Literature Review Assignment PDF
Added on 2021-04-24
25 Pages4078 Words68 Views
Literature Review (Secondary Research) TemplateStudent Name & CSU IDProject Topic TitleNOTE: Please you need to use YOUR OWN WORDS in writing this template.Your Literature Review Should be in Scope and MUST Address all Your Project's QuestionsYou should ONLY use CSU library, or other University Library, and Google search is NOT allowed. The papers you select should be in last 3 years. If you are in 2018, then you need to collect 2018, 2017, and 2016.We encourage you to search for Journal papers rather than conference papers as it will give you more details.Check the Journal ranking (Q1, Q2, ...etc) of the journal based on uploaded excel sheet in interact.1
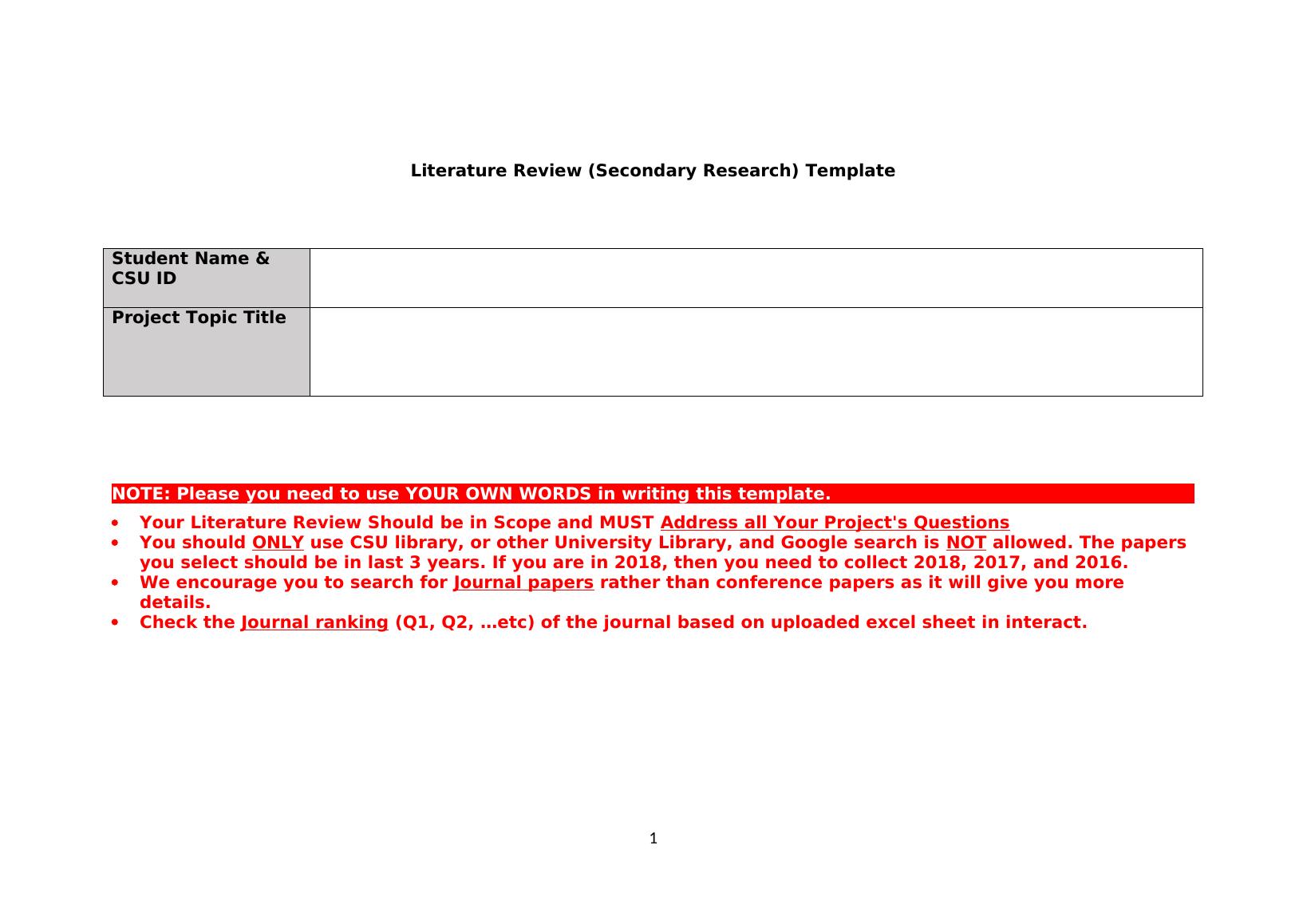
Example (How to work on each section in template below):2

3

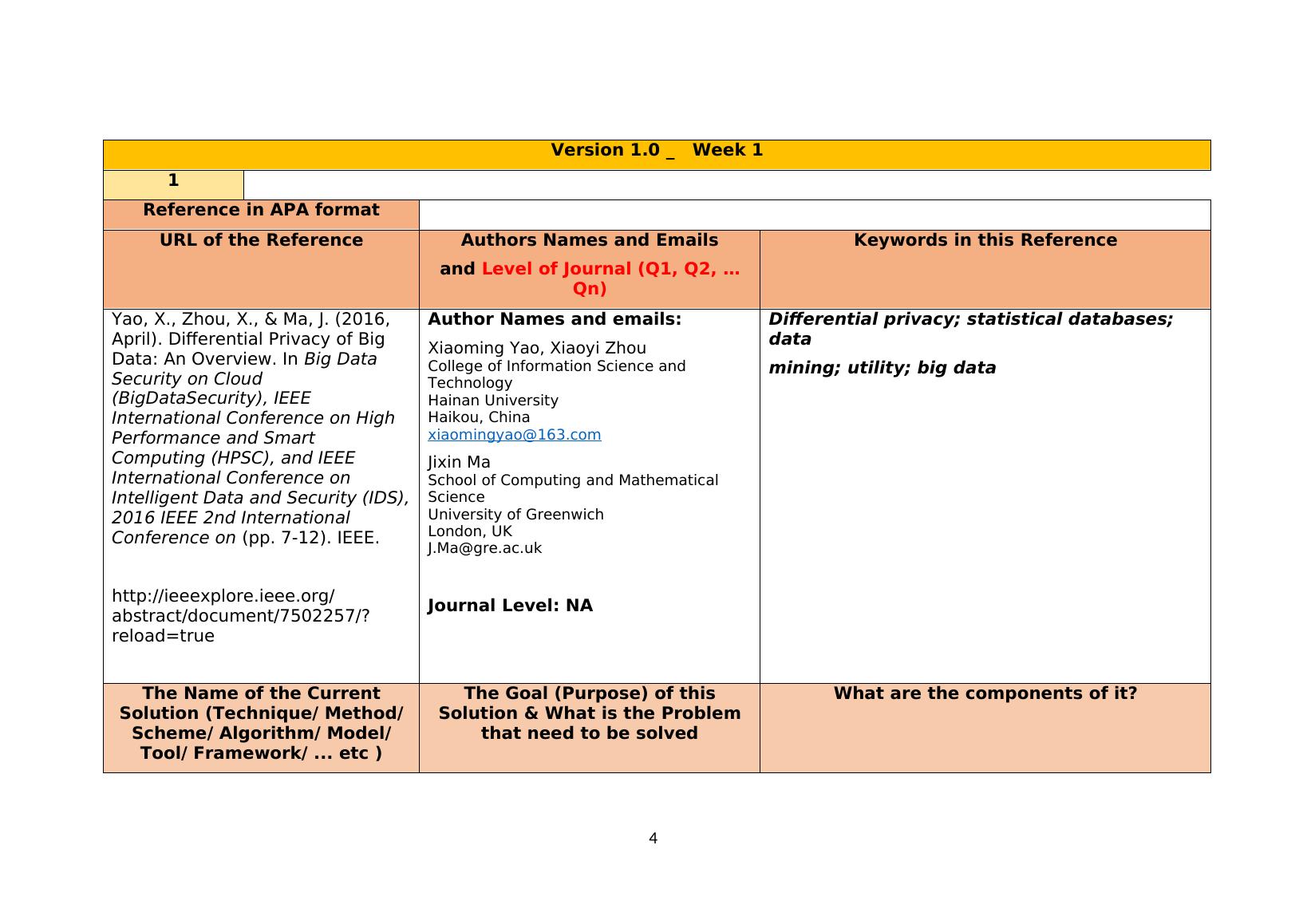
Version 1.0 _ Week 11Reference in APA formatURL of the ReferenceAuthors Names and Emailsand Level of Journal (Q1, Q2, ...Qn)Keywords in this ReferenceYao, X., Zhou, X., & Ma, J. (2016, April). Differential Privacy of Big Data: An Overview. InBig Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS), 2016 IEEE 2nd International Conference on(pp. 7-12). IEEE.http://ieeexplore.ieee.org/abstract/document/7502257/?reload=true Author Names and emails:Xiaoming Yao, Xiaoyi ZhouCollege of Information Science and TechnologyHainan UniversityHaikou, Chinaxiaomingyao@163.comJixin MaSchool of Computing and Mathematical ScienceUniversity of GreenwichLondon, UKJ.Ma@gre.ac.ukJournal Level: NADifferential privacy; statistical databases; datamining; utility; big dataThe Name of the CurrentSolution (Technique/ Method/Scheme/ Algorithm/ Model/Tool/ Framework/ ... etc ) The Goal (Purpose) of thisSolution & What is the Problemthat need to be solvedWhat are the components of it?4
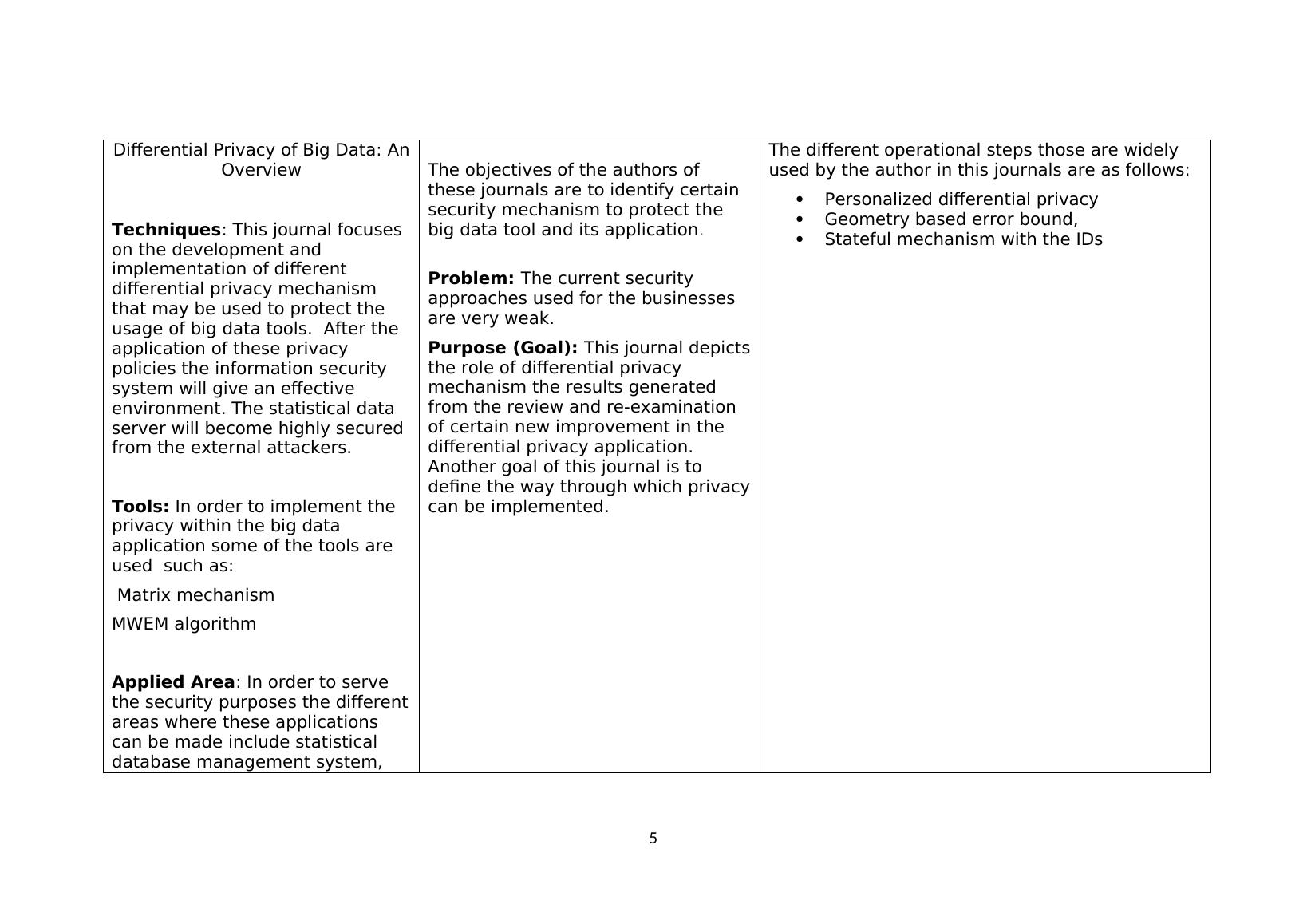
Differential Privacy of Big Data: AnOverviewTechniques: This journal focuses on the development and implementation of different differential privacy mechanism that may be used to protect the usage of big data tools. After the application of these privacy policies the information security system will give an effective environment. The statistical data server will become highly secured from the external attackers. Tools: In order to implement the privacy within the big data application some of the tools are used such as: Matrix mechanismMWEM algorithm Applied Area: In order to serve the security purposes the differentareas where these applications can be made include statistical database management system, The objectives of the authors of these journals are to identify certain security mechanism to protect the big data tool and its application. Problem: The current security approaches used for the businesses are very weak. Purpose (Goal): This journal depictsthe role of differential privacy mechanism the results generated from the review and re-examination of certain new improvement in the differential privacy application. Another goal of this journal is to define the way through which privacycan be implemented. The different operational steps those are widely used by the author in this journals are as follows:Personalized differential privacy Geometry based error bound,Stateful mechanism with the IDs 5
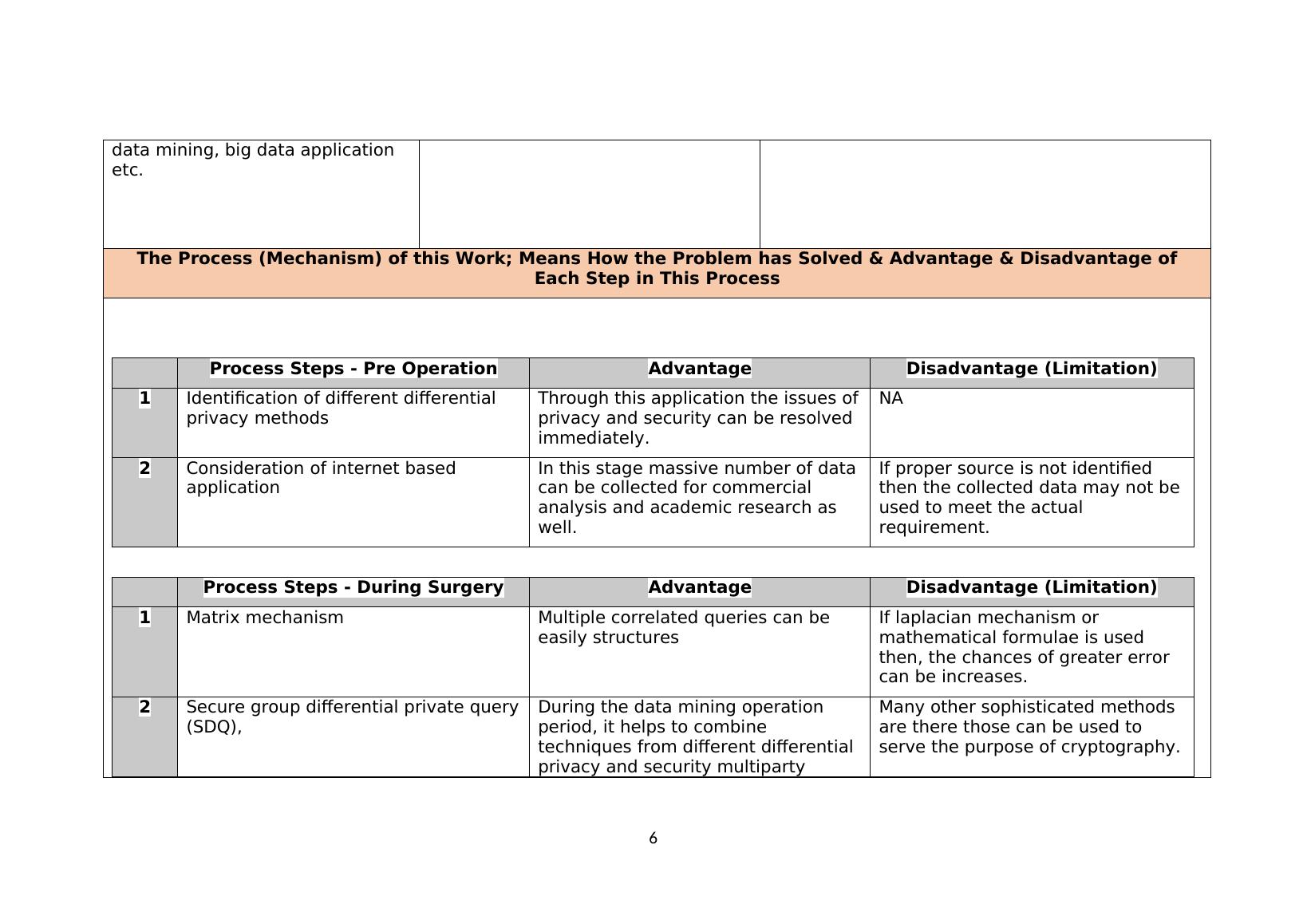
data mining, big data application etc. The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage ofEach Step in This ProcessProcess Steps - Pre OperationAdvantageDisadvantage (Limitation)1Identification of different differential privacy methods Through this application the issues ofprivacy and security can be resolved immediately. NA2Consideration of internet based application In this stage massive number of datacan be collected for commercial analysis and academic research as well.If proper source is not identified then the collected data may not beused to meet the actual requirement.Process Steps - During SurgeryAdvantageDisadvantage (Limitation)1Matrix mechanism Multiple correlated queries can be easily structures If laplacian mechanism or mathematical formulae is used then, the chances of greater error can be increases. 2Secure group differential private query(SDQ), During the data mining operation period, it helps to combine techniques from different differential privacy and security multiparty Many other sophisticated methods are there those can be used to serve the purpose of cryptography.6
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Review Based Project Literature Review (Secondary Research) Templatelg...
|134
|16192
|58
Cyber Physical System Structure of the Islanded Microgridlg...
|49
|4696
|40
Literature Review Template for Emerging Technology and Innovationlg...
|36
|6943
|381
Internet of Things for Smart Healthcare: Technologies, Challenges, and Opportunitieslg...
|95
|13000
|431
Literature Reviewlg...
|31
|3687
|399
