Optimizing IT Network Design for a Retail Store: LAN Analysis Report
VerifiedAdded on 2023/06/09
|7
|1164
|235
Report
AI Summary
This report provides a comprehensive analysis and redesign of a local area network (LAN) for a retail store, focusing on improving network traffic management, security, and scalability. The existing LAN design is revised to incorporate a client-server model, wireless access points secured with encryption, and a wireless intrusion detection system. Recommendations include implementing firewalls, a RADIUS server for secure remote access, and VLAN configuration for optimized VOIP services. The redesigned network emphasizes redundancy, quality of service, and future scalability, addressing current limitations such as the lack of security measures and VOIP support. The report also suggests segmenting the LAN for easier management and troubleshooting, and separating servers to enhance security. The success of the network relies on aligning the design with the retail store's needs, ensuring performance and reliability as the customer base expands.

Running head: IT NETWORK DESIGNING
IT Network Designing
Name of the Student
Name of the University
Author’s Note
IT Network Designing
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT NETWORK DESIGNING
Table of Contents
1. Local Area Network Design Diagram....................................................................................2
2. Revised LAN Design Diagram..............................................................................................2
2.1. Rationale for the network Design...................................................................................3
3. Recommendations for the changes in the LAN.....................................................................3
4. Analysis of the local area network design..............................................................................4
Bibliography...............................................................................................................................6
IT NETWORK DESIGNING
Table of Contents
1. Local Area Network Design Diagram....................................................................................2
2. Revised LAN Design Diagram..............................................................................................2
2.1. Rationale for the network Design...................................................................................3
3. Recommendations for the changes in the LAN.....................................................................3
4. Analysis of the local area network design..............................................................................4
Bibliography...............................................................................................................................6
2
IT NETWORK DESIGNING
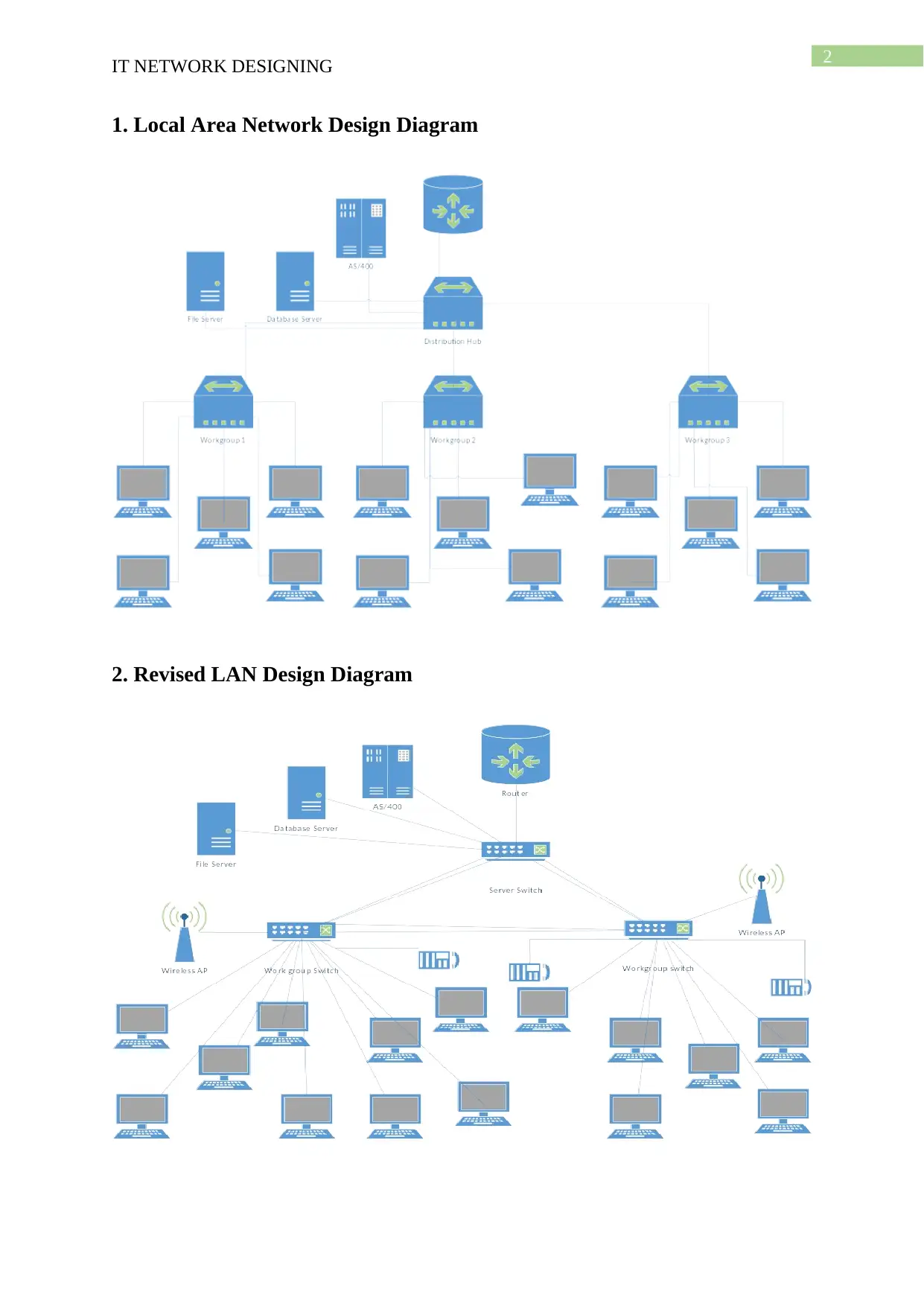
1. Local Area Network Design Diagram
2. Revised LAN Design Diagram
IT NETWORK DESIGNING
1. Local Area Network Design Diagram
2. Revised LAN Design Diagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT NETWORK DESIGNING
2.1. Rationale for the network Design
The flow of the data packets in the network should be identified for the management
of the network traffic and management of the service offered to the users connected in the
network. The client server model is used for separating the hosts and increase the scalability
of the network. The networking protocols that should be used for the configuration of the
router is analysed depending on the service and the type of server proposed for the retail store
network. There is need for the installation of wireless access point and secure it with the
application of encryption algorithm. The wireless intrusion detection system is used for the
management of the network resources and enforcement of the security policies for reducing
the risk associated with the access of the wireless network platform.
The telephony service should be enabled and the location of the installation of the IP
phones should be identified for configuring the network with IP telephony service. The
routers can be configured with DHCP address pool such that the complexity and
manageability of the network is reduced. The hubs used in the current design is replaced with
switches such that the traffic can be managed efficiently and the risk of narrow bandwidth is
eliminated in the proposed network framework. The network is tested using the HTTP
protocol and it is tested for management of the network policy. Active directory configuration
should be used for the management of the identity of the users and management of the
authentication of the user for the management of the inventory. The use of the redundant link
reduces the chances of network downtime and increases the availability of the resources.
3. Recommendations for the changes in the LAN
The current network diagram created for the retail store lacks in security since there
are no network firewall used. Firewall should be used for the network for blocking the
unknown IP address to access the internal resources of the network. A RADIUS server is also
IT NETWORK DESIGNING
2.1. Rationale for the network Design
The flow of the data packets in the network should be identified for the management
of the network traffic and management of the service offered to the users connected in the
network. The client server model is used for separating the hosts and increase the scalability
of the network. The networking protocols that should be used for the configuration of the
router is analysed depending on the service and the type of server proposed for the retail store
network. There is need for the installation of wireless access point and secure it with the
application of encryption algorithm. The wireless intrusion detection system is used for the
management of the network resources and enforcement of the security policies for reducing
the risk associated with the access of the wireless network platform.
The telephony service should be enabled and the location of the installation of the IP
phones should be identified for configuring the network with IP telephony service. The
routers can be configured with DHCP address pool such that the complexity and
manageability of the network is reduced. The hubs used in the current design is replaced with
switches such that the traffic can be managed efficiently and the risk of narrow bandwidth is
eliminated in the proposed network framework. The network is tested using the HTTP
protocol and it is tested for management of the network policy. Active directory configuration
should be used for the management of the identity of the users and management of the
authentication of the user for the management of the inventory. The use of the redundant link
reduces the chances of network downtime and increases the availability of the resources.
3. Recommendations for the changes in the LAN
The current network diagram created for the retail store lacks in security since there
are no network firewall used. Firewall should be used for the network for blocking the
unknown IP address to access the internal resources of the network. A RADIUS server is also
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT NETWORK DESIGNING
implemented in the network for the management of the remote connection for the five sales
representatives and enable them to access the files residing in the file server for increasing the
efficiency of the workplace. The current framework of the network should maintain the
quality of service and have the option for expansion of the network for management of the
future growth of the retail store.
Moreover in the current network there is no option for connecting VOIP device and
the changes is made and for the network and should be configured with VLAN such that
there is no congestion in the network. It helps in reducing the cost of telecommunication and
the service levels should be created for the management of the network framework. The local
area network is divided into smaller segments such that it can be managed easily and the
errors can be identified for troubleshooting the network. There is also need for wireless
connectivity for connecting the wireless device in the network and serve the needs of the
customer. The area covered by the retails store should be analysed for implementation of the
wireless access point in the network and provide service to the sales representatives to serve
the needs of the customer visiting the retail store. The servers connected in the network
should be installed separately from the network such that the access of the network is
prevented for the unknown users and the security of the network is maintained.
4. Analysis of the local area network design
The local area network design is created for the management of the different
operations of the small to medium sized retail store. The success of the network dependents
on the alignment of the needs of the retails store with the developed network. The network is
developed such that there is no performance issues and no problem rises during the
development of the network framework. The current needs of the organization that is the
IT NETWORK DESIGNING
implemented in the network for the management of the remote connection for the five sales
representatives and enable them to access the files residing in the file server for increasing the
efficiency of the workplace. The current framework of the network should maintain the
quality of service and have the option for expansion of the network for management of the
future growth of the retail store.
Moreover in the current network there is no option for connecting VOIP device and
the changes is made and for the network and should be configured with VLAN such that
there is no congestion in the network. It helps in reducing the cost of telecommunication and
the service levels should be created for the management of the network framework. The local
area network is divided into smaller segments such that it can be managed easily and the
errors can be identified for troubleshooting the network. There is also need for wireless
connectivity for connecting the wireless device in the network and serve the needs of the
customer. The area covered by the retails store should be analysed for implementation of the
wireless access point in the network and provide service to the sales representatives to serve
the needs of the customer visiting the retail store. The servers connected in the network
should be installed separately from the network such that the access of the network is
prevented for the unknown users and the security of the network is maintained.
4. Analysis of the local area network design
The local area network design is created for the management of the different
operations of the small to medium sized retail store. The success of the network dependents
on the alignment of the needs of the retails store with the developed network. The network is
developed such that there is no performance issues and no problem rises during the
development of the network framework. The current needs of the organization that is the

5
IT NETWORK DESIGNING
number of users is analysed with the increase in the customer base for the expansion of the
network.
The phone bills are also audited for the analysis of the implementation of the VOIP
system in the current network for reducing the telecommunication cost and get the maximum
benefit from the developed network. The needs of the server for recording the details and
implementation of the different technology for maintaining the security of the network is also
evaluated for the development of the network proposal. The current issues faced by the retail
store is eliminated for increasing the efficiency of the network and increasing the reliability
of the network.
IT NETWORK DESIGNING
number of users is analysed with the increase in the customer base for the expansion of the
network.
The phone bills are also audited for the analysis of the implementation of the VOIP
system in the current network for reducing the telecommunication cost and get the maximum
benefit from the developed network. The needs of the server for recording the details and
implementation of the different technology for maintaining the security of the network is also
evaluated for the development of the network proposal. The current issues faced by the retail
store is eliminated for increasing the efficiency of the network and increasing the reliability
of the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT NETWORK DESIGNING
Bibliography
Chen, X., Zhong, C., Yuen, C., & Chen, H. H. (2015). Multi-antenna relay aided wireless
physical layer security. IEEE Communications Magazine, 53(12), 40-46.
Ferreira, D., Kostakos, V., & Dey, A. K. (2015). AWARE: mobile context instrumentation
framework. Frontiers in ICT, 2, 6.
Li, J., Lu, H., & Guizani, M. (2015). ACPN: A novel authentication framework with
conditional privacy-preservation and non-repudiation for VANETs. IEEE
Transactions on Parallel and Distributed Systems, 26(4), 938-948.
Maslov, A. E., Katuntsev, S. L., & Maliavko, A. A. (2017, June). Study and implementation
of authentication mechanism by RADIUS-server in switches and routers using
NETCONF protocol. In Micro/Nanotechnologies and Electron Devices (EDM), 2017
18th International Conference of Young Specialists on (pp. 111-114). IEEE.
Sedjelmaci, H., & Senouci, S. M. (2015). An accurate and efficient collaborative intrusion
detection framework to secure vehicular networks. Computers & Electrical
Engineering, 43, 33-47.
Winter, S., & McCauley, M. (2015). Dynamic Peer Discovery for RADIUS/TLS and
RADIUS/DTLS Based on the Network Access Identifier (NAI) (No. RFC 7585).
IT NETWORK DESIGNING
Bibliography
Chen, X., Zhong, C., Yuen, C., & Chen, H. H. (2015). Multi-antenna relay aided wireless
physical layer security. IEEE Communications Magazine, 53(12), 40-46.
Ferreira, D., Kostakos, V., & Dey, A. K. (2015). AWARE: mobile context instrumentation
framework. Frontiers in ICT, 2, 6.
Li, J., Lu, H., & Guizani, M. (2015). ACPN: A novel authentication framework with
conditional privacy-preservation and non-repudiation for VANETs. IEEE
Transactions on Parallel and Distributed Systems, 26(4), 938-948.
Maslov, A. E., Katuntsev, S. L., & Maliavko, A. A. (2017, June). Study and implementation
of authentication mechanism by RADIUS-server in switches and routers using
NETCONF protocol. In Micro/Nanotechnologies and Electron Devices (EDM), 2017
18th International Conference of Young Specialists on (pp. 111-114). IEEE.
Sedjelmaci, H., & Senouci, S. M. (2015). An accurate and efficient collaborative intrusion
detection framework to secure vehicular networks. Computers & Electrical
Engineering, 43, 33-47.
Winter, S., & McCauley, M. (2015). Dynamic Peer Discovery for RADIUS/TLS and
RADIUS/DTLS Based on the Network Access Identifier (NAI) (No. RFC 7585).
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




