PenTest (PTE) Report: Task 3 - Penetration Testing and Mitigation
VerifiedAdded on 2023/05/29
|32
|3649
|332
Report
AI Summary
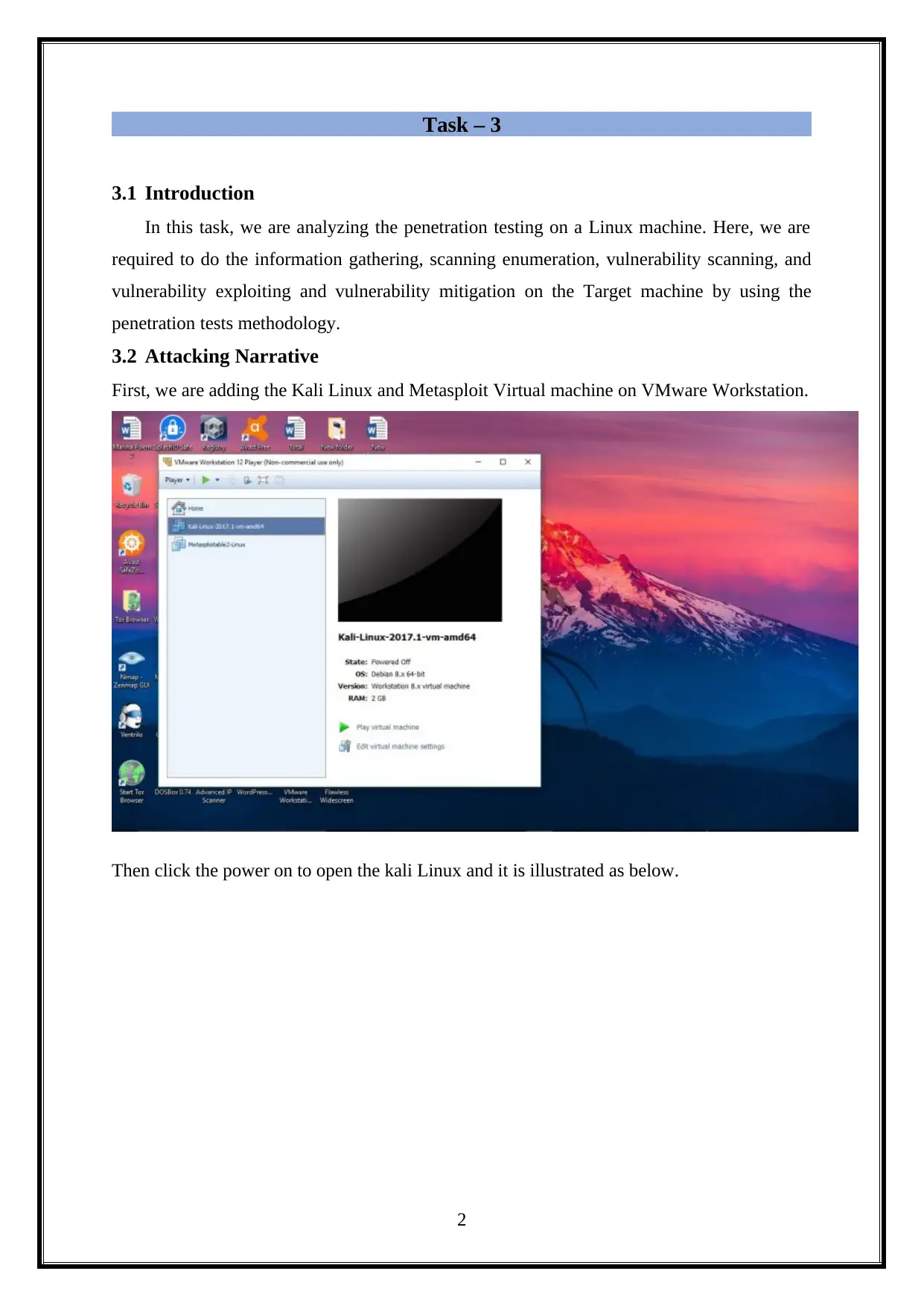
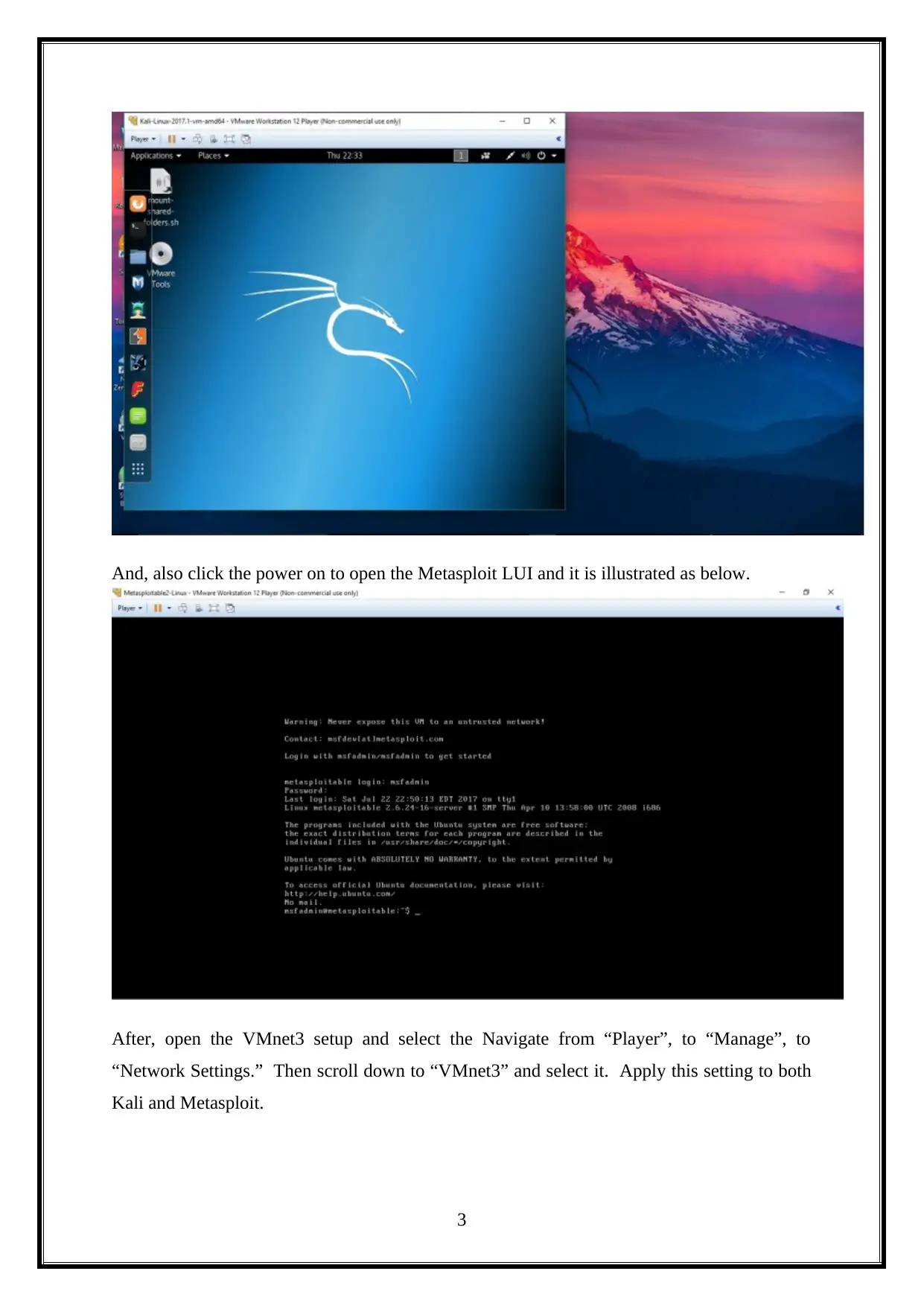
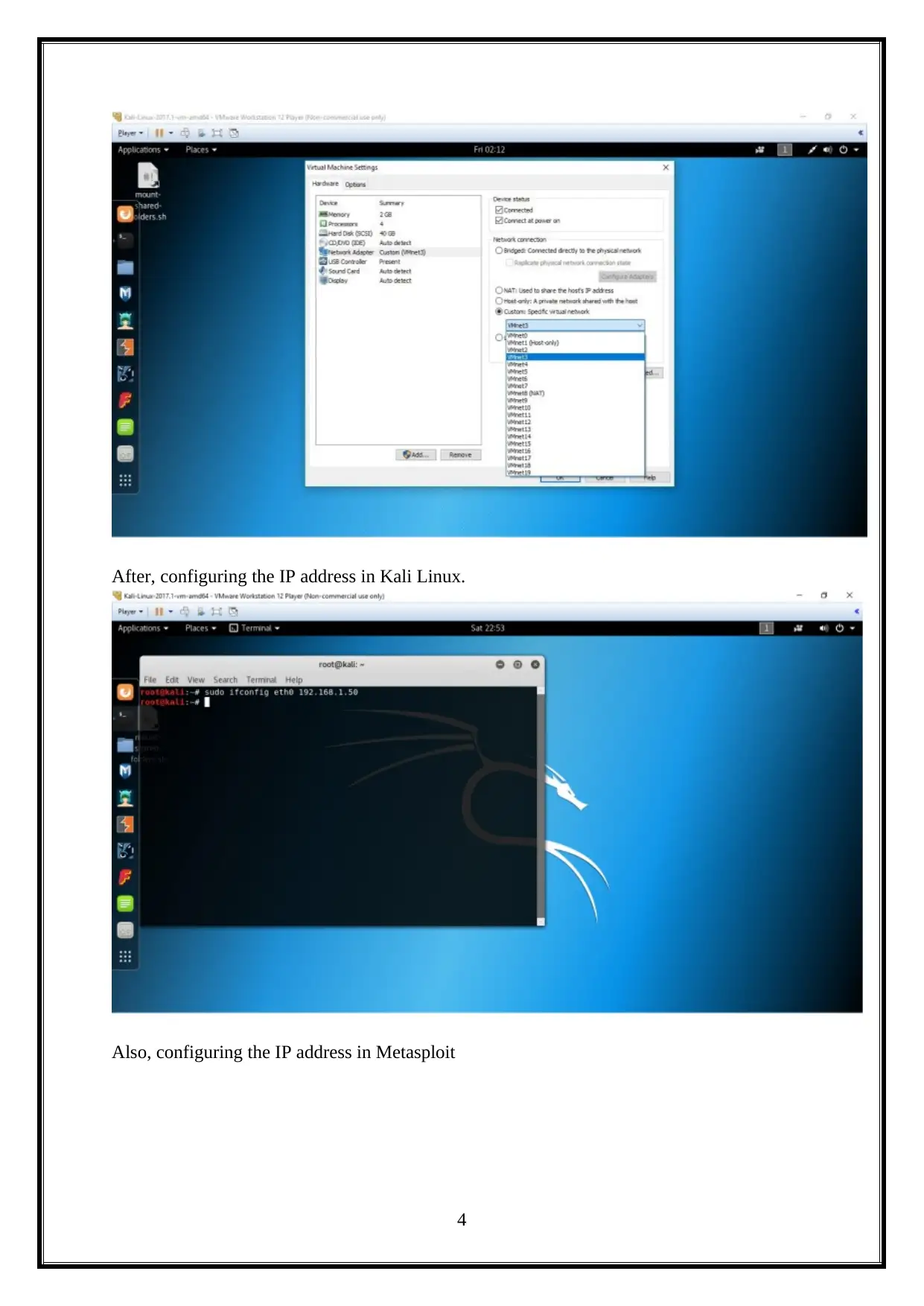
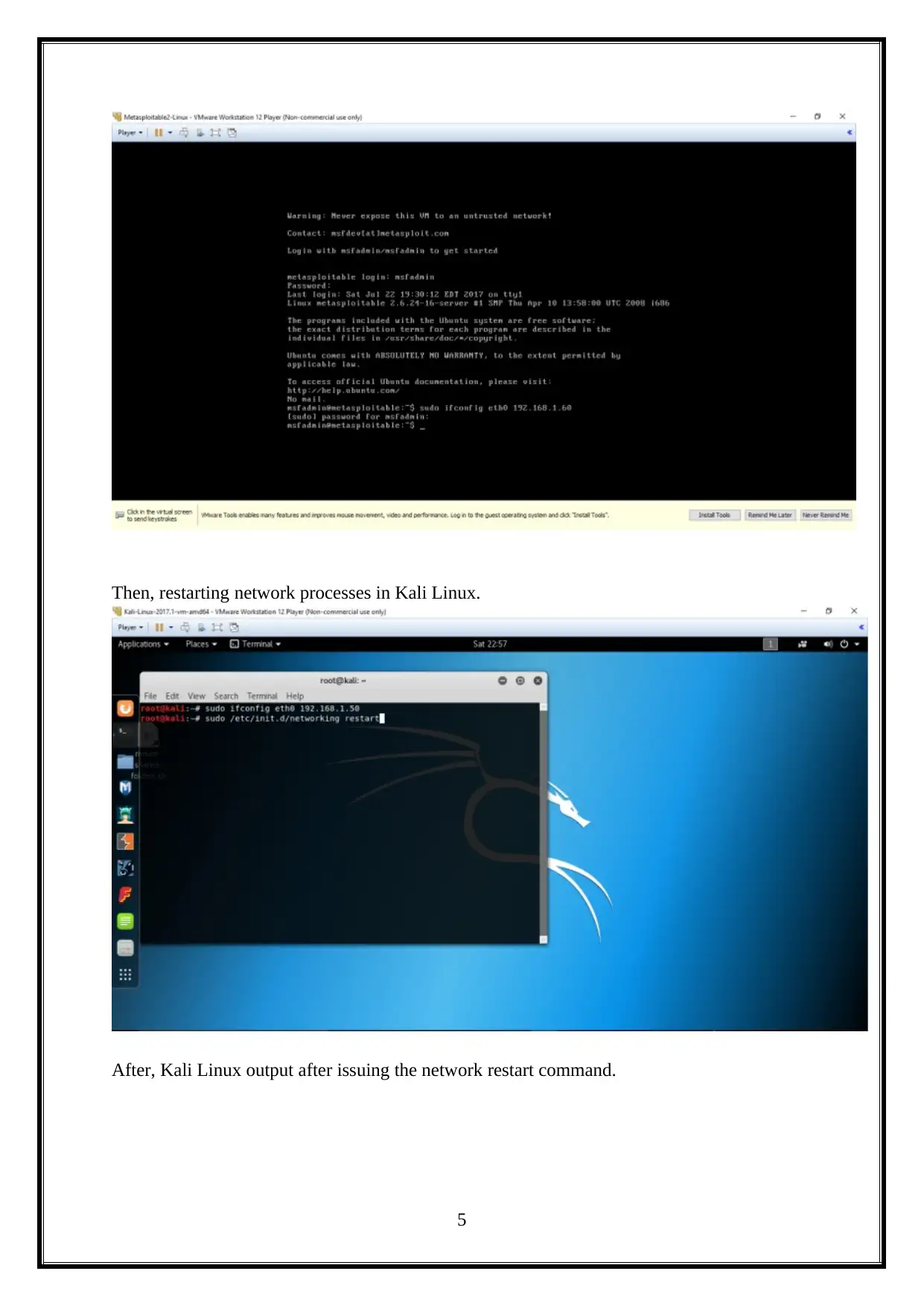
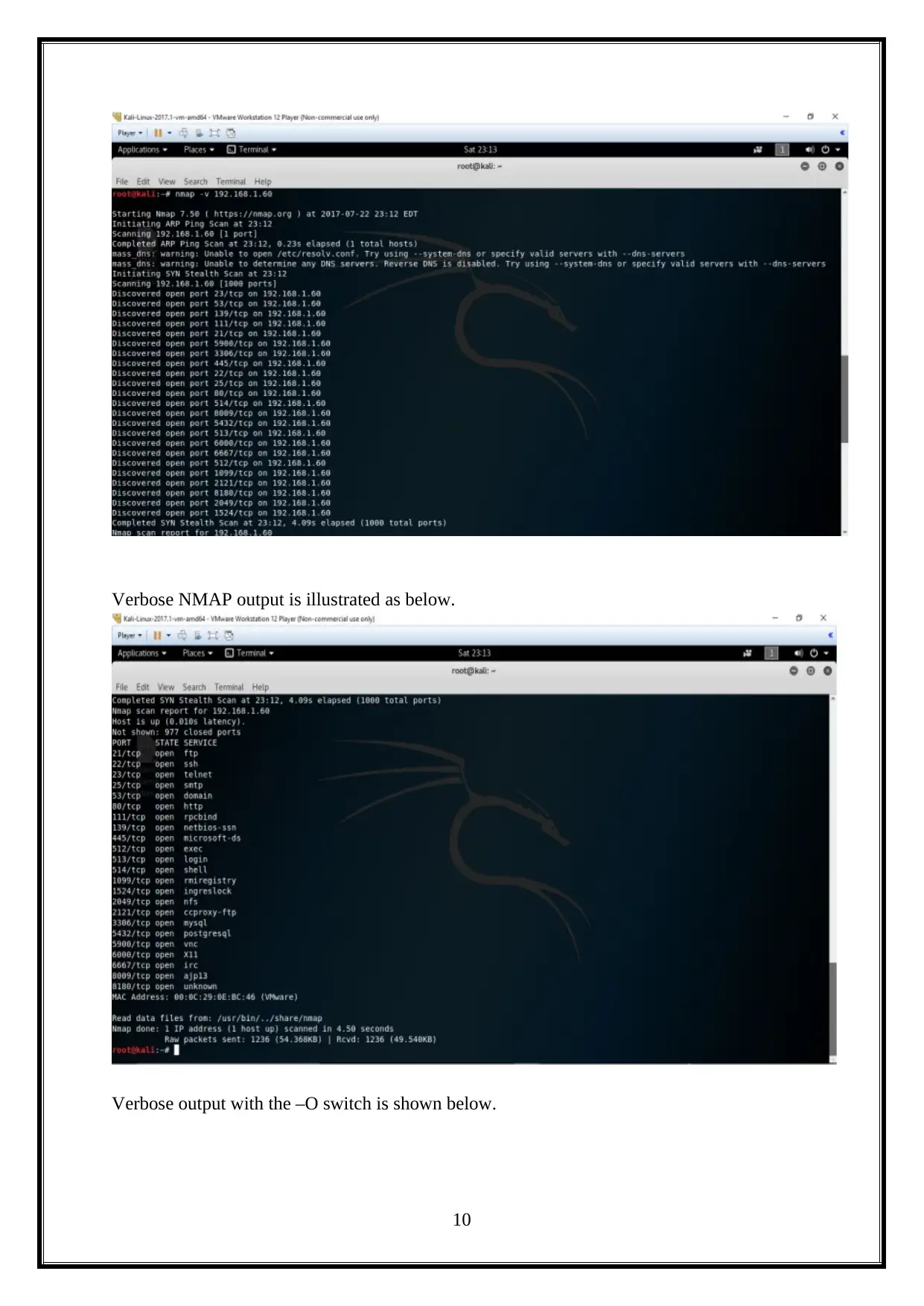
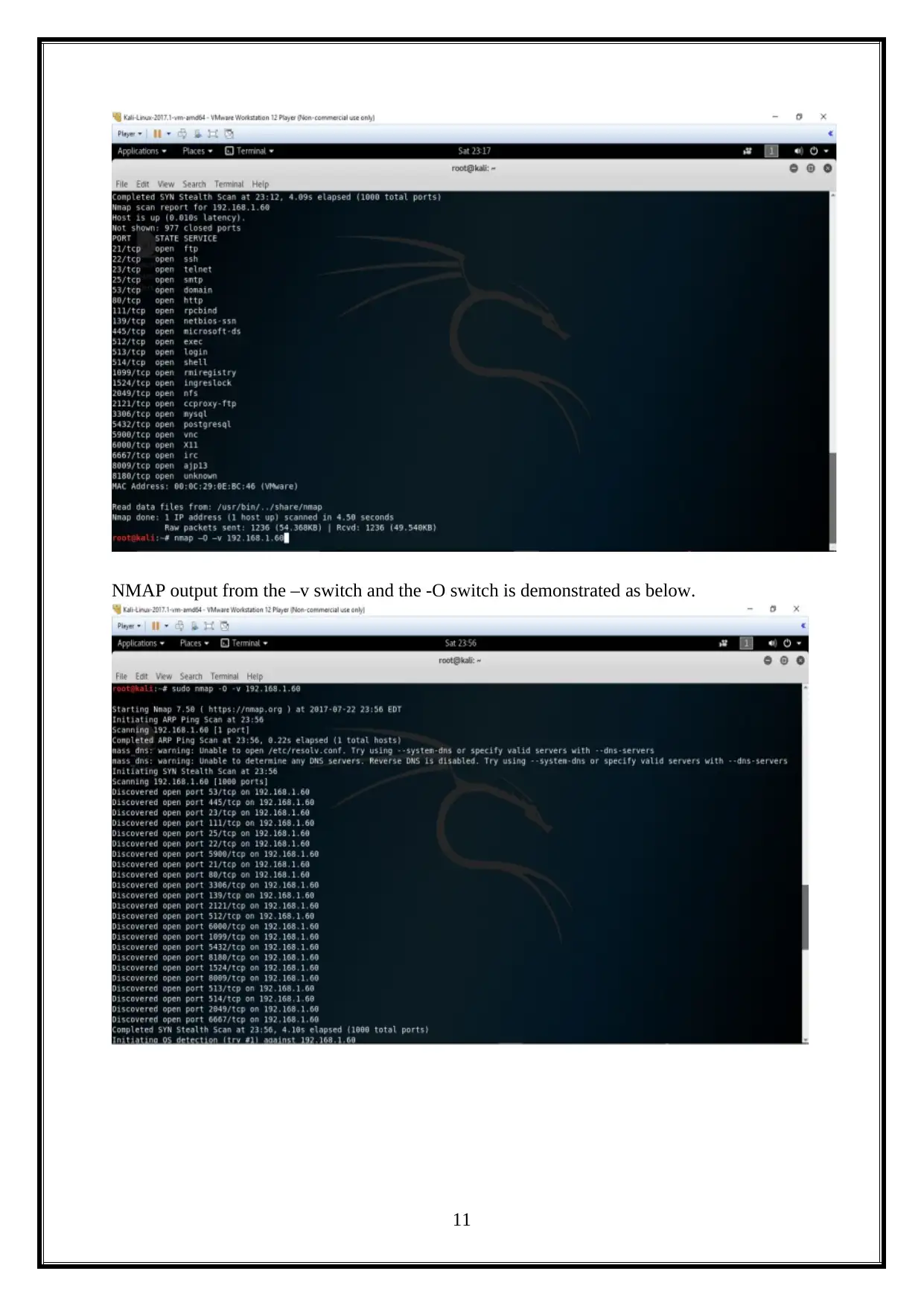
This report details a penetration test (PenTest) conducted on a Linux machine, encompassing information gathering, scanning, and vulnerability exploitation and mitigation. The report begins with an introduction to the methodology, followed by an attacking narrative that outlines the steps taken to compromise the target system. It covers information gathering using tools like Nmap, scanning and enumeration techniques, and vulnerability scanning with Nessus. The analysis includes exploiting vulnerabilities, such as command injection through DHCP, and concludes with a discussion of mitigation strategies. The assignment explores various tools and techniques, including attempts to retrieve WEP keys, Hydra attacks, and the use of tools like Wireshark and vulnerability scanners. The report also discusses different vulnerability scanning tools like Nessus and Tripwire IP360. The report culminates in conclusions and reflections on the overall penetration testing process.
1 out of 32









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)