Melbourne IT College: Advanced Network Design Report (BN321, Sem 1)
VerifiedAdded on 2023/06/04
|11
|2014
|407
Report
AI Summary
This report presents a comprehensive network design proposal for an IT college in Melbourne. The design encompasses two buildings connected by a network, accommodating approximately 400 users and featuring separate computer labs in each building. The report details the project scope, hardware components including servers, computers, switches, and routers, and the estimated cost of implementation. It also outlines security measures such as antivirus software and firewalls, along with a data backup plan utilizing cloud storage. The network diagram illustrates a star topology with switches in each room and a main switch per building. The configuration section specifies IP address allocation, router configuration commands, and the use of both Windows 7 and 8 operating systems. The report concludes by emphasizing the scalability and speed of the designed network, aiming to meet the college's expectations. The report is well-referenced with supporting literature.

NETWORK DESIGN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................2
Project scope...............................................................................................................................................2
Project hardware components......................................................................................................................2
Security...................................................................................................................................................5
Data backup.............................................................................................................................................5
Network diagram.........................................................................................................................................6
Network configuration.................................................................................................................................7
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9
Introduction.................................................................................................................................................2
Project scope...............................................................................................................................................2
Project hardware components......................................................................................................................2
Security...................................................................................................................................................5
Data backup.............................................................................................................................................5
Network diagram.........................................................................................................................................6
Network configuration.................................................................................................................................7
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9

Introduction
This documentation is a proposal for LAN network design for an IT college that has recently
leased a building in the Melbourne city for offering IT courses. The IT College which contains
two buildings named building 1 and building 2. The distance between the buildings is 500
meters. The estimated number of users in the college is about 400, 300 users in the building one
while 100 users in building 2.Each building has a lobby where Wi-Fi access points are fixed to
provide wireless internet to the students. The IT College requires highly secured network to be
implemented and used in the school. Building one is divided into four computers labs while
building two is divided into three labs. Each computer lab is expected to a have a server for data
storage and IP phones for making calls [1].
Project scope
This project aims at designing a network for the IT a college that is located in Melbourne city.
The college is expecting a well-designed network that is highly secured and scalable that will be
used by students in their studies. The college that has two buildings and each building having a
lobby provided with secured wireless access point. 35 computers working stations will be set up
in each computers lab. All of the 35 computers will connected to the internet .Servers in each
computer will highly secured and backup to enhance high security of data [2]. The aim of the
project is to come up with scalable network design that will be implemented in the IT College.
Project hardware components
The type of component that are used in any given network depend on the organization
requirement and the type of topology to be used in any given network [3]. Type of data that will
be used in the network will also determine the network plan to be used. Datatype used in this
network will include reports, internet activities including websites. This makes the network to be
implemented in the college to have the following devices [4].
Servers –This will be used for data storage.
Computers-will be used as end devices in the network.
Ethernet cables- for connection of network components together e,g switch and
computers.
Fiber cables- used in connecting the server and switches.
This documentation is a proposal for LAN network design for an IT college that has recently
leased a building in the Melbourne city for offering IT courses. The IT College which contains
two buildings named building 1 and building 2. The distance between the buildings is 500
meters. The estimated number of users in the college is about 400, 300 users in the building one
while 100 users in building 2.Each building has a lobby where Wi-Fi access points are fixed to
provide wireless internet to the students. The IT College requires highly secured network to be
implemented and used in the school. Building one is divided into four computers labs while
building two is divided into three labs. Each computer lab is expected to a have a server for data
storage and IP phones for making calls [1].
Project scope
This project aims at designing a network for the IT a college that is located in Melbourne city.
The college is expecting a well-designed network that is highly secured and scalable that will be
used by students in their studies. The college that has two buildings and each building having a
lobby provided with secured wireless access point. 35 computers working stations will be set up
in each computers lab. All of the 35 computers will connected to the internet .Servers in each
computer will highly secured and backup to enhance high security of data [2]. The aim of the
project is to come up with scalable network design that will be implemented in the IT College.
Project hardware components
The type of component that are used in any given network depend on the organization
requirement and the type of topology to be used in any given network [3]. Type of data that will
be used in the network will also determine the network plan to be used. Datatype used in this
network will include reports, internet activities including websites. This makes the network to be
implemented in the college to have the following devices [4].
Servers –This will be used for data storage.
Computers-will be used as end devices in the network.
Ethernet cables- for connection of network components together e,g switch and
computers.
Fiber cables- used in connecting the server and switches.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Others include:-Other devices that were implemented in the network in network include:
Switches
Routers.
Devices such UPS will be used to control the shutting down process of electrical components
when there is power loss [5].
The following tables show the device that were used in the network.
Device name Description Supplier Number
of items
Amount per
item
T. price
Router
24 gigabit routers Ramo
sellers
1 $200 $700
Server 360 Power
edge Server
10 tb
Aple sellers 7 $1000 $7000
RJ-45
connector
Connectors APP sellers 10pkt $10 $100
Printers
laser printers Dell Sellers 3 $900 $2700
48 & 24-
port switches
Cisco switches Cisco
Sellers
8 $200 $1600
Laptops
Hip Hp tech 3 $320 $960
Desktop
Computers
Intel core I3
8GB RAM
320GB hard
Hp
computers
100 $200 $2000
Switches
Routers.
Devices such UPS will be used to control the shutting down process of electrical components
when there is power loss [5].
The following tables show the device that were used in the network.
Device name Description Supplier Number
of items
Amount per
item
T. price
Router
24 gigabit routers Ramo
sellers
1 $200 $700
Server 360 Power
edge Server
10 tb
Aple sellers 7 $1000 $7000
RJ-45
connector
Connectors APP sellers 10pkt $10 $100
Printers
laser printers Dell Sellers 3 $900 $2700
48 & 24-
port switches
Cisco switches Cisco
Sellers
8 $200 $1600
Laptops
Hip Hp tech 3 $320 $960
Desktop
Computers
Intel core I3
8GB RAM
320GB hard
Hp
computers
100 $200 $2000
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

disk
32 inch
screen
Windows
operating
system
UPS
Contec-
48volts
hp sellers 7 $1000 $7000
Labor cost
$1000
Operating
systems
Windows 8 & 7 Microsoft
technologies
2 $1000 $2000
Surveillance
cameras
Wireless
security
camera
Hp
technologies
1 $400 &100
Total cost $60000o
The cost estimated for implementation was about & 600 000.
Operating system
Different type operating system will run in the network .Both windows 7 and 8 will be used in
the network. Windows 8 will be used in client computers while windows 7 will run from the
server side. The server side will serve information to other computers [5]. Heavy applications
32 inch
screen
Windows
operating
system
UPS
Contec-
48volts
hp sellers 7 $1000 $7000
Labor cost
$1000
Operating
systems
Windows 8 & 7 Microsoft
technologies
2 $1000 $2000
Surveillance
cameras
Wireless
security
camera
Hp
technologies
1 $400 &100
Total cost $60000o
The cost estimated for implementation was about & 600 000.
Operating system
Different type operating system will run in the network .Both windows 7 and 8 will be used in
the network. Windows 8 will be used in client computers while windows 7 will run from the
server side. The server side will serve information to other computers [5]. Heavy applications

will accessed from the server side. The website of the college will run from the server accessed
by clients over the internet. Other applications that are important to the institution will also run
from the server side. Other application like Microsoft word a will be installed in the client side.
Computers in the labs will have one or more account. Users of the network will have limited
access to network than the admins.The admin will have access to all areas with the network
while the users will only have access to few areas in then network. The network is expected to
serve around 400 users in the college [6]. Wi-Fi network will be secured to prevent unauthorized
users from accessing the network.
Security
The network will be secured in the following ways. Anti-viruses will be installed in lab
computers to prevent malicious soft wares from accessing causing arm or fetching information
from the network. Firewalls will be installed at various sections of the of the network especially
server areas in order to prevent viruses from causing harm to users in the network or collecting
information which is not allowed from the network [6]. Each computer will have a
password .This means no door will be left open for unauthorized users. On the other hand Wi-Fi
wireless networks will have strong and encrypted passwords to prevent attackers from accessing
it. AES algorithm will be used for password encryption in this category since is more secure and
hard to crack.
Data backup
The network will have a data backup plan where all servers will be connected to a secondary
server that will be in cloud. The data backup plan will be stored will use windows to
automatically update data in the cloud [7]. Data will automatically be updated in the cloudy and
the end of every day. Other recovery plans in the operating system will be activated to recover
data in case there is any data loss.
by clients over the internet. Other applications that are important to the institution will also run
from the server side. Other application like Microsoft word a will be installed in the client side.
Computers in the labs will have one or more account. Users of the network will have limited
access to network than the admins.The admin will have access to all areas with the network
while the users will only have access to few areas in then network. The network is expected to
serve around 400 users in the college [6]. Wi-Fi network will be secured to prevent unauthorized
users from accessing the network.
Security
The network will be secured in the following ways. Anti-viruses will be installed in lab
computers to prevent malicious soft wares from accessing causing arm or fetching information
from the network. Firewalls will be installed at various sections of the of the network especially
server areas in order to prevent viruses from causing harm to users in the network or collecting
information which is not allowed from the network [6]. Each computer will have a
password .This means no door will be left open for unauthorized users. On the other hand Wi-Fi
wireless networks will have strong and encrypted passwords to prevent attackers from accessing
it. AES algorithm will be used for password encryption in this category since is more secure and
hard to crack.
Data backup
The network will have a data backup plan where all servers will be connected to a secondary
server that will be in cloud. The data backup plan will be stored will use windows to
automatically update data in the cloud [7]. Data will automatically be updated in the cloudy and
the end of every day. Other recovery plans in the operating system will be activated to recover
data in case there is any data loss.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network diagram
The following shows how the network will be designed in the IT College
The above is the design of the IT college network for the two building. The sub-networks from
the two building are linked together through a router. Each building has its own main switch. The
main switch then connects to 48 port switches that are found in each room. Since building 1 has
four rooms, each room will have its own switch. The switch in each room will be connected to
35 computers and IP phones. Server in each room will also be connected to the switch so that
computers can read data from it. IP phones are used for calling. The wireless access point and
router is connected to the main switch of the of the building to serve users with wireless network.
In building two which is 500 meters away from building 2 and has three rooms the case is the
same. In building 1 the main switch connects to the three switches found in the in each room.
Each switch in each room connects 35 computers, IP phones and the server together. The above
method of designing the network will make it faster since star network topology will be
implemented .Star topology does not cause collision of packets in the network this makes it a
suitable topology to be implemented in any network.
The following shows how the network will be designed in the IT College
The above is the design of the IT college network for the two building. The sub-networks from
the two building are linked together through a router. Each building has its own main switch. The
main switch then connects to 48 port switches that are found in each room. Since building 1 has
four rooms, each room will have its own switch. The switch in each room will be connected to
35 computers and IP phones. Server in each room will also be connected to the switch so that
computers can read data from it. IP phones are used for calling. The wireless access point and
router is connected to the main switch of the of the building to serve users with wireless network.
In building two which is 500 meters away from building 2 and has three rooms the case is the
same. In building 1 the main switch connects to the three switches found in the in each room.
Each switch in each room connects 35 computers, IP phones and the server together. The above
method of designing the network will make it faster since star network topology will be
implemented .Star topology does not cause collision of packets in the network this makes it a
suitable topology to be implemented in any network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
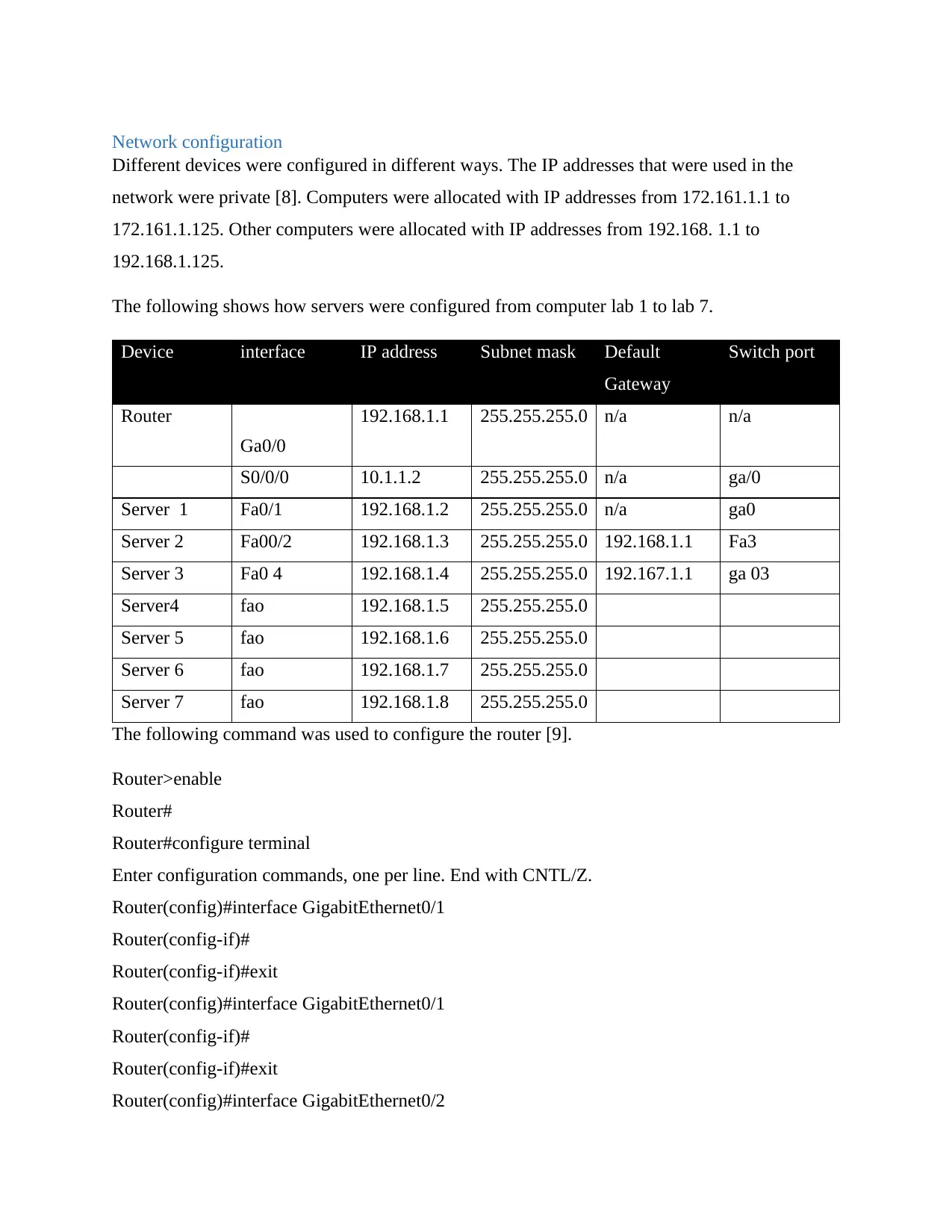
Network configuration
Different devices were configured in different ways. The IP addresses that were used in the
network were private [8]. Computers were allocated with IP addresses from 172.161.1.1 to
172.161.1.125. Other computers were allocated with IP addresses from 192.168. 1.1 to
192.168.1.125.
The following shows how servers were configured from computer lab 1 to lab 7.
Device interface IP address Subnet mask Default
Gateway
Switch port
Router
Ga0/0
192.168.1.1 255.255.255.0 n/a n/a
S0/0/0 10.1.1.2 255.255.255.0 n/a ga/0
Server 1 Fa0/1 192.168.1.2 255.255.255.0 n/a ga0
Server 2 Fa00/2 192.168.1.3 255.255.255.0 192.168.1.1 Fa3
Server 3 Fa0 4 192.168.1.4 255.255.255.0 192.167.1.1 ga 03
Server4 fao 192.168.1.5 255.255.255.0
Server 5 fao 192.168.1.6 255.255.255.0
Server 6 fao 192.168.1.7 255.255.255.0
Server 7 fao 192.168.1.8 255.255.255.0
The following command was used to configure the router [9].
Router>enable
Router#
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#interface GigabitEthernet0/1
Router(config-if)#
Router(config-if)#exit
Router(config)#interface GigabitEthernet0/1
Router(config-if)#
Router(config-if)#exit
Router(config)#interface GigabitEthernet0/2
Different devices were configured in different ways. The IP addresses that were used in the
network were private [8]. Computers were allocated with IP addresses from 172.161.1.1 to
172.161.1.125. Other computers were allocated with IP addresses from 192.168. 1.1 to
192.168.1.125.
The following shows how servers were configured from computer lab 1 to lab 7.
Device interface IP address Subnet mask Default
Gateway
Switch port
Router
Ga0/0
192.168.1.1 255.255.255.0 n/a n/a
S0/0/0 10.1.1.2 255.255.255.0 n/a ga/0
Server 1 Fa0/1 192.168.1.2 255.255.255.0 n/a ga0
Server 2 Fa00/2 192.168.1.3 255.255.255.0 192.168.1.1 Fa3
Server 3 Fa0 4 192.168.1.4 255.255.255.0 192.167.1.1 ga 03
Server4 fao 192.168.1.5 255.255.255.0
Server 5 fao 192.168.1.6 255.255.255.0
Server 6 fao 192.168.1.7 255.255.255.0
Server 7 fao 192.168.1.8 255.255.255.0
The following command was used to configure the router [9].
Router>enable
Router#
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#interface GigabitEthernet0/1
Router(config-if)#
Router(config-if)#exit
Router(config)#interface GigabitEthernet0/1
Router(config-if)#
Router(config-if)#exit
Router(config)#interface GigabitEthernet0/2
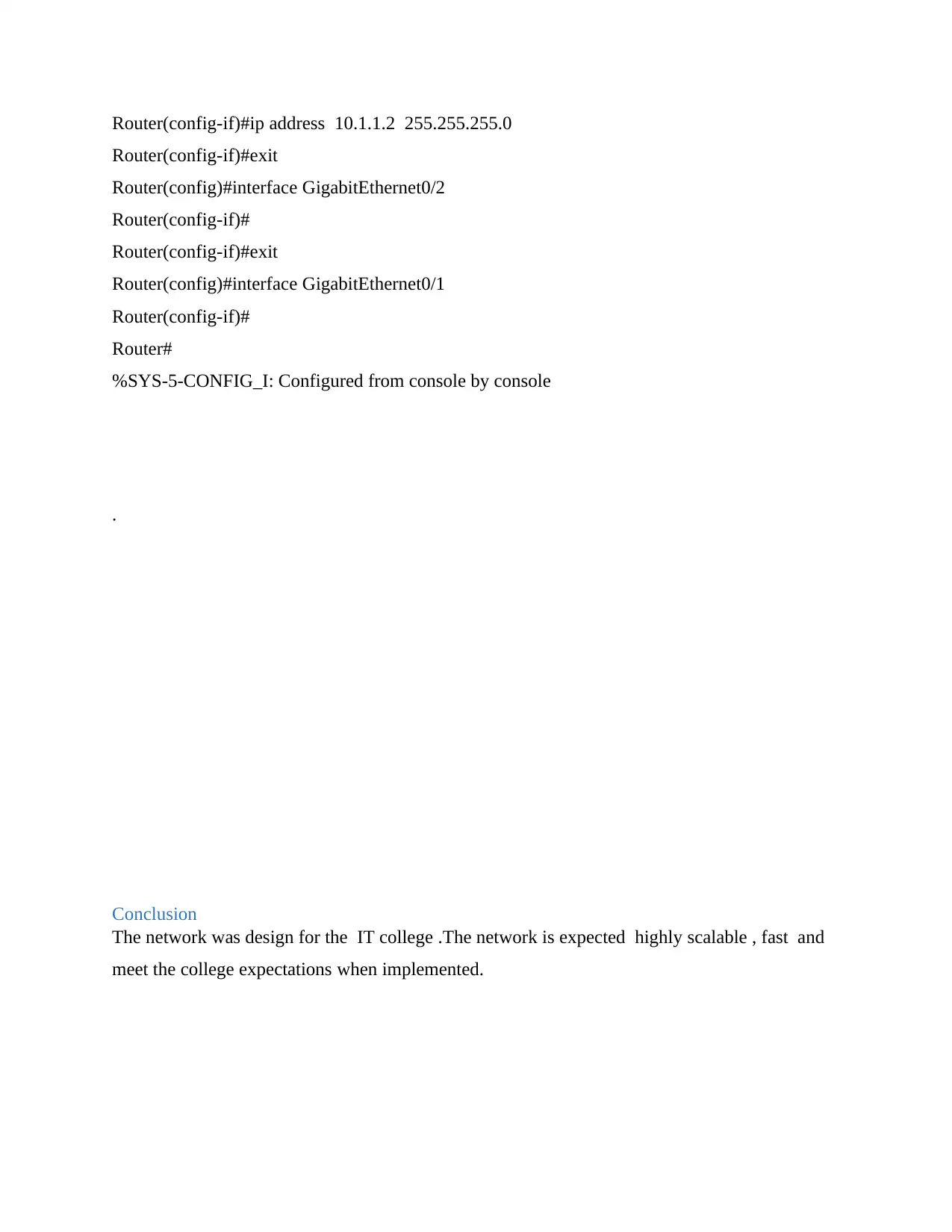
Router(config-if)#ip address 10.1.1.2 255.255.255.0
Router(config-if)#exit
Router(config)#interface GigabitEthernet0/2
Router(config-if)#
Router(config-if)#exit
Router(config)#interface GigabitEthernet0/1
Router(config-if)#
Router#
%SYS-5-CONFIG_I: Configured from console by console
.
Conclusion
The network was design for the IT college .The network is expected highly scalable , fast and
meet the college expectations when implemented.
Router(config-if)#exit
Router(config)#interface GigabitEthernet0/2
Router(config-if)#
Router(config-if)#exit
Router(config)#interface GigabitEthernet0/1
Router(config-if)#
Router#
%SYS-5-CONFIG_I: Configured from console by console
.
Conclusion
The network was design for the IT college .The network is expected highly scalable , fast and
meet the college expectations when implemented.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
[1]. Sun, Y., Hashiguchi, T., Minh, V.Q., Wang, X., Morikawa, H. and Aoyama, T. Design and
implementation of an optical burst-switched network testbed. IEEE Communications
Magazine, 43(11), pp.S48-S55, 2014.
[2] Jiang, X., Dawson-Haggerty, S., Dutta, P. and Culler,. Design and implementation of a high-
fidelity ac metering network. In Information Processing in Sensor Networks, 2009. IPSN 2009.
International Conference on (pp. 253-264). IEEE,2009.
[3]. Suh, C., Mir, Z.H. and Ko, Y.B.. Design and implementation of enhanced IEEE 802.15. 4
for supporting multimedia service in Wireless Sensor Networks. Computer Networks, 52(13),
pp.2568-2581,2010.
[4]. Miluzzo, E., Lane, N.D., Fodor, K., Peterson, R., Lu, H., Musolesi, M., Eisenman, S.B.,
Zheng, X. and Campbell, A.T.. Sensing meets mobile social networks: the design,
implementation and evaluation of the cenceme application. In Proceedings of the 6th ACM
conference on Embedded network sensor systems (pp. 337-350). ACM. 2009.
[5]. Martin, J. and Leben, J.. TCP/IP networking: architecture, administration, and
programming. PTR Prentice-Hall.2010.
[6]. Pakzad, S.N., Fenves, G.L., Kim, S. and Culler, D.E., Design and implementation of scalable
wireless sensor network for structural monitoring. Journal of infrastructure systems, 14(1),
pp.89-101,2011.
[8]. Forouzan, A.B.. Data communications & networking (sie). Tata McGraw-Hill
Education,2009
[9]. Priyantha, N.B., Kansal, A., Goraczko, M. and Zhao, F. Tiny web services: design and
implementation of interoperable and evolvable sensor networks. In Proceedings of the 6th ACM
conference on Embedded network sensor systems (pp. 253-266). ACM, 2010.
[10]. Mak, K.H. and Holland, B.L.,. Migrating electrical power network SCADA systems to
TCP/IP and Ethernet networking. Power Engineering Journal, 16(6), pp.305-311,2010.
.
[1]. Sun, Y., Hashiguchi, T., Minh, V.Q., Wang, X., Morikawa, H. and Aoyama, T. Design and
implementation of an optical burst-switched network testbed. IEEE Communications
Magazine, 43(11), pp.S48-S55, 2014.
[2] Jiang, X., Dawson-Haggerty, S., Dutta, P. and Culler,. Design and implementation of a high-
fidelity ac metering network. In Information Processing in Sensor Networks, 2009. IPSN 2009.
International Conference on (pp. 253-264). IEEE,2009.
[3]. Suh, C., Mir, Z.H. and Ko, Y.B.. Design and implementation of enhanced IEEE 802.15. 4
for supporting multimedia service in Wireless Sensor Networks. Computer Networks, 52(13),
pp.2568-2581,2010.
[4]. Miluzzo, E., Lane, N.D., Fodor, K., Peterson, R., Lu, H., Musolesi, M., Eisenman, S.B.,
Zheng, X. and Campbell, A.T.. Sensing meets mobile social networks: the design,
implementation and evaluation of the cenceme application. In Proceedings of the 6th ACM
conference on Embedded network sensor systems (pp. 337-350). ACM. 2009.
[5]. Martin, J. and Leben, J.. TCP/IP networking: architecture, administration, and
programming. PTR Prentice-Hall.2010.
[6]. Pakzad, S.N., Fenves, G.L., Kim, S. and Culler, D.E., Design and implementation of scalable
wireless sensor network for structural monitoring. Journal of infrastructure systems, 14(1),
pp.89-101,2011.
[8]. Forouzan, A.B.. Data communications & networking (sie). Tata McGraw-Hill
Education,2009
[9]. Priyantha, N.B., Kansal, A., Goraczko, M. and Zhao, F. Tiny web services: design and
implementation of interoperable and evolvable sensor networks. In Proceedings of the 6th ACM
conference on Embedded network sensor systems (pp. 253-266). ACM, 2010.
[10]. Mak, K.H. and Holland, B.L.,. Migrating electrical power network SCADA systems to
TCP/IP and Ethernet networking. Power Engineering Journal, 16(6), pp.305-311,2010.
.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





