Comprehensive Analysis of IT Risk Management in Big Data Applications
VerifiedAdded on 2020/02/19
|13
|3398
|75
Report
AI Summary
This report analyzes IT risk management within the context of big data applications, focusing on the European Union Agency for Network and Information Security (ENISA)'s role in assessing and mitigating threats. It explores the advantages and disadvantages of big data, highlighting privacy and security risks such as information leakage, web application vulnerabilities, and conflicts among stakeholders. The report identifies various threat agents, including corporations, cybercriminals, and nation-states, and examines the ETL process. It emphasizes the need for improved countermeasures, including defining major data problems, identifying gaps in current practices, investing in IT professional training, and developing tools to measure security and privacy. The report concludes with a discussion on the importance of proactive measures to protect big data environments.

Running head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of Student
Name of University
Author’s Note
IT RISK MANAGEMENT
Name of Student
Name of University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
1. This assignment is the analysis on the big data applications threats and the mentioned
ways which is taken by the company to minimize the threats of the big data. The given
assignment discusses about an organization known as the European Union Agency for Network
and Information Security (ENISA) which has been the network center and working in the
Information technology field to study the threat which can compromise the security of any nation
(Kimwele, 2014).. The ENISA also assists the European nation body’s members regarding the
improving network and its securities of the Information technology field. The big data concept
which is the collection of the wide data which is both complex and not understandable the main
purpose of big data is to draw some meaningful pattern or the algorithm from these data which
will help them to study and analyze how a customer is performing various activities like
shopping and accounting transaction. The source of the big data can come from anywhere be it a
bank or hospitals(Kitchin, 2014). The data entered in these organizations is the big data which is
utilized by the company. Various companies have reported that the application of the big data
has helped them in understanding their customers and take proper decision according to the
situation. Thus the big data application is not going to rise in the coming days and used in all the
sectors of the company for doing business. The big data has application in the government sector
which includes the military and the intelligence system. Despite of all the advantage of the big
data the article enlists varies limitation and drawbacks of using big data. Though the big data has
huge application it also has privacy and security threat to the country and the company. There are
various threats related to the big data some of them are:
The usage of the big data has not only put the ordinary and common data at risk but also
the private and the confidential data at the risk(Walker 2014). The high replication and the
1. This assignment is the analysis on the big data applications threats and the mentioned
ways which is taken by the company to minimize the threats of the big data. The given
assignment discusses about an organization known as the European Union Agency for Network
and Information Security (ENISA) which has been the network center and working in the
Information technology field to study the threat which can compromise the security of any nation
(Kimwele, 2014).. The ENISA also assists the European nation body’s members regarding the
improving network and its securities of the Information technology field. The big data concept
which is the collection of the wide data which is both complex and not understandable the main
purpose of big data is to draw some meaningful pattern or the algorithm from these data which
will help them to study and analyze how a customer is performing various activities like
shopping and accounting transaction. The source of the big data can come from anywhere be it a
bank or hospitals(Kitchin, 2014). The data entered in these organizations is the big data which is
utilized by the company. Various companies have reported that the application of the big data
has helped them in understanding their customers and take proper decision according to the
situation. Thus the big data application is not going to rise in the coming days and used in all the
sectors of the company for doing business. The big data has application in the government sector
which includes the military and the intelligence system. Despite of all the advantage of the big
data the article enlists varies limitation and drawbacks of using big data. Though the big data has
huge application it also has privacy and security threat to the country and the company. There are
various threats related to the big data some of them are:
The usage of the big data has not only put the ordinary and common data at risk but also
the private and the confidential data at the risk(Walker 2014). The high replication and the

2IT RISK MANAGEMENT
outsourcing of the big data are the new type of the ways which has resulted in breaching and the
leakage of the data.
The big data usage has posed the threat to the privacy of the people which has
compromised the security of the data. At the time of creation of the link in the case of the big
data the collection of the big data is the major cause of the penalization the extra creation of the
link is the major cause of the leakage of the information and data.
The stake holders in the big data such as the data owners or the data transformers or the
data providers differ in their view about the usage and security of the data their idea may conflict
which make it a difficult environment for them to operate and devise a proper security plan for
the data which compromise the security of the data.
Lastly in various sectors of the information and communication technology (ICT).
Different professionals are trying to apply their own privacy and security laws which are best
according to them but on the overall security of the data it significantly decreases(Halenar,
2012). The big data rising pattern is embracing the Security-by-default principle though it is still
in the early stage it has proved to be quite beneficial and highly practical in compare to the cost
and effort in the invested in the ad hoc solution at the later time.
The given assignment later focuses that there has been the huge gap between the issues of the
big data and the counter measures designed to tackle the problems of the big data(Kayworth &
Whitten, 2012). Analyzing the gap the assignment has enlisted some of its own counter measure
which can solve the limitation of the big data. The assignment further raises a valid question
regarding current trend of the countermeasures for adapting the existing solutions which can be
used against the current trends of the countermeasures for adapting the solution which is against
outsourcing of the big data are the new type of the ways which has resulted in breaching and the
leakage of the data.
The big data usage has posed the threat to the privacy of the people which has
compromised the security of the data. At the time of creation of the link in the case of the big
data the collection of the big data is the major cause of the penalization the extra creation of the
link is the major cause of the leakage of the information and data.
The stake holders in the big data such as the data owners or the data transformers or the
data providers differ in their view about the usage and security of the data their idea may conflict
which make it a difficult environment for them to operate and devise a proper security plan for
the data which compromise the security of the data.
Lastly in various sectors of the information and communication technology (ICT).
Different professionals are trying to apply their own privacy and security laws which are best
according to them but on the overall security of the data it significantly decreases(Halenar,
2012). The big data rising pattern is embracing the Security-by-default principle though it is still
in the early stage it has proved to be quite beneficial and highly practical in compare to the cost
and effort in the invested in the ad hoc solution at the later time.
The given assignment later focuses that there has been the huge gap between the issues of the
big data and the counter measures designed to tackle the problems of the big data(Kayworth &
Whitten, 2012). Analyzing the gap the assignment has enlisted some of its own counter measure
which can solve the limitation of the big data. The assignment further raises a valid question
regarding current trend of the countermeasures for adapting the existing solutions which can be
used against the current trends of the countermeasures for adapting the solution which is against
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
the traditional data threats. The current environment of the big data is currently focused on the
amount of the big data. The countermeasures which is currently existing is has been devised to
counter the scalabilities of the big data which does not fit the big data problems which results in
the partial and ineffective approach to the protection of the big data(Chen & Zhang, 2014). The
given assignment enlists some of its own guidelines and the countermeasures for the next
generation of the data. These are:
Firstly it tells to stop following the existing approach to the traditional data and work in
defining the major data problems.
Secondly it tells to identify the gaps and find the required needs for the current practices
and to work in planning the specific definition and the specific standardization activities.
Thirdly it tells to invest in training and teaching the IT professionals about the big data
and aware them about the correct measures of usage of the big data(O’Driscoll,
Daugelaite & Sleator, 2013).
Fourthly it tells to work in defining the correct tools and to measure the security and
privacy for the for the protection of Big Data and it environments.
Fifthly it tells to analyze and find the assets to the big data and accordingly select the
solutions which have minimal risk and threats.
the traditional data threats. The current environment of the big data is currently focused on the
amount of the big data. The countermeasures which is currently existing is has been devised to
counter the scalabilities of the big data which does not fit the big data problems which results in
the partial and ineffective approach to the protection of the big data(Chen & Zhang, 2014). The
given assignment enlists some of its own guidelines and the countermeasures for the next
generation of the data. These are:
Firstly it tells to stop following the existing approach to the traditional data and work in
defining the major data problems.
Secondly it tells to identify the gaps and find the required needs for the current practices
and to work in planning the specific definition and the specific standardization activities.
Thirdly it tells to invest in training and teaching the IT professionals about the big data
and aware them about the correct measures of usage of the big data(O’Driscoll,
Daugelaite & Sleator, 2013).
Fourthly it tells to work in defining the correct tools and to measure the security and
privacy for the for the protection of Big Data and it environments.
Fifthly it tells to analyze and find the assets to the big data and accordingly select the
solutions which have minimal risk and threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
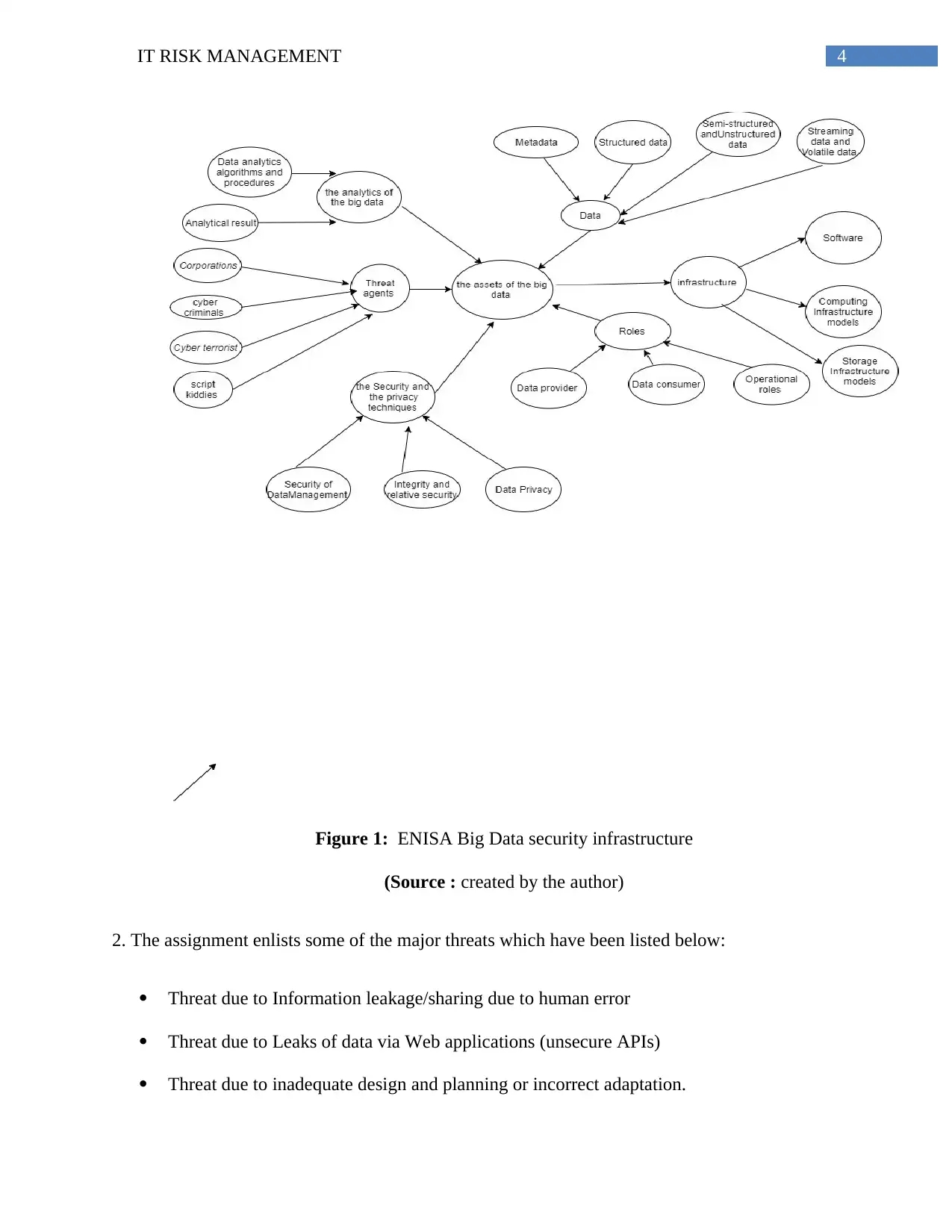
4IT RISK MANAGEMENT
Figure 1: ENISA Big Data security infrastructure
(Source : created by the author)
2. The assignment enlists some of the major threats which have been listed below:
Threat due to Information leakage/sharing due to human error
Threat due to Leaks of data via Web applications (unsecure APIs)
Threat due to inadequate design and planning or incorrect adaptation.
Figure 1: ENISA Big Data security infrastructure
(Source : created by the author)
2. The assignment enlists some of the major threats which have been listed below:
Threat due to Information leakage/sharing due to human error
Threat due to Leaks of data via Web applications (unsecure APIs)
Threat due to inadequate design and planning or incorrect adaptation.

5IT RISK MANAGEMENT
Threat due to inception of the information.
Threat: Violation of laws or regulations / Breach of legislation / Abuse of personal data
Threat: Failures of business process
Above all the enlisted major threats the threat due to Leaks of data via Web applications
(unsecure APIs) can be listed as the significant threat above all major threat(Labrinidis &
Jagadish, 2012). All other threat is due to the negligence of the human activity or failure in
protecting the data. These major threats can be controlled by employing the correct person but
the second major threat is due to the but the breaching of the data due to Web applications
(unsecure APIs) is the breach which can take place due to the software which do not have
enough capability to protect the data. According to the assignment various user of the big data
has claimed that the security is the least concern for them while using the big data. The new
software component designed for the big data is generally with the service-level authorization,
but there are few utilities which is available to protect the core features and application interfaces
(APIs). The big data are designed on the web service models. The application interfaces (APIs)
has become main target for all the cyber attack like in the case of like the Open Web Application
Security Project (OWASP) which comes in the list of top ten and there are few solutions which
can be used to stop them. The security software vendor Computer Associate (CA) and various
other related sources find out via report that the data breaches are due to not a secure application
interfaces (APIs) the social networks which includes the yahoo ,face book and snap chat and also
in various photo and video sharing apps(Crossler et al 2012). The given assignment also gives
the example of the Semantic Web technologies through its injection of its SPARQL code. It says
that the flaw in the big data security is common and in the newly available languages like RDQL
and the SPARQL where both are read-only query languages. There utilization has introduces a
Threat due to inception of the information.
Threat: Violation of laws or regulations / Breach of legislation / Abuse of personal data
Threat: Failures of business process
Above all the enlisted major threats the threat due to Leaks of data via Web applications
(unsecure APIs) can be listed as the significant threat above all major threat(Labrinidis &
Jagadish, 2012). All other threat is due to the negligence of the human activity or failure in
protecting the data. These major threats can be controlled by employing the correct person but
the second major threat is due to the but the breaching of the data due to Web applications
(unsecure APIs) is the breach which can take place due to the software which do not have
enough capability to protect the data. According to the assignment various user of the big data
has claimed that the security is the least concern for them while using the big data. The new
software component designed for the big data is generally with the service-level authorization,
but there are few utilities which is available to protect the core features and application interfaces
(APIs). The big data are designed on the web service models. The application interfaces (APIs)
has become main target for all the cyber attack like in the case of like the Open Web Application
Security Project (OWASP) which comes in the list of top ten and there are few solutions which
can be used to stop them. The security software vendor Computer Associate (CA) and various
other related sources find out via report that the data breaches are due to not a secure application
interfaces (APIs) the social networks which includes the yahoo ,face book and snap chat and also
in various photo and video sharing apps(Crossler et al 2012). The given assignment also gives
the example of the Semantic Web technologies through its injection of its SPARQL code. It says
that the flaw in the big data security is common and in the newly available languages like RDQL
and the SPARQL where both are read-only query languages. There utilization has introduces a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT RISK MANAGEMENT
new vulnerabilities in the big data which was already present in the flaw of old-style query
languages. The misuse of the languages is well aware and is dangerous for the usage. The
collection of these new languages has already given the tool to check the user and minimize the
risk. There are other big data software products for an example Monod, Hive and Couched who
also suffers from the traditional threats which includes the execution of the code and the remote
SQL injection(Provost & Fawcett, 2013). The assets targeted by these threats belong to group
“Data” and asset type “Storage Infrastructure models” (such as “Database management systems
(DBS)” and “Semantic Web tools”).
3. The threat agent is a person or organization who has the capability and clear intention to
plant threats related to certain application like the big data and use them to spread cyber
terrorism. Therefore it is crucial for the user to be well aware about the threats and to stay away
from them as far as possible. Some of the threat agents are:
Corporations: the cooperation category comes under the company which is involved in
the offensive tactics. The cooperation is considered to be the threat agents as this cooperation
spreads the cyber terrorism to gain the competitive advantage in the market by attacking its rival
companies(Singh & Khaira, 2013).Depending upon the cooperation’s market power and its
sector the corporations generally acquires significant capabilities which can range from the singe
technology up to human engineering intelligence, especially in their area of expertise.
Cyber criminals: the cyber criminals are the threat agent who spreads the virus online
and hack and breach the organization data for the financial reason. They hack into the companies
data and steal the private and the confidential data to demand the ransomed from the company to
give back the data like the winery ransomwae attack in the year 2017.
new vulnerabilities in the big data which was already present in the flaw of old-style query
languages. The misuse of the languages is well aware and is dangerous for the usage. The
collection of these new languages has already given the tool to check the user and minimize the
risk. There are other big data software products for an example Monod, Hive and Couched who
also suffers from the traditional threats which includes the execution of the code and the remote
SQL injection(Provost & Fawcett, 2013). The assets targeted by these threats belong to group
“Data” and asset type “Storage Infrastructure models” (such as “Database management systems
(DBS)” and “Semantic Web tools”).
3. The threat agent is a person or organization who has the capability and clear intention to
plant threats related to certain application like the big data and use them to spread cyber
terrorism. Therefore it is crucial for the user to be well aware about the threats and to stay away
from them as far as possible. Some of the threat agents are:
Corporations: the cooperation category comes under the company which is involved in
the offensive tactics. The cooperation is considered to be the threat agents as this cooperation
spreads the cyber terrorism to gain the competitive advantage in the market by attacking its rival
companies(Singh & Khaira, 2013).Depending upon the cooperation’s market power and its
sector the corporations generally acquires significant capabilities which can range from the singe
technology up to human engineering intelligence, especially in their area of expertise.
Cyber criminals: the cyber criminals are the threat agent who spreads the virus online
and hack and breach the organization data for the financial reason. They hack into the companies
data and steal the private and the confidential data to demand the ransomed from the company to
give back the data like the winery ransomwae attack in the year 2017.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
Cyber terrorist: The difference between the cyber criminals and the terrorist that their
demand above the financial reason. They want to destabilize the country’s political, social and
religious base and spread terror in the country. They operate at the international level and spread
the hatred message online to provoke the people.
Online social hackers (activists): The social hackers are the threat agents mainly target
the children and girls and torture them mentally promoting the cyber bully machines (Al-Aqrabi
et al 2012).
Script kiddies: they are basically unskilled or incapable hackers who use the programme
and scripts of the hackers to hack the computer system.
Employees: This category of the threat agent includes the employees who works for the
particular organization and have access to the data of the company. They can be the security
guards or the data operation manager.
Nation states: Nation state is the rising threat which has become prominent in the recent
times. Threat agent due to the deployment of sophisticated attacks that are considered as cyber
weapons through the capability of these malware
The above described threat agents are responsible for all the cybercrimes in the nation. In
order to be protected from these threat agents. People should disclose their private information
like photo or any private information. The hackers utilize this information to target these people
and mentally torture them for the money. . Secondly the company needs to keep tab on their
employees of their activities against and stealing of the data.
Cyber terrorist: The difference between the cyber criminals and the terrorist that their
demand above the financial reason. They want to destabilize the country’s political, social and
religious base and spread terror in the country. They operate at the international level and spread
the hatred message online to provoke the people.
Online social hackers (activists): The social hackers are the threat agents mainly target
the children and girls and torture them mentally promoting the cyber bully machines (Al-Aqrabi
et al 2012).
Script kiddies: they are basically unskilled or incapable hackers who use the programme
and scripts of the hackers to hack the computer system.
Employees: This category of the threat agent includes the employees who works for the
particular organization and have access to the data of the company. They can be the security
guards or the data operation manager.
Nation states: Nation state is the rising threat which has become prominent in the recent
times. Threat agent due to the deployment of sophisticated attacks that are considered as cyber
weapons through the capability of these malware
The above described threat agents are responsible for all the cybercrimes in the nation. In
order to be protected from these threat agents. People should disclose their private information
like photo or any private information. The hackers utilize this information to target these people
and mentally torture them for the money. . Secondly the company needs to keep tab on their
employees of their activities against and stealing of the data.

8IT RISK MANAGEMENT
4. The ETL is full form is extraction, transformation, and loading. It is defined as the stages
from the data is extracted from the desired location to the data is transformed into the desired
target and finally to the loading where the data is loaded to deliver to the desired
destination(Ackermann, 2012). According to the target requirement and last phase is the loading
phase it is the phase in which the data is loaded into its warehouse and ready for the delivery.
For the better performance of the ETL various steps are enlisted:
Loading the data incrementally: for the better and efficient access of the data. The data
should be arranged into certain pattern which can be increasing or decreasing according to the
user demands this will help in better management of the data and it will to find the record
afterward as the user will remember the pattern.
The partition of the large tables: For better and efficient access to the data the large data
table are divide into the smaller table so that data of the table can be easily seen ad be accessed.
It will also it will help in quicker and efficient access of the data. It will allow easier switching of
the data and quick insertion, deletion and updating of the table.
Cutting out the extra data: another way the data can be simplified by cutting and
eliminating the unwanted data. The data table should be regularly analyzed and the extra data
should be eliminated for efficient access to the data.
Usage of the software: there is software available in the market which can be used to
simplify the work of reducing the data. The software can be the hardtop. It uses the HDFS
application which segments data into the small part and make them into simple cluster. The data
which is duplicated through which the system maintains the integrity automatically.
4. The ETL is full form is extraction, transformation, and loading. It is defined as the stages
from the data is extracted from the desired location to the data is transformed into the desired
target and finally to the loading where the data is loaded to deliver to the desired
destination(Ackermann, 2012). According to the target requirement and last phase is the loading
phase it is the phase in which the data is loaded into its warehouse and ready for the delivery.
For the better performance of the ETL various steps are enlisted:
Loading the data incrementally: for the better and efficient access of the data. The data
should be arranged into certain pattern which can be increasing or decreasing according to the
user demands this will help in better management of the data and it will to find the record
afterward as the user will remember the pattern.
The partition of the large tables: For better and efficient access to the data the large data
table are divide into the smaller table so that data of the table can be easily seen ad be accessed.
It will also it will help in quicker and efficient access of the data. It will allow easier switching of
the data and quick insertion, deletion and updating of the table.
Cutting out the extra data: another way the data can be simplified by cutting and
eliminating the unwanted data. The data table should be regularly analyzed and the extra data
should be eliminated for efficient access to the data.
Usage of the software: there is software available in the market which can be used to
simplify the work of reducing the data. The software can be the hardtop. It uses the HDFS
application which segments data into the small part and make them into simple cluster. The data
which is duplicated through which the system maintains the integrity automatically.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
5. The given assignment discusses about an organization known as the European Union
Agency for Network and Information Security (ENISA) which has been the network center and
working in the Information technology field to study the threat which can compromise the
security of any nation (Ackermann et al 2012). It enlists the securities which include the usage
of the big data which are not only the original data but the confidential data which are at risk as
with the high replication of the big data for the purpose of storage and the outsourcing of the big
data these type of the technology are new ways of the breaching and the leakage of the data.
Secondly the big data are posing threat to the privacy of the individual which has the impact on
the data protection. The given assignment later focuses that there has been the huge gap between
the issues of the big data and the counter measures designed to tackle the problems of the big
data. Analyzing the gap the assignment has enlisted some of its own counter measure which can
solve the limitation of the big data. The assignment further raises a valid question regarding
current trend of the countermeasures for adapting the existing solutions which can be used
against the current trends. The assignment also enlists 5 major threats related to the data mining.
The assignment also enlists threat agent such as cooperation, people, cybercrime which spreads
the online hacking. Thus it can be conclude that the organization is not happy with the current
security of the big data and it also recommended various countermeasures from its own side
what can be done to prevent the misuses of the big data.
5. The given assignment discusses about an organization known as the European Union
Agency for Network and Information Security (ENISA) which has been the network center and
working in the Information technology field to study the threat which can compromise the
security of any nation (Ackermann et al 2012). It enlists the securities which include the usage
of the big data which are not only the original data but the confidential data which are at risk as
with the high replication of the big data for the purpose of storage and the outsourcing of the big
data these type of the technology are new ways of the breaching and the leakage of the data.
Secondly the big data are posing threat to the privacy of the individual which has the impact on
the data protection. The given assignment later focuses that there has been the huge gap between
the issues of the big data and the counter measures designed to tackle the problems of the big
data. Analyzing the gap the assignment has enlisted some of its own counter measure which can
solve the limitation of the big data. The assignment further raises a valid question regarding
current trend of the countermeasures for adapting the existing solutions which can be used
against the current trends. The assignment also enlists 5 major threats related to the data mining.
The assignment also enlists threat agent such as cooperation, people, cybercrime which spreads
the online hacking. Thus it can be conclude that the organization is not happy with the current
security of the big data and it also recommended various countermeasures from its own side
what can be done to prevent the misuses of the big data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RISK MANAGEMENT
References
Ackermann, T. (2012). IT security risk management: perceived IT security risks in the context of
Cloud Computing. Springer Science & Business Media.
Ackermann, T., Widjaja, T., Benlian, A., & Buxmann, P. (2012). Perceived IT security risks of
cloud computing: Conceptualization and scale development.
Al-Aqrabi, H., Liu, L., Xu, J., Hill, R., Antonopoulos, N., & Zhan, Y. (2012, April).
Investigation of IT security and compliance challenges in Security-as-a-Service for Cloud
Computing. In Object/Component/Service-Oriented Real-Time Distributed Computing
Workshops (ISORCW), 2012 15th IEEE International Symposium on (pp. 124-129).
IEEE.
Amanpartap Singh, P. A. L. L., & Khaira, J. S. (2013). A comparative review of extraction,
transformation and loading tools. Database Systems Journal BOARD, 42.
Boyd, D., & Crawford, K. (2012). Critical questions for big data: Provocations for a cultural,
technological, and scholarly phenomenon. Information, communication & society, 15(5),
662-679.
Chen, C. P., & Zhang, C. Y. (2014). Data-intensive applications, challenges, techniques and
technologies: A survey on Big Data. Information Sciences, 275, 314-347.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R. (2013).
Future directions for behavioral information security research. computers & security, 32,
90-101.
References
Ackermann, T. (2012). IT security risk management: perceived IT security risks in the context of
Cloud Computing. Springer Science & Business Media.
Ackermann, T., Widjaja, T., Benlian, A., & Buxmann, P. (2012). Perceived IT security risks of
cloud computing: Conceptualization and scale development.
Al-Aqrabi, H., Liu, L., Xu, J., Hill, R., Antonopoulos, N., & Zhan, Y. (2012, April).
Investigation of IT security and compliance challenges in Security-as-a-Service for Cloud
Computing. In Object/Component/Service-Oriented Real-Time Distributed Computing
Workshops (ISORCW), 2012 15th IEEE International Symposium on (pp. 124-129).
IEEE.
Amanpartap Singh, P. A. L. L., & Khaira, J. S. (2013). A comparative review of extraction,
transformation and loading tools. Database Systems Journal BOARD, 42.
Boyd, D., & Crawford, K. (2012). Critical questions for big data: Provocations for a cultural,
technological, and scholarly phenomenon. Information, communication & society, 15(5),
662-679.
Chen, C. P., & Zhang, C. Y. (2014). Data-intensive applications, challenges, techniques and
technologies: A survey on Big Data. Information Sciences, 275, 314-347.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R. (2013).
Future directions for behavioral information security research. computers & security, 32,
90-101.

11IT RISK MANAGEMENT
Halenar, R. (2012). Real Time ETL Improvement. International Journal of Computer Theory
and Engineering, 4(3), 405
John Walker, S. (2014). Big data: A revolution that will transform how we live, work, and think.
Kayworth, T., & Whitten, D. (2012). Effective information security requires a balance of social
and technology factors.
Kimwele, M. W. (2014). Information technology (IT) security in small and medium enterprises
(SMEs). In Information Systems for Small and Medium-sized Enterprises (pp. 47-64).
Springer Berlin Heidelberg.
Kitchin, R. (2014). The data revolution: Big data, open data, data infrastructures and their
consequences. Sage.
Labrinidis, A., & Jagadish, H. V. (2012). Challenges and opportunities with big
data. Proceedings of the VLDB Endowment, 5(12), 2032-2033.
Loske, A., Widjaja, T., & Buxmann, P. (2013). Cloud Computing Providers’ Unrealistic
Optimism regarding IT Security Risks: A Threat to Users?.
McAfee, A., Brynjolfsson, E., & Davenport, T. H. (2012). Big data: the management
revolution. Harvard business review, 90(10), 60-68.
O’Driscoll, A., Daugelaite, J., & Sleator, R. D. (2013). ‘Big data’, Hadoop and cloud computing
in genomics. Journal of biomedical informatics, 46(5), 774-781.
Provost, F., & Fawcett, T. (2013). Data science and its relationship to big data and data-driven
decision making. Big Data, 1(1), 51-59.
Halenar, R. (2012). Real Time ETL Improvement. International Journal of Computer Theory
and Engineering, 4(3), 405
John Walker, S. (2014). Big data: A revolution that will transform how we live, work, and think.
Kayworth, T., & Whitten, D. (2012). Effective information security requires a balance of social
and technology factors.
Kimwele, M. W. (2014). Information technology (IT) security in small and medium enterprises
(SMEs). In Information Systems for Small and Medium-sized Enterprises (pp. 47-64).
Springer Berlin Heidelberg.
Kitchin, R. (2014). The data revolution: Big data, open data, data infrastructures and their
consequences. Sage.
Labrinidis, A., & Jagadish, H. V. (2012). Challenges and opportunities with big
data. Proceedings of the VLDB Endowment, 5(12), 2032-2033.
Loske, A., Widjaja, T., & Buxmann, P. (2013). Cloud Computing Providers’ Unrealistic
Optimism regarding IT Security Risks: A Threat to Users?.
McAfee, A., Brynjolfsson, E., & Davenport, T. H. (2012). Big data: the management
revolution. Harvard business review, 90(10), 60-68.
O’Driscoll, A., Daugelaite, J., & Sleator, R. D. (2013). ‘Big data’, Hadoop and cloud computing
in genomics. Journal of biomedical informatics, 46(5), 774-781.
Provost, F., & Fawcett, T. (2013). Data science and its relationship to big data and data-driven
decision making. Big Data, 1(1), 51-59.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





