Comprehensive IT Operations Plan for TreasureChest SaaS Company
VerifiedAdded on 2022/08/20
|8
|1827
|31
Report
AI Summary
This report presents an IT operations plan for TreasureChest, a SaaS treasury management company. It begins with an analysis of the current environment, including SaaS operations, hardware, operating systems, networks, software, and databases. The plan then outlines strategic goals and corresponding IT operational goals, such as enhancing network scalability, upgrading database storage, and improving software testing. The report details enhancements needed to support each strategic objective and lists planned activities to meet each objective. A sustainability plan is provided, spanning one, three, and five-year timeframes. Furthermore, the report identifies potential security risks, like malware and data leakage, and proposes mitigation strategies. The report concludes with an operational workflow and references to relevant academic sources.

IT Operations Plan Template
Record all responses to C927 Task 1 in this template.
A. Current Environment Analysis
SaaS Operation: The major SaaS operatuions of TreasureChest company are web service and the co-
location data centre, security, networking, the infrastructure and the data management. The monthly
bills are provided to the customers for each of the subscriptions, on the basis of the quantity of the
users within that particular subscription. ProServices are offered by TreasureChest, along with the
professional services at cost for effective account configuration as well as the data migration. The main
flexibility of SaaS environment of the company is significantly extensive because it has executed
significantly innovative security measures to secure company cloud environment. TreasureChest has
also initiated providing the ProServices, the professional services at the cost for the account
configuration as well as the data migration. This could be considered as major SaaS task of company
and this particular service is extensively utilized for various business as the majority of businesses needs
reconfiguration as well as the implemented from mainly time-to-time.
Hardware: The main hardware of TreasureChest company are the network server, the desktops,
wireless routers, external hard drive as well as the printers. Various kinds of desktops are utilized by the
TreasureChest company that allows the employees to interpret various data from the multiple servers.
The implemented network server in the organization is mainly used to deliver the data to employees of
TreasureChest company and the various routers are implemented by the TreasureChest company to
allow the transfer of internet facilities to each department of TreasureChest company. Substantial
business value is gained by the TreasureChest company from implemented of modern technology along
with the implementation of the upgraded versions of hardware. As an instance, the data of all the
transactions of the customers are mainly stored in the servers of organization that could be accessed by
the employees of particular level.
Operating Systems: Windows operating system is the operating system that is presently being utilized
in the company. Windows operating system offers the enhanced platform for business that helps in
conducting normal business processes as well as the simplified methods of computation is offered to all
the employees of organization. In the present times, there are no significant issues of delay or any
damage of all the information that has been stored in computers as Windows operating system assists
the business with securing all the confidential data.
Record all responses to C927 Task 1 in this template.
A. Current Environment Analysis
SaaS Operation: The major SaaS operatuions of TreasureChest company are web service and the co-
location data centre, security, networking, the infrastructure and the data management. The monthly
bills are provided to the customers for each of the subscriptions, on the basis of the quantity of the
users within that particular subscription. ProServices are offered by TreasureChest, along with the
professional services at cost for effective account configuration as well as the data migration. The main
flexibility of SaaS environment of the company is significantly extensive because it has executed
significantly innovative security measures to secure company cloud environment. TreasureChest has
also initiated providing the ProServices, the professional services at the cost for the account
configuration as well as the data migration. This could be considered as major SaaS task of company
and this particular service is extensively utilized for various business as the majority of businesses needs
reconfiguration as well as the implemented from mainly time-to-time.
Hardware: The main hardware of TreasureChest company are the network server, the desktops,
wireless routers, external hard drive as well as the printers. Various kinds of desktops are utilized by the
TreasureChest company that allows the employees to interpret various data from the multiple servers.
The implemented network server in the organization is mainly used to deliver the data to employees of
TreasureChest company and the various routers are implemented by the TreasureChest company to
allow the transfer of internet facilities to each department of TreasureChest company. Substantial
business value is gained by the TreasureChest company from implemented of modern technology along
with the implementation of the upgraded versions of hardware. As an instance, the data of all the
transactions of the customers are mainly stored in the servers of organization that could be accessed by
the employees of particular level.
Operating Systems: Windows operating system is the operating system that is presently being utilized
in the company. Windows operating system offers the enhanced platform for business that helps in
conducting normal business processes as well as the simplified methods of computation is offered to all
the employees of organization. In the present times, there are no significant issues of delay or any
damage of all the information that has been stored in computers as Windows operating system assists
the business with securing all the confidential data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
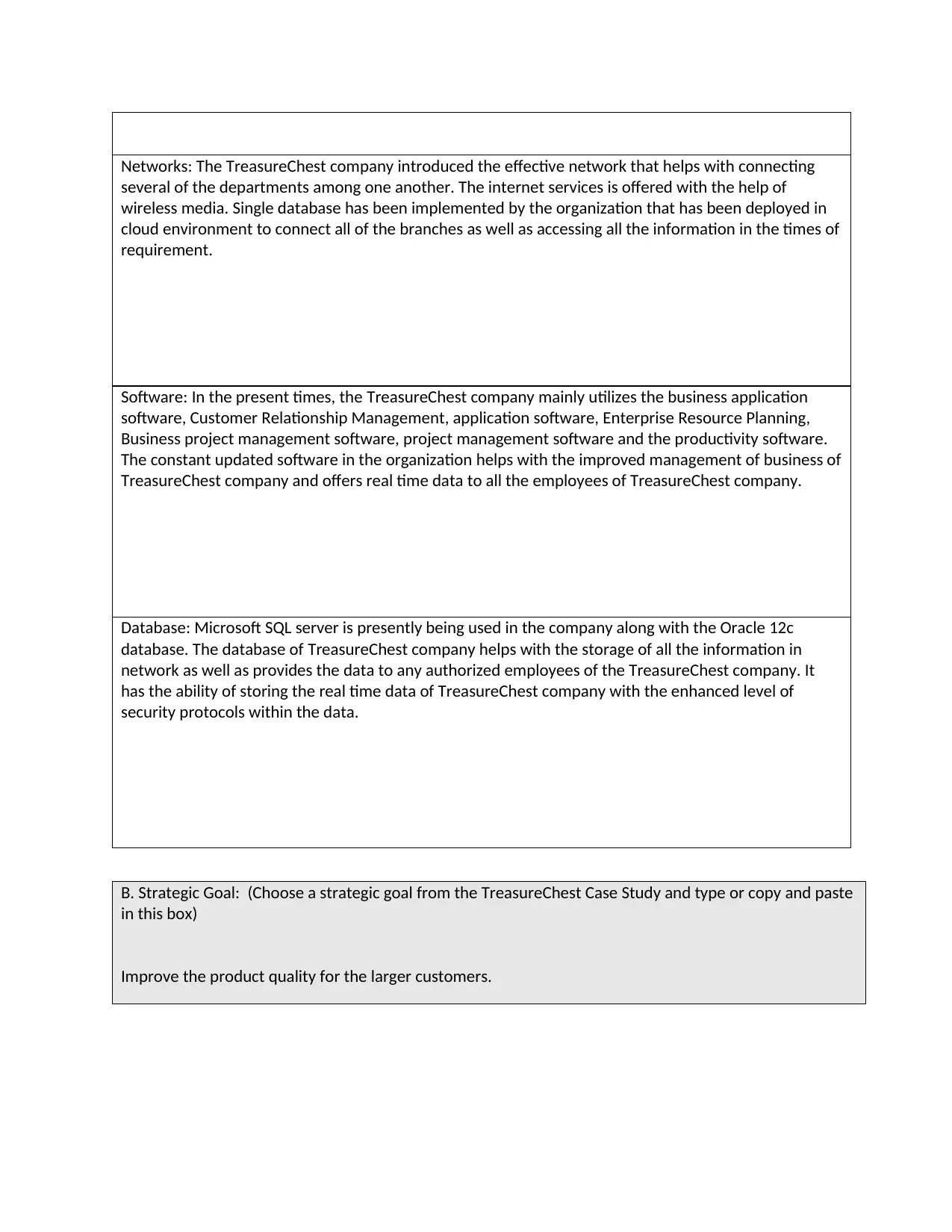
Networks: The TreasureChest company introduced the effective network that helps with connecting
several of the departments among one another. The internet services is offered with the help of
wireless media. Single database has been implemented by the organization that has been deployed in
cloud environment to connect all of the branches as well as accessing all the information in the times of
requirement.
Software: In the present times, the TreasureChest company mainly utilizes the business application
software, Customer Relationship Management, application software, Enterprise Resource Planning,
Business project management software, project management software and the productivity software.
The constant updated software in the organization helps with the improved management of business of
TreasureChest company and offers real time data to all the employees of TreasureChest company.
Database: Microsoft SQL server is presently being used in the company along with the Oracle 12c
database. The database of TreasureChest company helps with the storage of all the information in
network as well as provides the data to any authorized employees of the TreasureChest company. It
has the ability of storing the real time data of TreasureChest company with the enhanced level of
security protocols within the data.
B. Strategic Goal: (Choose a strategic goal from the TreasureChest Case Study and type or copy and paste
in this box)
Improve the product quality for the larger customers.
several of the departments among one another. The internet services is offered with the help of
wireless media. Single database has been implemented by the organization that has been deployed in
cloud environment to connect all of the branches as well as accessing all the information in the times of
requirement.
Software: In the present times, the TreasureChest company mainly utilizes the business application
software, Customer Relationship Management, application software, Enterprise Resource Planning,
Business project management software, project management software and the productivity software.
The constant updated software in the organization helps with the improved management of business of
TreasureChest company and offers real time data to all the employees of TreasureChest company.
Database: Microsoft SQL server is presently being used in the company along with the Oracle 12c
database. The database of TreasureChest company helps with the storage of all the information in
network as well as provides the data to any authorized employees of the TreasureChest company. It
has the ability of storing the real time data of TreasureChest company with the enhanced level of
security protocols within the data.
B. Strategic Goal: (Choose a strategic goal from the TreasureChest Case Study and type or copy and paste
in this box)
Improve the product quality for the larger customers.
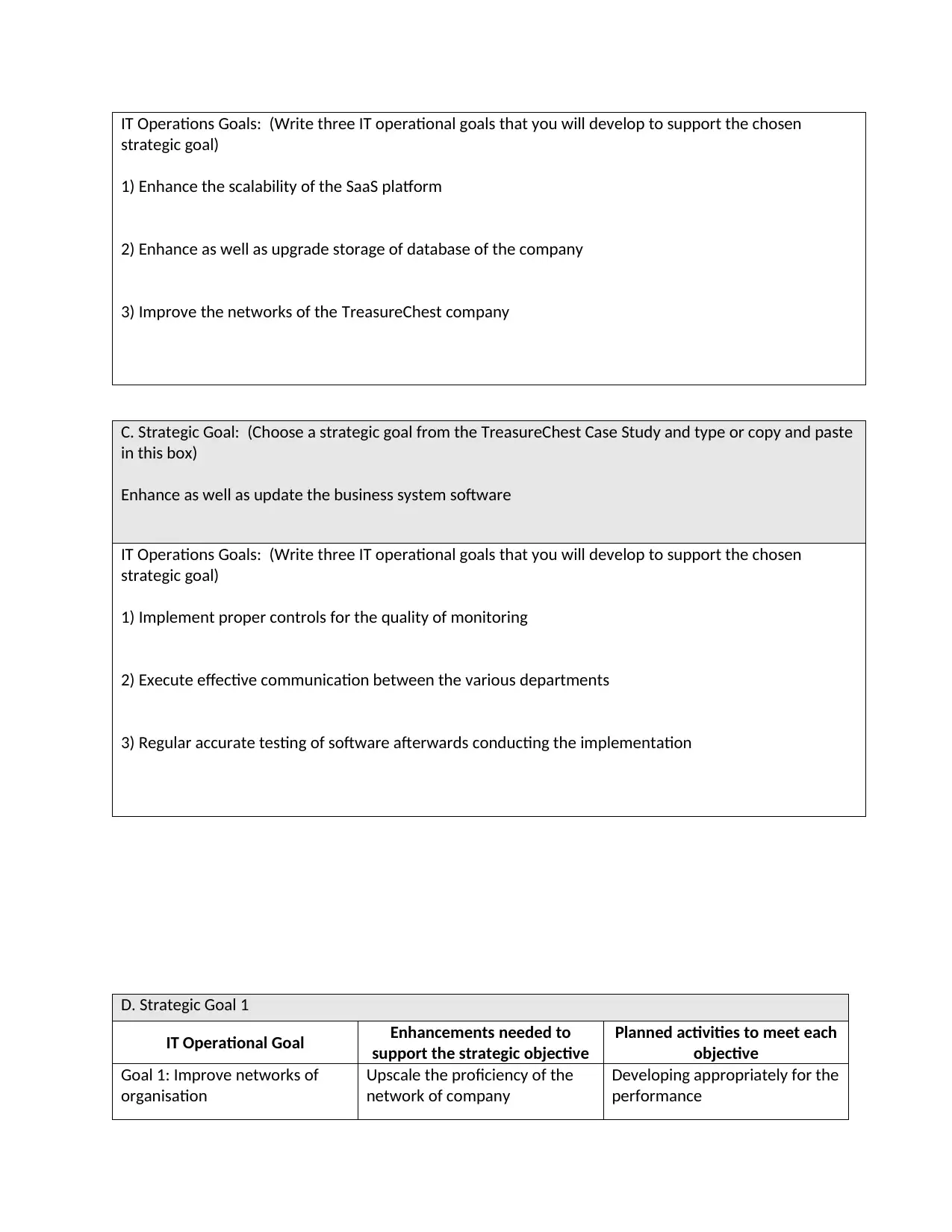
IT Operations Goals: (Write three IT operational goals that you will develop to support the chosen
strategic goal)
1) Enhance the scalability of the SaaS platform
2) Enhance as well as upgrade storage of database of the company
3) Improve the networks of the TreasureChest company
C. Strategic Goal: (Choose a strategic goal from the TreasureChest Case Study and type or copy and paste
in this box)
Enhance as well as update the business system software
IT Operations Goals: (Write three IT operational goals that you will develop to support the chosen
strategic goal)
1) Implement proper controls for the quality of monitoring
2) Execute effective communication between the various departments
3) Regular accurate testing of software afterwards conducting the implementation
D. Strategic Goal 1
IT Operational Goal Enhancements needed to
support the strategic objective
Planned activities to meet each
objective
Goal 1: Improve networks of
organisation
Upscale the proficiency of the
network of company
Developing appropriately for the
performance
strategic goal)
1) Enhance the scalability of the SaaS platform
2) Enhance as well as upgrade storage of database of the company
3) Improve the networks of the TreasureChest company
C. Strategic Goal: (Choose a strategic goal from the TreasureChest Case Study and type or copy and paste
in this box)
Enhance as well as update the business system software
IT Operations Goals: (Write three IT operational goals that you will develop to support the chosen
strategic goal)
1) Implement proper controls for the quality of monitoring
2) Execute effective communication between the various departments
3) Regular accurate testing of software afterwards conducting the implementation
D. Strategic Goal 1
IT Operational Goal Enhancements needed to
support the strategic objective
Planned activities to meet each
objective
Goal 1: Improve networks of
organisation
Upscale the proficiency of the
network of company
Developing appropriately for the
performance
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
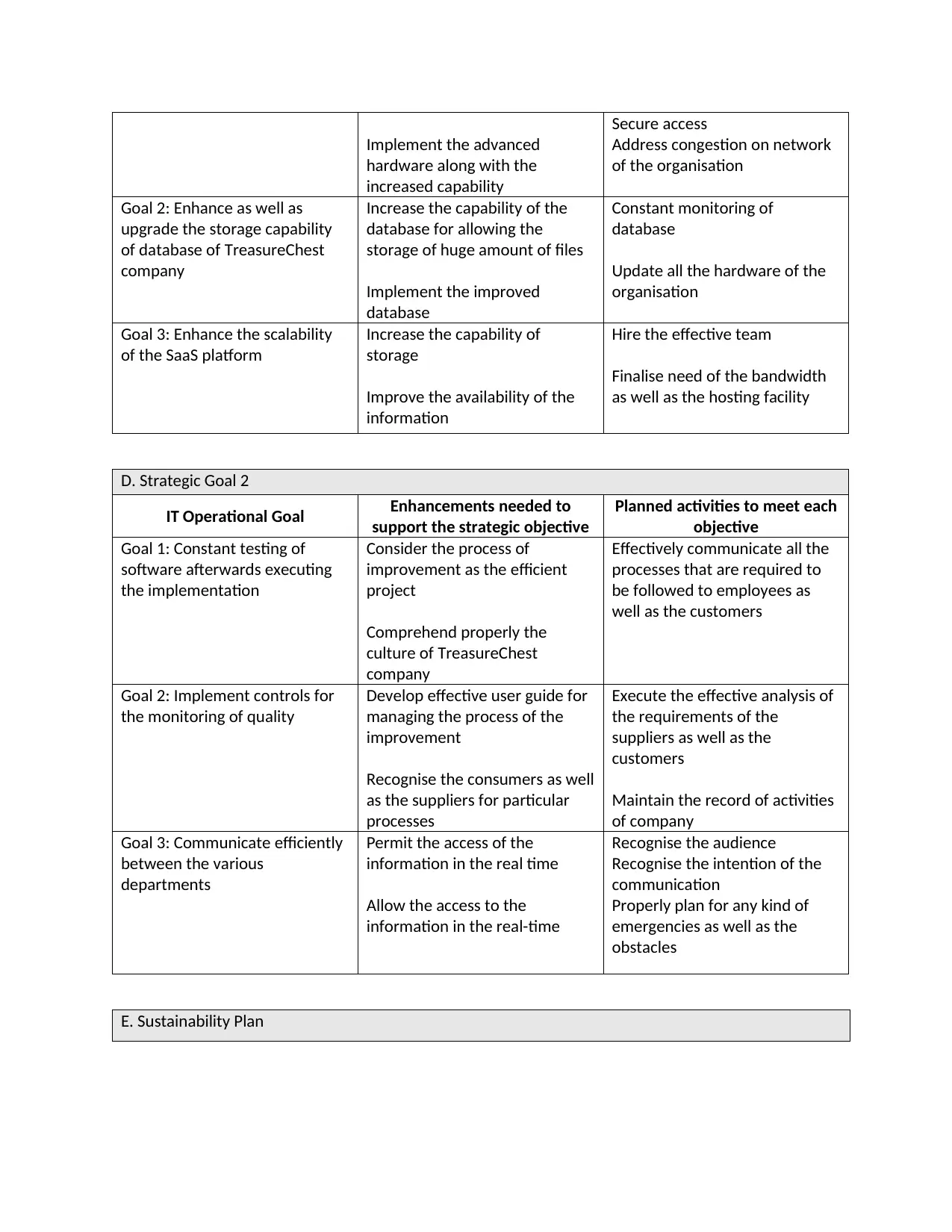
Implement the advanced
hardware along with the
increased capability
Secure access
Address congestion on network
of the organisation
Goal 2: Enhance as well as
upgrade the storage capability
of database of TreasureChest
company
Increase the capability of the
database for allowing the
storage of huge amount of files
Implement the improved
database
Constant monitoring of
database
Update all the hardware of the
organisation
Goal 3: Enhance the scalability
of the SaaS platform
Increase the capability of
storage
Improve the availability of the
information
Hire the effective team
Finalise need of the bandwidth
as well as the hosting facility
D. Strategic Goal 2
IT Operational Goal Enhancements needed to
support the strategic objective
Planned activities to meet each
objective
Goal 1: Constant testing of
software afterwards executing
the implementation
Consider the process of
improvement as the efficient
project
Comprehend properly the
culture of TreasureChest
company
Effectively communicate all the
processes that are required to
be followed to employees as
well as the customers
Goal 2: Implement controls for
the monitoring of quality
Develop effective user guide for
managing the process of the
improvement
Recognise the consumers as well
as the suppliers for particular
processes
Execute the effective analysis of
the requirements of the
suppliers as well as the
customers
Maintain the record of activities
of company
Goal 3: Communicate efficiently
between the various
departments
Permit the access of the
information in the real time
Allow the access to the
information in the real-time
Recognise the audience
Recognise the intention of the
communication
Properly plan for any kind of
emergencies as well as the
obstacles
E. Sustainability Plan
hardware along with the
increased capability
Secure access
Address congestion on network
of the organisation
Goal 2: Enhance as well as
upgrade the storage capability
of database of TreasureChest
company
Increase the capability of the
database for allowing the
storage of huge amount of files
Implement the improved
database
Constant monitoring of
database
Update all the hardware of the
organisation
Goal 3: Enhance the scalability
of the SaaS platform
Increase the capability of
storage
Improve the availability of the
information
Hire the effective team
Finalise need of the bandwidth
as well as the hosting facility
D. Strategic Goal 2
IT Operational Goal Enhancements needed to
support the strategic objective
Planned activities to meet each
objective
Goal 1: Constant testing of
software afterwards executing
the implementation
Consider the process of
improvement as the efficient
project
Comprehend properly the
culture of TreasureChest
company
Effectively communicate all the
processes that are required to
be followed to employees as
well as the customers
Goal 2: Implement controls for
the monitoring of quality
Develop effective user guide for
managing the process of the
improvement
Recognise the consumers as well
as the suppliers for particular
processes
Execute the effective analysis of
the requirements of the
suppliers as well as the
customers
Maintain the record of activities
of company
Goal 3: Communicate efficiently
between the various
departments
Permit the access of the
information in the real time
Allow the access to the
information in the real-time
Recognise the audience
Recognise the intention of the
communication
Properly plan for any kind of
emergencies as well as the
obstacles
E. Sustainability Plan
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
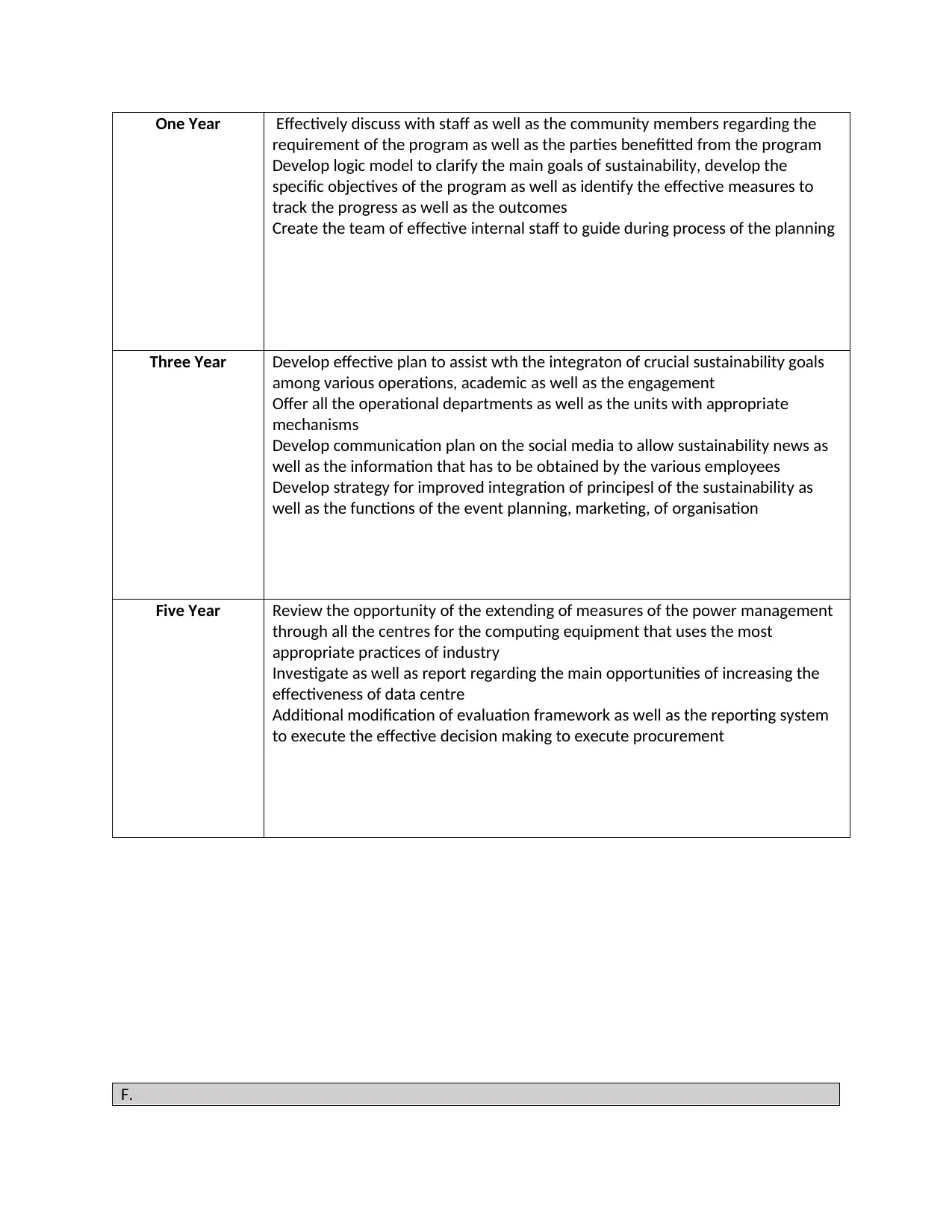
One Year Effectively discuss with staff as well as the community members regarding the
requirement of the program as well as the parties benefitted from the program
Develop logic model to clarify the main goals of sustainability, develop the
specific objectives of the program as well as identify the effective measures to
track the progress as well as the outcomes
Create the team of effective internal staff to guide during process of the planning
Three Year Develop effective plan to assist wth the integraton of crucial sustainability goals
among various operations, academic as well as the engagement
Offer all the operational departments as well as the units with appropriate
mechanisms
Develop communication plan on the social media to allow sustainability news as
well as the information that has to be obtained by the various employees
Develop strategy for improved integration of principesl of the sustainability as
well as the functions of the event planning, marketing, of organisation
Five Year Review the opportunity of the extending of measures of the power management
through all the centres for the computing equipment that uses the most
appropriate practices of industry
Investigate as well as report regarding the main opportunities of increasing the
effectiveness of data centre
Additional modification of evaluation framework as well as the reporting system
to execute the effective decision making to execute procurement
F.
requirement of the program as well as the parties benefitted from the program
Develop logic model to clarify the main goals of sustainability, develop the
specific objectives of the program as well as identify the effective measures to
track the progress as well as the outcomes
Create the team of effective internal staff to guide during process of the planning
Three Year Develop effective plan to assist wth the integraton of crucial sustainability goals
among various operations, academic as well as the engagement
Offer all the operational departments as well as the units with appropriate
mechanisms
Develop communication plan on the social media to allow sustainability news as
well as the information that has to be obtained by the various employees
Develop strategy for improved integration of principesl of the sustainability as
well as the functions of the event planning, marketing, of organisation
Five Year Review the opportunity of the extending of measures of the power management
through all the centres for the computing equipment that uses the most
appropriate practices of industry
Investigate as well as report regarding the main opportunities of increasing the
effectiveness of data centre
Additional modification of evaluation framework as well as the reporting system
to execute the effective decision making to execute procurement
F.
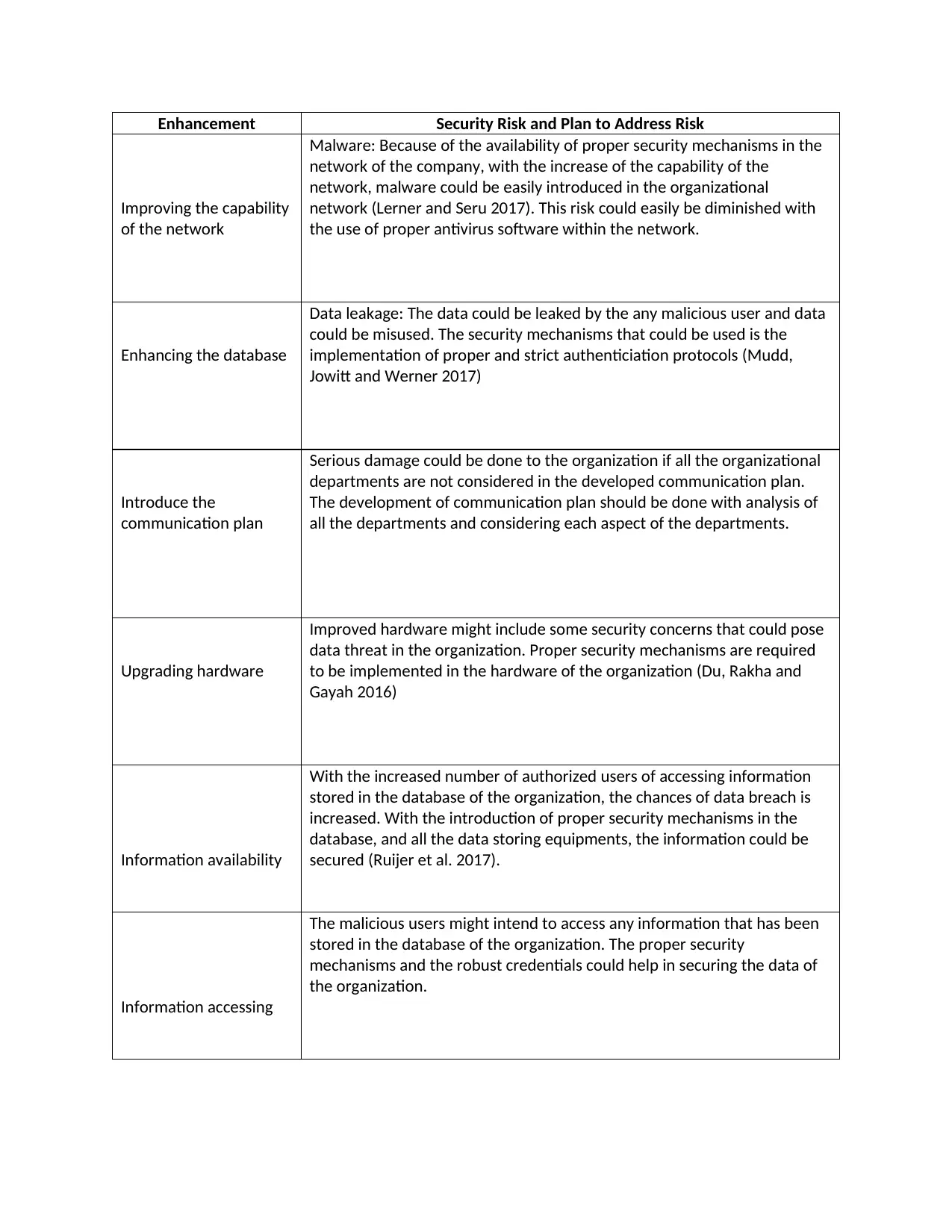
Enhancement Security Risk and Plan to Address Risk
Improving the capability
of the network
Malware: Because of the availability of proper security mechanisms in the
network of the company, with the increase of the capability of the
network, malware could be easily introduced in the organizational
network (Lerner and Seru 2017). This risk could easily be diminished with
the use of proper antivirus software within the network.
Enhancing the database
Data leakage: The data could be leaked by the any malicious user and data
could be misused. The security mechanisms that could be used is the
implementation of proper and strict authenticiation protocols (Mudd,
Jowitt and Werner 2017)
Introduce the
communication plan
Serious damage could be done to the organization if all the organizational
departments are not considered in the developed communication plan.
The development of communication plan should be done with analysis of
all the departments and considering each aspect of the departments.
Upgrading hardware
Improved hardware might include some security concerns that could pose
data threat in the organization. Proper security mechanisms are required
to be implemented in the hardware of the organization (Du, Rakha and
Gayah 2016)
Information availability
With the increased number of authorized users of accessing information
stored in the database of the organization, the chances of data breach is
increased. With the introduction of proper security mechanisms in the
database, and all the data storing equipments, the information could be
secured (Ruijer et al. 2017).
Information accessing
The malicious users might intend to access any information that has been
stored in the database of the organization. The proper security
mechanisms and the robust credentials could help in securing the data of
the organization.
Improving the capability
of the network
Malware: Because of the availability of proper security mechanisms in the
network of the company, with the increase of the capability of the
network, malware could be easily introduced in the organizational
network (Lerner and Seru 2017). This risk could easily be diminished with
the use of proper antivirus software within the network.
Enhancing the database
Data leakage: The data could be leaked by the any malicious user and data
could be misused. The security mechanisms that could be used is the
implementation of proper and strict authenticiation protocols (Mudd,
Jowitt and Werner 2017)
Introduce the
communication plan
Serious damage could be done to the organization if all the organizational
departments are not considered in the developed communication plan.
The development of communication plan should be done with analysis of
all the departments and considering each aspect of the departments.
Upgrading hardware
Improved hardware might include some security concerns that could pose
data threat in the organization. Proper security mechanisms are required
to be implemented in the hardware of the organization (Du, Rakha and
Gayah 2016)
Information availability
With the increased number of authorized users of accessing information
stored in the database of the organization, the chances of data breach is
increased. With the introduction of proper security mechanisms in the
database, and all the data storing equipments, the information could be
secured (Ruijer et al. 2017).
Information accessing
The malicious users might intend to access any information that has been
stored in the database of the organization. The proper security
mechanisms and the robust credentials could help in securing the data of
the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
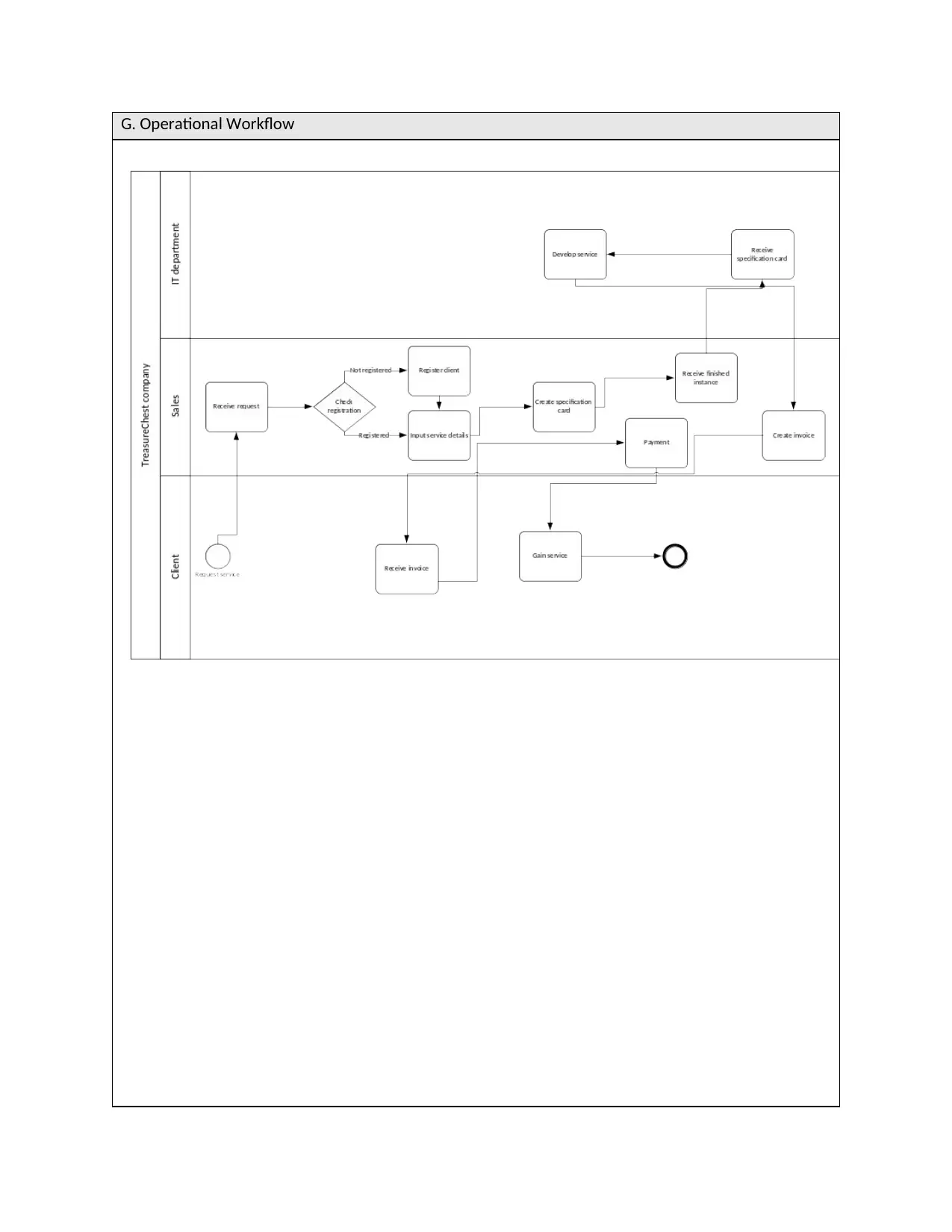
G. Operational Workflow
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Du, J., Rakha, H. and Gayah, V.V., 2016. Deriving macroscopic fundamental diagrams from probe data:
Issues and proposed solutions. Transportation Research Part C: Emerging Technologies, 66, pp.136-149.
Lerner, J. and Seru, A., 2017. The use and misuse of patent data: Issues for corporate finance and
beyond (No. w24053). National Bureau of Economic Research.
Mudd, G.M., Jowitt, S.M. and Werner, T.T., 2017. The world's lead-zinc mineral resources: Scarcity, data,
issues and opportunities. Ore Geology Reviews, 80, pp.1160-1190.
Ruijer, E., Grimmelikhuijsen, S., Hogan, M., Enzerink, S., Ojo, A. and Meijer, A., 2017. Connecting societal
issues, users and data. Scenario-based design of open data platforms. Government Information
Quarterly, 34(3), pp.470-480.
Du, J., Rakha, H. and Gayah, V.V., 2016. Deriving macroscopic fundamental diagrams from probe data:
Issues and proposed solutions. Transportation Research Part C: Emerging Technologies, 66, pp.136-149.
Lerner, J. and Seru, A., 2017. The use and misuse of patent data: Issues for corporate finance and
beyond (No. w24053). National Bureau of Economic Research.
Mudd, G.M., Jowitt, S.M. and Werner, T.T., 2017. The world's lead-zinc mineral resources: Scarcity, data,
issues and opportunities. Ore Geology Reviews, 80, pp.1160-1190.
Ruijer, E., Grimmelikhuijsen, S., Hogan, M., Enzerink, S., Ojo, A. and Meijer, A., 2017. Connecting societal
issues, users and data. Scenario-based design of open data platforms. Government Information
Quarterly, 34(3), pp.470-480.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





