Information Technology Software Upgrade Project Proposal, 2018
VerifiedAdded on 2023/05/29
|14
|2698
|68
Project
AI Summary
This document is a project proposal for a software upgrade from Windows XP to Windows 2016 for a single operator business. It outlines the project background, scope, high-level requirements, deliverables, and affected parties. The proposal details risk identification and mitigation strategies, specific exclusions from the project's scope, and a phased implementation plan. It includes a high-level budget and timeline, estimated using a bottom-up approach. The proposal covers various aspects of project management, including risk assessment, and provides a comprehensive overview of the project's objectives and execution strategy. The project aims to upgrade 500 desktops and laptops, and the document includes details on deliverables, milestones, and potential risks associated with the upgrade process. The implementation will be carried out in phases, and the proposal considers the impact on various stakeholders, including employees, customers, and competitors. The project is expected to be completed in 101 days, with a dedicated project team managing the upgrade process. The proposal also includes a risk management plan to address potential technical, security, and compatibility issues.
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Information Technology – Software Upgrade
Project Proposal
11/20/2018
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmqwertyuiopasdfghjkl
zxcvbnmqwertyuiopasdfghjklzxc
vbnmqwertyuiopasdfghjklzxcvb
nmqwertyuiopasdfghjklzxcvbnm
qwertyuiopasdfghjklzxcvbnmqw
ertyuiopasdfghjklzxcvbnmqwert
yuiopasdfghjklzxcvbnmqwertyui
opasdfghjklzxcvbnmqwertyuiop
asdfghjklzxcvbnmqwertyuiopasd
fghjklzxcvbnmqwertyuiopasdfgh
jklzxcvbnmrtyuiopasdfghjklzxcv
Information Technology – Software Upgrade
Project Proposal
11/20/2018
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Proposal
Table of Contents
Overview...............................................................................................................................................3
Project Background & Description........................................................................................................3
Project Scope.........................................................................................................................................3
High-Level Requirements......................................................................................................................4
Deliverables & Milestones....................................................................................................................4
Affected Parties.....................................................................................................................................5
Risk Identification & Strategy...............................................................................................................6
Specific Exclusions from Scope............................................................................................................8
Implementation Plan..............................................................................................................................9
High-Level Budget and Timeline/Schedule...........................................................................................9
References...........................................................................................................................................13
1
Table of Contents
Overview...............................................................................................................................................3
Project Background & Description........................................................................................................3
Project Scope.........................................................................................................................................3
High-Level Requirements......................................................................................................................4
Deliverables & Milestones....................................................................................................................4
Affected Parties.....................................................................................................................................5
Risk Identification & Strategy...............................................................................................................6
Specific Exclusions from Scope............................................................................................................8
Implementation Plan..............................................................................................................................9
High-Level Budget and Timeline/Schedule...........................................................................................9
References...........................................................................................................................................13
1

Project Proposal
2
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Proposal
Overview
The project is the information technology project that involves the software upgrade for a
single operator business. The upgrade is to be done for 500 desktops and laptops from current
operating system as Windows XP to the desired operating systems as Windows 2016. The
document is a project proposal that provides the project details and highlights and also covers
the managerial aspect of the project. The project has been proposed as the software upgrade
will allow the business firm to implement advanced operating system with better technical
and security features.
Project Background & Description
The project is being carried out for a single operator business and it includes the software
upgrade for 500 desktops and laptops that are installed in the enterprise. The current
operating system installed in the systems is Windows XP and the upgrade will be done to
Windows 2016.
The project will be completed in the estimated duration as 101 days starting from 20th
November 2018 and ending on 9th April 2019. The project will be headed by the Project
Manager and will involve additional resources as Technical Expert, System Engineer,
Business Analyst, Database Administrator, Technical Writer, System Tester, Third-Party
Trainer, Network Engineer, and Implementation Analyst.
Project Scope
The project will be carried out in a series of phases and the project scope will be expanded to
five phases.
The members of the project team will carry out the feasibility analysis for the proposed
project of software upgrade and the chartering of the project will be done. The technical
infrastructure analysis and environment analysis will be conducted in the second phase along
with the planning of the project in the areas as scope, schedule, costs, resources,
communication, risks, quality, and procurement. The set up for Windows 2016 operating
system and its installation in the desktops and laptops will be done in the third phase
(Wearne, 2014). The data sets and services from the current system will be migrated to the
new system along with the integration with the other applications. The project scope will
3
Overview
The project is the information technology project that involves the software upgrade for a
single operator business. The upgrade is to be done for 500 desktops and laptops from current
operating system as Windows XP to the desired operating systems as Windows 2016. The
document is a project proposal that provides the project details and highlights and also covers
the managerial aspect of the project. The project has been proposed as the software upgrade
will allow the business firm to implement advanced operating system with better technical
and security features.
Project Background & Description
The project is being carried out for a single operator business and it includes the software
upgrade for 500 desktops and laptops that are installed in the enterprise. The current
operating system installed in the systems is Windows XP and the upgrade will be done to
Windows 2016.
The project will be completed in the estimated duration as 101 days starting from 20th
November 2018 and ending on 9th April 2019. The project will be headed by the Project
Manager and will involve additional resources as Technical Expert, System Engineer,
Business Analyst, Database Administrator, Technical Writer, System Tester, Third-Party
Trainer, Network Engineer, and Implementation Analyst.
Project Scope
The project will be carried out in a series of phases and the project scope will be expanded to
five phases.
The members of the project team will carry out the feasibility analysis for the proposed
project of software upgrade and the chartering of the project will be done. The technical
infrastructure analysis and environment analysis will be conducted in the second phase along
with the planning of the project in the areas as scope, schedule, costs, resources,
communication, risks, quality, and procurement. The set up for Windows 2016 operating
system and its installation in the desktops and laptops will be done in the third phase
(Wearne, 2014). The data sets and services from the current system will be migrated to the
new system along with the integration with the other applications. The project scope will
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Proposal
include the testing of the installed operating system on the functional, performance, and
security aspects. The implementation, reviews, and management of the changes will be
included in the scope. The last phase will be the closure phase in which the acceptance of
deliverables will be carried out along with the project documentation and feedback
(Atkinson, Crawford & Ward, 2006).
High-Level Requirements
The high-level requirements of the project are listed below:
The software upgrade from Windows XP to Windows 2016 shall allow the users to
access the newly installed software. The user access control and permissions shall be
re-set and granted as per the user roles.
The migration of the data sets from the existing to the new system shall be done
making sure that the data integrity, security, and privacy is not impacted at any
instance.
The migration of the services from the existing to the new system shall be done
making sure that the service performance, access integrity, security, and privacy is not
impacted at any instance (Gushchin, 2013).
The newly installed software must be integrated with the business tools and
applications being used in the enterprise.
The software upgrade shall be done such that the reliability and accessibility of the
system is maintained.
There shall be no technical faults and failures after the installation and upgrade
process.
Deliverables & Milestones
The following deliverables shall be provided to the sponsor and the project stakeholders by
the members of the project team.
Project Statement of Work (SoW), Proposal, and Charter: These deliverables must be
provided in the initiation phase of the project and shall comprise of the high-level
details of the project. The purpose of the project along with the high-level budget,
schedule, scope, and requirements must be provided to the sponsor through these
deliverables.
4
include the testing of the installed operating system on the functional, performance, and
security aspects. The implementation, reviews, and management of the changes will be
included in the scope. The last phase will be the closure phase in which the acceptance of
deliverables will be carried out along with the project documentation and feedback
(Atkinson, Crawford & Ward, 2006).
High-Level Requirements
The high-level requirements of the project are listed below:
The software upgrade from Windows XP to Windows 2016 shall allow the users to
access the newly installed software. The user access control and permissions shall be
re-set and granted as per the user roles.
The migration of the data sets from the existing to the new system shall be done
making sure that the data integrity, security, and privacy is not impacted at any
instance.
The migration of the services from the existing to the new system shall be done
making sure that the service performance, access integrity, security, and privacy is not
impacted at any instance (Gushchin, 2013).
The newly installed software must be integrated with the business tools and
applications being used in the enterprise.
The software upgrade shall be done such that the reliability and accessibility of the
system is maintained.
There shall be no technical faults and failures after the installation and upgrade
process.
Deliverables & Milestones
The following deliverables shall be provided to the sponsor and the project stakeholders by
the members of the project team.
Project Statement of Work (SoW), Proposal, and Charter: These deliverables must be
provided in the initiation phase of the project and shall comprise of the high-level
details of the project. The purpose of the project along with the high-level budget,
schedule, scope, and requirements must be provided to the sponsor through these
deliverables.
4

Project Proposal
Project Plan: The deliverable must provide the project sponsor and the stakeholders
with the detailed information on the software upgrade in terms of the project
methodology to be used in the project, details of the project scope, information on the
project timeline and schedule, estimated project budget, details of resources allocated
to the project, risk management approach, procurement and communication plan, and
quality management plan.
Migrated Data sets & services: The data sets and services will be migrated from the
existing platform to the new platform and the technical report comprising of the
details and outcomes of the process shall be provided to the project stakeholders.
Implementation Plan: The implementation plan for the project would comprise of the
details implementation methodology to be used, schedule and budget details,
resources involved, and likewise (Rose & Indelicato, 2009).
Closure Report: This will be the final deliverable of the project in which the details of
the project activities completed by the project team will be included along with the
lessons learned and areas of improvement.
The milestone schedule of the project has been shown in the image below.
Affected Parties
There will be parties that will be affected from the project. The names and details of these
parties is as described below:
Management & Employees of the firm: The software upgrade is being done to make
sure that the employees are provided with technically advanced systems and platforms
and it will allow them to carry out the business tasks more efficiently. There will be
initial set of changes that will come up for the employees that will be required to be
managed.
Customers of the Business Enterprise: The software upgrade will positively affect the
customers of the business enterprise as the performance of the business operations
5
Project Plan: The deliverable must provide the project sponsor and the stakeholders
with the detailed information on the software upgrade in terms of the project
methodology to be used in the project, details of the project scope, information on the
project timeline and schedule, estimated project budget, details of resources allocated
to the project, risk management approach, procurement and communication plan, and
quality management plan.
Migrated Data sets & services: The data sets and services will be migrated from the
existing platform to the new platform and the technical report comprising of the
details and outcomes of the process shall be provided to the project stakeholders.
Implementation Plan: The implementation plan for the project would comprise of the
details implementation methodology to be used, schedule and budget details,
resources involved, and likewise (Rose & Indelicato, 2009).
Closure Report: This will be the final deliverable of the project in which the details of
the project activities completed by the project team will be included along with the
lessons learned and areas of improvement.
The milestone schedule of the project has been shown in the image below.
Affected Parties
There will be parties that will be affected from the project. The names and details of these
parties is as described below:
Management & Employees of the firm: The software upgrade is being done to make
sure that the employees are provided with technically advanced systems and platforms
and it will allow them to carry out the business tasks more efficiently. There will be
initial set of changes that will come up for the employees that will be required to be
managed.
Customers of the Business Enterprise: The software upgrade will positively affect the
customers of the business enterprise as the performance of the business operations
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Proposal
will improve leading to the streamlining of the services and products provided to
them.
Competitors: The business will be able to perform better with the installation of the
new operating system which will provide it a competitive edge in the market. The
competitors will be negatively affected by the project (Zwikael, 2009).
Project Team: The successful completion of the project will provide the project team
with positive feedback and comments from the sponsor which will be beneficial for
their professional growth.
Suppliers: The vendor of the software to be upgraded will be positively affected as the
price paid in return of the software will be high.
Risk Identification & Strategy
There will be several risks that the project will be exposed to. This is because the software
upgrade will involve the existing data sets and services along with the other applications and
tools. The risks associated with the project will be handled using a phased approach. The
strategy will involve risk identification as the first step. In this step, the data gathering
processes will be carried out using the techniques as observations, domain analysis,
brainstorming etc. The information collected using these techniques will be analysed to
identify and prepare a list of the risks that the project will be exposed to. In the second phase,
the analysis of these risks and threats will be done. There will be a likelihood and impact
score that will be granted to every risk and the risk score will be calculated on the basis of the
same. In the third step, the assessment of the risks will be done as acceptable or non-
acceptable. The fourth step will include the treatment of the risks using the mitigation,
transfer, avoidance, or sharing as the strategy (Patterson & Neailey, 2002). The fifth phase
will include the monitoring and control of the risks by using reviews and audits as the
techniques. The last phase will be the closure phase in which the risk will be marked as
treated and closed.
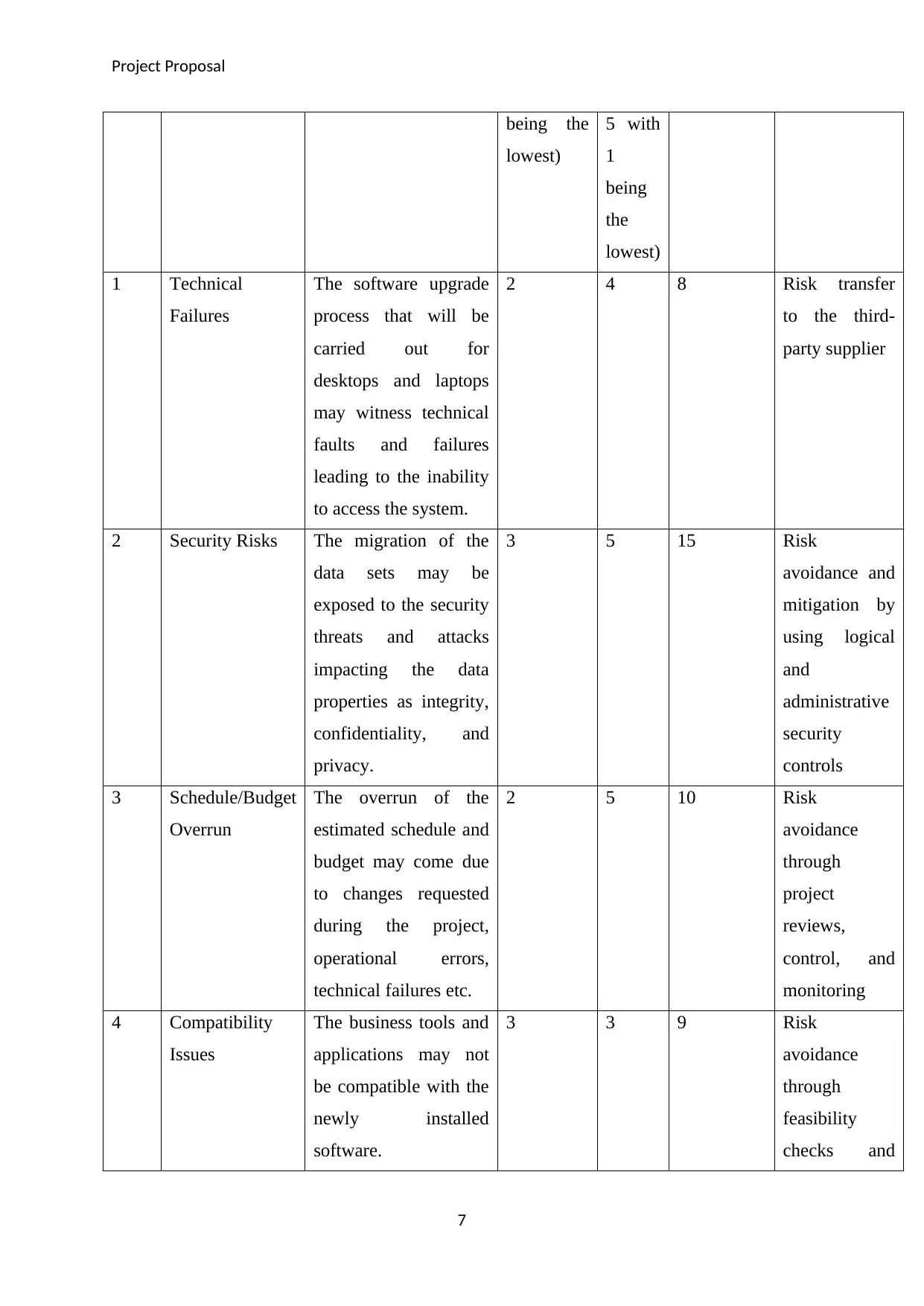
The details of the risks that have been identified for the project along with the risk description
have been included in the table below.
Risk
ID
Name Description Probability
(Scale of 1
to 5 with 1
Impact
(Scale
of 1 to
Score
(Probability
x Impact)
Strategy
6
will improve leading to the streamlining of the services and products provided to
them.
Competitors: The business will be able to perform better with the installation of the
new operating system which will provide it a competitive edge in the market. The
competitors will be negatively affected by the project (Zwikael, 2009).
Project Team: The successful completion of the project will provide the project team
with positive feedback and comments from the sponsor which will be beneficial for
their professional growth.
Suppliers: The vendor of the software to be upgraded will be positively affected as the
price paid in return of the software will be high.
Risk Identification & Strategy
There will be several risks that the project will be exposed to. This is because the software
upgrade will involve the existing data sets and services along with the other applications and
tools. The risks associated with the project will be handled using a phased approach. The
strategy will involve risk identification as the first step. In this step, the data gathering
processes will be carried out using the techniques as observations, domain analysis,
brainstorming etc. The information collected using these techniques will be analysed to
identify and prepare a list of the risks that the project will be exposed to. In the second phase,
the analysis of these risks and threats will be done. There will be a likelihood and impact
score that will be granted to every risk and the risk score will be calculated on the basis of the
same. In the third step, the assessment of the risks will be done as acceptable or non-
acceptable. The fourth step will include the treatment of the risks using the mitigation,
transfer, avoidance, or sharing as the strategy (Patterson & Neailey, 2002). The fifth phase
will include the monitoring and control of the risks by using reviews and audits as the
techniques. The last phase will be the closure phase in which the risk will be marked as
treated and closed.
The details of the risks that have been identified for the project along with the risk description
have been included in the table below.
Risk
ID
Name Description Probability
(Scale of 1
to 5 with 1
Impact
(Scale
of 1 to
Score
(Probability
x Impact)
Strategy
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project Proposal
being the
lowest)
5 with
1
being
the
lowest)
1 Technical
Failures
The software upgrade
process that will be
carried out for
desktops and laptops
may witness technical
faults and failures
leading to the inability
to access the system.
2 4 8 Risk transfer
to the third-
party supplier
2 Security Risks The migration of the
data sets may be
exposed to the security
threats and attacks
impacting the data
properties as integrity,
confidentiality, and
privacy.
3 5 15 Risk
avoidance and
mitigation by
using logical
and
administrative
security
controls
3 Schedule/Budget
Overrun
The overrun of the
estimated schedule and
budget may come due
to changes requested
during the project,
operational errors,
technical failures etc.
2 5 10 Risk
avoidance
through
project
reviews,
control, and
monitoring
4 Compatibility
Issues
The business tools and
applications may not
be compatible with the
newly installed
software.
3 3 9 Risk
avoidance
through
feasibility
checks and
7
being the
lowest)
5 with
1
being
the
lowest)
1 Technical
Failures
The software upgrade
process that will be
carried out for
desktops and laptops
may witness technical
faults and failures
leading to the inability
to access the system.
2 4 8 Risk transfer
to the third-
party supplier
2 Security Risks The migration of the
data sets may be
exposed to the security
threats and attacks
impacting the data
properties as integrity,
confidentiality, and
privacy.
3 5 15 Risk
avoidance and
mitigation by
using logical
and
administrative
security
controls
3 Schedule/Budget
Overrun
The overrun of the
estimated schedule and
budget may come due
to changes requested
during the project,
operational errors,
technical failures etc.
2 5 10 Risk
avoidance
through
project
reviews,
control, and
monitoring
4 Compatibility
Issues
The business tools and
applications may not
be compatible with the
newly installed
software.
3 3 9 Risk
avoidance
through
feasibility
checks and
7
Project Proposal
analysis
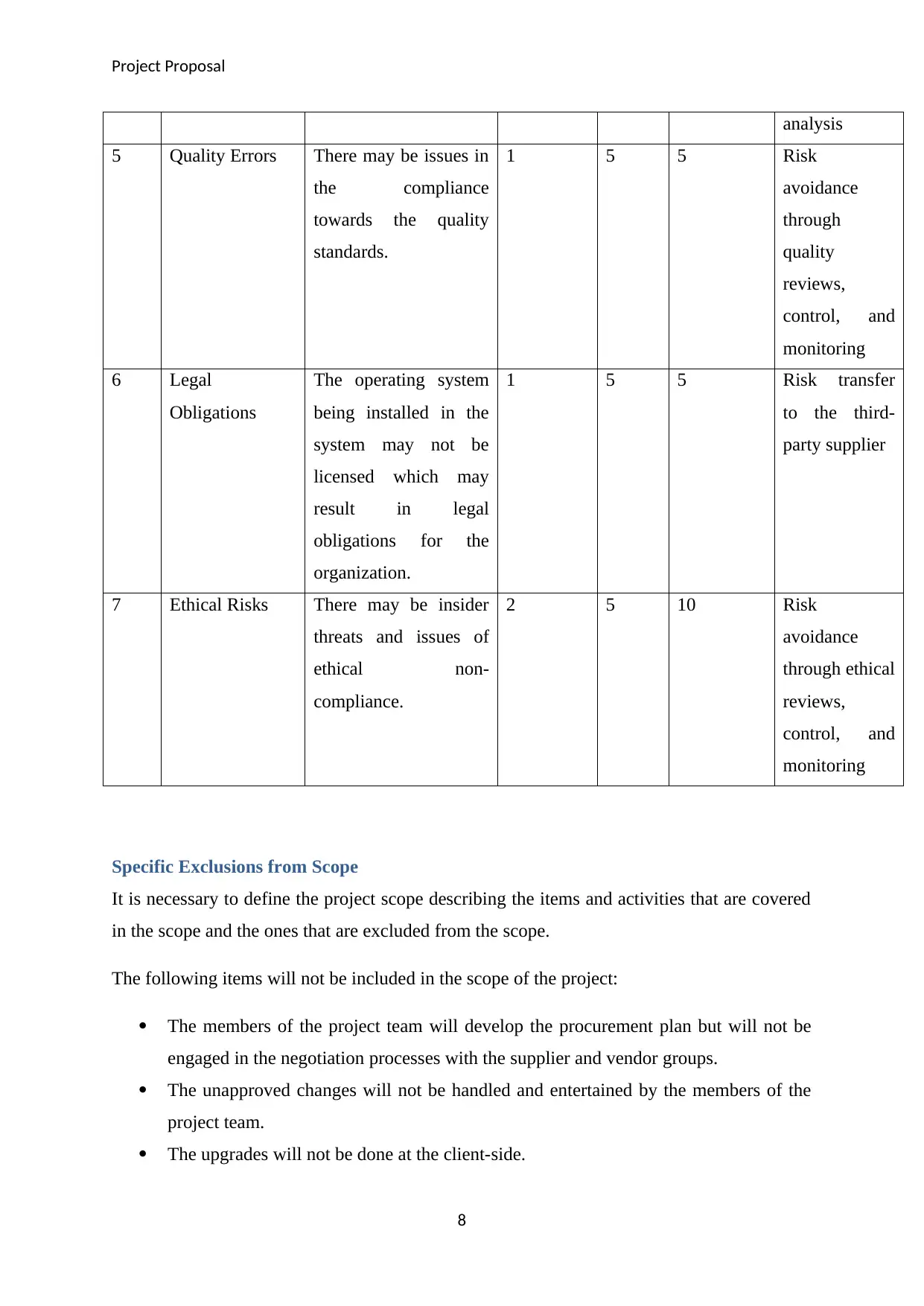
5 Quality Errors There may be issues in
the compliance
towards the quality
standards.
1 5 5 Risk
avoidance
through
quality
reviews,
control, and
monitoring
6 Legal
Obligations
The operating system
being installed in the
system may not be
licensed which may
result in legal
obligations for the
organization.
1 5 5 Risk transfer
to the third-
party supplier
7 Ethical Risks There may be insider
threats and issues of
ethical non-
compliance.
2 5 10 Risk
avoidance
through ethical
reviews,
control, and
monitoring
Specific Exclusions from Scope
It is necessary to define the project scope describing the items and activities that are covered
in the scope and the ones that are excluded from the scope.
The following items will not be included in the scope of the project:
The members of the project team will develop the procurement plan but will not be
engaged in the negotiation processes with the supplier and vendor groups.
The unapproved changes will not be handled and entertained by the members of the
project team.
The upgrades will not be done at the client-side.
8
analysis
5 Quality Errors There may be issues in
the compliance
towards the quality
standards.
1 5 5 Risk
avoidance
through
quality
reviews,
control, and
monitoring
6 Legal
Obligations
The operating system
being installed in the
system may not be
licensed which may
result in legal
obligations for the
organization.
1 5 5 Risk transfer
to the third-
party supplier
7 Ethical Risks There may be insider
threats and issues of
ethical non-
compliance.
2 5 10 Risk
avoidance
through ethical
reviews,
control, and
monitoring
Specific Exclusions from Scope
It is necessary to define the project scope describing the items and activities that are covered
in the scope and the ones that are excluded from the scope.
The following items will not be included in the scope of the project:
The members of the project team will develop the procurement plan but will not be
engaged in the negotiation processes with the supplier and vendor groups.
The unapproved changes will not be handled and entertained by the members of the
project team.
The upgrades will not be done at the client-side.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Proposal
Implementation Plan
The implementation of the project will be carried out in a series of phases. The first phase
will be the initiation and planning phase. The implementation methodology that will be
followed in the project will be phased implementation rather than the Big Bang
implementation. This will make sure that the software upgrade is carried out for a few
systems in one implementation cycle. The desktops will be covered first followed by the
laptops. Also, the upgrade will be done as per the employee association with the organization.
The project criticality will also be considered during the upgrade and implementation
process. The next phase will be the execution phase in which the implementation of the
system will be done followed by the control and monitoring phases. There will be reviews
and audit cycles that will be carried out so that implementation process is streamlined. Also,
there may be certain changes that may be detected. These changes shall be managed to make
sure that the project areas are improved upon (Al-Freidi, 2015). The last phase will be the
closure phase in which the final implementation report will be submitted.
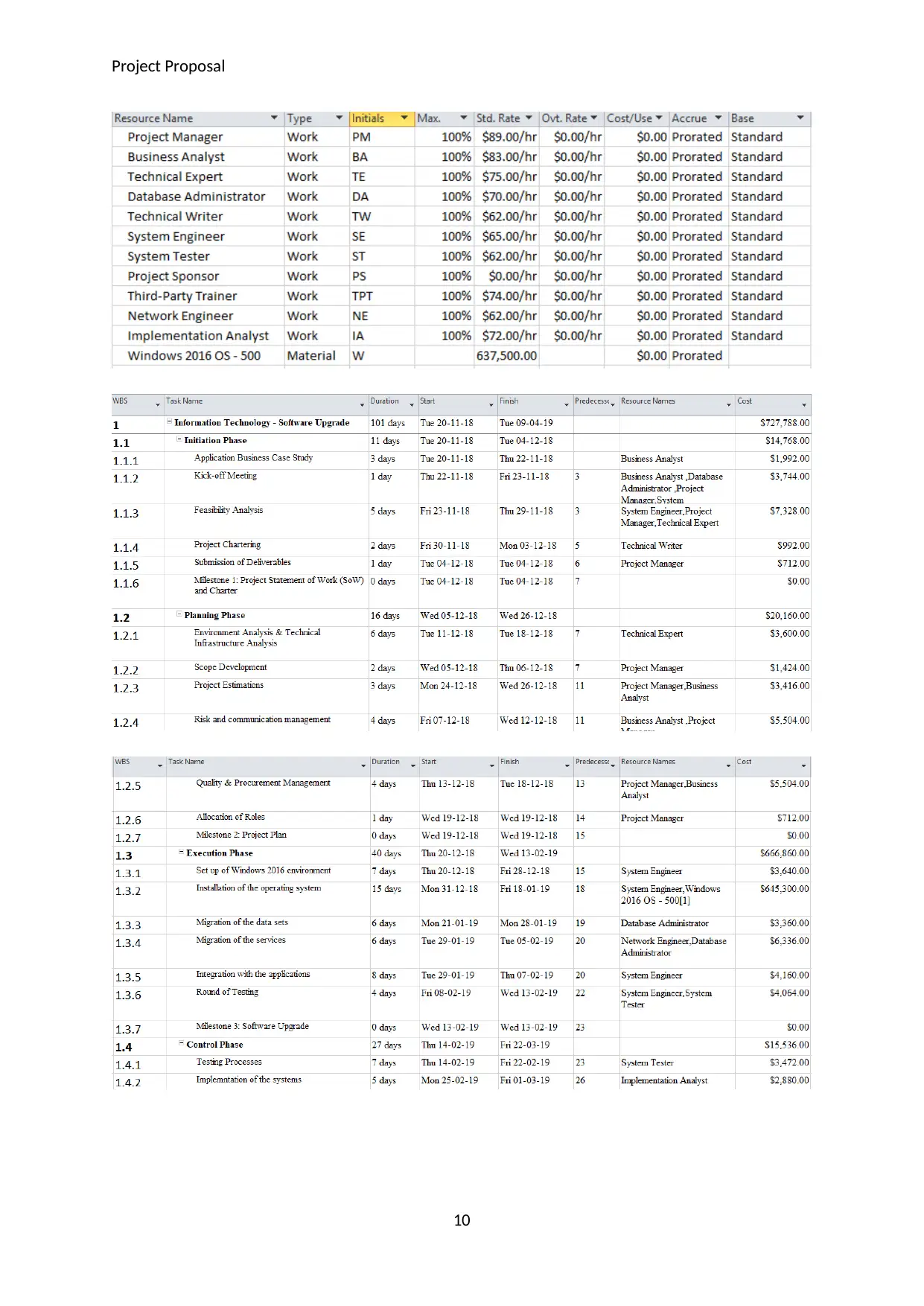
High-Level Budget and Timeline/Schedule
The technique that has been used to estimate the budget and schedule for the project is
bottom-up estimation technique. As per this technique, the activities at the lowermost level in
the project hierarchy were selected first. The estimation of the duration and costs for these
activities was done followed by the ones above them. In this manner, the overall estimation
of the costs and schedule was done for the project. The project will be completed in the
estimated duration as 101 days starting from 20th November 2018 and ending on 9th April
2019. The project will be headed by the Project Manager and will involve additional
resources as Technical Expert, System Engineer, Business Analyst, Database Administrator,
Technical Writer, System Tester, Third-Party Trainer, Network Engineer, and
Implementation Analyst.
The cost of Windows 2016 operating system is $1,275 and 500 such licenses will be required
to be obtained. Thus, the cost of the operating systems will be $637,500. There will be cost of
resources, implementation costs, planning costs, and closure costs that are also involved.
There will be trainings arranged for the end-users and the cost of training will also be
involved with the project. The details of the budget and schedule along with the resources
assigned are shown below.
9
Implementation Plan
The implementation of the project will be carried out in a series of phases. The first phase
will be the initiation and planning phase. The implementation methodology that will be
followed in the project will be phased implementation rather than the Big Bang
implementation. This will make sure that the software upgrade is carried out for a few
systems in one implementation cycle. The desktops will be covered first followed by the
laptops. Also, the upgrade will be done as per the employee association with the organization.
The project criticality will also be considered during the upgrade and implementation
process. The next phase will be the execution phase in which the implementation of the
system will be done followed by the control and monitoring phases. There will be reviews
and audit cycles that will be carried out so that implementation process is streamlined. Also,
there may be certain changes that may be detected. These changes shall be managed to make
sure that the project areas are improved upon (Al-Freidi, 2015). The last phase will be the
closure phase in which the final implementation report will be submitted.
High-Level Budget and Timeline/Schedule
The technique that has been used to estimate the budget and schedule for the project is
bottom-up estimation technique. As per this technique, the activities at the lowermost level in
the project hierarchy were selected first. The estimation of the duration and costs for these
activities was done followed by the ones above them. In this manner, the overall estimation
of the costs and schedule was done for the project. The project will be completed in the
estimated duration as 101 days starting from 20th November 2018 and ending on 9th April
2019. The project will be headed by the Project Manager and will involve additional
resources as Technical Expert, System Engineer, Business Analyst, Database Administrator,
Technical Writer, System Tester, Third-Party Trainer, Network Engineer, and
Implementation Analyst.
The cost of Windows 2016 operating system is $1,275 and 500 such licenses will be required
to be obtained. Thus, the cost of the operating systems will be $637,500. There will be cost of
resources, implementation costs, planning costs, and closure costs that are also involved.
There will be trainings arranged for the end-users and the cost of training will also be
involved with the project. The details of the budget and schedule along with the resources
assigned are shown below.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Project Proposal
10
10
Project Proposal
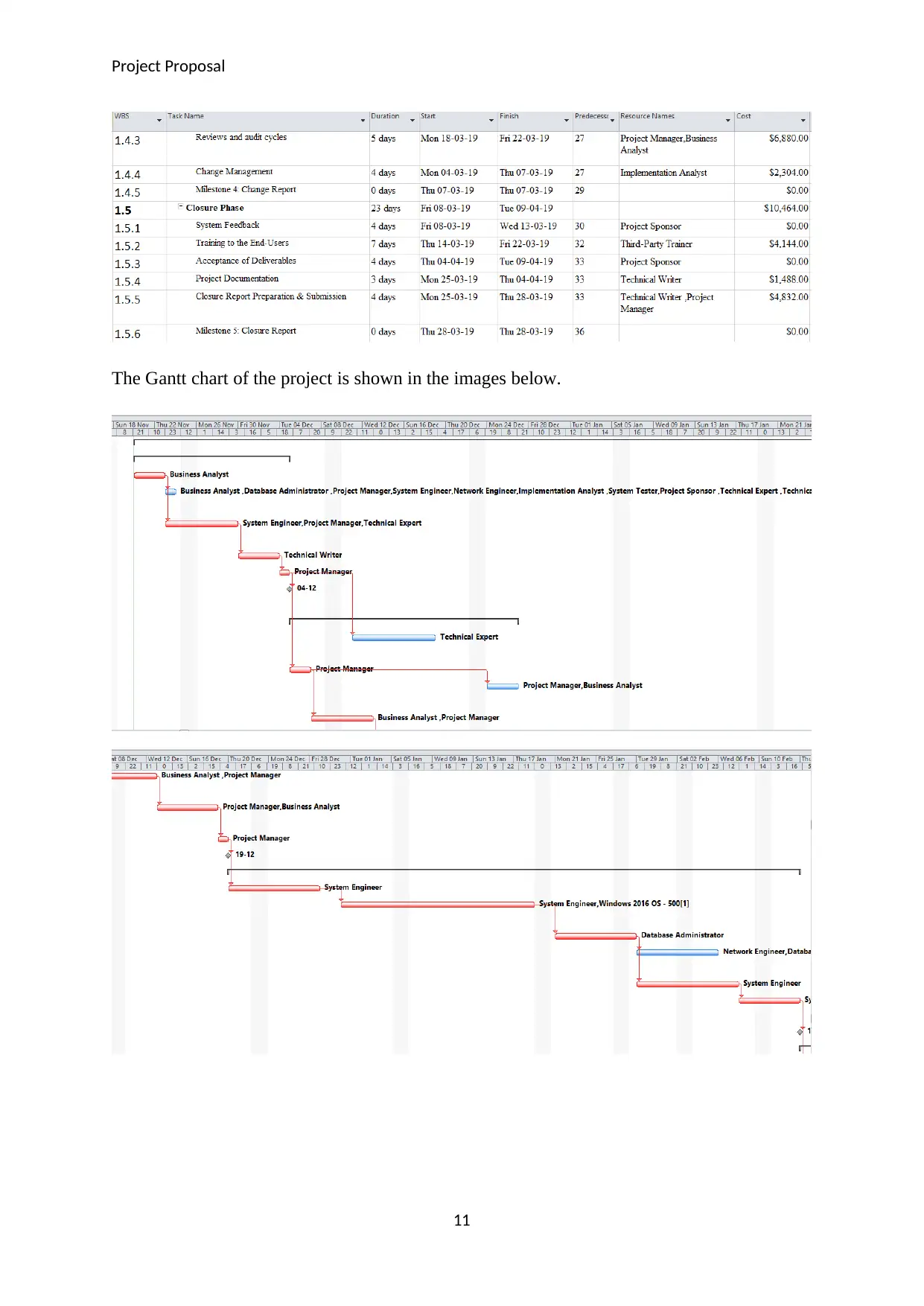
The Gantt chart of the project is shown in the images below.
11
The Gantt chart of the project is shown in the images below.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





