IT Infrastructure Management Report: ABC Company Network Analysis
VerifiedAdded on 2022/08/23
|12
|2597
|17
Report
AI Summary
This report provides a comprehensive analysis of the IT infrastructure for ABC Company, addressing the organization's requirements for providing IS services, including email, webpage, and database access to its staff and customers. The report begins with an introduction to the company's services and outlines the structure of the report. It identifies the essential network devices, such as switches, routers, and firewalls, required to support the company's operations across three floors, including the main office and shared printers. The report then delves into the communication software and applications used in client-server interactions, particularly focusing on email, network printing, and the World Wide Web. It also explains the working of the network devices within the OSI model, using a scenario of email transmission to illustrate the process through each layer. The conclusion summarizes the importance of the network infrastructure for ABC Company and the role of the OSI model in facilitating communication, with references to key concepts and models. The report is based on the provided assignment brief which includes the requirements of the ABC organization, such as the number of computers, printers, and the services offered.

Running head: IT INFRASTRUCTURE MANAGEMENT
IT INFRASTRUCTURE MANAGEMENT
Name of the Student
Name of the University
Author Note
IT INFRASTRUCTURE MANAGEMENT
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT INFRASTRUCTURE MANAGEMENT
Table of Contents
Introduction:...............................................................................................................................3
Network Devices Required........................................................................................................3
Communication Software and Application................................................................................4
Working of the Network Devices..............................................................................................6
Conclusion................................................................................................................................10
References................................................................................................................................11
Table of Contents
Introduction:...............................................................................................................................3
Network Devices Required........................................................................................................3
Communication Software and Application................................................................................4
Working of the Network Devices..............................................................................................6
Conclusion................................................................................................................................10
References................................................................................................................................11

2IT INFRASTRUCTURE MANAGEMENT
Introduction:
The ABC Company provides IS services to its services and clients that include
webpage, database and email. The floor plan of the company includes three floors where the
ground floor is the main office of the company. The three offices consist of various devices
such as computers, printers and many more. The website of the ABC Company provides
general information to the customers and clients can purchase various products and services.
All the employees of the company have an email account.
The report discusses about the devices of the network those are required in order to
accomplish the requirements of the organization. The report focuses on the communication
software between the client and the server. Lastly, the report discusses about the OSI model
and the working of the model using a diagram.
Network Devices Required
The network devices those are implemented in the ABC organization include
switches, routers that include ISP routers and service routers, firewalls, printers and the
computers in the three floors of the Company. These network devices will help the ABC
Company in order to accomplish the requirements of the organization consisting of the day to
day to actions of the company.
A switch is a network device that is utilised at the access of the layer 2 of the OSI
layer. A switch can be utilised in order to connect more than one host to the network. In this
network, a switch is utilised in order to connect all the computers and the printers to the
network of the company (Teuscher, Palsky and Palfreyman 2018). A switch sends a message
to a particular host. When any of the host on the network or a switch forwards a message to
any other host on the similar switch or network, the switch obtains and then decodes the
frames in order to read the portion of physical address of the message. There are various
Introduction:
The ABC Company provides IS services to its services and clients that include
webpage, database and email. The floor plan of the company includes three floors where the
ground floor is the main office of the company. The three offices consist of various devices
such as computers, printers and many more. The website of the ABC Company provides
general information to the customers and clients can purchase various products and services.
All the employees of the company have an email account.
The report discusses about the devices of the network those are required in order to
accomplish the requirements of the organization. The report focuses on the communication
software between the client and the server. Lastly, the report discusses about the OSI model
and the working of the model using a diagram.
Network Devices Required
The network devices those are implemented in the ABC organization include
switches, routers that include ISP routers and service routers, firewalls, printers and the
computers in the three floors of the Company. These network devices will help the ABC
Company in order to accomplish the requirements of the organization consisting of the day to
day to actions of the company.
A switch is a network device that is utilised at the access of the layer 2 of the OSI
layer. A switch can be utilised in order to connect more than one host to the network. In this
network, a switch is utilised in order to connect all the computers and the printers to the
network of the company (Teuscher, Palsky and Palfreyman 2018). A switch sends a message
to a particular host. When any of the host on the network or a switch forwards a message to
any other host on the similar switch or network, the switch obtains and then decodes the
frames in order to read the portion of physical address of the message. There are various
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT INFRASTRUCTURE MANAGEMENT
types of switches including modular switches, fixed configuration switches and stackable
switches.
A router is a device of switching for the networks that is capable of routing packets of
network that is based on their addresses to various other devices and networks. Among
different things, they are utilised for access of internet or to connect the offices of branch to
the main office through virtual private network (Alani 2017). The router works at the layer 3
of the OSI model. A router has more than one interface and obtains packets of data via them.
The main function of the router is to examine the packets of data those are incoming and then
determine the interface to forward the packets of data to.
A firewall is used in the network of the ABC Company. It can be a component of
hardware or program of software that is designed in order to administer and filter the traffic
of network that is incoming or outgoing. The firewalls are installed in order to prevent attacks
on the network (Shin 2019). A firewall usually works on the layer 3 and layer 4 of the model
of OSI that is network and the transport layer. The firewalls also work on the layer 7 of
model of OSI that is application layer.
Communication Software and Application
The client-server communication includes two mechanisms a client and a server. There
are usually more than one client in communication with a single server. The client first sends
a request to the server and then the server respond to the requests of the client. A client does
not split its assets but the client requests services from the server (de Souza Soares et al
2018). The clients start sessions of communications with the servers that make the incoming
requests wait. The communication software and application of client server include email,
network printing and the World Wide Web. The characteristics of the client-server
communication are as follows (Oakes et al 2019):
types of switches including modular switches, fixed configuration switches and stackable
switches.
A router is a device of switching for the networks that is capable of routing packets of
network that is based on their addresses to various other devices and networks. Among
different things, they are utilised for access of internet or to connect the offices of branch to
the main office through virtual private network (Alani 2017). The router works at the layer 3
of the OSI model. A router has more than one interface and obtains packets of data via them.
The main function of the router is to examine the packets of data those are incoming and then
determine the interface to forward the packets of data to.
A firewall is used in the network of the ABC Company. It can be a component of
hardware or program of software that is designed in order to administer and filter the traffic
of network that is incoming or outgoing. The firewalls are installed in order to prevent attacks
on the network (Shin 2019). A firewall usually works on the layer 3 and layer 4 of the model
of OSI that is network and the transport layer. The firewalls also work on the layer 7 of
model of OSI that is application layer.
Communication Software and Application
The client-server communication includes two mechanisms a client and a server. There
are usually more than one client in communication with a single server. The client first sends
a request to the server and then the server respond to the requests of the client. A client does
not split its assets but the client requests services from the server (de Souza Soares et al
2018). The clients start sessions of communications with the servers that make the incoming
requests wait. The communication software and application of client server include email,
network printing and the World Wide Web. The characteristics of the client-server
communication are as follows (Oakes et al 2019):
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT INFRASTRUCTURE MANAGEMENT
The client server computing works with a response and request system. The client first
sends a request to the server and then the server responds with the information that is
desired
The server and the client must follow protocol of communication in order interact among
each other. All the protocols of communication are easily available at the layer of
application
A server can put up a restricted number of requests of client. Therefore, is utilises a
system that is based on the priority in order to react to requests
The attacks of Denial of Service delays the capability of the servers in order to react to
the requests of the client by inundating it with requests those are generally false.
The employees of the company use email in order to communicate among themselves.
This is an application of client-server communication. The email servers communicate with
the help of protocols of Email. The transfer agents of mail communicate among each other
over the internet utilising the protocol of SMTP (Hu, Peng and Wang 2018). The recipient of
mail transfer agent sends the email on the mail server and then the mail is stored until the user
accepts it.
The ABC Company has a shared printer in the main office and six printers each on the
two floors. The network printer is used for the communication of the client-server. A server
of print or the printer is a device that connects the printers to the computers of client over the
network of the ABC Company (Mehta 2019). It accepts the jobs of print from the computers
of the company and then sends various jobs to the proper printers thus queuing the jobs
locally in order to accommodate the fact that work can reach faster then the printer in the
company can handle.
The client server computing works with a response and request system. The client first
sends a request to the server and then the server responds with the information that is
desired
The server and the client must follow protocol of communication in order interact among
each other. All the protocols of communication are easily available at the layer of
application
A server can put up a restricted number of requests of client. Therefore, is utilises a
system that is based on the priority in order to react to requests
The attacks of Denial of Service delays the capability of the servers in order to react to
the requests of the client by inundating it with requests those are generally false.
The employees of the company use email in order to communicate among themselves.
This is an application of client-server communication. The email servers communicate with
the help of protocols of Email. The transfer agents of mail communicate among each other
over the internet utilising the protocol of SMTP (Hu, Peng and Wang 2018). The recipient of
mail transfer agent sends the email on the mail server and then the mail is stored until the user
accepts it.
The ABC Company has a shared printer in the main office and six printers each on the
two floors. The network printer is used for the communication of the client-server. A server
of print or the printer is a device that connects the printers to the computers of client over the
network of the ABC Company (Mehta 2019). It accepts the jobs of print from the computers
of the company and then sends various jobs to the proper printers thus queuing the jobs
locally in order to accommodate the fact that work can reach faster then the printer in the
company can handle.

5IT INFRASTRUCTURE MANAGEMENT
The company also utilises the World Wide Web for the communication of client server.
The main idea behind the World Wide Web is generally based on application of client server
and the documents of hypertext. The ABC Company uses the internet where the World Wide
Web is present (Pesce 2017).
Working of the Network Devices
The ABC Company has 25 computers in the building and the main office of the
company has two computers and a shared printer. There are six printers in each of the floors
of the company. Each of the employees of the company has an email account and they
communicate with each other with the help of email. The network devices those are used in
the network of the company are routers switches and firewalls.
When an employee from the ground floor sends an email to the email at the third
floor, the email is sent to the outgoing mail server that is SMTP. The SMTP belongs to the
layer 7 of the OSI model (Englehardt, Han and Narayanan 2018). The job of SMTP is to
transport the email to its destination. The SMTP checks the address in order to see where to
send the email and it does not understand the way to read the name of domain. The SMTP
requires a IP address that is computer friendly in order to locate and then deliver the email to
the user in the third floor. In order to locate the address of IP, the SMTP then contacts the
server of DNS. The SMTP has all the required information about the employee in order to
send the email from its server on to the MTA server of the email recipients (Zhang and
Williamson 2018). The MTP then determines the address to send the email, if the user is
utilising a client that generally works through POP or IMAP. The recipient will then be
notified of the new email.
The employee in the ground floor will send an email to the employee to the third
floor. The employee will be using the client of email. It can be outlook express and many
The company also utilises the World Wide Web for the communication of client server.
The main idea behind the World Wide Web is generally based on application of client server
and the documents of hypertext. The ABC Company uses the internet where the World Wide
Web is present (Pesce 2017).
Working of the Network Devices
The ABC Company has 25 computers in the building and the main office of the
company has two computers and a shared printer. There are six printers in each of the floors
of the company. Each of the employees of the company has an email account and they
communicate with each other with the help of email. The network devices those are used in
the network of the company are routers switches and firewalls.
When an employee from the ground floor sends an email to the email at the third
floor, the email is sent to the outgoing mail server that is SMTP. The SMTP belongs to the
layer 7 of the OSI model (Englehardt, Han and Narayanan 2018). The job of SMTP is to
transport the email to its destination. The SMTP checks the address in order to see where to
send the email and it does not understand the way to read the name of domain. The SMTP
requires a IP address that is computer friendly in order to locate and then deliver the email to
the user in the third floor. In order to locate the address of IP, the SMTP then contacts the
server of DNS. The SMTP has all the required information about the employee in order to
send the email from its server on to the MTA server of the email recipients (Zhang and
Williamson 2018). The MTP then determines the address to send the email, if the user is
utilising a client that generally works through POP or IMAP. The recipient will then be
notified of the new email.
The employee in the ground floor will send an email to the employee to the third
floor. The employee will be using the client of email. It can be outlook express and many
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT INFRASTRUCTURE MANAGEMENT
more. This procedure then goes in to the layer of application of the OSI model. It offers the
interface for the user in order to instruct the computer the way to handle the data. The email
client will use the SMTP protocol (Mishra, Panwar and Singh 2018).
Then the email begins to operate on the layer of transport of the model of OSI. In this
layer, the content of email will be changes into the formats of network. The text of the email
will be changed to ASCII, the images will be changed to JPEG, and the other essential things
such as the encryption and compression of data will happen at this layer. With the data
compression in this layer can upgrade the throughput of the data along the layer those are at
the layer of the OSI model (Tan 2018).
Then the email will begin to operate at the session layer, and then this layer will be
responsible to start, handle and terminate the connection at the other end. The session layer is
responsible in order to keep the connection with the Head of IT in order to send the email
correctly.
After this layer, it begins to operate at the transport layer of the OSI model. This layer
will determine the reliability and the flow of control. In this layer, the email will get broken
into segments in order to transfer them. The segments will be transmitted as packets of UDP
or TCP. The email will utilise the port number 25 of TCP and utilise the protocol of SMTP
The network layer is responsible for the routing of the packets of data. In order to
send the packets of data, the receiver must be identified. The routes will be defined in this
layer and it will add the sender and receiver address of IP to the packets of data (Sadhasivam
et al 2017).
In the data link layer, the packets of email data will be prepared to be transmitted over
the Ethernet. The packets of data will be changed to frames of data. This address defines the
physical address to the frames of data.
more. This procedure then goes in to the layer of application of the OSI model. It offers the
interface for the user in order to instruct the computer the way to handle the data. The email
client will use the SMTP protocol (Mishra, Panwar and Singh 2018).
Then the email begins to operate on the layer of transport of the model of OSI. In this
layer, the content of email will be changes into the formats of network. The text of the email
will be changed to ASCII, the images will be changed to JPEG, and the other essential things
such as the encryption and compression of data will happen at this layer. With the data
compression in this layer can upgrade the throughput of the data along the layer those are at
the layer of the OSI model (Tan 2018).
Then the email will begin to operate at the session layer, and then this layer will be
responsible to start, handle and terminate the connection at the other end. The session layer is
responsible in order to keep the connection with the Head of IT in order to send the email
correctly.
After this layer, it begins to operate at the transport layer of the OSI model. This layer
will determine the reliability and the flow of control. In this layer, the email will get broken
into segments in order to transfer them. The segments will be transmitted as packets of UDP
or TCP. The email will utilise the port number 25 of TCP and utilise the protocol of SMTP
The network layer is responsible for the routing of the packets of data. In order to
send the packets of data, the receiver must be identified. The routes will be defined in this
layer and it will add the sender and receiver address of IP to the packets of data (Sadhasivam
et al 2017).
In the data link layer, the packets of email data will be prepared to be transmitted over
the Ethernet. The packets of data will be changed to frames of data. This address defines the
physical address to the frames of data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT INFRASTRUCTURE MANAGEMENT
After this, the data is ready in order to be transmitted to the side of the receiver. In the
physical layer, the frames of data will be prepared and it will be changed to bits. Then the
email goes to the email server and after that it will go to the switch and it will be transmitted
to the physical layer of the OSI model of the third floor employee and then procedure will be
followed where the email will be decrypted and the employee can view the email that is sent
to him by the ground floor employee.
After this, the data is ready in order to be transmitted to the side of the receiver. In the
physical layer, the frames of data will be prepared and it will be changed to bits. Then the
email goes to the email server and after that it will go to the switch and it will be transmitted
to the physical layer of the OSI model of the third floor employee and then procedure will be
followed where the email will be decrypted and the employee can view the email that is sent
to him by the ground floor employee.
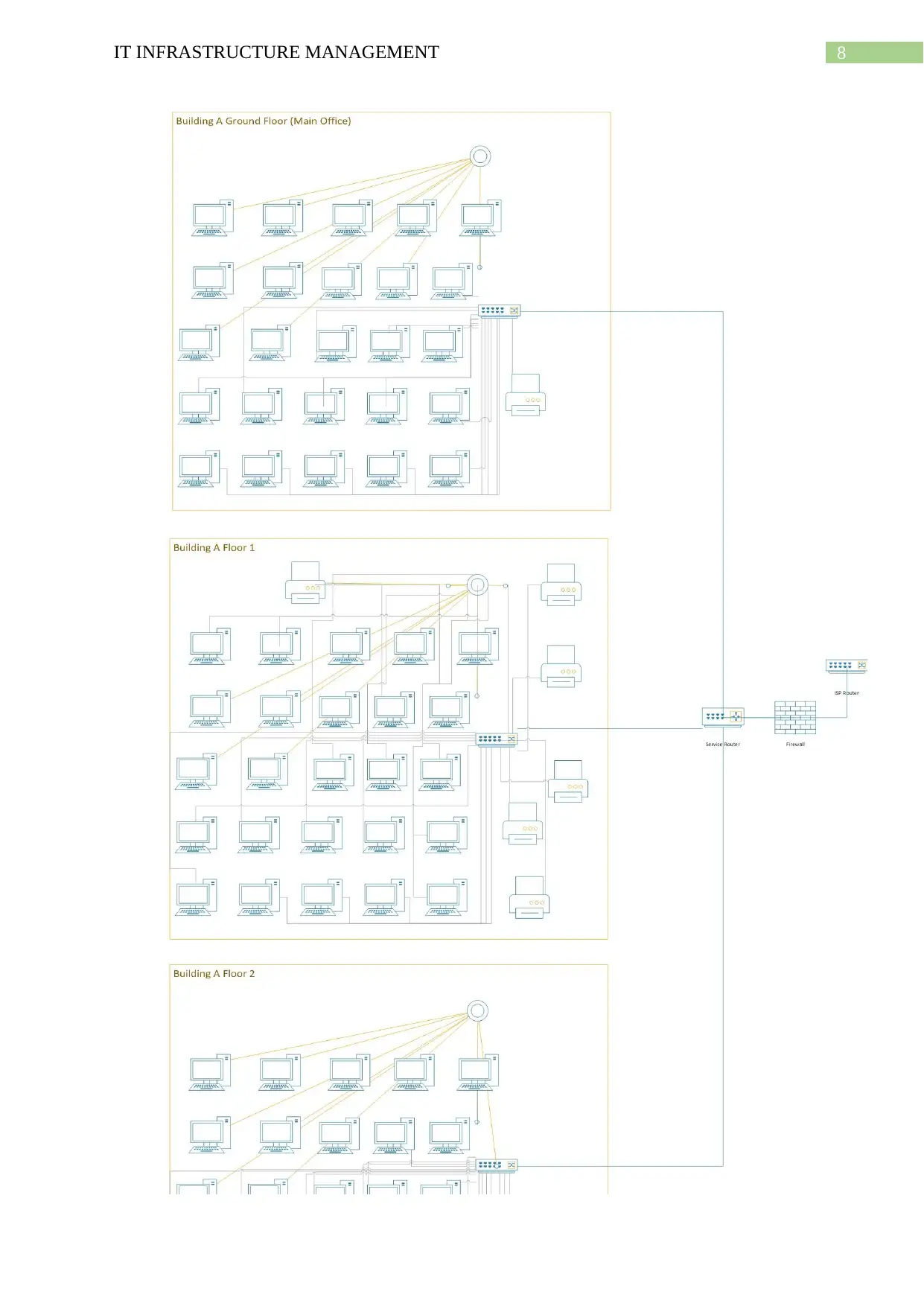
8IT INFRASTRUCTURE MANAGEMENT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT INFRASTRUCTURE MANAGEMENT
(Figure 1: Network Diagram
Source: Created By User)
Conclusion
From the report, it can be inferred that the network infrastructure is very important for
the ABC Company. The network requirements that are utilised in the network include switch,
routers and firewalls. The report discusses about the layer on which the network requirements
belong and the report provides an overview of the functions of the network devices. The
report provides an overview of the client server communication and the characteristics of the
client server communication. The softwares and the applications those are used in the client
server communication are identified and mentioned in the report. The report provides an
overview of a scenario and the explanation of the scenario. The report provides an overview
of the way a email is sent and how the mail can be sent with the help of the OSI model. The
OSI model is very important in order to send the information from the employee in the
ground floor to the employee in the third floor. Lastly, the network devices are very
important as it also helps in sending the email.
(Figure 1: Network Diagram
Source: Created By User)
Conclusion
From the report, it can be inferred that the network infrastructure is very important for
the ABC Company. The network requirements that are utilised in the network include switch,
routers and firewalls. The report discusses about the layer on which the network requirements
belong and the report provides an overview of the functions of the network devices. The
report provides an overview of the client server communication and the characteristics of the
client server communication. The softwares and the applications those are used in the client
server communication are identified and mentioned in the report. The report provides an
overview of a scenario and the explanation of the scenario. The report provides an overview
of the way a email is sent and how the mail can be sent with the help of the OSI model. The
OSI model is very important in order to send the information from the employee in the
ground floor to the employee in the third floor. Lastly, the network devices are very
important as it also helps in sending the email.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT INFRASTRUCTURE MANAGEMENT
References
Alani, M.M., 2017. Domestic Router Functions Configuration. In Guide to Cisco Routers
Configuration (pp. 11-39). Springer, Cham.
de Souza Soares, E.F., Thiago, R.M., Azevedo, L.G., de Bayser, M., da Silva, V.T. and
Cerqueira, R.F.D.G., 2018, March. Evaluation of Server Push Technologies for Scalable
Client-Server Communication. In 2018 IEEE Symposium on Service-Oriented System
Engineering (SOSE) (pp. 1-10). IEEE.
Englehardt, S., Han, J. and Narayanan, A., 2018. I never signed up for this! Privacy
implications of email tracking. Proceedings on Privacy Enhancing Technologies, 2018(1),
pp.109-126.
Hu, H., Peng, P. and Wang, G., 2018, September. Towards understanding the adoption of
anti-spoofing protocols in email systems. In 2018 IEEE Cybersecurity Development
(SecDev) (pp. 94-101). IEEE.
Mehta, K.S., 2019. Information Security Analysis of Modern Wireless Printers (Doctoral
dissertation, Illinois Institute of Technology).
Mishra, S., Panwar, A. and Singh, Y., 2018. Voice Based Email System for Visually
Impaired.
Oakes, E., Kline, J., Cahn, A., Funkhouser, K. and Barford, P., 2019, June. A Residential
Client-side Perspective on SSL Certificates. In 2019 Network Traffic Measurement and
Analysis Conference (TMA) (pp. 185-192). IEEE.
Pesce, M., 2017, April. The Web-Wide World. In Proceedings of the 26th International
Conference on World Wide Web (pp. 3-3).
References
Alani, M.M., 2017. Domestic Router Functions Configuration. In Guide to Cisco Routers
Configuration (pp. 11-39). Springer, Cham.
de Souza Soares, E.F., Thiago, R.M., Azevedo, L.G., de Bayser, M., da Silva, V.T. and
Cerqueira, R.F.D.G., 2018, March. Evaluation of Server Push Technologies for Scalable
Client-Server Communication. In 2018 IEEE Symposium on Service-Oriented System
Engineering (SOSE) (pp. 1-10). IEEE.
Englehardt, S., Han, J. and Narayanan, A., 2018. I never signed up for this! Privacy
implications of email tracking. Proceedings on Privacy Enhancing Technologies, 2018(1),
pp.109-126.
Hu, H., Peng, P. and Wang, G., 2018, September. Towards understanding the adoption of
anti-spoofing protocols in email systems. In 2018 IEEE Cybersecurity Development
(SecDev) (pp. 94-101). IEEE.
Mehta, K.S., 2019. Information Security Analysis of Modern Wireless Printers (Doctoral
dissertation, Illinois Institute of Technology).
Mishra, S., Panwar, A. and Singh, Y., 2018. Voice Based Email System for Visually
Impaired.
Oakes, E., Kline, J., Cahn, A., Funkhouser, K. and Barford, P., 2019, June. A Residential
Client-side Perspective on SSL Certificates. In 2019 Network Traffic Measurement and
Analysis Conference (TMA) (pp. 185-192). IEEE.
Pesce, M., 2017, April. The Web-Wide World. In Proceedings of the 26th International
Conference on World Wide Web (pp. 3-3).

11IT INFRASTRUCTURE MANAGEMENT
Sadhasivam, J., Jayavel, S., Jeyakumar, B. and Merchant, S., 2017. Hocs: Host
oscommunication service layer. International Journal of Civil Engineering and
Technology, 8(11), pp.35-41.
Shin, Y., 2019. Cross-VM Cache Timing Attacks on Virtualized Network Functions. IEICE
Transactions on Information and Systems, 102(9), pp.1874-1877.
Tan, T.Z., 2018. Separation of Layers.
Teuscher, D., Palsky, K. and Palfreyman, C.Y., 2018. Inverse functions: Why switch the
variable?. Mathematics Teacher, 111(5), pp.374-381.
Zhang, Z. and Williamson, C., 2018, December. A Campus-level View of Outlook Email
Traffic. In Proceedings of the 2018 VII International Conference on Network,
Communication and Computing (pp. 299-306).
Sadhasivam, J., Jayavel, S., Jeyakumar, B. and Merchant, S., 2017. Hocs: Host
oscommunication service layer. International Journal of Civil Engineering and
Technology, 8(11), pp.35-41.
Shin, Y., 2019. Cross-VM Cache Timing Attacks on Virtualized Network Functions. IEICE
Transactions on Information and Systems, 102(9), pp.1874-1877.
Tan, T.Z., 2018. Separation of Layers.
Teuscher, D., Palsky, K. and Palfreyman, C.Y., 2018. Inverse functions: Why switch the
variable?. Mathematics Teacher, 111(5), pp.374-381.
Zhang, Z. and Williamson, C., 2018, December. A Campus-level View of Outlook Email
Traffic. In Proceedings of the 2018 VII International Conference on Network,
Communication and Computing (pp. 299-306).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





