Developing Lightweight Encryption for Secure IoT Applications
VerifiedAdded on 2023/06/04
|53
|14901
|228
Project
AI Summary
This project delves into the critical area of securing Internet of Things (IoT) devices through lightweight encryption algorithms. The research begins with an introduction to the IoT, highlighting its architecture, components like RFID tags and sensors, and the paramount importance of security. It identifies the limitations of IoT devices, such as resource constraints, which necessitate the use of lightweight encryption. The project's aim is to propose a new lightweight encryption algorithm to provide security to IoT devices. A comprehensive literature review analyzes existing algorithms like AES, HIGHT, TEA, PRESENT, RC5, and others, evaluating their performance and identifying gaps. The study explores various security protocols at different layers of the IoT architecture. The core of the project involves proposing a new algorithm, detailing its mathematical functions, providing an illustrative example, and outlining an experimental setup for testing. The results, security analysis, recommendations, and future scope are also discussed, along with the limitations of the research. The project aims to enhance IoT security by providing a practical and efficient solution.

Lightweight Encryption Algorithm
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
1. Introduction.........................................................................................................................2
2. Research Aim:.....................................................................................................................3
3. Literature Review:..............................................................................................................3
Security in IOT Architecture..................................................................................................4
Major risks associated with RFID tags...................................................................................8
Types of Attack:.....................................................................................................................9
Basic Requirement of Lightweight cryptographic architecture:..........................................10
Symmetric and public Key cryptography procedures:.........................................................11
4. Findings............................................................................................................................14
Trends and technology used in the Light weight cryptographic procedures........................15
Measuring efficiency of the existing light weight cryptographic algorithms:.....................15
5. Discussion.........................................................................................................................19
6. Proposed Algorithm..........................................................................................................20
Proposed Mathematical Function:........................................................................................21
Explanation of Algorithm with Example.............................................................................23
Experimental Set up for the proposed algorithm..................................................................26
7. Results...............................................................................................................................29
8. Security Analysis..............................................................................................................33
9. Recommendation..............................................................................................................35
10. Future Scope..................................................................................................................36
11. Research Limitation:.....................................................................................................36
12. Conclusion.....................................................................................................................36
13. References.....................................................................................................................37
14. Appendix:......................................................................................................................41
1. Introduction.........................................................................................................................2
2. Research Aim:.....................................................................................................................3
3. Literature Review:..............................................................................................................3
Security in IOT Architecture..................................................................................................4
Major risks associated with RFID tags...................................................................................8
Types of Attack:.....................................................................................................................9
Basic Requirement of Lightweight cryptographic architecture:..........................................10
Symmetric and public Key cryptography procedures:.........................................................11
4. Findings............................................................................................................................14
Trends and technology used in the Light weight cryptographic procedures........................15
Measuring efficiency of the existing light weight cryptographic algorithms:.....................15
5. Discussion.........................................................................................................................19
6. Proposed Algorithm..........................................................................................................20
Proposed Mathematical Function:........................................................................................21
Explanation of Algorithm with Example.............................................................................23
Experimental Set up for the proposed algorithm..................................................................26
7. Results...............................................................................................................................29
8. Security Analysis..............................................................................................................33
9. Recommendation..............................................................................................................35
10. Future Scope..................................................................................................................36
11. Research Limitation:.....................................................................................................36
12. Conclusion.....................................................................................................................36
13. References.....................................................................................................................37
14. Appendix:......................................................................................................................41

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Lightweight Encryption Algorithm for Secure IOT
1. Introduction
Internet of thing is the emerging phenomenon in the digital world. It provides the
connectivity between digital tools and human interaction in the development of the real time
application. Security is the major concern with the IOT devices. The IOT environment is
composed of radio frequency Identifiers tags, sensors, actuators, routers, smart devices, and
human. The RFID tags helps in managing the communication between the human and the
physical smart devices for initializing the flow of information for making efficient real time
communication between them. The IOT environment is composed of three things which are
classified as pinpointing things, computation things, and interaction with the ubiquitous
computer digital world (Hasan and Ismail, 2017). The IOT architecture is composed of three
layers which are physical layer, commutation layer, and application layer. The connectivity
between the physical devices with the human is possible with the help of physical layer. The
4G network is required for managing the interaction with the physical devices. The public
network is developed for increasing the efficiency of the IOT application. The IOT devices
are equipped with some limitations such as these devices are incorporated with resource
constraints, having small memory sizes, limited bandwidth, time dependent, use of radio
frequency Identifiers, and others. These limitation makes difficulty in managing effective
security cryptographic procedures for the IOT devices to make it secure from unauthorised
modification, un-authentication accessing of account, data leakages and misuses, monitoring
of data flow, and others (Katagi, and Moriai, 2011). The vulnerabilities can be added by the
hackers in the IOT environment which can results into malfunctioning of the system. The
best solution to resolve the complexities of IOT devices in secure connection is the
development of the lightweight encryption algorithm (LEA). It is difficult for managing the
security to the complete IOT system because it will require greater capacity of memory, and
uninterrupted of the power supply which is not possible with the IOT environment. The
lightweight encryption algorithm provides security to the specific IOT devices to make it
secure from the external environment attacks (Bhardwaj, Kumar, and Bansal, 2017). It can be
the possibility that LEA developed for one device is not applicable to the other devices. The
lightweight cryptography is based on private keys developed for encrypting and decrypting
the text for security. The information in the RFID tags should present in the encrypted form
so that the efficiency and effectiveness of the data can be retrieved. The control system
1. Introduction
Internet of thing is the emerging phenomenon in the digital world. It provides the
connectivity between digital tools and human interaction in the development of the real time
application. Security is the major concern with the IOT devices. The IOT environment is
composed of radio frequency Identifiers tags, sensors, actuators, routers, smart devices, and
human. The RFID tags helps in managing the communication between the human and the
physical smart devices for initializing the flow of information for making efficient real time
communication between them. The IOT environment is composed of three things which are
classified as pinpointing things, computation things, and interaction with the ubiquitous
computer digital world (Hasan and Ismail, 2017). The IOT architecture is composed of three
layers which are physical layer, commutation layer, and application layer. The connectivity
between the physical devices with the human is possible with the help of physical layer. The
4G network is required for managing the interaction with the physical devices. The public
network is developed for increasing the efficiency of the IOT application. The IOT devices
are equipped with some limitations such as these devices are incorporated with resource
constraints, having small memory sizes, limited bandwidth, time dependent, use of radio
frequency Identifiers, and others. These limitation makes difficulty in managing effective
security cryptographic procedures for the IOT devices to make it secure from unauthorised
modification, un-authentication accessing of account, data leakages and misuses, monitoring
of data flow, and others (Katagi, and Moriai, 2011). The vulnerabilities can be added by the
hackers in the IOT environment which can results into malfunctioning of the system. The
best solution to resolve the complexities of IOT devices in secure connection is the
development of the lightweight encryption algorithm (LEA). It is difficult for managing the
security to the complete IOT system because it will require greater capacity of memory, and
uninterrupted of the power supply which is not possible with the IOT environment. The
lightweight encryption algorithm provides security to the specific IOT devices to make it
secure from the external environment attacks (Bhardwaj, Kumar, and Bansal, 2017). It can be
the possibility that LEA developed for one device is not applicable to the other devices. The
lightweight cryptography is based on private keys developed for encrypting and decrypting
the text for security. The information in the RFID tags should present in the encrypted form
so that the efficiency and effectiveness of the data can be retrieved. The control system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

architecture should be developed for preserving the flow of information from the third party.
The encryption procedures are used for increasing the error tolerance capability of public and
private keys for secure transmission of data.
2. Research Aim:
The aim of this research is to propose a new light weight encryption algorithm to provide
security to the IOT devices.
3. Literature Review:
The literature review is conducted for analysing the performance and gaps which exists in the
existing light weight encryption algorithm. The noise exerted in the path of data packets can
be effectively analysed with the development of public and private key (Usman, Ahmed,
Aslam, Khan, and Shah, 2017). The IOT architecture is equipped various cyber-attacks in the
process of data collection from the real time scenario. The sensors are used for analysing the
autonomous control over the working units of the physical devices. The encryption process
should be applied on sensor devices for managing the confidentiality and accuracy of the data
(Singh, Sharma, Moon, Park, 2017). The countermeasures and encryption process should be
used for preserving the confidentiality and sensitivity of the information to overcome the
threats and vulnerabilities (Naru, Saini, and Sharma, 2017). The following figure shows the
process of managing the countermeasure by using encryption process to manage the attack on
data collection methodology:
The data leakages can be effectively prevented by using the sensor technology and message
authentication protocols for managing the flow of information securely. The cryptographic
procedures are applied on the data link layer for securing the communication over the
physical layer connectivity between the devices (Venugopal, and Doraipandian, 2014). The
The encryption procedures are used for increasing the error tolerance capability of public and
private keys for secure transmission of data.
2. Research Aim:
The aim of this research is to propose a new light weight encryption algorithm to provide
security to the IOT devices.
3. Literature Review:
The literature review is conducted for analysing the performance and gaps which exists in the
existing light weight encryption algorithm. The noise exerted in the path of data packets can
be effectively analysed with the development of public and private key (Usman, Ahmed,
Aslam, Khan, and Shah, 2017). The IOT architecture is equipped various cyber-attacks in the
process of data collection from the real time scenario. The sensors are used for analysing the
autonomous control over the working units of the physical devices. The encryption process
should be applied on sensor devices for managing the confidentiality and accuracy of the data
(Singh, Sharma, Moon, Park, 2017). The countermeasures and encryption process should be
used for preserving the confidentiality and sensitivity of the information to overcome the
threats and vulnerabilities (Naru, Saini, and Sharma, 2017). The following figure shows the
process of managing the countermeasure by using encryption process to manage the attack on
data collection methodology:
The data leakages can be effectively prevented by using the sensor technology and message
authentication protocols for managing the flow of information securely. The cryptographic
procedures are applied on the data link layer for securing the communication over the
physical layer connectivity between the devices (Venugopal, and Doraipandian, 2014). The
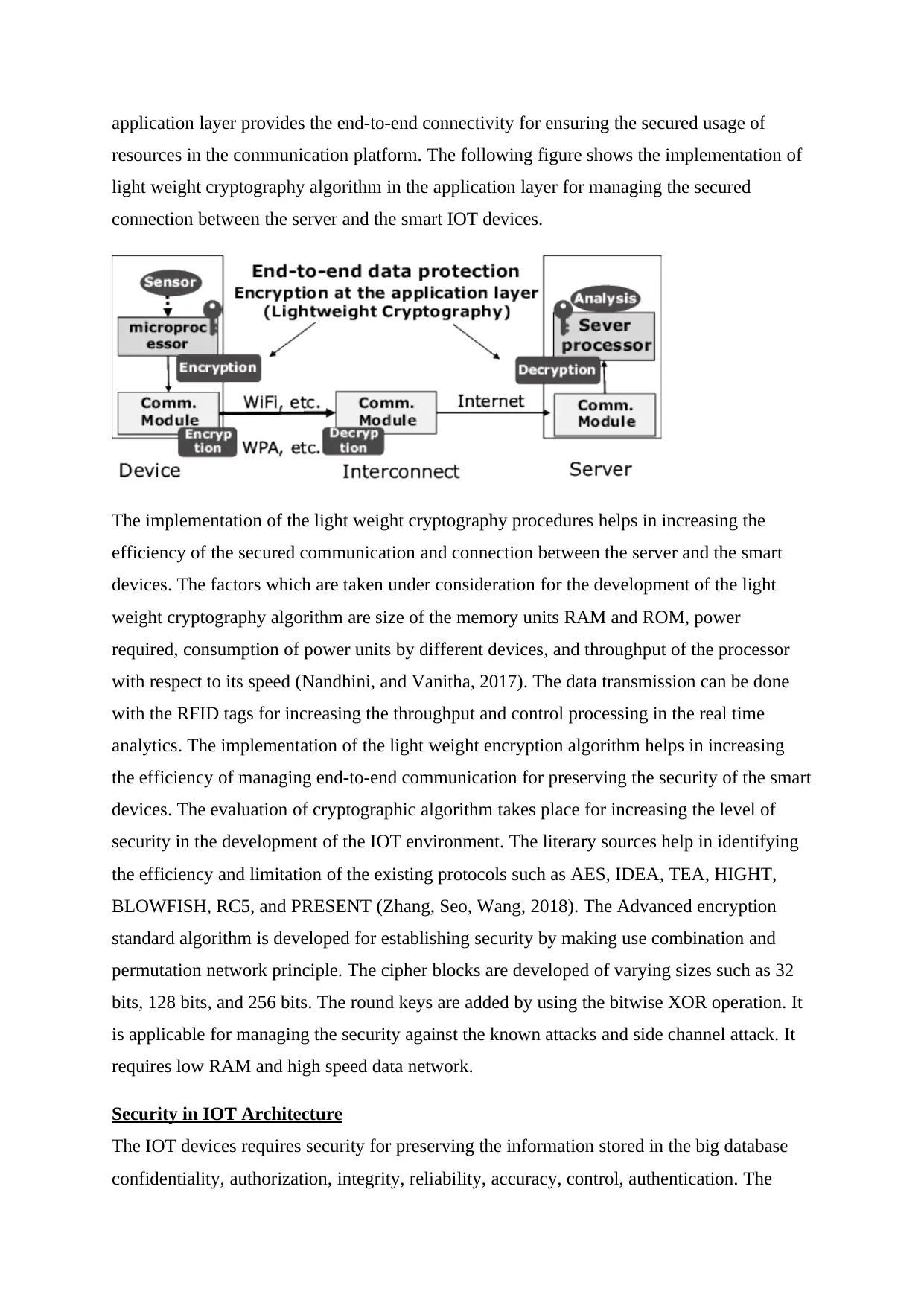
application layer provides the end-to-end connectivity for ensuring the secured usage of
resources in the communication platform. The following figure shows the implementation of
light weight cryptography algorithm in the application layer for managing the secured
connection between the server and the smart IOT devices.
The implementation of the light weight cryptography procedures helps in increasing the
efficiency of the secured communication and connection between the server and the smart
devices. The factors which are taken under consideration for the development of the light
weight cryptography algorithm are size of the memory units RAM and ROM, power
required, consumption of power units by different devices, and throughput of the processor
with respect to its speed (Nandhini, and Vanitha, 2017). The data transmission can be done
with the RFID tags for increasing the throughput and control processing in the real time
analytics. The implementation of the light weight encryption algorithm helps in increasing
the efficiency of managing end-to-end communication for preserving the security of the smart
devices. The evaluation of cryptographic algorithm takes place for increasing the level of
security in the development of the IOT environment. The literary sources help in identifying
the efficiency and limitation of the existing protocols such as AES, IDEA, TEA, HIGHT,
BLOWFISH, RC5, and PRESENT (Zhang, Seo, Wang, 2018). The Advanced encryption
standard algorithm is developed for establishing security by making use combination and
permutation network principle. The cipher blocks are developed of varying sizes such as 32
bits, 128 bits, and 256 bits. The round keys are added by using the bitwise XOR operation. It
is applicable for managing the security against the known attacks and side channel attack. It
requires low RAM and high speed data network.
Security in IOT Architecture
The IOT devices requires security for preserving the information stored in the big database
confidentiality, authorization, integrity, reliability, accuracy, control, authentication. The
resources in the communication platform. The following figure shows the implementation of
light weight cryptography algorithm in the application layer for managing the secured
connection between the server and the smart IOT devices.
The implementation of the light weight cryptography procedures helps in increasing the
efficiency of the secured communication and connection between the server and the smart
devices. The factors which are taken under consideration for the development of the light
weight cryptography algorithm are size of the memory units RAM and ROM, power
required, consumption of power units by different devices, and throughput of the processor
with respect to its speed (Nandhini, and Vanitha, 2017). The data transmission can be done
with the RFID tags for increasing the throughput and control processing in the real time
analytics. The implementation of the light weight encryption algorithm helps in increasing
the efficiency of managing end-to-end communication for preserving the security of the smart
devices. The evaluation of cryptographic algorithm takes place for increasing the level of
security in the development of the IOT environment. The literary sources help in identifying
the efficiency and limitation of the existing protocols such as AES, IDEA, TEA, HIGHT,
BLOWFISH, RC5, and PRESENT (Zhang, Seo, Wang, 2018). The Advanced encryption
standard algorithm is developed for establishing security by making use combination and
permutation network principle. The cipher blocks are developed of varying sizes such as 32
bits, 128 bits, and 256 bits. The round keys are added by using the bitwise XOR operation. It
is applicable for managing the security against the known attacks and side channel attack. It
requires low RAM and high speed data network.
Security in IOT Architecture
The IOT devices requires security for preserving the information stored in the big database
confidentiality, authorization, integrity, reliability, accuracy, control, authentication. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
exchange of data between the remote devices should be securely done for managing the
quality of operation performed by the IOT devices (Bansod, Pisharoty, and Patil, 2017). The
IOT architecture requires security at all levels of layer.
Physical Layer: The physical layer works on managing the integration of RFID tags,
actuators, sensors, data transmission, and others. The security of the physical layer is done
through the implementation of IEEE 802.15.4. It is used for securing the vulnerabilities
associated in the flow of data transmission at physical layer (Batra, 2017).
Network Layer: The transmission of data packets from data link layer to network layer can be
done securely by IPv6 and IPv4 protocol. The network layer in the IOT architecture is
deployed with inbuilt security protocol named as AES and DES.
Transport Layer: The user datagram protocol UDP is the used for managing peer to peer
communication between IOT devices.
Application layer: Constrained Application protocol is used for securing the different
application for the communication between IOT devices.
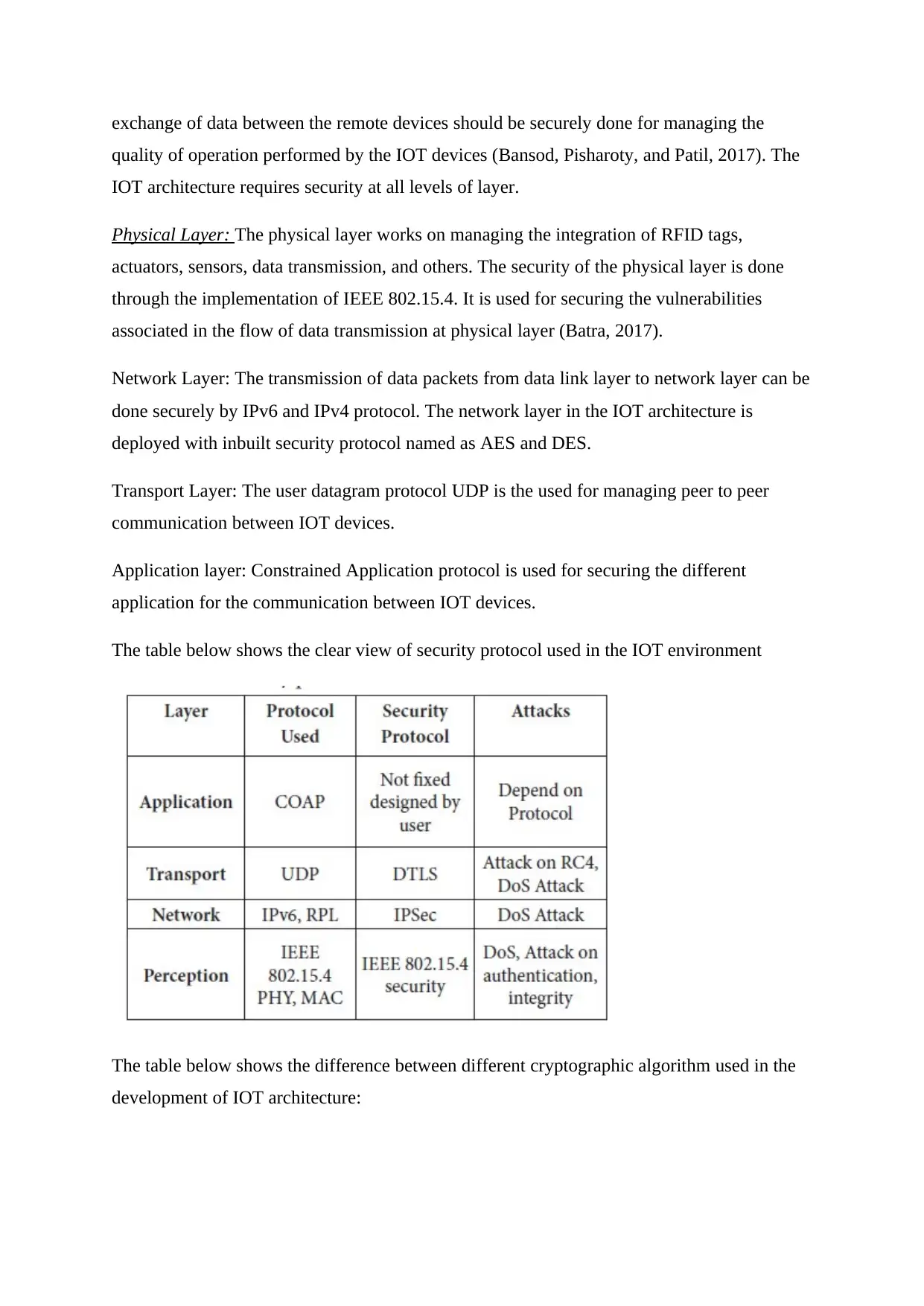
The table below shows the clear view of security protocol used in the IOT environment
The table below shows the difference between different cryptographic algorithm used in the
development of IOT architecture:
quality of operation performed by the IOT devices (Bansod, Pisharoty, and Patil, 2017). The
IOT architecture requires security at all levels of layer.
Physical Layer: The physical layer works on managing the integration of RFID tags,
actuators, sensors, data transmission, and others. The security of the physical layer is done
through the implementation of IEEE 802.15.4. It is used for securing the vulnerabilities
associated in the flow of data transmission at physical layer (Batra, 2017).
Network Layer: The transmission of data packets from data link layer to network layer can be
done securely by IPv6 and IPv4 protocol. The network layer in the IOT architecture is
deployed with inbuilt security protocol named as AES and DES.
Transport Layer: The user datagram protocol UDP is the used for managing peer to peer
communication between IOT devices.
Application layer: Constrained Application protocol is used for securing the different
application for the communication between IOT devices.
The table below shows the clear view of security protocol used in the IOT environment
The table below shows the difference between different cryptographic algorithm used in the
development of IOT architecture:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
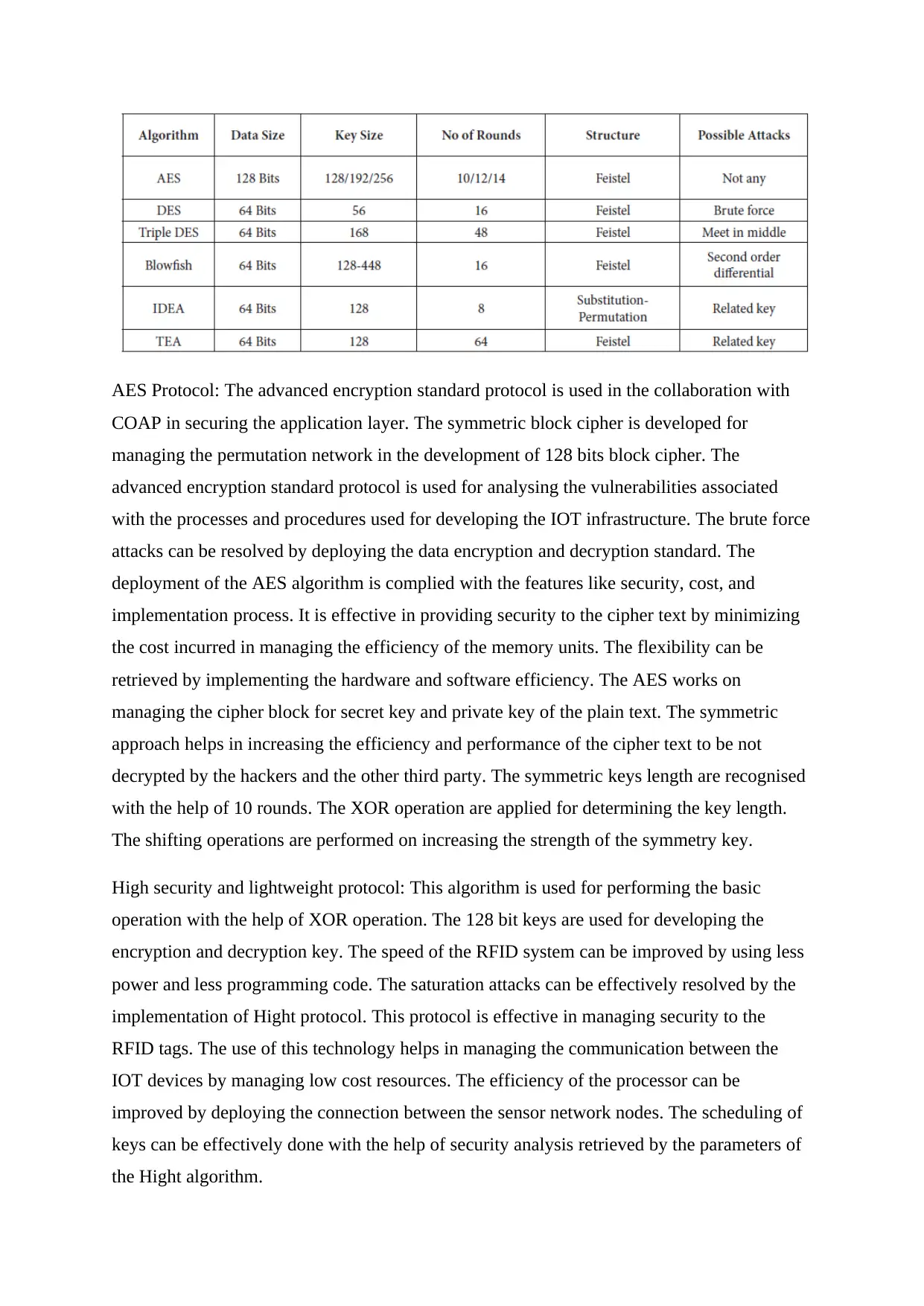
AES Protocol: The advanced encryption standard protocol is used in the collaboration with
COAP in securing the application layer. The symmetric block cipher is developed for
managing the permutation network in the development of 128 bits block cipher. The
advanced encryption standard protocol is used for analysing the vulnerabilities associated
with the processes and procedures used for developing the IOT infrastructure. The brute force
attacks can be resolved by deploying the data encryption and decryption standard. The
deployment of the AES algorithm is complied with the features like security, cost, and
implementation process. It is effective in providing security to the cipher text by minimizing
the cost incurred in managing the efficiency of the memory units. The flexibility can be
retrieved by implementing the hardware and software efficiency. The AES works on
managing the cipher block for secret key and private key of the plain text. The symmetric
approach helps in increasing the efficiency and performance of the cipher text to be not
decrypted by the hackers and the other third party. The symmetric keys length are recognised
with the help of 10 rounds. The XOR operation are applied for determining the key length.
The shifting operations are performed on increasing the strength of the symmetry key.
High security and lightweight protocol: This algorithm is used for performing the basic
operation with the help of XOR operation. The 128 bit keys are used for developing the
encryption and decryption key. The speed of the RFID system can be improved by using less
power and less programming code. The saturation attacks can be effectively resolved by the
implementation of Hight protocol. This protocol is effective in managing security to the
RFID tags. The use of this technology helps in managing the communication between the
IOT devices by managing low cost resources. The efficiency of the processor can be
improved by deploying the connection between the sensor network nodes. The scheduling of
keys can be effectively done with the help of security analysis retrieved by the parameters of
the Hight algorithm.
COAP in securing the application layer. The symmetric block cipher is developed for
managing the permutation network in the development of 128 bits block cipher. The
advanced encryption standard protocol is used for analysing the vulnerabilities associated
with the processes and procedures used for developing the IOT infrastructure. The brute force
attacks can be resolved by deploying the data encryption and decryption standard. The
deployment of the AES algorithm is complied with the features like security, cost, and
implementation process. It is effective in providing security to the cipher text by minimizing
the cost incurred in managing the efficiency of the memory units. The flexibility can be
retrieved by implementing the hardware and software efficiency. The AES works on
managing the cipher block for secret key and private key of the plain text. The symmetric
approach helps in increasing the efficiency and performance of the cipher text to be not
decrypted by the hackers and the other third party. The symmetric keys length are recognised
with the help of 10 rounds. The XOR operation are applied for determining the key length.
The shifting operations are performed on increasing the strength of the symmetry key.
High security and lightweight protocol: This algorithm is used for performing the basic
operation with the help of XOR operation. The 128 bit keys are used for developing the
encryption and decryption key. The speed of the RFID system can be improved by using less
power and less programming code. The saturation attacks can be effectively resolved by the
implementation of Hight protocol. This protocol is effective in managing security to the
RFID tags. The use of this technology helps in managing the communication between the
IOT devices by managing low cost resources. The efficiency of the processor can be
improved by deploying the connection between the sensor network nodes. The scheduling of
keys can be effectively done with the help of security analysis retrieved by the parameters of
the Hight algorithm.
TEA Protocol: The tiny encryption algorithm is specifically implied in the constrained
environment for managing the coordination between the smart devices. The complex
operation can be solved by XOR gate for developing the 128 bit key size (Raval, Bansod,
Pishroty, 2015). The TEA protocol is used for resolving the complexities associated with the
simple operation. The TEA algorithm developed the block cipher for the encrypted message
in the limited number of lines.
PRESENT Protocol: It is the light weight cryptographic procedures which are used for
optimizing the output based on 4 input variables. The 128 bits key is applied on managing the
operation of 64 bit cipher block. It can solved 26 types of vulnerabilities associated with the
development framework of the application layer between IOT devices. The S-box are created
with the help of PRESENT algorithm. The scheduling of keys can be effectively done with
the help of this algorithm. The S-box are created by analysing the permutation layer.
RC5: The RC5 protocol is used for managing the operation for data independency. The
management of the wireless sensor can be effectively laid down with the use of RC5
protocol. 255 rounds are developed for creating the keys of 32 bits for the RC5 protocol
security environment in the IOT infrastructure (Jammu, and Singh, 2017). This is the simplest
algorithm used for increasing the efficiency of the AES algorithm. The data dependency can
be effectively evaluated by analysing the primitive of block size and cryptographic
procedures. The data can be dependent on different parameters for analysing the sequential
efficiency of the block ciphers developed for securing the architecture of the IOT devices.
The table below shows the tabular difference between security cryptographic algorithm used
for securing the system:
Cryptographic
algorithm
Maximum
length of
the code
Rounds
for
encryptio
n
Size
of
the
key
Size
of
the
bloc
k
Type of
vulnerabilities
Description
Advanced
encryption
symmetric
algorithm
2674 12 128 128 Denial of
service attack
Man in the
middle attack
The symmetric block
cipher is developed for
managing the
permutation network
environment for managing the coordination between the smart devices. The complex
operation can be solved by XOR gate for developing the 128 bit key size (Raval, Bansod,
Pishroty, 2015). The TEA protocol is used for resolving the complexities associated with the
simple operation. The TEA algorithm developed the block cipher for the encrypted message
in the limited number of lines.
PRESENT Protocol: It is the light weight cryptographic procedures which are used for
optimizing the output based on 4 input variables. The 128 bits key is applied on managing the
operation of 64 bit cipher block. It can solved 26 types of vulnerabilities associated with the
development framework of the application layer between IOT devices. The S-box are created
with the help of PRESENT algorithm. The scheduling of keys can be effectively done with
the help of this algorithm. The S-box are created by analysing the permutation layer.
RC5: The RC5 protocol is used for managing the operation for data independency. The
management of the wireless sensor can be effectively laid down with the use of RC5
protocol. 255 rounds are developed for creating the keys of 32 bits for the RC5 protocol
security environment in the IOT infrastructure (Jammu, and Singh, 2017). This is the simplest
algorithm used for increasing the efficiency of the AES algorithm. The data dependency can
be effectively evaluated by analysing the primitive of block size and cryptographic
procedures. The data can be dependent on different parameters for analysing the sequential
efficiency of the block ciphers developed for securing the architecture of the IOT devices.
The table below shows the tabular difference between security cryptographic algorithm used
for securing the system:
Cryptographic
algorithm
Maximum
length of
the code
Rounds
for
encryptio
n
Size
of
the
key
Size
of
the
bloc
k
Type of
vulnerabilities
Description
Advanced
encryption
symmetric
algorithm
2674 12 128 128 Denial of
service attack
Man in the
middle attack
The symmetric block
cipher is developed for
managing the
permutation network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
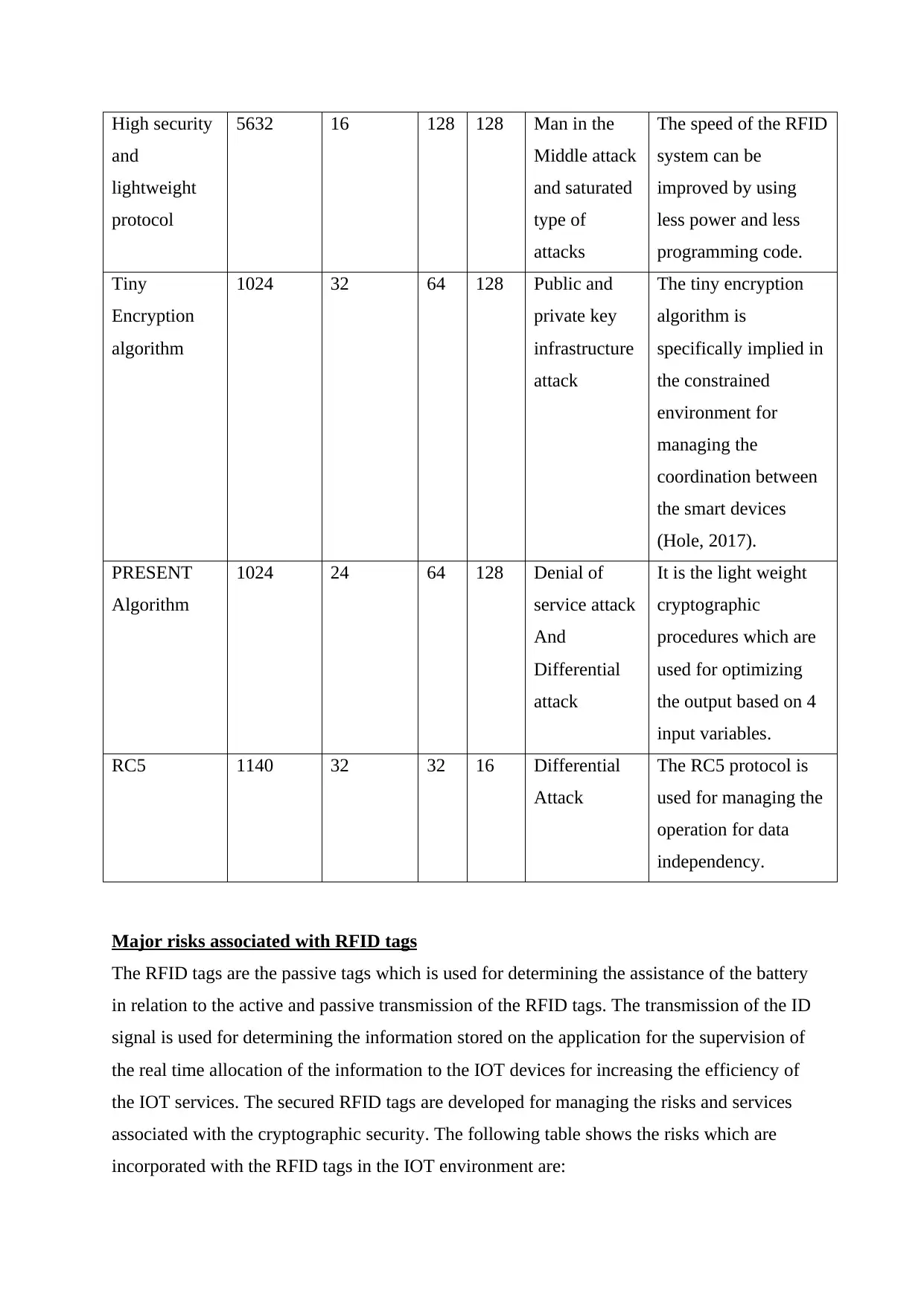
High security
and
lightweight
protocol
5632 16 128 128 Man in the
Middle attack
and saturated
type of
attacks
The speed of the RFID
system can be
improved by using
less power and less
programming code.
Tiny
Encryption
algorithm
1024 32 64 128 Public and
private key
infrastructure
attack
The tiny encryption
algorithm is
specifically implied in
the constrained
environment for
managing the
coordination between
the smart devices
(Hole, 2017).
PRESENT
Algorithm
1024 24 64 128 Denial of
service attack
And
Differential
attack
It is the light weight
cryptographic
procedures which are
used for optimizing
the output based on 4
input variables.
RC5 1140 32 32 16 Differential
Attack
The RC5 protocol is
used for managing the
operation for data
independency.
Major risks associated with RFID tags
The RFID tags are the passive tags which is used for determining the assistance of the battery
in relation to the active and passive transmission of the RFID tags. The transmission of the ID
signal is used for determining the information stored on the application for the supervision of
the real time allocation of the information to the IOT devices for increasing the efficiency of
the IOT services. The secured RFID tags are developed for managing the risks and services
associated with the cryptographic security. The following table shows the risks which are
incorporated with the RFID tags in the IOT environment are:
and
lightweight
protocol
5632 16 128 128 Man in the
Middle attack
and saturated
type of
attacks
The speed of the RFID
system can be
improved by using
less power and less
programming code.
Tiny
Encryption
algorithm
1024 32 64 128 Public and
private key
infrastructure
attack
The tiny encryption
algorithm is
specifically implied in
the constrained
environment for
managing the
coordination between
the smart devices
(Hole, 2017).
PRESENT
Algorithm
1024 24 64 128 Denial of
service attack
And
Differential
attack
It is the light weight
cryptographic
procedures which are
used for optimizing
the output based on 4
input variables.
RC5 1140 32 32 16 Differential
Attack
The RC5 protocol is
used for managing the
operation for data
independency.
Major risks associated with RFID tags
The RFID tags are the passive tags which is used for determining the assistance of the battery
in relation to the active and passive transmission of the RFID tags. The transmission of the ID
signal is used for determining the information stored on the application for the supervision of
the real time allocation of the information to the IOT devices for increasing the efficiency of
the IOT services. The secured RFID tags are developed for managing the risks and services
associated with the cryptographic security. The following table shows the risks which are
incorporated with the RFID tags in the IOT environment are:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
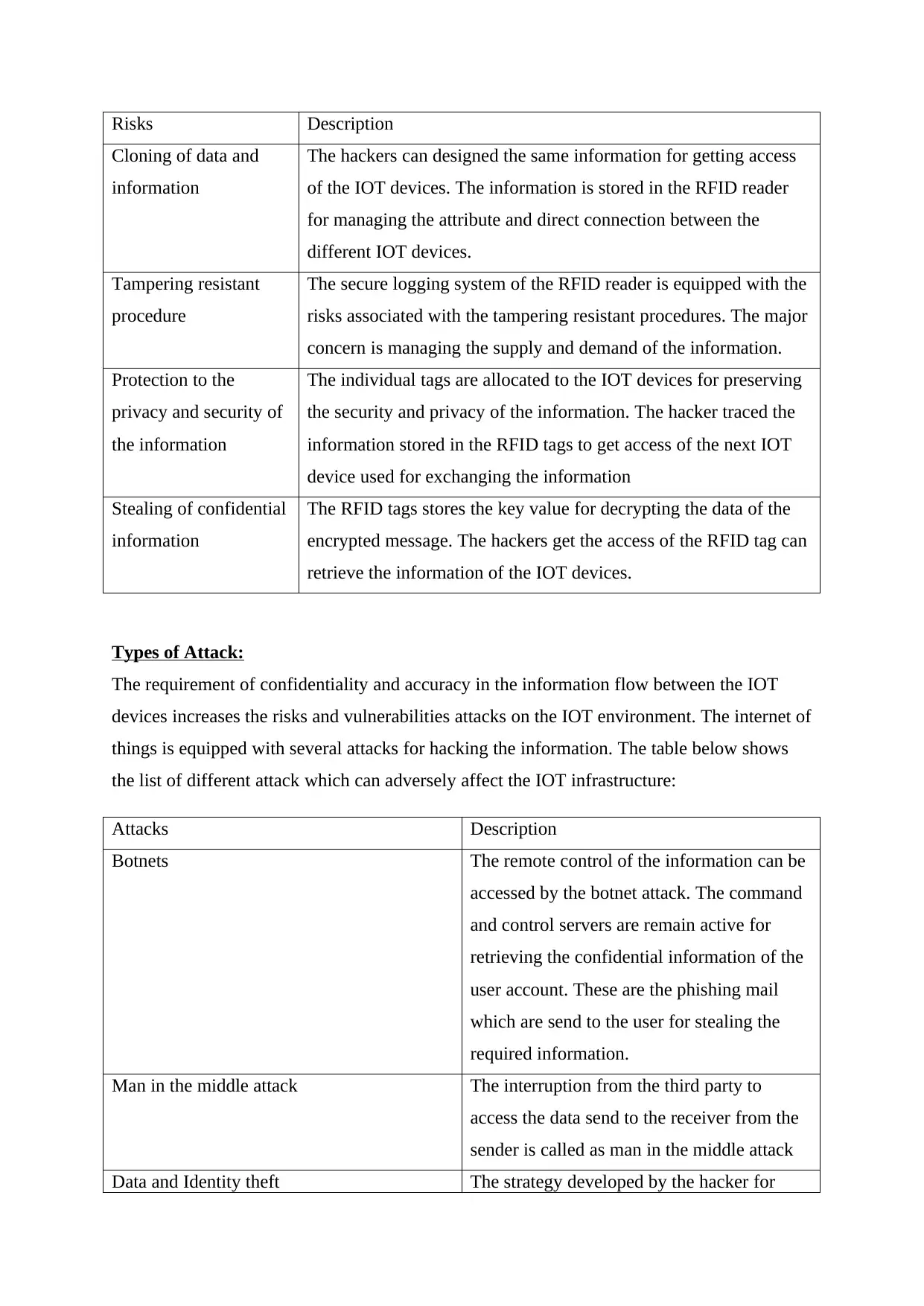
Risks Description
Cloning of data and
information
The hackers can designed the same information for getting access
of the IOT devices. The information is stored in the RFID reader
for managing the attribute and direct connection between the
different IOT devices.
Tampering resistant
procedure
The secure logging system of the RFID reader is equipped with the
risks associated with the tampering resistant procedures. The major
concern is managing the supply and demand of the information.
Protection to the
privacy and security of
the information
The individual tags are allocated to the IOT devices for preserving
the security and privacy of the information. The hacker traced the
information stored in the RFID tags to get access of the next IOT
device used for exchanging the information
Stealing of confidential
information
The RFID tags stores the key value for decrypting the data of the
encrypted message. The hackers get the access of the RFID tag can
retrieve the information of the IOT devices.
Types of Attack:
The requirement of confidentiality and accuracy in the information flow between the IOT
devices increases the risks and vulnerabilities attacks on the IOT environment. The internet of
things is equipped with several attacks for hacking the information. The table below shows
the list of different attack which can adversely affect the IOT infrastructure:
Attacks Description
Botnets The remote control of the information can be
accessed by the botnet attack. The command
and control servers are remain active for
retrieving the confidential information of the
user account. These are the phishing mail
which are send to the user for stealing the
required information.
Man in the middle attack The interruption from the third party to
access the data send to the receiver from the
sender is called as man in the middle attack
Data and Identity theft The strategy developed by the hacker for
Cloning of data and
information
The hackers can designed the same information for getting access
of the IOT devices. The information is stored in the RFID reader
for managing the attribute and direct connection between the
different IOT devices.
Tampering resistant
procedure
The secure logging system of the RFID reader is equipped with the
risks associated with the tampering resistant procedures. The major
concern is managing the supply and demand of the information.
Protection to the
privacy and security of
the information
The individual tags are allocated to the IOT devices for preserving
the security and privacy of the information. The hacker traced the
information stored in the RFID tags to get access of the next IOT
device used for exchanging the information
Stealing of confidential
information
The RFID tags stores the key value for decrypting the data of the
encrypted message. The hackers get the access of the RFID tag can
retrieve the information of the IOT devices.
Types of Attack:
The requirement of confidentiality and accuracy in the information flow between the IOT
devices increases the risks and vulnerabilities attacks on the IOT environment. The internet of
things is equipped with several attacks for hacking the information. The table below shows
the list of different attack which can adversely affect the IOT infrastructure:
Attacks Description
Botnets The remote control of the information can be
accessed by the botnet attack. The command
and control servers are remain active for
retrieving the confidential information of the
user account. These are the phishing mail
which are send to the user for stealing the
required information.
Man in the middle attack The interruption from the third party to
access the data send to the receiver from the
sender is called as man in the middle attack
Data and Identity theft The strategy developed by the hacker for
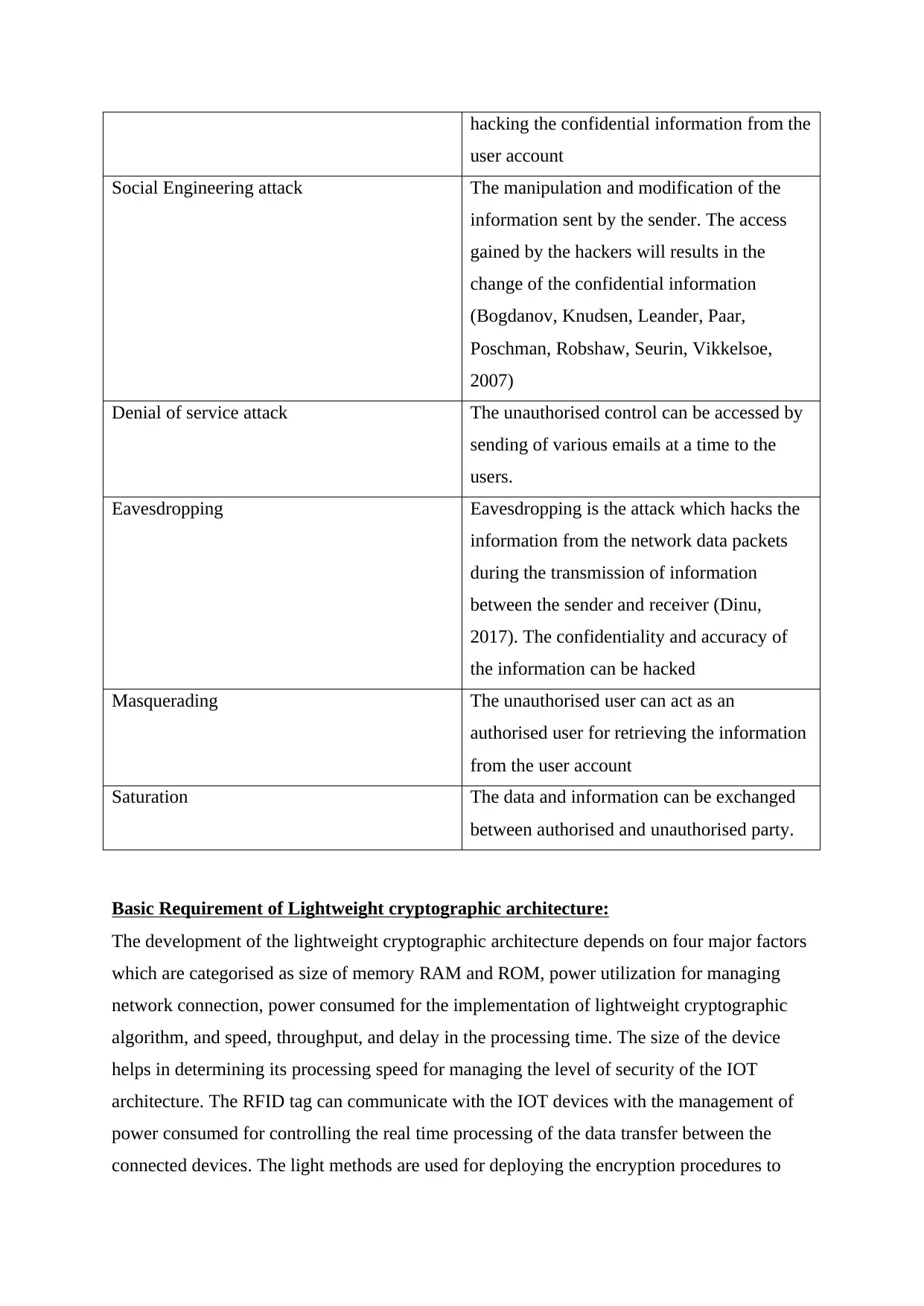
hacking the confidential information from the
user account
Social Engineering attack The manipulation and modification of the
information sent by the sender. The access
gained by the hackers will results in the
change of the confidential information
(Bogdanov, Knudsen, Leander, Paar,
Poschman, Robshaw, Seurin, Vikkelsoe,
2007)
Denial of service attack The unauthorised control can be accessed by
sending of various emails at a time to the
users.
Eavesdropping Eavesdropping is the attack which hacks the
information from the network data packets
during the transmission of information
between the sender and receiver (Dinu,
2017). The confidentiality and accuracy of
the information can be hacked
Masquerading The unauthorised user can act as an
authorised user for retrieving the information
from the user account
Saturation The data and information can be exchanged
between authorised and unauthorised party.
Basic Requirement of Lightweight cryptographic architecture:
The development of the lightweight cryptographic architecture depends on four major factors
which are categorised as size of memory RAM and ROM, power utilization for managing
network connection, power consumed for the implementation of lightweight cryptographic
algorithm, and speed, throughput, and delay in the processing time. The size of the device
helps in determining its processing speed for managing the level of security of the IOT
architecture. The RFID tag can communicate with the IOT devices with the management of
power consumed for controlling the real time processing of the data transfer between the
connected devices. The light methods are used for deploying the encryption procedures to
user account
Social Engineering attack The manipulation and modification of the
information sent by the sender. The access
gained by the hackers will results in the
change of the confidential information
(Bogdanov, Knudsen, Leander, Paar,
Poschman, Robshaw, Seurin, Vikkelsoe,
2007)
Denial of service attack The unauthorised control can be accessed by
sending of various emails at a time to the
users.
Eavesdropping Eavesdropping is the attack which hacks the
information from the network data packets
during the transmission of information
between the sender and receiver (Dinu,
2017). The confidentiality and accuracy of
the information can be hacked
Masquerading The unauthorised user can act as an
authorised user for retrieving the information
from the user account
Saturation The data and information can be exchanged
between authorised and unauthorised party.
Basic Requirement of Lightweight cryptographic architecture:
The development of the lightweight cryptographic architecture depends on four major factors
which are categorised as size of memory RAM and ROM, power utilization for managing
network connection, power consumed for the implementation of lightweight cryptographic
algorithm, and speed, throughput, and delay in the processing time. The size of the device
helps in determining its processing speed for managing the level of security of the IOT
architecture. The RFID tag can communicate with the IOT devices with the management of
power consumed for controlling the real time processing of the data transfer between the
connected devices. The light methods are used for deploying the encryption procedures to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 53
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




