Internet of Things: Challenges and Opportunities
VerifiedAdded on 2020/02/24
|16
|3851
|33
AI Summary
This assignment delves into the multifaceted aspects of the Internet of Things (IoT). It examines the technological underpinnings, explores its potential applications across diverse domains, and critically analyzes the inherent security challenges associated with IoT deployments. The discussion also encompasses current research trends and future prospects for this rapidly evolving field.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INTERNET OF THINGS
Internet of Things
Name of the Student
Name of the University
Author’s note
Internet of Things
Name of the Student
Name of the University
Author’s note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1INTERNET OF THINGS
Executive Summary
Internet of Things (IoT) involves the procedure of connecting the software, hardware and
sensors. The implementation of IoT technology in farming and agriculture has significantly
changed the scenario of farming as a whole. The quality has improved a lot with the advent of
IoT. The quality has enhanced a great deal with the appearance of IoT. The different
innovations related with the agriculture have changed the sustenance quality. The
agriculturists dependably remain associated with the Internet and utilize the network system
for the advantages. Presently, there is a downside, since the intruders utilize the unreliable
system they fall into prey of the cyber attackers, they attack their devices and lock their
devices and requesting cash. The ransomware attack cost them excessively. They take the
agriculturists' information also. This investigation features those issues and furthermore gives
helpful answers for the particular issues confronted by the clients. This examination study
highlighted the issues and give answers for reinforcing the security structure for the
improvement of the agriculturists so they can lead their activities securely and safely.
Executive Summary
Internet of Things (IoT) involves the procedure of connecting the software, hardware and
sensors. The implementation of IoT technology in farming and agriculture has significantly
changed the scenario of farming as a whole. The quality has improved a lot with the advent of
IoT. The quality has enhanced a great deal with the appearance of IoT. The different
innovations related with the agriculture have changed the sustenance quality. The
agriculturists dependably remain associated with the Internet and utilize the network system
for the advantages. Presently, there is a downside, since the intruders utilize the unreliable
system they fall into prey of the cyber attackers, they attack their devices and lock their
devices and requesting cash. The ransomware attack cost them excessively. They take the
agriculturists' information also. This investigation features those issues and furthermore gives
helpful answers for the particular issues confronted by the clients. This examination study
highlighted the issues and give answers for reinforcing the security structure for the
improvement of the agriculturists so they can lead their activities securely and safely.

2INTERNET OF THINGS
Table of Contents
1. Introduction............................................................................................................................3
2. Review....................................................................................................................................3
i. The common security issues with wireless technologies....................................................3
ii. The current security solutions for the security threats on Internet of Thing......................4
iii. How effective are the current security solutions..............................................................6
iv. The problems and issues and limitations residing with the current security solutions for
Internet of Things...................................................................................................................7
v. The better ways of overcoming the security challenges that can assist farmers................8
2.3. The proposed better method that can benefit the farmers...................................................9
i. Features that will provide security and enhance agriculture...............................................9
ii. The Model Diagram to simulate the IoT model for agriculture and farmers...................10
iii. Limited features of IoT...................................................................................................12
4. Conclusion............................................................................................................................12
5. References............................................................................................................................13
Table of Contents
1. Introduction............................................................................................................................3
2. Review....................................................................................................................................3
i. The common security issues with wireless technologies....................................................3
ii. The current security solutions for the security threats on Internet of Thing......................4
iii. How effective are the current security solutions..............................................................6
iv. The problems and issues and limitations residing with the current security solutions for
Internet of Things...................................................................................................................7
v. The better ways of overcoming the security challenges that can assist farmers................8
2.3. The proposed better method that can benefit the farmers...................................................9
i. Features that will provide security and enhance agriculture...............................................9
ii. The Model Diagram to simulate the IoT model for agriculture and farmers...................10
iii. Limited features of IoT...................................................................................................12
4. Conclusion............................................................................................................................12
5. References............................................................................................................................13

3INTERNET OF THINGS
1. Introduction
Internet of Things (IoT) involves the procedure of connecting the software, hardware
and sensors. The implementation of IoT technology in farming and agriculture has
significantly changed the scenario of farming as a whole. The quality has improved a lot
with the advent of IoT.
The various technologies associated with the IoT technology have changed the food
quality. The farmers always stay connected to the Internet and use the wireless network for
the benefits. Now, there is a drawback, since the farmers use the insecure network they fall
into prey of the cyber attackers, they attack their systems and lock their system and asking for
money. The ransomware attack cost them too much. They steal the farmers’ data as well.
This research study will review the issues and provide solutions to strengthen the
security framework for the betterment of the farmers so that they can conduct their activities
safely and securely over the network.
2. Review
i. The common security issues with wireless technologies
This research study will showcase the issues and provide solutions to strengthen the
security framework for the betterment of the farmers so that they can conduct their activities
safely and securely over the network.
Jing et al., (2014) suggested the common security solutions in the wireless
technology. The risks those are associated with the wireless technology are-
Intrusion: The mobile network is being more opened to the intruders, they easily gain
access to those mobile devices via an unprotected network and make it vulnerable.
1. Introduction
Internet of Things (IoT) involves the procedure of connecting the software, hardware
and sensors. The implementation of IoT technology in farming and agriculture has
significantly changed the scenario of farming as a whole. The quality has improved a lot
with the advent of IoT.
The various technologies associated with the IoT technology have changed the food
quality. The farmers always stay connected to the Internet and use the wireless network for
the benefits. Now, there is a drawback, since the farmers use the insecure network they fall
into prey of the cyber attackers, they attack their systems and lock their system and asking for
money. The ransomware attack cost them too much. They steal the farmers’ data as well.
This research study will review the issues and provide solutions to strengthen the
security framework for the betterment of the farmers so that they can conduct their activities
safely and securely over the network.
2. Review
i. The common security issues with wireless technologies
This research study will showcase the issues and provide solutions to strengthen the
security framework for the betterment of the farmers so that they can conduct their activities
safely and securely over the network.
Jing et al., (2014) suggested the common security solutions in the wireless
technology. The risks those are associated with the wireless technology are-
Intrusion: The mobile network is being more opened to the intruders, they easily gain
access to those mobile devices via an unprotected network and make it vulnerable.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4INTERNET OF THINGS
Exploitation: The network then is misused widely by means of DoS attacks and it
basically involves major criminal activities.
Granjal, Monteiro & Silva, (2015) depicted the active attack and the passive attack
involved elaborately and lack of security can lead to both physical and virtual intruder attack
such as hacking, data theft, the system integrity destruction. The active attack involves ID
spoofing is basically related to the unauthorised access or unauthorised privileges, the active
attack also involves the access of personal files in the computer system by means of
alternation or modification of the data, that active attack also correlates the dictionary attacks
to detect or identify a set of station service identifiers. According to Da et al., (2014) the
replay attack or DoS attack is associated with accessing and exploiting the wired equivalent
privacy encryption.
According to Gubbi et al., (2013) the passive attack involves the accumulation of the
information when the information is in transmitting in between the unauthorised devices. The
passive attack can occur by the following two methods-
Eavesdropping: this method involves the monitoring and administering of the
transmissions of the message components in between the devices
Traffic analysis: Loo, Mauri & Ortiz, (2016) mentioned the process which involves
monitoring and administrations of transmissions for particular patterns of communication.
All the techniques described above are a part of criminal activities that involves
hacking and exploiting the mobile system and wireless system and () depicted them
beautifully.
Exploitation: The network then is misused widely by means of DoS attacks and it
basically involves major criminal activities.
Granjal, Monteiro & Silva, (2015) depicted the active attack and the passive attack
involved elaborately and lack of security can lead to both physical and virtual intruder attack
such as hacking, data theft, the system integrity destruction. The active attack involves ID
spoofing is basically related to the unauthorised access or unauthorised privileges, the active
attack also involves the access of personal files in the computer system by means of
alternation or modification of the data, that active attack also correlates the dictionary attacks
to detect or identify a set of station service identifiers. According to Da et al., (2014) the
replay attack or DoS attack is associated with accessing and exploiting the wired equivalent
privacy encryption.
According to Gubbi et al., (2013) the passive attack involves the accumulation of the
information when the information is in transmitting in between the unauthorised devices. The
passive attack can occur by the following two methods-
Eavesdropping: this method involves the monitoring and administering of the
transmissions of the message components in between the devices
Traffic analysis: Loo, Mauri & Ortiz, (2016) mentioned the process which involves
monitoring and administrations of transmissions for particular patterns of communication.
All the techniques described above are a part of criminal activities that involves
hacking and exploiting the mobile system and wireless system and () depicted them
beautifully.

5INTERNET OF THINGS
ii. The current security solutions for the security threats on Internet of Thing
Borgohain, Kumar & Sanyal, (2015) presented the security solutions that are
associated with the IoT for diminishing the security threats are- authentication, securing
communication that means data protection while it is in transit, protection of data while in the
process, securing storage which involves protecting data while the data is at rest.
Authentication: Abomhara & Køien, (2014) depicted the common algorithm AES
and SHA-256 that aids in authentication; the authentication process involves the usage of the
asymmetric public key. In case of authentication public key concept is used to encipher and
decipher data for enhancing security. The sender sends a data encrypted with the secure key
and the receiver on the other end can only get access to the data by decrypting the same data
with the secure key. The sender and the receiver can only access the data and they have to
have the key, that means the intruders in between if try to access the data they will have to
know the key encryption ensures data safety. Whitmore, Agarwal & Da Xu, (2015)
highlighted that digital signature is another form of authentication. The concept of digital
certificate involves a private key encryption which can only be opened by the public key, the
private key is only known to the sender and the receiver.
Securing data communication by means of algorithms: According to Botta et al.,
(2016) the software implementations to secure the data my means for authentication can be
power consuming. When that software deployed in a system, it takes a lot of CPU cycles for
processing, hence the system becomes slow and sluggish at times, hence it delays other vital
works and makes the network slower. However, the problem can be solved by the
implementation of the symmetric encryption algorithms like AES and 3DES and the
asymmetric algorithms RSA and ECDSA. According to Al-Fuqahaet al., (2015)
implementations of all these algorithms make the system faster and hence make it power-
ii. The current security solutions for the security threats on Internet of Thing
Borgohain, Kumar & Sanyal, (2015) presented the security solutions that are
associated with the IoT for diminishing the security threats are- authentication, securing
communication that means data protection while it is in transit, protection of data while in the
process, securing storage which involves protecting data while the data is at rest.
Authentication: Abomhara & Køien, (2014) depicted the common algorithm AES
and SHA-256 that aids in authentication; the authentication process involves the usage of the
asymmetric public key. In case of authentication public key concept is used to encipher and
decipher data for enhancing security. The sender sends a data encrypted with the secure key
and the receiver on the other end can only get access to the data by decrypting the same data
with the secure key. The sender and the receiver can only access the data and they have to
have the key, that means the intruders in between if try to access the data they will have to
know the key encryption ensures data safety. Whitmore, Agarwal & Da Xu, (2015)
highlighted that digital signature is another form of authentication. The concept of digital
certificate involves a private key encryption which can only be opened by the public key, the
private key is only known to the sender and the receiver.
Securing data communication by means of algorithms: According to Botta et al.,
(2016) the software implementations to secure the data my means for authentication can be
power consuming. When that software deployed in a system, it takes a lot of CPU cycles for
processing, hence the system becomes slow and sluggish at times, hence it delays other vital
works and makes the network slower. However, the problem can be solved by the
implementation of the symmetric encryption algorithms like AES and 3DES and the
asymmetric algorithms RSA and ECDSA. According to Al-Fuqahaet al., (2015)
implementations of all these algorithms make the system faster and hence make it power-

6INTERNET OF THINGS
efficient. The software implications, on the other hand, can be tedious and can slow the
system and hence should be replaced by these algorithms.
Secure transit: Matharu, Upadhyay & Chaudhary, (2014) stated that the sensitive
information while in transit must remain safe and secure all throughout the transmission
between the sender and the receiver, and those must not be leaked in any way. However, in
some instances in case of payment applications, another safety and security layer is required,
certain software tools come into play in this case, and the execution of the code can be made
secure by implementing those tools. The secured environment can be achieved by the security
chips and the inbuilt security chips in the IoT device host CPU.
Securing the data while storing in the device: When the data is stored in the database
of the IoT devices, it can be made secure with the secure key and the unique device identifier.
From the root keys, the session keys are generated and these keys are for authentication and
securing connection among the devices. According to Chen et al., (2014), the authorised
users who know the keys' details can only access and can further communicate with the
devices; these data are secured in terms of warranty and privacy.
iii. How effective are the current security solutions
IoT helps in the following scenarios-
i. Securing personal information: IoT helps to secure and protect the assets of the
users. IoT helps to build custom applications to protect users' data; it makes users' life
simpler.
ii. Stay ahead of the customers: The developers or the manufacturers by taking the
help of cloud technology and advanced IoT solutions can stay ahead of their competitors.
efficient. The software implications, on the other hand, can be tedious and can slow the
system and hence should be replaced by these algorithms.
Secure transit: Matharu, Upadhyay & Chaudhary, (2014) stated that the sensitive
information while in transit must remain safe and secure all throughout the transmission
between the sender and the receiver, and those must not be leaked in any way. However, in
some instances in case of payment applications, another safety and security layer is required,
certain software tools come into play in this case, and the execution of the code can be made
secure by implementing those tools. The secured environment can be achieved by the security
chips and the inbuilt security chips in the IoT device host CPU.
Securing the data while storing in the device: When the data is stored in the database
of the IoT devices, it can be made secure with the secure key and the unique device identifier.
From the root keys, the session keys are generated and these keys are for authentication and
securing connection among the devices. According to Chen et al., (2014), the authorised
users who know the keys' details can only access and can further communicate with the
devices; these data are secured in terms of warranty and privacy.
iii. How effective are the current security solutions
IoT helps in the following scenarios-
i. Securing personal information: IoT helps to secure and protect the assets of the
users. IoT helps to build custom applications to protect users' data; it makes users' life
simpler.
ii. Stay ahead of the customers: The developers or the manufacturers by taking the
help of cloud technology and advanced IoT solutions can stay ahead of their competitors.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INTERNET OF THINGS
iii. Providing benefits to agriculture and farming: The farmers or any individuals
can use the IoT configured hardware and software solutions to get cost-effective and secured
service.
iv. IoT providing advanced data storage: According to Grieco et al., (2014), the
clients can get the advanced data storage facilities and standard, and also the advanced data
protection via IoT.
iv. The problems and issues and limitations residing with the current security
solutions for Internet of Things
The attackers or the intruders finding out the loopholes has spread their arms and the
cyber crimes are increasing day by day, ransomware is one of that kind, the ransomware virus
become popular because of the following flaws-
Lack of proper authorization technique: Lack of strong passwords can lead to
unauthorised access and lead to unethical data usage.
Encryption failure: Martínez-Pérez et al., (2015) showcased that the devices fail to
encrypt or decrypt data when the data is transferred, even though the device is connected to
the Internet.
The security credentials: The users use the same default username and password
preconfigured for the devices.
Privacy issues: The privacy issues incur as the organisations collect data from the
customers via an insecure network.
Open-source software: According to Trappe, Howard & Moore, (2015), IoT devices
must be configured with the open-source software and not the paid software, as these can
reduce the usage of IoT technology and the students and the educators can face challenges
iii. Providing benefits to agriculture and farming: The farmers or any individuals
can use the IoT configured hardware and software solutions to get cost-effective and secured
service.
iv. IoT providing advanced data storage: According to Grieco et al., (2014), the
clients can get the advanced data storage facilities and standard, and also the advanced data
protection via IoT.
iv. The problems and issues and limitations residing with the current security
solutions for Internet of Things
The attackers or the intruders finding out the loopholes has spread their arms and the
cyber crimes are increasing day by day, ransomware is one of that kind, the ransomware virus
become popular because of the following flaws-
Lack of proper authorization technique: Lack of strong passwords can lead to
unauthorised access and lead to unethical data usage.
Encryption failure: Martínez-Pérez et al., (2015) showcased that the devices fail to
encrypt or decrypt data when the data is transferred, even though the device is connected to
the Internet.
The security credentials: The users use the same default username and password
preconfigured for the devices.
Privacy issues: The privacy issues incur as the organisations collect data from the
customers via an insecure network.
Open-source software: According to Trappe, Howard & Moore, (2015), IoT devices
must be configured with the open-source software and not the paid software, as these can
reduce the usage of IoT technology and the students and the educators can face challenges

8INTERNET OF THINGS
adopting the new technology for them. Open-source software help to overcome the security
breaches easily.
IoT in testing mode: IoT technology is still in beta mode and needs to be
revolutionised, there are many security breaches and several pitfalls that need to be addressed
and solved as soon as possible.
v. The better ways of overcoming the security challenges that can assist farmers
The best possible solution for overcoming the security challenges in the IoT devices is
to protect the personal information and details and the specifications by implementing
required IoT devices that are IoT algorithms and associated IoT hardware. IoT hardware can
make the whole system cost-effective as well as the algorithms can help them to process
things over the Internet further. Moreover, it provides us with a secured solution. Lee & Lee,
(2015) depicted that the security can be achieved by following means –
Patching all the system requirements on a daily basis: The computer desktop, as
well as the mobile devices, must be configured and set up to install the daily updates. The
updated patches include all the solutions for the security breaches. So, the updated operating
system is less vulnerable to threats.
Backup system files and personal data: The backing up of system files and the
personal data help in this scenario. If any important files get affected then it will not hurt, so
the backup is easiest and cheapest method, it helps to mitigate the effect of ransomware
effect.
Updated software: According to Farooq et al., (2015), the software or apps installed
in the device must be updated all the time; the browsers must be updated, as the outdated
software is more vulnerable to security threats and risks.
adopting the new technology for them. Open-source software help to overcome the security
breaches easily.
IoT in testing mode: IoT technology is still in beta mode and needs to be
revolutionised, there are many security breaches and several pitfalls that need to be addressed
and solved as soon as possible.
v. The better ways of overcoming the security challenges that can assist farmers
The best possible solution for overcoming the security challenges in the IoT devices is
to protect the personal information and details and the specifications by implementing
required IoT devices that are IoT algorithms and associated IoT hardware. IoT hardware can
make the whole system cost-effective as well as the algorithms can help them to process
things over the Internet further. Moreover, it provides us with a secured solution. Lee & Lee,
(2015) depicted that the security can be achieved by following means –
Patching all the system requirements on a daily basis: The computer desktop, as
well as the mobile devices, must be configured and set up to install the daily updates. The
updated patches include all the solutions for the security breaches. So, the updated operating
system is less vulnerable to threats.
Backup system files and personal data: The backing up of system files and the
personal data help in this scenario. If any important files get affected then it will not hurt, so
the backup is easiest and cheapest method, it helps to mitigate the effect of ransomware
effect.
Updated software: According to Farooq et al., (2015), the software or apps installed
in the device must be updated all the time; the browsers must be updated, as the outdated
software is more vulnerable to security threats and risks.

9INTERNET OF THINGS
Blocking SMB inbound or outbound on the firewall: The ransomware virus
basically spread through Windows SMB services, so implementation and configuration of
firewall can mitigate the risk of ransomware.
Installation of antivirus software: Sicari et al., (2015) stated that the antivirus
software installation can help definitely help to fight against the ransomware, any basic
antivirus available in the market can secure the network from the potential attack of
ransomware virus.
2.3. The proposed better method that can benefit the farmers
i. Features that will provide security and enhance agriculture
The farmers must take the definite approaches discussed that will enhance the security
and also provide various farming facilities.
Installation of antivirus software
The farmers must install the antivirus software in their system and must keep it
updated; the software can definitely help them to stay away from the adverse effect of the
ransomware virus.
Backing up of important data and files
According to Anwar et al., (2014), the farmers should back up their business data and
files regularly. They can store the files on a USB stick or USB flash drive, they can be
ensured by simply testing whether the backup files are working or not.
Saving files in read-only mode
The farmers can make a simple move. The ransomware virus cannot attack the files
that are read-only. Therefore, they can make a trick and save their files in read-only mode, in
Blocking SMB inbound or outbound on the firewall: The ransomware virus
basically spread through Windows SMB services, so implementation and configuration of
firewall can mitigate the risk of ransomware.
Installation of antivirus software: Sicari et al., (2015) stated that the antivirus
software installation can help definitely help to fight against the ransomware, any basic
antivirus available in the market can secure the network from the potential attack of
ransomware virus.
2.3. The proposed better method that can benefit the farmers
i. Features that will provide security and enhance agriculture
The farmers must take the definite approaches discussed that will enhance the security
and also provide various farming facilities.
Installation of antivirus software
The farmers must install the antivirus software in their system and must keep it
updated; the software can definitely help them to stay away from the adverse effect of the
ransomware virus.
Backing up of important data and files
According to Anwar et al., (2014), the farmers should back up their business data and
files regularly. They can store the files on a USB stick or USB flash drive, they can be
ensured by simply testing whether the backup files are working or not.
Saving files in read-only mode
The farmers can make a simple move. The ransomware virus cannot attack the files
that are read-only. Therefore, they can make a trick and save their files in read-only mode, in
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10INTERNET OF THINGS
this way they can protect their files and they do not have to pay a large amount to the
intruders.
ii. The Model Diagram to simulate the IoT model for agriculture and farmers
Fig 1: General Overview of IoT working
(Source: Anwar et al., 2014, pp- 1224-1227)
According to Anwar et al., 2014, the above model demonstrates how IoT works. The
model gives a general overview of a secured connection established between IoT devices, IoT
server and the IoT-Ticket Dashboard. This ensures secure data transmission and protection
from ransomware.
this way they can protect their files and they do not have to pay a large amount to the
intruders.
ii. The Model Diagram to simulate the IoT model for agriculture and farmers
Fig 1: General Overview of IoT working
(Source: Anwar et al., 2014, pp- 1224-1227)
According to Anwar et al., 2014, the above model demonstrates how IoT works. The
model gives a general overview of a secured connection established between IoT devices, IoT
server and the IoT-Ticket Dashboard. This ensures secure data transmission and protection
from ransomware.
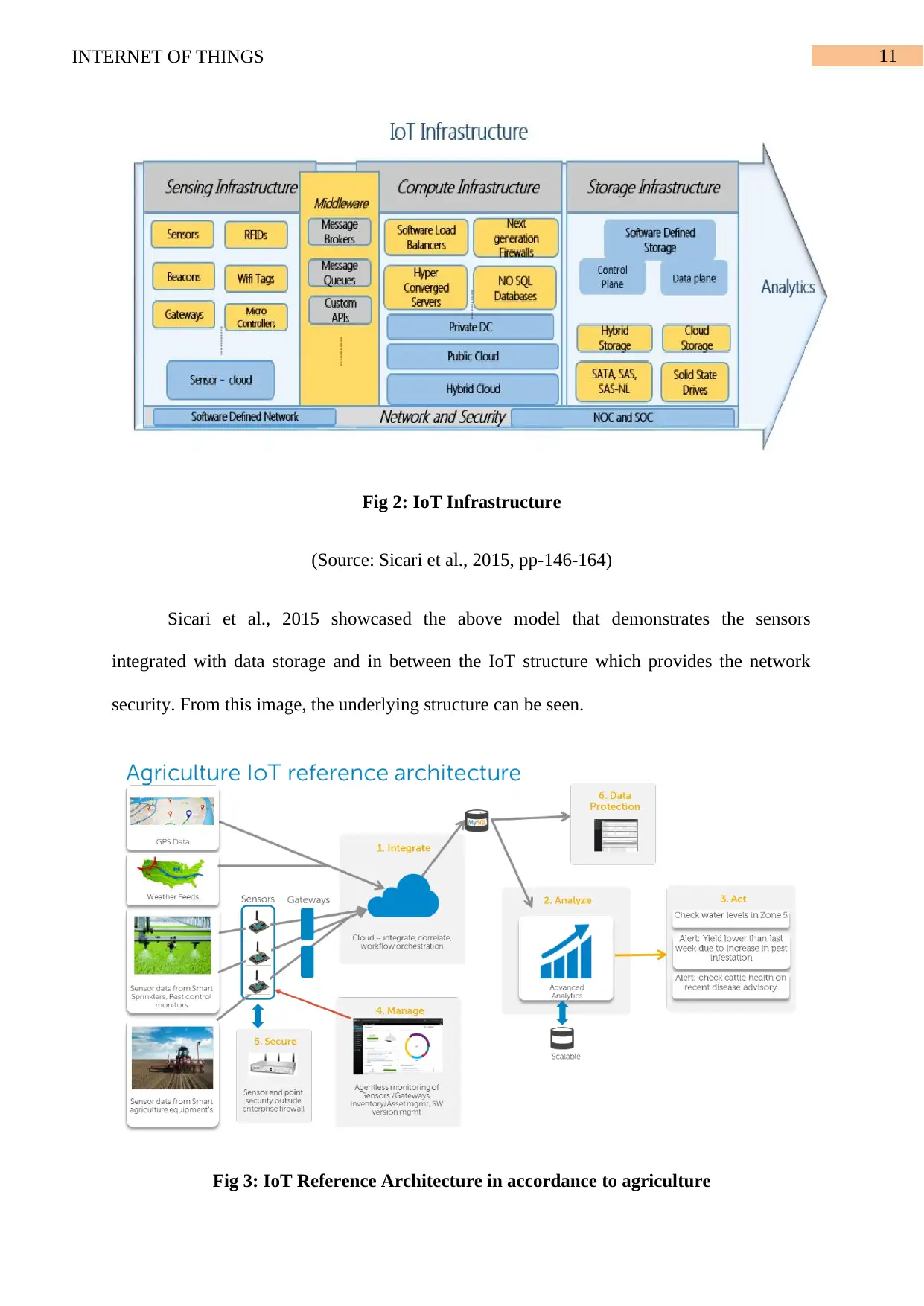
11INTERNET OF THINGS
Fig 2: IoT Infrastructure
(Source: Sicari et al., 2015, pp-146-164)
Sicari et al., 2015 showcased the above model that demonstrates the sensors
integrated with data storage and in between the IoT structure which provides the network
security. From this image, the underlying structure can be seen.
Fig 3: IoT Reference Architecture in accordance to agriculture
Fig 2: IoT Infrastructure
(Source: Sicari et al., 2015, pp-146-164)
Sicari et al., 2015 showcased the above model that demonstrates the sensors
integrated with data storage and in between the IoT structure which provides the network
security. From this image, the underlying structure can be seen.
Fig 3: IoT Reference Architecture in accordance to agriculture

12INTERNET OF THINGS
(Source: Granjal, Monteiro & Silva, 2015, 1294-1312)
Granjal, Monteiro & Silva, 2015 demonstrates the above model in details and the
applications of agriculture with the cloud and database, the data accumulated is stored
securely in the database for future analysis.
iii. Limited features of IoT
Li, Da & Zhao, (2015) stated that the IoT is in testing mode, the farmer can still get
enough advantages from the IoT services, though in mere future they will get more benefits
from the IoT.
4. Conclusion
It can be concluded from the above discourse that IoT has a lot to offer to the farmer
and agriculture. The quality has enhanced a great deal with the appearance of IoT. The
different innovations related with the agriculture have changed the sustenance quality. The
agriculturists dependably remain associated with the Internet and utilize the network system
for the advantages. Presently, there is a downside, since the intruders utilize the unreliable
system they fall into prey of the cyber attackers, they attack their devices and lock their
devices and requesting cash. The ransomware attack cost them excessively. They take the
agriculturists' information also. This investigation features those issues and furthermore gives
helpful answers for the particular issues confronted by the clients. This examination study
highlighted the issues and give answers for reinforcing the security structure for the
improvement of the agriculturists so they can lead their activities securely and safely. The
various approaches of IoT will help definitely help in agriculture to achieve the desired
security, the farmers will have to install antivirus and update them daily, should back up
important files. The limitations of IoT have also been discussed. It is hoped that IoT will
come up new security features that can embellish the overall structure of agriculture.
(Source: Granjal, Monteiro & Silva, 2015, 1294-1312)
Granjal, Monteiro & Silva, 2015 demonstrates the above model in details and the
applications of agriculture with the cloud and database, the data accumulated is stored
securely in the database for future analysis.
iii. Limited features of IoT
Li, Da & Zhao, (2015) stated that the IoT is in testing mode, the farmer can still get
enough advantages from the IoT services, though in mere future they will get more benefits
from the IoT.
4. Conclusion
It can be concluded from the above discourse that IoT has a lot to offer to the farmer
and agriculture. The quality has enhanced a great deal with the appearance of IoT. The
different innovations related with the agriculture have changed the sustenance quality. The
agriculturists dependably remain associated with the Internet and utilize the network system
for the advantages. Presently, there is a downside, since the intruders utilize the unreliable
system they fall into prey of the cyber attackers, they attack their devices and lock their
devices and requesting cash. The ransomware attack cost them excessively. They take the
agriculturists' information also. This investigation features those issues and furthermore gives
helpful answers for the particular issues confronted by the clients. This examination study
highlighted the issues and give answers for reinforcing the security structure for the
improvement of the agriculturists so they can lead their activities securely and safely. The
various approaches of IoT will help definitely help in agriculture to achieve the desired
security, the farmers will have to install antivirus and update them daily, should back up
important files. The limitations of IoT have also been discussed. It is hoped that IoT will
come up new security features that can embellish the overall structure of agriculture.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13INTERNET OF THINGS
5. References
Abomhara, M., & Køien, G. M. (2014, May). Security and privacy in the Internet of Things:
Current status and open issues. In Privacy and Security in Mobile Systems (PRISMS),
2014 International Conference on (pp. 1-8). IEEE.
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., & Ayyash, M. (2015). Internet
of things: A survey on enabling technologies, protocols, and applications. IEEE
Communications Surveys & Tutorials, 17(4), 2347-2376.
Anwar, R. W., Bakhtiari, M., Zainal, A., Abdullah, A. H., Qureshi, K. N., Computing, F., &
Bahru, J. (2014). Security issues and attacks in wireless sensor network. World
Applied Sciences Journal, 30(10), 1224-1227.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of
Internet of Things. arXiv preprint arXiv:1501.02211.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing
and internet of things: a survey. Future Generation Computer Systems, 56, 684-700.
Chen, S., Xu, H., Liu, D., Hu, B., & Wang, H. (2014). A vision of IoT: Applications,
challenges, and opportunities with china perspective. IEEE Internet of Things
journal, 1(4), 349-359.
Da Xu, L., He, W., & Li, S. (2014). Internet of things in industries: A survey. IEEE
Transactions on industrial informatics, 10(4), 2233-2243.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
5. References
Abomhara, M., & Køien, G. M. (2014, May). Security and privacy in the Internet of Things:
Current status and open issues. In Privacy and Security in Mobile Systems (PRISMS),
2014 International Conference on (pp. 1-8). IEEE.
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., & Ayyash, M. (2015). Internet
of things: A survey on enabling technologies, protocols, and applications. IEEE
Communications Surveys & Tutorials, 17(4), 2347-2376.
Anwar, R. W., Bakhtiari, M., Zainal, A., Abdullah, A. H., Qureshi, K. N., Computing, F., &
Bahru, J. (2014). Security issues and attacks in wireless sensor network. World
Applied Sciences Journal, 30(10), 1224-1227.
Borgohain, T., Kumar, U., & Sanyal, S. (2015). Survey of security and privacy issues of
Internet of Things. arXiv preprint arXiv:1501.02211.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing
and internet of things: a survey. Future Generation Computer Systems, 56, 684-700.
Chen, S., Xu, H., Liu, D., Hu, B., & Wang, H. (2014). A vision of IoT: Applications,
challenges, and opportunities with china perspective. IEEE Internet of Things
journal, 1(4), 349-359.
Da Xu, L., He, W., & Li, S. (2014). Internet of things in industries: A survey. IEEE
Transactions on industrial informatics, 10(4), 2233-2243.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).

14INTERNET OF THINGS
Granjal, J., Monteiro, E., & Silva, J. S. (2015). Security for the internet of things: a survey of
existing protocols and open research issues. IEEE Communications Surveys &
Tutorials, 17(3), 1294-1312.
Grieco, L. A., Rizzo, A., Colucci, S., Sicari, S., Piro, G., Di Paola, D., & Boggia, G. (2014).
IoT-aided robotics applications: Technological implications, target domains and open
issues. Computer Communications, 54, 32-47.
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A
vision, architectural elements, and future directions. Future generation computer
systems, 29(7), 1645-1660.
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the internet of
things: Perspectives and challenges. Wireless Networks, 20(8), 2481-2501.
Lee, I., & Lee, K. (2015). The Internet of Things (IoT): Applications, investments, and
challenges for enterprises. Business Horizons, 58(4), 431-440.
Li, S., Da Xu, L., & Zhao, S. (2015). The internet of things: a survey. Information Systems
Frontiers, 17(2), 243-259.
Loo, J., Mauri, J. L., & Ortiz, J. H. (Eds.). (2016). Mobile ad hoc networks: current status
and future trends. CRC Press.
Martínez-Pérez, B., De La Torre-Díez, I., & López-Coronado, M. (2015). Privacy and
security in mobile health apps: a review and recommendations. Journal of medical
systems, 39(1), 181.
Granjal, J., Monteiro, E., & Silva, J. S. (2015). Security for the internet of things: a survey of
existing protocols and open research issues. IEEE Communications Surveys &
Tutorials, 17(3), 1294-1312.
Grieco, L. A., Rizzo, A., Colucci, S., Sicari, S., Piro, G., Di Paola, D., & Boggia, G. (2014).
IoT-aided robotics applications: Technological implications, target domains and open
issues. Computer Communications, 54, 32-47.
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of Things (IoT): A
vision, architectural elements, and future directions. Future generation computer
systems, 29(7), 1645-1660.
Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., & Qiu, D. (2014). Security of the internet of
things: Perspectives and challenges. Wireless Networks, 20(8), 2481-2501.
Lee, I., & Lee, K. (2015). The Internet of Things (IoT): Applications, investments, and
challenges for enterprises. Business Horizons, 58(4), 431-440.
Li, S., Da Xu, L., & Zhao, S. (2015). The internet of things: a survey. Information Systems
Frontiers, 17(2), 243-259.
Loo, J., Mauri, J. L., & Ortiz, J. H. (Eds.). (2016). Mobile ad hoc networks: current status
and future trends. CRC Press.
Martínez-Pérez, B., De La Torre-Díez, I., & López-Coronado, M. (2015). Privacy and
security in mobile health apps: a review and recommendations. Journal of medical
systems, 39(1), 181.

15INTERNET OF THINGS
Matharu, G. S., Upadhyay, P., & Chaudhary, L. (2014, December). The Internet of Things:
challenges & security issues. In Emerging Technologies (ICET), 2014 International
Conference on (pp. 54-59). IEEE.
Sicari, S., Rizzardi, A., Grieco, L. A., & Coen-Porisini, A. (2015). Security, privacy and trust
in Internet of Things: The road ahead. Computer Networks, 76, 146-164.
Trappe, W., Howard, R., & Moore, R. S. (2015). Low-energy security: Limits and
opportunities in the internet of things. IEEE Security & Privacy, 13(1), 14-21.
Whitmore, A., Agarwal, A., & Da Xu, L. (2015). The Internet of Things—A survey of topics
and trends. Information Systems Frontiers, 17(2), 261-274.
Matharu, G. S., Upadhyay, P., & Chaudhary, L. (2014, December). The Internet of Things:
challenges & security issues. In Emerging Technologies (ICET), 2014 International
Conference on (pp. 54-59). IEEE.
Sicari, S., Rizzardi, A., Grieco, L. A., & Coen-Porisini, A. (2015). Security, privacy and trust
in Internet of Things: The road ahead. Computer Networks, 76, 146-164.
Trappe, W., Howard, R., & Moore, R. S. (2015). Low-energy security: Limits and
opportunities in the internet of things. IEEE Security & Privacy, 13(1), 14-21.
Whitmore, A., Agarwal, A., & Da Xu, L. (2015). The Internet of Things—A survey of topics
and trends. Information Systems Frontiers, 17(2), 261-274.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




