Local Area Network (LAN) to support Windows Server and Client Environment
VerifiedAdded on 2022/11/19
|12
|2470
|104
AI Summary
This report discusses the configuration of Local Area Network (LAN) to support Windows Server and Client Environment. It covers the requirement analysis, configuring process description, and conclusion. The report is prepared for Thinktank Company that needs to connect its headquarter in Sydney with the new branch office in Melbourne. The report suggests the use of VM Ware for configuring the server and Windows Server 2012 R2 as the operating system of the server. The report also suggests the use of DHCP configuration for automatically assigning IP address to the hosts connected in the network. The report recommends the use of a centralized authentication system for sharing data and information between the headquarter and the branches securely. The report also suggests the use of file server configuration for managing the access of files and information between each of the departments such as finance sales and managers. The report is useful for students studying computer networking and system administration.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Local Area Network (LAN) to support Windows Server and Client
Environment
Name of the Student
Name of the University
Author’s Note
Environment
Name of the Student
Name of the University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Introduction
For the preparation of the report the first scenario of “Local area network (LAN) to support
windows server client environment” is selected. The requirement of the scenario is evaluated and
the number of server required and their roles or services needed to be configured in order to meet
the specific requirement is evaluated. VM Ware is used for configuring the server and Windows
Server 2012 R2 is used as the operating system of the server. The network is prepared for Thinktank
Company that have a requirement of connecting the companies headquarter in Sydney with the new
branch office in Melbourne. A centralized authentication system is needed to be designed and such
that the data and information can be shared between the head quarter and the branches securely.
The access of the files and information between each of the departments such as finance sales and
managers are needed to be managed for maintaining privacy and security of the designed network
framework.
Requirement analysis
The network solution is designed for Thinktank such that the data generated from the daily activity
and old information are stored in a centralized location for providing its access from different
branches of the organization. Currently there are confusion between the staffs for maintaining the
records since all the data are stored centrally in two machines. Currently the company depends on
manual IP address that causes use of same IP in two of the computer and disruption in the network.
Thus the company needs to switch to DHCP configuration for automatically assigning IP address to
the hosts connected in the network. The problem of centrally access the files and information is also
needed to be resolved by configuring the server with IIS service and mapping an URL with the
server’s IP address. A space is needed to be provided to the user for storing their files securely such
that other users in the network cannot have access to the files. Changes are needed to be made in
the current network model and the new service are needed to be configured and it should also be
noted that the fault tolerance can be improved and the network disruption is eliminated. A security
policy configuration is needed to be developed and best industry practice is needed to apply for the
development of the network and presenting its prototype with virtual machines.
Configuring process description
For the configuration of the typical network scenario a virtual windows server is used and
the service that are needed to be installed in the server is identified. The number of departments
For the preparation of the report the first scenario of “Local area network (LAN) to support
windows server client environment” is selected. The requirement of the scenario is evaluated and
the number of server required and their roles or services needed to be configured in order to meet
the specific requirement is evaluated. VM Ware is used for configuring the server and Windows
Server 2012 R2 is used as the operating system of the server. The network is prepared for Thinktank
Company that have a requirement of connecting the companies headquarter in Sydney with the new
branch office in Melbourne. A centralized authentication system is needed to be designed and such
that the data and information can be shared between the head quarter and the branches securely.
The access of the files and information between each of the departments such as finance sales and
managers are needed to be managed for maintaining privacy and security of the designed network
framework.
Requirement analysis
The network solution is designed for Thinktank such that the data generated from the daily activity
and old information are stored in a centralized location for providing its access from different
branches of the organization. Currently there are confusion between the staffs for maintaining the
records since all the data are stored centrally in two machines. Currently the company depends on
manual IP address that causes use of same IP in two of the computer and disruption in the network.
Thus the company needs to switch to DHCP configuration for automatically assigning IP address to
the hosts connected in the network. The problem of centrally access the files and information is also
needed to be resolved by configuring the server with IIS service and mapping an URL with the
server’s IP address. A space is needed to be provided to the user for storing their files securely such
that other users in the network cannot have access to the files. Changes are needed to be made in
the current network model and the new service are needed to be configured and it should also be
noted that the fault tolerance can be improved and the network disruption is eliminated. A security
policy configuration is needed to be developed and best industry practice is needed to apply for the
development of the network and presenting its prototype with virtual machines.
Configuring process description
For the configuration of the typical network scenario a virtual windows server is used and
the service that are needed to be installed in the server is identified. The number of departments

and their service needs are also needed to be documented for such that the network is configured
and according to the department and the server is connected with the organizational network to
meet the needs of the users. The current problems in the network is identified and the server is
configures with the roles and services for the mitigation of the problem and increasing the efficiency
of the current business process.
A file server is needed to be configured and a groups of user is needed to be created for the
management of permission and allowing access and restriction of the users for the files. Each of the
users are needed to be provided space to store their files and thus the file server configuration is
used. The server is also configured with IIS service for hosting an internal website service for the
organization and enabling communication between the users of the each of the department and
branches. The server is also configured with print server and allowing the user to print their files and
documents using the remote printer. The network printer is shared with each of the user for
enabling them access the printer. The DHCP service is enabled for eliminating the problem of manual
IP configuration and automatically assigning IP address to the device connected in the network.
Centralised User-Authentication –
For management of authentication the virtual windows server is configured with active directory
such that the users can be managed centrally from different location in the network. Domain are
configured such that it can be configured with other services and a strong password is used for the
configuration of domain name. The password protection helps in management of the resources by
the server manager and have full control on the security of network framework.
Print servers for users –
The print service is enabled such that the network printer in the organization can be shared with
each of the department and all the user have access of the printer. The use of printing service
eliminated the needs of printers for each of the department and a single printer can be used for
managing the printing jobs.
DHCP Configuration –
The current problem of manually assigning IP address and causing overlapping of IP address is
resolved with the application of DHCP configuration and enabling DHCP scope in the server. A range
of IP address is used for each of the group such that they gets the IP address automatically when
connected with the network. For increasing the security the security groups are configured such that
illegal access of the network is prevented and the unknown users are restricted to connect with the
network.
and according to the department and the server is connected with the organizational network to
meet the needs of the users. The current problems in the network is identified and the server is
configures with the roles and services for the mitigation of the problem and increasing the efficiency
of the current business process.
A file server is needed to be configured and a groups of user is needed to be created for the
management of permission and allowing access and restriction of the users for the files. Each of the
users are needed to be provided space to store their files and thus the file server configuration is
used. The server is also configured with IIS service for hosting an internal website service for the
organization and enabling communication between the users of the each of the department and
branches. The server is also configured with print server and allowing the user to print their files and
documents using the remote printer. The network printer is shared with each of the user for
enabling them access the printer. The DHCP service is enabled for eliminating the problem of manual
IP configuration and automatically assigning IP address to the device connected in the network.
Centralised User-Authentication –
For management of authentication the virtual windows server is configured with active directory
such that the users can be managed centrally from different location in the network. Domain are
configured such that it can be configured with other services and a strong password is used for the
configuration of domain name. The password protection helps in management of the resources by
the server manager and have full control on the security of network framework.
Print servers for users –
The print service is enabled such that the network printer in the organization can be shared with
each of the department and all the user have access of the printer. The use of printing service
eliminated the needs of printers for each of the department and a single printer can be used for
managing the printing jobs.
DHCP Configuration –
The current problem of manually assigning IP address and causing overlapping of IP address is
resolved with the application of DHCP configuration and enabling DHCP scope in the server. A range
of IP address is used for each of the group such that they gets the IP address automatically when
connected with the network. For increasing the security the security groups are configured such that
illegal access of the network is prevented and the unknown users are restricted to connect with the
network.

Hosting Own Website –
For hosting the website the IIS service is enabled from the server manager and it is configured
hosting the internal website of the organization. There are different services such as FTP and WWW
that are needed to be enabled for hosting the website of the organisation. For hosting the internal
website Windows server is the best option and in future ASP.Net can be used for developing the
website and adding features to it and host the website.
Description of OUs, Groups, Users and Access Levels –
For the management of the information system it is essential to use the client server architecture
such that the response of the network increases and the network admin a centralized control of the
framework. The flow of the information to different location of the network is needed to be
managed and the services are needed to be configured according to the needs of the user. The
network is needed to be divided according to the department and they are needed to be grouped
for management of authentication and maintaining access to the resources of the organization from
different remote location. The server is needed to be configured as RADIUS server and the AAA
services are needed to be enabled for establishing a secure connection with the branch. Each of the
department is needed to be assigned with a separate VLAN for DHCP scope is needed to be
configured with a different range of IP address for each of the VLAN. The file server configuration is
needed to be used for the management of security policy and management of access of files for
each of the departments in the organization.
File Server configuration –
The file server configuration is made on the server by enabling File server resource manager from
add roles and features wizard. Necessary partitions are made on the hard drive of the server for
sharing the storage space with each of the department of Thinktank. Quota management is enabled
and a separate folder is created for each of the department for assigning permission for the folders
and enabling sharing of information between the users of the department.
For hosting the website the IIS service is enabled from the server manager and it is configured
hosting the internal website of the organization. There are different services such as FTP and WWW
that are needed to be enabled for hosting the website of the organisation. For hosting the internal
website Windows server is the best option and in future ASP.Net can be used for developing the
website and adding features to it and host the website.
Description of OUs, Groups, Users and Access Levels –
For the management of the information system it is essential to use the client server architecture
such that the response of the network increases and the network admin a centralized control of the
framework. The flow of the information to different location of the network is needed to be
managed and the services are needed to be configured according to the needs of the user. The
network is needed to be divided according to the department and they are needed to be grouped
for management of authentication and maintaining access to the resources of the organization from
different remote location. The server is needed to be configured as RADIUS server and the AAA
services are needed to be enabled for establishing a secure connection with the branch. Each of the
department is needed to be assigned with a separate VLAN for DHCP scope is needed to be
configured with a different range of IP address for each of the VLAN. The file server configuration is
needed to be used for the management of security policy and management of access of files for
each of the departments in the organization.
File Server configuration –
The file server configuration is made on the server by enabling File server resource manager from
add roles and features wizard. Necessary partitions are made on the hard drive of the server for
sharing the storage space with each of the department of Thinktank. Quota management is enabled
and a separate folder is created for each of the department for assigning permission for the folders
and enabling sharing of information between the users of the department.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Configuration Screenshots or commands
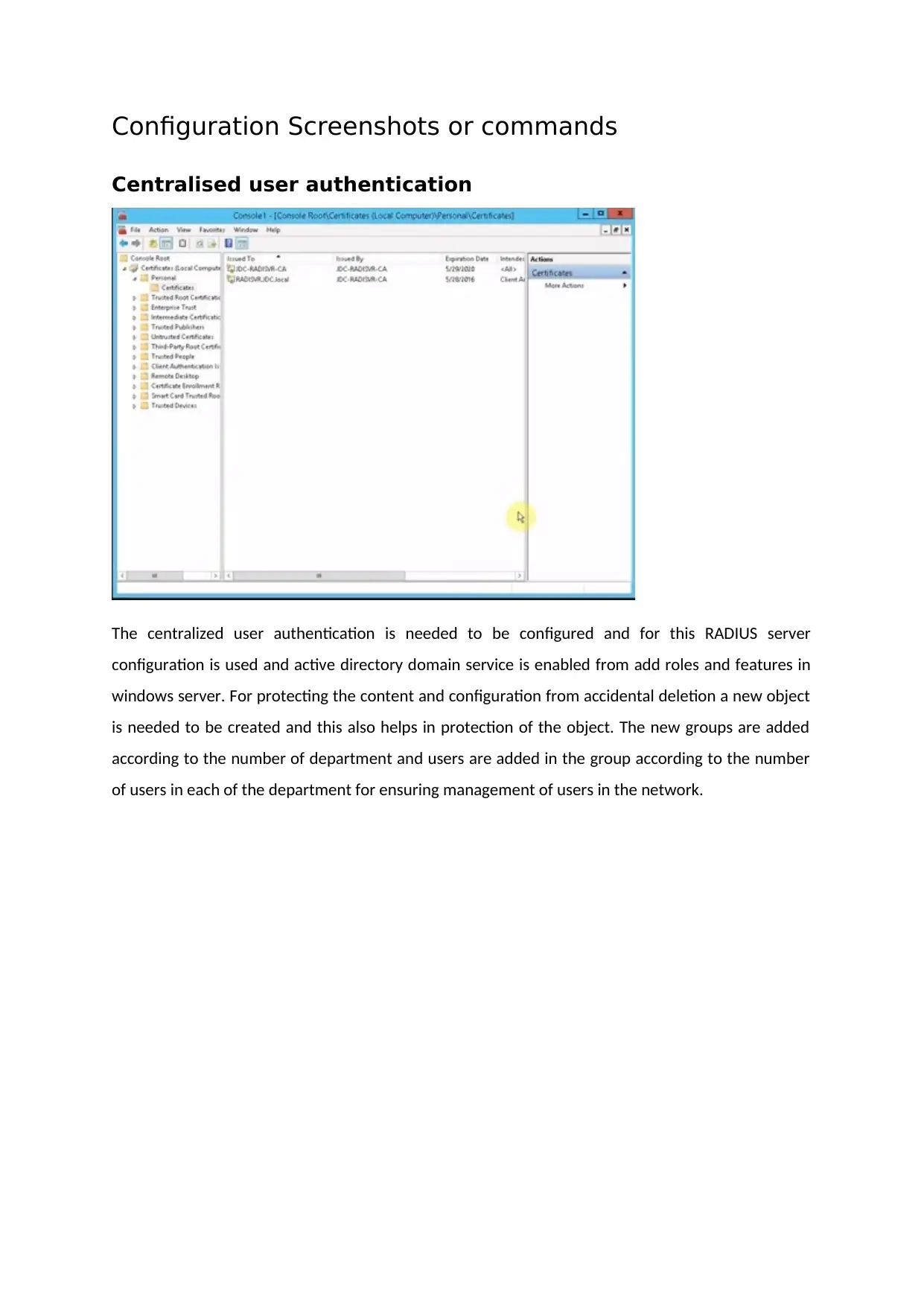
Centralised user authentication
The centralized user authentication is needed to be configured and for this RADIUS server
configuration is used and active directory domain service is enabled from add roles and features in
windows server. For protecting the content and configuration from accidental deletion a new object
is needed to be created and this also helps in protection of the object. The new groups are added
according to the number of department and users are added in the group according to the number
of users in each of the department for ensuring management of users in the network.
Centralised user authentication
The centralized user authentication is needed to be configured and for this RADIUS server
configuration is used and active directory domain service is enabled from add roles and features in
windows server. For protecting the content and configuration from accidental deletion a new object
is needed to be created and this also helps in protection of the object. The new groups are added
according to the number of department and users are added in the group according to the number
of users in each of the department for ensuring management of users in the network.
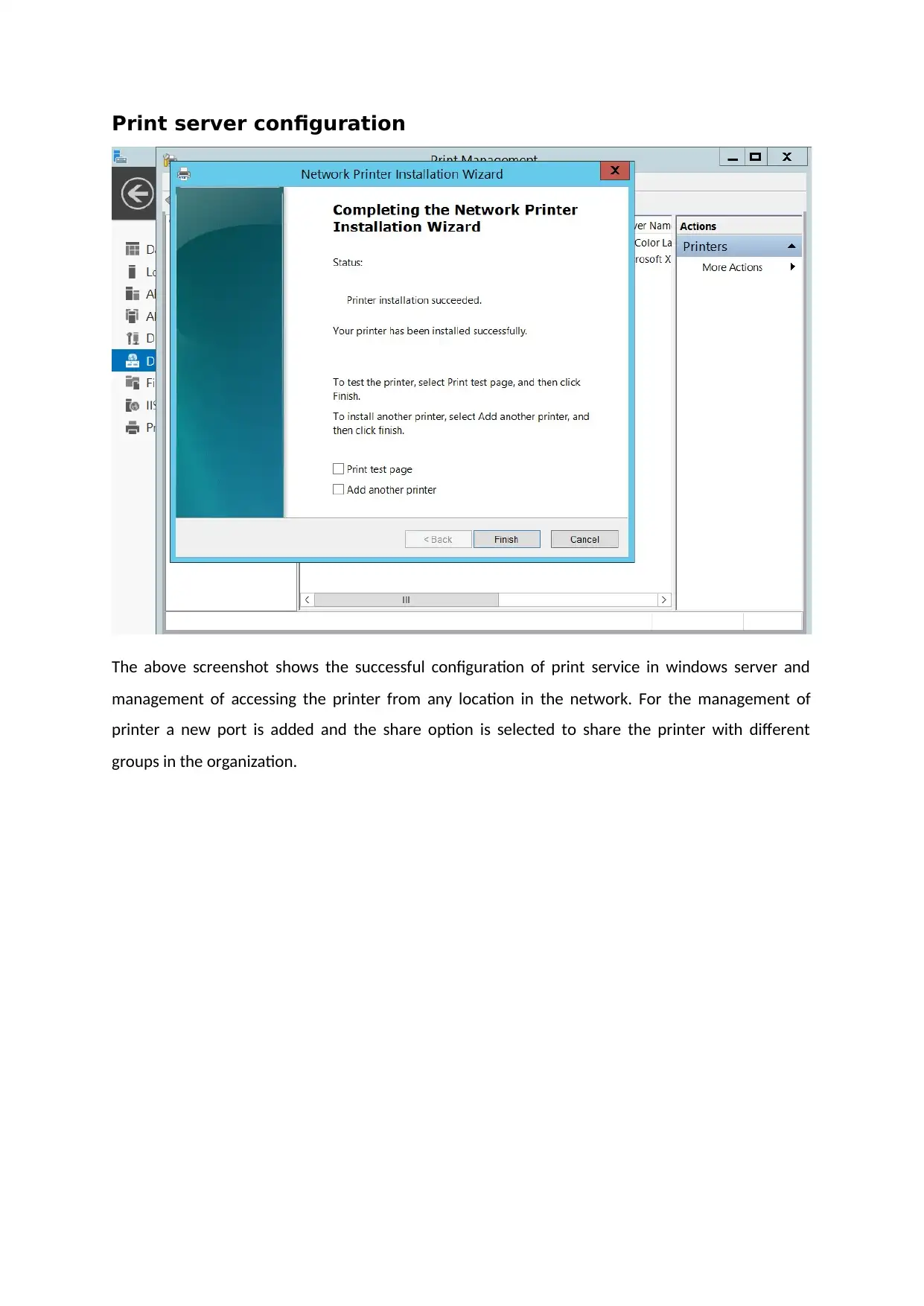
Print server configuration
The above screenshot shows the successful configuration of print service in windows server and
management of accessing the printer from any location in the network. For the management of
printer a new port is added and the share option is selected to share the printer with different
groups in the organization.
The above screenshot shows the successful configuration of print service in windows server and
management of accessing the printer from any location in the network. For the management of
printer a new port is added and the share option is selected to share the printer with different
groups in the organization.
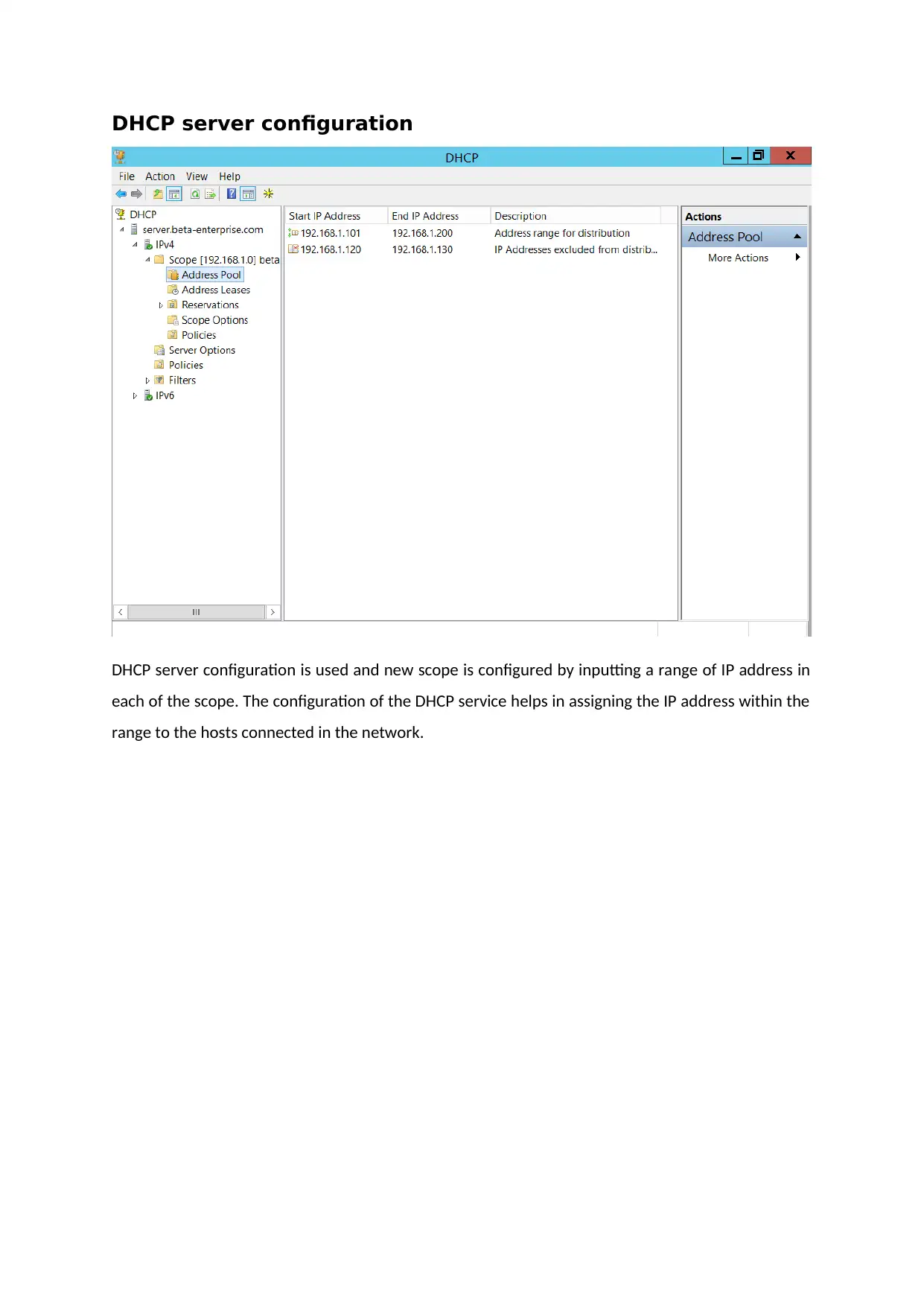
DHCP server configuration
DHCP server configuration is used and new scope is configured by inputting a range of IP address in
each of the scope. The configuration of the DHCP service helps in assigning the IP address within the
range to the hosts connected in the network.
DHCP server configuration is used and new scope is configured by inputting a range of IP address in
each of the scope. The configuration of the DHCP service helps in assigning the IP address within the
range to the hosts connected in the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
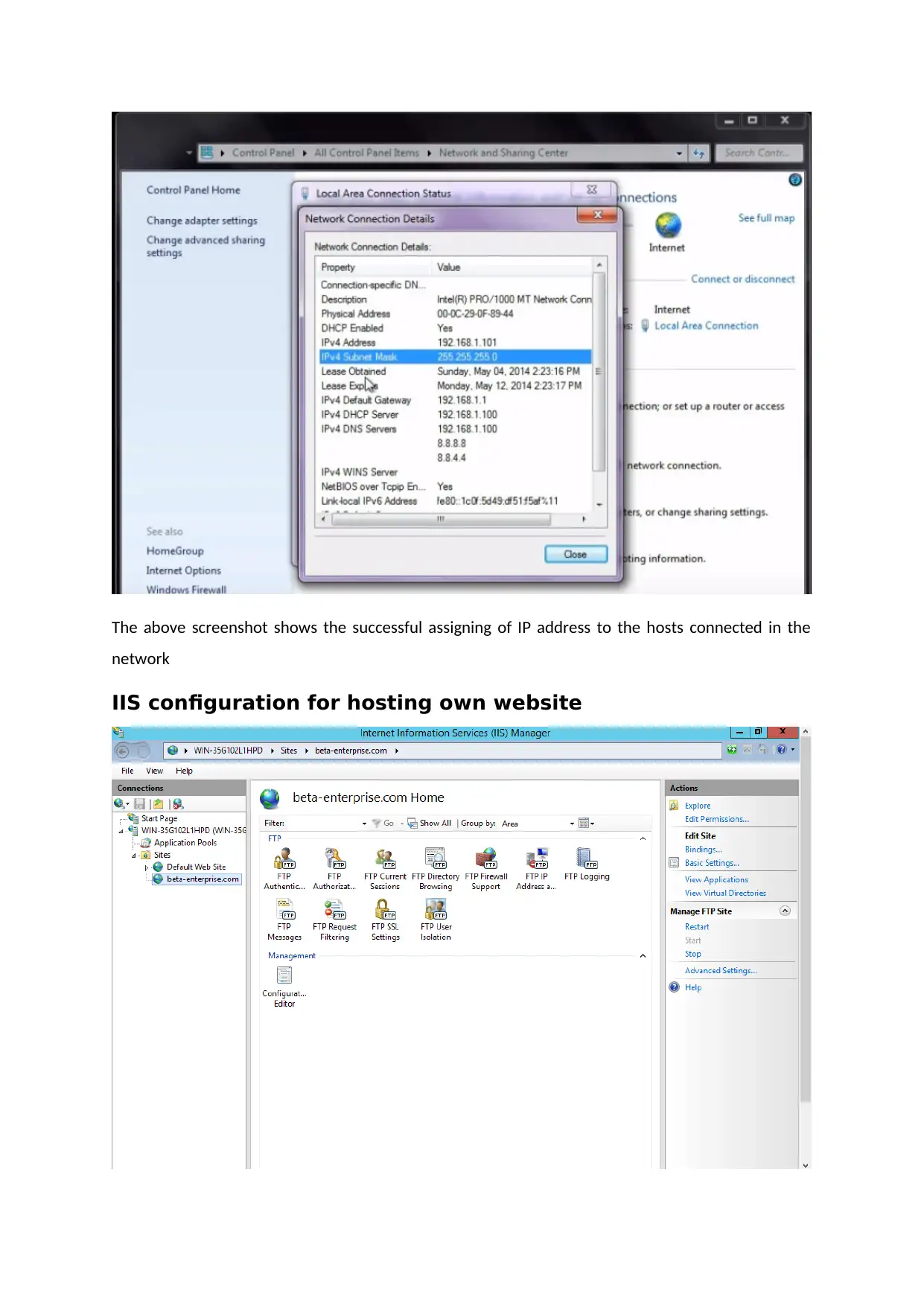
The above screenshot shows the successful assigning of IP address to the hosts connected in the
network
IIS configuration for hosting own website
network
IIS configuration for hosting own website
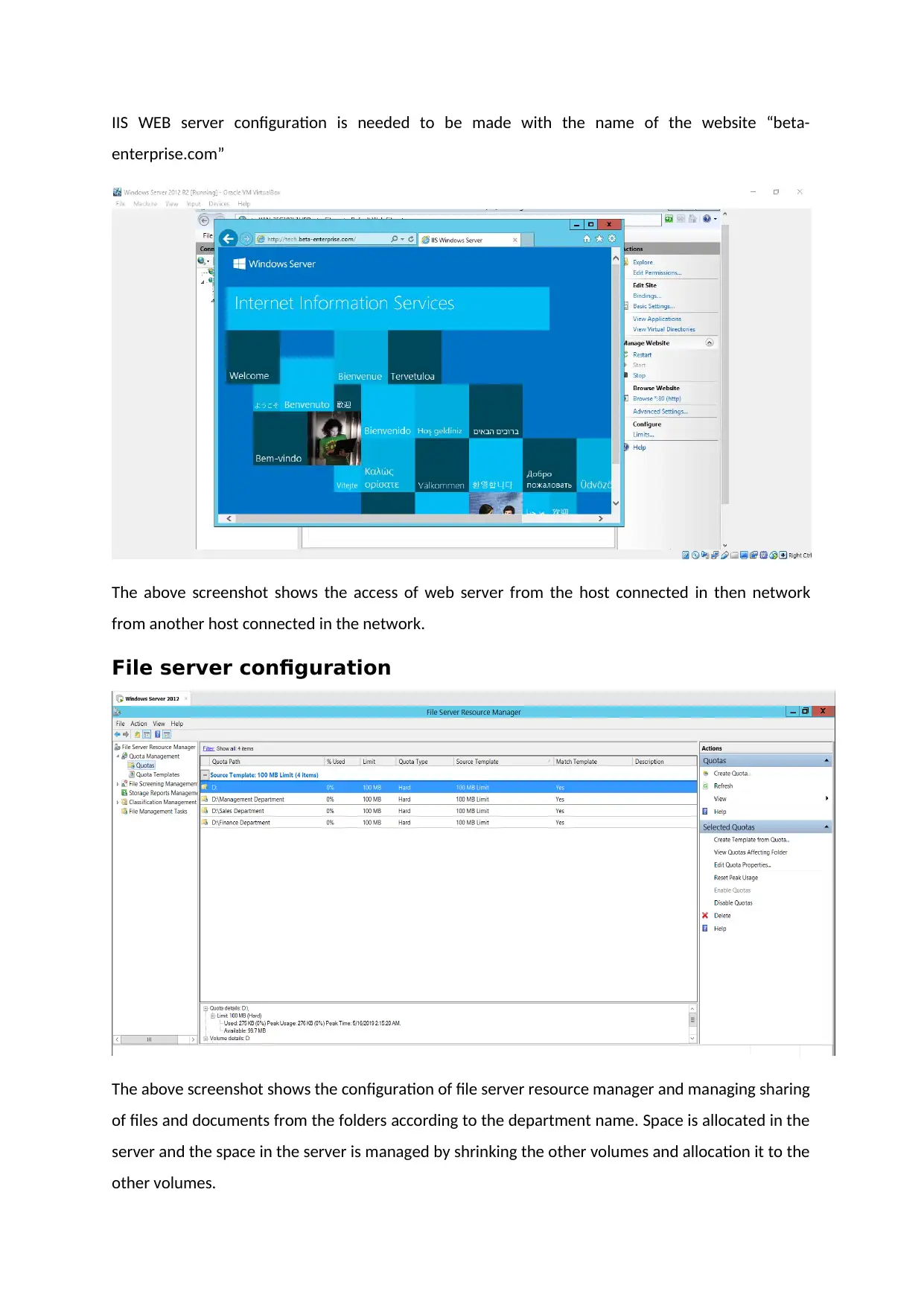
IIS WEB server configuration is needed to be made with the name of the website “beta-
enterprise.com”
The above screenshot shows the access of web server from the host connected in then network
from another host connected in the network.
File server configuration
The above screenshot shows the configuration of file server resource manager and managing sharing
of files and documents from the folders according to the department name. Space is allocated in the
server and the space in the server is managed by shrinking the other volumes and allocation it to the
other volumes.
enterprise.com”
The above screenshot shows the access of web server from the host connected in then network
from another host connected in the network.
File server configuration
The above screenshot shows the configuration of file server resource manager and managing sharing
of files and documents from the folders according to the department name. Space is allocated in the
server and the space in the server is managed by shrinking the other volumes and allocation it to the
other volumes.
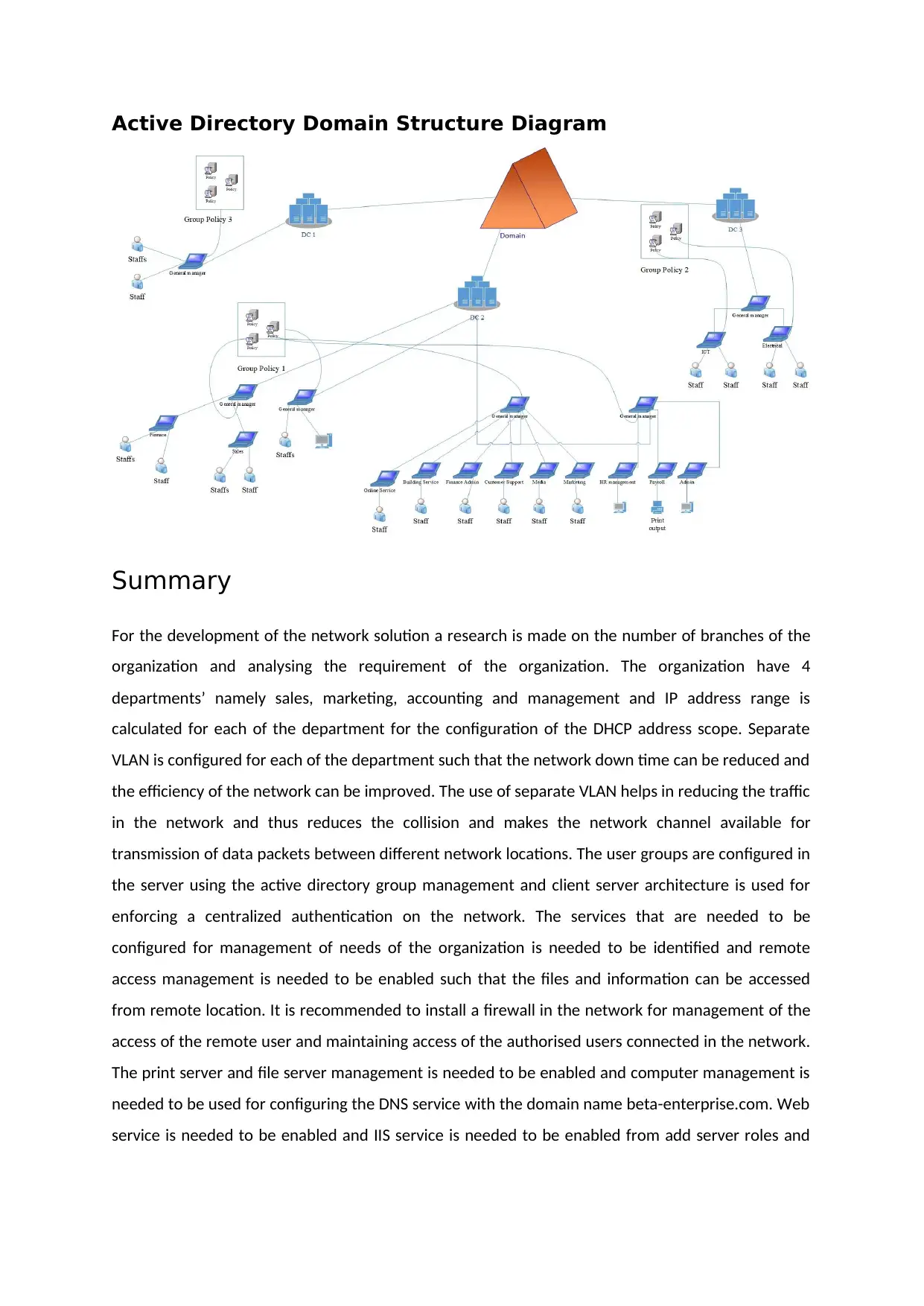
Active Directory Domain Structure Diagram
Summary
For the development of the network solution a research is made on the number of branches of the
organization and analysing the requirement of the organization. The organization have 4
departments’ namely sales, marketing, accounting and management and IP address range is
calculated for each of the department for the configuration of the DHCP address scope. Separate
VLAN is configured for each of the department such that the network down time can be reduced and
the efficiency of the network can be improved. The use of separate VLAN helps in reducing the traffic
in the network and thus reduces the collision and makes the network channel available for
transmission of data packets between different network locations. The user groups are configured in
the server using the active directory group management and client server architecture is used for
enforcing a centralized authentication on the network. The services that are needed to be
configured for management of needs of the organization is needed to be identified and remote
access management is needed to be enabled such that the files and information can be accessed
from remote location. It is recommended to install a firewall in the network for management of the
access of the remote user and maintaining access of the authorised users connected in the network.
The print server and file server management is needed to be enabled and computer management is
needed to be used for configuring the DNS service with the domain name beta-enterprise.com. Web
service is needed to be enabled and IIS service is needed to be enabled from add server roles and
Summary
For the development of the network solution a research is made on the number of branches of the
organization and analysing the requirement of the organization. The organization have 4
departments’ namely sales, marketing, accounting and management and IP address range is
calculated for each of the department for the configuration of the DHCP address scope. Separate
VLAN is configured for each of the department such that the network down time can be reduced and
the efficiency of the network can be improved. The use of separate VLAN helps in reducing the traffic
in the network and thus reduces the collision and makes the network channel available for
transmission of data packets between different network locations. The user groups are configured in
the server using the active directory group management and client server architecture is used for
enforcing a centralized authentication on the network. The services that are needed to be
configured for management of needs of the organization is needed to be identified and remote
access management is needed to be enabled such that the files and information can be accessed
from remote location. It is recommended to install a firewall in the network for management of the
access of the remote user and maintaining access of the authorised users connected in the network.
The print server and file server management is needed to be enabled and computer management is
needed to be used for configuring the DNS service with the domain name beta-enterprise.com. Web
service is needed to be enabled and IIS service is needed to be enabled from add server roles and
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

feature wizard such that an internal website can be hosted and the internal communication between
the employees working in the organization can be managed.
Conclusions
It can be concluded from the above report that the requirement of Thinktank is needed to be
evaluated for the development of the active directory network configuration. A client server
architecture is followed for the development of the framework and the roles and features that are
needed to be installed in the network is evaluated for configuring the server and improve the
security of the network. The group policy is configured for enforcing access control and dividing the
network in multiple subnet. A centralized authentication is maintained for the development of the
network and it is configured such that IP address are automatically assigned to the hosts connected
in each of the department. The file server resource manager is used for enabling quota management
and sharing of files with the different departments. The printer service is enabled for connecting the
network printer and sharing with the different departments such that the cost of the network is
reduced and the resources are utilized efficiently.
the employees working in the organization can be managed.
Conclusions
It can be concluded from the above report that the requirement of Thinktank is needed to be
evaluated for the development of the active directory network configuration. A client server
architecture is followed for the development of the framework and the roles and features that are
needed to be installed in the network is evaluated for configuring the server and improve the
security of the network. The group policy is configured for enforcing access control and dividing the
network in multiple subnet. A centralized authentication is maintained for the development of the
network and it is configured such that IP address are automatically assigned to the hosts connected
in each of the department. The file server resource manager is used for enabling quota management
and sharing of files with the different departments. The printer service is enabled for connecting the
network printer and sharing with the different departments such that the cost of the network is
reduced and the resources are utilized efficiently.

Bibliography
[1]. Bartram, A., El-Bizri, N. and Gittens, D. Introduction. In Recto Verso: Redefining the
Sketchbook (pp. 23-32). Routledge., 2016.
[2]. Ferdoush, Sheikh, and Xinrong Li. "Wireless sensor network system design using
Raspberry Pi and Arduino for environmental monitoring applications." Procedia
Computer Science 34 (2014): 103-110.
[3]. Guo, Bingli, Chunming Qiao, Jianping Wang, Hongfang Yu, Yongxia Zuo, Juhao Li,
Zhangyuan Chen, and Yongqi He. "Survivable virtual network design and embedding to
survive a facility node failure." Journal of Lightwave Technology 32, no. 3 (2014): 483-
493.
[4]. Huh, J.H., Otgonchimeg, S. and Seo, K. Advanced metering infrastructure design and test
bed experiment using intelligent agents: focusing on the PLC network base technology
for Smart Grid system. The Journal of Supercomputing, 72(5), pp.1862-1877., 2016.
[5]. Jurado, F. and Rodriguez, P. Sentiment Analysis in monitoring software development
processes: An exploratory case study on GitHub's project issues. Journal of Systems and
Software, 104, pp.82-89., 2015.
[6]. Marchetti, M., Pierazzi, F., Colajanni, M. and Guido, A. Analysis of high volumes of
network traffic for Advanced Persistent Threat detection. Computer Networks, 109,
pp.127-141., 2016.
[7]. McCormack, K.P. and Johnson, W.C. Supply chain networks and business process
orientation: advanced strategies and best practices. CRC Press., 2016.
[8]. Sandhu, R., Gill, H.K. and Sood, S.K. Smart monitoring and controlling of Pandemic
Influenza A (H1N1) using Social Network Analysis and cloud computing. Journal of
Computational Science, 12, pp.11-22., 2016.
[9]. Simmons, J.M. Optical network design and planning. Springer., 2014.
[10]. Tree, Star. "Wireless sensor networks." Self 1, no. R2 (2014): C0.
[1]. Bartram, A., El-Bizri, N. and Gittens, D. Introduction. In Recto Verso: Redefining the
Sketchbook (pp. 23-32). Routledge., 2016.
[2]. Ferdoush, Sheikh, and Xinrong Li. "Wireless sensor network system design using
Raspberry Pi and Arduino for environmental monitoring applications." Procedia
Computer Science 34 (2014): 103-110.
[3]. Guo, Bingli, Chunming Qiao, Jianping Wang, Hongfang Yu, Yongxia Zuo, Juhao Li,
Zhangyuan Chen, and Yongqi He. "Survivable virtual network design and embedding to
survive a facility node failure." Journal of Lightwave Technology 32, no. 3 (2014): 483-
493.
[4]. Huh, J.H., Otgonchimeg, S. and Seo, K. Advanced metering infrastructure design and test
bed experiment using intelligent agents: focusing on the PLC network base technology
for Smart Grid system. The Journal of Supercomputing, 72(5), pp.1862-1877., 2016.
[5]. Jurado, F. and Rodriguez, P. Sentiment Analysis in monitoring software development
processes: An exploratory case study on GitHub's project issues. Journal of Systems and
Software, 104, pp.82-89., 2015.
[6]. Marchetti, M., Pierazzi, F., Colajanni, M. and Guido, A. Analysis of high volumes of
network traffic for Advanced Persistent Threat detection. Computer Networks, 109,
pp.127-141., 2016.
[7]. McCormack, K.P. and Johnson, W.C. Supply chain networks and business process
orientation: advanced strategies and best practices. CRC Press., 2016.
[8]. Sandhu, R., Gill, H.K. and Sood, S.K. Smart monitoring and controlling of Pandemic
Influenza A (H1N1) using Social Network Analysis and cloud computing. Journal of
Computational Science, 12, pp.11-22., 2016.
[9]. Simmons, J.M. Optical network design and planning. Springer., 2014.
[10]. Tree, Star. "Wireless sensor networks." Self 1, no. R2 (2014): C0.
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





