Detailed IT Infrastructure Project Report for Wetspec Company
VerifiedAdded on 2020/11/23
|16
|3234
|210
Report
AI Summary
This report details the IT infrastructure project for Wetspec, a financial services company, focusing on the networking design for a new branch. It explores the geographical scope using a Campus Area Network (CAN) to interconnect computers across eight floors, each with 30 systems. The report examines the logical design, employing a three-layered architecture (Core, Distributed, and Access layers). It defines IP addresses and subnet masks, including examples of IP ranges and subnet masks. Furthermore, the report analyzes cloud providers, specifically AWS and Adobe, detailing their services such as compute storage, data management, and mobile development. The report also discusses virtualization and cloud computing techniques, including network and storage virtualization, and how they enhance flexibility and control. The document covers dynamic scaling and concludes with references.

It infrastructure
project
project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
MAIN BODY ..................................................................................................................................1
Geographical Scope....................................................................................................................1
Logical Design.............................................................................................................................3
IP Address and Subnet mask........................................................................................................4
Cloud provider.............................................................................................................................5
Techniques supporting the virtualisation and cloud computing..................................................7
Dynamic scaling...........................................................................................................................9
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10
INTRODUCTION...........................................................................................................................1
MAIN BODY ..................................................................................................................................1
Geographical Scope....................................................................................................................1
Logical Design.............................................................................................................................3
IP Address and Subnet mask........................................................................................................4
Cloud provider.............................................................................................................................5
Techniques supporting the virtualisation and cloud computing..................................................7
Dynamic scaling...........................................................................................................................9
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10

INTRODUCTION
IT infrastructure within the organization is referred as the combination of the hardware,
software and network and human resource that allow an organization to deliver the informational
technology services to people within an organization. This report is based on the networking
design of the Wetspec company which deals with financial services to the customer. This report
will explore the networking design made for the new branch of the organization. Also, it will
help in determining the IP addresses and subnet mask which helps in configuration of the
networking system developed within Wetspec.
Moreover, the present study will also help in understanding the complete knowledge
about the cloud provider company which enhance the data storage, data manipulation and output
storage for customers. It will also create a proper understanding about the development of the
dynamic scaling which supports the data security along with wider storage space.
MAIN BODY
Geographical Scope
A computer network refers to various hardware and software devices that are
interconnected for the sharing and communication purpose. So in order to establish a
geographical scope of network within new branch of Wetspec company, CAN is going to be
established for developing the network of interconnected networks. Within the organization
(Benitez, Ray and Henseler, 2018). Campus area network allows the interconnected computers
of the Sydney branch in which IT manager wants to develop a network interface between 8
floors and each floor consists of 30 computer systems. This allow the interconnection of various
LAN's together in order to establish a powerful networking infrastructure for the company.
The Type of Geographical design used in Wetspec Sydney
1
IT infrastructure within the organization is referred as the combination of the hardware,
software and network and human resource that allow an organization to deliver the informational
technology services to people within an organization. This report is based on the networking
design of the Wetspec company which deals with financial services to the customer. This report
will explore the networking design made for the new branch of the organization. Also, it will
help in determining the IP addresses and subnet mask which helps in configuration of the
networking system developed within Wetspec.
Moreover, the present study will also help in understanding the complete knowledge
about the cloud provider company which enhance the data storage, data manipulation and output
storage for customers. It will also create a proper understanding about the development of the
dynamic scaling which supports the data security along with wider storage space.
MAIN BODY
Geographical Scope
A computer network refers to various hardware and software devices that are
interconnected for the sharing and communication purpose. So in order to establish a
geographical scope of network within new branch of Wetspec company, CAN is going to be
established for developing the network of interconnected networks. Within the organization
(Benitez, Ray and Henseler, 2018). Campus area network allows the interconnected computers
of the Sydney branch in which IT manager wants to develop a network interface between 8
floors and each floor consists of 30 computer systems. This allow the interconnection of various
LAN's together in order to establish a powerful networking infrastructure for the company.
The Type of Geographical design used in Wetspec Sydney
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
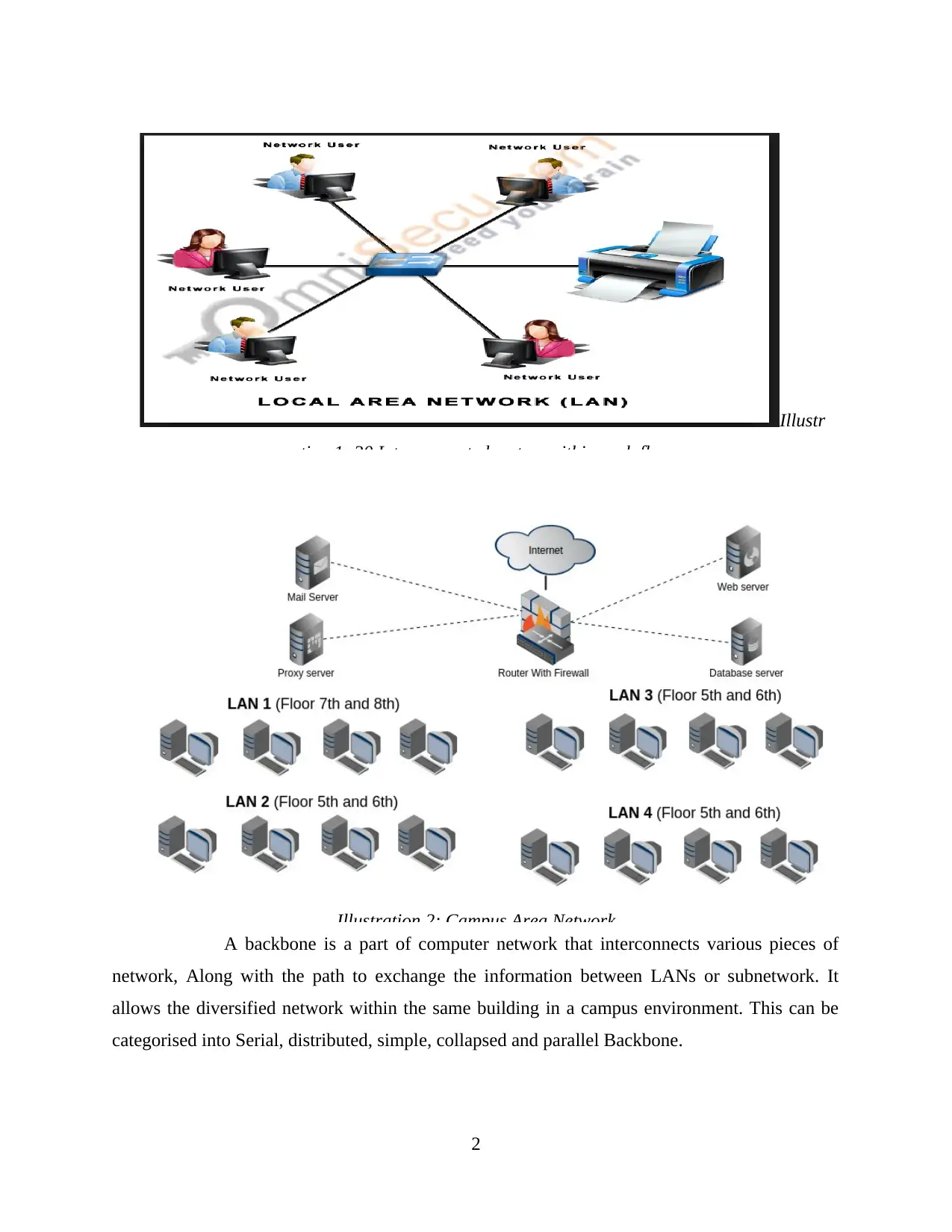
A backbone is a part of computer network that interconnects various pieces of
network, Along with the path to exchange the information between LANs or subnetwork. It
allows the diversified network within the same building in a campus environment. This can be
categorised into Serial, distributed, simple, collapsed and parallel Backbone.
2
Illustr
ation 1: 30 Interconnected system within each floor
Illustration 2: Campus Area Network
network, Along with the path to exchange the information between LANs or subnetwork. It
allows the diversified network within the same building in a campus environment. This can be
categorised into Serial, distributed, simple, collapsed and parallel Backbone.
2
Illustr
ation 1: 30 Interconnected system within each floor
Illustration 2: Campus Area Network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
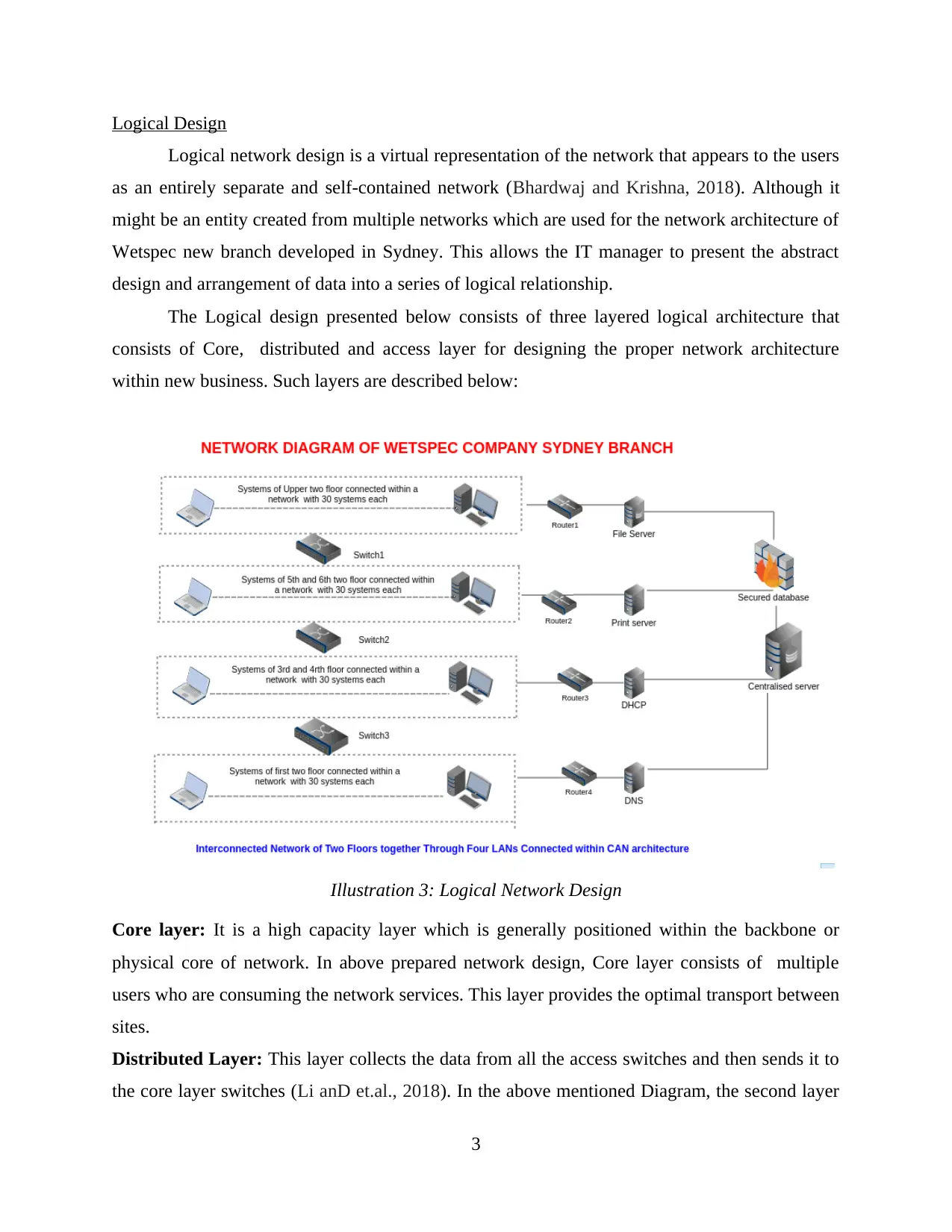
Logical Design
Logical network design is a virtual representation of the network that appears to the users
as an entirely separate and self-contained network (Bhardwaj and Krishna, 2018). Although it
might be an entity created from multiple networks which are used for the network architecture of
Wetspec new branch developed in Sydney. This allows the IT manager to present the abstract
design and arrangement of data into a series of logical relationship.
The Logical design presented below consists of three layered logical architecture that
consists of Core, distributed and access layer for designing the proper network architecture
within new business. Such layers are described below:
Core layer: It is a high capacity layer which is generally positioned within the backbone or
physical core of network. In above prepared network design, Core layer consists of multiple
users who are consuming the network services. This layer provides the optimal transport between
sites.
Distributed Layer: This layer collects the data from all the access switches and then sends it to
the core layer switches (Li anD et.al., 2018). In the above mentioned Diagram, the second layer
3
Illustration 3: Logical Network Design
Logical network design is a virtual representation of the network that appears to the users
as an entirely separate and self-contained network (Bhardwaj and Krishna, 2018). Although it
might be an entity created from multiple networks which are used for the network architecture of
Wetspec new branch developed in Sydney. This allows the IT manager to present the abstract
design and arrangement of data into a series of logical relationship.
The Logical design presented below consists of three layered logical architecture that
consists of Core, distributed and access layer for designing the proper network architecture
within new business. Such layers are described below:
Core layer: It is a high capacity layer which is generally positioned within the backbone or
physical core of network. In above prepared network design, Core layer consists of multiple
users who are consuming the network services. This layer provides the optimal transport between
sites.
Distributed Layer: This layer collects the data from all the access switches and then sends it to
the core layer switches (Li anD et.al., 2018). In the above mentioned Diagram, the second layer
3
Illustration 3: Logical Network Design
consists of four data servers which are placed between two interconnected computers of two
floor each. This layer connects the network services to access layer.
Access layer: It is the lowest level in network architecture which mainly consists of routers at
the edge of the campus networks. This ensures the proper delivery of the data packets to end
users as it mainly focuses on connecting client nodes of network.
IP Address and Subnet mask
It is defined as a unique string of numbers separated by fullstops that identifies each
system using the internet protocol to communicate over a network. A subnet mask is a 32- or 128
bit number that segments an existing IP Address In a TCP/IP network divides the addresses into
discrete network and host addresses (Rodriguez and Buyya, 2018). Subnetting allows the user to
further divide the IP address of host into subnets in order to route the traffic within larger
subnet. It is a logical partition of an IP network into multiple smaller network.
IP address and its subnet masking of network which is established in Sydney Wetspec is
as follows:
IP address : 191.168.1.2 …........ 192.1668.1.32
Subnet mask: 255.255.255.0
Default gateway: 192.168.1.1
Address class Number of
network bits
Number of Host
bits
Subnet mask CIDR Notation
C 24 8 255.255.255.0 /24
C 25 7 255.255.255.240 /25
C 28 4 255.255.255.240 /28
C 30 2 255.255.255.252 /30
Cloud provider
Cloud provider (CSP) is basically a company which delivers the cloud computing based
services and solutions to business and individuals (Talia, 2019). This service organization may
provide rented and provide managed virtual hardware, software, infrastructure and other related
service. Customers generally purchase a variety of services from cloud service provider. It offers
various cloud services such as Iaas (Infrastructure-as-a-service), Paas (Software-as-a-service),
4
floor each. This layer connects the network services to access layer.
Access layer: It is the lowest level in network architecture which mainly consists of routers at
the edge of the campus networks. This ensures the proper delivery of the data packets to end
users as it mainly focuses on connecting client nodes of network.
IP Address and Subnet mask
It is defined as a unique string of numbers separated by fullstops that identifies each
system using the internet protocol to communicate over a network. A subnet mask is a 32- or 128
bit number that segments an existing IP Address In a TCP/IP network divides the addresses into
discrete network and host addresses (Rodriguez and Buyya, 2018). Subnetting allows the user to
further divide the IP address of host into subnets in order to route the traffic within larger
subnet. It is a logical partition of an IP network into multiple smaller network.
IP address and its subnet masking of network which is established in Sydney Wetspec is
as follows:
IP address : 191.168.1.2 …........ 192.1668.1.32
Subnet mask: 255.255.255.0
Default gateway: 192.168.1.1
Address class Number of
network bits
Number of Host
bits
Subnet mask CIDR Notation
C 24 8 255.255.255.0 /24
C 25 7 255.255.255.240 /25
C 28 4 255.255.255.240 /28
C 30 2 255.255.255.252 /30
Cloud provider
Cloud provider (CSP) is basically a company which delivers the cloud computing based
services and solutions to business and individuals (Talia, 2019). This service organization may
provide rented and provide managed virtual hardware, software, infrastructure and other related
service. Customers generally purchase a variety of services from cloud service provider. It offers
various cloud services such as Iaas (Infrastructure-as-a-service), Paas (Software-as-a-service),
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Saas (Software-as-a-service). AWS (Amazon Web services) and Adobe are the two
organizations which provides the cloud services and hosts the email and web server. The services
provided by each company is described below:
AWS
Amazon Web service is a comprehensive and evolving cloud computing platforms which
are provided by Amazon. It offers the mix services which includes Iaas, Paas and Saas as a
package cloud service. This organization has established as a t op contender in cloud computing
market. It was one of the first company which has introduced Pay-as-you-go cloud computing
model which offers large variety of services such as storage, computing operations and output
according to the needs of the user. AWS also provides the large number of data centres which are
typically present in various regions across the world (Varghese and Buyya, 2018). It allows the
customers to use the virtual machines and provides replicated data in different regions in order to
achieve highly reliable infrastructure which resists the failure of individual or entire data centre.
AWS offers more then 100 services which includes database storage, Infrastructure management,
development of application and data security.
Compute storage: Amazon Elastic Compute cloud (EC2) provides the virtual server for
computing capacity and various instances. AWS also provides an Auto scaling tool to
dynamically scale capacity and performance. The Amazon E2C container service enable the
users to work with Docker containers and AWS platform and it alos provides the AWS Lambda
functions for applications and services.
Data management: It provides Managed database services through its Amazon relational
database service (Wang, Jie and Chen, 2018). For maintaining the database, Amazon has also
offered various query based servers such as Oracle, SQL server, MySQL.
Migration, hybrid cloud: AWS also includes the different services and tools in order to migrate
the applications, database servers on public cloud. There is a hub provided which ensures the
management of migration from on premises to cloud.
Networking: An Amazon Virtual private cloud (VPN) gives the administration that offers the
virtual network as a isolated network for the AWS cloud.
application services: AWS command line tools and software development kit help in deploying
and managing the cloud services and applications within the organization. It alos provides the
5
organizations which provides the cloud services and hosts the email and web server. The services
provided by each company is described below:
AWS
Amazon Web service is a comprehensive and evolving cloud computing platforms which
are provided by Amazon. It offers the mix services which includes Iaas, Paas and Saas as a
package cloud service. This organization has established as a t op contender in cloud computing
market. It was one of the first company which has introduced Pay-as-you-go cloud computing
model which offers large variety of services such as storage, computing operations and output
according to the needs of the user. AWS also provides the large number of data centres which are
typically present in various regions across the world (Varghese and Buyya, 2018). It allows the
customers to use the virtual machines and provides replicated data in different regions in order to
achieve highly reliable infrastructure which resists the failure of individual or entire data centre.
AWS offers more then 100 services which includes database storage, Infrastructure management,
development of application and data security.
Compute storage: Amazon Elastic Compute cloud (EC2) provides the virtual server for
computing capacity and various instances. AWS also provides an Auto scaling tool to
dynamically scale capacity and performance. The Amazon E2C container service enable the
users to work with Docker containers and AWS platform and it alos provides the AWS Lambda
functions for applications and services.
Data management: It provides Managed database services through its Amazon relational
database service (Wang, Jie and Chen, 2018). For maintaining the database, Amazon has also
offered various query based servers such as Oracle, SQL server, MySQL.
Migration, hybrid cloud: AWS also includes the different services and tools in order to migrate
the applications, database servers on public cloud. There is a hub provided which ensures the
management of migration from on premises to cloud.
Networking: An Amazon Virtual private cloud (VPN) gives the administration that offers the
virtual network as a isolated network for the AWS cloud.
application services: AWS command line tools and software development kit help in deploying
and managing the cloud services and applications within the organization. It alos provides the
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

API gateway which enables the developers in deploying, managing and monitoring the
customised Application program interface for users.
Management and monitoring: Cloud resources and configurations are tracked via AWS
configuration. It also provides several automation tools that enables the automatic configuration
of the system.
Security management: AWS provides the range of cloud security in order to identify and varify
the client authentication. It prevents the information of the organization from DDOS attacks,
which is kept safe by the cloud provider
Big data analytics: AWS also provides the variety of Big data analytics and applications which
offers the Hadoop framework in order to manage and process large amount of data.
Mobile development: The AWS mobile hub offers variety of tools and applications for
application development in the mobile (Zamora-Izquierdo And et.al., 2019). It also offers the
range of AI model development which enables the user in providing the feature such as Amazon
polly for text-to-speech translation.
Adobe
Abode creative cloud is a set of applications and services from Abode systems which
allows the subscribers to use the wide variety of services such as graphics, design, video editing,
web development, photography etc. Adobe provides the set of mobile applications and also some
optional cloud services. It allows the users to enjoy the monthly subscription over internet. It
provides the variety of software which allows the users to use the four tier creative cloud
subscription. Adobe Acrobat is a software family which is dedicated to adobe's software family
dedicated to Adobe's portable document. This allows the creation of PDF files and Adobe reader
is the application which allows the reading of PDF files. Adobe has also adopted the shifting to
Software as a service model which offers more frequent updates to its features. Although,
Creative cloud was also expected to curtail the privacy of the Photoshop which is a pirated piece
of software. However, it was once hacked and its applications were made available through the
unauthorised means which allows the company to introduce the subscription payment plan that
avails the accessibility to users who has earlier pirated it (Network design for building, 2018).
Furthermore, A creative cloud provides has the design tool which ensures the customers
about bringing the ideas to life via applications for image composition, website design, photo
editing, Digital and 3D paintings. It also allows the customers in creating the logos, posters,
6
customised Application program interface for users.
Management and monitoring: Cloud resources and configurations are tracked via AWS
configuration. It also provides several automation tools that enables the automatic configuration
of the system.
Security management: AWS provides the range of cloud security in order to identify and varify
the client authentication. It prevents the information of the organization from DDOS attacks,
which is kept safe by the cloud provider
Big data analytics: AWS also provides the variety of Big data analytics and applications which
offers the Hadoop framework in order to manage and process large amount of data.
Mobile development: The AWS mobile hub offers variety of tools and applications for
application development in the mobile (Zamora-Izquierdo And et.al., 2019). It also offers the
range of AI model development which enables the user in providing the feature such as Amazon
polly for text-to-speech translation.
Adobe
Abode creative cloud is a set of applications and services from Abode systems which
allows the subscribers to use the wide variety of services such as graphics, design, video editing,
web development, photography etc. Adobe provides the set of mobile applications and also some
optional cloud services. It allows the users to enjoy the monthly subscription over internet. It
provides the variety of software which allows the users to use the four tier creative cloud
subscription. Adobe Acrobat is a software family which is dedicated to adobe's software family
dedicated to Adobe's portable document. This allows the creation of PDF files and Adobe reader
is the application which allows the reading of PDF files. Adobe has also adopted the shifting to
Software as a service model which offers more frequent updates to its features. Although,
Creative cloud was also expected to curtail the privacy of the Photoshop which is a pirated piece
of software. However, it was once hacked and its applications were made available through the
unauthorised means which allows the company to introduce the subscription payment plan that
avails the accessibility to users who has earlier pirated it (Network design for building, 2018).
Furthermore, A creative cloud provides has the design tool which ensures the customers
about bringing the ideas to life via applications for image composition, website design, photo
editing, Digital and 3D paintings. It also allows the customers in creating the logos, posters,
6

advertisements, packaging etc. This type of cloud provider mainly concentrates towards
providing the cloud based storage to the customers which offers variety of services related to
Adobe Acrobat, Photoshop and PDF files.
Techniques supporting the virtualisation and cloud computing
A technology is called the Virtual machine Monitor which is controlled by the virtual
manager. Virtualisation is the creation of Virtual servers, infrastructure, devices and computing
resources. This technology allows the the user to run multiple Operating system on one hardware
which provides the vital part in testing and cloud based computing. Virtualisation changes
relation of the hardware and software which ensures the use of cloud computing technology that
Network virtualisation. Although cloud computing is a service which has been produced from
the change. It offers the delivery of shared computing resources. It provides the SaaS and on-
demand services through the internet. Most of time cloud computing and virtualisation work
together in order to provide different types of services. The cloud often uses the virtualisation as
a part of services package. This technology is referred as a Virtual machine monitor which
encapsulates very basic of virtualisation in cloud computing. It often includes the CPU's memory
, input output and network device to interact with other hardware and software devices.
Virtualisation along with the cloud computing allows the greater flexibility, control and isolation
by eliminating the dependency on the hardware platform. Here is a abstraction layer present
which is called as “Hypervisor”. There are various different types of techniques which are
involved in Virtualisation and cloud computing such are as follows:
Network virtualisation
Network virtualisation in cloud computing is defined as a met hod of combining the
available resources within a network by splitting the available bandwidth into different channels.
This idea allows the technology in minimising the complexity and isolating the network into
different parts which are easy to manage. This ensures the proper management of files.
Storage virtualisation
This technique provides the ability to pool the hardware storage space from several
interconnected storage device into simulated single storage which can be managed from one
single command console (Xiao and et.al., 2018). This technique is often used in storage area
networks which allows the manipulation of the data into the cloud. This can be entertained
within the organization by employing hardware and software appliance. Storage Virtualisation
7
providing the cloud based storage to the customers which offers variety of services related to
Adobe Acrobat, Photoshop and PDF files.
Techniques supporting the virtualisation and cloud computing
A technology is called the Virtual machine Monitor which is controlled by the virtual
manager. Virtualisation is the creation of Virtual servers, infrastructure, devices and computing
resources. This technology allows the the user to run multiple Operating system on one hardware
which provides the vital part in testing and cloud based computing. Virtualisation changes
relation of the hardware and software which ensures the use of cloud computing technology that
Network virtualisation. Although cloud computing is a service which has been produced from
the change. It offers the delivery of shared computing resources. It provides the SaaS and on-
demand services through the internet. Most of time cloud computing and virtualisation work
together in order to provide different types of services. The cloud often uses the virtualisation as
a part of services package. This technology is referred as a Virtual machine monitor which
encapsulates very basic of virtualisation in cloud computing. It often includes the CPU's memory
, input output and network device to interact with other hardware and software devices.
Virtualisation along with the cloud computing allows the greater flexibility, control and isolation
by eliminating the dependency on the hardware platform. Here is a abstraction layer present
which is called as “Hypervisor”. There are various different types of techniques which are
involved in Virtualisation and cloud computing such are as follows:
Network virtualisation
Network virtualisation in cloud computing is defined as a met hod of combining the
available resources within a network by splitting the available bandwidth into different channels.
This idea allows the technology in minimising the complexity and isolating the network into
different parts which are easy to manage. This ensures the proper management of files.
Storage virtualisation
This technique provides the ability to pool the hardware storage space from several
interconnected storage device into simulated single storage which can be managed from one
single command console (Xiao and et.al., 2018). This technique is often used in storage area
networks which allows the manipulation of the data into the cloud. This can be entertained
within the organization by employing hardware and software appliance. Storage Virtualisation
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

technique is often used for backup, archiving and recovering of the data by abstraction of the real
and physical complex storage architecture.
Server Virtualisation
This technique helps in masking of the server resources. It also simulates the physical
server by changing the Identity, number, processor and OS. It also helps in expanding the server
response capacity according to the requirements of the user. It also allows the user in managing t
he complex resources of the server and also avails the resources for sharing and utilising
purpose.
Data Virtualisation
This technique helps in providing the abstracted view to the users. The technical details
which are used in management of the large amount of data within the enterprise such as format,
location, performance are kept hidden from the naïve users.
Desktop
This technique allows the Operating system to be remotely stored on a server in the data
centre. It allows the user to access their desktop virtually from any location through different
machines. This technique also allow the users in user mobility, potability and easy management
of software installation, updates and patches.
Application
This virtualisation technique allow user to have remote access of an application from a
server. This server helps in storing the personal information and other characteristics of
application. This technique allows the users to run the application on a local workstation via
internet. Those companies which uses the application virtualisation are the form of hosted
application and packaged applications.
Dynamic scaling
Dynamic scaling can be considered as the litmus test of showing that an evolving system
exhibits self-similarity Cloud computing provides a powerful computing model that allows the
user to access the resources on-demand. A dynamic scaling is referred as a algorithm for
the automated provisioning of the virtual machine resources. Cloud computing has emerged as a
platform upon which innovation, flexibility, innovation and availability which supports efficient
operations in small and medium organizations (Yaibuates and Chaisricharoen, 2018). However,
dynamic scaling ensures the automation which meets the unexpected demand and also the
8
and physical complex storage architecture.
Server Virtualisation
This technique helps in masking of the server resources. It also simulates the physical
server by changing the Identity, number, processor and OS. It also helps in expanding the server
response capacity according to the requirements of the user. It also allows the user in managing t
he complex resources of the server and also avails the resources for sharing and utilising
purpose.
Data Virtualisation
This technique helps in providing the abstracted view to the users. The technical details
which are used in management of the large amount of data within the enterprise such as format,
location, performance are kept hidden from the naïve users.
Desktop
This technique allows the Operating system to be remotely stored on a server in the data
centre. It allows the user to access their desktop virtually from any location through different
machines. This technique also allow the users in user mobility, potability and easy management
of software installation, updates and patches.
Application
This virtualisation technique allow user to have remote access of an application from a
server. This server helps in storing the personal information and other characteristics of
application. This technique allows the users to run the application on a local workstation via
internet. Those companies which uses the application virtualisation are the form of hosted
application and packaged applications.
Dynamic scaling
Dynamic scaling can be considered as the litmus test of showing that an evolving system
exhibits self-similarity Cloud computing provides a powerful computing model that allows the
user to access the resources on-demand. A dynamic scaling is referred as a algorithm for
the automated provisioning of the virtual machine resources. Cloud computing has emerged as a
platform upon which innovation, flexibility, innovation and availability which supports efficient
operations in small and medium organizations (Yaibuates and Chaisricharoen, 2018). However,
dynamic scaling ensures the automation which meets the unexpected demand and also the
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

resources are scaled up to meet up the unexpected demand. Although these resources are scaled
down to meet the decreased demand of the resources. AWS allows the organization to add or
subtract the resources to the applications in order to meet the demand of the customer while
managing the cost.
In addition to this, dynamic scaling solution could be deployed by Wetspec Sydney
branch in order to build the infrastructure on cloud platform. According to the change in the
traffic, Dynamic scaling easily scale up and down their cloud infrastructure. It allows the Sydney
branch of the Wetspec to focus on the other important functions of the business and they do not
have to worry about the service availability. As dynamic scaled infrastructure ensure the service
availability during high demand.
CONCLUSION
From the above study it can be concluded that, designing a IT structure within the
organization requires large number of data and resources along with the network configurations.
This study has also produced the logical design of the Sydney branch which is based on three
layered hierarchical modal. Moreover, it has also helped the organization in identifying the IP
addresses and subnet mask that can be used for the easy accessibility of client and server within
the Sydney branch of Wetspec. It has also helped the readers in making a clear understanding
about virtualisation and cloud computing techniques which allows the storage for storing large
number of data and information. Also it has explored the concept about dynamic scaling which is
supported by cloud computing.
9
down to meet the decreased demand of the resources. AWS allows the organization to add or
subtract the resources to the applications in order to meet the demand of the customer while
managing the cost.
In addition to this, dynamic scaling solution could be deployed by Wetspec Sydney
branch in order to build the infrastructure on cloud platform. According to the change in the
traffic, Dynamic scaling easily scale up and down their cloud infrastructure. It allows the Sydney
branch of the Wetspec to focus on the other important functions of the business and they do not
have to worry about the service availability. As dynamic scaled infrastructure ensure the service
availability during high demand.
CONCLUSION
From the above study it can be concluded that, designing a IT structure within the
organization requires large number of data and resources along with the network configurations.
This study has also produced the logical design of the Sydney branch which is based on three
layered hierarchical modal. Moreover, it has also helped the organization in identifying the IP
addresses and subnet mask that can be used for the easy accessibility of client and server within
the Sydney branch of Wetspec. It has also helped the readers in making a clear understanding
about virtualisation and cloud computing techniques which allows the storage for storing large
number of data and information. Also it has explored the concept about dynamic scaling which is
supported by cloud computing.
9

REFERENCES
Books and Journals
Benitez, J., Ray, G. and Henseler, J., 2018. Impact of information technology infrastructure
flexibility on mergers and acquisitions. MIS Quarterly. 42(1). pp.25-43.
Bhardwaj, A. and Krishna, C.R., 2018. Performance evaluation of bandwidth for virtual
machine migration in cloud computing. International Journal of Knowledge Engineering
and Data Mining. 5(3). pp.139-152.
Li, R. anD et.al., 2018, June. Research of Subnetting Based on Huffman Coding.
In International Conference on Cloud Computing and Security (pp. 606-616). Springer,
Cham.
Rodriguez, M.A. and Buyya, R., 2018. Scheduling dynamic workloads in multi-tenant scientific
workflow as a service platforms. Future Generation Computer Systems, 79, pp.739-750.
Talia, D., 2019. A view of programming scalable data analysis: from clouds to
exascale. Journal of Cloud Computing. 8(1). p.4.
Varghese, B. and Buyya, R., 2018. Next generation cloud computing: New trends and research
directions. Future Generation Computer Systems. 79. pp.849-861.
Wang, L., Jie, W. and Chen, J., 2018. Grid computing: infrastructure, service, and applications.
CRC Press.
Xiao, S. and et.al., 2018. Cloud platform wireless sensor network detection system based on
data sharing. Cluster Computing. pp.1-12.
Yaibuates, M. and Chaisricharoen, R., 2018. Implementing of IP address Recovery for DHCP
Service. International Journal of Applied Engineering Research. 13(5). pp.2659-2662.
Zamora-Izquierdo, M.A. And et.al., 2019. Smart farming IoT platform based on edge and cloud
computing. Biosystems Engineering. 177. pp.4-17.
Online
Network design for building. 2018. [Online]. Available
through:<https://www.techopedia.com/definition/14760/logical-network>
10
Books and Journals
Benitez, J., Ray, G. and Henseler, J., 2018. Impact of information technology infrastructure
flexibility on mergers and acquisitions. MIS Quarterly. 42(1). pp.25-43.
Bhardwaj, A. and Krishna, C.R., 2018. Performance evaluation of bandwidth for virtual
machine migration in cloud computing. International Journal of Knowledge Engineering
and Data Mining. 5(3). pp.139-152.
Li, R. anD et.al., 2018, June. Research of Subnetting Based on Huffman Coding.
In International Conference on Cloud Computing and Security (pp. 606-616). Springer,
Cham.
Rodriguez, M.A. and Buyya, R., 2018. Scheduling dynamic workloads in multi-tenant scientific
workflow as a service platforms. Future Generation Computer Systems, 79, pp.739-750.
Talia, D., 2019. A view of programming scalable data analysis: from clouds to
exascale. Journal of Cloud Computing. 8(1). p.4.
Varghese, B. and Buyya, R., 2018. Next generation cloud computing: New trends and research
directions. Future Generation Computer Systems. 79. pp.849-861.
Wang, L., Jie, W. and Chen, J., 2018. Grid computing: infrastructure, service, and applications.
CRC Press.
Xiao, S. and et.al., 2018. Cloud platform wireless sensor network detection system based on
data sharing. Cluster Computing. pp.1-12.
Yaibuates, M. and Chaisricharoen, R., 2018. Implementing of IP address Recovery for DHCP
Service. International Journal of Applied Engineering Research. 13(5). pp.2659-2662.
Zamora-Izquierdo, M.A. And et.al., 2019. Smart farming IoT platform based on edge and cloud
computing. Biosystems Engineering. 177. pp.4-17.
Online
Network design for building. 2018. [Online]. Available
through:<https://www.techopedia.com/definition/14760/logical-network>
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





