Local Area Networking Technologies: Design, Implementation, and Management
VerifiedAdded on 2024/05/29
|44
|4999
|454
AI Summary
This comprehensive guide explores the fundamentals of Local Area Networks (LANs), encompassing design, implementation, and management aspects. It delves into various LAN technologies, topologies, and protocols, critically evaluating their suitability for different scenarios. The document provides a step-by-step approach to designing and configuring a robust LAN infrastructure, including security measures like VLANs and ACLs. It also covers network monitoring and troubleshooting techniques, emphasizing the importance of security, reliability, and performance optimization. This resource serves as a valuable reference for students and professionals seeking to gain a deep understanding of LAN technologies and their practical applications.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Local Area Networking Technologies
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction:....................................................................................................................................5
LO1: Understand the impact of LAN technologies.........................................................................6
1.1 With the aid of diagram (if applicable), critically evaluate different technologies/topologies
available in the market, establishing the most appropriate and suitable technology that can be
used in the above scenario?..........................................................................................................6
1.2 Local Area Networks need to be robust both at the level of availability and quality of
service, critically analyses traffic intensive services of network performance and Quality of
Services (QoS) providing some example of applicable use?.....................................................10
1.3 Discuss & evaluate Local Area Network concerns and make recommendations showing
how a hierarchal network model can improve security, reliability and performance?..............12
LO2: Be able to design LAN infrastructures.................................................................................13
2.1 Design network infrastructure to fulfil the requirement of above scenario, your network
design guidance include: [P2.1, D2]..........................................................................................13
2.2 Critically evaluate your network components and design, including [P2.2, M2]................15
LO3: Be able to implement LAN infrastructures..........................................................................17
3.1 Build and configure a LAN (including services) to meet a given requirement...................17
3.2 implement network security on a LAN................................................................................29
3.3 critically review and test a LAN (M3).................................................................................31
LO4: Be able to manage LAN infrastructures...............................................................................38
4.1 There are many tools available in the market to monitor the network, describe and choose
one showing the usefulness of this tool to monitor and troubleshoot a LAN? [P4.1]...............38
4.2 Local Area Network is not immune from many attacks and threats produce a report to
improve security, reliability and performance. [P4.2]...............................................................39
4.3 Critically evaluate the performance of your network proposing a solution to improve
network performance in relation to server’s traffic. [P4.3, M3]................................................40
Introduction:....................................................................................................................................5
LO1: Understand the impact of LAN technologies.........................................................................6
1.1 With the aid of diagram (if applicable), critically evaluate different technologies/topologies
available in the market, establishing the most appropriate and suitable technology that can be
used in the above scenario?..........................................................................................................6
1.2 Local Area Networks need to be robust both at the level of availability and quality of
service, critically analyses traffic intensive services of network performance and Quality of
Services (QoS) providing some example of applicable use?.....................................................10
1.3 Discuss & evaluate Local Area Network concerns and make recommendations showing
how a hierarchal network model can improve security, reliability and performance?..............12
LO2: Be able to design LAN infrastructures.................................................................................13
2.1 Design network infrastructure to fulfil the requirement of above scenario, your network
design guidance include: [P2.1, D2]..........................................................................................13
2.2 Critically evaluate your network components and design, including [P2.2, M2]................15
LO3: Be able to implement LAN infrastructures..........................................................................17
3.1 Build and configure a LAN (including services) to meet a given requirement...................17
3.2 implement network security on a LAN................................................................................29
3.3 critically review and test a LAN (M3).................................................................................31
LO4: Be able to manage LAN infrastructures...............................................................................38
4.1 There are many tools available in the market to monitor the network, describe and choose
one showing the usefulness of this tool to monitor and troubleshoot a LAN? [P4.1]...............38
4.2 Local Area Network is not immune from many attacks and threats produce a report to
improve security, reliability and performance. [P4.2]...............................................................39
4.3 Critically evaluate the performance of your network proposing a solution to improve
network performance in relation to server’s traffic. [P4.3, M3]................................................40

Conclusion.....................................................................................................................................41
Reference:......................................................................................................................................42
Appendix........................................................................................................................................44
List of figure:
Figure 1: Star...................................................................................................................................5
Figure 2: Ring..................................................................................................................................6
Figure 3: Bus....................................................................................................................................6
Figure 4: Hybrid or tree...................................................................................................................7
Figure 5: Mesh.................................................................................................................................7
Figure 6: Proposed Network..........................................................................................................13
Figure 7: Design View of network................................................................................................16
Figure 8: Metadata 1......................................................................................................................17
Figure 9 Metadata 2.......................................................................................................................18
Figure 10: Metadata 3....................................................................................................................19
Figure 11: Metadata 4...................................................................................................................20
Figure 12: Web server implementation.........................................................................................21
Figure 13: Implemented LAN network design..............................................................................21
Figure 14: DNS Configuration......................................................................................................22
Figure 15: DHCP Configuration....................................................................................................22
Figure 16: Switch Configuration 1................................................................................................23
Figure 17: Switch Configuration 2................................................................................................24
Figure 18: Switch Configuration 3................................................................................................25
Figure 19: Email service Implemented..........................................................................................25
Figure 20: FTP server....................................................................................................................26
Figure 21: SSH access on router from remote user.......................................................................26
Figure 22: VLAN configuration over switch.................................................................................27
Figure 23: ACL configuration over router.....................................................................................28
Figure 24: Router configuration....................................................................................................28
Reference:......................................................................................................................................42
Appendix........................................................................................................................................44
List of figure:
Figure 1: Star...................................................................................................................................5
Figure 2: Ring..................................................................................................................................6
Figure 3: Bus....................................................................................................................................6
Figure 4: Hybrid or tree...................................................................................................................7
Figure 5: Mesh.................................................................................................................................7
Figure 6: Proposed Network..........................................................................................................13
Figure 7: Design View of network................................................................................................16
Figure 8: Metadata 1......................................................................................................................17
Figure 9 Metadata 2.......................................................................................................................18
Figure 10: Metadata 3....................................................................................................................19
Figure 11: Metadata 4...................................................................................................................20
Figure 12: Web server implementation.........................................................................................21
Figure 13: Implemented LAN network design..............................................................................21
Figure 14: DNS Configuration......................................................................................................22
Figure 15: DHCP Configuration....................................................................................................22
Figure 16: Switch Configuration 1................................................................................................23
Figure 17: Switch Configuration 2................................................................................................24
Figure 18: Switch Configuration 3................................................................................................25
Figure 19: Email service Implemented..........................................................................................25
Figure 20: FTP server....................................................................................................................26
Figure 21: SSH access on router from remote user.......................................................................26
Figure 22: VLAN configuration over switch.................................................................................27
Figure 23: ACL configuration over router.....................................................................................28
Figure 24: Router configuration....................................................................................................28

Figure 25: Test Plan 1....................................................................................................................30
Figure 26: Test Plan 2....................................................................................................................31
Figure 27: Test Plan 3...................................................................................................................31
Figure 28: Test Plan 4....................................................................................................................32
Figure 29: Test Plan 5....................................................................................................................32
Figure 30: Test Plan 6....................................................................................................................33
Figure 31: Test Plan 7....................................................................................................................33
Figure 32: Test Plan 8....................................................................................................................34
Figure 33: Test Plan 9....................................................................................................................34
Figure 34: Test Plan 10..................................................................................................................35
Figure 26: Test Plan 2....................................................................................................................31
Figure 27: Test Plan 3...................................................................................................................31
Figure 28: Test Plan 4....................................................................................................................32
Figure 29: Test Plan 5....................................................................................................................32
Figure 30: Test Plan 6....................................................................................................................33
Figure 31: Test Plan 7....................................................................................................................33
Figure 32: Test Plan 8....................................................................................................................34
Figure 33: Test Plan 9....................................................................................................................34
Figure 34: Test Plan 10..................................................................................................................35
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Introduction:
LAN mentioned to as Local Area Network. It covered small geographical area for the Network
that gives their facility in the university, college, small agency, workplace, or company.
Documents and assets are mutual at the LAN for the communication. The organization has
wanted a community so that it will deliver connectivity to their staff and place of business. Here,
I should scheme the LAN for the organization. There are 4 elements in the assignments.
The first part of the file will supply a reason for LAN network with the wi-fi and stressed out the
community. Then, the VLAN, device of LAN community, intensive services of traffic, and cable
will be described that beneficial for the Given LAN Network. design Network could be planned
in line with enterprise agency requirements and might be anticipated of the device inside the
second component. LAN Network may be carried out and configured inside the third elements.
There may be a communication approximately the network safety after which trying out of the
connection of community is executed. Troubleshooting and Monitoring procedure might be well-
defined and can be solved protection, reliability, and performance concerns inside the fourth
elements.
LAN mentioned to as Local Area Network. It covered small geographical area for the Network
that gives their facility in the university, college, small agency, workplace, or company.
Documents and assets are mutual at the LAN for the communication. The organization has
wanted a community so that it will deliver connectivity to their staff and place of business. Here,
I should scheme the LAN for the organization. There are 4 elements in the assignments.
The first part of the file will supply a reason for LAN network with the wi-fi and stressed out the
community. Then, the VLAN, device of LAN community, intensive services of traffic, and cable
will be described that beneficial for the Given LAN Network. design Network could be planned
in line with enterprise agency requirements and might be anticipated of the device inside the
second component. LAN Network may be carried out and configured inside the third elements.
There may be a communication approximately the network safety after which trying out of the
connection of community is executed. Troubleshooting and Monitoring procedure might be well-
defined and can be solved protection, reliability, and performance concerns inside the fourth
elements.
LO1: Understand the impact of LAN technologies
1.1 With the aid of diagram (if applicable), critically evaluate different
technologies/topologies available in the market, establishing the most appropriate and
suitable technology that can be used in the above scenario?
Ans. Different type of topologies are:
Star (Stub)
Ring
Bus
Hybrid
Mesh
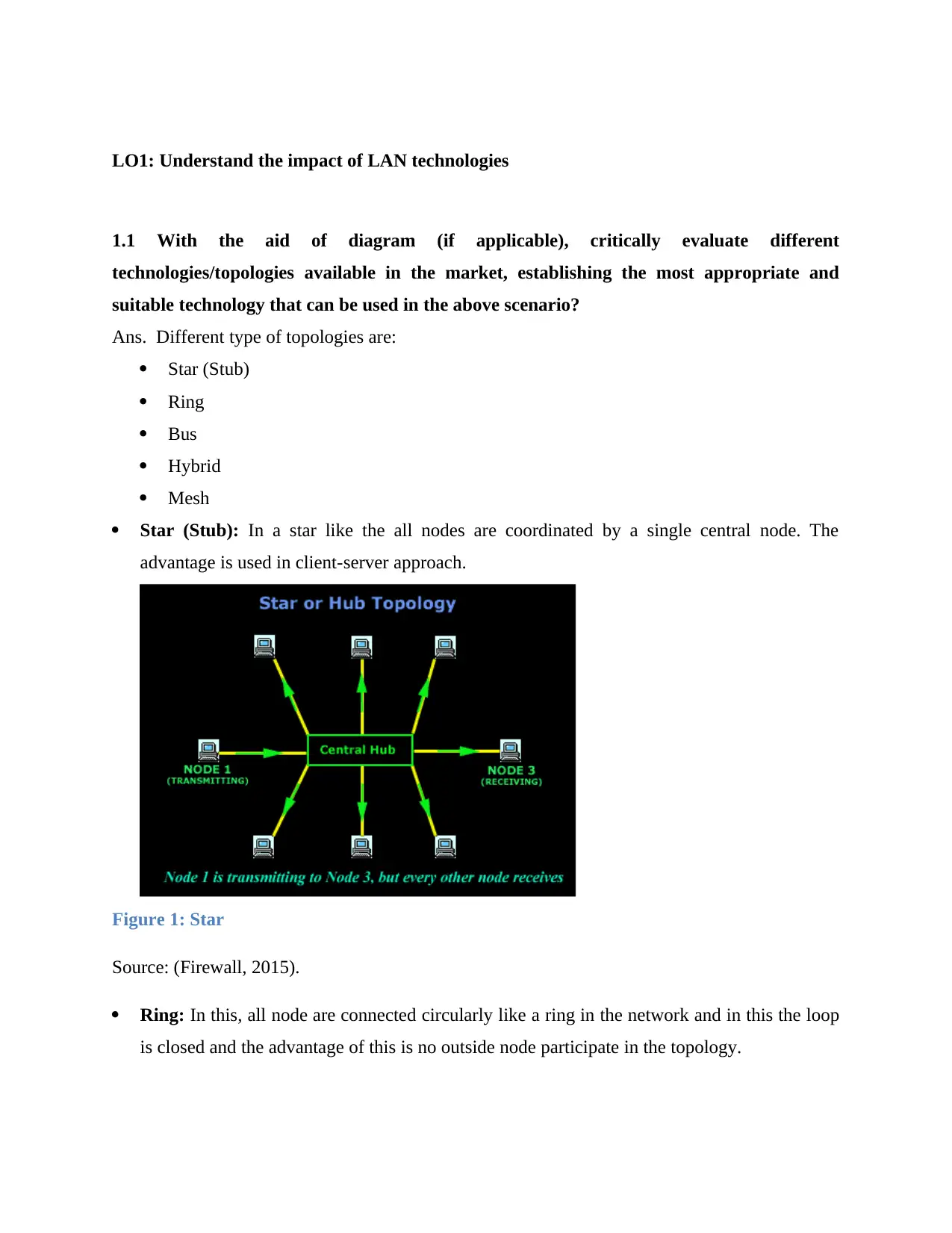
Star (Stub): In a star like the all nodes are coordinated by a single central node. The
advantage is used in client-server approach.
Figure 1: Star
Source: (Firewall, 2015).
Ring: In this, all node are connected circularly like a ring in the network and in this the loop
is closed and the advantage of this is no outside node participate in the topology.
1.1 With the aid of diagram (if applicable), critically evaluate different
technologies/topologies available in the market, establishing the most appropriate and
suitable technology that can be used in the above scenario?
Ans. Different type of topologies are:
Star (Stub)
Ring
Bus
Hybrid
Mesh
Star (Stub): In a star like the all nodes are coordinated by a single central node. The
advantage is used in client-server approach.
Figure 1: Star
Source: (Firewall, 2015).
Ring: In this, all node are connected circularly like a ring in the network and in this the loop
is closed and the advantage of this is no outside node participate in the topology.
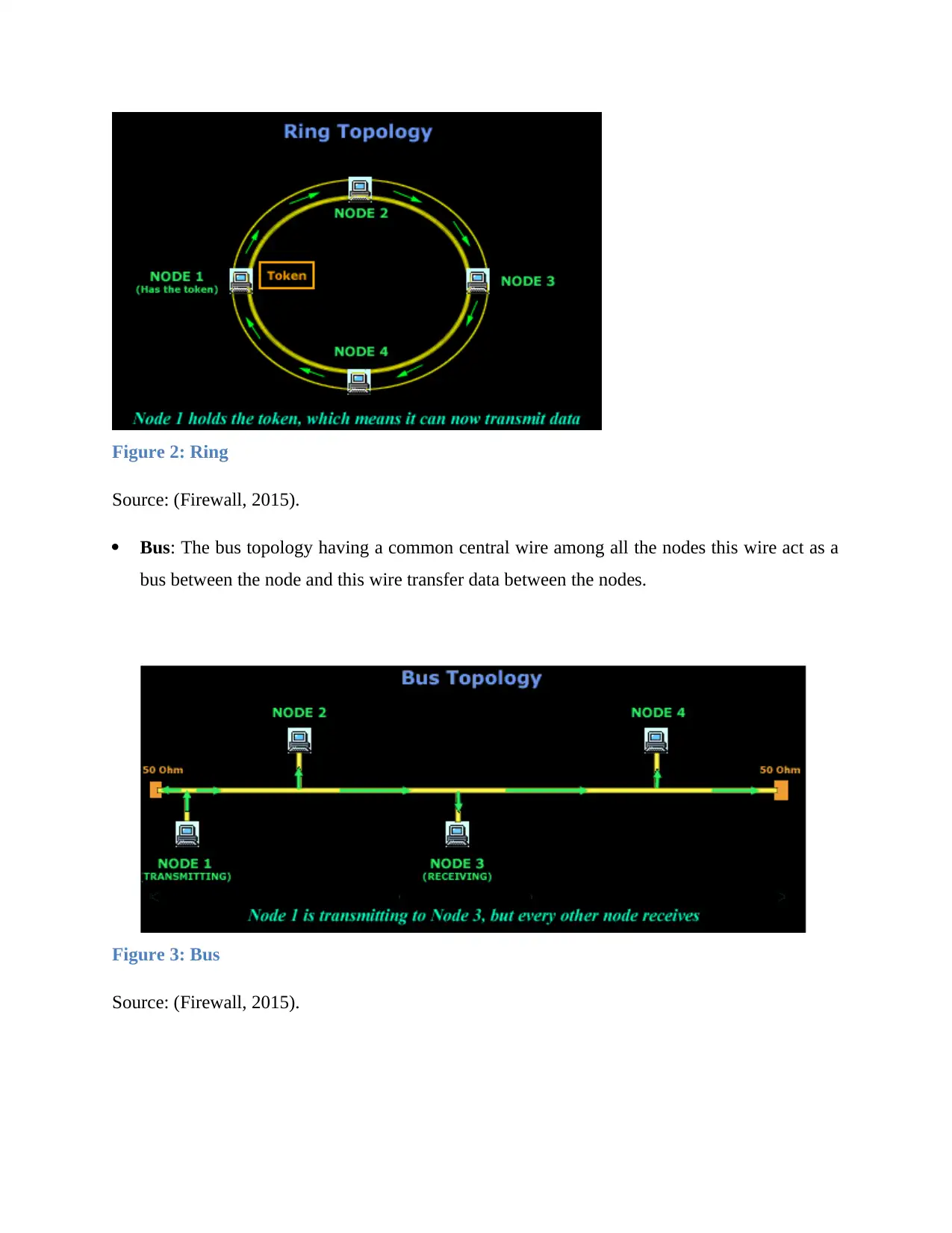
Figure 2: Ring
Source: (Firewall, 2015).
Bus: The bus topology having a common central wire among all the nodes this wire act as a
bus between the node and this wire transfer data between the nodes.
Figure 3: Bus
Source: (Firewall, 2015).
Source: (Firewall, 2015).
Bus: The bus topology having a common central wire among all the nodes this wire act as a
bus between the node and this wire transfer data between the nodes.
Figure 3: Bus
Source: (Firewall, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
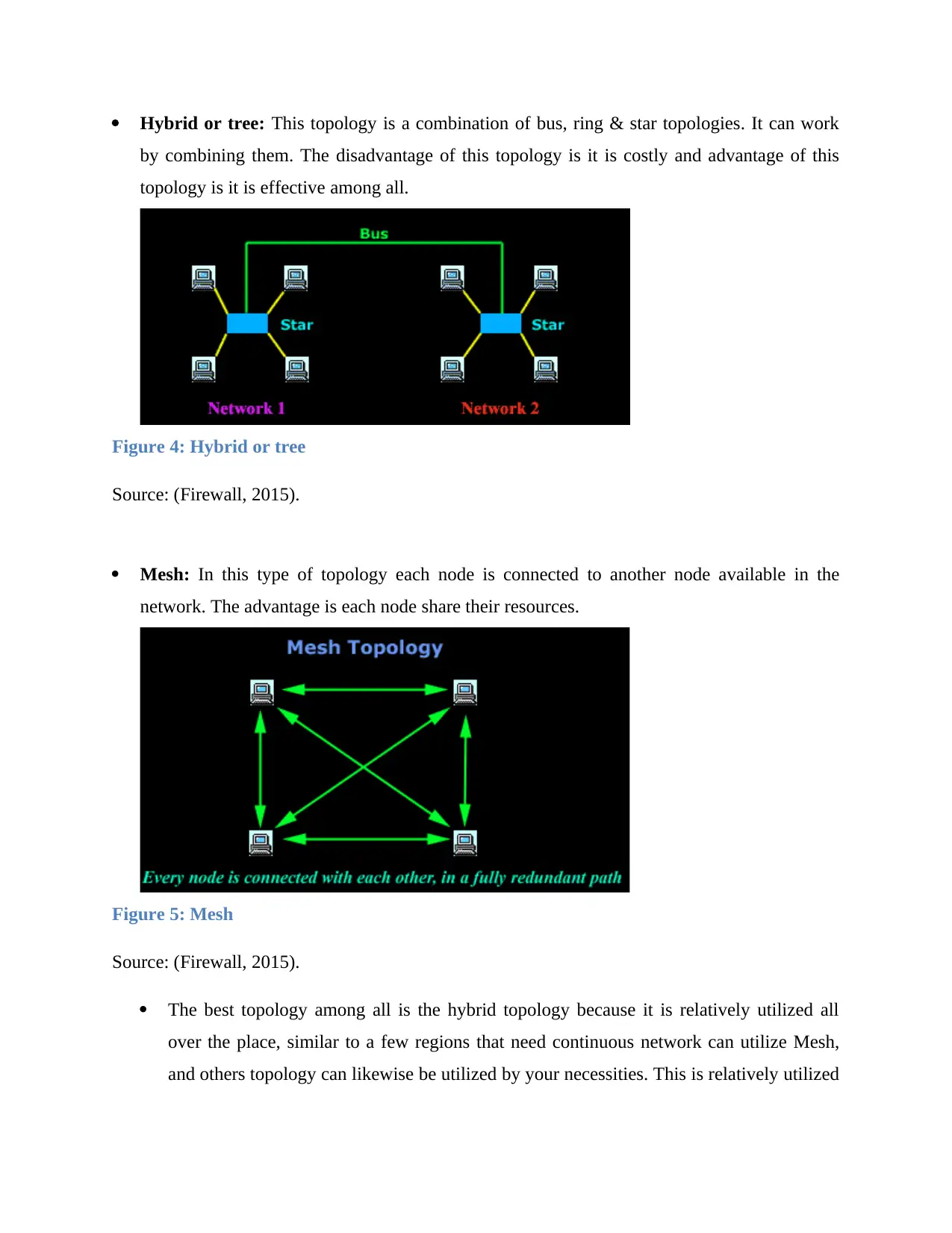
Hybrid or tree: This topology is a combination of bus, ring & star topologies. It can work
by combining them. The disadvantage of this topology is it is costly and advantage of this
topology is it is effective among all.
Figure 4: Hybrid or tree
Source: (Firewall, 2015).
Mesh: In this type of topology each node is connected to another node available in the
network. The advantage is each node share their resources.
Figure 5: Mesh
Source: (Firewall, 2015).
The best topology among all is the hybrid topology because it is relatively utilized all
over the place, similar to a few regions that need continuous network can utilize Mesh,
and others topology can likewise be utilized by your necessities. This is relatively utilized
by combining them. The disadvantage of this topology is it is costly and advantage of this
topology is it is effective among all.
Figure 4: Hybrid or tree
Source: (Firewall, 2015).
Mesh: In this type of topology each node is connected to another node available in the
network. The advantage is each node share their resources.
Figure 5: Mesh
Source: (Firewall, 2015).
The best topology among all is the hybrid topology because it is relatively utilized all
over the place, similar to a few regions that need continuous network can utilize Mesh,
and others topology can likewise be utilized by your necessities. This is relatively utilized

all around, similar to a few zones that need continuous network can utilize Mesh, and
others topology can likewise be utilized by your necessities (Differencebetween, 2018).
others topology can likewise be utilized by your necessities (Differencebetween, 2018).

1.2 Local Area Networks need to be robust both at the level of availability and quality of
service, critically analyses traffic intensive services of network performance and Quality of
Services (QoS) providing some example of applicable use?
Ans. The LAN should provide robustness among the network components because at any time
when any system fails then it should not stop working. Other components in the network may
work. Like in a road at a time from a road only 150 vehicle are use the road if the limit exceeds
then it should break the network due to this the availability for the vehicle may not achieve so
when this problem strike in the network the other path may be started which serves them.
Another example of robust is at a time one server accepts request up to certain limit when it
reaches the other server start receiving a request from client side so at one server no load is
provided. By this, the system QoS is achieved by available the resources to each and every
component which require them without the deadlock in the network. The exchange press and
merchant publicizing have a tendency to underline transmission speed instead of what truly
checks and that is the strength of the remote associations, all things considered, conditions. In the
lab, the transmission speed is estimated under perfect conditions e.g. a coordinated association
and no obstruction.
Several features which improve the QoS in the LAN are:
It should have the feature of load sharing and load balancing.
It does not provide any deadlock with high priority component cannot wait long for a
resource which should be utilized by another component in the network.
It should be transferable in case of failure.
Security constraints may be used to provide flexibility among the components in the local
area network.
In the LAN only authenticated a user can access a resource by successful authorization.
It should always flexible in terms of topology requirement in the network because at any
time any requirement may adopt new features so it should use best to reduce cost and
always available serves in the network.
Power should be effectively utilized by each and every component in the local area
network.
service, critically analyses traffic intensive services of network performance and Quality of
Services (QoS) providing some example of applicable use?
Ans. The LAN should provide robustness among the network components because at any time
when any system fails then it should not stop working. Other components in the network may
work. Like in a road at a time from a road only 150 vehicle are use the road if the limit exceeds
then it should break the network due to this the availability for the vehicle may not achieve so
when this problem strike in the network the other path may be started which serves them.
Another example of robust is at a time one server accepts request up to certain limit when it
reaches the other server start receiving a request from client side so at one server no load is
provided. By this, the system QoS is achieved by available the resources to each and every
component which require them without the deadlock in the network. The exchange press and
merchant publicizing have a tendency to underline transmission speed instead of what truly
checks and that is the strength of the remote associations, all things considered, conditions. In the
lab, the transmission speed is estimated under perfect conditions e.g. a coordinated association
and no obstruction.
Several features which improve the QoS in the LAN are:
It should have the feature of load sharing and load balancing.
It does not provide any deadlock with high priority component cannot wait long for a
resource which should be utilized by another component in the network.
It should be transferable in case of failure.
Security constraints may be used to provide flexibility among the components in the local
area network.
In the LAN only authenticated a user can access a resource by successful authorization.
It should always flexible in terms of topology requirement in the network because at any
time any requirement may adopt new features so it should use best to reduce cost and
always available serves in the network.
Power should be effectively utilized by each and every component in the local area
network.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Each component may serve in specific time domain no component may be waiting for an
infinitely long time because it can degrade the performance of the network.
A node may follow both encryption and decryption process in the network because for
one node act as a client for other served as a server in the network.
LAN should provide smart access to resources in a round robin network and the resources
available on the network should be transferable and various replications are provided of
the resources at various places (Slattery,2013).
infinitely long time because it can degrade the performance of the network.
A node may follow both encryption and decryption process in the network because for
one node act as a client for other served as a server in the network.
LAN should provide smart access to resources in a round robin network and the resources
available on the network should be transferable and various replications are provided of
the resources at various places (Slattery,2013).

1.3 Discuss & evaluate Local Area Network concerns and make recommendations showing
how a hierarchal network model can improve security, reliability and performance?
Ans. Local area network several issues are faced by clients and server. Some of them are:
Security
Performance
Efficiency
Reliability
Authenticity
Failure Handling or fixing
Utilization
Utilization of failed (or no) remote encryption. Trust it or not, numerous ventures still utilize
WEP encryption to "secure" their systems. As I specified in a before the article, WEP
encryption is on a very basic level defective and ought to never be depended upon to secure a
remote system. Utilize WPA encryption.
Efficiency can be achieved by distributing the load or divide the network into several levels.
Only the authenticated user can use the LAN and after successful authorization they provide
access.
LAN should always provide performance among the entire user by load sharing and balance.
Encryption is used so no attacker attacks on the network areas.
The hierarchal network should be very useful at several places where we want security,
performance and reliability because it can separate the network into the various level of
hierarchy so that each hierarchy provide the separate security features needed in the network.
Like an organization, each employee has a different set of power so we provide access according
to that same as we do in a hierarchical network. So by this security is improved in between the
nodes (Ubiquiti, 2017).
The load is shared among different network so when high load on network strike then
performance cannot be degraded or at any time any system in the network fail it does not affect
the other network component. So by this, the reliability of components in the network can be
achieved.
how a hierarchal network model can improve security, reliability and performance?
Ans. Local area network several issues are faced by clients and server. Some of them are:
Security
Performance
Efficiency
Reliability
Authenticity
Failure Handling or fixing
Utilization
Utilization of failed (or no) remote encryption. Trust it or not, numerous ventures still utilize
WEP encryption to "secure" their systems. As I specified in a before the article, WEP
encryption is on a very basic level defective and ought to never be depended upon to secure a
remote system. Utilize WPA encryption.
Efficiency can be achieved by distributing the load or divide the network into several levels.
Only the authenticated user can use the LAN and after successful authorization they provide
access.
LAN should always provide performance among the entire user by load sharing and balance.
Encryption is used so no attacker attacks on the network areas.
The hierarchal network should be very useful at several places where we want security,
performance and reliability because it can separate the network into the various level of
hierarchy so that each hierarchy provide the separate security features needed in the network.
Like an organization, each employee has a different set of power so we provide access according
to that same as we do in a hierarchical network. So by this security is improved in between the
nodes (Ubiquiti, 2017).
The load is shared among different network so when high load on network strike then
performance cannot be degraded or at any time any system in the network fail it does not affect
the other network component. So by this, the reliability of components in the network can be
achieved.

LO2: Be able to design LAN infrastructures
2.1 Design network infrastructure to fulfil the requirement of above scenario, your network
design guidance include: [P2.1, D2]
A hybrid topology is the combination of more than one type of topology it is a combination of
several types of network topology. In hybrid topology, several topologies like a ring, star, & bus
are simultaneously used this makes the powerful among all other types. In this type of topology,
the user has to use one topology may connect to another user who uses another type of topology
at another place. The advantage of hybrid topology is :
Flexible
Scalable
Reliable
Effective
The devices which used in the configuration are CISCO Catalyst 9300 switch (Sparrow, 2014).
Router: Cisco uBR10012 universal broadband routers. It provides transparency among the users
with voice, data and video services.
Wire: Coaxial cables are used to connect routers and witches. The cable should be high quality.
Either squad shield coaxial wire or headend-grade coaxial wire is used for connecting the
components.
VLANs: It is the collection of devices on one or more LAN that is connected and visible on a
single wire to achieve the result.
IP Address: It the unique address of each physical device on the network through this address the
data are sent and receive.
The range of IP Address: In IPV4 protocol there are five classes are defined in the network and
each device has a unique set of the address range. There are A, B, C, D & E classes. Only first
three classes are mainly used (Arstechnica, 2002).
2.1 Design network infrastructure to fulfil the requirement of above scenario, your network
design guidance include: [P2.1, D2]
A hybrid topology is the combination of more than one type of topology it is a combination of
several types of network topology. In hybrid topology, several topologies like a ring, star, & bus
are simultaneously used this makes the powerful among all other types. In this type of topology,
the user has to use one topology may connect to another user who uses another type of topology
at another place. The advantage of hybrid topology is :
Flexible
Scalable
Reliable
Effective
The devices which used in the configuration are CISCO Catalyst 9300 switch (Sparrow, 2014).
Router: Cisco uBR10012 universal broadband routers. It provides transparency among the users
with voice, data and video services.
Wire: Coaxial cables are used to connect routers and witches. The cable should be high quality.
Either squad shield coaxial wire or headend-grade coaxial wire is used for connecting the
components.
VLANs: It is the collection of devices on one or more LAN that is connected and visible on a
single wire to achieve the result.
IP Address: It the unique address of each physical device on the network through this address the
data are sent and receive.
The range of IP Address: In IPV4 protocol there are five classes are defined in the network and
each device has a unique set of the address range. There are A, B, C, D & E classes. Only first
three classes are mainly used (Arstechnica, 2002).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
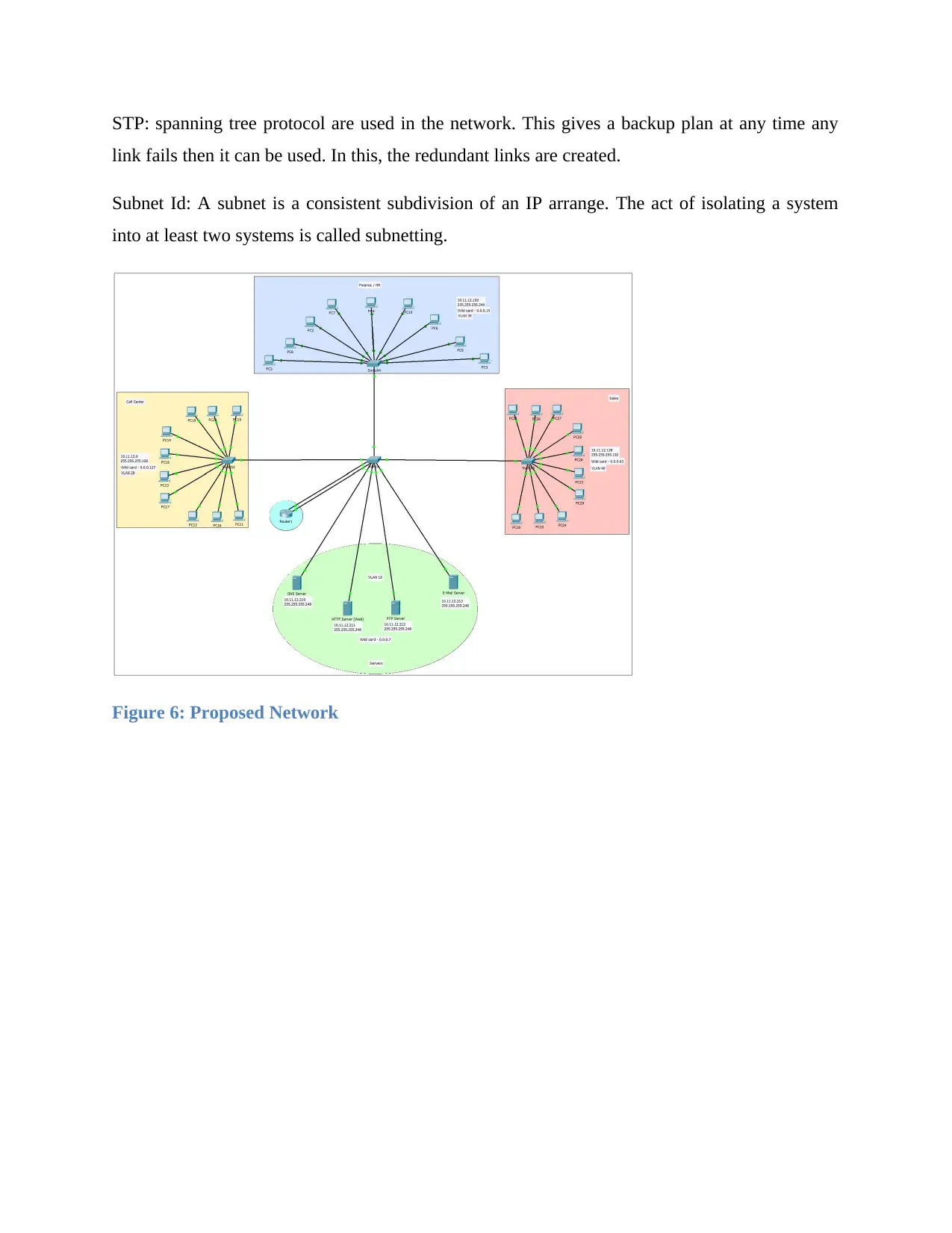
STP: spanning tree protocol are used in the network. This gives a backup plan at any time any
link fails then it can be used. In this, the redundant links are created.
Subnet Id: A subnet is a consistent subdivision of an IP arrange. The act of isolating a system
into at least two systems is called subnetting.
Figure 6: Proposed Network
link fails then it can be used. In this, the redundant links are created.
Subnet Id: A subnet is a consistent subdivision of an IP arrange. The act of isolating a system
into at least two systems is called subnetting.
Figure 6: Proposed Network

2.2 Critically evaluate your network components and design, including [P2.2, M2]
Ans. In hybrid topology the switches, routers and coaxial wire for communication are used in the
network the various topology like a star, bus, etc. are created and by that, the user connects
through a wireless link through distant places. All switches and routers are of CISCO. Coaxial
cable is used due to their high and bandwidth. A hybrid topology is best because it works two or
three topology work simultaneously.
Router: Cisco uBR10012 universal broadband routers. It provides transparency among the users
with voice, data and video services.
CISCO 9300 Series get to switches give you brilliant, straightforward, and exceptionally secure
bound together access
For security, there is a wide range of approaches to give security to the neighbourhood (LANs).
Huge numbers of these apply to the basic sorts of equipment that are utilized for these little,
neighbourhood organizes setups.
One regular procedure is to introduce a firewall asset behind a solitary access point, for example,
an underlying remote switch. It's likewise suitable to utilize particular security conventions like
WPA or WPA2 for secret key encryption on activity rolling in from the web. Creators may
likewise need to secure different switches and switches that serve distinctive parts of the system.
Chairmen can likewise channel activity utilizing an itemized learning of trusted system
territories. LANs regularly require inside security techniques. These include including
components like against infection or hostile to malware security, on the off chance that a portion
of these sorts of hacking capacities is acquainted with systems through client movement. For
instance, numerous meddlesome infections and malignant projects work off of a client opening
an email, downloading a record from an ill-conceived source or generally opening up the inside
LAN to outside dangers. By using the security feature the user access the network application
without any worry. For private as well as the public application it becomes available for the use
(Differencebetween, 2011).
Ans. In hybrid topology the switches, routers and coaxial wire for communication are used in the
network the various topology like a star, bus, etc. are created and by that, the user connects
through a wireless link through distant places. All switches and routers are of CISCO. Coaxial
cable is used due to their high and bandwidth. A hybrid topology is best because it works two or
three topology work simultaneously.
Router: Cisco uBR10012 universal broadband routers. It provides transparency among the users
with voice, data and video services.
CISCO 9300 Series get to switches give you brilliant, straightforward, and exceptionally secure
bound together access
For security, there is a wide range of approaches to give security to the neighbourhood (LANs).
Huge numbers of these apply to the basic sorts of equipment that are utilized for these little,
neighbourhood organizes setups.
One regular procedure is to introduce a firewall asset behind a solitary access point, for example,
an underlying remote switch. It's likewise suitable to utilize particular security conventions like
WPA or WPA2 for secret key encryption on activity rolling in from the web. Creators may
likewise need to secure different switches and switches that serve distinctive parts of the system.
Chairmen can likewise channel activity utilizing an itemized learning of trusted system
territories. LANs regularly require inside security techniques. These include including
components like against infection or hostile to malware security, on the off chance that a portion
of these sorts of hacking capacities is acquainted with systems through client movement. For
instance, numerous meddlesome infections and malignant projects work off of a client opening
an email, downloading a record from an ill-conceived source or generally opening up the inside
LAN to outside dangers. By using the security feature the user access the network application
without any worry. For private as well as the public application it becomes available for the use
(Differencebetween, 2011).

For becoming the network scalable the links are replicated so at any time anyone link fails other
available backup plans is used. We can also use CISCO 3tier architecture in which the user has
not to change configuration when the parts or devices increase in future.
At every link the firewall is established through authentication then only they have crossed the
firewall by authentication through username and password.
available backup plans is used. We can also use CISCO 3tier architecture in which the user has
not to change configuration when the parts or devices increase in future.
At every link the firewall is established through authentication then only they have crossed the
firewall by authentication through username and password.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
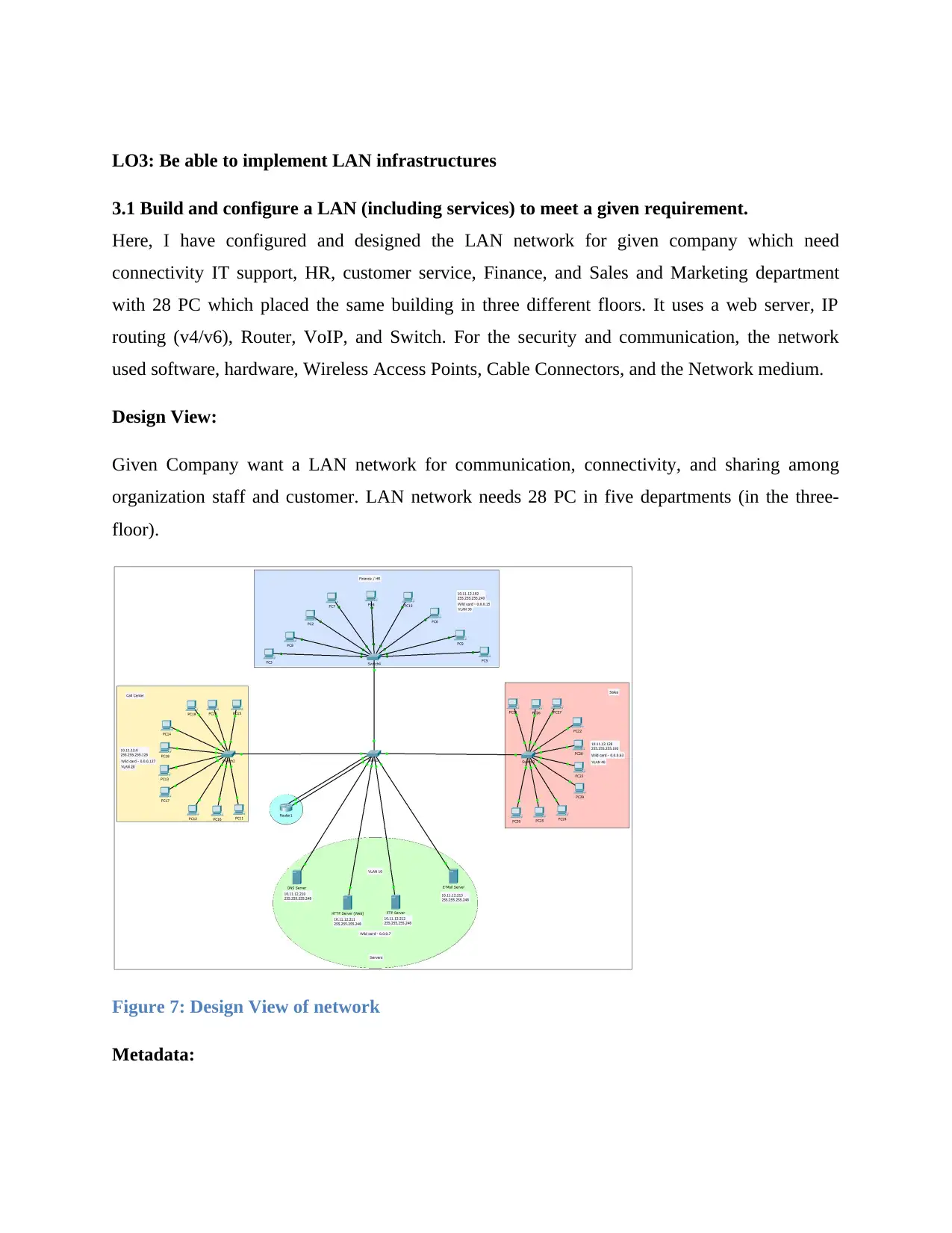
LO3: Be able to implement LAN infrastructures
3.1 Build and configure a LAN (including services) to meet a given requirement.
Here, I have configured and designed the LAN network for given company which need
connectivity IT support, HR, customer service, Finance, and Sales and Marketing department
with 28 PC which placed the same building in three different floors. It uses a web server, IP
routing (v4/v6), Router, VoIP, and Switch. For the security and communication, the network
used software, hardware, Wireless Access Points, Cable Connectors, and the Network medium.
Design View:
Given Company want a LAN network for communication, connectivity, and sharing among
organization staff and customer. LAN network needs 28 PC in five departments (in the three-
floor).
Figure 7: Design View of network
Metadata:
3.1 Build and configure a LAN (including services) to meet a given requirement.
Here, I have configured and designed the LAN network for given company which need
connectivity IT support, HR, customer service, Finance, and Sales and Marketing department
with 28 PC which placed the same building in three different floors. It uses a web server, IP
routing (v4/v6), Router, VoIP, and Switch. For the security and communication, the network
used software, hardware, Wireless Access Points, Cable Connectors, and the Network medium.
Design View:
Given Company want a LAN network for communication, connectivity, and sharing among
organization staff and customer. LAN network needs 28 PC in five departments (in the three-
floor).
Figure 7: Design View of network
Metadata:
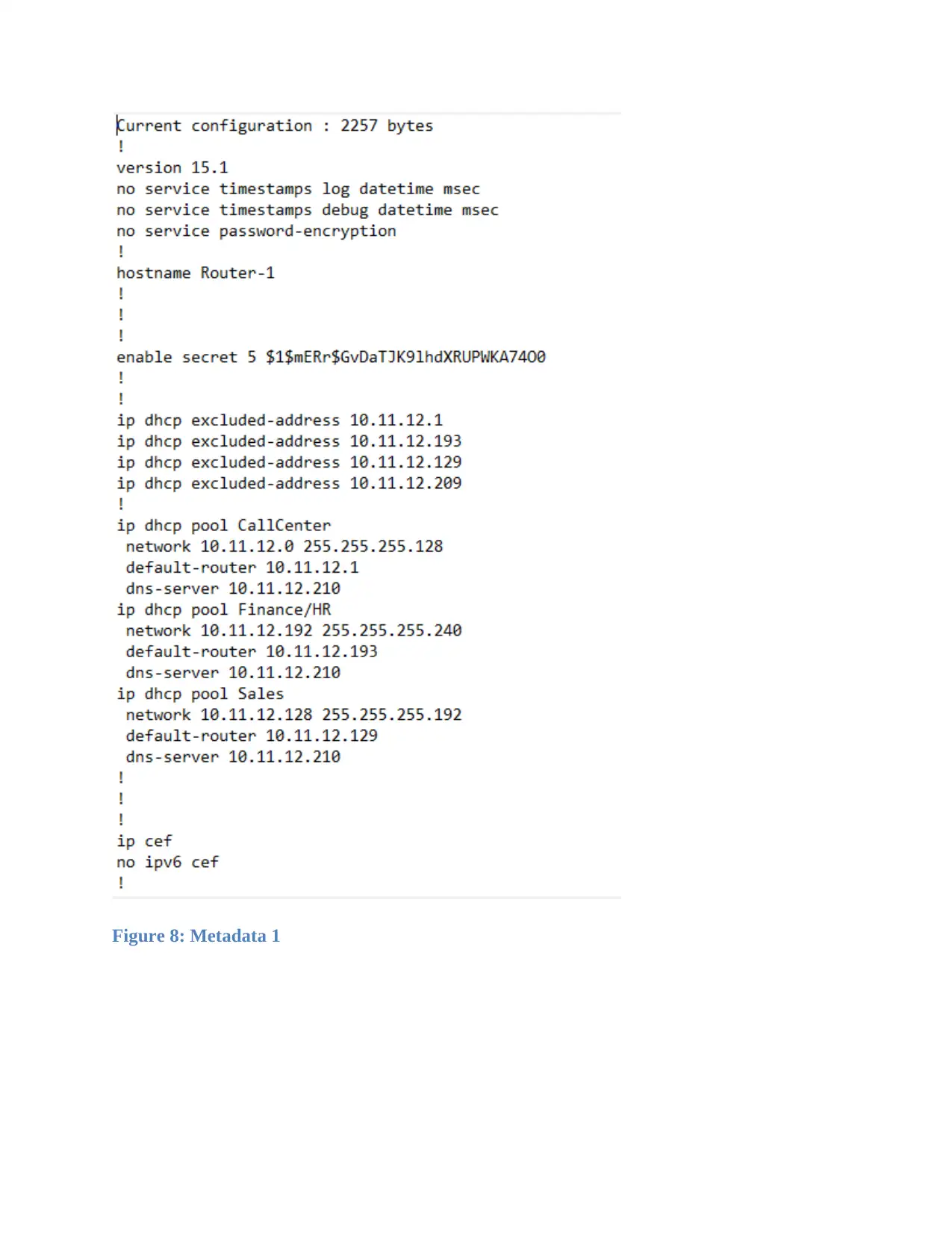
Figure 8: Metadata 1
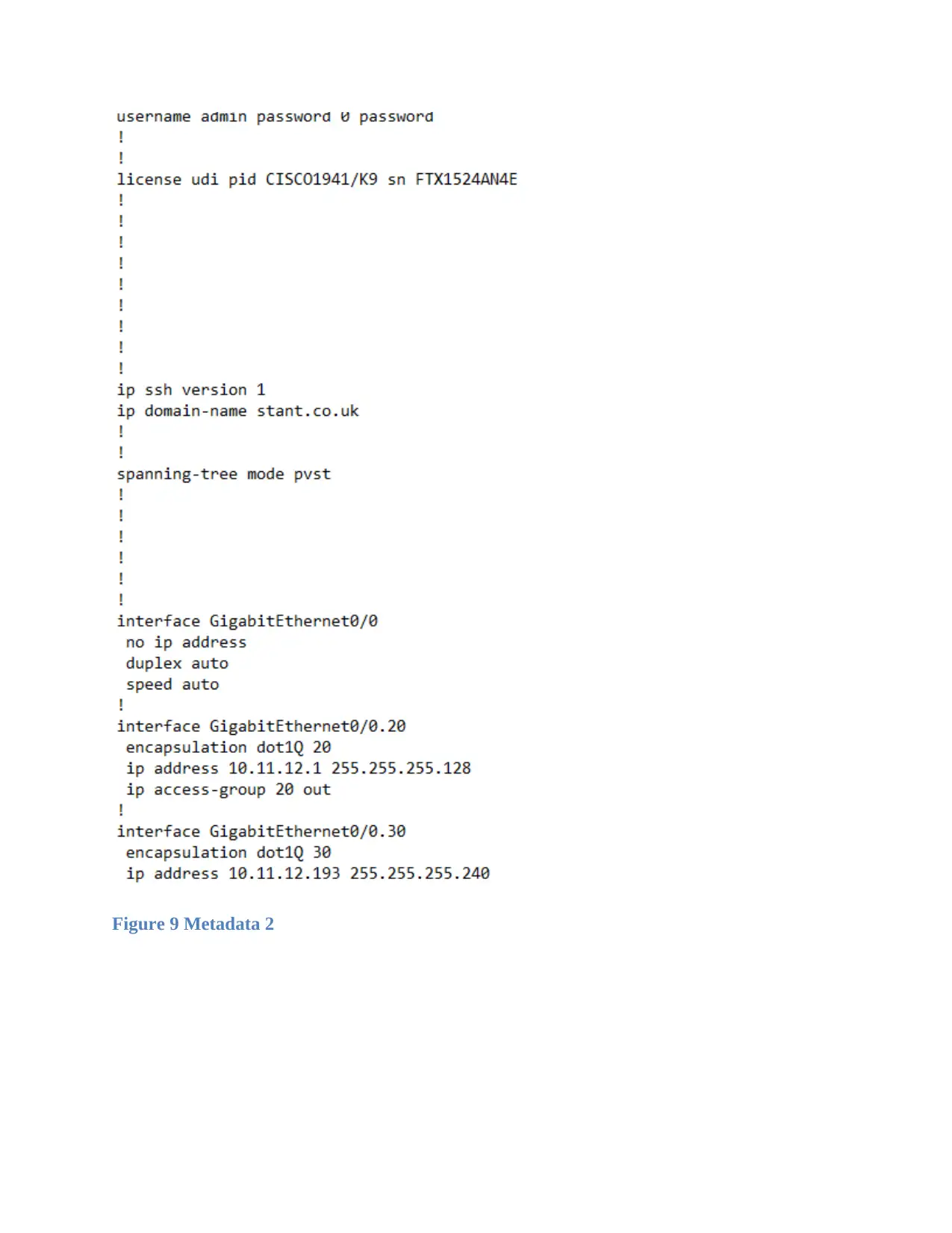
Figure 9 Metadata 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
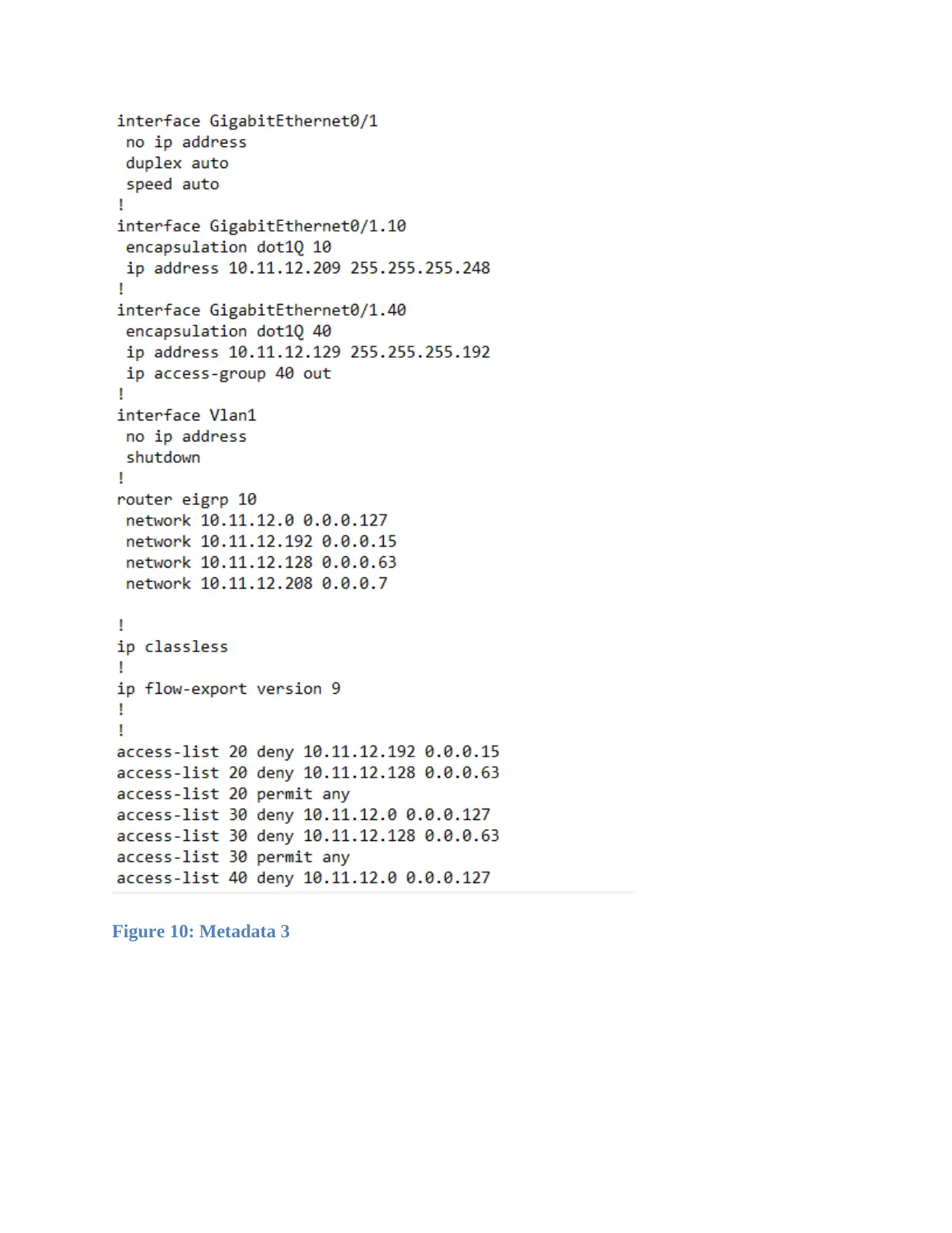
Figure 10: Metadata 3
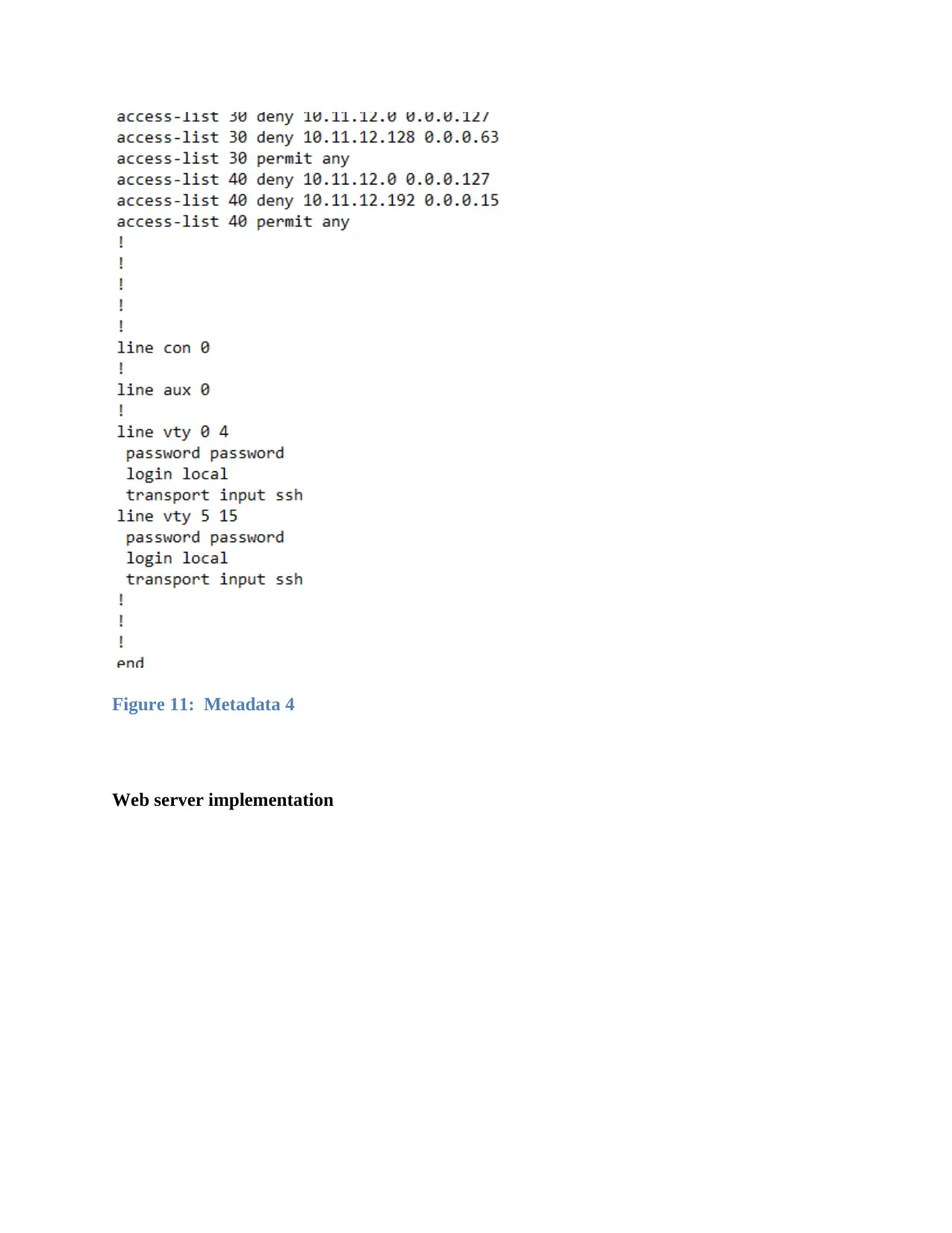
Figure 11: Metadata 4
Web server implementation
Web server implementation
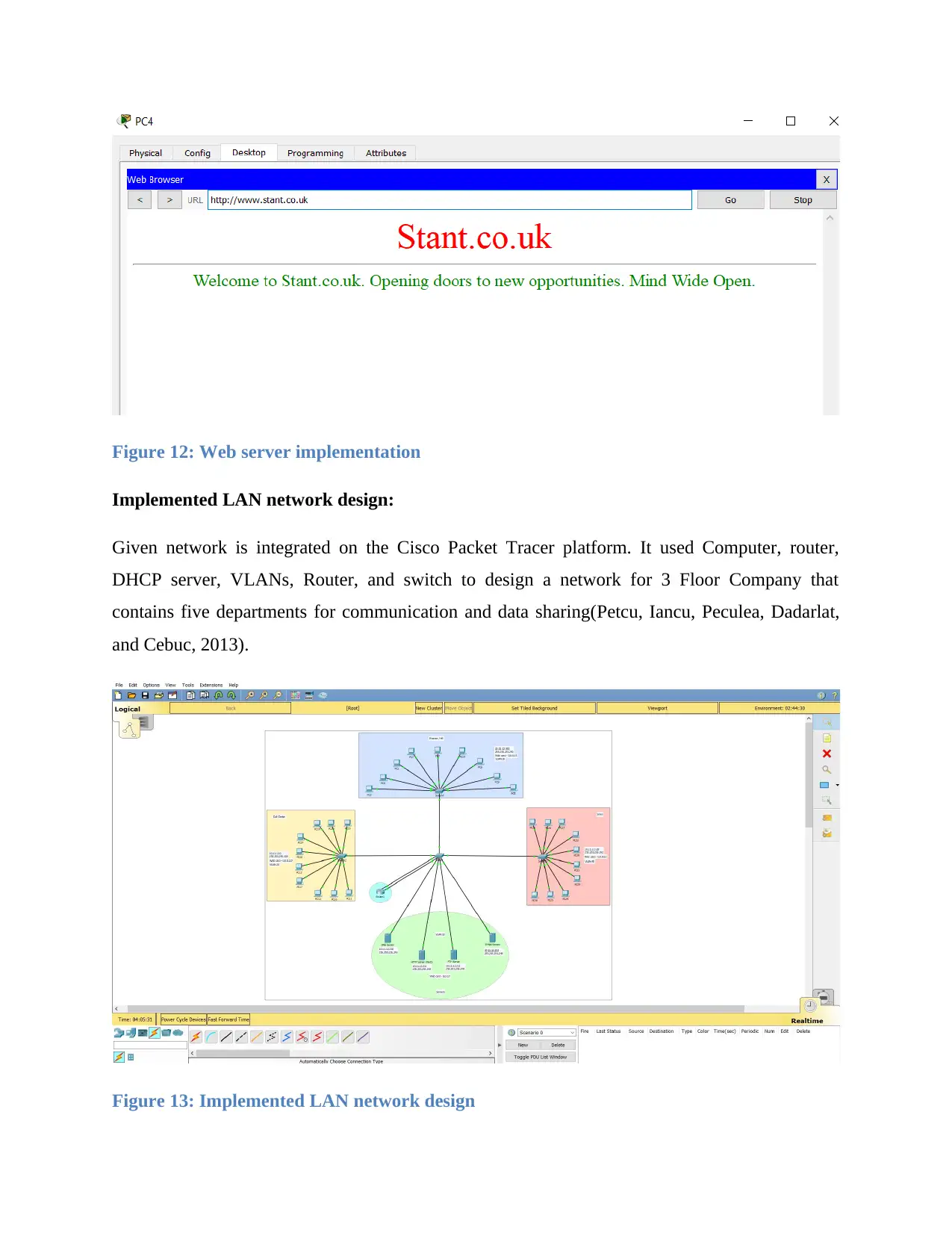
Figure 12: Web server implementation
Implemented LAN network design:
Given network is integrated on the Cisco Packet Tracer platform. It used Computer, router,
DHCP server, VLANs, Router, and switch to design a network for 3 Floor Company that
contains five departments for communication and data sharing(Petcu, Iancu, Peculea, Dadarlat,
and Cebuc, 2013).
Figure 13: Implemented LAN network design
Implemented LAN network design:
Given network is integrated on the Cisco Packet Tracer platform. It used Computer, router,
DHCP server, VLANs, Router, and switch to design a network for 3 Floor Company that
contains five departments for communication and data sharing(Petcu, Iancu, Peculea, Dadarlat,
and Cebuc, 2013).
Figure 13: Implemented LAN network design
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
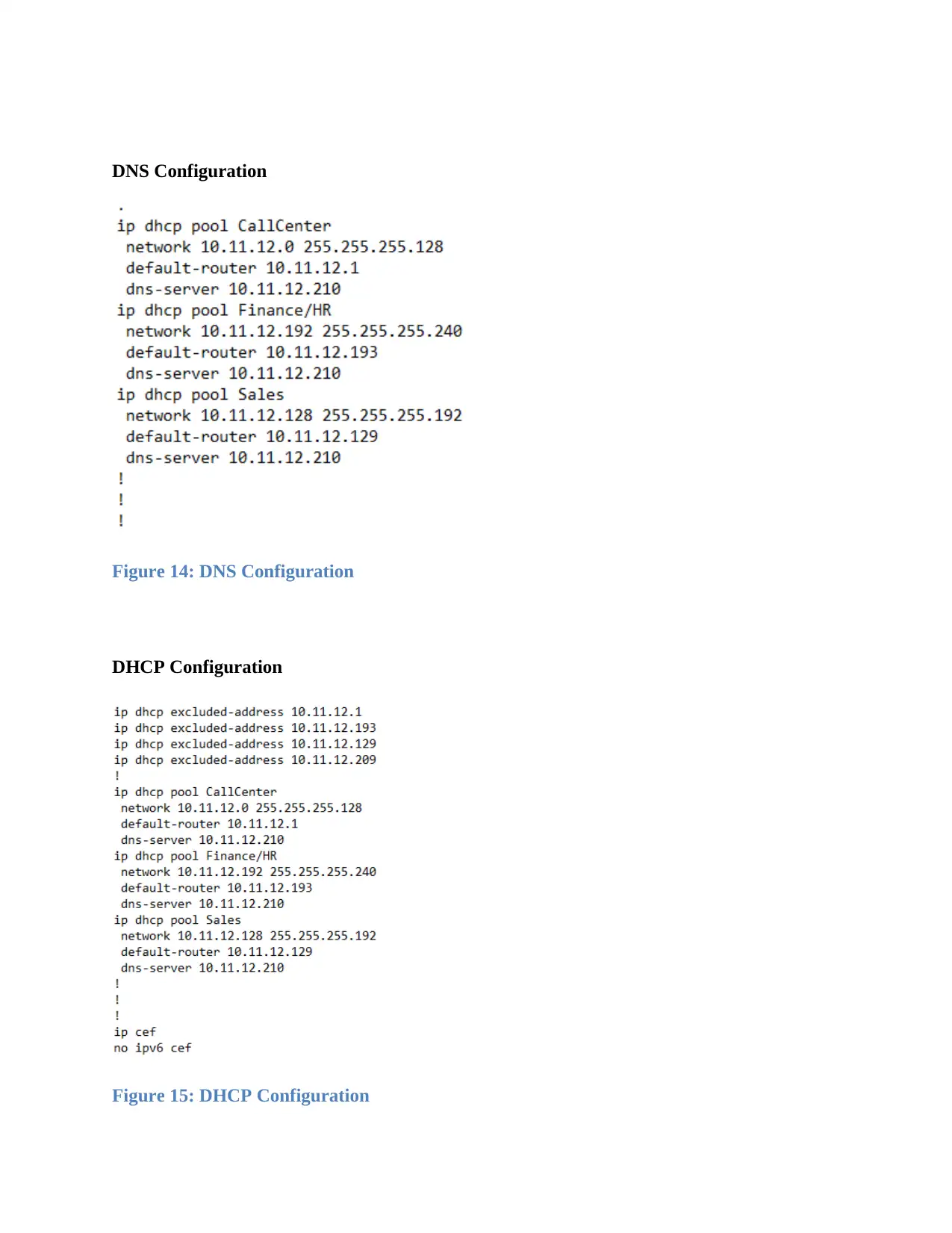
DNS Configuration
Figure 14: DNS Configuration
DHCP Configuration
Figure 15: DHCP Configuration
Figure 14: DNS Configuration
DHCP Configuration
Figure 15: DHCP Configuration
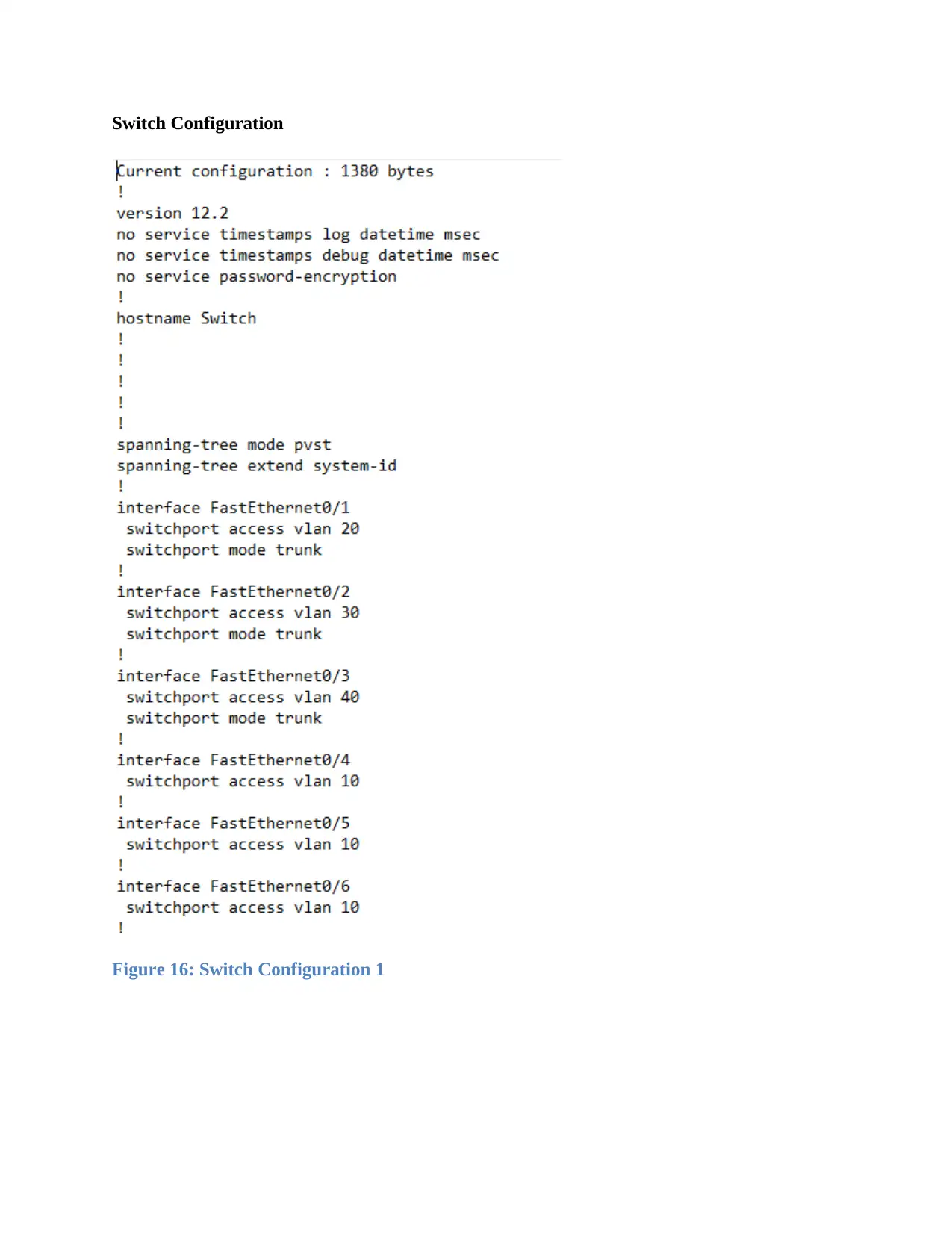
Switch Configuration
Figure 16: Switch Configuration 1
Figure 16: Switch Configuration 1
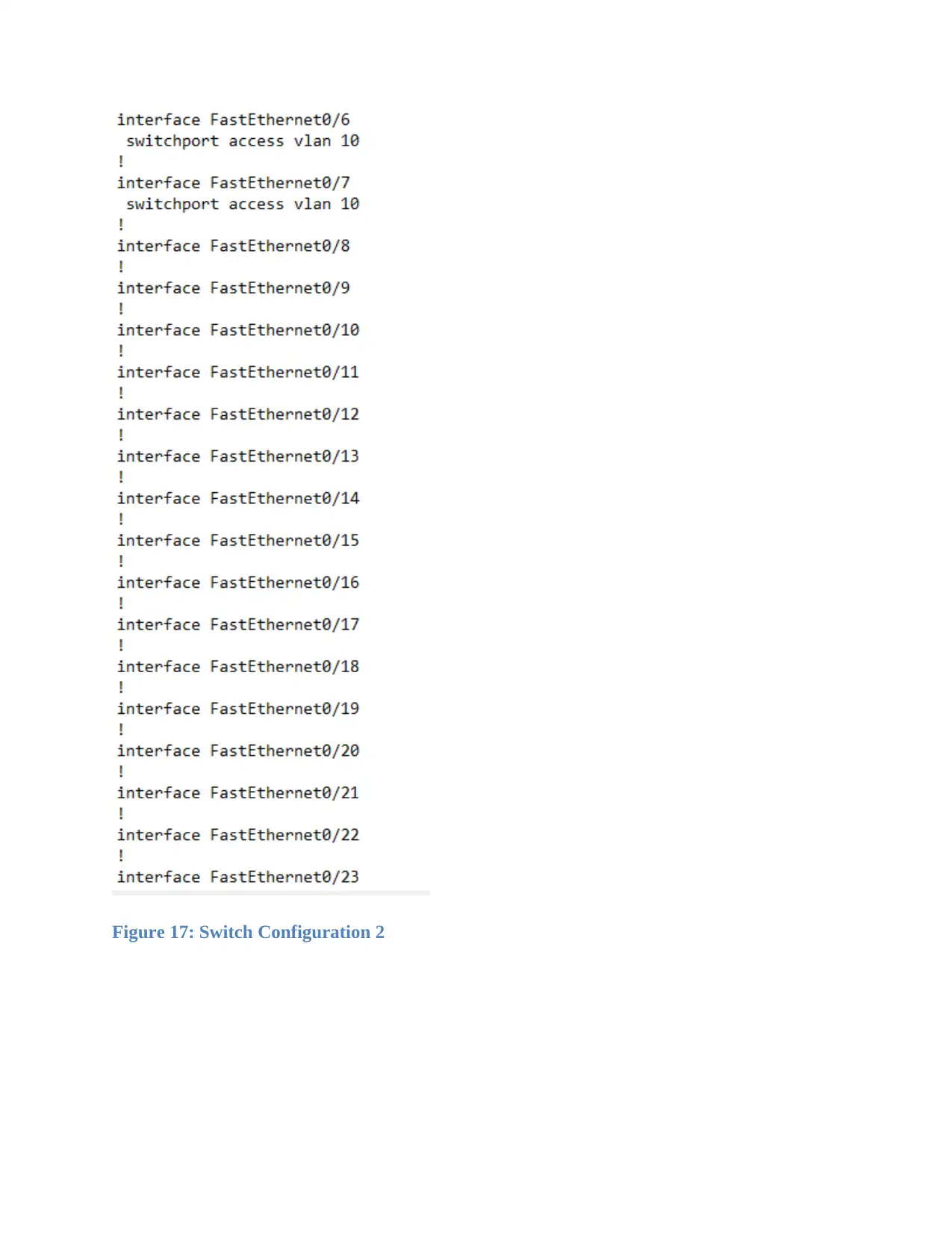
Figure 17: Switch Configuration 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
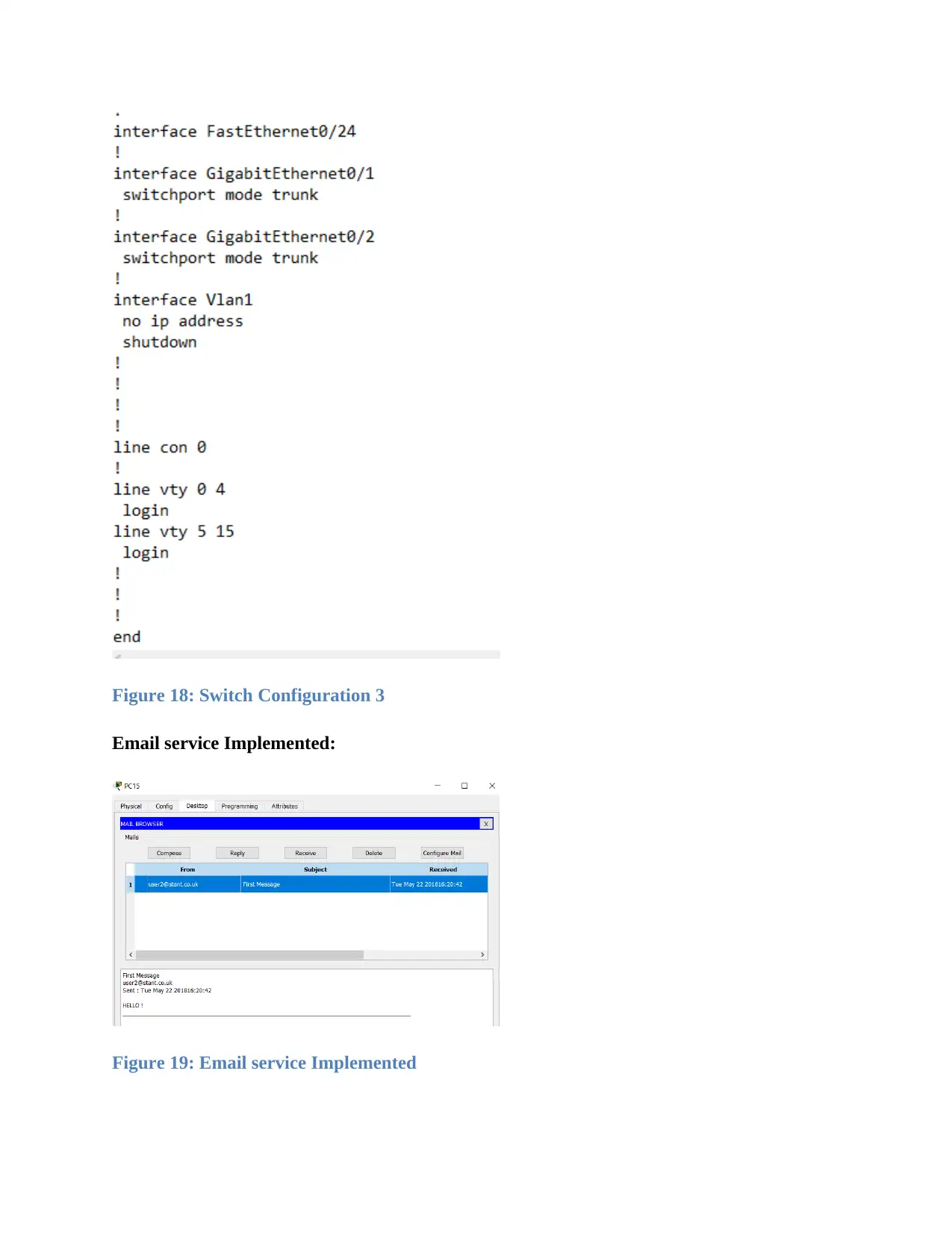
Figure 18: Switch Configuration 3
Email service Implemented:
Figure 19: Email service Implemented
Email service Implemented:
Figure 19: Email service Implemented
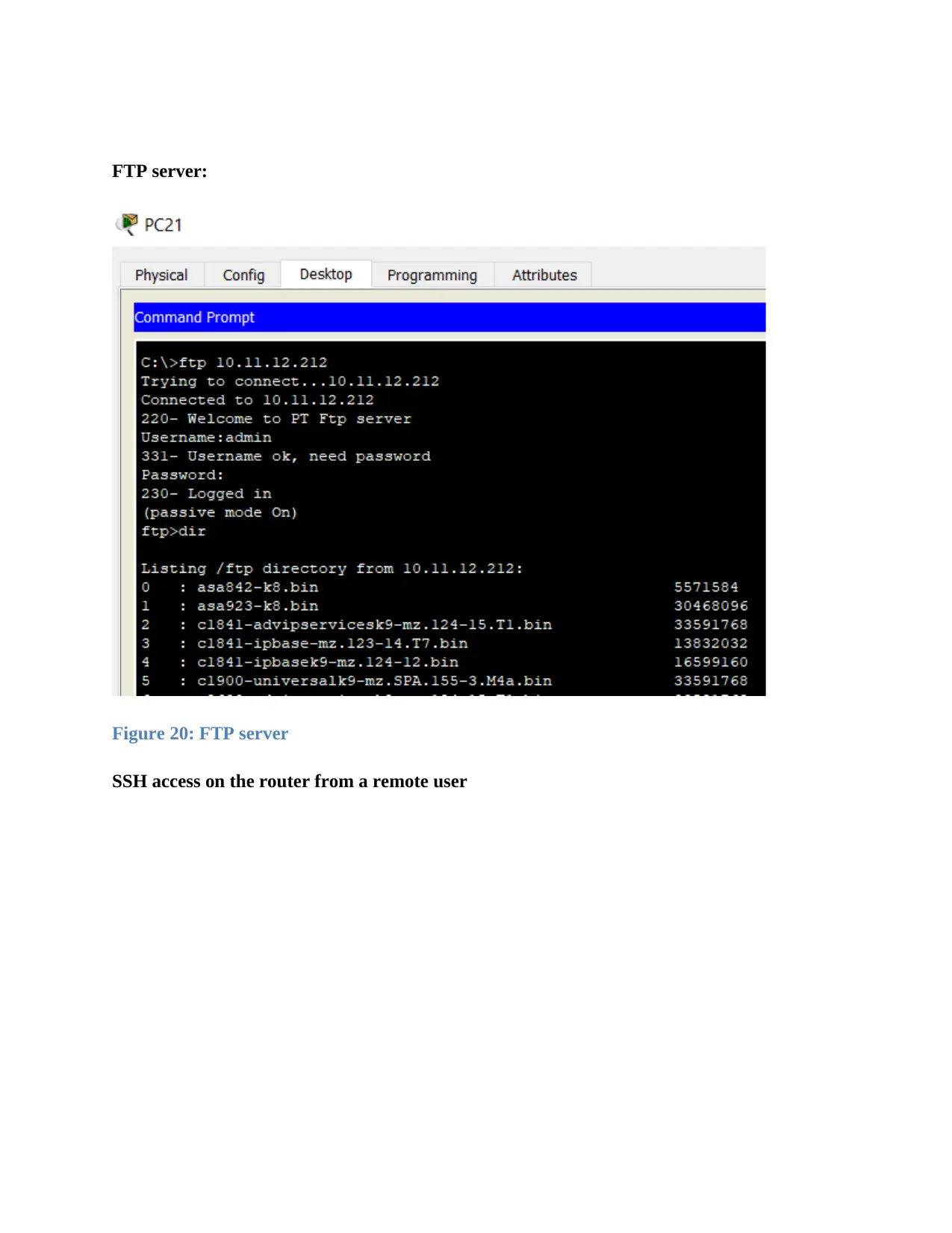
FTP server:
Figure 20: FTP server
SSH access on the router from a remote user
Figure 20: FTP server
SSH access on the router from a remote user
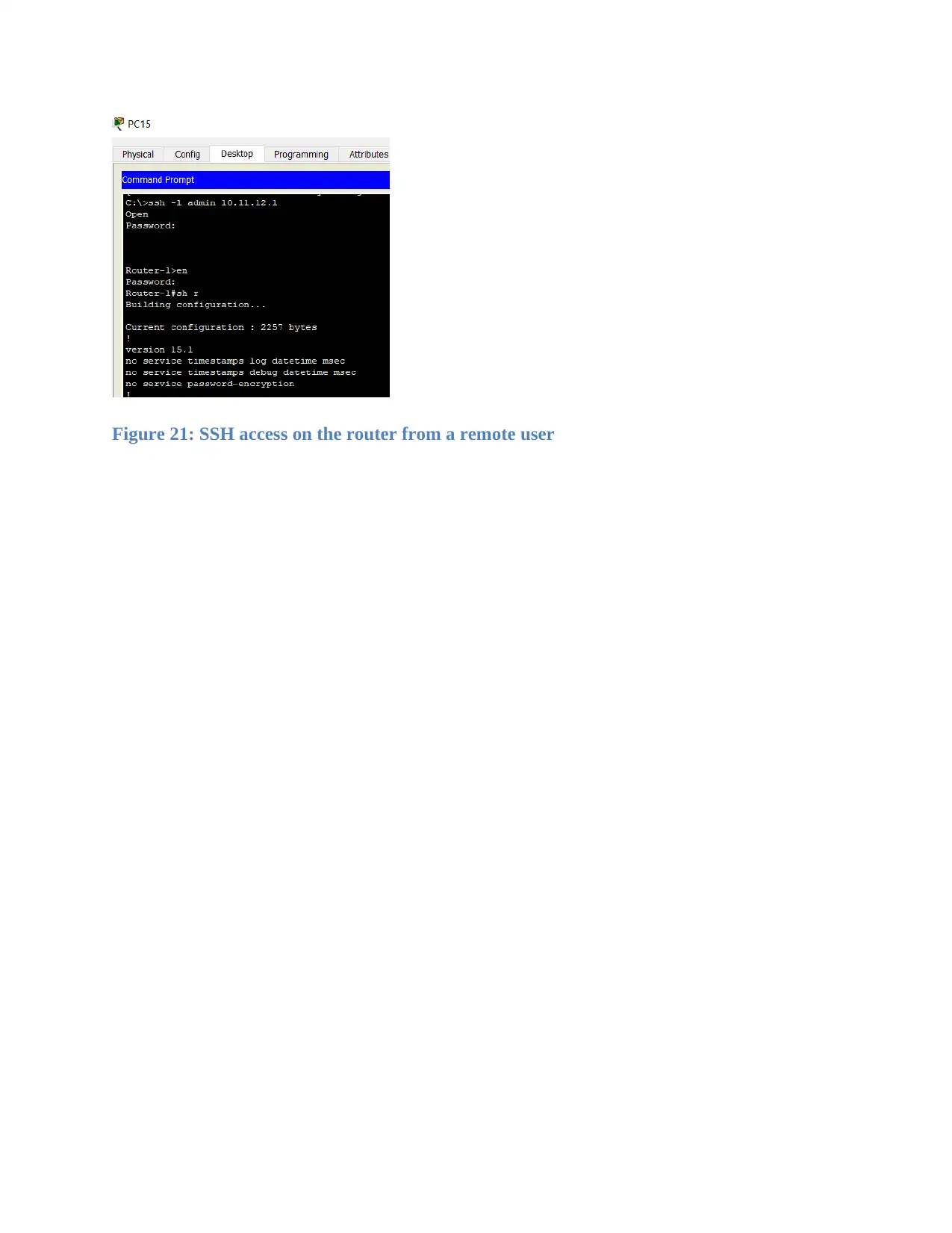
Figure 21: SSH access on the router from a remote user
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

3.2 implement network security on a LAN
Here, I have designed the LAN network for the given organization. For the LAN network
security, I have implemented VLANs and ACL on the network that provide high-level security
during communication and information sharing.
(VLANs):
Here, I even have designed the VLANs which achieved the wireless network for the safety
motive within the Association LAN. It accomplishes the community visitors and does no longer
allow site visitors transmission among community because it violates community security.
VLANs is implemented on the communication device such as a router, switch for the secure
communication. It expended the dangerous site visitors because of protection reason
(Rouse,2015).
Figure 22: VLAN configuration over switch
Access Control List (ACL):
ACL is managing the traffic on the network boundaries. It gives permission to a person to access
the network. With the help of permission, it also denies and permits the network traffic. Permit
Here, I have designed the LAN network for the given organization. For the LAN network
security, I have implemented VLANs and ACL on the network that provide high-level security
during communication and information sharing.
(VLANs):
Here, I even have designed the VLANs which achieved the wireless network for the safety
motive within the Association LAN. It accomplishes the community visitors and does no longer
allow site visitors transmission among community because it violates community security.
VLANs is implemented on the communication device such as a router, switch for the secure
communication. It expended the dangerous site visitors because of protection reason
(Rouse,2015).
Figure 22: VLAN configuration over switch
Access Control List (ACL):
ACL is managing the traffic on the network boundaries. It gives permission to a person to access
the network. With the help of permission, it also denies and permits the network traffic. Permit
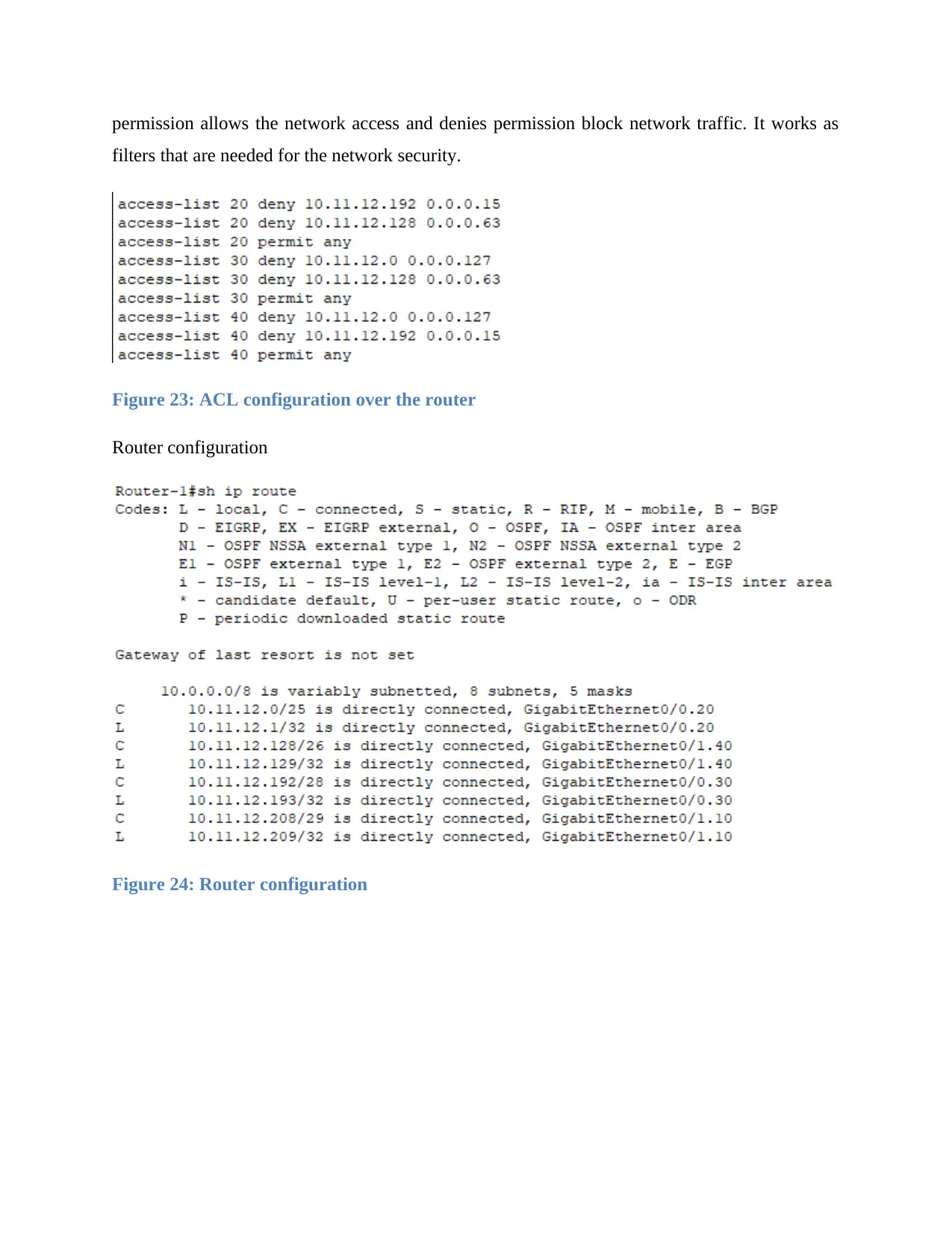
permission allows the network access and denies permission block network traffic. It works as
filters that are needed for the network security.
Figure 23: ACL configuration over the router
Router configuration
Figure 24: Router configuration
filters that are needed for the network security.
Figure 23: ACL configuration over the router
Router configuration
Figure 24: Router configuration
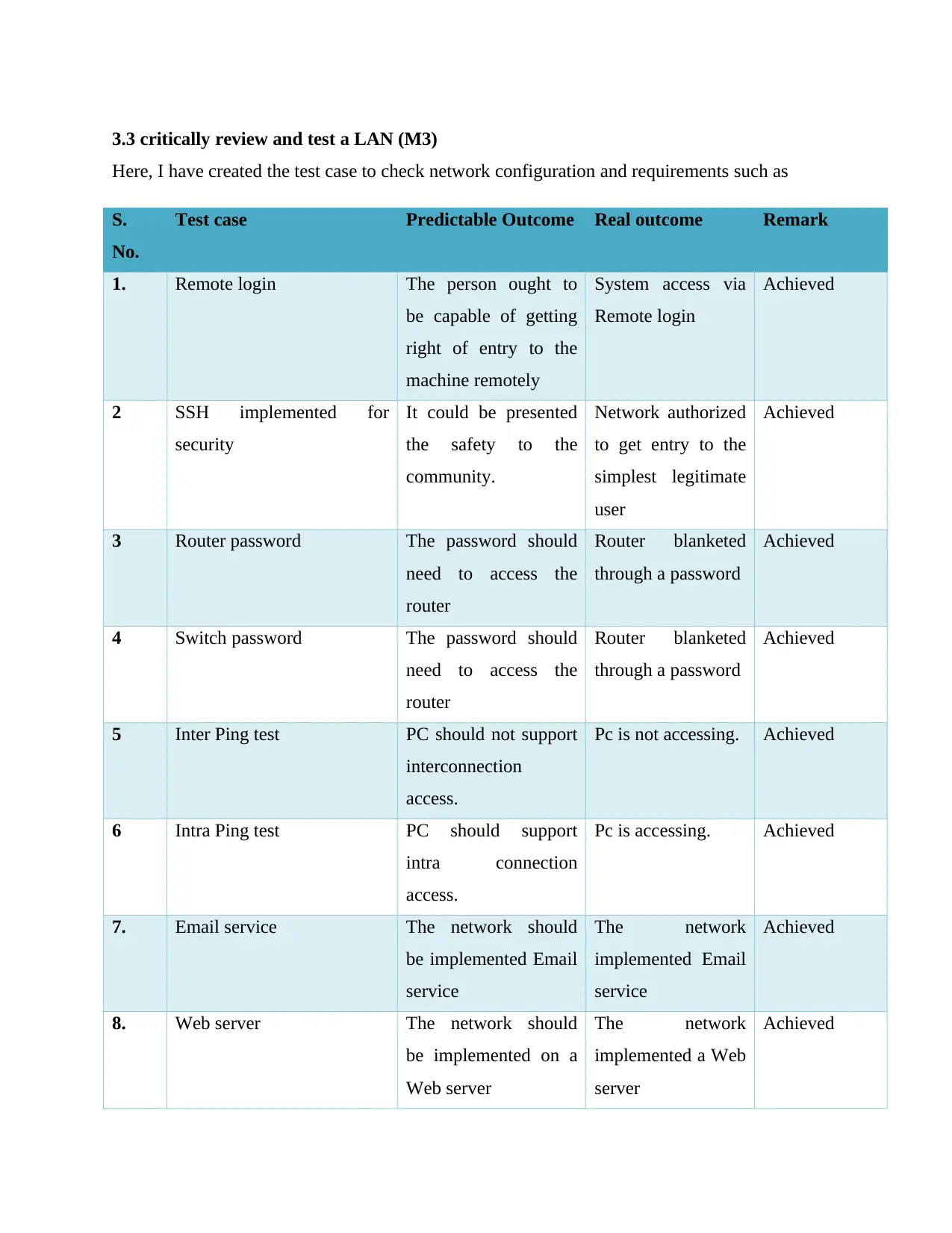
3.3 critically review and test a LAN (M3)
Here, I have created the test case to check network configuration and requirements such as
S.
No.
Test case Predictable Outcome Real outcome Remark
1. Remote login The person ought to
be capable of getting
right of entry to the
machine remotely
System access via
Remote login
Achieved
2 SSH implemented for
security
It could be presented
the safety to the
community.
Network authorized
to get entry to the
simplest legitimate
user
Achieved
3 Router password The password should
need to access the
router
Router blanketed
through a password
Achieved
4 Switch password The password should
need to access the
router
Router blanketed
through a password
Achieved
5 Inter Ping test PC should not support
interconnection
access.
Pc is not accessing. Achieved
6 Intra Ping test PC should support
intra connection
access.
Pc is accessing. Achieved
7. Email service The network should
be implemented Email
service
The network
implemented Email
service
Achieved
8. Web server The network should
be implemented on a
Web server
The network
implemented a Web
server
Achieved
Here, I have created the test case to check network configuration and requirements such as
S.
No.
Test case Predictable Outcome Real outcome Remark
1. Remote login The person ought to
be capable of getting
right of entry to the
machine remotely
System access via
Remote login
Achieved
2 SSH implemented for
security
It could be presented
the safety to the
community.
Network authorized
to get entry to the
simplest legitimate
user
Achieved
3 Router password The password should
need to access the
router
Router blanketed
through a password
Achieved
4 Switch password The password should
need to access the
router
Router blanketed
through a password
Achieved
5 Inter Ping test PC should not support
interconnection
access.
Pc is not accessing. Achieved
6 Intra Ping test PC should support
intra connection
access.
Pc is accessing. Achieved
7. Email service The network should
be implemented Email
service
The network
implemented Email
service
Achieved
8. Web server The network should
be implemented on a
Web server
The network
implemented a Web
server
Achieved
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
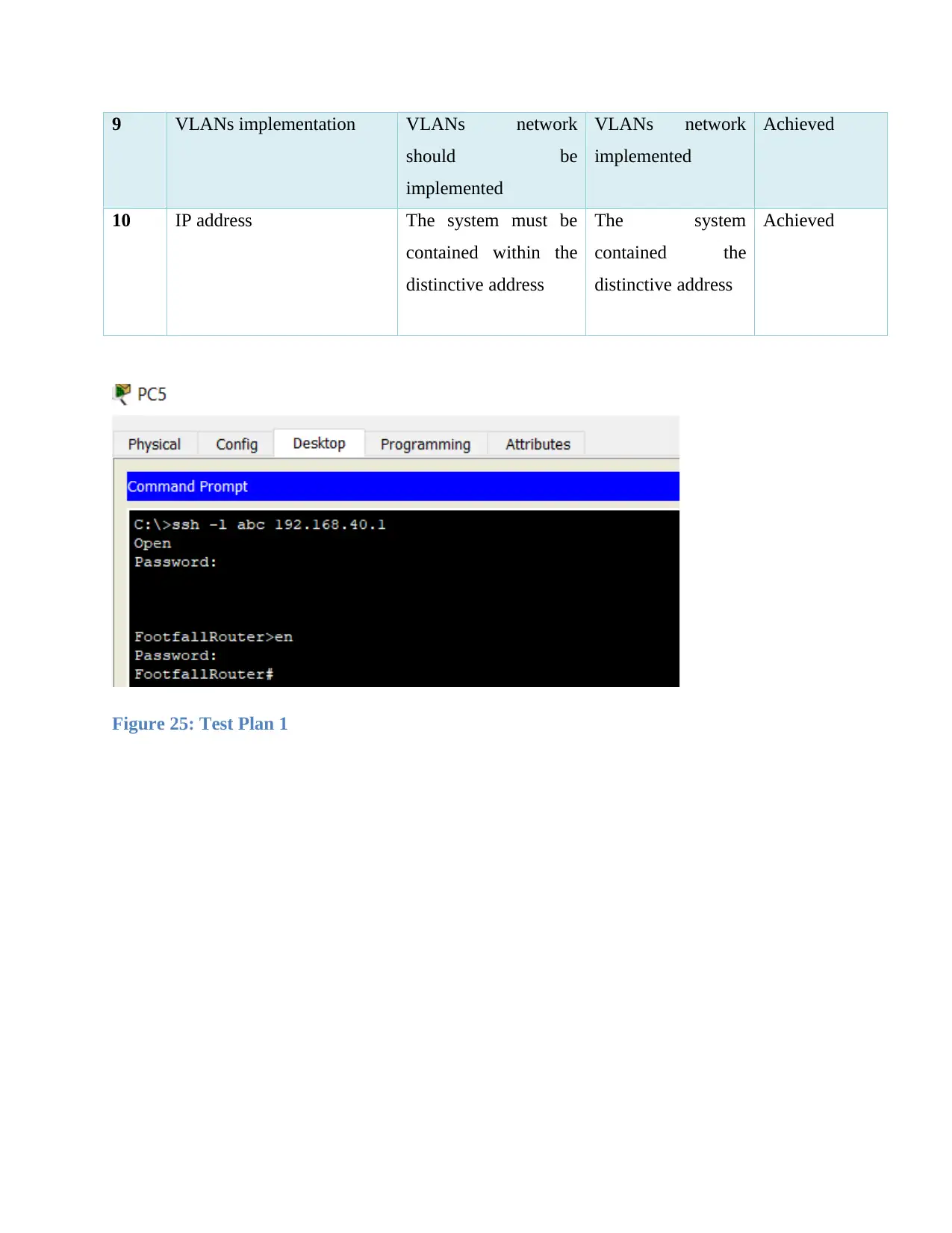
9 VLANs implementation VLANs network
should be
implemented
VLANs network
implemented
Achieved
10 IP address The system must be
contained within the
distinctive address
The system
contained the
distinctive address
Achieved
Figure 25: Test Plan 1
should be
implemented
VLANs network
implemented
Achieved
10 IP address The system must be
contained within the
distinctive address
The system
contained the
distinctive address
Achieved
Figure 25: Test Plan 1
Figure 26: Test Plan 2
Figure 27: Test Plan 3
Figure 27: Test Plan 3
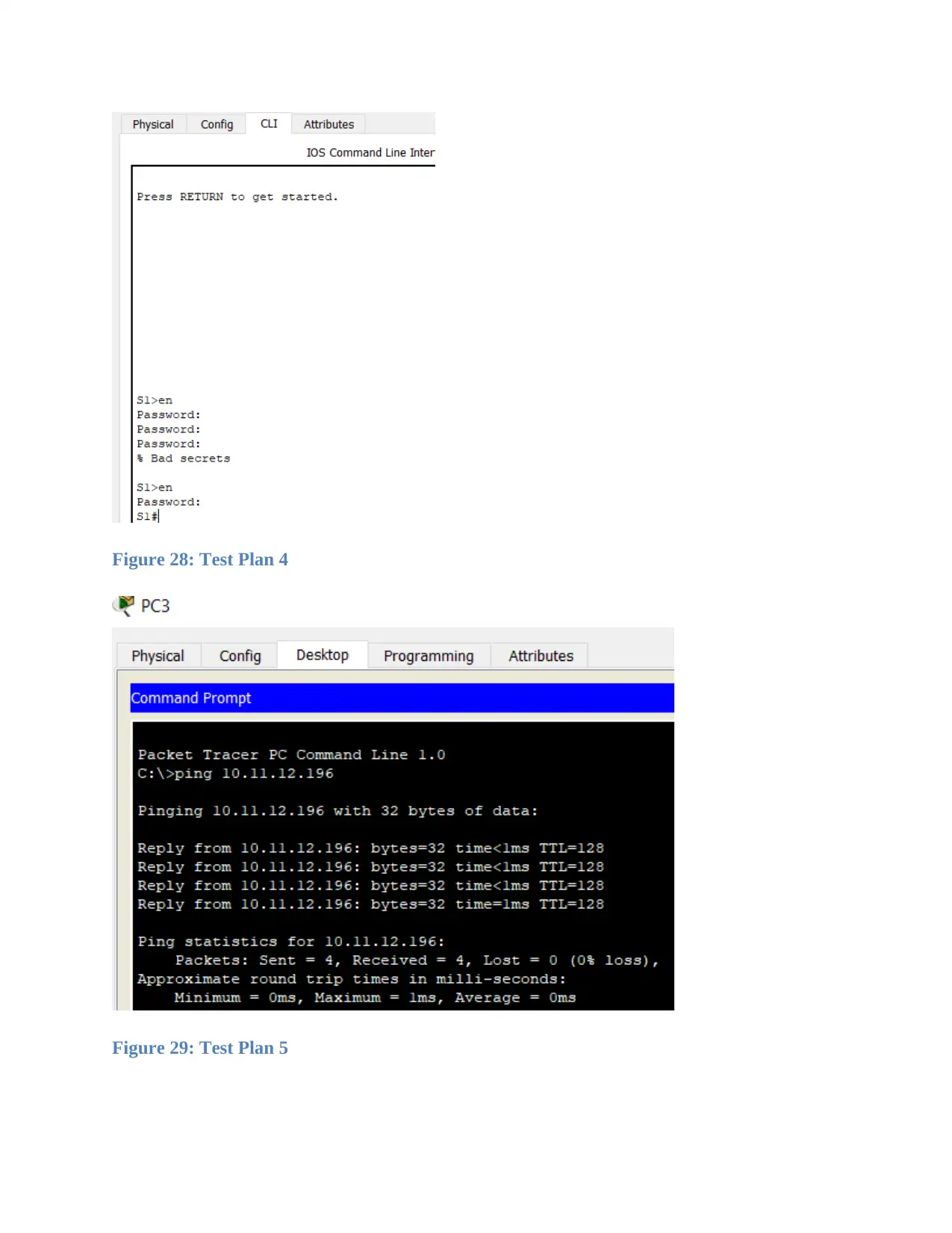
Figure 28: Test Plan 4
Figure 29: Test Plan 5
Figure 29: Test Plan 5
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
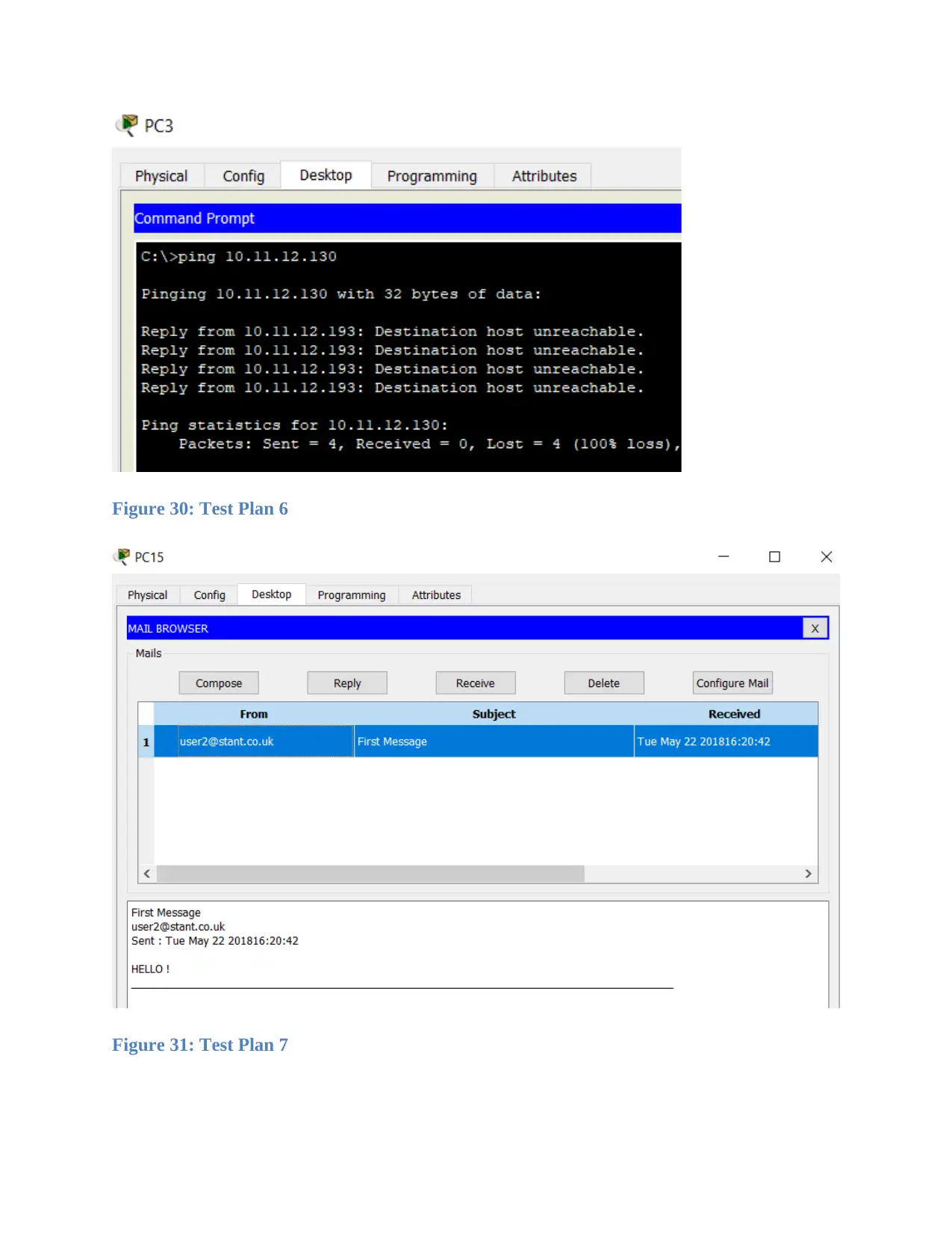
Figure 30: Test Plan 6
Figure 31: Test Plan 7
Figure 31: Test Plan 7
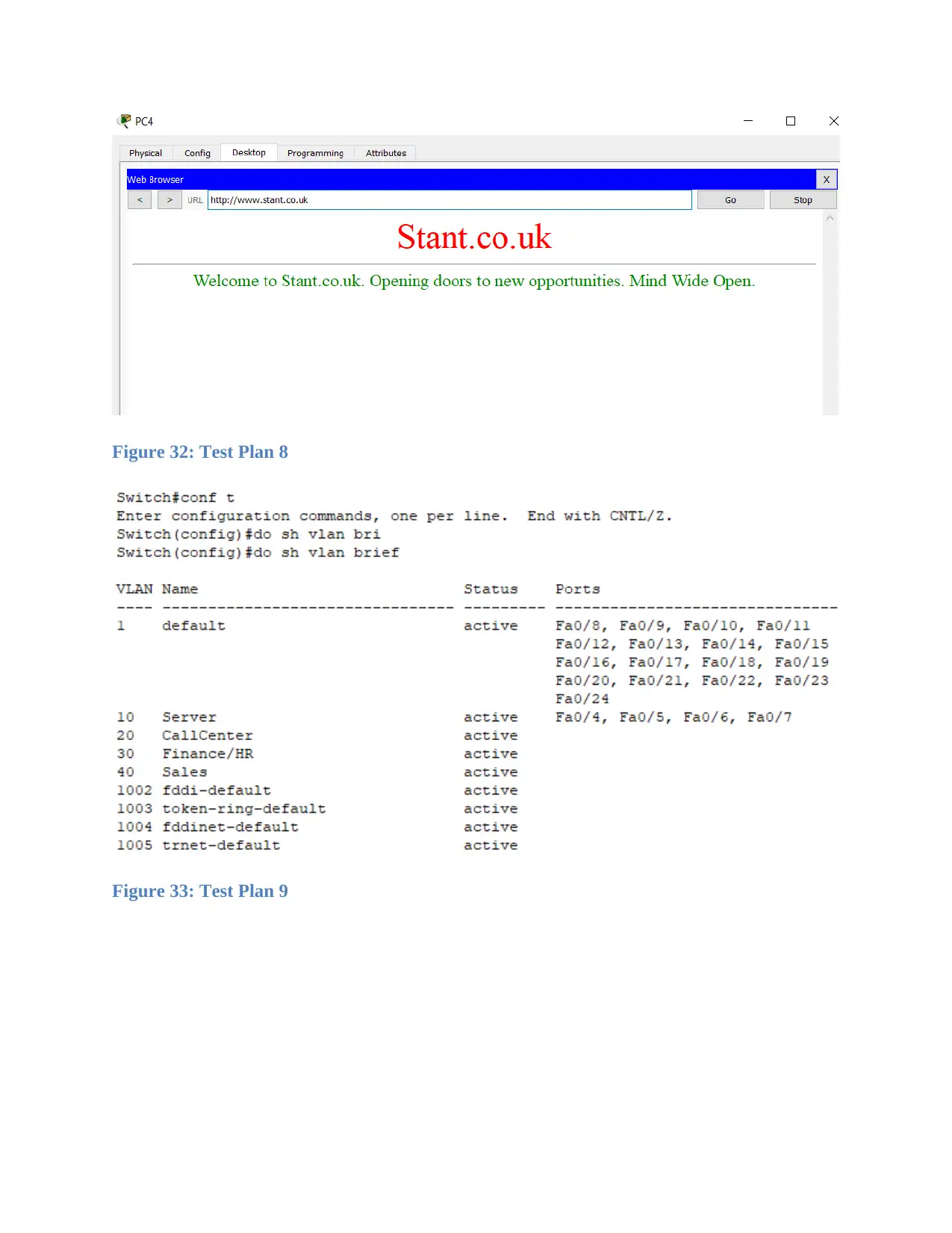
Figure 32: Test Plan 8
Figure 33: Test Plan 9
Figure 33: Test Plan 9
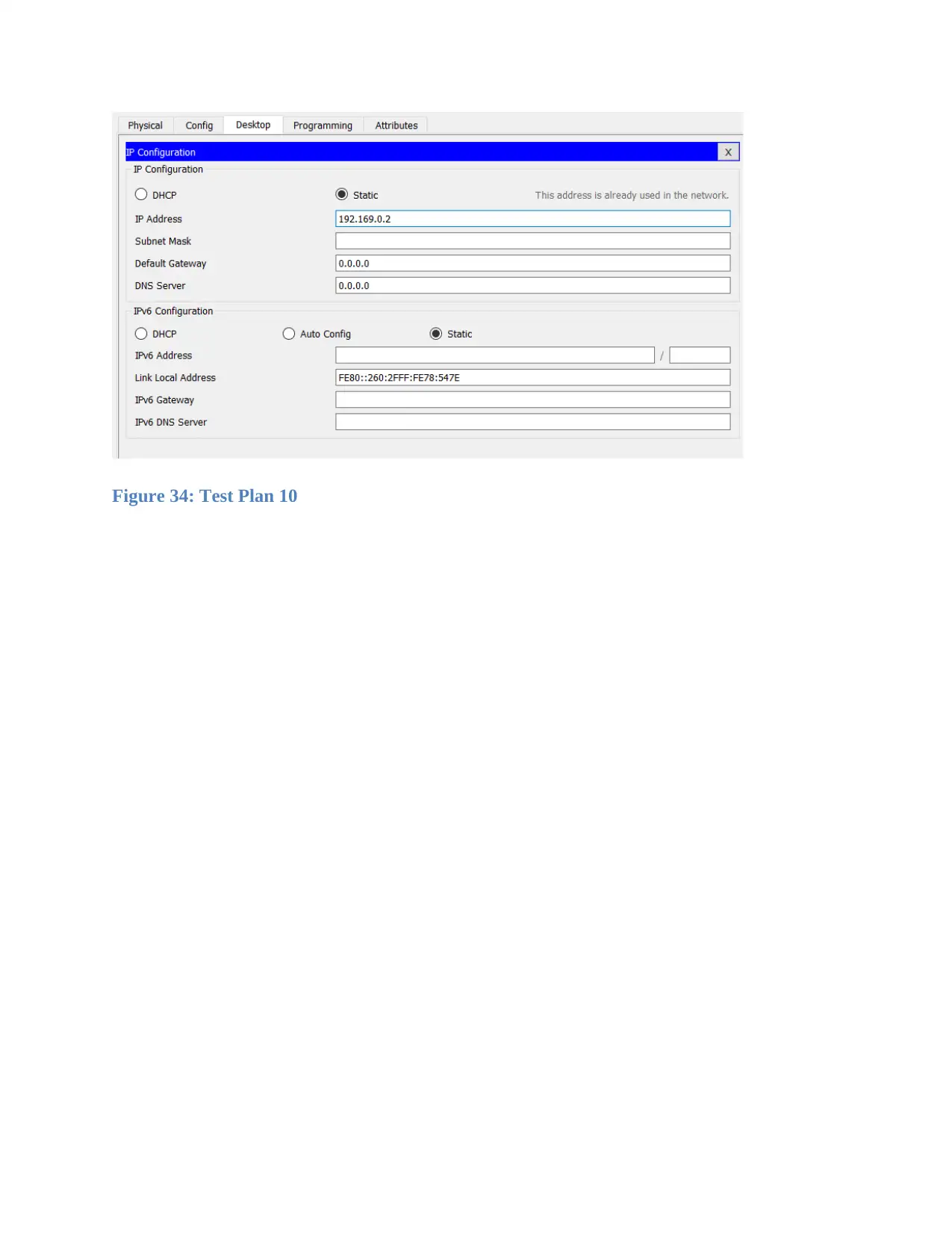
Figure 34: Test Plan 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

LO4: Be able to manage LAN infrastructures
4.1 There are many tools available in the market to monitor the network, describe and
choose one showing the usefulness of this tool to monitor and troubleshoot a LAN? [P4.1]
Ans. In the market, several tools are available which have distinguished feature one with the
other. Some of the tools are:
Zabbix
Datadog
Incinga:
Solar wind
Connect wise
Logic monitor
Paessler PRTG
Solar wind: in energy and retail industry it is very useful. It solves the problem of monitor the
remote location in detail. In the network dashboard, it should manage Wi-Fi network. Make
Heat Maps of Wifi Networks to stick point Wifi Dead Spots
Screen Hardware Health of all Servers, Firewalls, Routers, Switches, Desktops, workstations
and the sky is the limit from there. Ongoing Network and Net flow Monitoring for Critical
Network Components and Devices. Consequently Network Discovery and Scanning for
Wired and Wifi Computers and Devices. Support for Wide Array of OEM Vendors.
Conjecture and Capacity Planning. Rapidly Pinpoint Issues with Network Performance with
Net Path™ Critical Path representation include. Simple to Use Performance Dashboard to
Analyze Critical Data focus and ways over your system. Vigorous Alerting System with
choices for Simple/Complex Triggers.
For troubleshooting with the web interface solar winds NPM streamlines arrange
investigating with a Web interface that is LUCID (Logical, Useable, Adaptable, Interactive,
and Drill-down) enabling you to oversee by special case and spotlight on featured issues that
cross predefined edges and also modifying and seeing information in diagrams, tables, maps
(Computer Hope, 2018).
4.1 There are many tools available in the market to monitor the network, describe and
choose one showing the usefulness of this tool to monitor and troubleshoot a LAN? [P4.1]
Ans. In the market, several tools are available which have distinguished feature one with the
other. Some of the tools are:
Zabbix
Datadog
Incinga:
Solar wind
Connect wise
Logic monitor
Paessler PRTG
Solar wind: in energy and retail industry it is very useful. It solves the problem of monitor the
remote location in detail. In the network dashboard, it should manage Wi-Fi network. Make
Heat Maps of Wifi Networks to stick point Wifi Dead Spots
Screen Hardware Health of all Servers, Firewalls, Routers, Switches, Desktops, workstations
and the sky is the limit from there. Ongoing Network and Net flow Monitoring for Critical
Network Components and Devices. Consequently Network Discovery and Scanning for
Wired and Wifi Computers and Devices. Support for Wide Array of OEM Vendors.
Conjecture and Capacity Planning. Rapidly Pinpoint Issues with Network Performance with
Net Path™ Critical Path representation include. Simple to Use Performance Dashboard to
Analyze Critical Data focus and ways over your system. Vigorous Alerting System with
choices for Simple/Complex Triggers.
For troubleshooting with the web interface solar winds NPM streamlines arrange
investigating with a Web interface that is LUCID (Logical, Useable, Adaptable, Interactive,
and Drill-down) enabling you to oversee by special case and spotlight on featured issues that
cross predefined edges and also modifying and seeing information in diagrams, tables, maps
(Computer Hope, 2018).

4.2 Local Area Network is not immune from many attacks and threats produce a report to
improve security, reliability and performance. [P4.2]
In local area network if the system is not powerful then it will breach security easily on the
network. So our major concern is improving the security. If the performance of the system is not
as much as required then the user does not use the network for their work. Wired LAN is
providing better security than the wireless LAN. So to improve wired technology we should do
these things:
The network should always up-to-date
The network should be always physically secure
For authentication use 802.1X
Entire network should be in encrypted form
To encrypt server & PC use VPNs
Mapping and auditing should be performed on a regular basis
To improve the network infrastructure it is challenging for the data centre to become fast,
reliable & significant for this some of the principles are:
Deliver server farm application versatility, high accessibility and adaptation to
internal failure.
Secure server farm applications by giving movement assessment and security
approach implementation.
Achieve most extreme server farm application conveyance advancement and
quickening.
The network should be in load balancing condition
Replication links are created which are used as a backup
Virtual devices in the network are attached so they handle the request in high traffic
(Radware, 2013)
improve security, reliability and performance. [P4.2]
In local area network if the system is not powerful then it will breach security easily on the
network. So our major concern is improving the security. If the performance of the system is not
as much as required then the user does not use the network for their work. Wired LAN is
providing better security than the wireless LAN. So to improve wired technology we should do
these things:
The network should always up-to-date
The network should be always physically secure
For authentication use 802.1X
Entire network should be in encrypted form
To encrypt server & PC use VPNs
Mapping and auditing should be performed on a regular basis
To improve the network infrastructure it is challenging for the data centre to become fast,
reliable & significant for this some of the principles are:
Deliver server farm application versatility, high accessibility and adaptation to
internal failure.
Secure server farm applications by giving movement assessment and security
approach implementation.
Achieve most extreme server farm application conveyance advancement and
quickening.
The network should be in load balancing condition
Replication links are created which are used as a backup
Virtual devices in the network are attached so they handle the request in high traffic
(Radware, 2013)

4.3 Critically evaluate the performance of your network proposing a solution to improve
network performance in relation to server’s traffic. [P4.3, M3]
Ans. To improve the network performance we should do:
The user should be educated and involved
Use firewall by using antivirus on the start so the junk traffic can be minimized
Consume limited bandwidth because some user may consume five times bandwidth
and only deliver one-quarter of the total bandwidth consumption.
Get the application be arranged in prioritized to improve the performance.
Most of the people without understanding their network add access bandwidth to
improve the performance but this is the biggest mistake they do. So the information
should be understandable and only the required information is added
Use compression techniques so the bandwidth consumption may reduce because
when file are transferred if they are in the compressed format they pass fast on the
network.
The network should be adaptable to changes because when applications on the
network are increasing it should be carefully handled to improve performance
(Wolber, 2015).
network performance in relation to server’s traffic. [P4.3, M3]
Ans. To improve the network performance we should do:
The user should be educated and involved
Use firewall by using antivirus on the start so the junk traffic can be minimized
Consume limited bandwidth because some user may consume five times bandwidth
and only deliver one-quarter of the total bandwidth consumption.
Get the application be arranged in prioritized to improve the performance.
Most of the people without understanding their network add access bandwidth to
improve the performance but this is the biggest mistake they do. So the information
should be understandable and only the required information is added
Use compression techniques so the bandwidth consumption may reduce because
when file are transferred if they are in the compressed format they pass fast on the
network.
The network should be adaptable to changes because when applications on the
network are increasing it should be carefully handled to improve performance
(Wolber, 2015).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Conclusion
Here, I have designed the LAN network on the Cisco Packet Tracer platform with the given
requirements. It provides the communication and data sharing on the network. It uses network
device, technology and methodology with the safe, reliable, and fixable format. Here I have
designed report with four sections.
In the reviews, I have nicely-defined LAN community and their kind, devices, cables, resource,
and technologies, which are essential for the given organization. The system and user
requirement are fulfilled in the course of the network designed and evaluated the sources of the
community. Standards of Security are instigated at the given LAN community and looked at the
going for walks of LAN community. In the give up, monitoring and troubleshooting
methodology is described that defined reliability, performance, and protection situation and
considered the performance of LAN community.
Here, I have designed the LAN network on the Cisco Packet Tracer platform with the given
requirements. It provides the communication and data sharing on the network. It uses network
device, technology and methodology with the safe, reliable, and fixable format. Here I have
designed report with four sections.
In the reviews, I have nicely-defined LAN community and their kind, devices, cables, resource,
and technologies, which are essential for the given organization. The system and user
requirement are fulfilled in the course of the network designed and evaluated the sources of the
community. Standards of Security are instigated at the given LAN community and looked at the
going for walks of LAN community. In the give up, monitoring and troubleshooting
methodology is described that defined reliability, performance, and protection situation and
considered the performance of LAN community.

Reference:
Firewall (2015). LAN Network Topologies. [online] Available at:
http://www.firewall.cx/networking-topics/general-networking/103-network-topologies.html
[Accessed 24 May 2018].
Differencebetween (2018). Different Types of Network Topologies [online] Available at:
http://www.differencebetween.info/different-types-of-network-topologies [Accessed 24 May
2018].
Slattery, T. (2013). QoS in the LAN? You're Kidding!. [online] Nojitter Available at:
https://www.nojitter.com/post/240147232/qos-in-the-lan-youre-kidding [Accessed 24 May
2018].
Ubiquiti (2017). Intro to Networking [online] Available at:
https://help.ubnt.com/hc/en-us/articles/115007129507-Intro-to-Networking-Hierarchical-
Network-Topology [Accessed 24 May 2018].
Sparrow, P. (2014). Hybrid Topology: Advantages and Disadvantages of Hybrid Topology.
[online] Ianswer4u.com. Available at: https://www.ianswer4u.com/2012/05/hybrid-topology-
advantages-and.html [Accessed 24 May 2018].
Arstechnica (2002). what does 192.168.0.1/32 mean? [online] Available at:
https://arstechnica.com/civis/viewtopic.php?t=751834 [Accessed 24 May 2018].
Differencebetween (2011). Difference Between WPA and WPA2 [online] Available at:
http://www.differencebetween.net/technology/difference-between-wpa-and-wpa2/ [Accessed
24 May 2018].
Petcu, D., Iancu, B., Peculea, A., Dadarlat, V. and Cebuc, E., (2013), Integrating Cisco
Packet Tracer with Moodle platform: Support for teaching and automatic evaluation.
In Networking in Education and Research, 2013 RoEduNet International Conference 12th
Edition (pp. 1-6). IEEE.
Rouse, M. (2015). What is virtual LAN (VLAN)? [online] Available at:
https://searchnetworking.techtarget.com/definition/virtual-LAN [Accessed 24 May 2018].
Computer Hope, (2018). Basic network troubleshooting. [online] Computerhope.com.
Available at: https://www.computerhope.com/issues/ch000445.htm [Accessed 24 May 2018].
Radware, Y. (2013). 5 Ways to Improve Your Network Infrastructure’s Performance.
[online] Available at:
Firewall (2015). LAN Network Topologies. [online] Available at:
http://www.firewall.cx/networking-topics/general-networking/103-network-topologies.html
[Accessed 24 May 2018].
Differencebetween (2018). Different Types of Network Topologies [online] Available at:
http://www.differencebetween.info/different-types-of-network-topologies [Accessed 24 May
2018].
Slattery, T. (2013). QoS in the LAN? You're Kidding!. [online] Nojitter Available at:
https://www.nojitter.com/post/240147232/qos-in-the-lan-youre-kidding [Accessed 24 May
2018].
Ubiquiti (2017). Intro to Networking [online] Available at:
https://help.ubnt.com/hc/en-us/articles/115007129507-Intro-to-Networking-Hierarchical-
Network-Topology [Accessed 24 May 2018].
Sparrow, P. (2014). Hybrid Topology: Advantages and Disadvantages of Hybrid Topology.
[online] Ianswer4u.com. Available at: https://www.ianswer4u.com/2012/05/hybrid-topology-
advantages-and.html [Accessed 24 May 2018].
Arstechnica (2002). what does 192.168.0.1/32 mean? [online] Available at:
https://arstechnica.com/civis/viewtopic.php?t=751834 [Accessed 24 May 2018].
Differencebetween (2011). Difference Between WPA and WPA2 [online] Available at:
http://www.differencebetween.net/technology/difference-between-wpa-and-wpa2/ [Accessed
24 May 2018].
Petcu, D., Iancu, B., Peculea, A., Dadarlat, V. and Cebuc, E., (2013), Integrating Cisco
Packet Tracer with Moodle platform: Support for teaching and automatic evaluation.
In Networking in Education and Research, 2013 RoEduNet International Conference 12th
Edition (pp. 1-6). IEEE.
Rouse, M. (2015). What is virtual LAN (VLAN)? [online] Available at:
https://searchnetworking.techtarget.com/definition/virtual-LAN [Accessed 24 May 2018].
Computer Hope, (2018). Basic network troubleshooting. [online] Computerhope.com.
Available at: https://www.computerhope.com/issues/ch000445.htm [Accessed 24 May 2018].
Radware, Y. (2013). 5 Ways to Improve Your Network Infrastructure’s Performance.
[online] Available at:

https://blog.radware.com/applicationdelivery/applicationaccelerationoptimization/2013/06/5-
ways-to-improve-your-network-infrastructures-performance/ [Accessed 24 May 2018].
Wolber, A. (2015). How to potentially increase the performance of your network. [online]
Available at: https://www.techrepublic.com/article/how-to-potentially-increase-the-
performance-of-your-network/ [Accessed 24 May 2018].
ways-to-improve-your-network-infrastructures-performance/ [Accessed 24 May 2018].
Wolber, A. (2015). How to potentially increase the performance of your network. [online]
Available at: https://www.techrepublic.com/article/how-to-potentially-increase-the-
performance-of-your-network/ [Accessed 24 May 2018].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Appendix
1 out of 44
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





