Exploring Cybersecurity Threat Landscape and Good Practices
VerifiedAdded on 2019/11/20
|18
|4070
|295
Report
AI Summary
The assignment content is a comprehensive report on the threat landscape and good practices guide for various sectors such as software defined networks/5G, internet infrastructure, and critical infrastructure protection. The report provides an overview of current and emerging cyber-threats, risk perception and management in cloud computing, malicious threat agents for the smart connected home, and automatic binary execution environment based on real-machines for intelligent malware analysis.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of the Student
Name of the University
IT RISK MANAGEMENT
Name of the Student
Name of the University
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1IT RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
Question 1..................................................................................................................................3
Question 2..................................................................................................................................5
Question 3..................................................................................................................................7
Question 4................................................................................................................................10
Question 5................................................................................................................................12
Conclusion................................................................................................................................14
References................................................................................................................................16
Table of Contents
Introduction................................................................................................................................2
Question 1..................................................................................................................................3
Question 2..................................................................................................................................5
Question 3..................................................................................................................................7
Question 4................................................................................................................................10
Question 5................................................................................................................................12
Conclusion................................................................................................................................14
References................................................................................................................................16

2IT RISK MANAGEMENT
Introduction
Big Data often indicates the designated palette of algorithms, system employment and
technology that collects the data of unmatched values, variety and volume. This extraction is
done by massive amount of analytics that are advanced and has the ability to parallel
computation. The Big Data sources are diverse and are in large number. The multimedia
sensors are distributed over several aspects mobile telecommunication devices, IoT (Internet
of Things), business process distribution and other web-based applications. These are all
candidate data providers. With the increase of Big Data algorithms and technologies,
aregradually increasing the effectiveness in decision-making in complex communities and
organization. But the increase of benefits there are also increment of malicious technologies
that creates risks to the organization. ENISA discusses the above issue in this research paper
and explores the aspects of both the importance and risks related to Big Data.
Introduction
Big Data often indicates the designated palette of algorithms, system employment and
technology that collects the data of unmatched values, variety and volume. This extraction is
done by massive amount of analytics that are advanced and has the ability to parallel
computation. The Big Data sources are diverse and are in large number. The multimedia
sensors are distributed over several aspects mobile telecommunication devices, IoT (Internet
of Things), business process distribution and other web-based applications. These are all
candidate data providers. With the increase of Big Data algorithms and technologies,
aregradually increasing the effectiveness in decision-making in complex communities and
organization. But the increase of benefits there are also increment of malicious technologies
that creates risks to the organization. ENISA discusses the above issue in this research paper
and explores the aspects of both the importance and risks related to Big Data.

3IT RISK MANAGEMENT
Question 1
Provide a brief overview of the case study and prepare a diagram for the ENISA Big Data
security infrastructure.
For the situation investigation of ENISA, there is an elaboration on dangers that are
identified with Big Data. There has been highly picked up footing inside most recent couple
of years and consequently the information stockpiling and data innovation has been expected
to assume a genuine part on a few new viewpoints in the general public (Marinos, 2013). The
perspectives that must be create and influenced by the improvement of data innovation and
Big information are nourishment security, wellbeing security, atmosphere and assets that are
proficient to vitality, shrewd transport framework and savvy urban communities. The
potential effect of the Big Data has been recognized by the European Commission by
distinguishing the vital approach in the Big Data. The information is accordingly possible to
the financial drive in the authoritative framework. In the field of science and research there is
additionally a huge effect of the Big Data that keeps on raising. In this way, numerous offices
and foundation everywhere throughout the globe are wanting to dispatch the Big Data
ventures for better misuse of information examination and distributed computing. Innovations
of Big Data can likewise be utilized as a part of the use of military field, for example, battle
pleasing or battling virtual or genuine psychological warfare. Along these lines distinguishing
and gathering the data from heterogeneous sources from any genuine recorded or open
sources has an extraordinary effect (Marinos, Belmonte &Rekleitis, 2014). Cutting edge and
very novel ICT frameworks are utilized as a part of the approach of Big Data. Yet, increment
in the utilization of this Big Data innovation has likewise as often as possible expanded the
odds of digital assaults, information breaks and hacking. The increments of this sort of
difficulties are both slanting the number in complex and effect. By increment in the quantity
Question 1
Provide a brief overview of the case study and prepare a diagram for the ENISA Big Data
security infrastructure.
For the situation investigation of ENISA, there is an elaboration on dangers that are
identified with Big Data. There has been highly picked up footing inside most recent couple
of years and consequently the information stockpiling and data innovation has been expected
to assume a genuine part on a few new viewpoints in the general public (Marinos, 2013). The
perspectives that must be create and influenced by the improvement of data innovation and
Big information are nourishment security, wellbeing security, atmosphere and assets that are
proficient to vitality, shrewd transport framework and savvy urban communities. The
potential effect of the Big Data has been recognized by the European Commission by
distinguishing the vital approach in the Big Data. The information is accordingly possible to
the financial drive in the authoritative framework. In the field of science and research there is
additionally a huge effect of the Big Data that keeps on raising. In this way, numerous offices
and foundation everywhere throughout the globe are wanting to dispatch the Big Data
ventures for better misuse of information examination and distributed computing. Innovations
of Big Data can likewise be utilized as a part of the use of military field, for example, battle
pleasing or battling virtual or genuine psychological warfare. Along these lines distinguishing
and gathering the data from heterogeneous sources from any genuine recorded or open
sources has an extraordinary effect (Marinos, Belmonte &Rekleitis, 2014). Cutting edge and
very novel ICT frameworks are utilized as a part of the approach of Big Data. Yet, increment
in the utilization of this Big Data innovation has likewise as often as possible expanded the
odds of digital assaults, information breaks and hacking. The increments of this sort of
difficulties are both slanting the number in complex and effect. By increment in the quantity
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4IT RISK MANAGEMENT
of ease of use of Big Data in business and associations, the aggressors get motivating forces
for creating and practices assaults against Big Data examination. This innovation has
additionally the capacity to be utilized as a device that battles the digital dangers by offering
security and protection experts that has important bits of knowledge in occurrence
administration and dangers. ENISA conveys the range of this Threats Landscapes in the field
of Big Data investigation, by the contributions from the ENISA Threat Landscape exercises.
The contextual analysis examines about the design, the benefit scientific classification of Big
Data, ENISA danger scientific classification the focused on group of onlookers of Big Data
approach, the procedure by which the contextual investigation has been done, holes of the
examination lastly prescribing the approach.
Distributed computing is portrayed as the foundation layer of Big Data framework in
ENISA. This may meet the framework prerequisite like the versatility, cost-adequacy and the
capacity to scale here and there (Marinos, Belmonte &Rekleitis, 2014). The security
framework of Big Data framework in ENISA takes after:
Data sources layer: This layer comprises of gushing information from the sensor,
unique information sources, and organized data like social database, semi-organized
and unstructured information.
Integration process layer: This layer just worries with vital information having pre-
preparing operation getting information thus incorporated the datasets into an
organized frame.
Data stockpiling layer: This information layer is comprising of substantial assortment
of assets like RDF stores, NoSQL, dispersed record framework and NewSQL
database, that are reasonable for extensive number of datasets that constant
stockpiling.
of ease of use of Big Data in business and associations, the aggressors get motivating forces
for creating and practices assaults against Big Data examination. This innovation has
additionally the capacity to be utilized as a device that battles the digital dangers by offering
security and protection experts that has important bits of knowledge in occurrence
administration and dangers. ENISA conveys the range of this Threats Landscapes in the field
of Big Data investigation, by the contributions from the ENISA Threat Landscape exercises.
The contextual analysis examines about the design, the benefit scientific classification of Big
Data, ENISA danger scientific classification the focused on group of onlookers of Big Data
approach, the procedure by which the contextual investigation has been done, holes of the
examination lastly prescribing the approach.
Distributed computing is portrayed as the foundation layer of Big Data framework in
ENISA. This may meet the framework prerequisite like the versatility, cost-adequacy and the
capacity to scale here and there (Marinos, Belmonte &Rekleitis, 2014). The security
framework of Big Data framework in ENISA takes after:
Data sources layer: This layer comprises of gushing information from the sensor,
unique information sources, and organized data like social database, semi-organized
and unstructured information.
Integration process layer: This layer just worries with vital information having pre-
preparing operation getting information thus incorporated the datasets into an
organized frame.
Data stockpiling layer: This information layer is comprising of substantial assortment
of assets like RDF stores, NoSQL, dispersed record framework and NewSQL
database, that are reasonable for extensive number of datasets that constant
stockpiling.
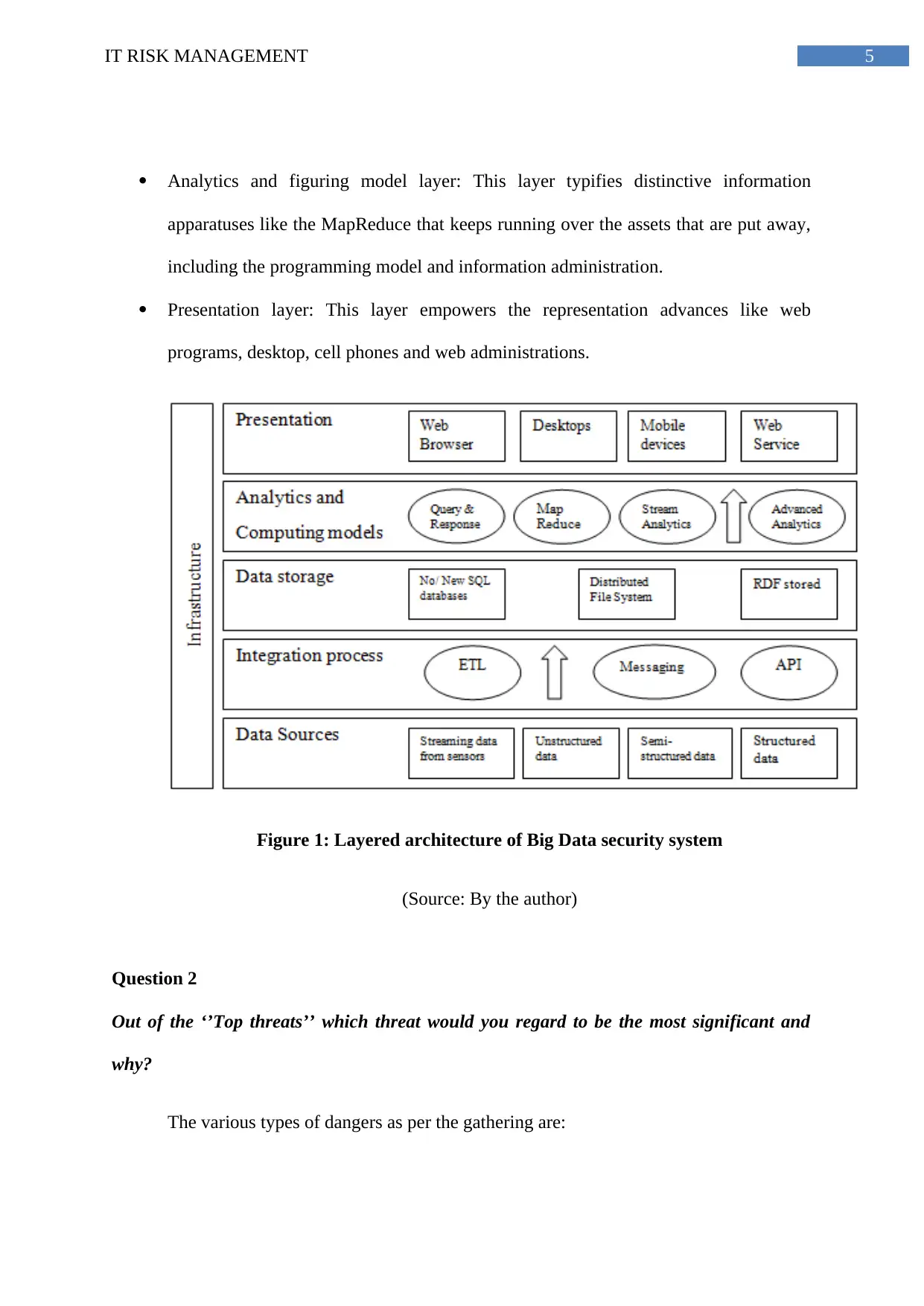
5IT RISK MANAGEMENT
Analytics and figuring model layer: This layer typifies distinctive information
apparatuses like the MapReduce that keeps running over the assets that are put away,
including the programming model and information administration.
Presentation layer: This layer empowers the representation advances like web
programs, desktop, cell phones and web administrations.
Figure 1: Layered architecture of Big Data security system
(Source: By the author)
Question 2
Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The various types of dangers as per the gathering are:
Analytics and figuring model layer: This layer typifies distinctive information
apparatuses like the MapReduce that keeps running over the assets that are put away,
including the programming model and information administration.
Presentation layer: This layer empowers the representation advances like web
programs, desktop, cell phones and web administrations.
Figure 1: Layered architecture of Big Data security system
(Source: By the author)
Question 2
Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The various types of dangers as per the gathering are:

6IT RISK MANAGEMENT
Risk Group: Eavesdropping, Interception and Hijacking
Sharing of information and spillage of data due the human mistake (Barnard-Wills,
2014)
Leaks of information by means of uses in Web (unsecure APIs)
Incorrect adjustment or insufficient arranging and plan
Interception of data
Risk Group: Nefarious Activity/Abuse
Identity extortion
Denial of administration
Malicious code/programming/movement
Generation and utilization of rebel declaration
Unauthorized exercises/Misuse of review instruments/Abuse of approvals
Business process disappointment (Lévy-Bencheton et al., 2015)
Risk Group: Legal
Breach of enactment/Abuse of individual information/Violation of laws or directions
Skill lack
Agreeing the examination of the three dangers bunches the most noteworthy risk is
the "Listening stealthily, Interception and Hijacking", since the most information and security
dangers are identified with this danger confronts greatest troubles, similar to the information
breaches, hacking, digital assault and some more. Influencing the most private and classified
assets of the organization (Cho et al., 2016). The principle assaults by this risk bunches are
Risk Group: Eavesdropping, Interception and Hijacking
Sharing of information and spillage of data due the human mistake (Barnard-Wills,
2014)
Leaks of information by means of uses in Web (unsecure APIs)
Incorrect adjustment or insufficient arranging and plan
Interception of data
Risk Group: Nefarious Activity/Abuse
Identity extortion
Denial of administration
Malicious code/programming/movement
Generation and utilization of rebel declaration
Unauthorized exercises/Misuse of review instruments/Abuse of approvals
Business process disappointment (Lévy-Bencheton et al., 2015)
Risk Group: Legal
Breach of enactment/Abuse of individual information/Violation of laws or directions
Skill lack
Agreeing the examination of the three dangers bunches the most noteworthy risk is
the "Listening stealthily, Interception and Hijacking", since the most information and security
dangers are identified with this danger confronts greatest troubles, similar to the information
breaches, hacking, digital assault and some more. Influencing the most private and classified
assets of the organization (Cho et al., 2016). The principle assaults by this risk bunches are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
Leakage of Information/sharing because of human blunder, Leaks of information by means of
Web applications (unsecure APIs), lacking outline and arranging or inaccurate adjustment
and Interception of data. The commitment of keen gadgets and PC stage from the
phenomenal systems administration to the Big Data may posture protection concern where a
person's area, exchange and other conduct are recorded carefully (Scott et al., 2016). This
danger specialist is antagonistic in nature. Their objective is essentially monetary benefit
having higher ability level. Cybercriminals can be sorted out on a neighborhood, national or
even worldwide level. These specialists are socially and politically inspired people utilizing
the system or the PC framework for challenging and advancing reasons for the harm (Wang,
Anokhin&Anderl, 2017). Prominent sites are for the most part being focused alongside
knowledge organizations and military establishments.
Question 3
Identify and discuss the key Threat Agents. What could be done to minimize their impact
on the system? Based on the data provided, discuss the trends in threat probability.
Agreeing the ENISA danger Landscape, the risk specialist is depicted as "somebody
or something with better than average capacities, a reasonable aim to show a risk and a record
of past exercises in such manner" (Barnard-Wills, Marinos&Portesi, 2014). The association
utilizing Big Data application must know about the dangers that are rising and from which
risk bunches that they have a place. There are classifications by which the danger operators
have been isolated in:
Partnerships: This classification alludes to the undertakings or associations that may draw in
or adjust any strategies that might be exploitative and hostile to the venture. These are the
threatening risk operators having the thought process to assemble upper hand over the
contenders. The association for the most part sorts their principle targets and centering over
Leakage of Information/sharing because of human blunder, Leaks of information by means of
Web applications (unsecure APIs), lacking outline and arranging or inaccurate adjustment
and Interception of data. The commitment of keen gadgets and PC stage from the
phenomenal systems administration to the Big Data may posture protection concern where a
person's area, exchange and other conduct are recorded carefully (Scott et al., 2016). This
danger specialist is antagonistic in nature. Their objective is essentially monetary benefit
having higher ability level. Cybercriminals can be sorted out on a neighborhood, national or
even worldwide level. These specialists are socially and politically inspired people utilizing
the system or the PC framework for challenging and advancing reasons for the harm (Wang,
Anokhin&Anderl, 2017). Prominent sites are for the most part being focused alongside
knowledge organizations and military establishments.
Question 3
Identify and discuss the key Threat Agents. What could be done to minimize their impact
on the system? Based on the data provided, discuss the trends in threat probability.
Agreeing the ENISA danger Landscape, the risk specialist is depicted as "somebody
or something with better than average capacities, a reasonable aim to show a risk and a record
of past exercises in such manner" (Barnard-Wills, Marinos&Portesi, 2014). The association
utilizing Big Data application must know about the dangers that are rising and from which
risk bunches that they have a place. There are classifications by which the danger operators
have been isolated in:
Partnerships: This classification alludes to the undertakings or associations that may draw in
or adjust any strategies that might be exploitative and hostile to the venture. These are the
threatening risk operators having the thought process to assemble upper hand over the
contenders. The association for the most part sorts their principle targets and centering over

8IT RISK MANAGEMENT
the size and segments the undertakings have abilities to the region of essentialness, and from
the territory of innovative perspective to human building insight in the field of mastery
(Brender& Markov, 2013).
Digital Criminals: This risk operator is threatening in nature. Their objective is essentially
monetary profit having higher aptitude level (Le Bray, Mayer &Aubert, 2016).
Cybercriminals can be sorted out on a nearby, national or even worldwide level.
Digital psychological oppressors: The inspiration of this risk operator can either be religious
or political, that extends the movement taking part in digital assaults. The objectives that are
favored by the digital psychological oppressors are fundamentally finished basic framework
like in media transmission, vitality generation or open human services framework (Olesen,
2016). This perplexing framework is by and large picked since disappointment of this
association makes as mayhem and cause extreme effect in the legislature and society.
Content kiddies: These specialists utilize the contents and the projects created since these are
for the most part incompetent, that assaults the system or the PC frameworks and additionally
sites.
Online social programmers (hacktivists): These specialists are socially and politically
inspired people utilizing the system or the PC framework for dissenting and advancing
reasons for the harm (Bugeja, Jacobsson&Davidsson, 2017). Prominent sites are for the most
part being focused alongside insight organizations and military establishments.
Representatives: Sometime the workers for the disintegration of the organization get to the
organization's assets from inside and subsequently unfriendly and non-antagonistic specialists
both of these can considered to the representative. This operator incorporates staffs,
operational staffs, temporary workers or security watchmen of the organization (Belmonte
the size and segments the undertakings have abilities to the region of essentialness, and from
the territory of innovative perspective to human building insight in the field of mastery
(Brender& Markov, 2013).
Digital Criminals: This risk operator is threatening in nature. Their objective is essentially
monetary profit having higher aptitude level (Le Bray, Mayer &Aubert, 2016).
Cybercriminals can be sorted out on a nearby, national or even worldwide level.
Digital psychological oppressors: The inspiration of this risk operator can either be religious
or political, that extends the movement taking part in digital assaults. The objectives that are
favored by the digital psychological oppressors are fundamentally finished basic framework
like in media transmission, vitality generation or open human services framework (Olesen,
2016). This perplexing framework is by and large picked since disappointment of this
association makes as mayhem and cause extreme effect in the legislature and society.
Content kiddies: These specialists utilize the contents and the projects created since these are
for the most part incompetent, that assaults the system or the PC frameworks and additionally
sites.
Online social programmers (hacktivists): These specialists are socially and politically
inspired people utilizing the system or the PC framework for dissenting and advancing
reasons for the harm (Bugeja, Jacobsson&Davidsson, 2017). Prominent sites are for the most
part being focused alongside insight organizations and military establishments.
Representatives: Sometime the workers for the disintegration of the organization get to the
organization's assets from inside and subsequently unfriendly and non-antagonistic specialists
both of these can considered to the representative. This operator incorporates staffs,
operational staffs, temporary workers or security watchmen of the organization (Belmonte

9IT RISK MANAGEMENT
Martin et al., 2015). A lot of information is required for this sort of dangers, which causes
them in setting the viable assault against the advantages of the organization.
Country expresses: these operators for the most part have hostile abilities in digital security
and may utilize it over an endeavor.
Securing the Big Data resources by utilizing pertinent strategies and procedures in the
association. There has been a mutual duty regarding the protection, security and framework
administration of each association. Since, the specialists focus on the fundamental partners of
the Big Data concentrating on the substantial measure of datasets (Belmonte Martin et al.,
2015). After a watchful development of the life cycle of Big Data there ought to be point of
checking and demonstrating the right conduct. There can be achievement in merchants
submitted by the outsider, applying safety efforts and consequently stay refreshed and
centered.
On the premise of the information gave the pattern in the risk likelihood it has been
clarified that:
a) The most data spillage, arranging or despicably adjustment, Inadequate outline and,
Identity extortion, Malicious code, Misuse of review instruments, Failures of business
process, Breach of enactment or Abuse of individual information has been
undermined by the workers (Rhee et al., 2013).
b) Cyber crooks, companies and digital fear mongers for the most part influences the
Leaks of information by means of Web applications having unsecure APIs,
Interception of data, Identity misrepresentation, DOI (Denial of administration),
Malicious code approval and utilization of rebel testaments.
Martin et al., 2015). A lot of information is required for this sort of dangers, which causes
them in setting the viable assault against the advantages of the organization.
Country expresses: these operators for the most part have hostile abilities in digital security
and may utilize it over an endeavor.
Securing the Big Data resources by utilizing pertinent strategies and procedures in the
association. There has been a mutual duty regarding the protection, security and framework
administration of each association. Since, the specialists focus on the fundamental partners of
the Big Data concentrating on the substantial measure of datasets (Belmonte Martin et al.,
2015). After a watchful development of the life cycle of Big Data there ought to be point of
checking and demonstrating the right conduct. There can be achievement in merchants
submitted by the outsider, applying safety efforts and consequently stay refreshed and
centered.
On the premise of the information gave the pattern in the risk likelihood it has been
clarified that:
a) The most data spillage, arranging or despicably adjustment, Inadequate outline and,
Identity extortion, Malicious code, Misuse of review instruments, Failures of business
process, Breach of enactment or Abuse of individual information has been
undermined by the workers (Rhee et al., 2013).
b) Cyber crooks, companies and digital fear mongers for the most part influences the
Leaks of information by means of Web applications having unsecure APIs,
Interception of data, Identity misrepresentation, DOI (Denial of administration),
Malicious code approval and utilization of rebel testaments.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10IT RISK MANAGEMENT
c) The slightest harmed has been finished by the content kiddies as there are
incompetent specialists.
Question 4
How could the ETL process be improved? Discuss.
The dangers scientific categorization as created by the ENISA Threat Landscape
(ETL) Group and this incorporates dangers that are pertinent for the advantages of the Big
Data and these can be enhances by the accompanying ways:
Tackling Bottlenecks: Making without question you log estimations, for instance,
time, number of records arranged and utilization of hardware. Checking what number
of advantages each bit of the methodology takes and address the heaviest one.
Building facts and estimations in the orchestrating condition. Wherever your
bottleneck may be, take a full breath and hop into the code. The power is most likely
going to be with the customers endorsed (Rhee et al., 2013).
Load Data Incrementally: Changes stacked within the old and new data that spares
highly deals of the present time, whereas these are been organized with total loads. It
is much difficult to execute and hence hold on to the routine, not depending on the
inconvenience. Thus the incremented stacking can execute the ETL enhancement.
Partition substantial tables: The use of extensive social database that may enhance the
information handling windows can be parceled in huge tables. Means chop enormous
tables that are physically smaller mainly by the date of execution. Each parcel has its
own records and the files tree is shallower subsequently taking into account snappier
access to the information. It likewise helps in exchanging the data within a table
snappy Meta information operation rather than real addition or erasure of data
records.
c) The slightest harmed has been finished by the content kiddies as there are
incompetent specialists.
Question 4
How could the ETL process be improved? Discuss.
The dangers scientific categorization as created by the ENISA Threat Landscape
(ETL) Group and this incorporates dangers that are pertinent for the advantages of the Big
Data and these can be enhances by the accompanying ways:
Tackling Bottlenecks: Making without question you log estimations, for instance,
time, number of records arranged and utilization of hardware. Checking what number
of advantages each bit of the methodology takes and address the heaviest one.
Building facts and estimations in the orchestrating condition. Wherever your
bottleneck may be, take a full breath and hop into the code. The power is most likely
going to be with the customers endorsed (Rhee et al., 2013).
Load Data Incrementally: Changes stacked within the old and new data that spares
highly deals of the present time, whereas these are been organized with total loads. It
is much difficult to execute and hence hold on to the routine, not depending on the
inconvenience. Thus the incremented stacking can execute the ETL enhancement.
Partition substantial tables: The use of extensive social database that may enhance the
information handling windows can be parceled in huge tables. Means chop enormous
tables that are physically smaller mainly by the date of execution. Each parcel has its
own records and the files tree is shallower subsequently taking into account snappier
access to the information. It likewise helps in exchanging the data within a table
snappy Meta information operation rather than real addition or erasure of data
records.

11IT RISK MANAGEMENT
Cut out incidental information: The gathering of information however much as could
reasonably be expected is imperative, might be not every one of the information but
rather it is exclusive commendable to enter the data centre distribution. For an
example: BI investigators futile by the furniture model’s picture. The only thing that
needs to be changed in the enhancement of the ETL execution, taking a seat and
nature precisely that the information must be prepared and left unessential
segments/lines out. It is a good plan to begin small and develop with the growth rather
than making a unreasonable plan that may take ages to get execute.
Cache the information: It is feasible for the reserve information to accelerate
significantly since get to memory performs faster than the hard drives. It is to be noted
that storing is constrained by the most outrageous measure of memory your gear
support, so it is hard to fit all the plastics data.
Process in parallel: Other than serial preparing, improvement of assets is imperative
by parallel adjustment the whole time. These procedures can scale up by redesigning
the CPU, yet just up to a constrained part. There can be better arrangements also.
Use Hadoop: Apache Hadoop programming is an open source library including
programming administration that permits the dispersion procedure of substantial
arrangements of information over the bunches of PCs by utilizing straightforward
program models. It has been intended to scale up from one-to-different machines that
is, from single server to numerous different servers or machines, which offers
neighborhood stockpiling and calculation.
Cut out incidental information: The gathering of information however much as could
reasonably be expected is imperative, might be not every one of the information but
rather it is exclusive commendable to enter the data centre distribution. For an
example: BI investigators futile by the furniture model’s picture. The only thing that
needs to be changed in the enhancement of the ETL execution, taking a seat and
nature precisely that the information must be prepared and left unessential
segments/lines out. It is a good plan to begin small and develop with the growth rather
than making a unreasonable plan that may take ages to get execute.
Cache the information: It is feasible for the reserve information to accelerate
significantly since get to memory performs faster than the hard drives. It is to be noted
that storing is constrained by the most outrageous measure of memory your gear
support, so it is hard to fit all the plastics data.
Process in parallel: Other than serial preparing, improvement of assets is imperative
by parallel adjustment the whole time. These procedures can scale up by redesigning
the CPU, yet just up to a constrained part. There can be better arrangements also.
Use Hadoop: Apache Hadoop programming is an open source library including
programming administration that permits the dispersion procedure of substantial
arrangements of information over the bunches of PCs by utilizing straightforward
program models. It has been intended to scale up from one-to-different machines that
is, from single server to numerous different servers or machines, which offers
neighborhood stockpiling and calculation.

12IT RISK MANAGEMENT
Question 5
To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or Why
not?
According to the ENISA Big Data there are few focuses on the security framework:
For the application level to the system convention the trusted segments might
dependably be utilized as a part of all levels of the data framework, which are
generally in view of the key administration and the most grounded strategy to encode
(Karchefsky& Rao, 2017). A portion of the cases of this trusted foundation are secure
correspondence conventions, validation framework open key foundation parts and
some more.
It is fundamental for the association to claim a put stock in foundation, to such an
extent that to assemble the data security on the premise of the safety effort at each
level and along these lines giving the validation frameworks and accomplices with
confide in worth exchanges, association and electronic marks.
As the ENISA clarified, there would be an incredible potential effect on increment in
the grouping of information in distributed computing for the programmers, since there
is dependably a possibility for misuse of private and individual data. The digital
offenders regularly store malwares in the system framework or may utilize the stage
to dispatch an assault for their own benefit.
As a developing security issue huge information is on the highest priority on the
rundown as a broadly spreading outcome of distributed computing, social innovations
and other web memberships. This has turned into a recently developing security issue.
The information protection is mostly influenced by the abuse of this huge information
by unapproved clients. Be that as it may, if there should be an occurrence of ad, huge
information abuse may welcome new sorts of assault vectors.
Question 5
To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or Why
not?
According to the ENISA Big Data there are few focuses on the security framework:
For the application level to the system convention the trusted segments might
dependably be utilized as a part of all levels of the data framework, which are
generally in view of the key administration and the most grounded strategy to encode
(Karchefsky& Rao, 2017). A portion of the cases of this trusted foundation are secure
correspondence conventions, validation framework open key foundation parts and
some more.
It is fundamental for the association to claim a put stock in foundation, to such an
extent that to assemble the data security on the premise of the safety effort at each
level and along these lines giving the validation frameworks and accomplices with
confide in worth exchanges, association and electronic marks.
As the ENISA clarified, there would be an incredible potential effect on increment in
the grouping of information in distributed computing for the programmers, since there
is dependably a possibility for misuse of private and individual data. The digital
offenders regularly store malwares in the system framework or may utilize the stage
to dispatch an assault for their own benefit.
As a developing security issue huge information is on the highest priority on the
rundown as a broadly spreading outcome of distributed computing, social innovations
and other web memberships. This has turned into a recently developing security issue.
The information protection is mostly influenced by the abuse of this huge information
by unapproved clients. Be that as it may, if there should be an occurrence of ad, huge
information abuse may welcome new sorts of assault vectors.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13IT RISK MANAGEMENT
There are a few sorts of difficulties distinguishes in the security arrangement of Big Data.
These difficulties must need information security, control availability of information and
information sifting (Lykou, 2016). As said by the ENISA there are a few issues with respect
to colossal measure of information control that is past the preparing energy of items in
Security data and Event Management (SIEM).
Truly, ENISA be happy with its present territory of IT Security. There are holes in
information insurance because of the dangers and secrecy of sensor information streams. In
instances of character extortion, the movement caught and the Big Data examination helps in
encouraging the security interruption by fortifying the normal systems and on additionally
look into in the required fields. In year 2009 the ENISA has chosen to refresh and survey the
dangers and advantages for higher reflection to the present circumstance of the association. It
has been recognized that the fundamental hazard that is by utilizing distributed computing
has not changed but rather there has been a choice of reproducing the dangers having the
point of making the depictions much uniform (Lévy-Bencheton et al., 2015). There has been
a presentation of legitimate and information security parts of Big Data and distributed
computing. There is a continuation of checking the improvement identified with the dangers
and danger of distributed computing and as needs be refresh the Risk Assessment.
There are a few sorts of difficulties distinguishes in the security arrangement of Big Data.
These difficulties must need information security, control availability of information and
information sifting (Lykou, 2016). As said by the ENISA there are a few issues with respect
to colossal measure of information control that is past the preparing energy of items in
Security data and Event Management (SIEM).
Truly, ENISA be happy with its present territory of IT Security. There are holes in
information insurance because of the dangers and secrecy of sensor information streams. In
instances of character extortion, the movement caught and the Big Data examination helps in
encouraging the security interruption by fortifying the normal systems and on additionally
look into in the required fields. In year 2009 the ENISA has chosen to refresh and survey the
dangers and advantages for higher reflection to the present circumstance of the association. It
has been recognized that the fundamental hazard that is by utilizing distributed computing
has not changed but rather there has been a choice of reproducing the dangers having the
point of making the depictions much uniform (Lévy-Bencheton et al., 2015). There has been
a presentation of legitimate and information security parts of Big Data and distributed
computing. There is a continuation of checking the improvement identified with the dangers
and danger of distributed computing and as needs be refresh the Risk Assessment.

14IT RISK MANAGEMENT
Conclusion
This report goes for investigating the way that innovative headway for huge
information can meet and incorporate innovative progressions in security. This ought not be
considered as a comprehensive introduction of all accessible and conceivable strategies, but
instead as an endeavor to take this exchange a stage forward and to connect with every single
significant partner in a more humanistic information security driven investigation
improvement in Big Data.
Conclusion
This report goes for investigating the way that innovative headway for huge
information can meet and incorporate innovative progressions in security. This ought not be
considered as a comprehensive introduction of all accessible and conceivable strategies, but
instead as an endeavor to take this exchange a stage forward and to connect with every single
significant partner in a more humanistic information security driven investigation
improvement in Big Data.

15IT RISK MANAGEMENT
References
Barnard-Wills, D. (2014). ENISA Threat Landscape and Good Practice Guide for Smart
Home and Converged Media. ENISA (The European Network and Information
Security Agency).
Barnard-Wills, D., Marinos, L., &Portesi, S. (2014). Threat landscape and good practice
guide for smart home and converged media. European Union Agency for Network
and Information Security, ENISA.
Belmonte Martin, A., Marinos, L., Rekleitis, E., Spanoudakis, G., &Petroulakis, N. E. (2015).
Threat Landscape and Good Practice Guide for Software Defined Networks/5G.
Brender, N., & Markov, I. (2013). Risk perception and risk management in cloud computing:
Results from a case study of Swiss companies. International journal of information
management, 33(5), 726-733.
Bugeja, J., Jacobsson, A., &Davidsson, P. (2017, March). An analysis of malicious threat
agents for the smart connected home. In Pervasive Computing and Communications
Workshops (PerCom Workshops), 2017 IEEE International Conference on (pp. 557-
562). IEEE.
Cho, H., Yoon, K., Choi, S., & Kim, Y. M. (2016). Automatic Binary Execution
Environment based on Real-machines for Intelligent Malware Analysis. KIISE
Transactions on Computing Practices, 22(3), 139-144.
Gorton, D. (2015). IncidentResponseSim: An agent-based simulation tool for risk
management of online Fraud. In Secure IT Systems (pp. 172-187). Springer, Cham.
References
Barnard-Wills, D. (2014). ENISA Threat Landscape and Good Practice Guide for Smart
Home and Converged Media. ENISA (The European Network and Information
Security Agency).
Barnard-Wills, D., Marinos, L., &Portesi, S. (2014). Threat landscape and good practice
guide for smart home and converged media. European Union Agency for Network
and Information Security, ENISA.
Belmonte Martin, A., Marinos, L., Rekleitis, E., Spanoudakis, G., &Petroulakis, N. E. (2015).
Threat Landscape and Good Practice Guide for Software Defined Networks/5G.
Brender, N., & Markov, I. (2013). Risk perception and risk management in cloud computing:
Results from a case study of Swiss companies. International journal of information
management, 33(5), 726-733.
Bugeja, J., Jacobsson, A., &Davidsson, P. (2017, March). An analysis of malicious threat
agents for the smart connected home. In Pervasive Computing and Communications
Workshops (PerCom Workshops), 2017 IEEE International Conference on (pp. 557-
562). IEEE.
Cho, H., Yoon, K., Choi, S., & Kim, Y. M. (2016). Automatic Binary Execution
Environment based on Real-machines for Intelligent Malware Analysis. KIISE
Transactions on Computing Practices, 22(3), 139-144.
Gorton, D. (2015). IncidentResponseSim: An agent-based simulation tool for risk
management of online Fraud. In Secure IT Systems (pp. 172-187). Springer, Cham.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16IT RISK MANAGEMENT
Karchefsky, S., & Rao, H. R. (2017). Toward a Safer Tomorrow: Cybersecurity and Critical
Infrastructure. In The Palgrave Handbook of Managing Continuous Business
Transformation (pp. 335-352). Palgrave Macmillan UK.
Le Bray, Y., Mayer, N., &Aubert, J. (2016, April). Defining measurements for analyzing
information security risk reports in the telecommunications sector. In Proceedings of
the 31st Annual ACM Symposium on Applied Computing(pp. 2189-2194). ACM.
Lehto, M. (2015). Phenomena in the Cyber World. In Cyber Security: Analytics, Technology
and Automation (pp. 3-29). Springer International Publishing.
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., &Stumpf, J. (2015).
Threat landscape and good practice guide for internet infrastructure. Report, European
Union Agency for Network and Information Security (ENISA).
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., &Stumpf, J. (2015).
Threat landscape and good practice guide for internet infrastructure. Report, European
Union Agency for Network and Information Security (ENISA).
Lykou, G. (2016). Critical Infrastructure Protection: Protecting Public Welfare.
Marinos, L. (2013). ENISA Threat Landscape 2013: Overview of current and emerging
cyber-threats. Heraklion: European Union Agency for Network and Information
Security Publishing. doi, 10, 14231.
Marinos, L., Belmonte, A., &Rekleitis, E. (2014). ENISA Threat Landscape Report
2013. European Union Agency for Network and Information Security.
Marinos, L., Belmonte, A., &Rekleitis, E. (2014). ENISA Threat Landscape 2015. Heraklion,
Greece: ENISA. doi, 10, 061861.
Karchefsky, S., & Rao, H. R. (2017). Toward a Safer Tomorrow: Cybersecurity and Critical
Infrastructure. In The Palgrave Handbook of Managing Continuous Business
Transformation (pp. 335-352). Palgrave Macmillan UK.
Le Bray, Y., Mayer, N., &Aubert, J. (2016, April). Defining measurements for analyzing
information security risk reports in the telecommunications sector. In Proceedings of
the 31st Annual ACM Symposium on Applied Computing(pp. 2189-2194). ACM.
Lehto, M. (2015). Phenomena in the Cyber World. In Cyber Security: Analytics, Technology
and Automation (pp. 3-29). Springer International Publishing.
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., &Stumpf, J. (2015).
Threat landscape and good practice guide for internet infrastructure. Report, European
Union Agency for Network and Information Security (ENISA).
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., &Stumpf, J. (2015).
Threat landscape and good practice guide for internet infrastructure. Report, European
Union Agency for Network and Information Security (ENISA).
Lykou, G. (2016). Critical Infrastructure Protection: Protecting Public Welfare.
Marinos, L. (2013). ENISA Threat Landscape 2013: Overview of current and emerging
cyber-threats. Heraklion: European Union Agency for Network and Information
Security Publishing. doi, 10, 14231.
Marinos, L., Belmonte, A., &Rekleitis, E. (2014). ENISA Threat Landscape Report
2013. European Union Agency for Network and Information Security.
Marinos, L., Belmonte, A., &Rekleitis, E. (2014). ENISA Threat Landscape 2015. Heraklion,
Greece: ENISA. doi, 10, 061861.

17IT RISK MANAGEMENT
Olesen, N. (2016). European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting
Cybercrime and Cyberterrorism (pp. 259-278). Springer International Publishing.
Rhee, K., Won, D., Jang, S. W., Chae, S., & Park, S. (2013). Threat modeling of a mobile
device management system for secure smart work. Electronic Commerce
Research, 13(3), 243-256.
Scott, K. (2016, November). Phobic Cartography: a Human-Centred, Communicative
Analysis of the Cyber Threat Landscape.
Wang, Y., Anokhin, O., &Anderl, R. (2017). Concept and use Case Driven Approach for
Mapping IT Security Requirements on System Assets and Processes in Industrie
4.0. Procedia CIRP, 63, 207-212.
Olesen, N. (2016). European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting
Cybercrime and Cyberterrorism (pp. 259-278). Springer International Publishing.
Rhee, K., Won, D., Jang, S. W., Chae, S., & Park, S. (2013). Threat modeling of a mobile
device management system for secure smart work. Electronic Commerce
Research, 13(3), 243-256.
Scott, K. (2016, November). Phobic Cartography: a Human-Centred, Communicative
Analysis of the Cyber Threat Landscape.
Wang, Y., Anokhin, O., &Anderl, R. (2017). Concept and use Case Driven Approach for
Mapping IT Security Requirements on System Assets and Processes in Industrie
4.0. Procedia CIRP, 63, 207-212.
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





