.
Storage – It can be used for getting more storage for storing more files and documents in
the cloud storage.
Migration – It is used as a commercial platform to move the current resources and
increase the proficiency of the system.
Database – It is used for management of the unstructured data generated from different
sources of the network and record the details of the employees working in the
organization.
Substance and Network Delivery – It is used for enforcing authorization and reduce the
congestion and better management of the different components of the network.
Developer Tools – It is used for testing the codes developed by the software development
team working in the organization and minimizes the cost for purchasing new applications
for testing.
Management Instruments – It is used for the management of the assets of the organization
and improvement of the cloud service framework and secure it from external agents.
Security – Different security options are provided such as private clouds that can be used
for storing the sensitive data and information about the organization in the cloud
platform.
Mobile benefits – It can be used for testing mobile applications and building mobile apps
for fifferent platforms.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
IT INFRASTRUCTURE
IoT support – It can be used for the management of the data generated from the IoT
devices such as motion sensors, CCTV and storing them for free up the space on the local
servers.
Analytics – It can be used for forecasting the future demands of the software application
and used for administrative purpose for better control on the business process.
Dynamic Application Scaling using virtualization
The web server and the database server needs to be virtualized for handling the
emergency conditions. The load balancers are used for dividing the loads on physical server to
the virtual servers for increasing the availability of the data and reducing the waiting time of the
users. The virtualization of the server helps in increasing the redundancy of the network and can
be used for creating backup of the current state of the network.
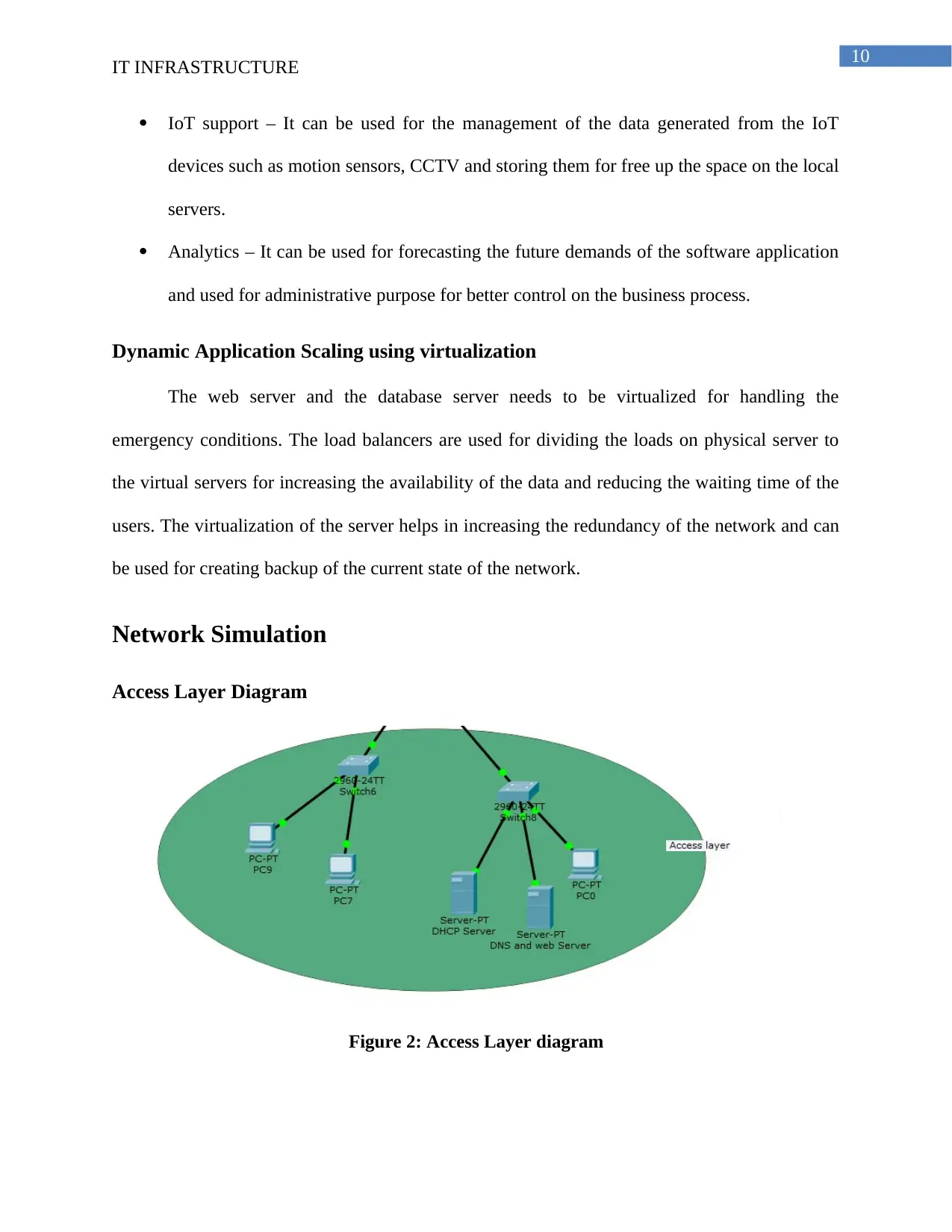
Network Simulation
Access Layer Diagram
Figure 2: Access Layer diagram
IT INFRASTRUCTURE
IoT support – It can be used for the management of the data generated from the IoT
devices such as motion sensors, CCTV and storing them for free up the space on the local
servers.
Analytics – It can be used for forecasting the future demands of the software application
and used for administrative purpose for better control on the business process.
Dynamic Application Scaling using virtualization
The web server and the database server needs to be virtualized for handling the
emergency conditions. The load balancers are used for dividing the loads on physical server to
the virtual servers for increasing the availability of the data and reducing the waiting time of the
users. The virtualization of the server helps in increasing the redundancy of the network and can
be used for creating backup of the current state of the network.
Network Simulation
Access Layer Diagram
Figure 2: Access Layer diagram
11
IT INFRASTRUCTURE
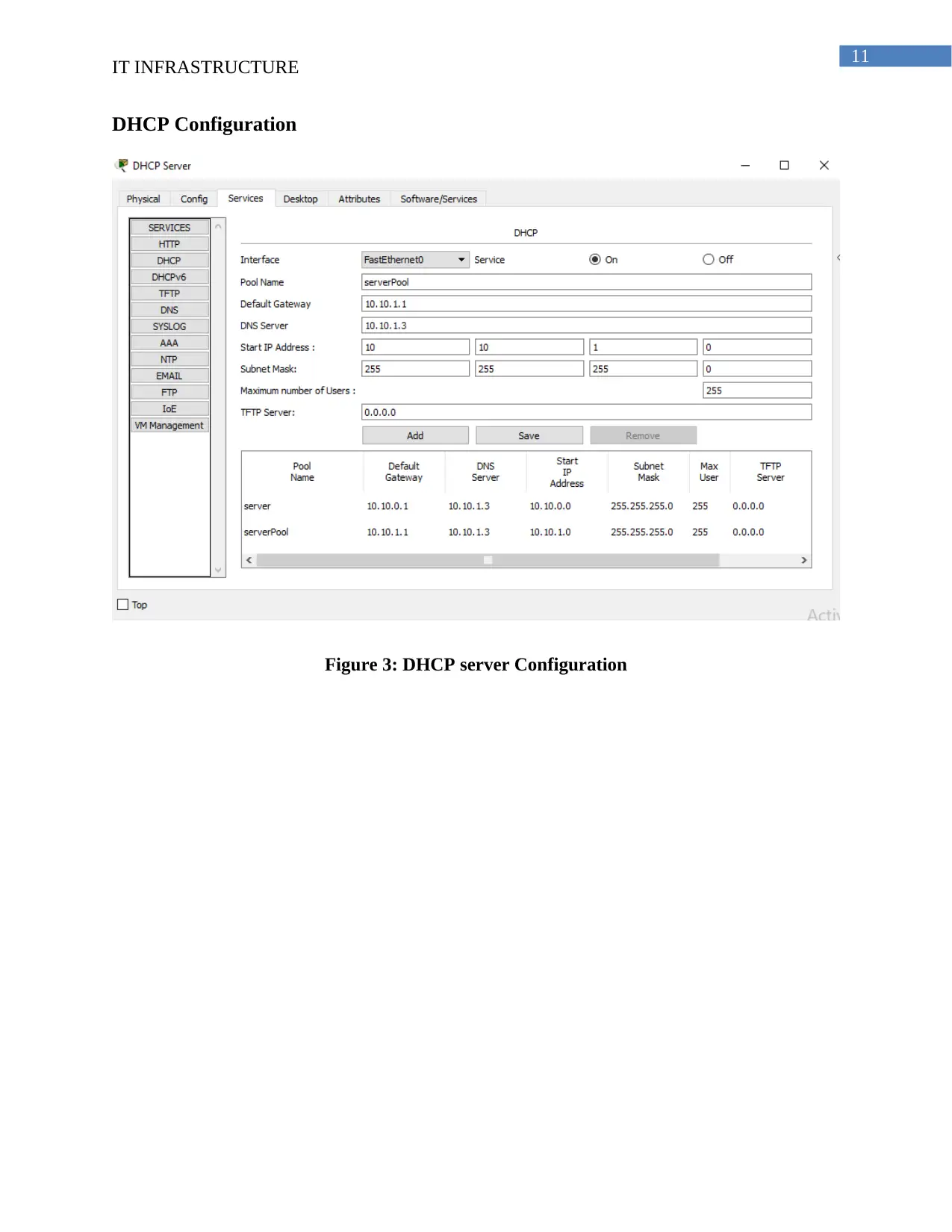
DHCP Configuration
Figure 3: DHCP server Configuration
IT INFRASTRUCTURE
DHCP Configuration
Figure 3: DHCP server Configuration
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





