COMP247 Data Communications Assignment Solution - General Answers
VerifiedAdded on 2023/06/09
|33
|9025
|178
Homework Assignment
AI Summary
This document provides comprehensive solutions to a COMP247 Data Communications assignment. The answers cover a wide range of topics, starting with general networking concepts like network layers, hosts, switches, routers, and protocols. It then delves into Local Area Networks (LANs), discussing topics such as logical and physical topologies, broadcast and collision domains, and the components of a wired LAN, including network interface cards (NICs). The document further explains the differences between hub-based and switch-based LANs, and details concepts like Carrier Sense Multiple Access with Collision Detection (CSMA/CD). The assignment also explores error-checking mechanisms, including parity and CRC, and discusses token passing and various Automatic Repeat Request (ARQ) protocols such as Stop and Wait ARQ, addressing their performance implications in different network scenarios. The answers are detailed, providing clear explanations and definitions for each question.

Running head: NETWORKING
NETWORKING
NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORKING
General
Answers to question number 1
The network layer provides the means of transferring variable-length network packets from a
source to a destination host via one or more networks. Within the service layering semantics
of the OSI network architecture, the network layer responds to service requests from the
transport layer and issues service requests to the data link layer.
Functions of the network layer include:
Connectionless communication
For example, IP is connectionless, in that a data packet can travel from a sender to a recipient
without the recipient having to send an acknowledgement. Connection-oriented protocols
exist at other, higher layers of the OSI model.
Host addressing
Every host in the network must have a unique address that determines where it is. This
address is normally assigned from a hierarchical system. For example, you can be "Fred
Murphy" to people in your house, "Fred Murphy, 1 Main Street" to Dubliners, or "Fred
Murphy, 1 Main Street, Dublin" to people in Ireland, or "Fred Murphy, 1 Main Street,
Dublin, Ireland" to people anywhere in the world. On the Internet, addresses are known as IP
addresses.
Message forwarding
Since many networks are partitioned into subnetworks and connect to other networks for
wide-area communications, networks use specialized hosts, called gateways or routers, to
forward packets between networks.
NETWORKING
General
Answers to question number 1
The network layer provides the means of transferring variable-length network packets from a
source to a destination host via one or more networks. Within the service layering semantics
of the OSI network architecture, the network layer responds to service requests from the
transport layer and issues service requests to the data link layer.
Functions of the network layer include:
Connectionless communication
For example, IP is connectionless, in that a data packet can travel from a sender to a recipient
without the recipient having to send an acknowledgement. Connection-oriented protocols
exist at other, higher layers of the OSI model.
Host addressing
Every host in the network must have a unique address that determines where it is. This
address is normally assigned from a hierarchical system. For example, you can be "Fred
Murphy" to people in your house, "Fred Murphy, 1 Main Street" to Dubliners, or "Fred
Murphy, 1 Main Street, Dublin" to people in Ireland, or "Fred Murphy, 1 Main Street,
Dublin, Ireland" to people anywhere in the world. On the Internet, addresses are known as IP
addresses.
Message forwarding
Since many networks are partitioned into subnetworks and connect to other networks for
wide-area communications, networks use specialized hosts, called gateways or routers, to
forward packets between networks.

2
NETWORKING
Answer to question number 2
A host (also known as "network host") is a computer or other device that communicates with
other hosts on a network. Hosts on a network include clients and servers -- that send or
receive data, services or applications.
The router forwards data packets along networks. It is connected to at least two networks,
commonly two LANs or WANs or a LAN and its ISP's network. Routers are located at
gateways, the places where two or more networks connect. Routers use headers and
forwarding tables to determine the best path for forwarding the packets, and they use
protocols to communicate with each other and configure the best route between any two
hosts.
In networks the switch is the device that filters and forwards packets between LAN segments.
Switches operate at the data link layer (layer 2) and sometimes the network layer (layer 3) of
the OSI Reference Model and therefore support any packet protocol. LANs that use switches
to join segments are called switched LANs or, in the case of Ethernet networks, switched
Ethernet LANs.
Answer to question number 3
A protocol is a set of rules and guidelines for communicating data. Rules are defined for each
step and process during communication between two or more computers. Networks have to
follow these rules to successfully transmit data.
Answer to question number 4
Data communication networks can affect businesses by being the foundations for distributed
systems in which information system applications are divided among a network of
computers. Data communication networks facilitate more efficient use of computers and
NETWORKING
Answer to question number 2
A host (also known as "network host") is a computer or other device that communicates with
other hosts on a network. Hosts on a network include clients and servers -- that send or
receive data, services or applications.
The router forwards data packets along networks. It is connected to at least two networks,
commonly two LANs or WANs or a LAN and its ISP's network. Routers are located at
gateways, the places where two or more networks connect. Routers use headers and
forwarding tables to determine the best path for forwarding the packets, and they use
protocols to communicate with each other and configure the best route between any two
hosts.
In networks the switch is the device that filters and forwards packets between LAN segments.
Switches operate at the data link layer (layer 2) and sometimes the network layer (layer 3) of
the OSI Reference Model and therefore support any packet protocol. LANs that use switches
to join segments are called switched LANs or, in the case of Ethernet networks, switched
Ethernet LANs.
Answer to question number 3
A protocol is a set of rules and guidelines for communicating data. Rules are defined for each
step and process during communication between two or more computers. Networks have to
follow these rules to successfully transmit data.
Answer to question number 4
Data communication networks can affect businesses by being the foundations for distributed
systems in which information system applications are divided among a network of
computers. Data communication networks facilitate more efficient use of computers and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORKING
improve the day-to-day control of a business by providing faster information flow. They also
provide message transfer services to allow computer users to talk to one another via
electronic mail.
Answer to question number 5
Scalability is an attribute that describes the ability of a process, network, software or
organization to grow and manage increased demand. A system, business or software that is
described as scalable has an advantage because it is more adaptable to the changing needs or
demands of its users or clients.
Compatibility is the capacity for two systems to work together without having to be altered to
do so. Compatible software applications use the same data formats. For example, if word
processor applications are compatible, the user should be able to open their document files in
either product.
Heterogeneous computing environments are a reality today. Users purchase systems from
many vendors to implement the solutions they need. Standardization and clear interfaces are
critical to a heterogeneous environment, enabling users to develop strategies for
communicating throughout their network.
Local Area Network
Answer to question number 1
A Hub is a networking device that allows one to connect multiple PCs to a single network.
Hubs may be based on Ethernet, Fire wire, or USB connections. A switch is a control unit
that turns the flow of electricity on or off in a circuit. It may also be used to route information
patterns in streaming electronic data sent over networks. In the context of a network, a switch
NETWORKING
improve the day-to-day control of a business by providing faster information flow. They also
provide message transfer services to allow computer users to talk to one another via
electronic mail.
Answer to question number 5
Scalability is an attribute that describes the ability of a process, network, software or
organization to grow and manage increased demand. A system, business or software that is
described as scalable has an advantage because it is more adaptable to the changing needs or
demands of its users or clients.
Compatibility is the capacity for two systems to work together without having to be altered to
do so. Compatible software applications use the same data formats. For example, if word
processor applications are compatible, the user should be able to open their document files in
either product.
Heterogeneous computing environments are a reality today. Users purchase systems from
many vendors to implement the solutions they need. Standardization and clear interfaces are
critical to a heterogeneous environment, enabling users to develop strategies for
communicating throughout their network.
Local Area Network
Answer to question number 1
A Hub is a networking device that allows one to connect multiple PCs to a single network.
Hubs may be based on Ethernet, Fire wire, or USB connections. A switch is a control unit
that turns the flow of electricity on or off in a circuit. It may also be used to route information
patterns in streaming electronic data sent over networks. In the context of a network, a switch
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORKING
is a computer networking device that connects network segments. Hence a switch is better
than a Hub.
Answer to question number 2
A logical topology is how devices appear connected to the user. A physical topology is how
they are actually interconnected with wires and cables. For example, in a shared Ethernet
network that uses hubs rather than switches, the logical topology appears as if every node is
connected to a common bus that runs from node to node. However, its physical topology is a
star, in which every node on the network connects to a central hub.
Answer to question number 3
A broadcast domain is a logical division of a computer network, in which all nodes can reach
each other by broadcast at the data link layer. A broadcast domain can be within the same
LAN segment or it can be bridged to other LAN segments. ... Routers and other higher-layer
devices form boundaries between broadcast domains.
Answer to question number 4
A collision domain is a network segment connected by a shared medium or through repeaters
where data packets may collide with one another while being sent. The collision domain
applies particularly in wireless networks, but also affected early versions of Ethernet.
Answer to question number 5
The basic components of a wired LAN are the NICs, circuits, access points, and network
operating systems - The network interface card (NIC) allows the computer to be physically
connected to the network cable, which provides the physical layer connection among the
computers in the network The circuits are the cables that connect devices together. In a LAN,
these cables are generally twisted pair from the client to the hub or server. Outside the
NETWORKING
is a computer networking device that connects network segments. Hence a switch is better
than a Hub.
Answer to question number 2
A logical topology is how devices appear connected to the user. A physical topology is how
they are actually interconnected with wires and cables. For example, in a shared Ethernet
network that uses hubs rather than switches, the logical topology appears as if every node is
connected to a common bus that runs from node to node. However, its physical topology is a
star, in which every node on the network connects to a central hub.
Answer to question number 3
A broadcast domain is a logical division of a computer network, in which all nodes can reach
each other by broadcast at the data link layer. A broadcast domain can be within the same
LAN segment or it can be bridged to other LAN segments. ... Routers and other higher-layer
devices form boundaries between broadcast domains.
Answer to question number 4
A collision domain is a network segment connected by a shared medium or through repeaters
where data packets may collide with one another while being sent. The collision domain
applies particularly in wireless networks, but also affected early versions of Ethernet.
Answer to question number 5
The basic components of a wired LAN are the NICs, circuits, access points, and network
operating systems - The network interface card (NIC) allows the computer to be physically
connected to the network cable, which provides the physical layer connection among the
computers in the network The circuits are the cables that connect devices together. In a LAN,
these cables are generally twisted pair from the client to the hub or server. Outside the

5
NETWORKING
building, fiber optic is generally used. Network hubs and switches serve two purposes. First,
they provide an easy way to connect network cables. Network cables can be directly
connected by splicing two cables together. Second, many hubs and switches act as repeaters
or amplifiers. Signals can travel only so far in a network cables before they attenuate and can
no longer be recognized.
Answer to question number 6
A network interface card (NIC) is a circuit board or card that is installed in a computer so that
it can be connected to a network. A network interface card provides the computer with a
dedicated, full-time connection to a network.
Answer to question number 7
A Hub is a networking device that allows one to connect multiple PCs to a single network.
Hubs may be based on Ethernet, Fire wire, or USB connections. A switch is a control unit
that turns the flow of electricity on or off in a circuit. It may also be used to route information
patterns in streaming electronic data sent over networks. In the context of a network, a switch
is a computer networking device that connects network segments. Hence a switch is better
than a Hub. In a shared Ethernet network that uses hubs rather than switches, the logical
topology appears as if every node is connected to a common bus that runs from node to node.
However, its physical topology is a star, in which every node on the network connects to a
central hub.
Answer to question number 8
Carrier Sense Multiple Access with Collision Detection is a type of protocol for networks that
helps to triage transmissions and control network traffic. collision detection is the process by
which a node determines that a collision has occurred. Collisions occur with most networks,
NETWORKING
building, fiber optic is generally used. Network hubs and switches serve two purposes. First,
they provide an easy way to connect network cables. Network cables can be directly
connected by splicing two cables together. Second, many hubs and switches act as repeaters
or amplifiers. Signals can travel only so far in a network cables before they attenuate and can
no longer be recognized.
Answer to question number 6
A network interface card (NIC) is a circuit board or card that is installed in a computer so that
it can be connected to a network. A network interface card provides the computer with a
dedicated, full-time connection to a network.
Answer to question number 7
A Hub is a networking device that allows one to connect multiple PCs to a single network.
Hubs may be based on Ethernet, Fire wire, or USB connections. A switch is a control unit
that turns the flow of electricity on or off in a circuit. It may also be used to route information
patterns in streaming electronic data sent over networks. In the context of a network, a switch
is a computer networking device that connects network segments. Hence a switch is better
than a Hub. In a shared Ethernet network that uses hubs rather than switches, the logical
topology appears as if every node is connected to a common bus that runs from node to node.
However, its physical topology is a star, in which every node on the network connects to a
central hub.
Answer to question number 8
Carrier Sense Multiple Access with Collision Detection is a type of protocol for networks that
helps to triage transmissions and control network traffic. collision detection is the process by
which a node determines that a collision has occurred. Collisions occur with most networks,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORKING
so a protocol is required to recover from such events. Ethernet uses CSMA/CDas its collision
detection and recovery system.
Answer to question number 9
The correctness of a distributed algorithm is expressed through safety and liveness properties.
These properties can be defined as sets of histories (traces). More specifically, a safety
property is defined as a prefix-closed and limit-closed set of well-formed histories. Whereas,
a liveness property is defined as a set of histories that permits any finite well-formed history,
i.e., for every finite history there exists a continuation of that history in the liveness property.
Answer to question number 10
A three-way handshake is a method used in a TCP/IP network to create a connection between
a local host/client and server. It is a three-step method that requires both the client and server
to exchange SYN and ACK (acknowledgment) packets before actual data communication
begins.
Data link layer
Answer to question number 1
One of the issues which must be faced in any system is the problem of errors. We make an
assumption - which is often justified - that a digital bit pattern remains constant in time and
therefore information does not “decay away’. Error-checking is a device we use to confirm
our prejudices or alert us to a failure in the system. Virtually all forms of error checking
involve adding something to the digital pattern. This increases the number of possible
patterns (adding one bit to a pattern doubles the number of possibilities) If we then place
rules on valid patterns we can arrange things so that valid patterns do not become other valid
patterns through small errors. Parity is the simplest form of error checking. It adds one bit to
NETWORKING
so a protocol is required to recover from such events. Ethernet uses CSMA/CDas its collision
detection and recovery system.
Answer to question number 9
The correctness of a distributed algorithm is expressed through safety and liveness properties.
These properties can be defined as sets of histories (traces). More specifically, a safety
property is defined as a prefix-closed and limit-closed set of well-formed histories. Whereas,
a liveness property is defined as a set of histories that permits any finite well-formed history,
i.e., for every finite history there exists a continuation of that history in the liveness property.
Answer to question number 10
A three-way handshake is a method used in a TCP/IP network to create a connection between
a local host/client and server. It is a three-step method that requires both the client and server
to exchange SYN and ACK (acknowledgment) packets before actual data communication
begins.
Data link layer
Answer to question number 1
One of the issues which must be faced in any system is the problem of errors. We make an
assumption - which is often justified - that a digital bit pattern remains constant in time and
therefore information does not “decay away’. Error-checking is a device we use to confirm
our prejudices or alert us to a failure in the system. Virtually all forms of error checking
involve adding something to the digital pattern. This increases the number of possible
patterns (adding one bit to a pattern doubles the number of possibilities) If we then place
rules on valid patterns we can arrange things so that valid patterns do not become other valid
patterns through small errors. Parity is the simplest form of error checking. It adds one bit to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORKING
the pattern and then requires that the modulo-2 sum of all the bits of the pattern and the parity
bit have a defined answer. The answer is 0 for even parity and 1 for odd parity. An alternative
way of making the same statement is that odd(even) parity constrains there to be an
odd(even) number of “1"s in the pattern plus parity bit. A CRC check can catch all single,
and a large number of other, errors. It is not prone to the “bursting” problem above. It is used
extensively in disk systems, communication systems and other places where a check on a
pattern has to be maintained.
Answer to question number 2
Token passing. On a local area network, token passing is a channel access method where a
signal called a token is passed between nodes to authorize that node to communicate. ... Some
types of token passing schemes do not need to explicitly send a token between systems
because the process of "passing the token" is implicit.
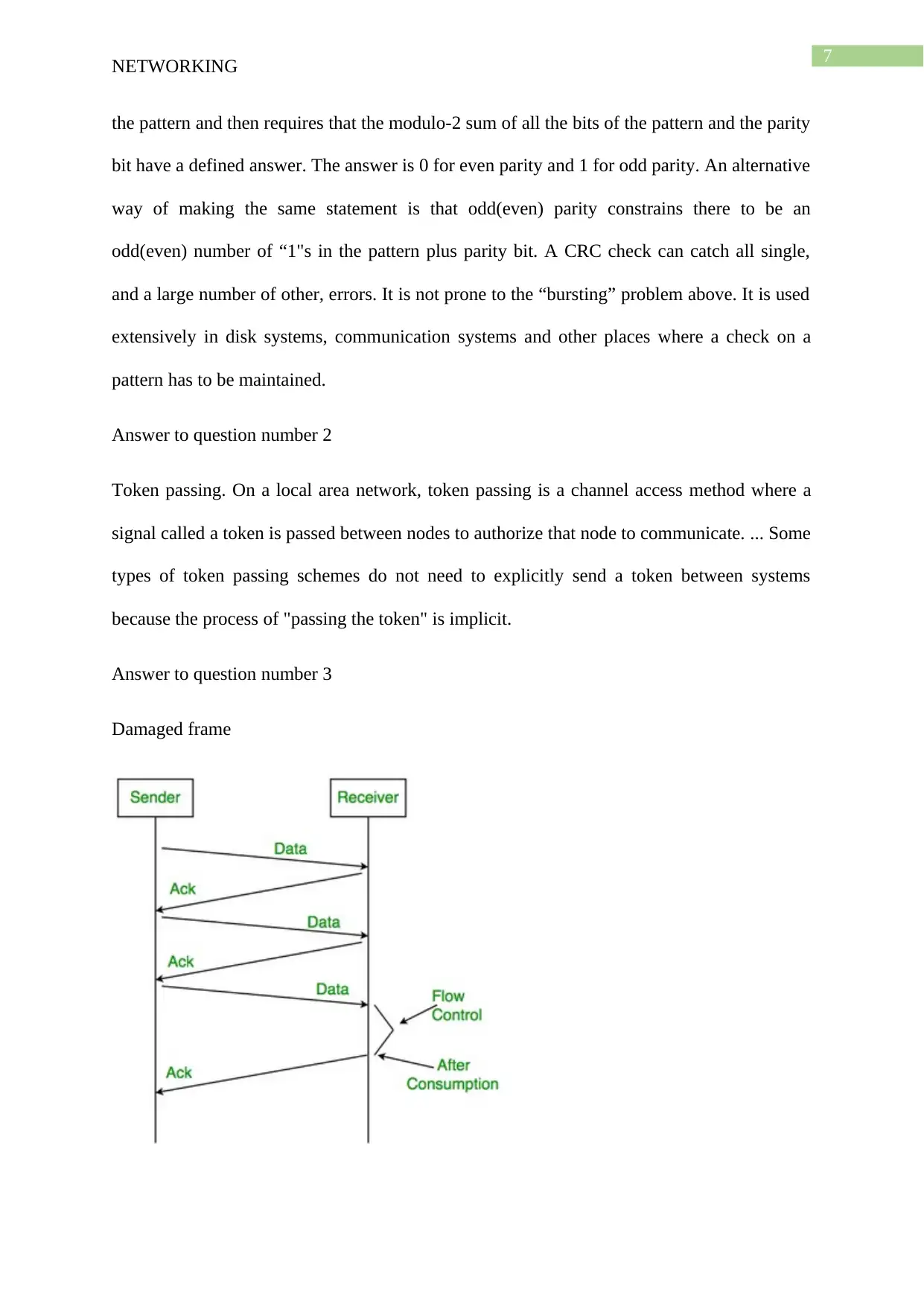
Answer to question number 3
Damaged frame
NETWORKING
the pattern and then requires that the modulo-2 sum of all the bits of the pattern and the parity
bit have a defined answer. The answer is 0 for even parity and 1 for odd parity. An alternative
way of making the same statement is that odd(even) parity constrains there to be an
odd(even) number of “1"s in the pattern plus parity bit. A CRC check can catch all single,
and a large number of other, errors. It is not prone to the “bursting” problem above. It is used
extensively in disk systems, communication systems and other places where a check on a
pattern has to be maintained.
Answer to question number 2
Token passing. On a local area network, token passing is a channel access method where a
signal called a token is passed between nodes to authorize that node to communicate. ... Some
types of token passing schemes do not need to explicitly send a token between systems
because the process of "passing the token" is implicit.
Answer to question number 3
Damaged frame
8
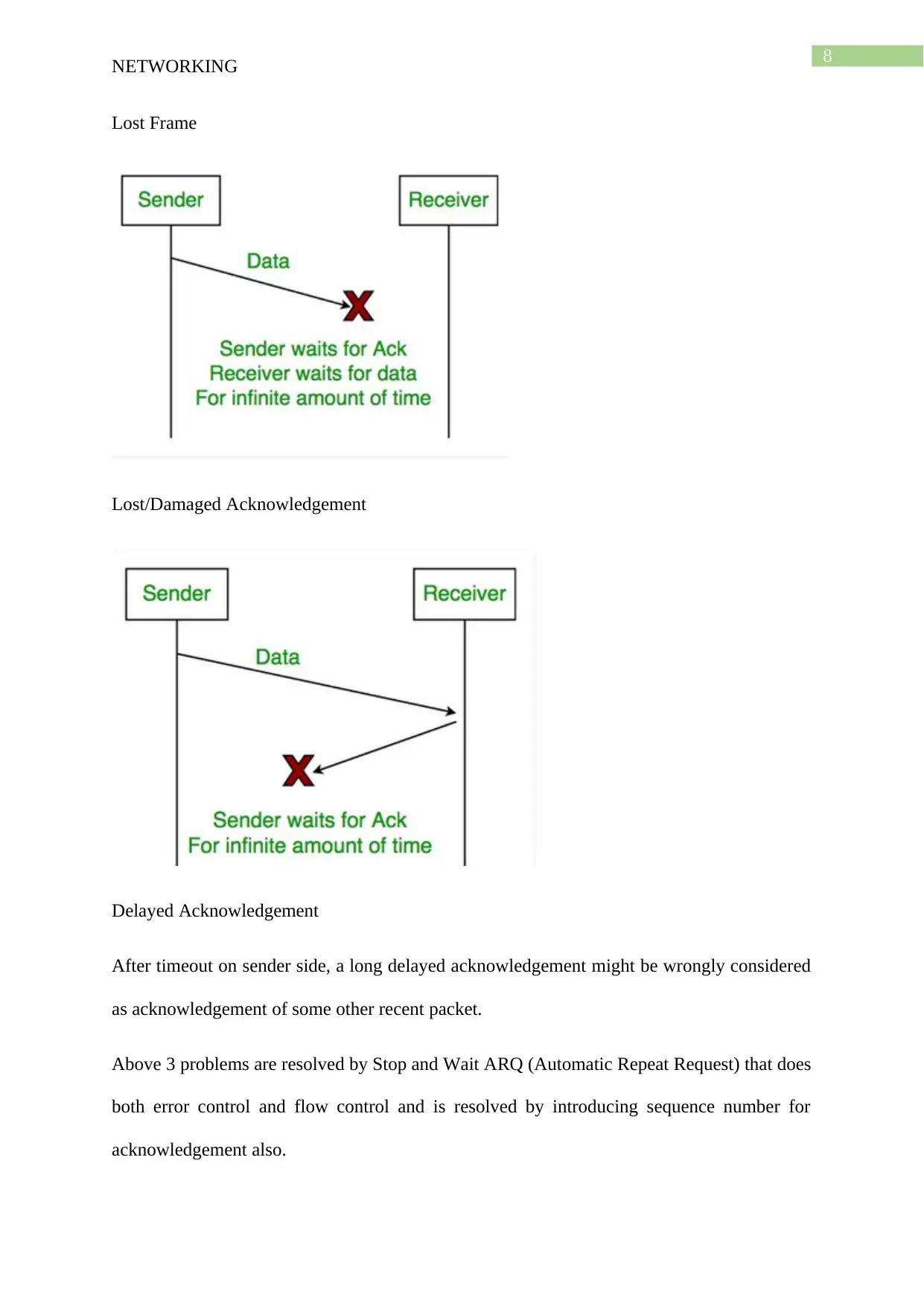
NETWORKING
Lost Frame
Lost/Damaged Acknowledgement
Delayed Acknowledgement
After timeout on sender side, a long delayed acknowledgement might be wrongly considered
as acknowledgement of some other recent packet.
Above 3 problems are resolved by Stop and Wait ARQ (Automatic Repeat Request) that does
both error control and flow control and is resolved by introducing sequence number for
acknowledgement also.
NETWORKING
Lost Frame
Lost/Damaged Acknowledgement
Delayed Acknowledgement
After timeout on sender side, a long delayed acknowledgement might be wrongly considered
as acknowledgement of some other recent packet.
Above 3 problems are resolved by Stop and Wait ARQ (Automatic Repeat Request) that does
both error control and flow control and is resolved by introducing sequence number for
acknowledgement also.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORKING
The Stop and Wait ARQ solves main three problems, but may cause big performance issues
as sender always waits for acknowledgement even if it has next packet ready to send.
Consider a situation where you have a high bandwidth connection and propagation delay is
also high (you are connected to some server in some other country though a high speed
connection). To solve this problem, we can send more than one packet at a time with a larger
sequence numbers. We will be discussing these protocols in next articles.
So Stop and Wait ARQ may work fine where propagation delay is very less for example
LAN connections, but performs badly for distant connections like satellite connection.
Answer to question number 4
If no acknowledgement is received after sending 6 frames, the sender takes the help of a timer.
After the time-out, it resumes retransmission. The go-Back-N protocol also takes care of
damaged frames and damaged ACKs.
Answer to question number 5
Synchronous timing occurs when a signal has a fixed relationship with a clock edge.
Synchronous timing ensures that data arrives at a digital tester at a known time relative to a
clock edge. Interfaces are said to be "source synchronous" if the data is transmitted or
received along with the clock.
Answer to question number 6
Due to various topologies used across the networks, the Maximum transmission unit differs.
Framing does the job for it. A frame is also used to wrap the payload with additional
information such as addressing information and checksum. Data link layer also delineates the
frames, commonly termed as Frame synchronization. Framing or the addition of L2 header is
done to send the packet from one node to another in same network, cause each node is
NETWORKING
The Stop and Wait ARQ solves main three problems, but may cause big performance issues
as sender always waits for acknowledgement even if it has next packet ready to send.
Consider a situation where you have a high bandwidth connection and propagation delay is
also high (you are connected to some server in some other country though a high speed
connection). To solve this problem, we can send more than one packet at a time with a larger
sequence numbers. We will be discussing these protocols in next articles.
So Stop and Wait ARQ may work fine where propagation delay is very less for example
LAN connections, but performs badly for distant connections like satellite connection.
Answer to question number 4
If no acknowledgement is received after sending 6 frames, the sender takes the help of a timer.
After the time-out, it resumes retransmission. The go-Back-N protocol also takes care of
damaged frames and damaged ACKs.
Answer to question number 5
Synchronous timing occurs when a signal has a fixed relationship with a clock edge.
Synchronous timing ensures that data arrives at a digital tester at a known time relative to a
clock edge. Interfaces are said to be "source synchronous" if the data is transmitted or
received along with the clock.
Answer to question number 6
Due to various topologies used across the networks, the Maximum transmission unit differs.
Framing does the job for it. A frame is also used to wrap the payload with additional
information such as addressing information and checksum. Data link layer also delineates the
frames, commonly termed as Frame synchronization. Framing or the addition of L2 header is
done to send the packet from one node to another in same network, cause each node is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORKING
identified using a unique mac address in a broadcast domain. There are also some services
that Data link layer provides like flow control, error detection and correction, frame
synchronisation (to mark the end of one frame ) for that mac trailer is added . The final
framing method is physical layer coding violations and is applicable to networks in which the
encoding on the physical medium contains some redundancy. In such cases normally, a 1 bit
is a high-low pair and a 0 bit is a low-high pair. The combinations of low-low and high-high
which are not used for data may be used for marking frame boundaries.
Answer to question number 7
Controlled access-one node consult with the other node for sending data packets.so, there is
no collision. three types-reservation, polling, token passing. contention based access-node
send the packet without consulting with the other node.so, there is a chance of collision. four
types-aloha, csma, csma/cd, csma/ca. Hence, the former is distributed and the latter is
centralized.
Answer to question number 8
The various codes are used for the error detection and correction in the field of
communication. Some are for the single bit error and some are for the multiple bits error.
Reed-Muller algorithm realizes the ability of multiple bits error detection and correction.
With the superior error correction capability, these codes have initiated wide scale interests in
satellite communication, wireless communication, and storage fields. Reed-Muller codes
cover a wide range of service requirements and diverse interference conditions in wireless
applications and can operate at both high and low code rates. In this paper, the comparison of
Reed-Muller codes with different other codes for error detection and correction of multiple
bits is proposed and further we can implement it on a Xilinx field programmable gate array
(FPGA) device. Using Reed-Muller method the data is transferred from transmitter to
NETWORKING
identified using a unique mac address in a broadcast domain. There are also some services
that Data link layer provides like flow control, error detection and correction, frame
synchronisation (to mark the end of one frame ) for that mac trailer is added . The final
framing method is physical layer coding violations and is applicable to networks in which the
encoding on the physical medium contains some redundancy. In such cases normally, a 1 bit
is a high-low pair and a 0 bit is a low-high pair. The combinations of low-low and high-high
which are not used for data may be used for marking frame boundaries.
Answer to question number 7
Controlled access-one node consult with the other node for sending data packets.so, there is
no collision. three types-reservation, polling, token passing. contention based access-node
send the packet without consulting with the other node.so, there is a chance of collision. four
types-aloha, csma, csma/cd, csma/ca. Hence, the former is distributed and the latter is
centralized.
Answer to question number 8
The various codes are used for the error detection and correction in the field of
communication. Some are for the single bit error and some are for the multiple bits error.
Reed-Muller algorithm realizes the ability of multiple bits error detection and correction.
With the superior error correction capability, these codes have initiated wide scale interests in
satellite communication, wireless communication, and storage fields. Reed-Muller codes
cover a wide range of service requirements and diverse interference conditions in wireless
applications and can operate at both high and low code rates. In this paper, the comparison of
Reed-Muller codes with different other codes for error detection and correction of multiple
bits is proposed and further we can implement it on a Xilinx field programmable gate array
(FPGA) device. Using Reed-Muller method the data is transferred from transmitter to

11
NETWORKING
receiver without any error. The error detection and correction principle and realization
methods are described in detail. The multiple bits error detection and correction with Reed-
Muller algorithm method can improve the bit error rate and packet error rate effectively.
Physical Layer
Answer to question number 1
Modulation allows us to send a signal over a bandpass frequency range. If every signal gets
its own frequency range, then we can transmit multiple signals simultaneously over a single
channel, all using different frequency ranges. Another reason to modulate a signal is to allow
the use of a smaller antenna.
Answer to question number 2
Attenuation is a general term that refers to any reduction in the strength of a signal.
Attenuation occurs with any type of signal, whether digital or analog. Sometimes called loss,
attenuation is a natural consequence of signal transmission over long distances. Although
attenuation is significantly lower for optical fiber than for other media, it still occurs in both
multimode and single-mode transmission. An efficient optical data link must have enough
light available to overcome attenuation.
Answer to question number 3
This corresponds to a transfer rate of about 960 bytes per second.
Answer to question number 4
an amplifier amplifies everything to increase signal level, inlcuding noise received before and
after the last link, and adds it own noise. Using a large number of amplifiers over a long,
lossy link inevitably increases the noise and decreases the signal to noise levels. A repeater is
NETWORKING
receiver without any error. The error detection and correction principle and realization
methods are described in detail. The multiple bits error detection and correction with Reed-
Muller algorithm method can improve the bit error rate and packet error rate effectively.
Physical Layer
Answer to question number 1
Modulation allows us to send a signal over a bandpass frequency range. If every signal gets
its own frequency range, then we can transmit multiple signals simultaneously over a single
channel, all using different frequency ranges. Another reason to modulate a signal is to allow
the use of a smaller antenna.
Answer to question number 2
Attenuation is a general term that refers to any reduction in the strength of a signal.
Attenuation occurs with any type of signal, whether digital or analog. Sometimes called loss,
attenuation is a natural consequence of signal transmission over long distances. Although
attenuation is significantly lower for optical fiber than for other media, it still occurs in both
multimode and single-mode transmission. An efficient optical data link must have enough
light available to overcome attenuation.
Answer to question number 3
This corresponds to a transfer rate of about 960 bytes per second.
Answer to question number 4
an amplifier amplifies everything to increase signal level, inlcuding noise received before and
after the last link, and adds it own noise. Using a large number of amplifiers over a long,
lossy link inevitably increases the noise and decreases the signal to noise levels. A repeater is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 33
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




