Local Area Network (LAN) Design and Implementation
VerifiedAdded on 2024/05/29
|34
|5014
|290
AI Summary
This document explores the design and implementation of a Local Area Network (LAN) infrastructure. It critically evaluates different LAN technologies, analyzes traffic-intensive services and their performance, and discusses concerns related to network security, reliability, and performance. The document also provides recommendations for sustaining network security, reliability, and performance, and critically evaluates the suitability of LAN components. Furthermore, it outlines the steps involved in building and configuring a LAN, including network security and configuration. The document concludes by discussing how the LAN infrastructure will be monitored and managed, resolving LAN issues to improve security, reliability, and performance, and critically evaluating the performance of the LAN.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Local Area Network
1
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Contents
Task 1..........................................................................................................................................................3
A.C 1.1 critically evaluate different LAN technologies.............................................................................3
The different types of networks..........................................................................................................3
The architecture of local networks......................................................................................................3
A.C 1.2 critically analyse traffic intensive services and their performance..............................................5
A.C 1.3 Discuss LAN concerns and make recommendations to sustain network security, reliability and
performance............................................................................................................................................7
Task 2..........................................................................................................................................................9
A.C 2.1 design a LAN infrastructure for the company which will facilitate all of their requirements......9
Design of network: concepts...............................................................................................................9
A.C 2.2 critically evaluate the suitability of LAN components................................................................11
Task 3........................................................................................................................................................14
A.C 3.1 build and configure a LAN.........................................................................................................14
AC 3.2 Network security and configuration...........................................................................................16
Task 4........................................................................................................................................................27
A.C 4.1 critically discuss how this LAN infrastructure will be monitored and managed........................27
A.C 4.2 resolve LAN issues to improve security, reliability and performance........................................29
The file must always reside in the c: \ windows , and on all network computers......................................29
A.C 4.3 critically evaluate the performance of a LAN............................................................................31
References.................................................................................................................................................32
2
Task 1..........................................................................................................................................................3
A.C 1.1 critically evaluate different LAN technologies.............................................................................3
The different types of networks..........................................................................................................3
The architecture of local networks......................................................................................................3
A.C 1.2 critically analyse traffic intensive services and their performance..............................................5
A.C 1.3 Discuss LAN concerns and make recommendations to sustain network security, reliability and
performance............................................................................................................................................7
Task 2..........................................................................................................................................................9
A.C 2.1 design a LAN infrastructure for the company which will facilitate all of their requirements......9
Design of network: concepts...............................................................................................................9
A.C 2.2 critically evaluate the suitability of LAN components................................................................11
Task 3........................................................................................................................................................14
A.C 3.1 build and configure a LAN.........................................................................................................14
AC 3.2 Network security and configuration...........................................................................................16
Task 4........................................................................................................................................................27
A.C 4.1 critically discuss how this LAN infrastructure will be monitored and managed........................27
A.C 4.2 resolve LAN issues to improve security, reliability and performance........................................29
The file must always reside in the c: \ windows , and on all network computers......................................29
A.C 4.3 critically evaluate the performance of a LAN............................................................................31
References.................................................................................................................................................32
2

Task 1
A.C 1.1 critically evaluate different LAN technologies
A network is a set of interrelated elements that are regulated in such a way that they can communicate.
It is fashionable to emphasize here the computer adage that says the network is the computer, that is to
say, that without the network the computer is under-exploited. Here are some examples of networking.
The establishment of a computer network facilitates and secures the storage of information.
It allows the standardization of applications and the sharing of data between workstations
efficiently.
Well-designed networking facilitates management and maintenance of applications and computer
equipment.
Networking can significantly reduce infrastructure costs.
Through the network, hardware and software resources are shared among several users. For example,
instead of buying multiple printers for each service, a printer can be shared by all services. It is the same
for distributed applications.
The different types of networks
There are different kinds of networks, depending on the size, information rate, types of communication
protocols, etc.
The architecture of local networks
There are several types of networks that differentiate among themselves according to the distance
between the computer systems or depending on the technology that allows to implement them.
Local area networks (LAN)
These are networks of more or less modest size, complex, which allow the exchange of computer data
and the sharing of resources (data, hard disks, various peripherals, etc.). The geographical extent of local
networks does not exceed 10 km (eg for a building or campus). The flow, or speed of communication,
varies from a few Mbps to 100 Mbps. The number of stations typically exceeds 1,000. A variant of the
LAN is the backbone or network basic (backbone) which is the main route taken by the traffic (Cisco, nd).
3
A.C 1.1 critically evaluate different LAN technologies
A network is a set of interrelated elements that are regulated in such a way that they can communicate.
It is fashionable to emphasize here the computer adage that says the network is the computer, that is to
say, that without the network the computer is under-exploited. Here are some examples of networking.
The establishment of a computer network facilitates and secures the storage of information.
It allows the standardization of applications and the sharing of data between workstations
efficiently.
Well-designed networking facilitates management and maintenance of applications and computer
equipment.
Networking can significantly reduce infrastructure costs.
Through the network, hardware and software resources are shared among several users. For example,
instead of buying multiple printers for each service, a printer can be shared by all services. It is the same
for distributed applications.
The different types of networks
There are different kinds of networks, depending on the size, information rate, types of communication
protocols, etc.
The architecture of local networks
There are several types of networks that differentiate among themselves according to the distance
between the computer systems or depending on the technology that allows to implement them.
Local area networks (LAN)
These are networks of more or less modest size, complex, which allow the exchange of computer data
and the sharing of resources (data, hard disks, various peripherals, etc.). The geographical extent of local
networks does not exceed 10 km (eg for a building or campus). The flow, or speed of communication,
varies from a few Mbps to 100 Mbps. The number of stations typically exceeds 1,000. A variant of the
LAN is the backbone or network basic (backbone) which is the main route taken by the traffic (Cisco, nd).
3
Virtual Local Area Networks (VLANs)
A VLAN is a logical group of units or users that can be grouped by function, service or application
regardless of the location of their physical segment. The configuration of a VLAN is done in the switch by
software. Virtual Local Area Networks are not standardized and require the use of proprietary software
sold by the provider of switches. This type of network is seen in more detail in the next section.
Wireless local area networks (wireless, LAN or WLAN)
These are networks without visible physical connections. These networks use the waves (radio, infrared,
etc.) as a communication medium. Computers mobiles or personal assistants (Palm Pilot, etc.) constitute
the sector IT is growing faster. Many owners of this type of computers also have a computer connected
to LANs or WANs, at home or at home. Office, to which they are connected at all times
4
A VLAN is a logical group of units or users that can be grouped by function, service or application
regardless of the location of their physical segment. The configuration of a VLAN is done in the switch by
software. Virtual Local Area Networks are not standardized and require the use of proprietary software
sold by the provider of switches. This type of network is seen in more detail in the next section.
Wireless local area networks (wireless, LAN or WLAN)
These are networks without visible physical connections. These networks use the waves (radio, infrared,
etc.) as a communication medium. Computers mobiles or personal assistants (Palm Pilot, etc.) constitute
the sector IT is growing faster. Many owners of this type of computers also have a computer connected
to LANs or WANs, at home or at home. Office, to which they are connected at all times
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

A.C 1.2 critically analyse traffic intensive services and their performance
The term local area network, formerly defined as a network of computers located in the same enclosure,
currently designates a set of connected machines in the same field of diffusion. Information sent by a
computer in a broadcast to its network is thus received by all the stations of this network. The broadcast
domains, separated by routers, depend on architectures physical connection hardware. In local
networks, switches pose a problem. Indeed, it is the fact that switch fails to provide good information
access filtering contained in the frame headers of the network, transport or application layers. This
prompted manufacturers to think about a solution that can ensure the speed of the data. That’s the
reason that made the best solution was to replace in this architecture the switch by a router. This is able
not only to apply advanced filtering but also to split the “dissemination domain” into subdomains.
Unfortunately, the use a router to interconnect subnets also presents some disadvantages. Here are a
few:
An increase in slow communication between subnetworks: where the switch was simply guiding the
frame, the router must handle the header of the package contained in the frame.
More complicated management of IP addresses, because of the division into several DHCP domains,
each with its own DHCP server. It is noted that some routers can provide the DHCP server function
themselves. DHCP is the acronym of Dynamic Host Configuration Protocol which is a service
implemented in a network to automatically provide IP addresses to a device that connects.
Reduced flexibility: a machine that moves between two subnets can not, in general, keep its IP network
address, IPX, etc.
Also, the connection of machines to a concentrator - and, therefore, subnetting - is usually done on a
criterion of physical proximity, which does not correspond always to the organizational divisions and
therefore to the needs of access filtering (Cisco, nd).
It was, therefore, necessary that a new technology be developed to overcome these shortcomings. This
is how virtual local networks or VLANs came into being. The VLAN brought solutions, sometimes partial,
to these rather complex problems. Indeed, thanks to VLAN, it is now possible to disconnect the logical
structure of groups of workers of the physical structure of the network. Initially, this type of network
was based on proprietary solutions, but the development of IEEE 802.1Q standards has allowed today to
guarantee a certain interoperability. The purpose of the 802.1Q standard requires VLANs to be
compatible with MAC protocols of all standards802 series LAN (Ethernet, Token Ring, FDDI, Fast
5
The term local area network, formerly defined as a network of computers located in the same enclosure,
currently designates a set of connected machines in the same field of diffusion. Information sent by a
computer in a broadcast to its network is thus received by all the stations of this network. The broadcast
domains, separated by routers, depend on architectures physical connection hardware. In local
networks, switches pose a problem. Indeed, it is the fact that switch fails to provide good information
access filtering contained in the frame headers of the network, transport or application layers. This
prompted manufacturers to think about a solution that can ensure the speed of the data. That’s the
reason that made the best solution was to replace in this architecture the switch by a router. This is able
not only to apply advanced filtering but also to split the “dissemination domain” into subdomains.
Unfortunately, the use a router to interconnect subnets also presents some disadvantages. Here are a
few:
An increase in slow communication between subnetworks: where the switch was simply guiding the
frame, the router must handle the header of the package contained in the frame.
More complicated management of IP addresses, because of the division into several DHCP domains,
each with its own DHCP server. It is noted that some routers can provide the DHCP server function
themselves. DHCP is the acronym of Dynamic Host Configuration Protocol which is a service
implemented in a network to automatically provide IP addresses to a device that connects.
Reduced flexibility: a machine that moves between two subnets can not, in general, keep its IP network
address, IPX, etc.
Also, the connection of machines to a concentrator - and, therefore, subnetting - is usually done on a
criterion of physical proximity, which does not correspond always to the organizational divisions and
therefore to the needs of access filtering (Cisco, nd).
It was, therefore, necessary that a new technology be developed to overcome these shortcomings. This
is how virtual local networks or VLANs came into being. The VLAN brought solutions, sometimes partial,
to these rather complex problems. Indeed, thanks to VLAN, it is now possible to disconnect the logical
structure of groups of workers of the physical structure of the network. Initially, this type of network
was based on proprietary solutions, but the development of IEEE 802.1Q standards has allowed today to
guarantee a certain interoperability. The purpose of the 802.1Q standard requires VLANs to be
compatible with MAC protocols of all standards802 series LAN (Ethernet, Token Ring, FDDI, Fast
5

Ethernet, Gigabit, etc.).A VLAN, therefore, uses next-generation switches of the same type that Ethernet
or heterogeneous technology and which are interconnected by a network broadband backbone ( Fast
Ethernet, Gigabit Ethernet, FDDI, ATM ). A very important aspect for VLANs is that they can be limited to
a single switch or connect remote machines, connected to different switches. Thus, the “domains
“broadcast” are the individual VLANs. Even if the connection of a machine to a switch is done on a
criterion of physical proximity, this does not prevent this machine to be part of the same VLAN as
machines connected to another switch.
6
or heterogeneous technology and which are interconnected by a network broadband backbone ( Fast
Ethernet, Gigabit Ethernet, FDDI, ATM ). A very important aspect for VLANs is that they can be limited to
a single switch or connect remote machines, connected to different switches. Thus, the “domains
“broadcast” are the individual VLANs. Even if the connection of a machine to a switch is done on a
criterion of physical proximity, this does not prevent this machine to be part of the same VLAN as
machines connected to another switch.
6

A.C 1.3 Discuss LAN concerns and make recommendations to sustain network security,
reliability and performance
It was discussed as to why the VLAN is used and this was recommended as an improvement over LAN.
But, VLANs have intrinsic problems as well. As far as operation is concerned, we can distinguish different
types of VLAN.
Level 1 VLANs based on port numbers. In that case, the membership of a machine to a VLAN
depends on the number of the port through which it is connected to the switch. This technique is
not flexible, in the where, whenever a machine has to be moved, it is necessary to redefine its VLAN
membership. Moreover, in some configurations, it is difficult to ensure a strict separation between
VLANs: a machine can possibly receive frames that are not intended for the VLAN to which she
belongs to.
Level 2 VLANs based on the IEEE 802 MAC address (or address”Physical”). In this case, the
membership of a machine to a VLAN depends on the MAC address (Ethernet, etc.) of the machine. A
very good level of security can be assured because the MAC address is intrinsic to the network card
of the machine, and therefore cannot be modified by a malicious user. Furthermore, if the machine
is moved, the filter tables can be updated from automatically, so the administration of the VLAN is
simplified. On the other hand, initially set VLANs from MAC addresses is extremely tedious because
the MAC addresses are not structured and must be entered one by one.
The VLAN Layer 2 based on the identity of the higher level protocol indicated in the IEEE 802.2 header.
This technique can be applied to the condition of heterogeneity at level 3 protocols. interesting in that it
allows for the restriction of “broadcast” to machines whose network protocols make frequent use
diffusion (IPX, Appletalk, etc.), thus reducing the negative impact of this one on the other machines in
the network (Cisco, nd).
• The VLAN level 3 based on level 3 address (IP, network number IPX, etc.). All Level 3 address or
part only, sub number network, can be used to define the membership of a machine to a VLAN. Even if
the machine is moved, it keeps its level 3 address and therefore its membership in a VLAN. Since the
level 3 address can be modified by a malicious user (to change VLANs), this technology may pose
security problems. In addition, the obligation for a switch to look at the address in the level 3 header
increases its latency. In general, the switches used do not perform any function of routing and use the
level 3 address only to determine the VLAN to which the machine belongs. The definition of a VLAN from
7
reliability and performance
It was discussed as to why the VLAN is used and this was recommended as an improvement over LAN.
But, VLANs have intrinsic problems as well. As far as operation is concerned, we can distinguish different
types of VLAN.
Level 1 VLANs based on port numbers. In that case, the membership of a machine to a VLAN
depends on the number of the port through which it is connected to the switch. This technique is
not flexible, in the where, whenever a machine has to be moved, it is necessary to redefine its VLAN
membership. Moreover, in some configurations, it is difficult to ensure a strict separation between
VLANs: a machine can possibly receive frames that are not intended for the VLAN to which she
belongs to.
Level 2 VLANs based on the IEEE 802 MAC address (or address”Physical”). In this case, the
membership of a machine to a VLAN depends on the MAC address (Ethernet, etc.) of the machine. A
very good level of security can be assured because the MAC address is intrinsic to the network card
of the machine, and therefore cannot be modified by a malicious user. Furthermore, if the machine
is moved, the filter tables can be updated from automatically, so the administration of the VLAN is
simplified. On the other hand, initially set VLANs from MAC addresses is extremely tedious because
the MAC addresses are not structured and must be entered one by one.
The VLAN Layer 2 based on the identity of the higher level protocol indicated in the IEEE 802.2 header.
This technique can be applied to the condition of heterogeneity at level 3 protocols. interesting in that it
allows for the restriction of “broadcast” to machines whose network protocols make frequent use
diffusion (IPX, Appletalk, etc.), thus reducing the negative impact of this one on the other machines in
the network (Cisco, nd).
• The VLAN level 3 based on level 3 address (IP, network number IPX, etc.). All Level 3 address or
part only, sub number network, can be used to define the membership of a machine to a VLAN. Even if
the machine is moved, it keeps its level 3 address and therefore its membership in a VLAN. Since the
level 3 address can be modified by a malicious user (to change VLANs), this technology may pose
security problems. In addition, the obligation for a switch to look at the address in the level 3 header
increases its latency. In general, the switches used do not perform any function of routing and use the
level 3 address only to determine the VLAN to which the machine belongs. The definition of a VLAN from
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the level 3 addresses is simplified thanks to the hierarchical logical structure of these addresses
(network number, subnet number, number of machines).
• Higher level VLANs, based on different information present in successive headers of level 3, 4, or
more. The need to search information in successive headers, sometimes of variable format, significantly
increases the response time of the switches. We thus see that the definition of VLANs makes it possible
to separate groups of machines from the point of view of physical access. In addition, access to
machines several VLANs (servers, administrative stations) also exist, although general source of
problems for type 1 VLANs
8
(network number, subnet number, number of machines).
• Higher level VLANs, based on different information present in successive headers of level 3, 4, or
more. The need to search information in successive headers, sometimes of variable format, significantly
increases the response time of the switches. We thus see that the definition of VLANs makes it possible
to separate groups of machines from the point of view of physical access. In addition, access to
machines several VLANs (servers, administrative stations) also exist, although general source of
problems for type 1 VLANs
8

Task 2
In this section, we are to demonstrate ability towards planning and prioritising tasks and
responsibilities and be able to discuss the benefits of design a network system for the given case study
9
In this section, we are to demonstrate ability towards planning and prioritising tasks and
responsibilities and be able to discuss the benefits of design a network system for the given case study
9
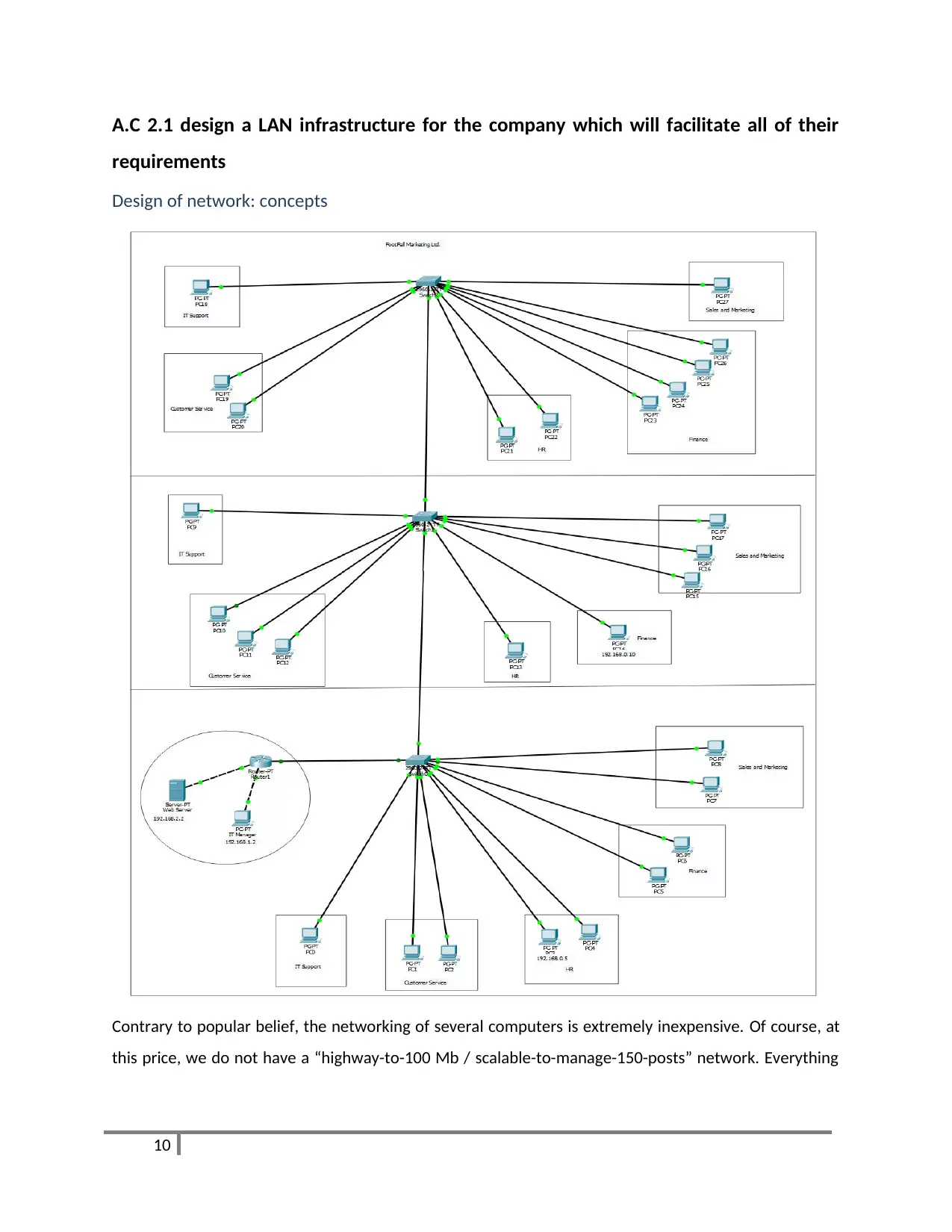
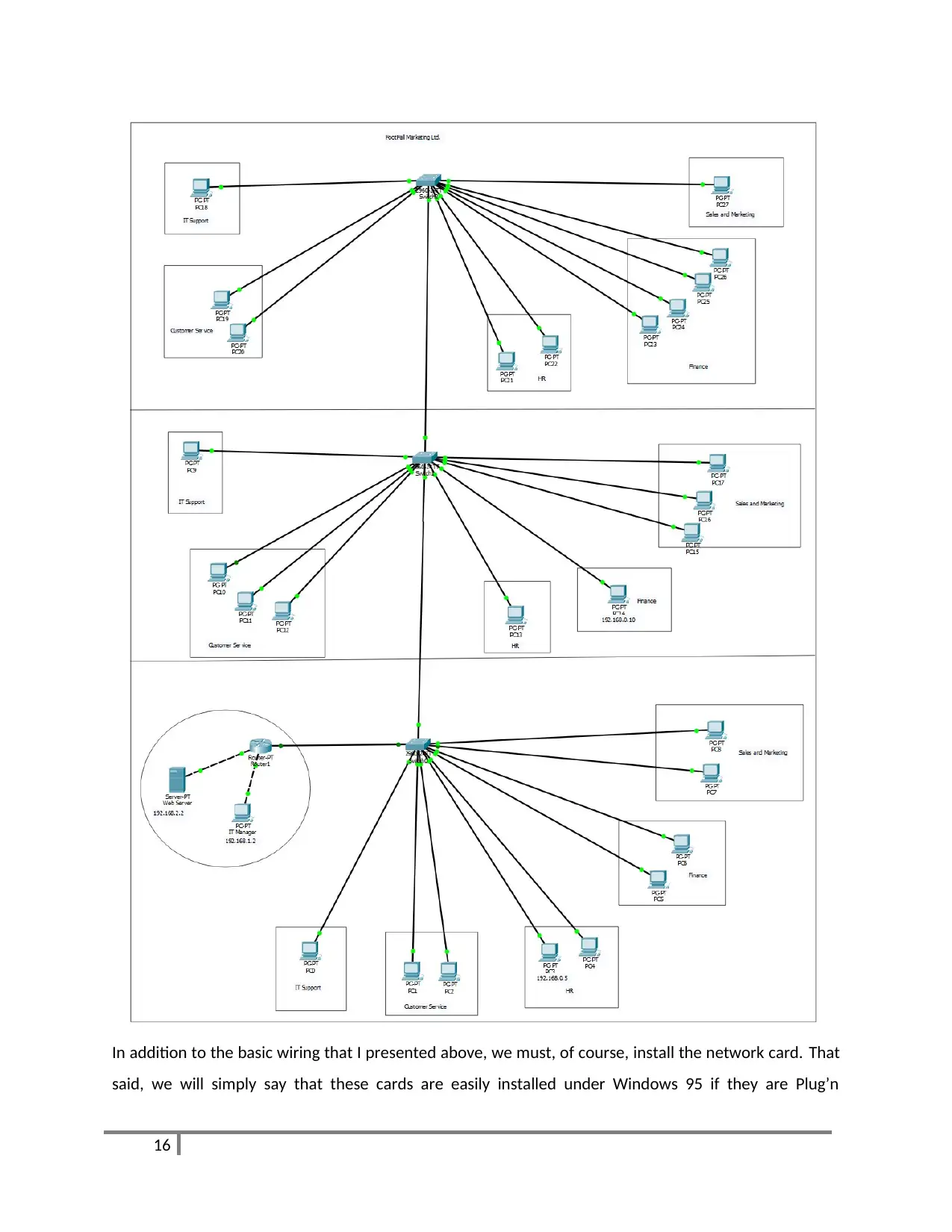
A.C 2.1 design a LAN infrastructure for the company which will facilitate all of their
requirements
Design of network: concepts
Contrary to popular belief, the networking of several computers is extremely inexpensive. Of course, at
this price, we do not have a “highway-to-100 Mb / scalable-to-manage-150-posts” network. Everything
10
requirements
Design of network: concepts
Contrary to popular belief, the networking of several computers is extremely inexpensive. Of course, at
this price, we do not have a “highway-to-100 Mb / scalable-to-manage-150-posts” network. Everything
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

depends on the use we want to make: it is really useless to equip with high-end equipment (and much
more expensive) for a network of fewer than 15 positions that has no professional purpose.
For a simple network of this type, the only hardware that needs to be equipped is:
a NE2000 Ethernet network card (up to 10 Mb / s) on ISA or PCI port per station. As an indication,
such cards are less than CHF 30 (Swiss), which is not ruinous.
Thin-Ethernet cables (RG-68) (often referred to as coaxial cable) not always cheap. That said, it is
best to build the cable sections themselves: there are easily shops that sell the cable separately
by the meter and the BNC (British Naval Connectors) connectors (screw or crimp). It is then
necessary to count about Sfr. 1.50. -- / meter of cable and 4.—per connector. (Cisco, nd).
An alternative to coaxial cable is the use of UTP (Unshielded Twisted Pairs) cable with RJ-45 (registered
jack) connectors, but this involves the acquisition of a HUB and complicates the network structure (see
next paragraph). This solution is also a bit more expensive.
11
more expensive) for a network of fewer than 15 positions that has no professional purpose.
For a simple network of this type, the only hardware that needs to be equipped is:
a NE2000 Ethernet network card (up to 10 Mb / s) on ISA or PCI port per station. As an indication,
such cards are less than CHF 30 (Swiss), which is not ruinous.
Thin-Ethernet cables (RG-68) (often referred to as coaxial cable) not always cheap. That said, it is
best to build the cable sections themselves: there are easily shops that sell the cable separately
by the meter and the BNC (British Naval Connectors) connectors (screw or crimp). It is then
necessary to count about Sfr. 1.50. -- / meter of cable and 4.—per connector. (Cisco, nd).
An alternative to coaxial cable is the use of UTP (Unshielded Twisted Pairs) cable with RJ-45 (registered
jack) connectors, but this involves the acquisition of a HUB and complicates the network structure (see
next paragraph). This solution is also a bit more expensive.
11
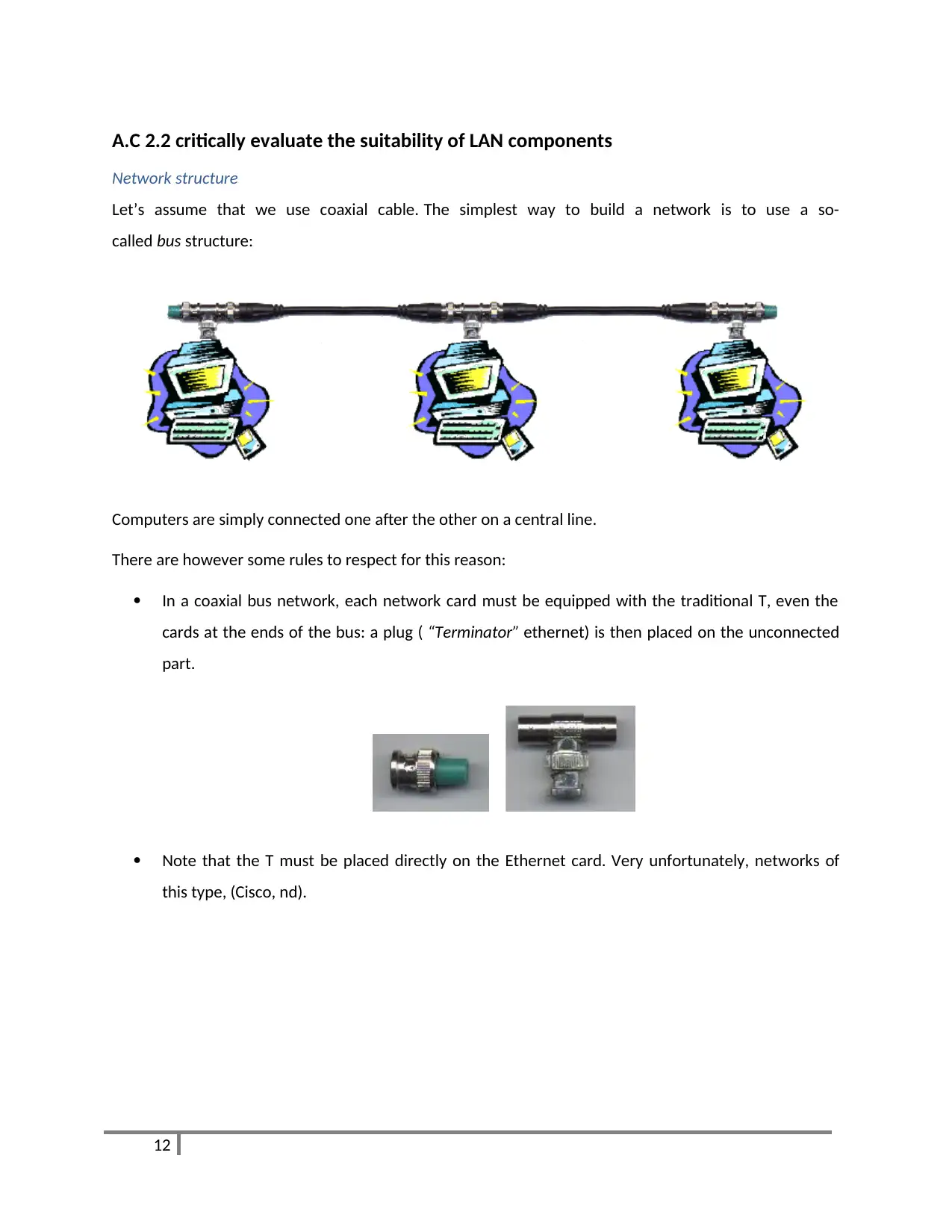
A.C 2.2 critically evaluate the suitability of LAN components
Network structure
Let’s assume that we use coaxial cable. The simplest way to build a network is to use a so-
called bus structure:
Computers are simply connected one after the other on a central line.
There are however some rules to respect for this reason:
In a coaxial bus network, each network card must be equipped with the traditional T, even the
cards at the ends of the bus: a plug ( “Terminator” ethernet) is then placed on the unconnected
part.
Note that the T must be placed directly on the Ethernet card. Very unfortunately, networks of
this type, (Cisco, nd).
12
Network structure
Let’s assume that we use coaxial cable. The simplest way to build a network is to use a so-
called bus structure:
Computers are simply connected one after the other on a central line.
There are however some rules to respect for this reason:
In a coaxial bus network, each network card must be equipped with the traditional T, even the
cards at the ends of the bus: a plug ( “Terminator” ethernet) is then placed on the unconnected
part.
Note that the T must be placed directly on the Ethernet card. Very unfortunately, networks of
this type, (Cisco, nd).
12

Which would be very practical in their design, do not work for reasons of impedance, as remarkably
explained to me a visitor (electrician!) of this site. In fact, the electrician will tell us that, on a coaxial
bus, we can still afford only 1 computer with a “remote T” (and so the above network should
work!). In the same vein, we obviously ban “whimsical” type networks
Coaxial networks are by far the least expensive. They simply require a number of Ethernet cables to
connect the different computers to each other and purchase two terminators. On the other hand, they
have an intrinsic defect: a cable break (or any fault (which may be common on home-made cables)) at a
certain location may at best “split” the network in two or worse paralyze the entire network. The big
disadvantage of the coaxial cable is the great difficulty of locating the location of a breakdown.
The alternative is to use UTP (RJ-45) cable. Unlike coax, the
computers are connected to a central unit called HUB (which is
quite expensive). Depending on the topology of the premises, this
solution may be less practical in terms of wiring that is more
13
explained to me a visitor (electrician!) of this site. In fact, the electrician will tell us that, on a coaxial
bus, we can still afford only 1 computer with a “remote T” (and so the above network should
work!). In the same vein, we obviously ban “whimsical” type networks
Coaxial networks are by far the least expensive. They simply require a number of Ethernet cables to
connect the different computers to each other and purchase two terminators. On the other hand, they
have an intrinsic defect: a cable break (or any fault (which may be common on home-made cables)) at a
certain location may at best “split” the network in two or worse paralyze the entire network. The big
disadvantage of the coaxial cable is the great difficulty of locating the location of a breakdown.
The alternative is to use UTP (RJ-45) cable. Unlike coax, the
computers are connected to a central unit called HUB (which is
quite expensive). Depending on the topology of the premises, this
solution may be less practical in terms of wiring that is more
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

abundant. On the other hand, it has a certain advantage: if a segment is damaged, the rest of the
network is not affected. In addition, UTP is faster than coaxial, but this difference is almost negligible
with the use of NE2000 10 Mbps cards (Cisco, nd).
At the moment, however (given the sharp drop in prices of RJ-45 components), I recommend that we
prefer, if we have the means, the UTP coaxial: we will enjoy more “safe” and more performance. If we
only need to connect two computers, we can do it directly with RJ-45 without having to buy a HUB. But
beware: we must use for this an RJ-45 cable called “cross” that we will surely find in speciality shops.
14
network is not affected. In addition, UTP is faster than coaxial, but this difference is almost negligible
with the use of NE2000 10 Mbps cards (Cisco, nd).
At the moment, however (given the sharp drop in prices of RJ-45 components), I recommend that we
prefer, if we have the means, the UTP coaxial: we will enjoy more “safe” and more performance. If we
only need to connect two computers, we can do it directly with RJ-45 without having to buy a HUB. But
beware: we must use for this an RJ-45 cable called “cross” that we will surely find in speciality shops.
14

Task 3
A.C 3.1 build and configure a LAN
15
A.C 3.1 build and configure a LAN
15
In addition to the basic wiring that I presented above, we must, of course, install the network card. That
said, we will simply say that these cards are easily installed under Windows 95 if they are Plug’n
16
said, we will simply say that these cards are easily installed under Windows 95 if they are Plug’n
16
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Play. We can usually put aside the floppy disk provided by the manufacturer, Windows95 providing
almost universal “NE2000 compatible” drivers. These generic drivers work very well for a BNC network,
but are not always efficient for an RJ-45 network (collision problems in the HUB); in this case, find
specific drivers for our card.
We will eventually notice that these cards, besides an I / O port, also require a free IRQ. I hope for we
that there is at least one left on our PC.
17
almost universal “NE2000 compatible” drivers. These generic drivers work very well for a BNC network,
but are not always efficient for an RJ-45 network (collision problems in the HUB); in this case, find
specific drivers for our card.
We will eventually notice that these cards, besides an I / O port, also require a free IRQ. I hope for we
that there is at least one left on our PC.
17
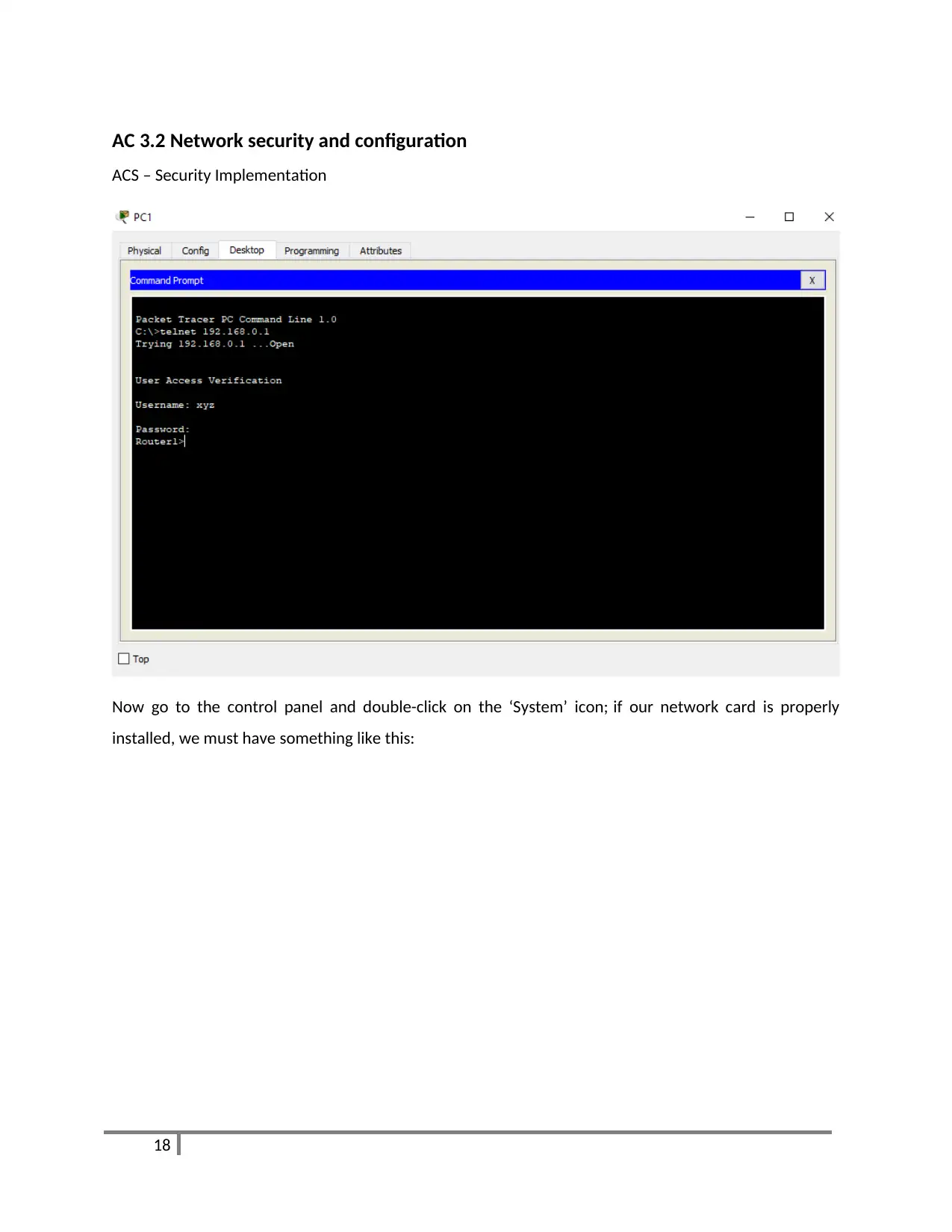
AC 3.2 Network security and configuration
ACS – Security Implementation
Now go to the control panel and double-click on the ‘System’ icon; if our network card is properly
installed, we must have something like this:
18
ACS – Security Implementation
Now go to the control panel and double-click on the ‘System’ icon; if our network card is properly
installed, we must have something like this:
18
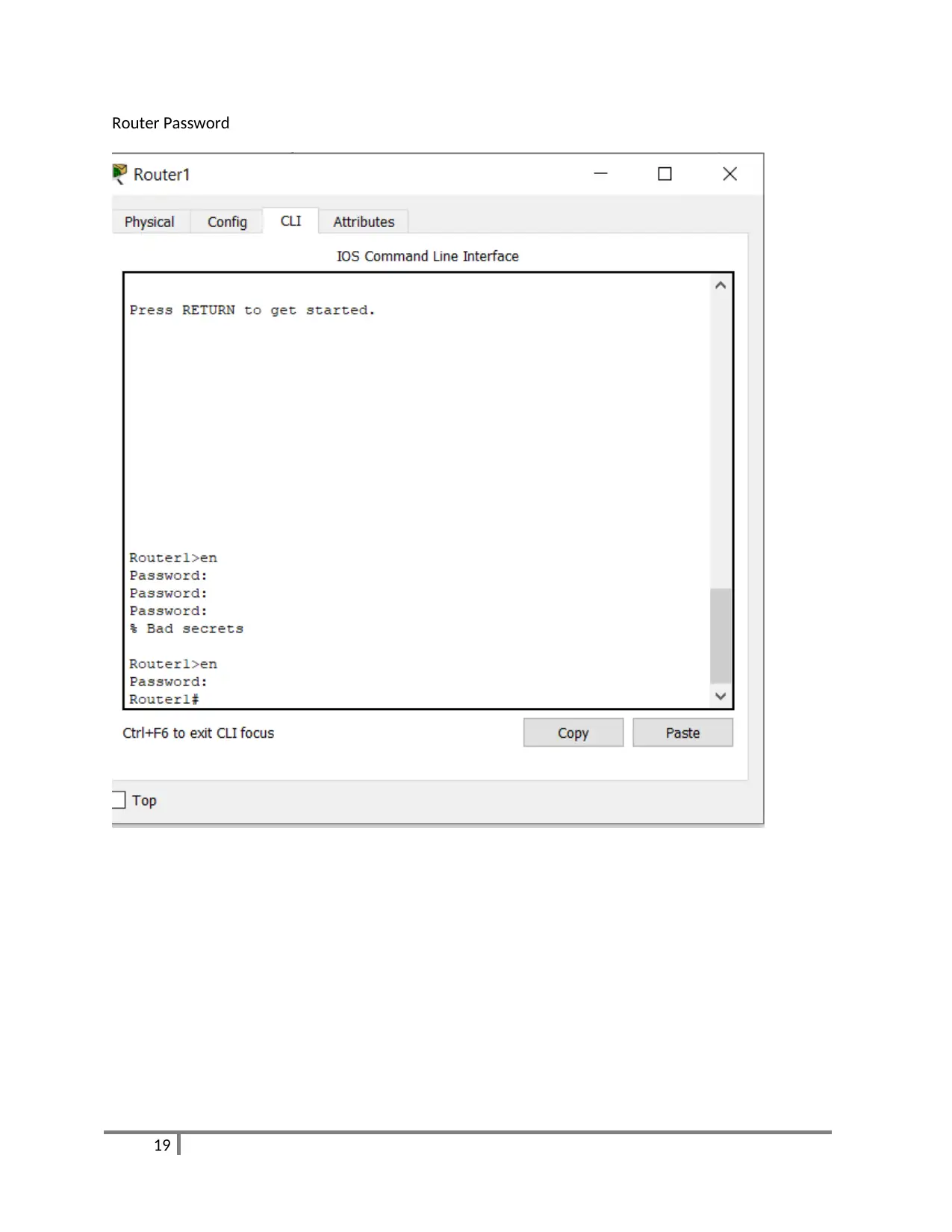
Router Password
19
19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
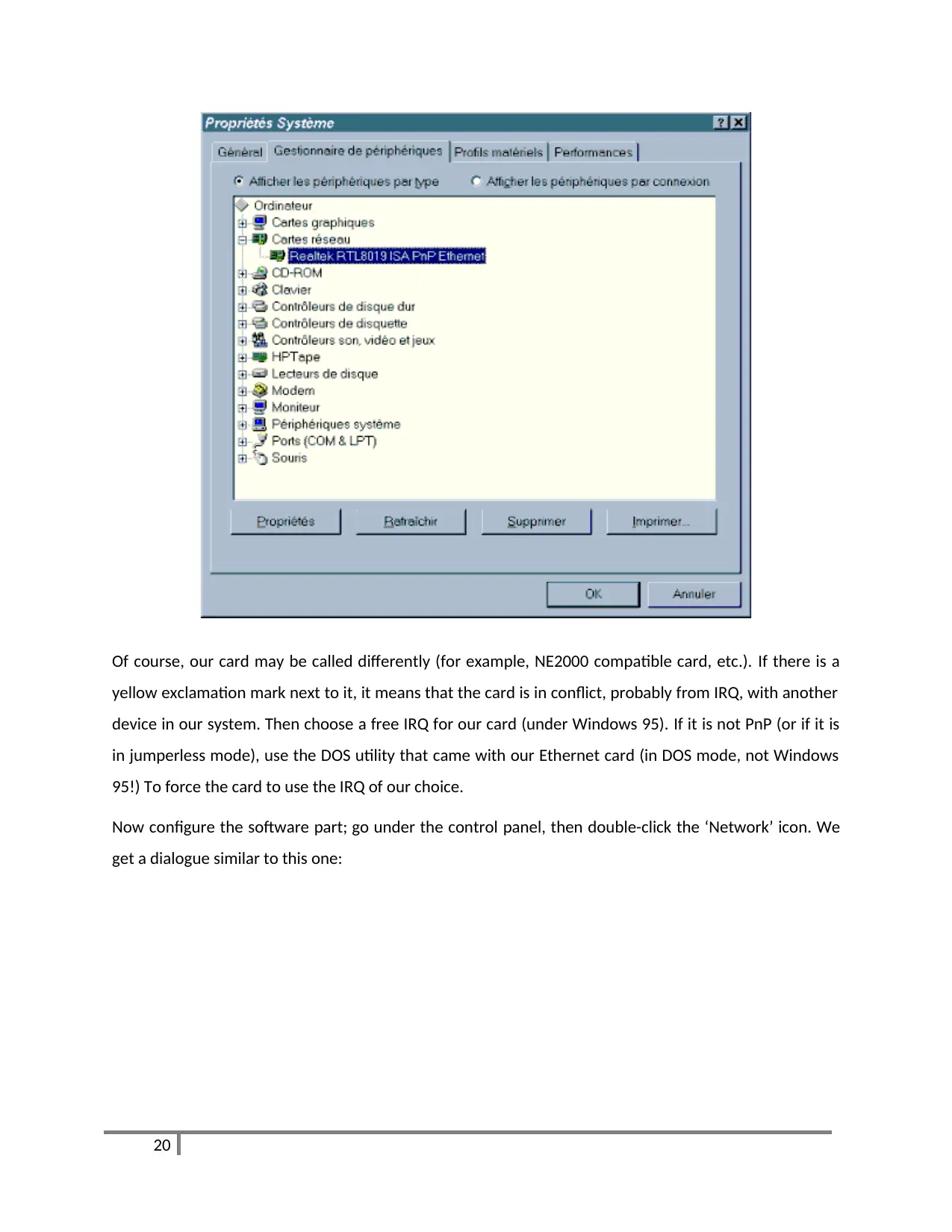
Of course, our card may be called differently (for example, NE2000 compatible card, etc.). If there is a
yellow exclamation mark next to it, it means that the card is in conflict, probably from IRQ, with another
device in our system. Then choose a free IRQ for our card (under Windows 95). If it is not PnP (or if it is
in jumperless mode), use the DOS utility that came with our Ethernet card (in DOS mode, not Windows
95!) To force the card to use the IRQ of our choice.
Now configure the software part; go under the control panel, then double-click the ‘Network’ icon. We
get a dialogue similar to this one:
20
yellow exclamation mark next to it, it means that the card is in conflict, probably from IRQ, with another
device in our system. Then choose a free IRQ for our card (under Windows 95). If it is not PnP (or if it is
in jumperless mode), use the DOS utility that came with our Ethernet card (in DOS mode, not Windows
95!) To force the card to use the IRQ of our choice.
Now configure the software part; go under the control panel, then double-click the ‘Network’ icon. We
get a dialogue similar to this one:
20
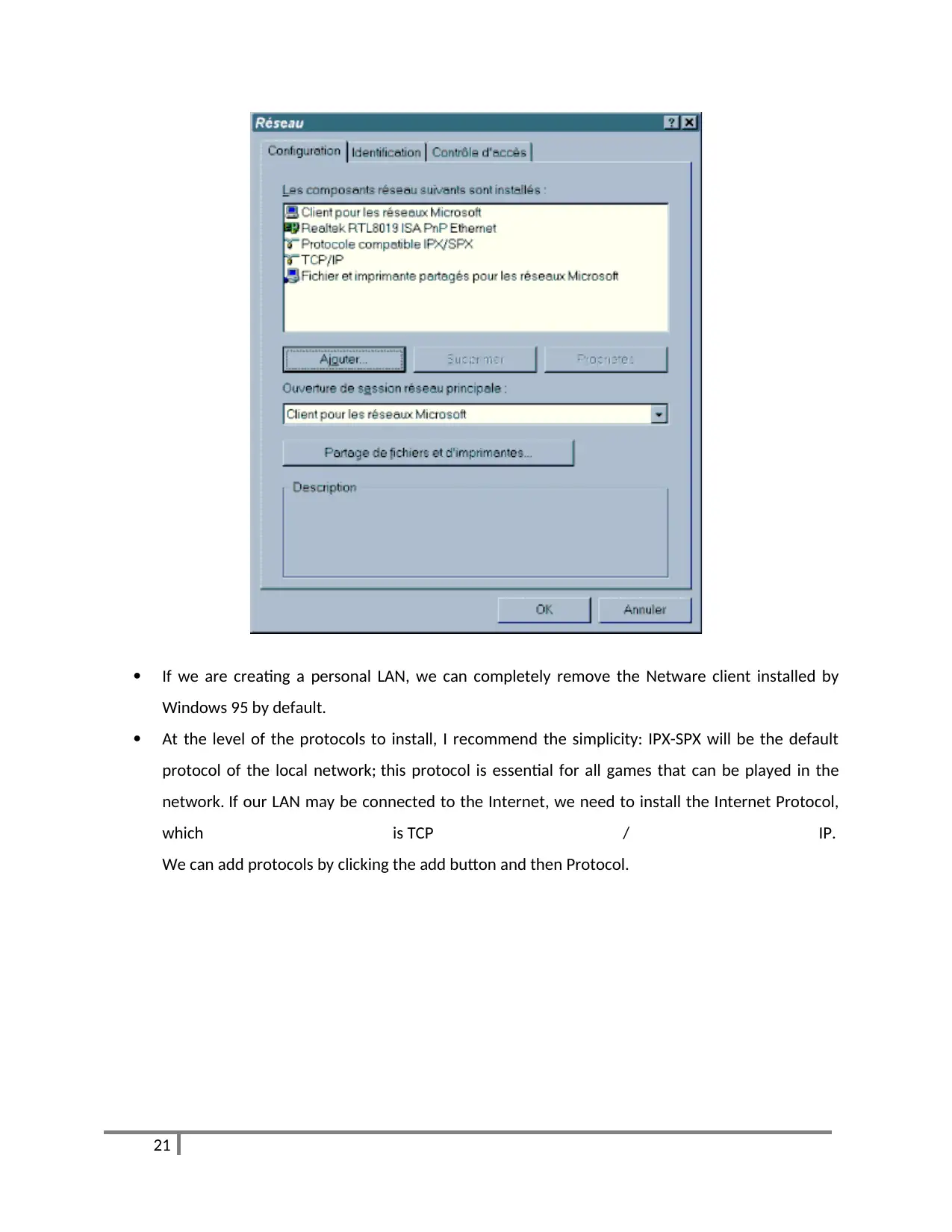
If we are creating a personal LAN, we can completely remove the Netware client installed by
Windows 95 by default.
At the level of the protocols to install, I recommend the simplicity: IPX-SPX will be the default
protocol of the local network; this protocol is essential for all games that can be played in the
network. If our LAN may be connected to the Internet, we need to install the Internet Protocol,
which is TCP / IP.
We can add protocols by clicking the add button and then Protocol.
21
Windows 95 by default.
At the level of the protocols to install, I recommend the simplicity: IPX-SPX will be the default
protocol of the local network; this protocol is essential for all games that can be played in the
network. If our LAN may be connected to the Internet, we need to install the Internet Protocol,
which is TCP / IP.
We can add protocols by clicking the add button and then Protocol.
21
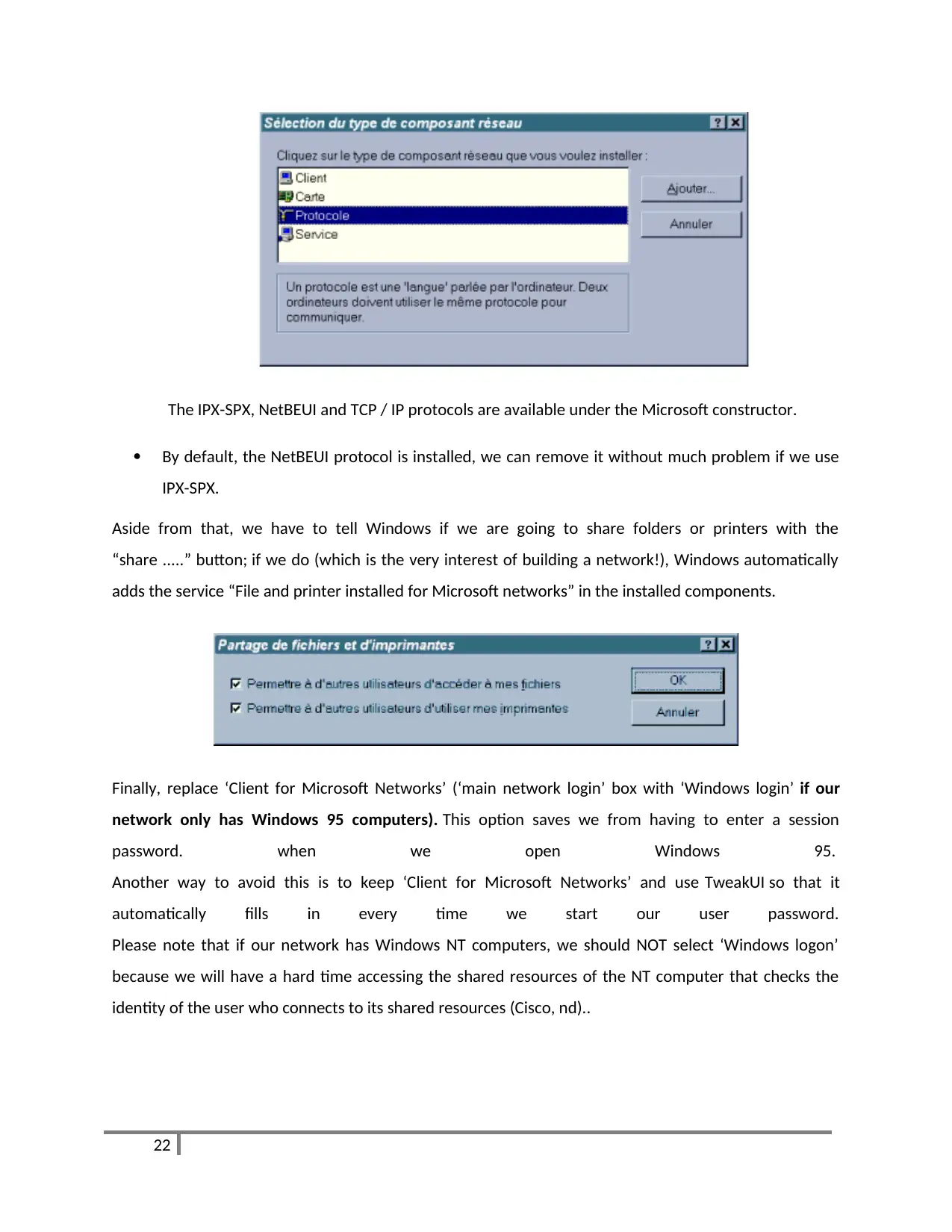
The IPX-SPX, NetBEUI and TCP / IP protocols are available under the Microsoft constructor.
By default, the NetBEUI protocol is installed, we can remove it without much problem if we use
IPX-SPX.
Aside from that, we have to tell Windows if we are going to share folders or printers with the
“share .....” button; if we do (which is the very interest of building a network!), Windows automatically
adds the service “File and printer installed for Microsoft networks” in the installed components.
Finally, replace ‘Client for Microsoft Networks’ (‘main network login’ box with ‘Windows login’ if our
network only has Windows 95 computers). This option saves we from having to enter a session
password. when we open Windows 95.
Another way to avoid this is to keep ‘Client for Microsoft Networks’ and use TweakUI so that it
automatically fills in every time we start our user password.
Please note that if our network has Windows NT computers, we should NOT select ‘Windows logon’
because we will have a hard time accessing the shared resources of the NT computer that checks the
identity of the user who connects to its shared resources (Cisco, nd)..
22
By default, the NetBEUI protocol is installed, we can remove it without much problem if we use
IPX-SPX.
Aside from that, we have to tell Windows if we are going to share folders or printers with the
“share .....” button; if we do (which is the very interest of building a network!), Windows automatically
adds the service “File and printer installed for Microsoft networks” in the installed components.
Finally, replace ‘Client for Microsoft Networks’ (‘main network login’ box with ‘Windows login’ if our
network only has Windows 95 computers). This option saves we from having to enter a session
password. when we open Windows 95.
Another way to avoid this is to keep ‘Client for Microsoft Networks’ and use TweakUI so that it
automatically fills in every time we start our user password.
Please note that if our network has Windows NT computers, we should NOT select ‘Windows logon’
because we will have a hard time accessing the shared resources of the NT computer that checks the
identity of the user who connects to its shared resources (Cisco, nd)..
22
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
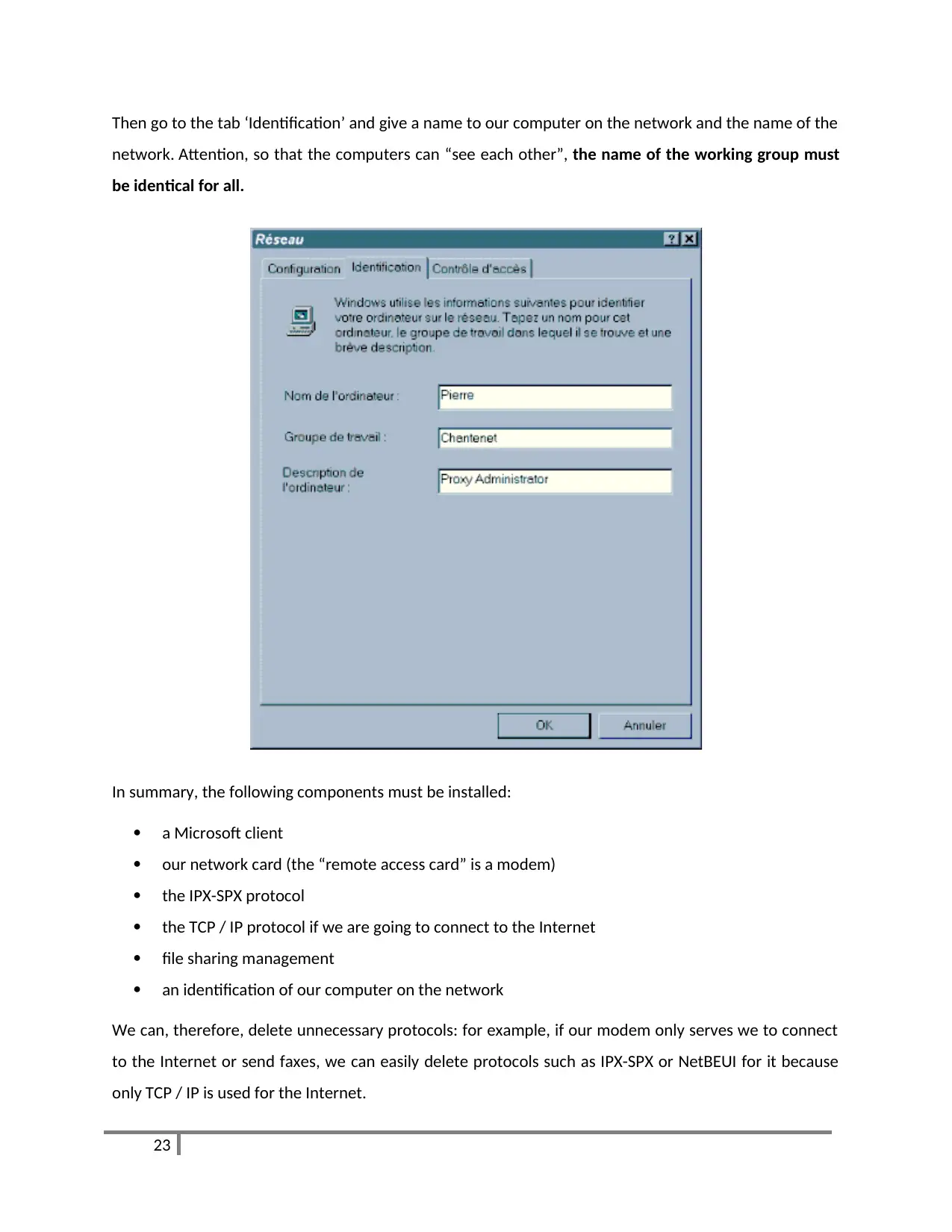
Then go to the tab ‘Identification’ and give a name to our computer on the network and the name of the
network. Attention, so that the computers can “see each other”, the name of the working group must
be identical for all.
In summary, the following components must be installed:
a Microsoft client
our network card (the “remote access card” is a modem)
the IPX-SPX protocol
the TCP / IP protocol if we are going to connect to the Internet
file sharing management
an identification of our computer on the network
We can, therefore, delete unnecessary protocols: for example, if our modem only serves we to connect
to the Internet or send faxes, we can easily delete protocols such as IPX-SPX or NetBEUI for it because
only TCP / IP is used for the Internet.
23
network. Attention, so that the computers can “see each other”, the name of the working group must
be identical for all.
In summary, the following components must be installed:
a Microsoft client
our network card (the “remote access card” is a modem)
the IPX-SPX protocol
the TCP / IP protocol if we are going to connect to the Internet
file sharing management
an identification of our computer on the network
We can, therefore, delete unnecessary protocols: for example, if our modem only serves we to connect
to the Internet or send faxes, we can easily delete protocols such as IPX-SPX or NetBEUI for it because
only TCP / IP is used for the Internet.
23
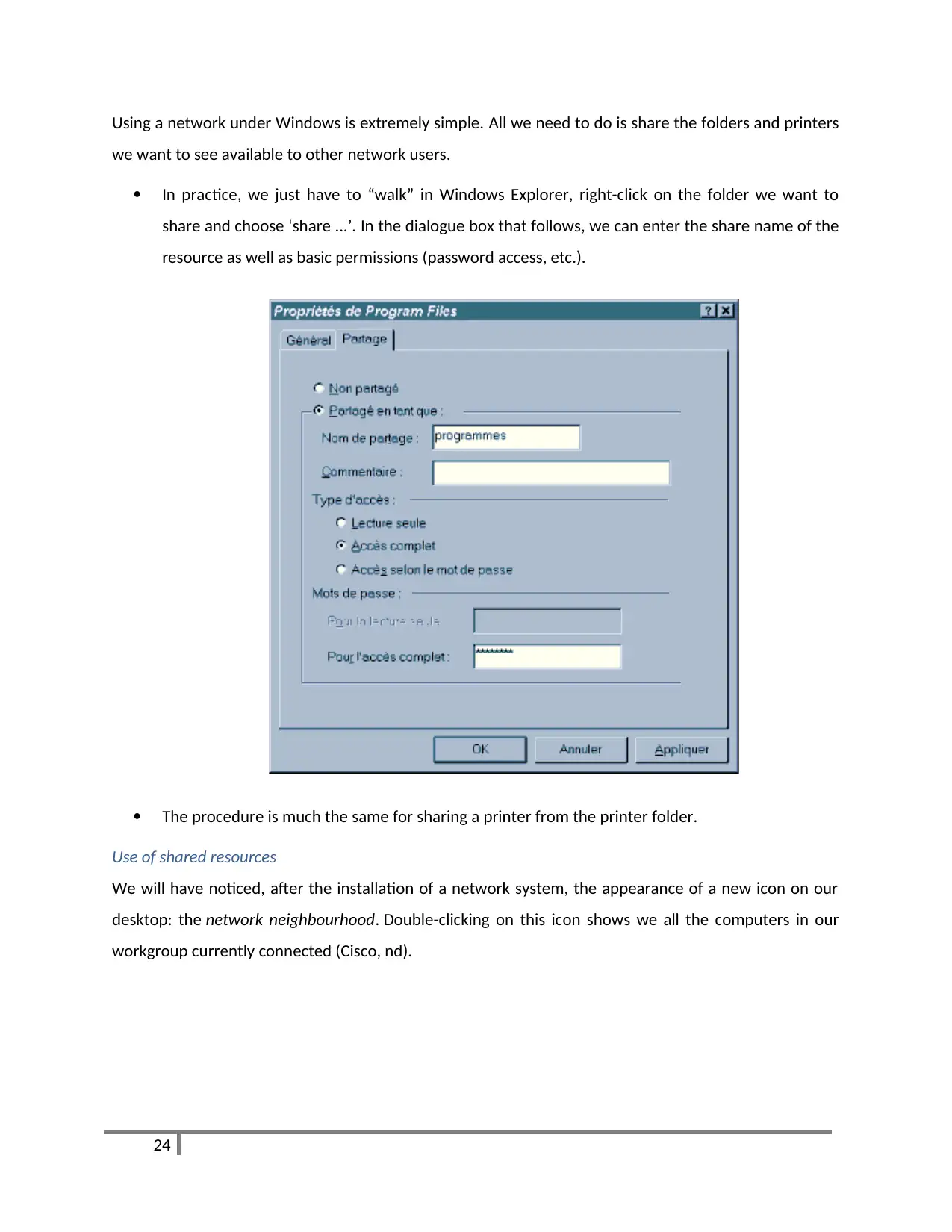
Using a network under Windows is extremely simple. All we need to do is share the folders and printers
we want to see available to other network users.
In practice, we just have to “walk” in Windows Explorer, right-click on the folder we want to
share and choose ‘share ...’. In the dialogue box that follows, we can enter the share name of the
resource as well as basic permissions (password access, etc.).
The procedure is much the same for sharing a printer from the printer folder.
Use of shared resources
We will have noticed, after the installation of a network system, the appearance of a new icon on our
desktop: the network neighbourhood. Double-clicking on this icon shows we all the computers in our
workgroup currently connected (Cisco, nd).
24
we want to see available to other network users.
In practice, we just have to “walk” in Windows Explorer, right-click on the folder we want to
share and choose ‘share ...’. In the dialogue box that follows, we can enter the share name of the
resource as well as basic permissions (password access, etc.).
The procedure is much the same for sharing a printer from the printer folder.
Use of shared resources
We will have noticed, after the installation of a network system, the appearance of a new icon on our
desktop: the network neighbourhood. Double-clicking on this icon shows we all the computers in our
workgroup currently connected (Cisco, nd).
24
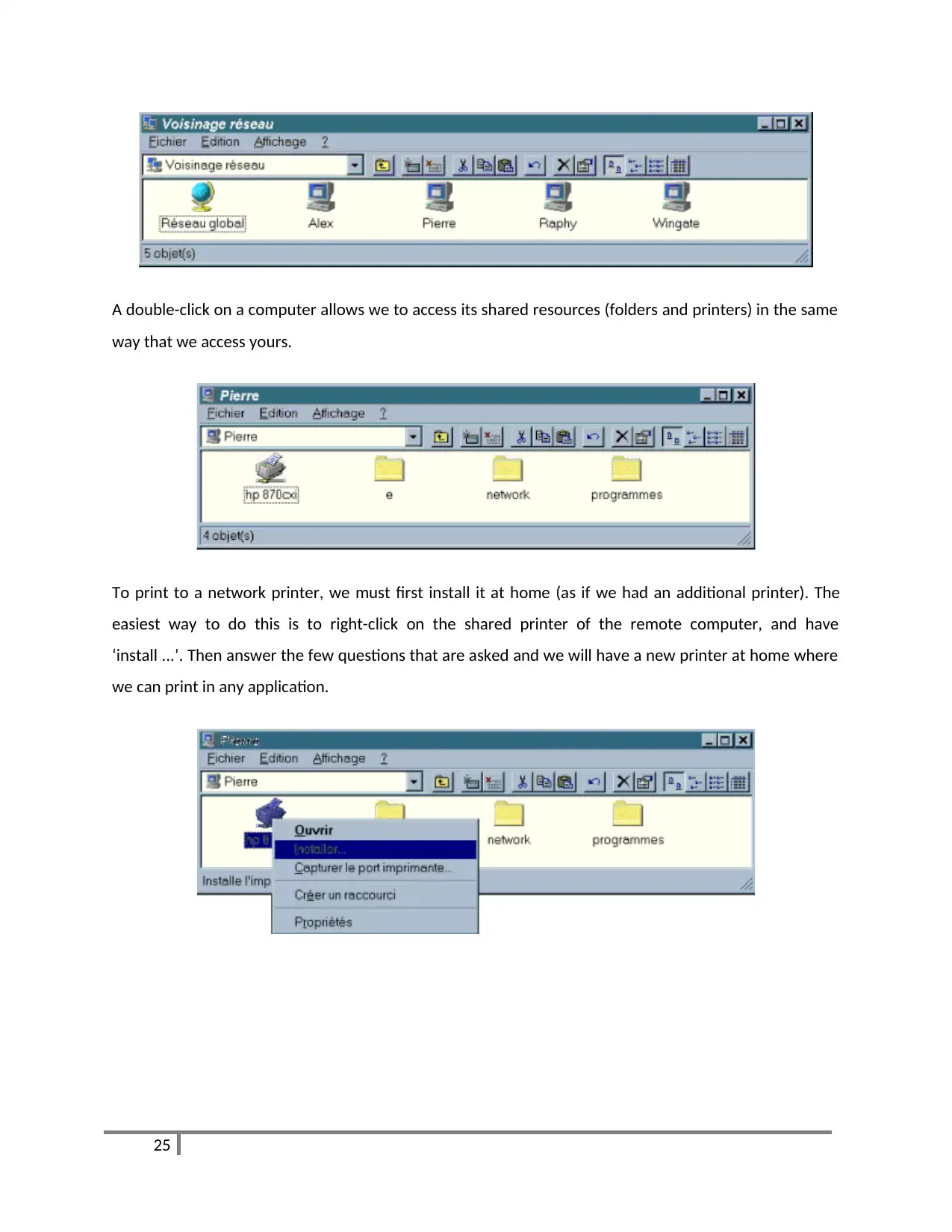
A double-click on a computer allows we to access its shared resources (folders and printers) in the same
way that we access yours.
To print to a network printer, we must first install it at home (as if we had an additional printer). The
easiest way to do this is to right-click on the shared printer of the remote computer, and have
‘install ...’. Then answer the few questions that are asked and we will have a new printer at home where
we can print in any application.
25
way that we access yours.
To print to a network printer, we must first install it at home (as if we had an additional printer). The
easiest way to do this is to right-click on the shared printer of the remote computer, and have
‘install ...’. Then answer the few questions that are asked and we will have a new printer at home where
we can print in any application.
25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
A.C 3.3 critically review and test a LAN
So we decided to use the TCP / IP protocol for our local network. Remember that we MUST install this
protocol if we plan to connect our Local Area Network (LAN) to the Internet, but of course, nothing
prevents us from installing TCP / IP anyway; even without the Internet, this flexible protocol has many
interesting features for a network administrator.
If we have read the section I dedicate to TCP / IP, we understand that one of the basics of this software
is to assign a personal IP address (such as a phone number) to each computer on the network. A
problem arises: is there a limitation in the allocation of these numbers?
In fact, if our network is totally isolated from the rest of the world, we can put the numbers that we
like. An IP address is in the form and where a, b, c, d are numbers between 0 and 255 (for example
195.38.55.252). If we have read my section on the subject, we know however that in order to
communicate with each other, the computers must have the first 3 numbers of the identical IP
address; for example, 192.168.0.4 can communicate with 192.168.0.99, but not with 194.168.0.5.
On the other hand, if a computer on our network can “communicate further”, for example, if it is
equipped with a modem and can access the Internet, we have no choice but to use any which IP
addresses.
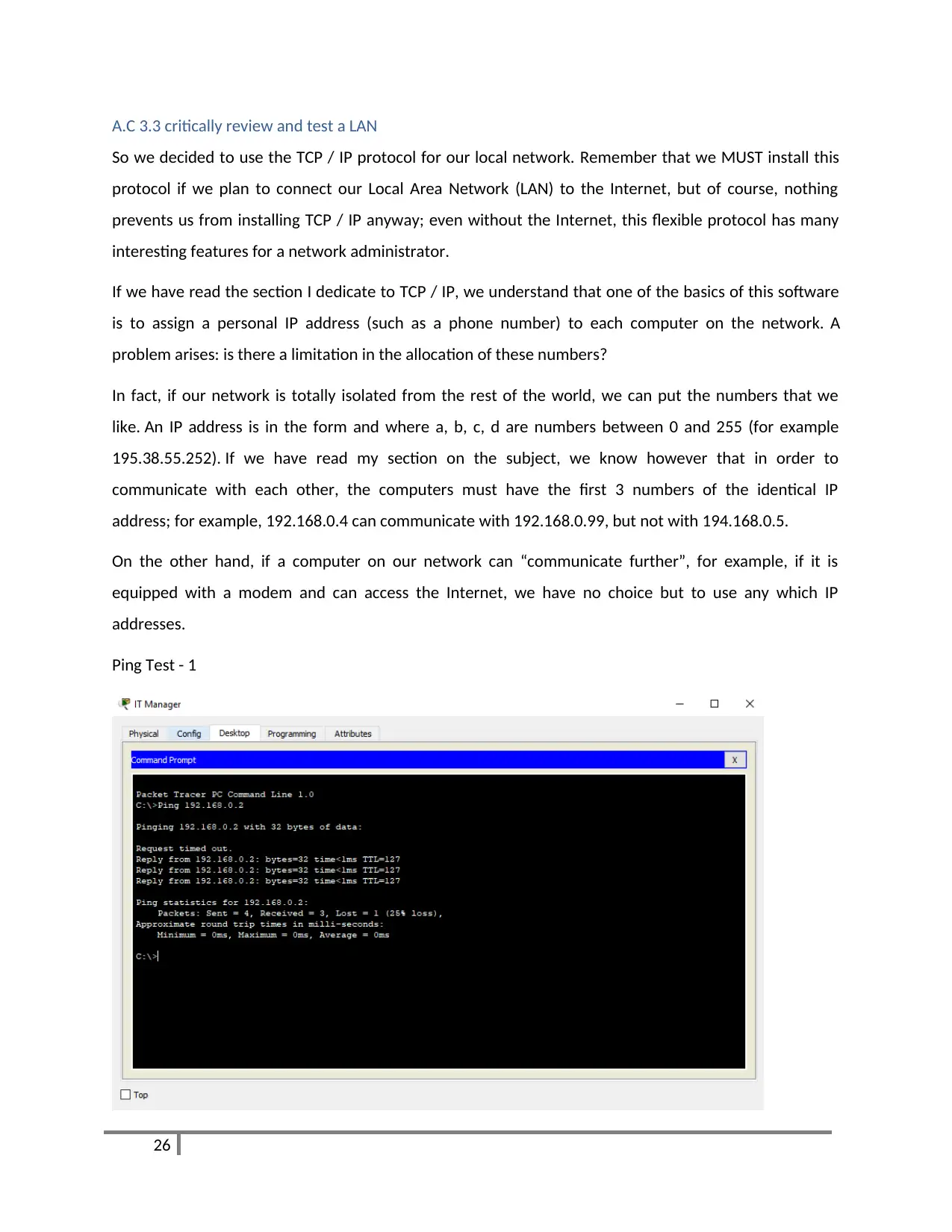
Ping Test - 1
26
So we decided to use the TCP / IP protocol for our local network. Remember that we MUST install this
protocol if we plan to connect our Local Area Network (LAN) to the Internet, but of course, nothing
prevents us from installing TCP / IP anyway; even without the Internet, this flexible protocol has many
interesting features for a network administrator.
If we have read the section I dedicate to TCP / IP, we understand that one of the basics of this software
is to assign a personal IP address (such as a phone number) to each computer on the network. A
problem arises: is there a limitation in the allocation of these numbers?
In fact, if our network is totally isolated from the rest of the world, we can put the numbers that we
like. An IP address is in the form and where a, b, c, d are numbers between 0 and 255 (for example
195.38.55.252). If we have read my section on the subject, we know however that in order to
communicate with each other, the computers must have the first 3 numbers of the identical IP
address; for example, 192.168.0.4 can communicate with 192.168.0.99, but not with 194.168.0.5.
On the other hand, if a computer on our network can “communicate further”, for example, if it is
equipped with a modem and can access the Internet, we have no choice but to use any which IP
addresses.
Ping Test - 1
26
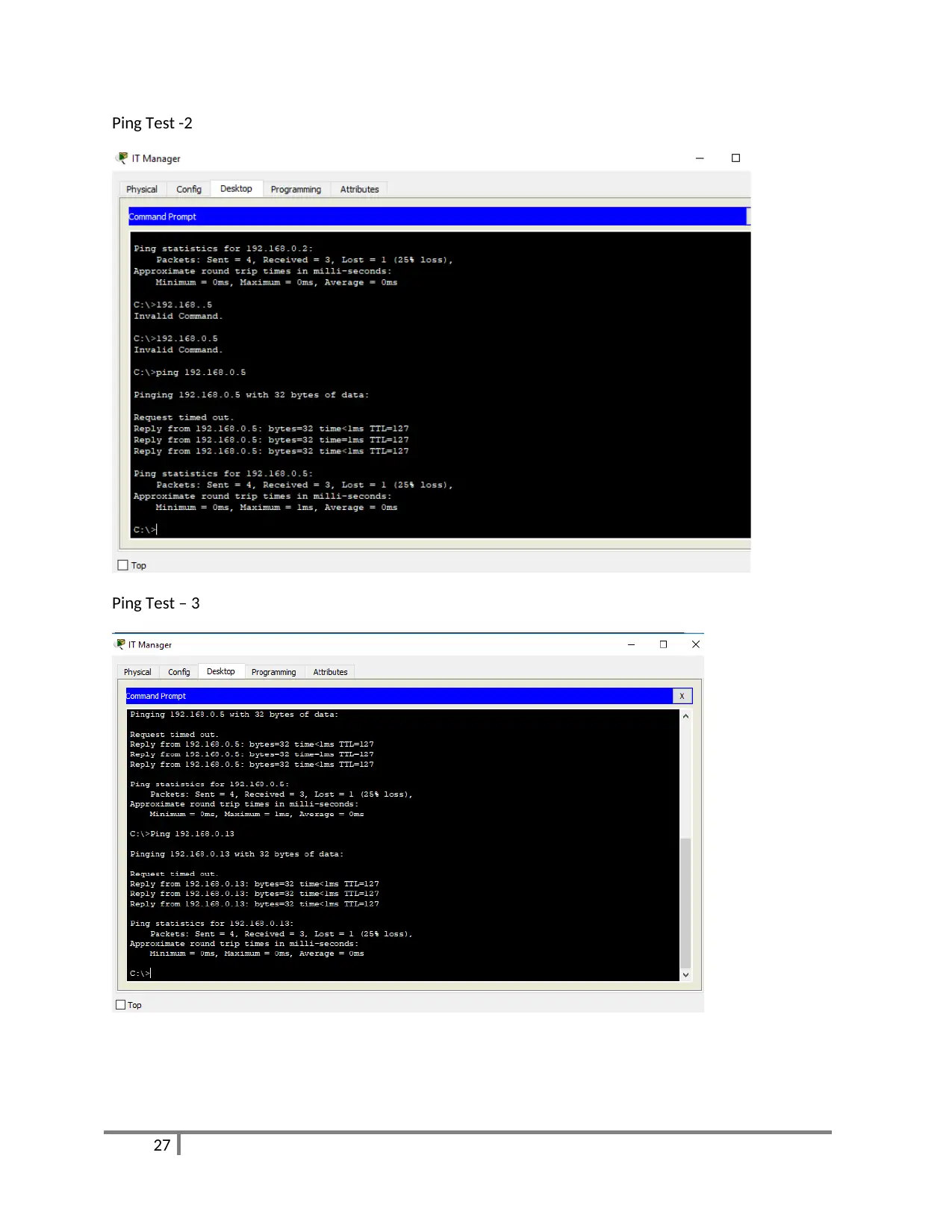
Ping Test -2
Ping Test – 3
27
Ping Test – 3
27
Web Server
28
28
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Task 4
A.C 4.1 critically discuss how this LAN infrastructure will be monitored and managed
For the configuration of a simple LAN in TCP / IP, only three points interest us:
1. Assigning IP addresses : We strongly recommend that we use IP 192.168.0.1, 192.168.0.2,
192.168.0.3, etc.
2. the subnet mask: 255.255.255.0
3. a hostname naming system
Let’s take these points one by one and configure our network (I assume that our computers are properly
connected to each other and the essential network components are installed).
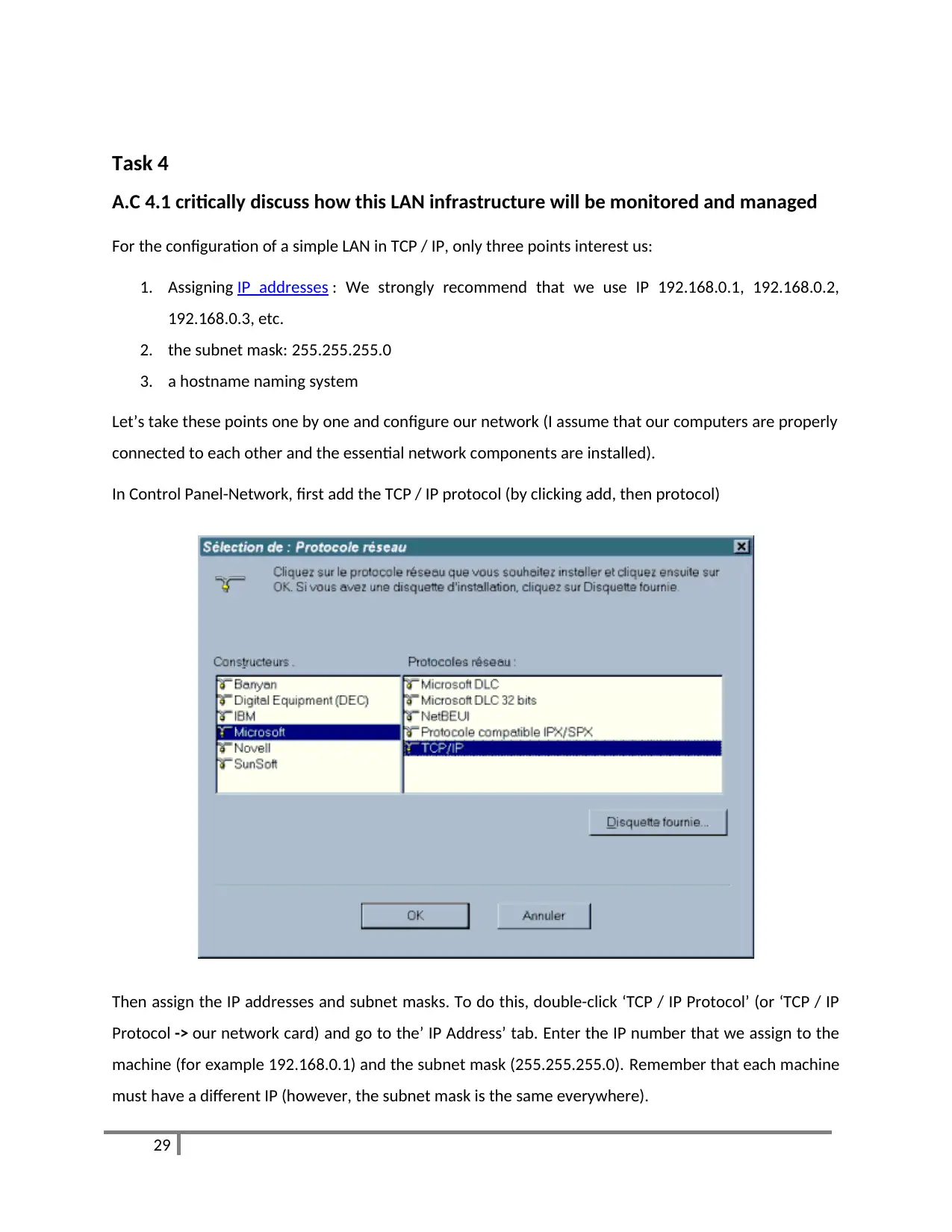
In Control Panel-Network, first add the TCP / IP protocol (by clicking add, then protocol)
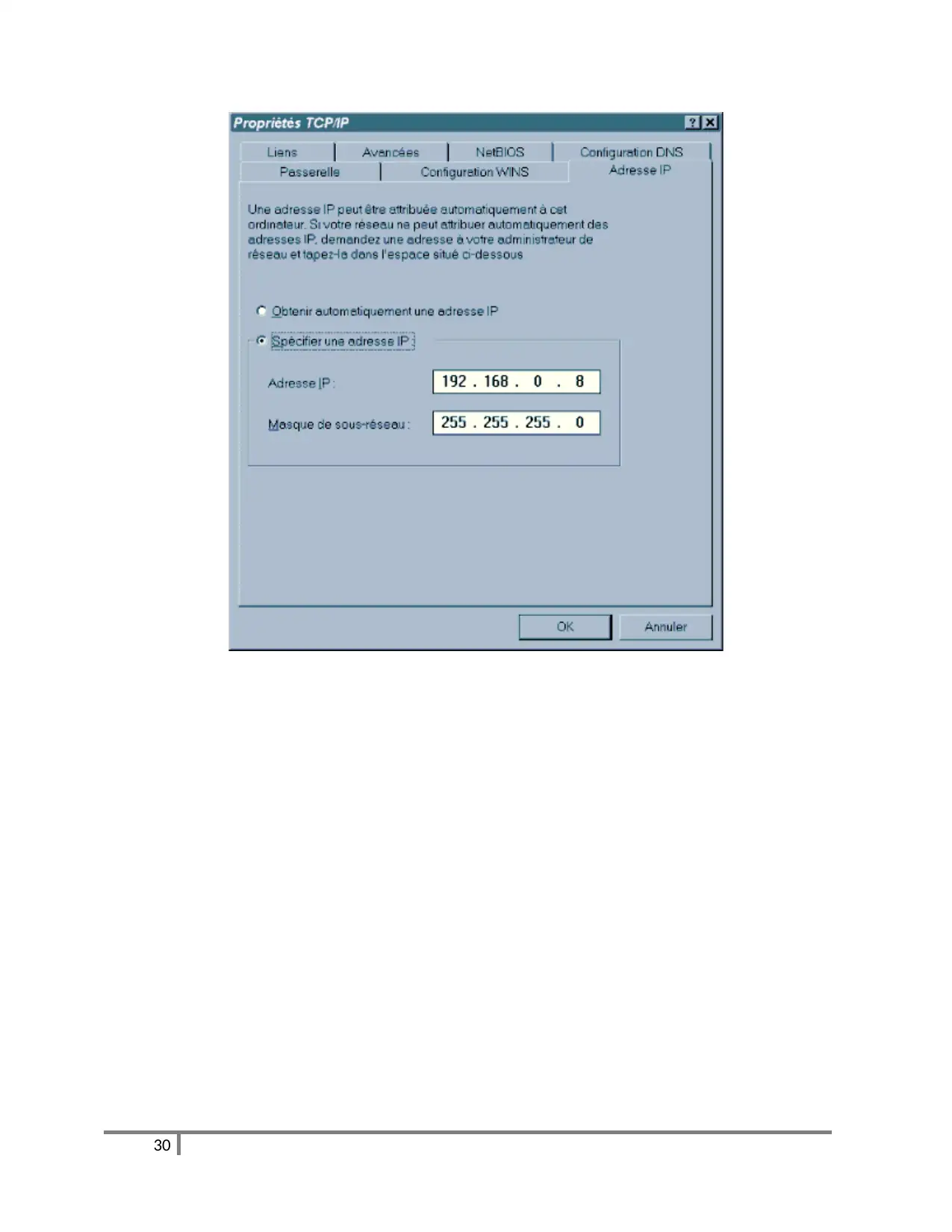
Then assign the IP addresses and subnet masks. To do this, double-click ‘TCP / IP Protocol’ (or ‘TCP / IP
Protocol -> our network card) and go to the’ IP Address’ tab. Enter the IP number that we assign to the
machine (for example 192.168.0.1) and the subnet mask (255.255.255.0). Remember that each machine
must have a different IP (however, the subnet mask is the same everywhere).
29
A.C 4.1 critically discuss how this LAN infrastructure will be monitored and managed
For the configuration of a simple LAN in TCP / IP, only three points interest us:
1. Assigning IP addresses : We strongly recommend that we use IP 192.168.0.1, 192.168.0.2,
192.168.0.3, etc.
2. the subnet mask: 255.255.255.0
3. a hostname naming system
Let’s take these points one by one and configure our network (I assume that our computers are properly
connected to each other and the essential network components are installed).
In Control Panel-Network, first add the TCP / IP protocol (by clicking add, then protocol)
Then assign the IP addresses and subnet masks. To do this, double-click ‘TCP / IP Protocol’ (or ‘TCP / IP
Protocol -> our network card) and go to the’ IP Address’ tab. Enter the IP number that we assign to the
machine (for example 192.168.0.1) and the subnet mask (255.255.255.0). Remember that each machine
must have a different IP (however, the subnet mask is the same everywhere).
29
30
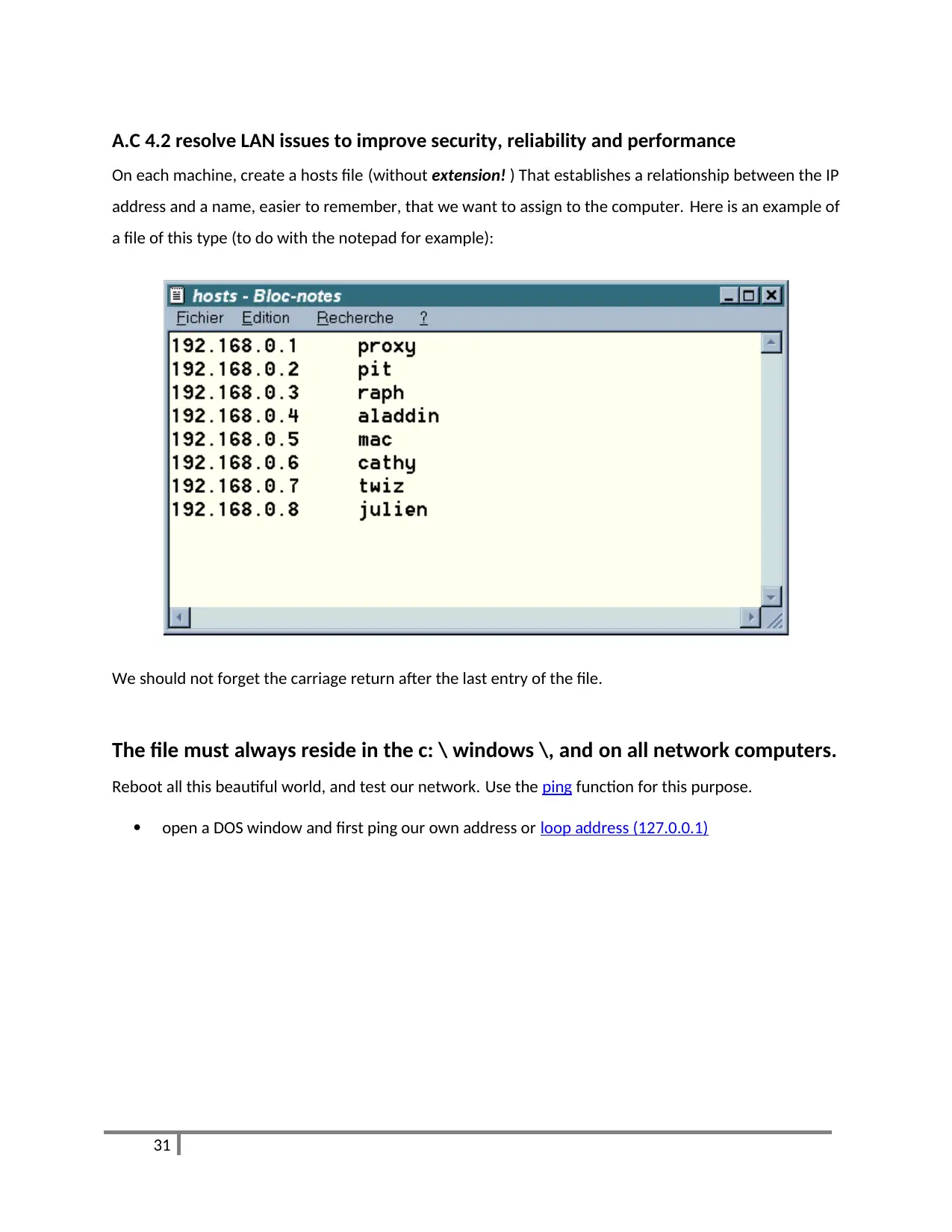
A.C 4.2 resolve LAN issues to improve security, reliability and performance
On each machine, create a hosts file (without extension! ) That establishes a relationship between the IP
address and a name, easier to remember, that we want to assign to the computer. Here is an example of
a file of this type (to do with the notepad for example):
We should not forget the carriage return after the last entry of the file.
The file must always reside in the c: \ windows \, and on all network computers.
Reboot all this beautiful world, and test our network. Use the ping function for this purpose.
open a DOS window and first ping our own address or loop address (127.0.0.1)
31
On each machine, create a hosts file (without extension! ) That establishes a relationship between the IP
address and a name, easier to remember, that we want to assign to the computer. Here is an example of
a file of this type (to do with the notepad for example):
We should not forget the carriage return after the last entry of the file.
The file must always reside in the c: \ windows \, and on all network computers.
Reboot all this beautiful world, and test our network. Use the ping function for this purpose.
open a DOS window and first ping our own address or loop address (127.0.0.1)
31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
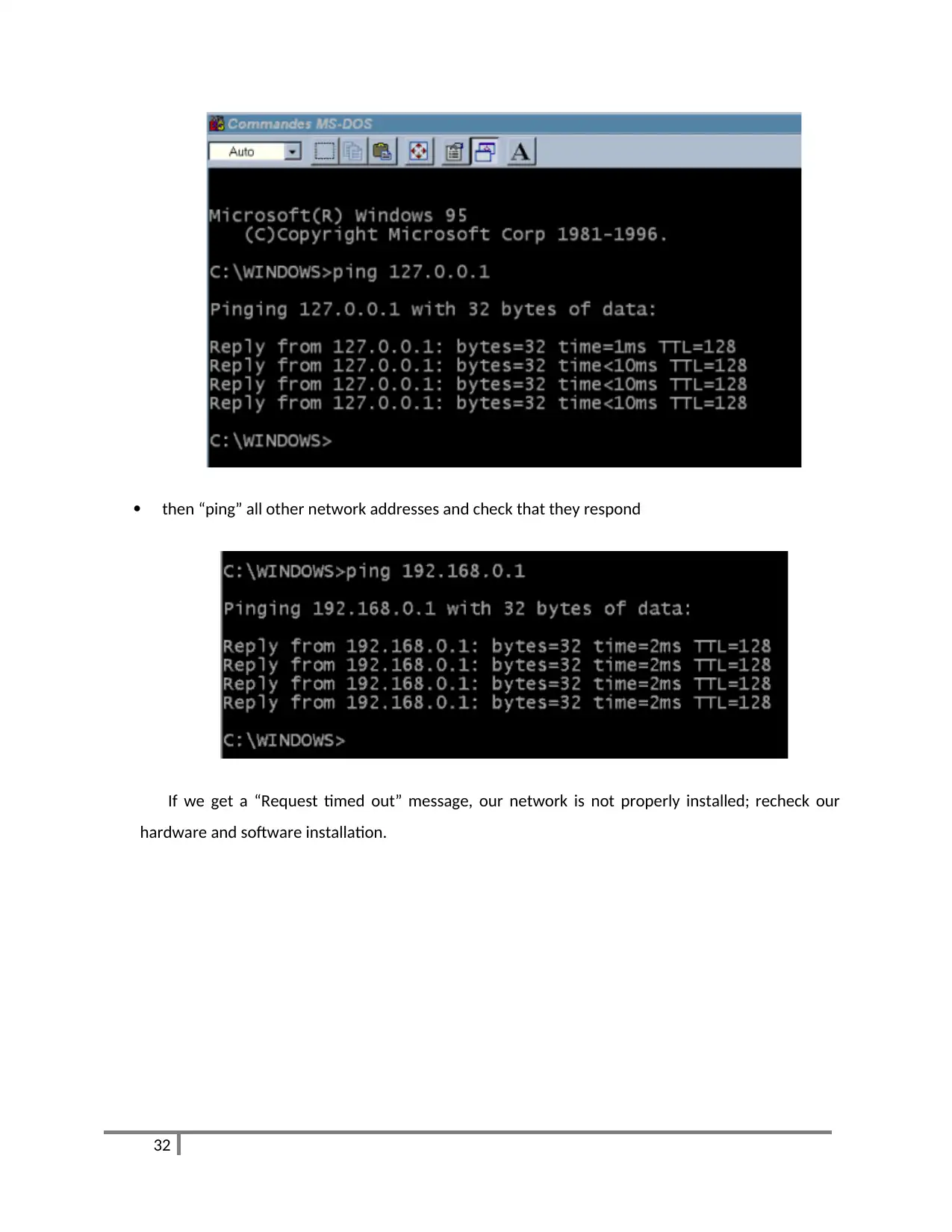
then “ping” all other network addresses and check that they respond
If we get a “Request timed out” message, our network is not properly installed; recheck our
hardware and software installation.
32
If we get a “Request timed out” message, our network is not properly installed; recheck our
hardware and software installation.
32

A.C 4.3 critically evaluate the performance of a LAN
We test our host's file: instead of pinging the IP number, ping the name we assigned to our
machines; the result must be the same. Incidentally, we will see that the computer indicates the
corresponding IP address.
If we get a “Bad IP address ...” message, our host's file is not correct. We can check that it does not have
an extension and it is well placed in the directory c: \ windows \. Finally, we will check whether it is
named correctly (hosts and not host).
If everything works, our network is properly installed and is ready to connect to the Internet. So we can
increase the maximum number of connections or open sessions or timeout settings as desired to
improve the performance.
33
We test our host's file: instead of pinging the IP number, ping the name we assigned to our
machines; the result must be the same. Incidentally, we will see that the computer indicates the
corresponding IP address.
If we get a “Bad IP address ...” message, our host's file is not correct. We can check that it does not have
an extension and it is well placed in the directory c: \ windows \. Finally, we will check whether it is
named correctly (hosts and not host).
If everything works, our network is properly installed and is ready to connect to the Internet. So we can
increase the maximum number of connections or open sessions or timeout settings as desired to
improve the performance.
33

References
Cisco(nd). Cisco Active Network Abstraction 3.7 Reference Guide. Chapter 10. Available from
http://www.cisco.com/c/en/us/td/docs/net_mgmt/active_network_abstraction/3-
7/reference/guide/ANARefGuide37.pdf
Cisco, f(2015). fSpanning fTree fPortFast fBPDU fGuard fEnhancement. f[online] fAvailable fat:
fhttp://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10586-65.html
f[Accessed f30 fDec. f2015].
Doyle, J. (1997).Routing TCP/IP (Volume I). Cisco Systems Press. Chapter 5-9. Available from
http://www.net130.com/tutorial/cisco-pdf/routingtcpipv1.pd
Forouzan, B. A. (2009) TCP/IP Protocol Suite, McGraw-Hill Education Press. P. 269. ISBN 0-073-37604-3.
Hubert, P. (2001). Convergence Behavior of RIP and OSPF Network Protocols. Available from . Internet:
http://www2.ensc.sfu.ca/~ljilja/cnl/pdf/hubert.pdf
Scott M. B. (1997). Managing IP Networks with Cisco Routers, O‟REILLY Press. Chapter 5. ISBN: 1-56592-
320-0. Available from http://phucchau.tran.free.fr/book/O%27Reilly%20-%20Managing%20Ip
%20Networks%20With%20Cisco%20Routers.pdf
Thorenoor, S. G. (2010) Dynamic Routing Protocol Implementation Decision between EIGRP, OSPF and
RIP Based on Technical Background Using OPNET Modeler. P. 191-195. ISBN: 978-1-4244-6962-8.
Available from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=5474509
Wu, B. (2013). Simulation Based Performance Analysis on RIPv2, EIGRP and OSPF Using OPNET”.
Available from http://digitalcommons.uncfsu.edu/cgi/viewcontent.cgi?
article=1011&context=macsc_wp
Appendix:
34
Cisco(nd). Cisco Active Network Abstraction 3.7 Reference Guide. Chapter 10. Available from
http://www.cisco.com/c/en/us/td/docs/net_mgmt/active_network_abstraction/3-
7/reference/guide/ANARefGuide37.pdf
Cisco, f(2015). fSpanning fTree fPortFast fBPDU fGuard fEnhancement. f[online] fAvailable fat:
fhttp://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10586-65.html
f[Accessed f30 fDec. f2015].
Doyle, J. (1997).Routing TCP/IP (Volume I). Cisco Systems Press. Chapter 5-9. Available from
http://www.net130.com/tutorial/cisco-pdf/routingtcpipv1.pd
Forouzan, B. A. (2009) TCP/IP Protocol Suite, McGraw-Hill Education Press. P. 269. ISBN 0-073-37604-3.
Hubert, P. (2001). Convergence Behavior of RIP and OSPF Network Protocols. Available from . Internet:
http://www2.ensc.sfu.ca/~ljilja/cnl/pdf/hubert.pdf
Scott M. B. (1997). Managing IP Networks with Cisco Routers, O‟REILLY Press. Chapter 5. ISBN: 1-56592-
320-0. Available from http://phucchau.tran.free.fr/book/O%27Reilly%20-%20Managing%20Ip
%20Networks%20With%20Cisco%20Routers.pdf
Thorenoor, S. G. (2010) Dynamic Routing Protocol Implementation Decision between EIGRP, OSPF and
RIP Based on Technical Background Using OPNET Modeler. P. 191-195. ISBN: 978-1-4244-6962-8.
Available from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=5474509
Wu, B. (2013). Simulation Based Performance Analysis on RIPv2, EIGRP and OSPF Using OPNET”.
Available from http://digitalcommons.uncfsu.edu/cgi/viewcontent.cgi?
article=1011&context=macsc_wp
Appendix:
34
1 out of 34
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





