LAN Infrastructure: Design, Security, Performance and Management
VerifiedAdded on 2024/05/20
|37
|5933
|184
Report
AI Summary
This report provides a detailed analysis of Local Area Network (LAN) technologies, focusing on their implementation, security, and management within an organization, specifically FootFall Field Marketing. It critically evaluates various LAN technologies such as Ethernet, WLAN, and Token Ring, highlighting their advantages and disadvantages. The report also examines traffic-intensive services and their impact on network performance, discussing Quality of Service (QoS) techniques for optimization. Security concerns, including viruses and unauthorized access, are addressed with recommendations for switch port control, Access Control Lists (ACLs), wireless security measures, and data encryption. The report further details the design and configuration of a LAN infrastructure, including component suitability, network security implementation, and testing procedures. Finally, it discusses network monitoring and troubleshooting strategies to improve security, reliability, and performance, offering recommendations for resolving LAN issues and evaluating network performance.

LOCAL AREA NETWORK
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
LO 1.................................................................................................................................................2
1.1critically evaluate different LAN technologies.......................................................................2
1.2 critically analyse traffic intensive services and their performance........................................6
1.3 Discuss LAN concerns and make recommendations to sustain network security, reliability
and performance..........................................................................................................................9
LO2................................................................................................................................................12
2.1 design a LAN infrastructure for the company which will facilitate all of their requirements
...................................................................................................................................................12
2.2 critically evaluate the suitability of LAN components........................................................14
LO3................................................................................................................................................16
3.1 build and configure a LAN (including services) to meet a given requirement...................16
3.2 implement network security on a LAN...............................................................................20
3.3 critically review and test a LAN..........................................................................................24
LO4................................................................................................................................................27
4.1 critically discuss how this LAN infrastructure will be monitored and managed (via
troubleshooting) if there is any issue during post implementation period.................................27
4.2 Resolve LAN issues to improve security, reliability and performance...............................28
4.3 critically evaluate the performance of a LAN.....................................................................30
CONCLUSION..............................................................................................................................32
REFERENCES..............................................................................................................................33
INTRODUCTION...........................................................................................................................1
LO 1.................................................................................................................................................2
1.1critically evaluate different LAN technologies.......................................................................2
1.2 critically analyse traffic intensive services and their performance........................................6
1.3 Discuss LAN concerns and make recommendations to sustain network security, reliability
and performance..........................................................................................................................9
LO2................................................................................................................................................12
2.1 design a LAN infrastructure for the company which will facilitate all of their requirements
...................................................................................................................................................12
2.2 critically evaluate the suitability of LAN components........................................................14
LO3................................................................................................................................................16
3.1 build and configure a LAN (including services) to meet a given requirement...................16
3.2 implement network security on a LAN...............................................................................20
3.3 critically review and test a LAN..........................................................................................24
LO4................................................................................................................................................27
4.1 critically discuss how this LAN infrastructure will be monitored and managed (via
troubleshooting) if there is any issue during post implementation period.................................27
4.2 Resolve LAN issues to improve security, reliability and performance...............................28
4.3 critically evaluate the performance of a LAN.....................................................................30
CONCLUSION..............................................................................................................................32
REFERENCES..............................................................................................................................33

LIST OF TABLES
Table 1: Table representing test feature of the LAN.....................................................................24
Table 2: Table For Evaluating The Network Performance...........................................................30
Table 1: Table representing test feature of the LAN.....................................................................24
Table 2: Table For Evaluating The Network Performance...........................................................30
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF FIGURES
Figure 1: Ethernet connection using the Ethernet cable..................................................................2
Figure 2: Wired Ethernet network using fibre optic cable..............................................................3
Figure 3: Wireless Ethernet Network using NIC.............................................................................3
Figure 4: Wireless LAN...................................................................................................................4
Figure 5: Interconnected devices using token ring..........................................................................5
Figure 6: Port security configuration script.....................................................................................9
Figure 7: ACLs used for network security....................................................................................10
Figure 8: Ingress and Egress of ACLs...........................................................................................10
Figure 9: Network Design For The Organisation..........................................................................12
Figure 10: Switch configuration...................................................................................................16
Figure 11: Configuration of a wireless router with Class C IP address.........................................17
Figure 12: Firewall configuration on server..................................................................................17
Figure 13: Window server manager's dashboard...........................................................................18
Figure 14: Table representing the address location in class C.......................................................19
Figure 15: Configuration of Local client device............................................................................19
Figure 16: Steps for configuring of VLAN membership...............................................................20
Figure 17: Implementation of ACLs..............................................................................................21
Figure 18: Configuration of DNS..................................................................................................21
Figure 19: Authentication of server service...................................................................................22
Figure 20: Configuration of a switch in first building...................................................................23
Figure 21:Configurations of network design.................................................................................23
Figure 22: Successful Ping test for connecting computers to same department and Ping test fails
when done for connecting computers of the management...........................................................24
Figure 1: Ethernet connection using the Ethernet cable..................................................................2
Figure 2: Wired Ethernet network using fibre optic cable..............................................................3
Figure 3: Wireless Ethernet Network using NIC.............................................................................3
Figure 4: Wireless LAN...................................................................................................................4
Figure 5: Interconnected devices using token ring..........................................................................5
Figure 6: Port security configuration script.....................................................................................9
Figure 7: ACLs used for network security....................................................................................10
Figure 8: Ingress and Egress of ACLs...........................................................................................10
Figure 9: Network Design For The Organisation..........................................................................12
Figure 10: Switch configuration...................................................................................................16
Figure 11: Configuration of a wireless router with Class C IP address.........................................17
Figure 12: Firewall configuration on server..................................................................................17
Figure 13: Window server manager's dashboard...........................................................................18
Figure 14: Table representing the address location in class C.......................................................19
Figure 15: Configuration of Local client device............................................................................19
Figure 16: Steps for configuring of VLAN membership...............................................................20
Figure 17: Implementation of ACLs..............................................................................................21
Figure 18: Configuration of DNS..................................................................................................21
Figure 19: Authentication of server service...................................................................................22
Figure 20: Configuration of a switch in first building...................................................................23
Figure 21:Configurations of network design.................................................................................23
Figure 22: Successful Ping test for connecting computers to same department and Ping test fails
when done for connecting computers of the management...........................................................24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
Local area network is a computer network that is used for linking computers over a restricted
geographical area that can be a building or an organisation. In the present report, FootFall Field
Marketing is considered as a case study for studying LAN. The organisation is medium sized that
is involved in function like marketing and sales. The report discusses about various LAN
technologies, traffic intensive services and security concerns related to LAN along with
recommendations regarding maintenance of the network in terms of reliability, security and
performance. The report discusses about the infrastructure of the LAN for the organisation with
suitability network components. The present report analyses the configuration of LAN for the
organisation along with the implementation of network security and testing of LAN in regarding
with expected and actual result achieved. Lastly, the report also studies about checking and
troubleshoot LAN errors. Proper recommendation regarding the issues related to LAN is also
discussed in the report for improving reliability, security and performance are provided in the
report.
1
Local area network is a computer network that is used for linking computers over a restricted
geographical area that can be a building or an organisation. In the present report, FootFall Field
Marketing is considered as a case study for studying LAN. The organisation is medium sized that
is involved in function like marketing and sales. The report discusses about various LAN
technologies, traffic intensive services and security concerns related to LAN along with
recommendations regarding maintenance of the network in terms of reliability, security and
performance. The report discusses about the infrastructure of the LAN for the organisation with
suitability network components. The present report analyses the configuration of LAN for the
organisation along with the implementation of network security and testing of LAN in regarding
with expected and actual result achieved. Lastly, the report also studies about checking and
troubleshoot LAN errors. Proper recommendation regarding the issues related to LAN is also
discussed in the report for improving reliability, security and performance are provided in the
report.
1

LO 1
1.1critically evaluate different LAN technologies
LAN stands for Local Area Network which is a part of computer network for connecting various
terminals located in a place or a building for proper communication among them to share
information and resources. Devices in the network can be connected either using or wires or
wireless. All the devices in the network can receive and send information that is addressed to it
specifically. Some of the examples of LAN technologies are Ethernet, WLAN (using 802.11),
and Token Ring. Standards are sets of rules that are followed for data transmission.
Ethernet
One of the most commonly used LAN technology is Ethernet because it is quite easy to
understand, implementing the network structure is simple and maintenance and implementation
is very less when compared with other LAN technologies. Under 802.3 of IEEE standards,
Ethernet is defined. In Ethernet computers are connected using cables and this network can
connect 1024 workstations and computers.
In terms of topology Ethernet is very flexible. Ethernet is capable of providing 100mpbs speed
but most of the network used only 10mpbs.
Figure 1: Ethernet connection using the Ethernet cable
2
1.1critically evaluate different LAN technologies
LAN stands for Local Area Network which is a part of computer network for connecting various
terminals located in a place or a building for proper communication among them to share
information and resources. Devices in the network can be connected either using or wires or
wireless. All the devices in the network can receive and send information that is addressed to it
specifically. Some of the examples of LAN technologies are Ethernet, WLAN (using 802.11),
and Token Ring. Standards are sets of rules that are followed for data transmission.
Ethernet
One of the most commonly used LAN technology is Ethernet because it is quite easy to
understand, implementing the network structure is simple and maintenance and implementation
is very less when compared with other LAN technologies. Under 802.3 of IEEE standards,
Ethernet is defined. In Ethernet computers are connected using cables and this network can
connect 1024 workstations and computers.
In terms of topology Ethernet is very flexible. Ethernet is capable of providing 100mpbs speed
but most of the network used only 10mpbs.
Figure 1: Ethernet connection using the Ethernet cable
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 2: Wired Ethernet network using fibre optic cable
In wired Ethernet all the devices in the network are connected with one other using a fibre optic
cable and the network is mostly within 10km (Kumar and Malhotra, 2015). To resolve issues of
collisions for sending information CSMA/CD is used. While on other hand in wireless Ethernet,
systems are connected using NIC (Network Interface Card). NIC uses radio waves for
establishing communication using a wireless switch.
Figure 3: Wireless Ethernet Network using NIC
Wireless LAN (WAN)
3
In wired Ethernet all the devices in the network are connected with one other using a fibre optic
cable and the network is mostly within 10km (Kumar and Malhotra, 2015). To resolve issues of
collisions for sending information CSMA/CD is used. While on other hand in wireless Ethernet,
systems are connected using NIC (Network Interface Card). NIC uses radio waves for
establishing communication using a wireless switch.
Figure 3: Wireless Ethernet Network using NIC
Wireless LAN (WAN)
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WAN or wireless LAN is also called as LAWN (Local Area wireless Network) in this type of
network mobile devices is capable of connecting to a LAN using a wireless connection. WLAN
is defined by using radio or wireless connection (Rao et al 2017). It is well defined by IEEE
802.11. This network allows the user to move free around the coverage area of the network.
Figure 4: Wireless LAN
Every element of WLAN is considered as station that is categories as either clients or access
point. APs are the one that receives or transmits signals using radio frequency operating like a
router whereas client can be a workstation, computer or phones.
Token ring
Token ring network also falls in LAN; here all the computers in the network are interconnected
in star topology or in ring topology. And logical token are being passed from one host to other.
In a network using token ring does not support colliding of data packets as data here can be sent
by only the token holders. IEEE standard defining this network is 802.5. Data in this network can
be sent at speed of 4, 16 and 100Mpbs.
4
network mobile devices is capable of connecting to a LAN using a wireless connection. WLAN
is defined by using radio or wireless connection (Rao et al 2017). It is well defined by IEEE
802.11. This network allows the user to move free around the coverage area of the network.
Figure 4: Wireless LAN
Every element of WLAN is considered as station that is categories as either clients or access
point. APs are the one that receives or transmits signals using radio frequency operating like a
router whereas client can be a workstation, computer or phones.
Token ring
Token ring network also falls in LAN; here all the computers in the network are interconnected
in star topology or in ring topology. And logical token are being passed from one host to other.
In a network using token ring does not support colliding of data packets as data here can be sent
by only the token holders. IEEE standard defining this network is 802.5. Data in this network can
be sent at speed of 4, 16 and 100Mpbs.
4
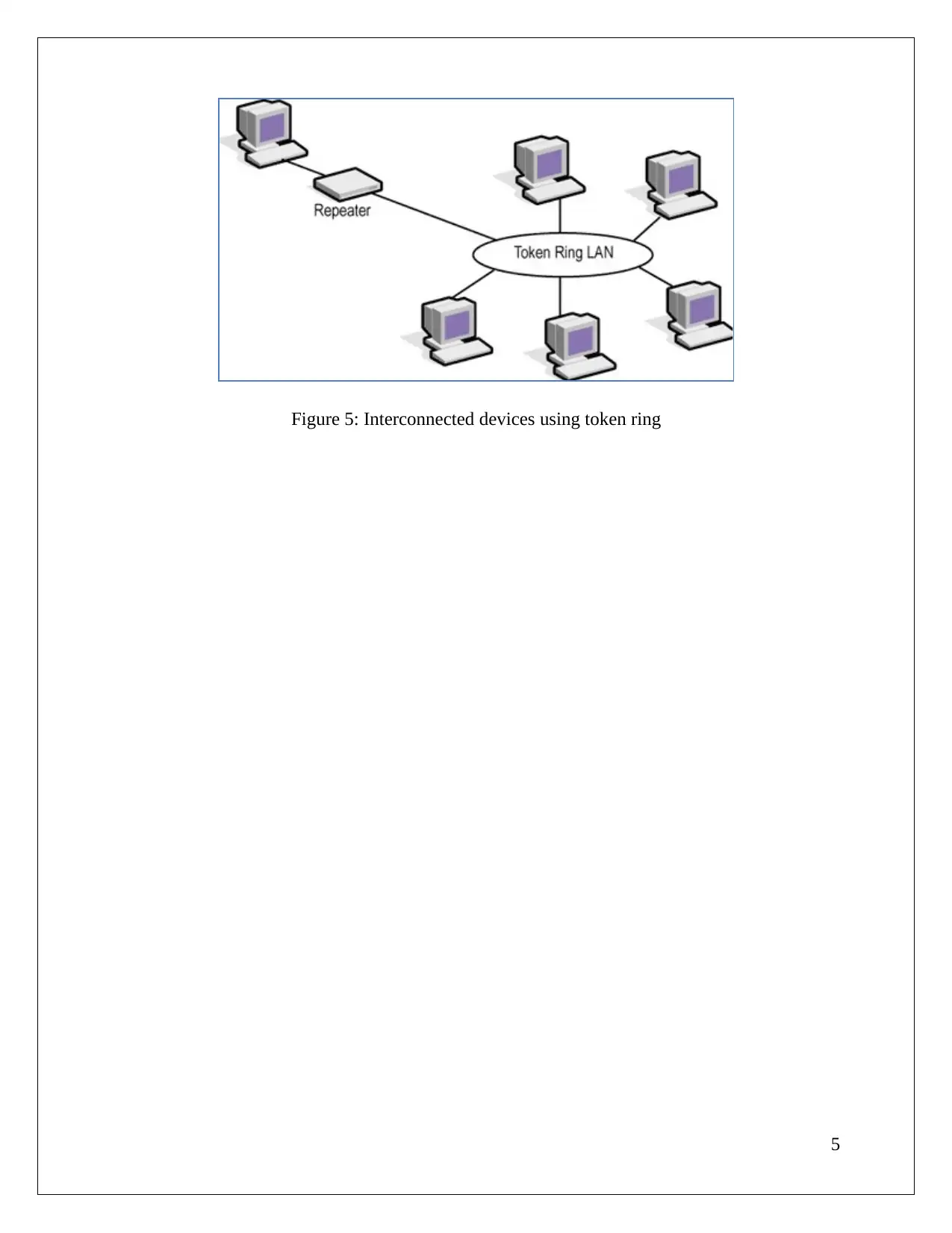
Figure 5: Interconnected devices using token ring
5
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.2 critically analyse traffic intensive services and their performance
QoS or Quality of service in the ability of network to provide maximum output by achieving
maximum possible bandwidth along with overcoming of other network issue related to
performance such as error rate, latency and uptime. Proper management of quality of service is
required in a network for proper management and controlling the resources by prioritising data in
the network (Ali, 2017). QoS of a network can effectively improve by using various techniques
of traffic shaping. Main aim of QoS technologies applied in a network is make video, voice and
data union more clear to all the end users. QoS is considered to be an essential element for an
efficient network convergence of video audio and various data in the network.
The first aim of the QoS policy applied in any network is to identify the traffic that needs
attention. Various marking tools are used for doing these some of them has been mentioned
below:
In Layer 2, Multiprotocol Label Switching Experimental Values, 802.1Q Class of
Service bits.
In Layer 3, IP Precedence, Differentiated Services Code Points and IP Explicit
Congestion Notification
In Layer 4 , TCP/UDP and source-destination ports
In case of Layer 7, Network Based Application Recognition is used for signing
applications.
802.1Q/p CoS
In layer 2, Ethernet frames can possibly be marked according to their importance. It can be done
effectively for which User Priority bits 802.1p is set from the header 802.1Qr. Marking is
possible for only 3 bits in 802.1p. In the Ethernet frame of layer 2 it is possible to set only 8
different classes of service.
DSCP
In modern 3 IP network qualities of services can be provided by using DSCP or Differentiated
Services Code Point. For classification of packets in the network, DSCP mainly uses 6-bit field
for Differentiated Services in IP header. DiffServ referred to a networking architecture. Here
6
QoS or Quality of service in the ability of network to provide maximum output by achieving
maximum possible bandwidth along with overcoming of other network issue related to
performance such as error rate, latency and uptime. Proper management of quality of service is
required in a network for proper management and controlling the resources by prioritising data in
the network (Ali, 2017). QoS of a network can effectively improve by using various techniques
of traffic shaping. Main aim of QoS technologies applied in a network is make video, voice and
data union more clear to all the end users. QoS is considered to be an essential element for an
efficient network convergence of video audio and various data in the network.
The first aim of the QoS policy applied in any network is to identify the traffic that needs
attention. Various marking tools are used for doing these some of them has been mentioned
below:
In Layer 2, Multiprotocol Label Switching Experimental Values, 802.1Q Class of
Service bits.
In Layer 3, IP Precedence, Differentiated Services Code Points and IP Explicit
Congestion Notification
In Layer 4 , TCP/UDP and source-destination ports
In case of Layer 7, Network Based Application Recognition is used for signing
applications.
802.1Q/p CoS
In layer 2, Ethernet frames can possibly be marked according to their importance. It can be done
effectively for which User Priority bits 802.1p is set from the header 802.1Qr. Marking is
possible for only 3 bits in 802.1p. In the Ethernet frame of layer 2 it is possible to set only 8
different classes of service.
DSCP
In modern 3 IP network qualities of services can be provided by using DSCP or Differentiated
Services Code Point. For classification of packets in the network, DSCP mainly uses 6-bit field
for Differentiated Services in IP header. DiffServ referred to a networking architecture. Here
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

managing and classification of the traffic in the network in an organisation is done using a very
scalable and simple mechanism.
In the above figure the 1st six bit represents code-point which affects mainly per hob behaviour of
every node. When two devices are connected in a network, to achieve proper QoS those devices
must be connected and configured end-to-end.
IP precedence
ToS has 8 bit and the first three bits denotes precedence. When an IP pocket is more significant
then value of precedence is higher (Karakus and Durresi, 2017). If any kind of congestion is
found in the network, then the packet with low precedence will be dropped from the network by
the router. ToS is a network has the bit that denotes the kind of throughput, delay, reliability the
user wants.
IPP value Reserved
6 and 7 Network control traffic like routing
5 Voice
4 Video conferencing and streaming video.
3 voice control
2and 1 Data applications.
7
scalable and simple mechanism.
In the above figure the 1st six bit represents code-point which affects mainly per hob behaviour of
every node. When two devices are connected in a network, to achieve proper QoS those devices
must be connected and configured end-to-end.
IP precedence
ToS has 8 bit and the first three bits denotes precedence. When an IP pocket is more significant
then value of precedence is higher (Karakus and Durresi, 2017). If any kind of congestion is
found in the network, then the packet with low precedence will be dropped from the network by
the router. ToS is a network has the bit that denotes the kind of throughput, delay, reliability the
user wants.
IPP value Reserved
6 and 7 Network control traffic like routing
5 Voice
4 Video conferencing and streaming video.
3 voice control
2and 1 Data applications.
7

0 default marking value
8
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 37
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





