LAN Infrastructure: Design, Security, Reliability and Performance
VerifiedAdded on 2024/05/20
|56
|7645
|229
Report
AI Summary
This report provides a comprehensive overview of Local Area Network (LAN) technologies, focusing on their impact, design, implementation, and management. It begins by evaluating different LAN technologies such as wired, wireless, and virtual LANs (VLANs), discussing their characteristics, advantages, and disadvantages. The report analyzes traffic-intensive services like Voice-over-IP (VoIP), Video-on-Demand (VoD), and audio/video streaming, examining their performance implications and quality-of-service (QoS) requirements. Furthermore, it addresses LAN security concerns and offers recommendations for sustaining network security, reliability, and performance. The report details the design and implementation of a LAN infrastructure, covering component suitability, network configuration, and security measures. It also includes testing procedures and troubleshooting strategies to ensure optimal LAN performance. Finally, the report discusses tools for monitoring and troubleshooting LANs, resolving security and performance issues, and critically evaluating overall LAN performance.

LOCAL AREA NETOWRK
0
0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction:....................................................................................................................................4
LO1 Understand the impact of LAN technologies...........................................................................5
A.C 1.1 critically evaluate different LAN technologies.................................................................5
A.C 1.2 critically analyse traffic intensive services and their performance...............................15
A.C 1.3 Discuss LAN concerns and make recommendations to sustain network security,
reliability and performance.......................................................................................................19
LO2 - Be able to design LAN infrastructures..................................................................................21
A.C 2.1 design a LAN infrastructure to meet a given requirement.....................................21
A.C 2.2 critically evaluate the suitability of LAN components...................................................24
LO3- Be able to implement LAN infrastructures............................................................................25
A.C 3.1 build and configure a LAN (including services) to meet a given requirement..............25
A.C 3.2 implement network security on a LAN..........................................................................33
A.C 3.3 critically review and test a LAN.....................................................................................42
LO4- Be able to manage LAN infrastructures................................................................................46
AC 4.1 Monitor and troubleshoot a LAN................................................................................46
AC 4.2 Resolve LAN issues to improve security, reliability and performance........................47
AC 4.3 Critically evaluate the performance of a LAN.............................................................49
Conclusion:.....................................................................................................................................50
References.....................................................................................................................................51
1
Introduction:....................................................................................................................................4
LO1 Understand the impact of LAN technologies...........................................................................5
A.C 1.1 critically evaluate different LAN technologies.................................................................5
A.C 1.2 critically analyse traffic intensive services and their performance...............................15
A.C 1.3 Discuss LAN concerns and make recommendations to sustain network security,
reliability and performance.......................................................................................................19
LO2 - Be able to design LAN infrastructures..................................................................................21
A.C 2.1 design a LAN infrastructure to meet a given requirement.....................................21
A.C 2.2 critically evaluate the suitability of LAN components...................................................24
LO3- Be able to implement LAN infrastructures............................................................................25
A.C 3.1 build and configure a LAN (including services) to meet a given requirement..............25
A.C 3.2 implement network security on a LAN..........................................................................33
A.C 3.3 critically review and test a LAN.....................................................................................42
LO4- Be able to manage LAN infrastructures................................................................................46
AC 4.1 Monitor and troubleshoot a LAN................................................................................46
AC 4.2 Resolve LAN issues to improve security, reliability and performance........................47
AC 4.3 Critically evaluate the performance of a LAN.............................................................49
Conclusion:.....................................................................................................................................50
References.....................................................................................................................................51
1

List of Figures:
Figure 1: Wired LAN Network..........................................................................................................6
Figure 2: Wireless LAN Network......................................................................................................6
Figure 3: Virtual LAN Network.........................................................................................................8
Figure 4: Repeaters..........................................................................................................................9
Figure 5: Switches..........................................................................................................................10
Figure 6: Hub..................................................................................................................................10
Figure 7: Bridges............................................................................................................................11
Figure 8: Router.............................................................................................................................12
Figure 9: Coaxial cable...................................................................................................................12
Figure 10: Fibre optic cable............................................................................................................13
Figure 11: an Unshielded twisted pair...........................................................................................14
Figure 12: STP cable.......................................................................................................................14
Figure 13: working of Voice-over-IP..............................................................................................15
Figure 14: Video-on-Demand.........................................................................................................16
Figure 15: Audio and video streaming...........................................................................................17
Figure 16: Star Topologies.............................................................................................................22
Figure 17: Design View organization LAN Network.......................................................................26
Figure 18: Metadata part one........................................................................................................27
Figure 19: Meta Data part 2...........................................................................................................28
Figure 20: Metadata part 3............................................................................................................29
Figure 21: Metadata part 4............................................................................................................30
Figure 22: Metadata part 5............................................................................................................30
Figure 23: DNS (Domain Name Server) and HTTP service in the LAN network.............................31
Figure 24: DHCP Server in the LAN network..................................................................................31
Figure 25: Network Design on the Cisco packet tracer.................................................................32
Figure 26: Virtual Local Area Network in the network..................................................................34
Figure 27: Router 0 configuration part one...................................................................................35
Figure 28: Router 0 configuration part two...................................................................................36
2
Figure 1: Wired LAN Network..........................................................................................................6
Figure 2: Wireless LAN Network......................................................................................................6
Figure 3: Virtual LAN Network.........................................................................................................8
Figure 4: Repeaters..........................................................................................................................9
Figure 5: Switches..........................................................................................................................10
Figure 6: Hub..................................................................................................................................10
Figure 7: Bridges............................................................................................................................11
Figure 8: Router.............................................................................................................................12
Figure 9: Coaxial cable...................................................................................................................12
Figure 10: Fibre optic cable............................................................................................................13
Figure 11: an Unshielded twisted pair...........................................................................................14
Figure 12: STP cable.......................................................................................................................14
Figure 13: working of Voice-over-IP..............................................................................................15
Figure 14: Video-on-Demand.........................................................................................................16
Figure 15: Audio and video streaming...........................................................................................17
Figure 16: Star Topologies.............................................................................................................22
Figure 17: Design View organization LAN Network.......................................................................26
Figure 18: Metadata part one........................................................................................................27
Figure 19: Meta Data part 2...........................................................................................................28
Figure 20: Metadata part 3............................................................................................................29
Figure 21: Metadata part 4............................................................................................................30
Figure 22: Metadata part 5............................................................................................................30
Figure 23: DNS (Domain Name Server) and HTTP service in the LAN network.............................31
Figure 24: DHCP Server in the LAN network..................................................................................31
Figure 25: Network Design on the Cisco packet tracer.................................................................32
Figure 26: Virtual Local Area Network in the network..................................................................34
Figure 27: Router 0 configuration part one...................................................................................35
Figure 28: Router 0 configuration part two...................................................................................36
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Figure 29: Router 0 configuration part three................................................................................37
Figure 30: Router 1 configuration part one...................................................................................38
Figure 31: Router 1 configuration part two...................................................................................39
Figure 32: Router 1 configuration part three................................................................................40
Figure 33: DHCP Configuration in the LAN network......................................................................40
Figure 34: DNS Configuration in the LAN network........................................................................41
Figure 35: Test Scenario one..........................................................................................................43
Figure 36: Test Scenario two.........................................................................................................44
Figure 37: Test Scenario three.......................................................................................................44
Figure 38: Test Scenario four.........................................................................................................45
List of Table
Table 1: Difference between Ethernet IEEE 802.3 and Wifi IEEE 802.11........................................7
Table 2: IP Precedence Table.........................................................................................................18
3
Figure 30: Router 1 configuration part one...................................................................................38
Figure 31: Router 1 configuration part two...................................................................................39
Figure 32: Router 1 configuration part three................................................................................40
Figure 33: DHCP Configuration in the LAN network......................................................................40
Figure 34: DNS Configuration in the LAN network........................................................................41
Figure 35: Test Scenario one..........................................................................................................43
Figure 36: Test Scenario two.........................................................................................................44
Figure 37: Test Scenario three.......................................................................................................44
Figure 38: Test Scenario four.........................................................................................................45
List of Table
Table 1: Difference between Ethernet IEEE 802.3 and Wifi IEEE 802.11........................................7
Table 2: IP Precedence Table.........................................................................................................18
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction:
LAN is a local area network which provides the service medium size area. It offered service in
school, college, small office or firm. LAN managed sharing, communication, and exchange in the
network. It may be useful for The FootFall Field Marketing organization. LAN will offer
interconnection between offices and their departments. I have designed a local area network
report for the FootFall Field Marketing organization. There are four sections in the report.
In the first section, I will be describing a different type of technology Technologies such as wired
and wireless LAN network. Then, virtual area network, the traffic intensive services, and LAN
components will be discussed which help to design the network. In the second section, I will be
creating LAN infrastructure according to client requirements and evaluate of LAN components.
In the third section, I will be implementing and configuration the LAN network. I will be
implemented security in the LAN Network and test the network. In the fourth section, I will be
explaining tools that will be monitoring and troubleshooting the LAN network. Then,
performance, reliability, and security issue of LAN network will be resolved and measured the
LAN performance.
4
LAN is a local area network which provides the service medium size area. It offered service in
school, college, small office or firm. LAN managed sharing, communication, and exchange in the
network. It may be useful for The FootFall Field Marketing organization. LAN will offer
interconnection between offices and their departments. I have designed a local area network
report for the FootFall Field Marketing organization. There are four sections in the report.
In the first section, I will be describing a different type of technology Technologies such as wired
and wireless LAN network. Then, virtual area network, the traffic intensive services, and LAN
components will be discussed which help to design the network. In the second section, I will be
creating LAN infrastructure according to client requirements and evaluate of LAN components.
In the third section, I will be implementing and configuration the LAN network. I will be
implemented security in the LAN Network and test the network. In the fourth section, I will be
explaining tools that will be monitoring and troubleshooting the LAN network. Then,
performance, reliability, and security issue of LAN network will be resolved and measured the
LAN performance.
4
LO1 Understand the impact of LAN technologies
A.C 1.1 critically evaluate different LAN technologies
LAN is a local area network that built for the sharing of service and resources like as
applications, files, internet access, games, email, and printers. LAN network designs for the
home, office building, and school because it provides the service where a group of computers
near each other. In the Traditional network offered Single LAN service but Modern network
offered a number of LAN service in the building (Mitchell, 2017).
Type of LAN Network:
Wired LAN Wireless LAN
Wired network works on high bandwidth but
provides the low bandwidth variability.
Wireless network works on Low bandwidth
but provides the high bandwidth variability.
It can listen on the wire. It has hidden terminal problem
It uses high power machines and resources
machines.
It uses Low power machines and resources
machines.
Packet delay is low. Packet delay is high.
Wired LAN needs more security. Wired LAN needs more proximity.
5
A.C 1.1 critically evaluate different LAN technologies
LAN is a local area network that built for the sharing of service and resources like as
applications, files, internet access, games, email, and printers. LAN network designs for the
home, office building, and school because it provides the service where a group of computers
near each other. In the Traditional network offered Single LAN service but Modern network
offered a number of LAN service in the building (Mitchell, 2017).
Type of LAN Network:
Wired LAN Wireless LAN
Wired network works on high bandwidth but
provides the low bandwidth variability.
Wireless network works on Low bandwidth
but provides the high bandwidth variability.
It can listen on the wire. It has hidden terminal problem
It uses high power machines and resources
machines.
It uses Low power machines and resources
machines.
Packet delay is low. Packet delay is high.
Wired LAN needs more security. Wired LAN needs more proximity.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
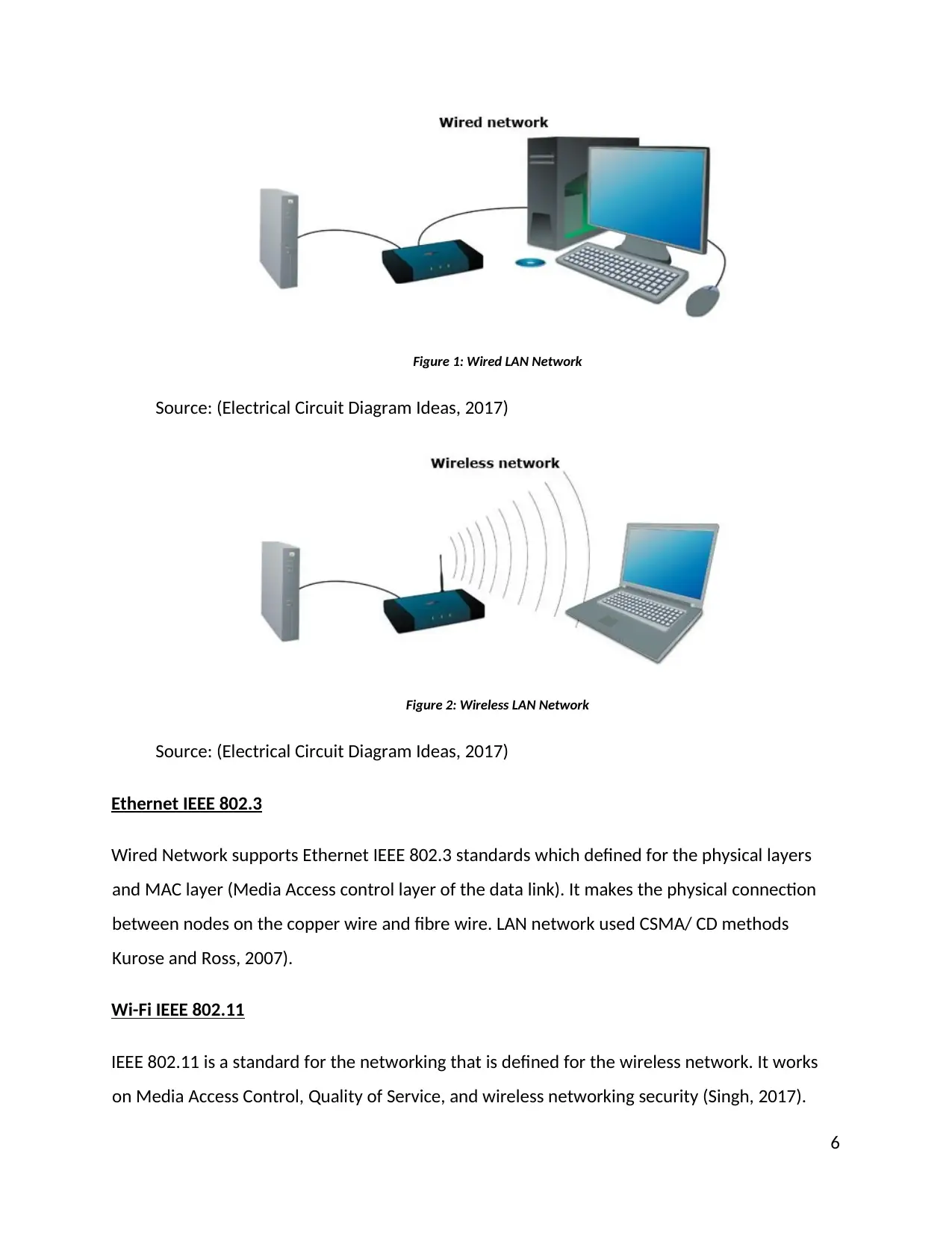
Figure 1: Wired LAN Network
Source: (Electrical Circuit Diagram Ideas, 2017)
Figure 2: Wireless LAN Network
Source: (Electrical Circuit Diagram Ideas, 2017)
Ethernet IEEE 802.3
Wired Network supports Ethernet IEEE 802.3 standards which defined for the physical layers
and MAC layer (Media Access control layer of the data link). It makes the physical connection
between nodes on the copper wire and fibre wire. LAN network used CSMA/ CD methods
Kurose and Ross, 2007).
Wi-Fi IEEE 802.11
IEEE 802.11 is a standard for the networking that is defined for the wireless network. It works
on Media Access Control, Quality of Service, and wireless networking security (Singh, 2017).
6
Source: (Electrical Circuit Diagram Ideas, 2017)
Figure 2: Wireless LAN Network
Source: (Electrical Circuit Diagram Ideas, 2017)
Ethernet IEEE 802.3
Wired Network supports Ethernet IEEE 802.3 standards which defined for the physical layers
and MAC layer (Media Access control layer of the data link). It makes the physical connection
between nodes on the copper wire and fibre wire. LAN network used CSMA/ CD methods
Kurose and Ross, 2007).
Wi-Fi IEEE 802.11
IEEE 802.11 is a standard for the networking that is defined for the wireless network. It works
on Media Access Control, Quality of Service, and wireless networking security (Singh, 2017).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
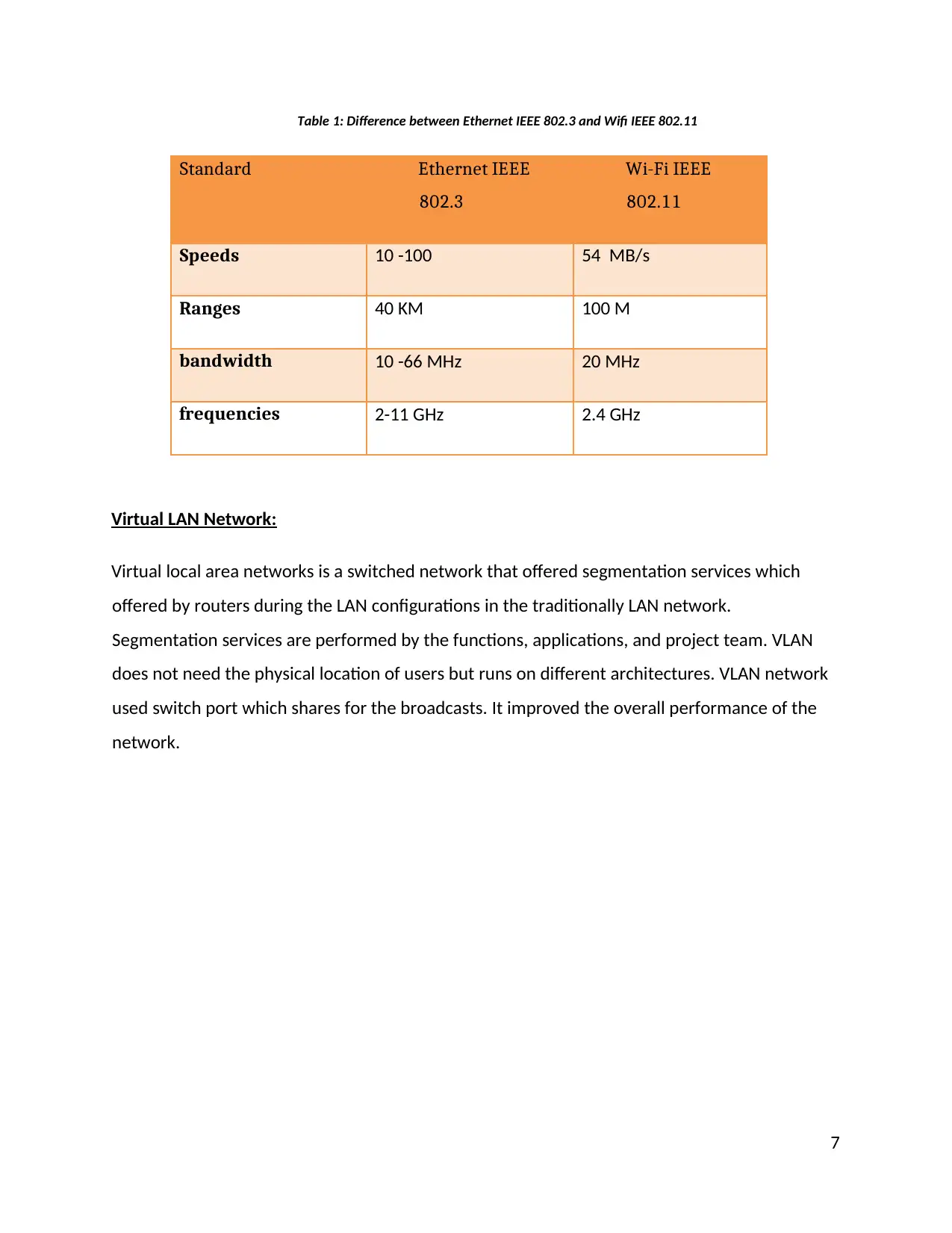
Table 1: Difference between Ethernet IEEE 802.3 and Wifi IEEE 802.11
Standard Ethernet IEEE
802.3
Wi-Fi IEEE
802.11
Speeds 10 -100 54 MB/s
Ranges 40 KM 100 M
bandwidth 10 -66 MHz 20 MHz
frequencies 2-11 GHz 2.4 GHz
Virtual LAN Network:
Virtual local area networks is a switched network that offered segmentation services which
offered by routers during the LAN configurations in the traditionally LAN network.
Segmentation services are performed by the functions, applications, and project team. VLAN
does not need the physical location of users but runs on different architectures. VLAN network
used switch port which shares for the broadcasts. It improved the overall performance of the
network.
7
Standard Ethernet IEEE
802.3
Wi-Fi IEEE
802.11
Speeds 10 -100 54 MB/s
Ranges 40 KM 100 M
bandwidth 10 -66 MHz 20 MHz
frequencies 2-11 GHz 2.4 GHz
Virtual LAN Network:
Virtual local area networks is a switched network that offered segmentation services which
offered by routers during the LAN configurations in the traditionally LAN network.
Segmentation services are performed by the functions, applications, and project team. VLAN
does not need the physical location of users but runs on different architectures. VLAN network
used switch port which shares for the broadcasts. It improved the overall performance of the
network.
7
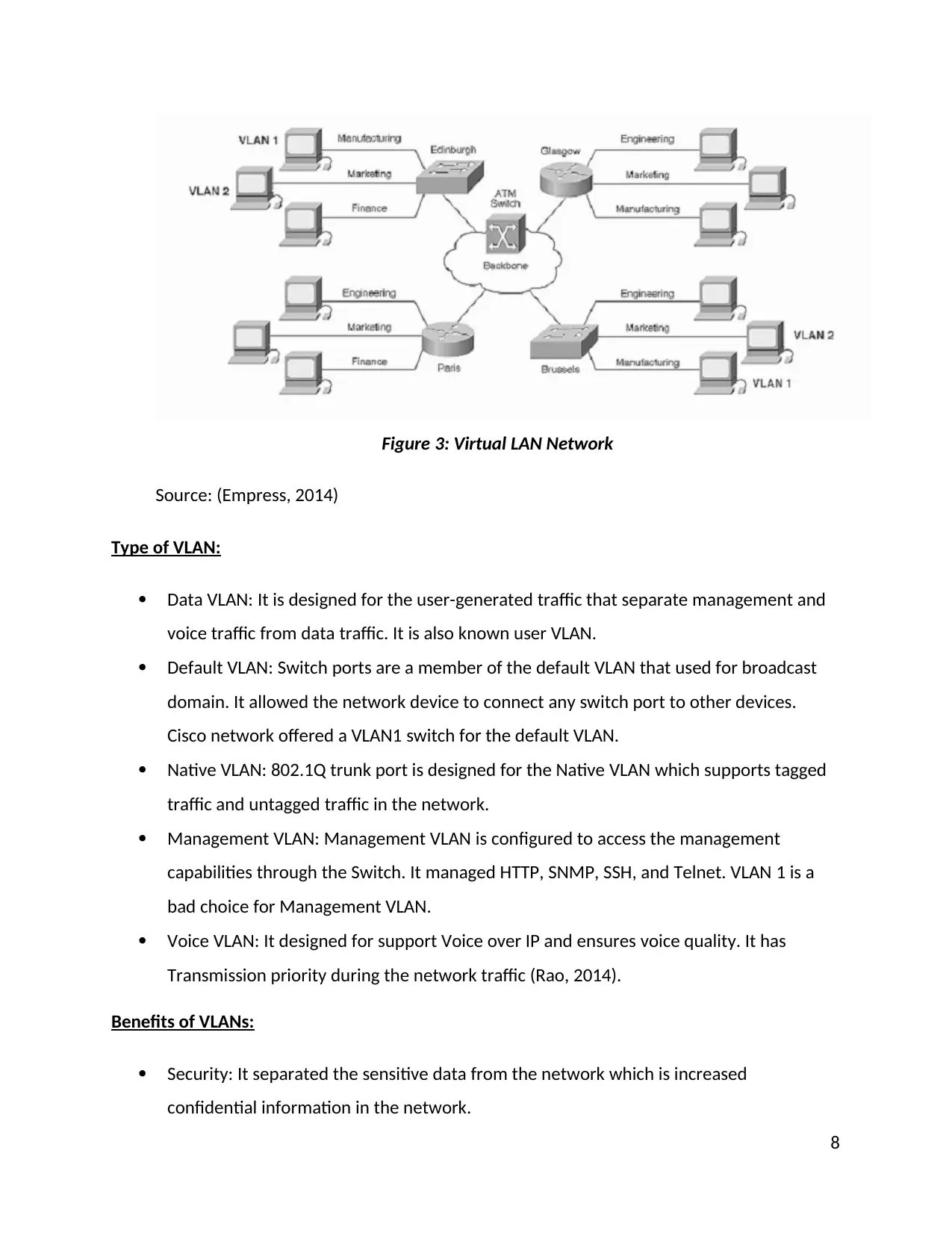
Figure 3: Virtual LAN Network
Source: (Empress, 2014)
Type of VLAN:
Data VLAN: It is designed for the user-generated traffic that separate management and
voice traffic from data traffic. It is also known user VLAN.
Default VLAN: Switch ports are a member of the default VLAN that used for broadcast
domain. It allowed the network device to connect any switch port to other devices.
Cisco network offered a VLAN1 switch for the default VLAN.
Native VLAN: 802.1Q trunk port is designed for the Native VLAN which supports tagged
traffic and untagged traffic in the network.
Management VLAN: Management VLAN is configured to access the management
capabilities through the Switch. It managed HTTP, SNMP, SSH, and Telnet. VLAN 1 is a
bad choice for Management VLAN.
Voice VLAN: It designed for support Voice over IP and ensures voice quality. It has
Transmission priority during the network traffic (Rao, 2014).
Benefits of VLANs:
Security: It separated the sensitive data from the network which is increased
confidential information in the network.
8
Source: (Empress, 2014)
Type of VLAN:
Data VLAN: It is designed for the user-generated traffic that separate management and
voice traffic from data traffic. It is also known user VLAN.
Default VLAN: Switch ports are a member of the default VLAN that used for broadcast
domain. It allowed the network device to connect any switch port to other devices.
Cisco network offered a VLAN1 switch for the default VLAN.
Native VLAN: 802.1Q trunk port is designed for the Native VLAN which supports tagged
traffic and untagged traffic in the network.
Management VLAN: Management VLAN is configured to access the management
capabilities through the Switch. It managed HTTP, SNMP, SSH, and Telnet. VLAN 1 is a
bad choice for Management VLAN.
Voice VLAN: It designed for support Voice over IP and ensures voice quality. It has
Transmission priority during the network traffic (Rao, 2014).
Benefits of VLANs:
Security: It separated the sensitive data from the network which is increased
confidential information in the network.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cost Reduction: VLAN used efficiently the bandwidth and decrease the expensive
network which saved the cost in the network.
Higher Performance: it works in the multiple logical workgroups that reduce network
traffic and increased the performance.
Broadcast storm mitigation: VLANs network reduce the number of the device in the
broadcast storm because it divides the network (Rao, 2014).
LAN Data Communication Equipment
LAN network used repeaters, switches, hubs, bridges, and routers as Data Communication
Equipment.
Repeaters:
It is a physical device which connected two segments of the network that reduced the distance
for the transmission media. Repeater forwards every frame without filtering capability and
amplifier.
Figure 4: Repeaters
Source: (Matrox, 2012)
Switches:
9
network which saved the cost in the network.
Higher Performance: it works in the multiple logical workgroups that reduce network
traffic and increased the performance.
Broadcast storm mitigation: VLANs network reduce the number of the device in the
broadcast storm because it divides the network (Rao, 2014).
LAN Data Communication Equipment
LAN network used repeaters, switches, hubs, bridges, and routers as Data Communication
Equipment.
Repeaters:
It is a physical device which connected two segments of the network that reduced the distance
for the transmission media. Repeater forwards every frame without filtering capability and
amplifier.
Figure 4: Repeaters
Source: (Matrox, 2012)
Switches:
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The switch is a hardware device in the network that connected the number of computer in the
local area network. It identical to hubs but switch work more intelligence in the network.
Switch received the data packets and determines their destination device and source device
then tramismted.it optimized the network bandwidth which enhances the performance.
Figure 5: Switches
Source: (Carter, 2012)
Hubs:
It is network devices that are used for connecting number of Ethernet devices. Hubs work as a
single network segment. Hubs are work on a physical layer in the OSI model. It contained a
number of input/output (I/O) ports. Signals are introduced one input port and output appears
on each part except the input port (pillai, 2015).
Figure 6: Hub
10
local area network. It identical to hubs but switch work more intelligence in the network.
Switch received the data packets and determines their destination device and source device
then tramismted.it optimized the network bandwidth which enhances the performance.
Figure 5: Switches
Source: (Carter, 2012)
Hubs:
It is network devices that are used for connecting number of Ethernet devices. Hubs work as a
single network segment. Hubs are work on a physical layer in the OSI model. It contained a
number of input/output (I/O) ports. Signals are introduced one input port and output appears
on each part except the input port (pillai, 2015).
Figure 6: Hub
10

Source: (Trendnet, n.d.)
Bridges:
Bridges are two layers device that creates a number of LAN segments. LAN segments have a
separate impact domain. Bridges are allowed the connectivity with other segments in the
network and keep local traffic separated in the network. It used for the Frame filtering in the
network.
Figure 7: Bridges
Source: (Simpson, 2015)
Routers:
Router forwards data packets between computer internetwork and network. It connected data
lines from a different network. The router reads address information of data packets which
come from one data line and defined the ultimate destination. Router contained router table
that stored the information about packet network journey. It is a device that performed the
traffic directing functions in the networks (pillai, 2015).
11
Bridges:
Bridges are two layers device that creates a number of LAN segments. LAN segments have a
separate impact domain. Bridges are allowed the connectivity with other segments in the
network and keep local traffic separated in the network. It used for the Frame filtering in the
network.
Figure 7: Bridges
Source: (Simpson, 2015)
Routers:
Router forwards data packets between computer internetwork and network. It connected data
lines from a different network. The router reads address information of data packets which
come from one data line and defined the ultimate destination. Router contained router table
that stored the information about packet network journey. It is a device that performed the
traffic directing functions in the networks (pillai, 2015).
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 56
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





