Local Area Networking Technology: Design, Implementation, and Management
VerifiedAdded on 2024/05/20
|44
|8567
|496
AI Summary
This project explores the fundamentals of Local Area Networking (LAN) technologies, encompassing design, implementation, and management. It delves into various LAN standards, including IEEE 802, VLANs, and STP, and analyzes traffic-intensive services and their performance. The project also examines security concerns and recommends strategies to enhance network security, reliability, and performance. Through practical implementation using Cisco Packet Tracer, the report demonstrates the configuration of a secure and scalable LAN infrastructure for a hypothetical organization, 'Footfall Field Marketing Ltd.' The project concludes with a critical evaluation of the implemented LAN, highlighting its strengths and areas for improvement.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Local Area Networking
Technology
Technology
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
INTRODUCTION..........................................................................................................................3
LO1 Understand the impact of LAN technologies......................................................................4
A.C 1.1 critically evaluates different LAN technologies.........................................................4
A.C 1.2 critically analyze traffic intensive services and their performance.........................12
A.C 1.3 Discuss LAN concerns and makes recommendations to sustain network..............14
M1. Identify and apply strategies to find appropriate solutions.........................................15
LO2 Be able to design LAN infrastructures..............................................................................16
A.C 2.1 Designs a LAN infrastructure for the company which will facilitate all of their
requirements........................................................................................................................16
A.C 2.2 critically evaluates the suitability of LAN component.............................................19
LO3 Be able to implement LAN infrastructures.......................................................................20
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement........20
A.C 3.2 Implement network securities on a LAN.................................................................25
A.C 3.3 critically reviews and tests a LAN............................................................................29
M2. Select/ design and apply appropriate methods/ techniques.......................................32
M3. Present and communicate appropriate findings..........................................................32
D2. Take responsibility for managing and organizing activities...........................................33
D3. Demonstrate convergent, lateral and creative thinking...............................................33
LO4. Be able to manage LAN infrastructures...........................................................................34
A.C 4.1 critically discusses how this LAN infrastructure will be monitored and managed
(via troubleshooting)............................................................................................................34
A.C 4.2 Resolve LAN issues to improve security, reliability, and performance.......................35
A.C 4.3 critically evaluates the performance of a LAN.........................................................37
D1. Use critical reflection to evaluate own work and justify the valid conclusion..............38
1
INTRODUCTION..........................................................................................................................3
LO1 Understand the impact of LAN technologies......................................................................4
A.C 1.1 critically evaluates different LAN technologies.........................................................4
A.C 1.2 critically analyze traffic intensive services and their performance.........................12
A.C 1.3 Discuss LAN concerns and makes recommendations to sustain network..............14
M1. Identify and apply strategies to find appropriate solutions.........................................15
LO2 Be able to design LAN infrastructures..............................................................................16
A.C 2.1 Designs a LAN infrastructure for the company which will facilitate all of their
requirements........................................................................................................................16
A.C 2.2 critically evaluates the suitability of LAN component.............................................19
LO3 Be able to implement LAN infrastructures.......................................................................20
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement........20
A.C 3.2 Implement network securities on a LAN.................................................................25
A.C 3.3 critically reviews and tests a LAN............................................................................29
M2. Select/ design and apply appropriate methods/ techniques.......................................32
M3. Present and communicate appropriate findings..........................................................32
D2. Take responsibility for managing and organizing activities...........................................33
D3. Demonstrate convergent, lateral and creative thinking...............................................33
LO4. Be able to manage LAN infrastructures...........................................................................34
A.C 4.1 critically discusses how this LAN infrastructure will be monitored and managed
(via troubleshooting)............................................................................................................34
A.C 4.2 Resolve LAN issues to improve security, reliability, and performance.......................35
A.C 4.3 critically evaluates the performance of a LAN.........................................................37
D1. Use critical reflection to evaluate own work and justify the valid conclusion..............38
1

Conclusion................................................................................................................................40
References................................................................................................................................41
List of Figures
Figure 1 IEEE 802........................................................................................................................4
Figure 2 IEEE 802.11...................................................................................................................5
Figure 3 STP................................................................................................................................5
Figure 4 VLAN.............................................................................................................................6
Figure 5 VTP...............................................................................................................................6
Figure 6 Standby routing............................................................................................................7
Figure 7 Ether channel...............................................................................................................7
Figure 8 ISL.................................................................................................................................8
Figure 9 DHCP.............................................................................................................................8
Figure 10 Layer 2 switches.........................................................................................................9
Figure 11 Layer 3 switches.........................................................................................................9
Figure 12 Layer 4 switches.......................................................................................................10
Figure 13 Wireless devices.......................................................................................................10
Figure 14 Network interfaces...................................................................................................11
Figure 15 Client devices...........................................................................................................11
Figure 16 IP precedence...........................................................................................................12
Figure 17 Design view of an arganization................................................................................16
Figure 18 Router 0 configuration.............................................................................................23
Figure 19 DNS server of the company.....................................................................................24
Figure 20 Network diagram on Cisco Packet tracer.................................................................24
Figure 21 Router 1 configuartion.............................................................................................28
Figure 22 Test case 1................................................................................................................30
Figure 23 Test case 2................................................................................................................30
Figure 24 Test case 3................................................................................................................31
Figure 25 Test case 4................................................................................................................31
Figure 26 Test case 5................................................................................................................32
List of Tables
2
References................................................................................................................................41
List of Figures
Figure 1 IEEE 802........................................................................................................................4
Figure 2 IEEE 802.11...................................................................................................................5
Figure 3 STP................................................................................................................................5
Figure 4 VLAN.............................................................................................................................6
Figure 5 VTP...............................................................................................................................6
Figure 6 Standby routing............................................................................................................7
Figure 7 Ether channel...............................................................................................................7
Figure 8 ISL.................................................................................................................................8
Figure 9 DHCP.............................................................................................................................8
Figure 10 Layer 2 switches.........................................................................................................9
Figure 11 Layer 3 switches.........................................................................................................9
Figure 12 Layer 4 switches.......................................................................................................10
Figure 13 Wireless devices.......................................................................................................10
Figure 14 Network interfaces...................................................................................................11
Figure 15 Client devices...........................................................................................................11
Figure 16 IP precedence...........................................................................................................12
Figure 17 Design view of an arganization................................................................................16
Figure 18 Router 0 configuration.............................................................................................23
Figure 19 DNS server of the company.....................................................................................24
Figure 20 Network diagram on Cisco Packet tracer.................................................................24
Figure 21 Router 1 configuartion.............................................................................................28
Figure 22 Test case 1................................................................................................................30
Figure 23 Test case 2................................................................................................................30
Figure 24 Test case 3................................................................................................................31
Figure 25 Test case 4................................................................................................................31
Figure 26 Test case 5................................................................................................................32
List of Tables
2

Table 1 Test cases.....................................................................................................................33
INTRODUCTION
The purpose of this project is to understand the concept of LAN technologies. This project
will help to learn the LAN technology in depth and the designing of network infrastructure
will take place. The requirements of LAN network will be understood and identified in this
project. In the project, I will learn how to implement a secure network according to the
requirement. Also, the network designed should be scalable for the company. By the help of
this project, various network technologies will be understood that are IEEE 802 standards of
LAN, VLAN, ether channel, VTP, DHCP, LAN hardware and various security
recommendations. In this project, I will also analyze traffic intensive interfaces, various LAN
concerns, and LAN performance.
In this report, I will learn the methodologies to secure the data from unauthorized access.
Data or information of an organization is important and needs to be secured. I will also test
the infrastructure of LAN implemented and review it.
3
INTRODUCTION
The purpose of this project is to understand the concept of LAN technologies. This project
will help to learn the LAN technology in depth and the designing of network infrastructure
will take place. The requirements of LAN network will be understood and identified in this
project. In the project, I will learn how to implement a secure network according to the
requirement. Also, the network designed should be scalable for the company. By the help of
this project, various network technologies will be understood that are IEEE 802 standards of
LAN, VLAN, ether channel, VTP, DHCP, LAN hardware and various security
recommendations. In this project, I will also analyze traffic intensive interfaces, various LAN
concerns, and LAN performance.
In this report, I will learn the methodologies to secure the data from unauthorized access.
Data or information of an organization is important and needs to be secured. I will also test
the infrastructure of LAN implemented and review it.
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
LO1 Understand the impact of LAN technologies
A.C 1.1 critically evaluates different LAN technologies
Local area network
The Local network is the sort of the system, which incorporates gathering of a PC
framework, diverse gadgets, and so forth. The LAN network is utilized to exchange the
information and data starting with one end then onto the next end with no issue. This
system is utilized by various organization, office, universities or business. The setup of this
system is simple and the man preferred standpoint of this system is that it diminishes the
cost of the system and it incorporates least segment look at then different systems. Be that
as it may, the negative purpose of LAN organizes that is utilized for the just little region.
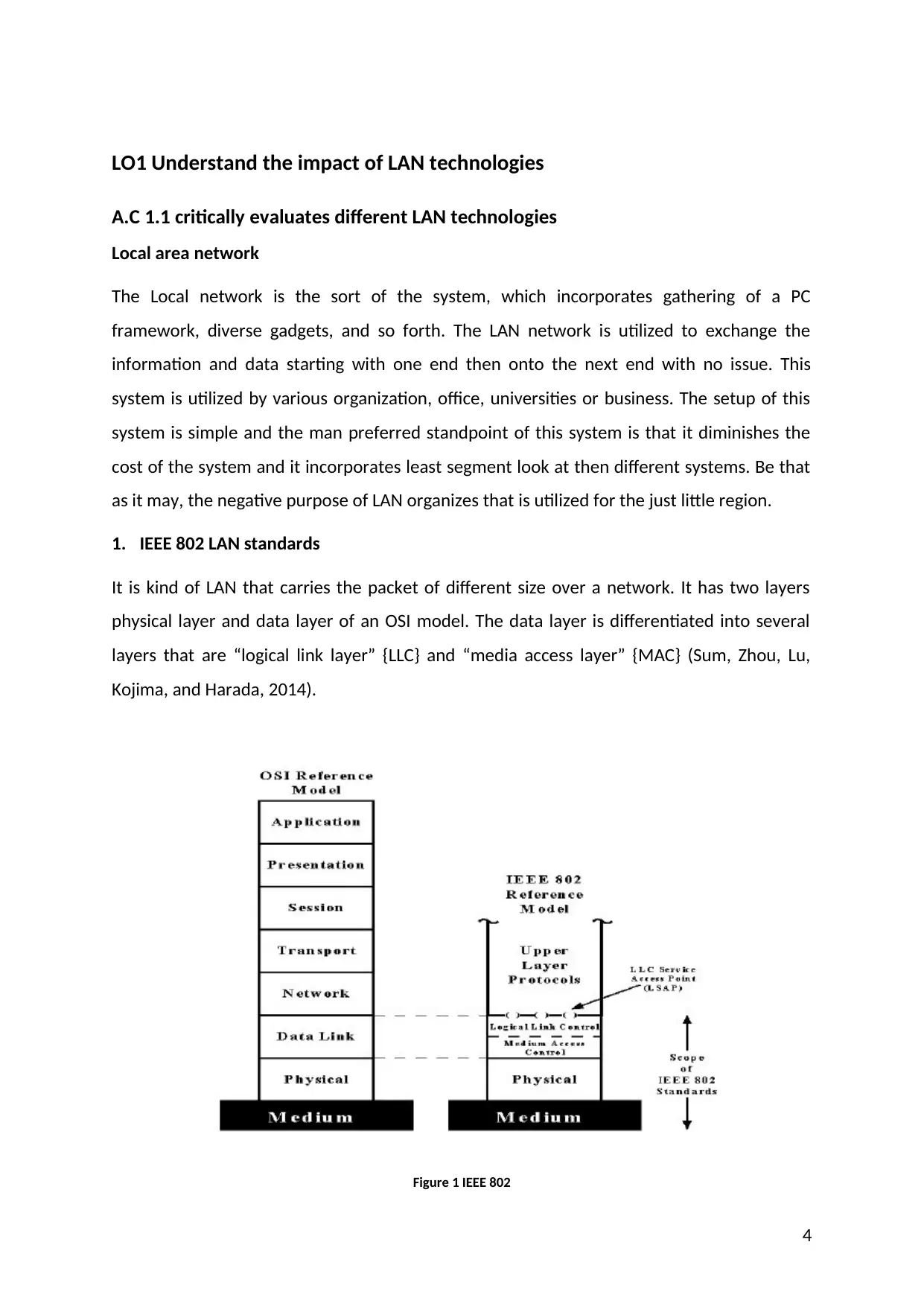
1. IEEE 802 LAN standards
It is kind of LAN that carries the packet of different size over a network. It has two layers
physical layer and data layer of an OSI model. The data layer is differentiated into several
layers that are “logical link layer” {LLC} and “media access layer” {MAC} (Sum, Zhou, Lu,
Kojima, and Harada, 2014).
Figure 1 IEEE 802
4
A.C 1.1 critically evaluates different LAN technologies
Local area network
The Local network is the sort of the system, which incorporates gathering of a PC
framework, diverse gadgets, and so forth. The LAN network is utilized to exchange the
information and data starting with one end then onto the next end with no issue. This
system is utilized by various organization, office, universities or business. The setup of this
system is simple and the man preferred standpoint of this system is that it diminishes the
cost of the system and it incorporates least segment look at then different systems. Be that
as it may, the negative purpose of LAN organizes that is utilized for the just little region.
1. IEEE 802 LAN standards
It is kind of LAN that carries the packet of different size over a network. It has two layers
physical layer and data layer of an OSI model. The data layer is differentiated into several
layers that are “logical link layer” {LLC} and “media access layer” {MAC} (Sum, Zhou, Lu,
Kojima, and Harada, 2014).
Figure 1 IEEE 802
4
2. IEEE 802.11 wireless standards
It is the collection of the physical layer and media access (MAC) for completing LAN
connection. It is used for providing wireless services like Bluetooth and Wi-Fi (Au, 2016).
Figure 2 IEEE 802.11
3. STP (Spanning Tree Protocol)
For connecting two networks of the different computer a protocol is needed that will allow
information exchange among the computer present in the network. The protocol needed
for the purpose is spanning tree (Cohen, 2015).
Figure 3 STP
4. VLANs (Virtual LAN)
5
It is the collection of the physical layer and media access (MAC) for completing LAN
connection. It is used for providing wireless services like Bluetooth and Wi-Fi (Au, 2016).
Figure 2 IEEE 802.11
3. STP (Spanning Tree Protocol)
For connecting two networks of the different computer a protocol is needed that will allow
information exchange among the computer present in the network. The protocol needed
for the purpose is spanning tree (Cohen, 2015).
Figure 3 STP
4. VLANs (Virtual LAN)
5
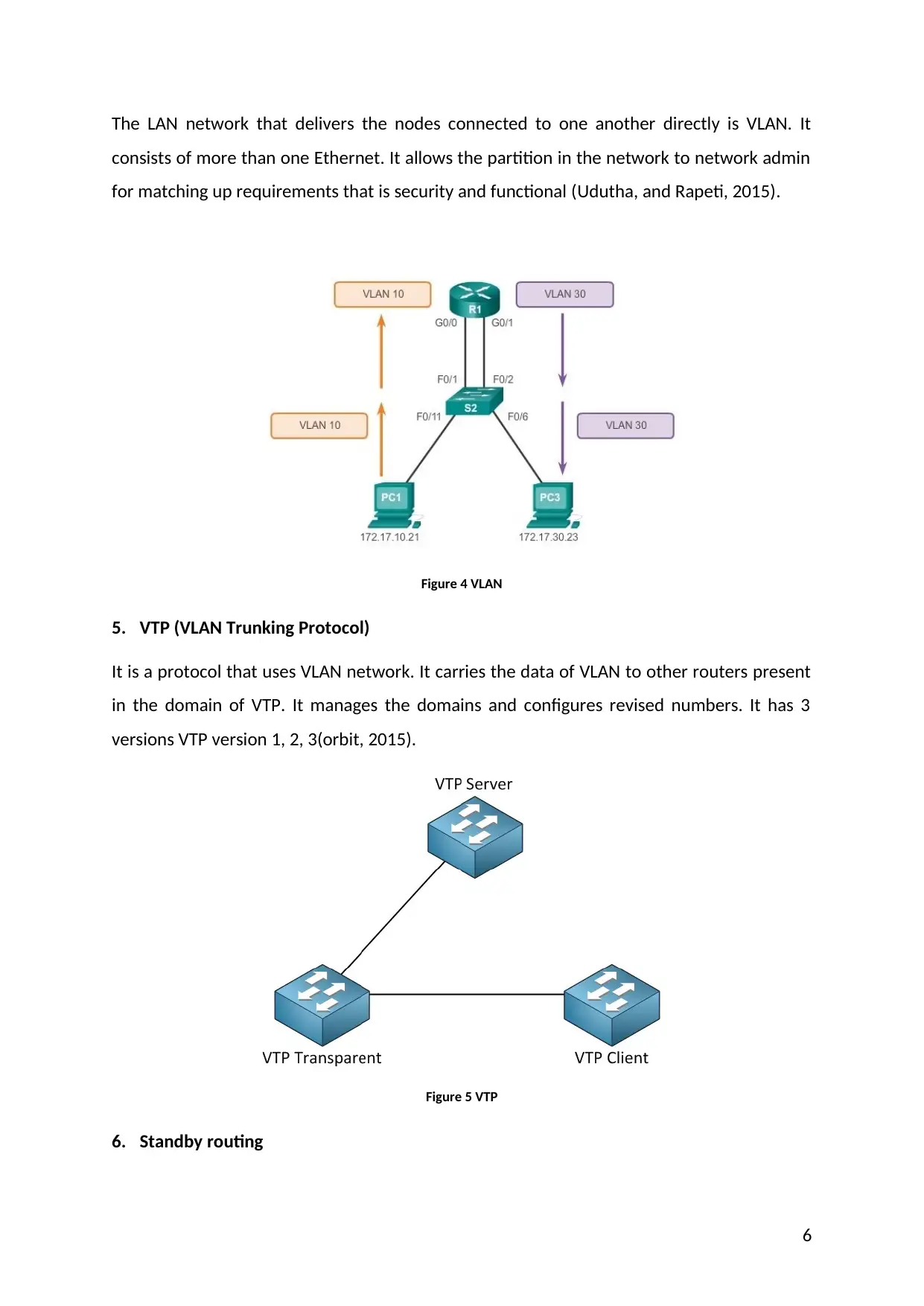
The LAN network that delivers the nodes connected to one another directly is VLAN. It
consists of more than one Ethernet. It allows the partition in the network to network admin
for matching up requirements that is security and functional (Udutha, and Rapeti, 2015).
Figure 4 VLAN
5. VTP (VLAN Trunking Protocol)
It is a protocol that uses VLAN network. It carries the data of VLAN to other routers present
in the domain of VTP. It manages the domains and configures revised numbers. It has 3
versions VTP version 1, 2, 3(orbit, 2015).
Figure 5 VTP
6. Standby routing
6
consists of more than one Ethernet. It allows the partition in the network to network admin
for matching up requirements that is security and functional (Udutha, and Rapeti, 2015).
Figure 4 VLAN
5. VTP (VLAN Trunking Protocol)
It is a protocol that uses VLAN network. It carries the data of VLAN to other routers present
in the domain of VTP. It manages the domains and configures revised numbers. It has 3
versions VTP version 1, 2, 3(orbit, 2015).
Figure 5 VTP
6. Standby routing
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
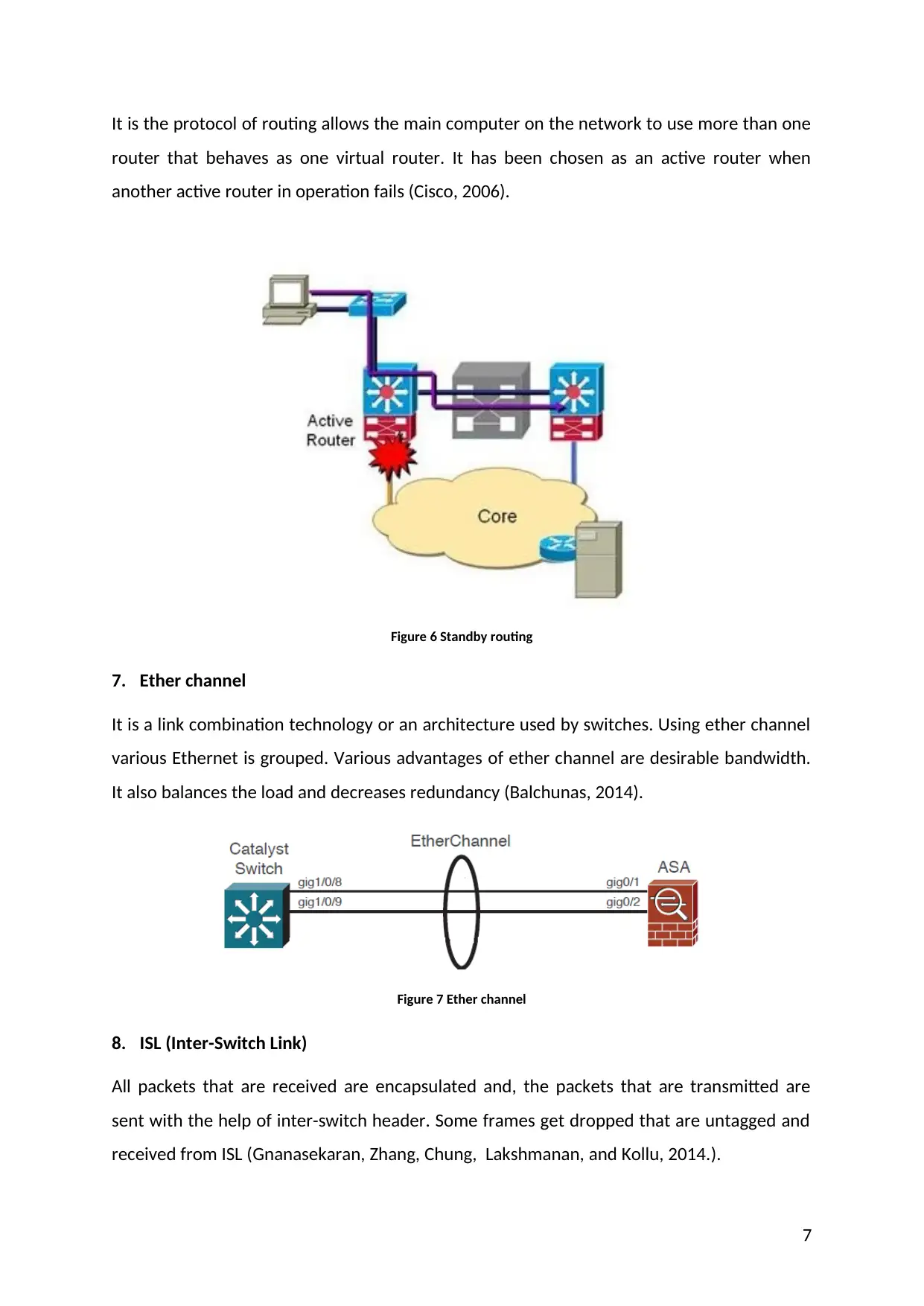
It is the protocol of routing allows the main computer on the network to use more than one
router that behaves as one virtual router. It has been chosen as an active router when
another active router in operation fails (Cisco, 2006).
Figure 6 Standby routing
7. Ether channel
It is a link combination technology or an architecture used by switches. Using ether channel
various Ethernet is grouped. Various advantages of ether channel are desirable bandwidth.
It also balances the load and decreases redundancy (Balchunas, 2014).
Figure 7 Ether channel
8. ISL (Inter-Switch Link)
All packets that are received are encapsulated and, the packets that are transmitted are
sent with the help of inter-switch header. Some frames get dropped that are untagged and
received from ISL (Gnanasekaran, Zhang, Chung, Lakshmanan, and Kollu, 2014.).
7
router that behaves as one virtual router. It has been chosen as an active router when
another active router in operation fails (Cisco, 2006).
Figure 6 Standby routing
7. Ether channel
It is a link combination technology or an architecture used by switches. Using ether channel
various Ethernet is grouped. Various advantages of ether channel are desirable bandwidth.
It also balances the load and decreases redundancy (Balchunas, 2014).
Figure 7 Ether channel
8. ISL (Inter-Switch Link)
All packets that are received are encapsulated and, the packets that are transmitted are
sent with the help of inter-switch header. Some frames get dropped that are untagged and
received from ISL (Gnanasekaran, Zhang, Chung, Lakshmanan, and Kollu, 2014.).
7
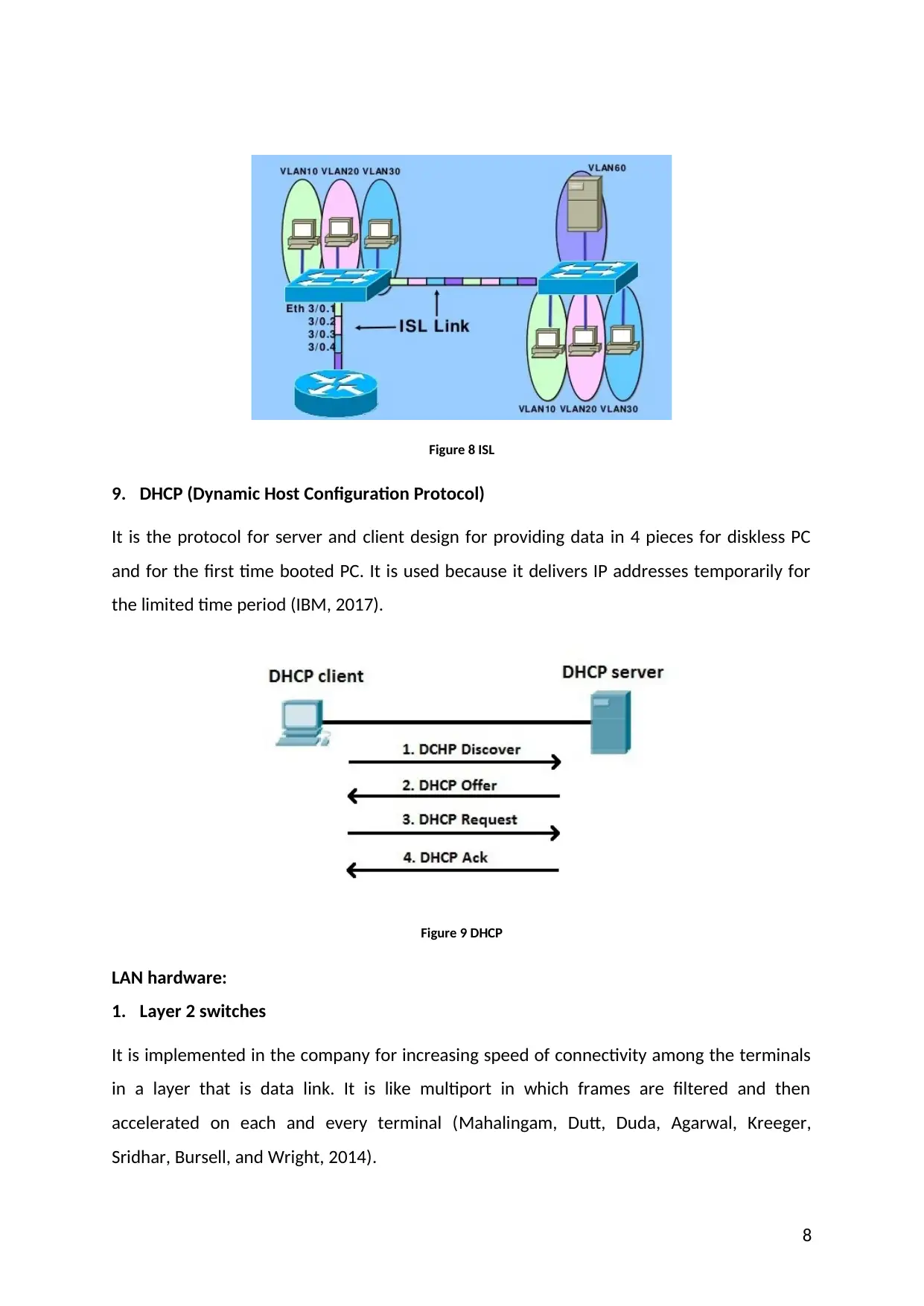
Figure 8 ISL
9. DHCP (Dynamic Host Configuration Protocol)
It is the protocol for server and client design for providing data in 4 pieces for diskless PC
and for the first time booted PC. It is used because it delivers IP addresses temporarily for
the limited time period (IBM, 2017).
Figure 9 DHCP
LAN hardware:
1. Layer 2 switches
It is implemented in the company for increasing speed of connectivity among the terminals
in a layer that is data link. It is like multiport in which frames are filtered and then
accelerated on each and every terminal (Mahalingam, Dutt, Duda, Agarwal, Kreeger,
Sridhar, Bursell, and Wright, 2014).
8
9. DHCP (Dynamic Host Configuration Protocol)
It is the protocol for server and client design for providing data in 4 pieces for diskless PC
and for the first time booted PC. It is used because it delivers IP addresses temporarily for
the limited time period (IBM, 2017).
Figure 9 DHCP
LAN hardware:
1. Layer 2 switches
It is implemented in the company for increasing speed of connectivity among the terminals
in a layer that is data link. It is like multiport in which frames are filtered and then
accelerated on each and every terminal (Mahalingam, Dutt, Duda, Agarwal, Kreeger,
Sridhar, Bursell, and Wright, 2014).
8
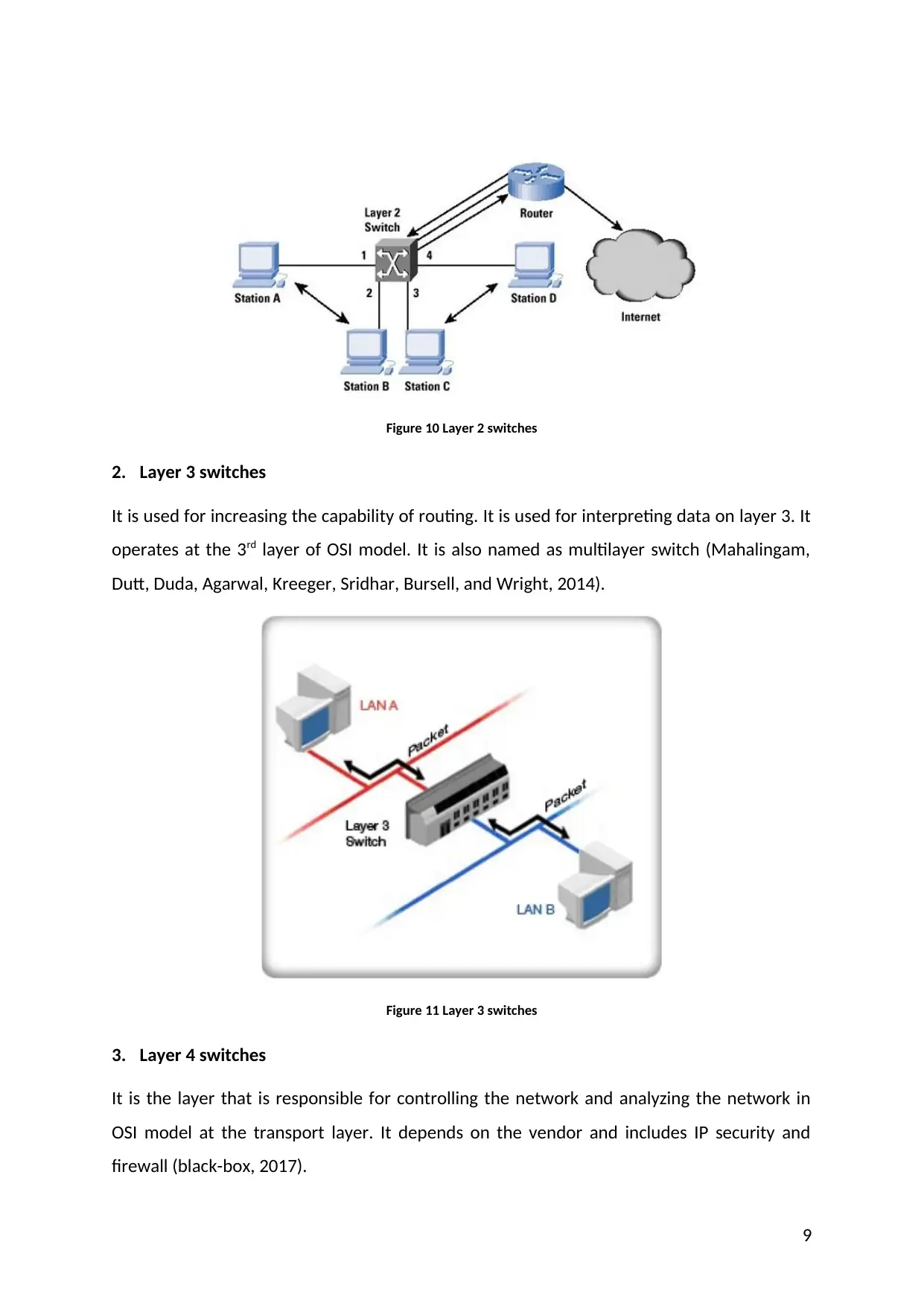
Figure 10 Layer 2 switches
2. Layer 3 switches
It is used for increasing the capability of routing. It is used for interpreting data on layer 3. It
operates at the 3rd layer of OSI model. It is also named as multilayer switch (Mahalingam,
Dutt, Duda, Agarwal, Kreeger, Sridhar, Bursell, and Wright, 2014).
Figure 11 Layer 3 switches
3. Layer 4 switches
It is the layer that is responsible for controlling the network and analyzing the network in
OSI model at the transport layer. It depends on the vendor and includes IP security and
firewall (black-box, 2017).
9
2. Layer 3 switches
It is used for increasing the capability of routing. It is used for interpreting data on layer 3. It
operates at the 3rd layer of OSI model. It is also named as multilayer switch (Mahalingam,
Dutt, Duda, Agarwal, Kreeger, Sridhar, Bursell, and Wright, 2014).
Figure 11 Layer 3 switches
3. Layer 4 switches
It is the layer that is responsible for controlling the network and analyzing the network in
OSI model at the transport layer. It depends on the vendor and includes IP security and
firewall (black-box, 2017).
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Figure 12 Layer 4 switches
4. Wireless devices
The device that communicates through radio signals is wireless devices. Nowadays it is used
in all the new technical devices like smartphone, laptops, and more. Various wireless
devices run by installing GPS, Wi-Fi, Bluetooth and more in technical equipment’s
(Balazinska, and Castro, 2003).
Figure 13 Wireless devices
5. Network interfaces
It is the controller or the physical component that is installed in a computer network. It was
implemented in the bus previously. It is a type of adapter or the Ethernet card. Using
10
4. Wireless devices
The device that communicates through radio signals is wireless devices. Nowadays it is used
in all the new technical devices like smartphone, laptops, and more. Various wireless
devices run by installing GPS, Wi-Fi, Bluetooth and more in technical equipment’s
(Balazinska, and Castro, 2003).
Figure 13 Wireless devices
5. Network interfaces
It is the controller or the physical component that is installed in a computer network. It was
implemented in the bus previously. It is a type of adapter or the Ethernet card. Using
10
network interface computer system gets connected to the network. An example of the
network interface is RJ-45 (Sqa, 2010).
Figure 14 Network interfaces
6. Client devices
These are the peripherals that are used by the user or client. The devices accessible by the
user are client devices. Various client devices are PC, mobile, laptop and more.
Figure 15 Client devices
11
network interface is RJ-45 (Sqa, 2010).
Figure 14 Network interfaces
6. Client devices
These are the peripherals that are used by the user or client. The devices accessible by the
user are client devices. Various client devices are PC, mobile, laptop and more.
Figure 15 Client devices
11

A.C 1.2 critically analyze traffic intensive services and their performance.
Traffic intensive services:
Audio and videos that streams over IP are the traffic intensive. When many activities run
simultaneously the network becomes busy and this is the concept of traffic intensive.
Quality of service management
It is known for dependability of huge network technologies for delivering outcomes that are
expected. Under quality of service management, various technologies are measured like
bandwidth, accessibility, interruption, and faults. It is necessary to manage the quality of
service. The reason behind this is as the quality of service management helps in evaluating,
analyzing the performance and making recommendations accordingly. Some methods are
used for managing quality of service is (Cisco, 2008);
DSCP (Differentiated Service Code Point)
It is the layer in IPv4, IPv6 header in networking. Its value is used as the match criteria
1. Choice from the list.
2. Match the assessment (Dialogic, 2017).
IP precedence
In the TOS byte starting 3 bits are the precedence bits. As the value increases, IP packet
importance increases simultaneously. The kind of Service bit is used for assigning the type of
delay, output, and dependability. Every web resolution includes kinds of administration
byte. The byte is separated in the file, which is utilized to give the nature of administration
duty in the system. It is used before the DSCP (NetFlow Analyzer, 2012).
Figure 16 IP precedence
Queues
12
Traffic intensive services:
Audio and videos that streams over IP are the traffic intensive. When many activities run
simultaneously the network becomes busy and this is the concept of traffic intensive.
Quality of service management
It is known for dependability of huge network technologies for delivering outcomes that are
expected. Under quality of service management, various technologies are measured like
bandwidth, accessibility, interruption, and faults. It is necessary to manage the quality of
service. The reason behind this is as the quality of service management helps in evaluating,
analyzing the performance and making recommendations accordingly. Some methods are
used for managing quality of service is (Cisco, 2008);
DSCP (Differentiated Service Code Point)
It is the layer in IPv4, IPv6 header in networking. Its value is used as the match criteria
1. Choice from the list.
2. Match the assessment (Dialogic, 2017).
IP precedence
In the TOS byte starting 3 bits are the precedence bits. As the value increases, IP packet
importance increases simultaneously. The kind of Service bit is used for assigning the type of
delay, output, and dependability. Every web resolution includes kinds of administration
byte. The byte is separated in the file, which is utilized to give the nature of administration
duty in the system. It is used before the DSCP (NetFlow Analyzer, 2012).
Figure 16 IP precedence
Queues
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

For this purpose, WRED is used which uses a number of random early detections for the
particular weight. Every profile is identified in WRED on the basis of minimum and maximum
threshold, mark probability denominator. It is applied at the class level or interface.
1. Log into the utility configuration and afterward click the systems administration and
after that click on QOS and afterward click on LAN QOS at that point choose “Queue
setting”, and lines setting page will be open.
2. At the initial step strict priority alternative chooses on the grounds that the strict
priority gives a level of the movement.
3. Click button that is saved after few seconds and settings will be saved.
Base rules
The practical execution of company’s policy is known as base rules.
802.1q frame tagging
It is the standard of networking which uses VLAN for Ethernet connection. 802.1q adds code
to Ethernet frame for highlighting the VLAN to the frame it is associated with. When frames
of Ethernet are put on the trunk then frames need more data about VLAN through which
they are associated (Omnisecu, 2014).
Quality of service need
Voice over IP
It is the technique of pocketing and transporting audio of public telephone system over the
IP network. Two-way transmissions over the network are allowed (Savvius, 2017).
Video streaming
It is a media streaming where video file gets delivered continuously through an internet to a
user. Videos available for the online view but cannot be downloaded by the user is allowed
(BusinessDictionary, 2017).
Audio streaming
It is the media streaming in which audio or music files that get delivered over the network to
the users. Here the regular playback of audio is allowed without downloading the audio file.
It works on the phenomenon voice over IP (BusinessDictionary, 2017).
13
particular weight. Every profile is identified in WRED on the basis of minimum and maximum
threshold, mark probability denominator. It is applied at the class level or interface.
1. Log into the utility configuration and afterward click the systems administration and
after that click on QOS and afterward click on LAN QOS at that point choose “Queue
setting”, and lines setting page will be open.
2. At the initial step strict priority alternative chooses on the grounds that the strict
priority gives a level of the movement.
3. Click button that is saved after few seconds and settings will be saved.
Base rules
The practical execution of company’s policy is known as base rules.
802.1q frame tagging
It is the standard of networking which uses VLAN for Ethernet connection. 802.1q adds code
to Ethernet frame for highlighting the VLAN to the frame it is associated with. When frames
of Ethernet are put on the trunk then frames need more data about VLAN through which
they are associated (Omnisecu, 2014).
Quality of service need
Voice over IP
It is the technique of pocketing and transporting audio of public telephone system over the
IP network. Two-way transmissions over the network are allowed (Savvius, 2017).
Video streaming
It is a media streaming where video file gets delivered continuously through an internet to a
user. Videos available for the online view but cannot be downloaded by the user is allowed
(BusinessDictionary, 2017).
Audio streaming
It is the media streaming in which audio or music files that get delivered over the network to
the users. Here the regular playback of audio is allowed without downloading the audio file.
It works on the phenomenon voice over IP (BusinessDictionary, 2017).
13

A.C 1.3 Discuss LAN concerns and makes recommendations to sustain network
security, reliability, and performance.
LAN security is important as the data transferred over network needs to be securely
delivered to the right owner. If the information gets access by an unauthorized person than
it will cause the great threat so the LAN security needs to be implemented (Total Computer
Solutions, 2017).
LAN networking problems are:
• The confirmation process in the system is powerless.
• The outsider can undoubtedly get the information and data.
• Privacy issues.
• Due to LAN system security decreases.
• Weak activity encryption.
For this purpose, various methods are used for securing LAN.
1. VLANs: The LAN network that delivers the nodes connected to one another directly
is VLAN. It consists of more than one Ethernet. It is needed to implement VLAN as it
protects the data on LAN (Udutha, and Rapeti, 2015).
2. Switch port control: As the DATA on unsecured LAN can be accessed by all the users
so to make the data access specifically to the particular user the switch control is
needed. It is done by securing address like MAC address dynamically and statically
(Wilkins, 2012).
3. ACLs (Access Control Lists): It is the filter used for the network by switch or router
for restricting or allowing the flow of data in the network interface. It is used for
security purpose. It provides security for interfaces having high speed. It limits the
alteration in routing and defines flow in network making network more secure.
4. Macaca's, MACACL’s is the filter used on LAN for filtering traffic on the network with
the help of layer 2 headers of LAN architecture. It is present on the cross-connect
and EFP, but cannot be supported on the port trunk and interface.
5. MAC (Media Access Control) addresses filtering: It makes a separate list of the
device that can access over a particular Wi-Fi network. List of MAC address of
devices that belongs to an organization is prepared and the access to organization
Wi-Fi is given to only those devices whose MAC address is present in the list. It
14
security, reliability, and performance.
LAN security is important as the data transferred over network needs to be securely
delivered to the right owner. If the information gets access by an unauthorized person than
it will cause the great threat so the LAN security needs to be implemented (Total Computer
Solutions, 2017).
LAN networking problems are:
• The confirmation process in the system is powerless.
• The outsider can undoubtedly get the information and data.
• Privacy issues.
• Due to LAN system security decreases.
• Weak activity encryption.
For this purpose, various methods are used for securing LAN.
1. VLANs: The LAN network that delivers the nodes connected to one another directly
is VLAN. It consists of more than one Ethernet. It is needed to implement VLAN as it
protects the data on LAN (Udutha, and Rapeti, 2015).
2. Switch port control: As the DATA on unsecured LAN can be accessed by all the users
so to make the data access specifically to the particular user the switch control is
needed. It is done by securing address like MAC address dynamically and statically
(Wilkins, 2012).
3. ACLs (Access Control Lists): It is the filter used for the network by switch or router
for restricting or allowing the flow of data in the network interface. It is used for
security purpose. It provides security for interfaces having high speed. It limits the
alteration in routing and defines flow in network making network more secure.
4. Macaca's, MACACL’s is the filter used on LAN for filtering traffic on the network with
the help of layer 2 headers of LAN architecture. It is present on the cross-connect
and EFP, but cannot be supported on the port trunk and interface.
5. MAC (Media Access Control) addresses filtering: It makes a separate list of the
device that can access over a particular Wi-Fi network. List of MAC address of
devices that belongs to an organization is prepared and the access to organization
Wi-Fi is given to only those devices whose MAC address is present in the list. It
14

makes a list of MAC address instead of IP address because every device has a unique
MAC address and Several IP addresses.
6. Wireless security: It is used for implementing, designing and securing the devices
that are connected to the network wirelessly. It secures the wireless network from
threats like unauthorized access, viruses, spoofing, malicious attack and more. For
implementing wireless security several algorithms are used that are WEP and WPA
(Balazinska, and Castro, 2003).
7. Port spanning: It is the concept of mirroring or replicating packets on the network
and sending them from one port to other of a device. It is normally implemented on
router, switch or similar type of devices. In LAN or VLAN it is used for monitoring,
identifying and handling threats on the network. The port spanning is not visible to
the nodes and sources on the network.
7. Bandwidth: It is the quantity of data bits transported per second. It is important for
devices like Input-output devices. Due to bandwidth modern buses are implemented
in PC.
8. Latency: It is the amount of duration that data packet takes for transferring from
start point to its endpoint that is a destination. It is calculated on the basis of
following measures that are the transmission, router, propagation and other PC’s.
9. Jitter: It is an interruption in the signal in a digital signal with large frequency. It
comes in the form of phase time, width, amplitude. The jitter amount depends highly
on the type of application.
10. Packet Loss (Reliability): While transmission when the data packets get lost in the
network due to failure in the network then this is the issue of LAN. The loss is due to
a fault in files while reaching the endpoint.
11. Throughput: It is the information or data packet that reached successfully to the
endpoint. It can be calculated as “bits per second”, “kilobytes per second”,
“megabytes per second” and “gigabyte per second”.
M1. Identify and apply strategies to find appropriate solutions.
Different LAN technologies and traffic intensive services are found in the above tasks and
their performance is evaluated. These findings are the appropriate solution for building a
good LAN network for an organization.
15
MAC address and Several IP addresses.
6. Wireless security: It is used for implementing, designing and securing the devices
that are connected to the network wirelessly. It secures the wireless network from
threats like unauthorized access, viruses, spoofing, malicious attack and more. For
implementing wireless security several algorithms are used that are WEP and WPA
(Balazinska, and Castro, 2003).
7. Port spanning: It is the concept of mirroring or replicating packets on the network
and sending them from one port to other of a device. It is normally implemented on
router, switch or similar type of devices. In LAN or VLAN it is used for monitoring,
identifying and handling threats on the network. The port spanning is not visible to
the nodes and sources on the network.
7. Bandwidth: It is the quantity of data bits transported per second. It is important for
devices like Input-output devices. Due to bandwidth modern buses are implemented
in PC.
8. Latency: It is the amount of duration that data packet takes for transferring from
start point to its endpoint that is a destination. It is calculated on the basis of
following measures that are the transmission, router, propagation and other PC’s.
9. Jitter: It is an interruption in the signal in a digital signal with large frequency. It
comes in the form of phase time, width, amplitude. The jitter amount depends highly
on the type of application.
10. Packet Loss (Reliability): While transmission when the data packets get lost in the
network due to failure in the network then this is the issue of LAN. The loss is due to
a fault in files while reaching the endpoint.
11. Throughput: It is the information or data packet that reached successfully to the
endpoint. It can be calculated as “bits per second”, “kilobytes per second”,
“megabytes per second” and “gigabyte per second”.
M1. Identify and apply strategies to find appropriate solutions.
Different LAN technologies and traffic intensive services are found in the above tasks and
their performance is evaluated. These findings are the appropriate solution for building a
good LAN network for an organization.
15
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
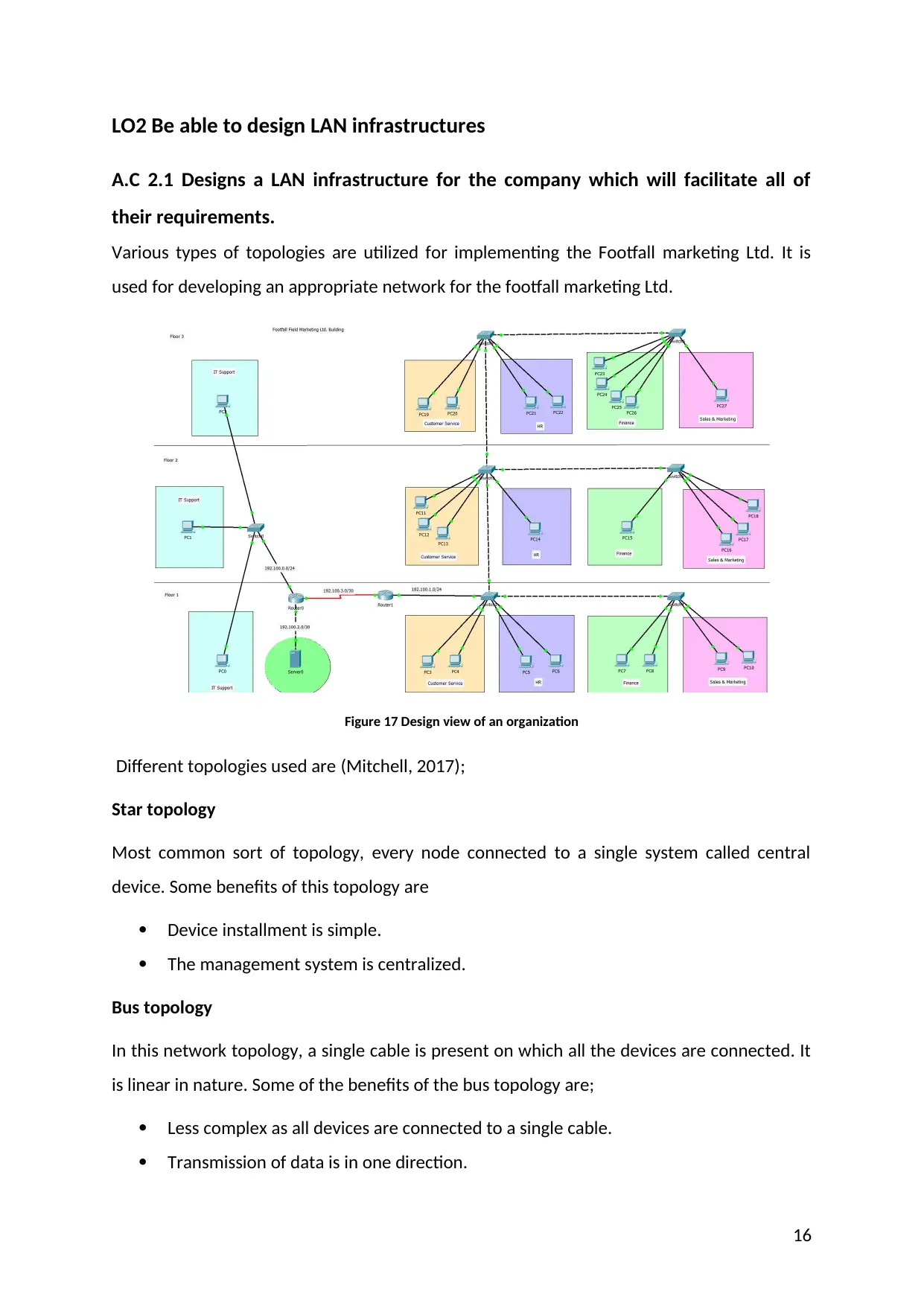
LO2 Be able to design LAN infrastructures
A.C 2.1 Designs a LAN infrastructure for the company which will facilitate all of
their requirements.
Various types of topologies are utilized for implementing the Footfall marketing Ltd. It is
used for developing an appropriate network for the footfall marketing Ltd.
Figure 17 Design view of an organization
Different topologies used are (Mitchell, 2017);
Star topology
Most common sort of topology, every node connected to a single system called central
device. Some benefits of this topology are
Device installment is simple.
The management system is centralized.
Bus topology
In this network topology, a single cable is present on which all the devices are connected. It
is linear in nature. Some of the benefits of the bus topology are;
Less complex as all devices are connected to a single cable.
Transmission of data is in one direction.
16
A.C 2.1 Designs a LAN infrastructure for the company which will facilitate all of
their requirements.
Various types of topologies are utilized for implementing the Footfall marketing Ltd. It is
used for developing an appropriate network for the footfall marketing Ltd.
Figure 17 Design view of an organization
Different topologies used are (Mitchell, 2017);
Star topology
Most common sort of topology, every node connected to a single system called central
device. Some benefits of this topology are
Device installment is simple.
The management system is centralized.
Bus topology
In this network topology, a single cable is present on which all the devices are connected. It
is linear in nature. Some of the benefits of the bus topology are;
Less complex as all devices are connected to a single cable.
Transmission of data is in one direction.
16

Mesh topology
It is the type of topology in which each system is connected to rest all system in the network
through the cable. Some benefits of using mesh topology are
Better privacy and security.
Troubleshooting is simple.
Ring topology
In this topology, the system is connected with the neighbors that are one on the right and
other on the left and the structure created looks like a ring. Some benefits of using ring
topology are;
Not much expensive.
High traffic is not a problem.
Tree topology
In this topology, the parent system is connected to its child nodes, and the hierarchy follows
up. In this topology on one root system exists and rest all are child nodes. Benefits of using
this topology are;
Error detection is simple.
Network maintenance is easy.
Easily manageable.
Hybrid topology
Hybrid is the combination of bus, star and ring topology. Some of the benefits of a hybrid
are;
Flexible to use.
The effectiveness of the topology is more
Scalable to any size.
To design the network for football, it required routers and switches and devices in the
network. For security, the Ethernet cables are installed in the network.
To design the network installs:
Routers
17
It is the type of topology in which each system is connected to rest all system in the network
through the cable. Some benefits of using mesh topology are
Better privacy and security.
Troubleshooting is simple.
Ring topology
In this topology, the system is connected with the neighbors that are one on the right and
other on the left and the structure created looks like a ring. Some benefits of using ring
topology are;
Not much expensive.
High traffic is not a problem.
Tree topology
In this topology, the parent system is connected to its child nodes, and the hierarchy follows
up. In this topology on one root system exists and rest all are child nodes. Benefits of using
this topology are;
Error detection is simple.
Network maintenance is easy.
Easily manageable.
Hybrid topology
Hybrid is the combination of bus, star and ring topology. Some of the benefits of a hybrid
are;
Flexible to use.
The effectiveness of the topology is more
Scalable to any size.
To design the network for football, it required routers and switches and devices in the
network. For security, the Ethernet cables are installed in the network.
To design the network installs:
Routers
17
Switches
Computers
Ethernet cables
To design the network, the star topology is selected. To secure the network implement
routers and switches.
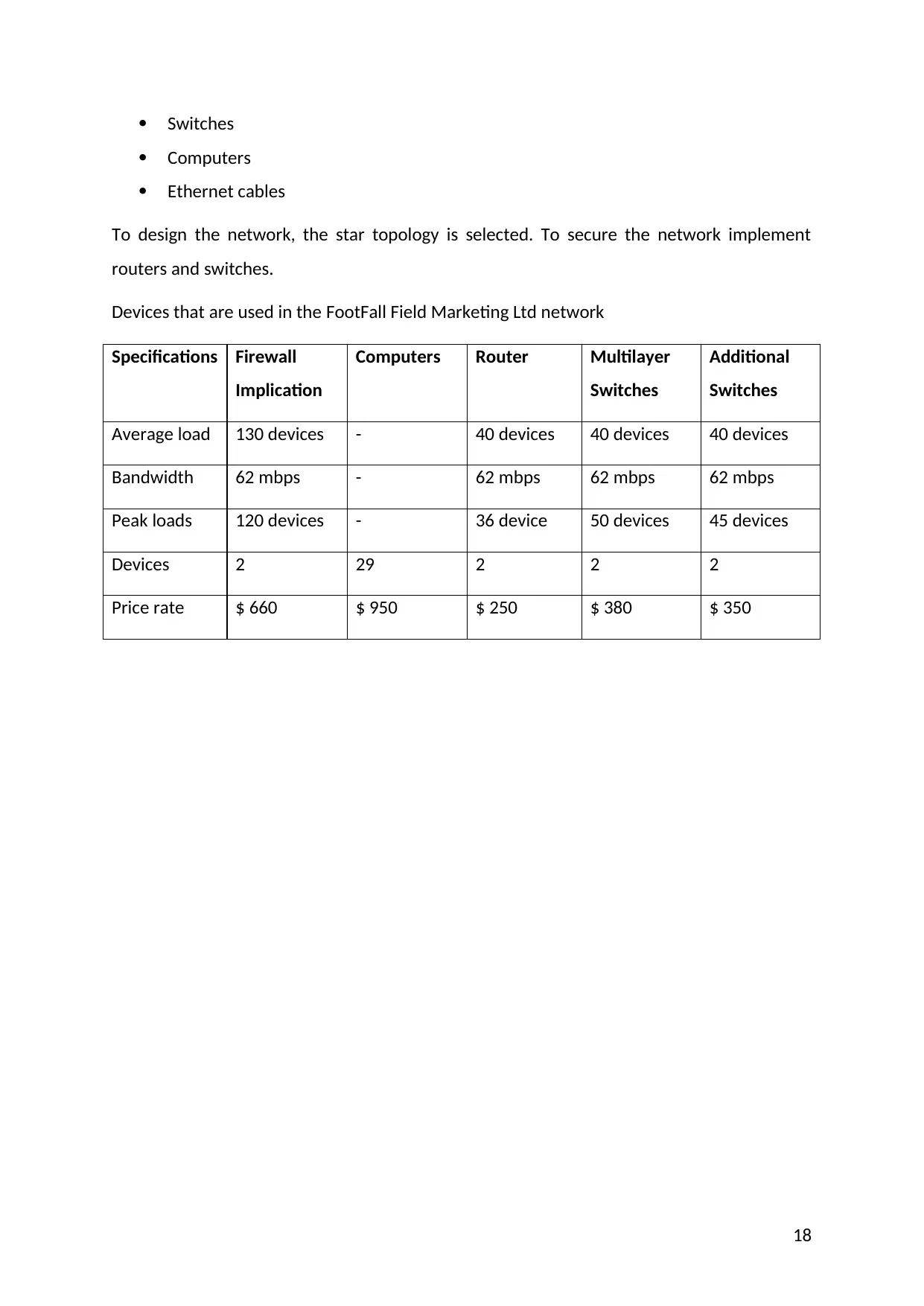
Devices that are used in the FootFall Field Marketing Ltd network
Specifications Firewall
Implication
Computers Router Multilayer
Switches
Additional
Switches
Average load 130 devices - 40 devices 40 devices 40 devices
Bandwidth 62 mbps - 62 mbps 62 mbps 62 mbps
Peak loads 120 devices - 36 device 50 devices 45 devices
Devices 2 29 2 2 2
Price rate $ 660 $ 950 $ 250 $ 380 $ 350
18
Computers
Ethernet cables
To design the network, the star topology is selected. To secure the network implement
routers and switches.
Devices that are used in the FootFall Field Marketing Ltd network
Specifications Firewall
Implication
Computers Router Multilayer
Switches
Additional
Switches
Average load 130 devices - 40 devices 40 devices 40 devices
Bandwidth 62 mbps - 62 mbps 62 mbps 62 mbps
Peak loads 120 devices - 36 device 50 devices 45 devices
Devices 2 29 2 2 2
Price rate $ 660 $ 950 $ 250 $ 380 $ 350
18
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

A.C 2.2 critically evaluates the suitability of LAN component.
Security:
The LAN structure is a complex structure; it is needed to implement system security in the
network. The security can be included by adding firewalls to the network. Firewalls are the
guard that protects the system from various threats. The company wants an easy flow of
data in their organization with the secured internet connection. For this purpose, the
appropriate solution is a firewall which acts as a bridge among the communication forms
that is secured. Firewall works like a guard that checks the several protocols when a
particular person tries to enter in the organization network. Firewall is a type of filtering
technique that filters the packets. The packet contains data which is the small part of the
information, and packets are only accessible to the authorized person. Also including
firewall, in the network, some more secured equipment’s are implemented for the secured
communication over a network that is routers that are cryptography enabled, modems
having security systems and more.
Scalability:
Scalability is one of the factors that can be attained vertically and horizontally. In a vertical
way, more components like processors, nodes, and memory (like RAM) can be added. Also,
the load balancer can be implemented for routing input to different servers by using routing
algorithm for same. Using load balancer in network infrastructure the application handles
more load easily as the load is divided among the network servers.
Availability:
It is one of the factors which are taken by users. Considering this network diagram the
availability of the user is checked. In the network structure made if any of the components
stop working, the complete system will not go to affect and disrupted. This can be reversed
at the second layer where single component failure can cause entire system failure.
Following are the consideration can be taken for availability;
Interruption
Rebooting period
Fluctuation in temperature
19
Security:
The LAN structure is a complex structure; it is needed to implement system security in the
network. The security can be included by adding firewalls to the network. Firewalls are the
guard that protects the system from various threats. The company wants an easy flow of
data in their organization with the secured internet connection. For this purpose, the
appropriate solution is a firewall which acts as a bridge among the communication forms
that is secured. Firewall works like a guard that checks the several protocols when a
particular person tries to enter in the organization network. Firewall is a type of filtering
technique that filters the packets. The packet contains data which is the small part of the
information, and packets are only accessible to the authorized person. Also including
firewall, in the network, some more secured equipment’s are implemented for the secured
communication over a network that is routers that are cryptography enabled, modems
having security systems and more.
Scalability:
Scalability is one of the factors that can be attained vertically and horizontally. In a vertical
way, more components like processors, nodes, and memory (like RAM) can be added. Also,
the load balancer can be implemented for routing input to different servers by using routing
algorithm for same. Using load balancer in network infrastructure the application handles
more load easily as the load is divided among the network servers.
Availability:
It is one of the factors which are taken by users. Considering this network diagram the
availability of the user is checked. In the network structure made if any of the components
stop working, the complete system will not go to affect and disrupted. This can be reversed
at the second layer where single component failure can cause entire system failure.
Following are the consideration can be taken for availability;
Interruption
Rebooting period
Fluctuation in temperature
19

LO3 Be able to implement LAN infrastructures
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement.
For the company “footfall field marketing Ltd.” I have implemented the LAN network to
fulfill the requirements. Various hardware components are used for the purpose that is
Router, Switches, PC, Servers, IPv4 routing, IPv6 routing, VoIP. The use of following
components in LAN network would increase the network functionality. Here is the network
diagram that I have implemented as per the company requirements. The network
implementation was done on the platform that is “Cisco Packet Tracer” which is a well-
known platform.
The company has a three-story building and each floor has numbers of employees and five
departments. The departments on each floor are customer support, HR department, IT
support, sales and marketing and last finance department. As in the network, a diagram
switch of IT department are connected to each floor and is connected to router number
zero. The other departments that are HR and customer department are connected to the
switch on each and every floor with router number 1. The remaining two departments are
finance and sales & marketing which are connected to switch on each floor through router
number 1.
Local client Configuration:
In the configuration for local clients in the network;
I have chosen the network first and then continued with the IPv4 LAN network.
Secondly, the hostname is entered in the respective field and the hostname format
includes alphabets, numeric and hyphen.
At last, the save button is clicked.
Router running configuration
20
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement.
For the company “footfall field marketing Ltd.” I have implemented the LAN network to
fulfill the requirements. Various hardware components are used for the purpose that is
Router, Switches, PC, Servers, IPv4 routing, IPv6 routing, VoIP. The use of following
components in LAN network would increase the network functionality. Here is the network
diagram that I have implemented as per the company requirements. The network
implementation was done on the platform that is “Cisco Packet Tracer” which is a well-
known platform.
The company has a three-story building and each floor has numbers of employees and five
departments. The departments on each floor are customer support, HR department, IT
support, sales and marketing and last finance department. As in the network, a diagram
switch of IT department are connected to each floor and is connected to router number
zero. The other departments that are HR and customer department are connected to the
switch on each and every floor with router number 1. The remaining two departments are
finance and sales & marketing which are connected to switch on each floor through router
number 1.
Local client Configuration:
In the configuration for local clients in the network;
I have chosen the network first and then continued with the IPv4 LAN network.
Secondly, the hostname is entered in the respective field and the hostname format
includes alphabets, numeric and hyphen.
At last, the save button is clicked.
Router running configuration
20

21
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22

Figure 18 Router 0 configuration
23
23
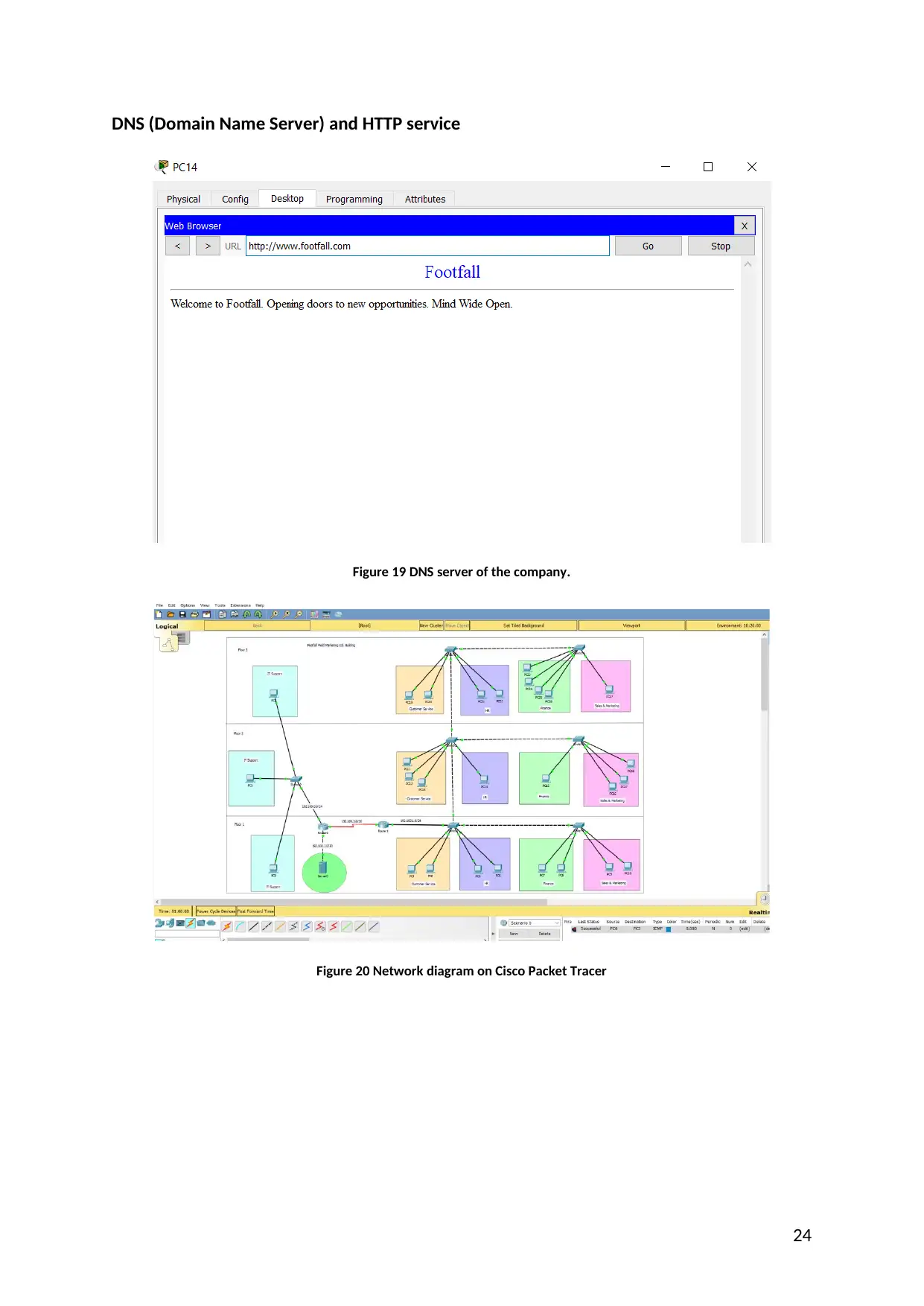
DNS (Domain Name Server) and HTTP service
Figure 19 DNS server of the company.
Figure 20 Network diagram on Cisco Packet Tracer
24
Figure 19 DNS server of the company.
Figure 20 Network diagram on Cisco Packet Tracer
24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

A.C 3.2 Implement network securities on a LAN.
The “footfall field marketing Ltd.” contains sensitive and important information and data.
Subsequently, to ensure the information and data security in the system I have utilized
some security convention in the LAN network. I have used the validation process in the
system. The procedure which is utilized to validate the client before getting the information
is authentication. The clients can get the information only if the client is approved. For the
verification, the client required to sign in the network and needs to fill following details that
are username and client unique password. As the client fills the username and password
then it will check the database. If both the username and password are coordinating from
the database then the client is approved and he can get the information. This procedure
expands the security of the LAN network. The SSH convention is used by me for the security
purpose. It is utilized for remote login that is secured. Using this methodology the client is
able to utilize the remote login of the network. The username and client password are
required to sign into the network which proves as a principal advantage. Other security
strategies that I have implemented to keep the network secure
Port Blocking
Information in the network is in the form of packets to a firewall function similar to guard
that protects unauthorized access as they try to get the information that is confidential. So
in the “Footfall field marketing ltd. I have implemented the firewall filters that are used for
filtering of inappropriate and destructive information.
Encryption
It is the cryptography methodology used for the secure processing of the network to
happen. It provides higher authentication. The information is encrypted first and then it is
transferred to the network for secure transmission of information in the unreadable form.
Authentication
It is the process by which network confirms whether the person accessing data is the right
person or not.
25
The “footfall field marketing Ltd.” contains sensitive and important information and data.
Subsequently, to ensure the information and data security in the system I have utilized
some security convention in the LAN network. I have used the validation process in the
system. The procedure which is utilized to validate the client before getting the information
is authentication. The clients can get the information only if the client is approved. For the
verification, the client required to sign in the network and needs to fill following details that
are username and client unique password. As the client fills the username and password
then it will check the database. If both the username and password are coordinating from
the database then the client is approved and he can get the information. This procedure
expands the security of the LAN network. The SSH convention is used by me for the security
purpose. It is utilized for remote login that is secured. Using this methodology the client is
able to utilize the remote login of the network. The username and client password are
required to sign into the network which proves as a principal advantage. Other security
strategies that I have implemented to keep the network secure
Port Blocking
Information in the network is in the form of packets to a firewall function similar to guard
that protects unauthorized access as they try to get the information that is confidential. So
in the “Footfall field marketing ltd. I have implemented the firewall filters that are used for
filtering of inappropriate and destructive information.
Encryption
It is the cryptography methodology used for the secure processing of the network to
happen. It provides higher authentication. The information is encrypted first and then it is
transferred to the network for secure transmission of information in the unreadable form.
Authentication
It is the process by which network confirms whether the person accessing data is the right
person or not.
25

Router configuration
In the “Footfall field marketing Ltd.” Network two routers have been used that is router 0
and router 1. Routers are used to increase the communication in the network. It is used for
managing the directions of packets and the traffic in LAN network and provides the fastest
track for the communication.
Router1 configuration
26
In the “Footfall field marketing Ltd.” Network two routers have been used that is router 0
and router 1. Routers are used to increase the communication in the network. It is used for
managing the directions of packets and the traffic in LAN network and provides the fastest
track for the communication.
Router1 configuration
26

27
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
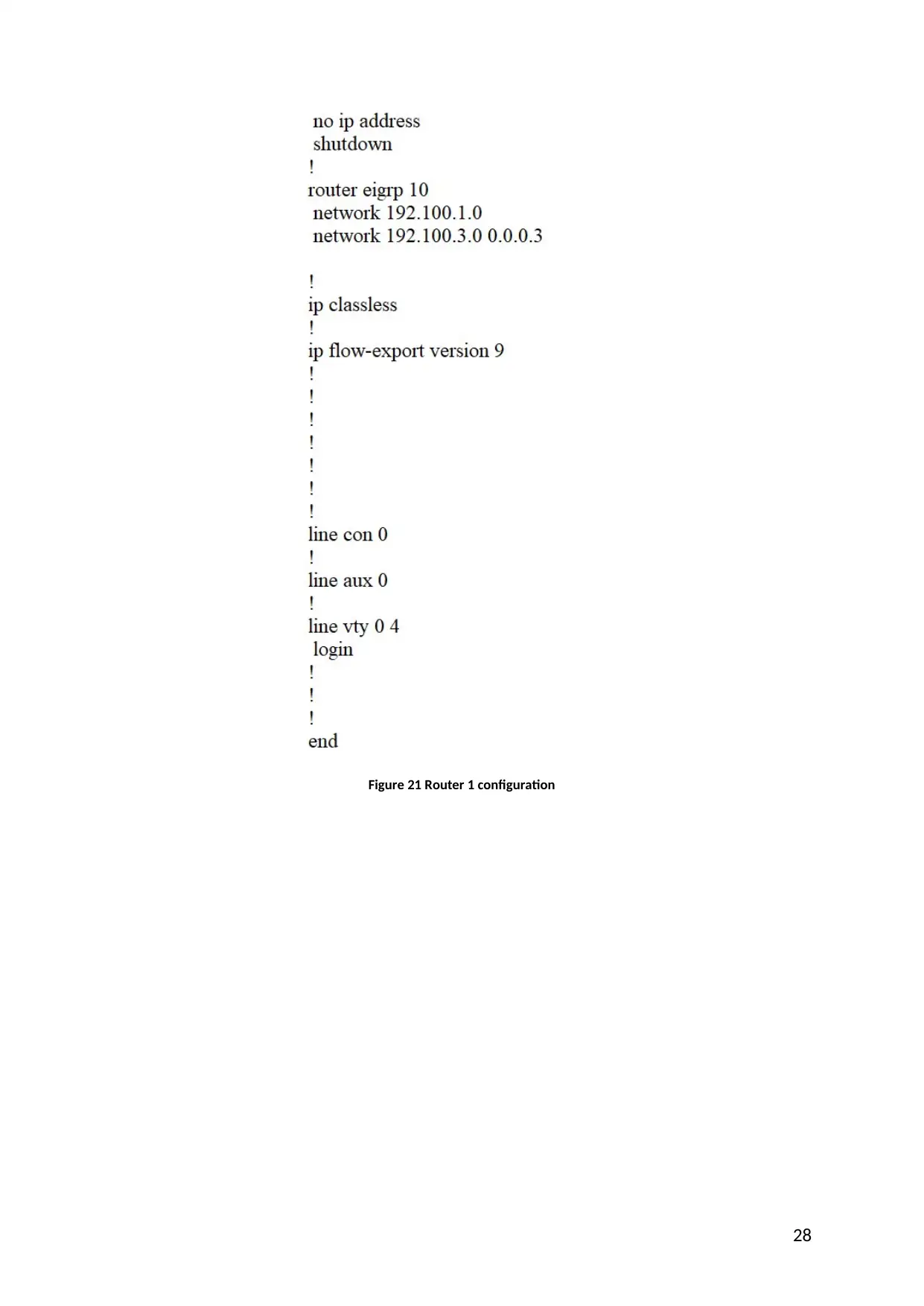
Figure 21 Router 1 configuration
28
28
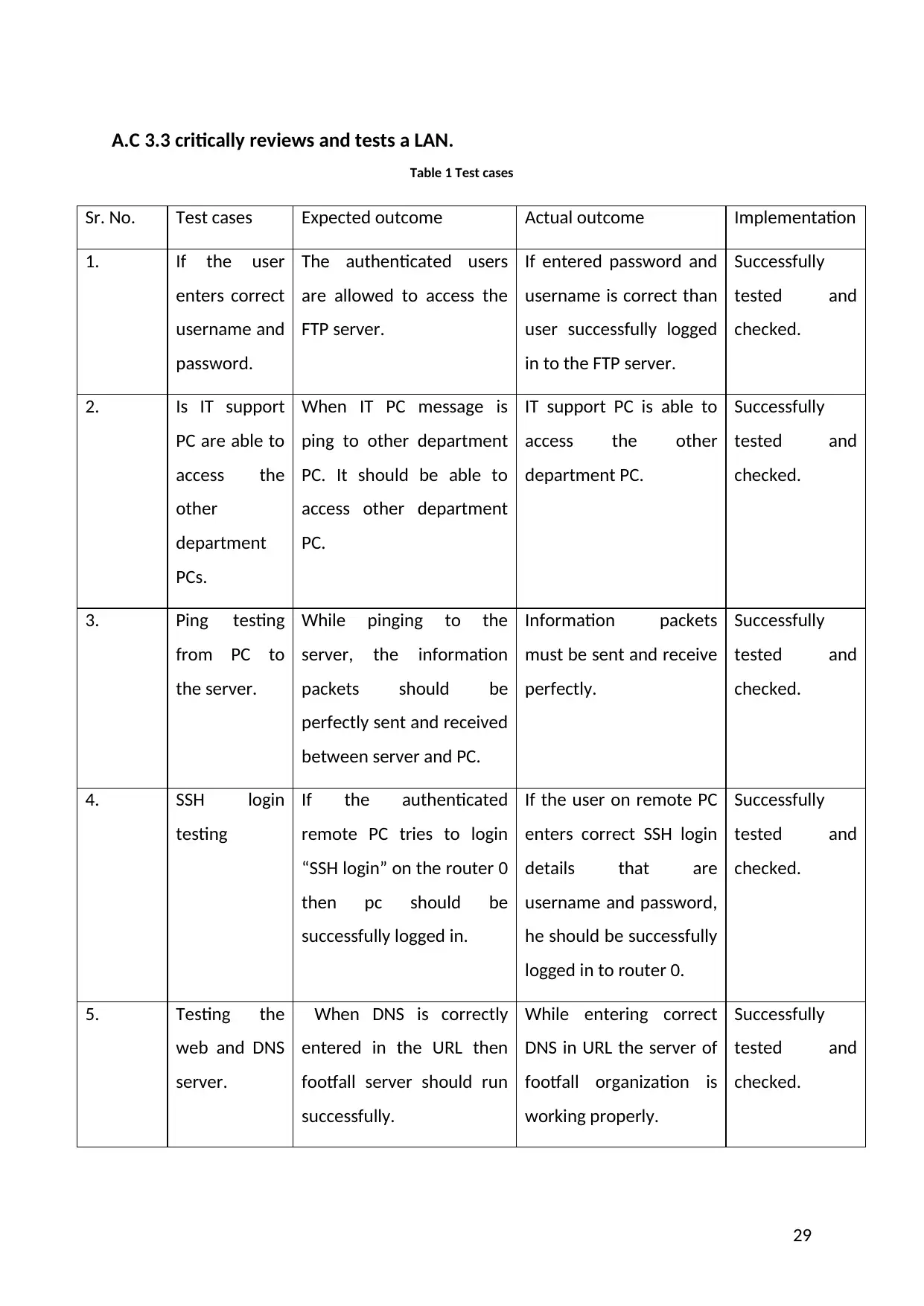
A.C 3.3 critically reviews and tests a LAN.
Table 1 Test cases
Sr. No. Test cases Expected outcome Actual outcome Implementation
1. If the user
enters correct
username and
password.
The authenticated users
are allowed to access the
FTP server.
If entered password and
username is correct than
user successfully logged
in to the FTP server.
Successfully
tested and
checked.
2. Is IT support
PC are able to
access the
other
department
PCs.
When IT PC message is
ping to other department
PC. It should be able to
access other department
PC.
IT support PC is able to
access the other
department PC.
Successfully
tested and
checked.
3. Ping testing
from PC to
the server.
While pinging to the
server, the information
packets should be
perfectly sent and received
between server and PC.
Information packets
must be sent and receive
perfectly.
Successfully
tested and
checked.
4. SSH login
testing
If the authenticated
remote PC tries to login
“SSH login” on the router 0
then pc should be
successfully logged in.
If the user on remote PC
enters correct SSH login
details that are
username and password,
he should be successfully
logged in to router 0.
Successfully
tested and
checked.
5. Testing the
web and DNS
server.
When DNS is correctly
entered in the URL then
footfall server should run
successfully.
While entering correct
DNS in URL the server of
footfall organization is
working properly.
Successfully
tested and
checked.
29
Table 1 Test cases
Sr. No. Test cases Expected outcome Actual outcome Implementation
1. If the user
enters correct
username and
password.
The authenticated users
are allowed to access the
FTP server.
If entered password and
username is correct than
user successfully logged
in to the FTP server.
Successfully
tested and
checked.
2. Is IT support
PC are able to
access the
other
department
PCs.
When IT PC message is
ping to other department
PC. It should be able to
access other department
PC.
IT support PC is able to
access the other
department PC.
Successfully
tested and
checked.
3. Ping testing
from PC to
the server.
While pinging to the
server, the information
packets should be
perfectly sent and received
between server and PC.
Information packets
must be sent and receive
perfectly.
Successfully
tested and
checked.
4. SSH login
testing
If the authenticated
remote PC tries to login
“SSH login” on the router 0
then pc should be
successfully logged in.
If the user on remote PC
enters correct SSH login
details that are
username and password,
he should be successfully
logged in to router 0.
Successfully
tested and
checked.
5. Testing the
web and DNS
server.
When DNS is correctly
entered in the URL then
footfall server should run
successfully.
While entering correct
DNS in URL the server of
footfall organization is
working properly.
Successfully
tested and
checked.
29
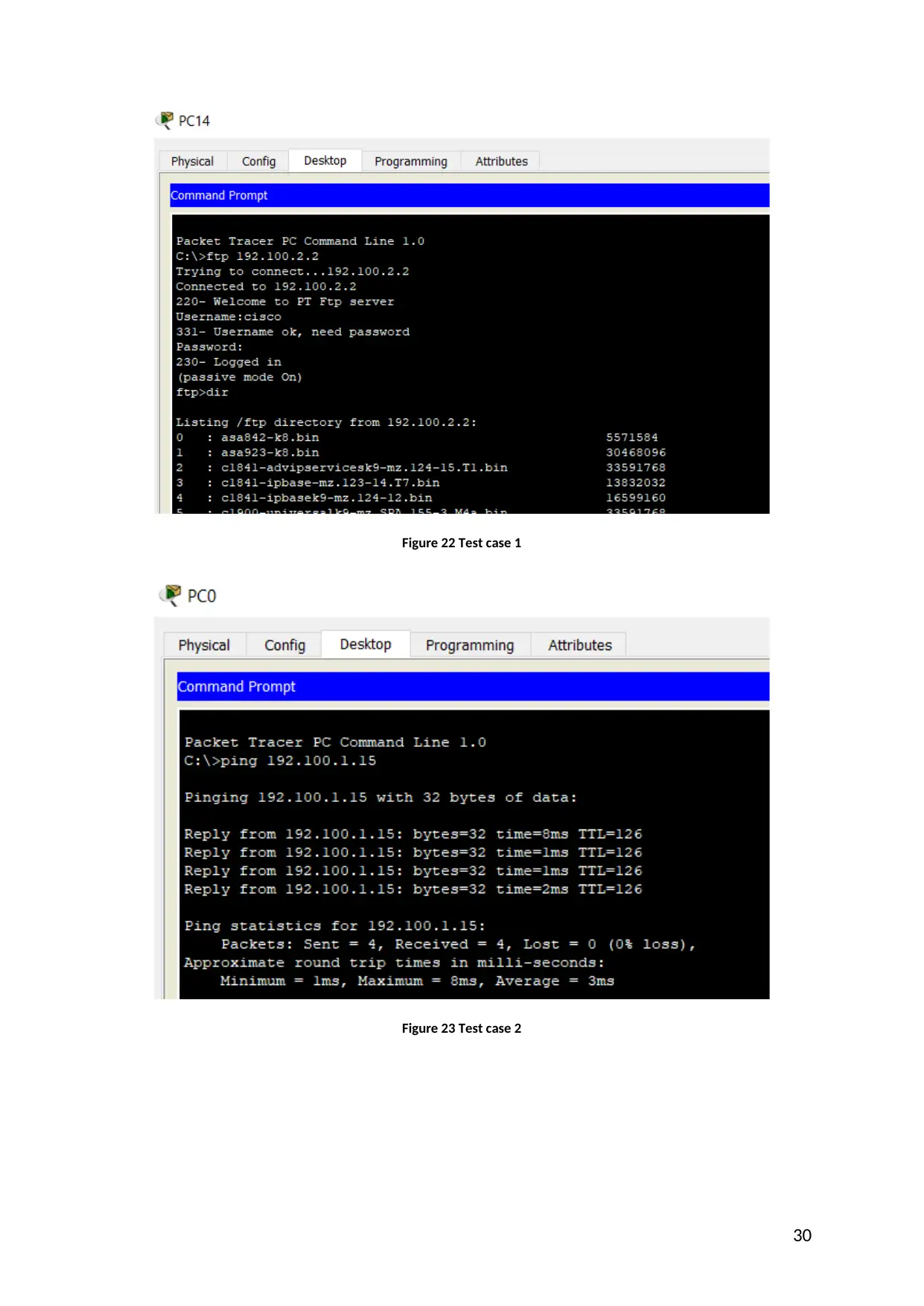
Figure 22 Test case 1
Figure 23 Test case 2
30
Figure 23 Test case 2
30
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
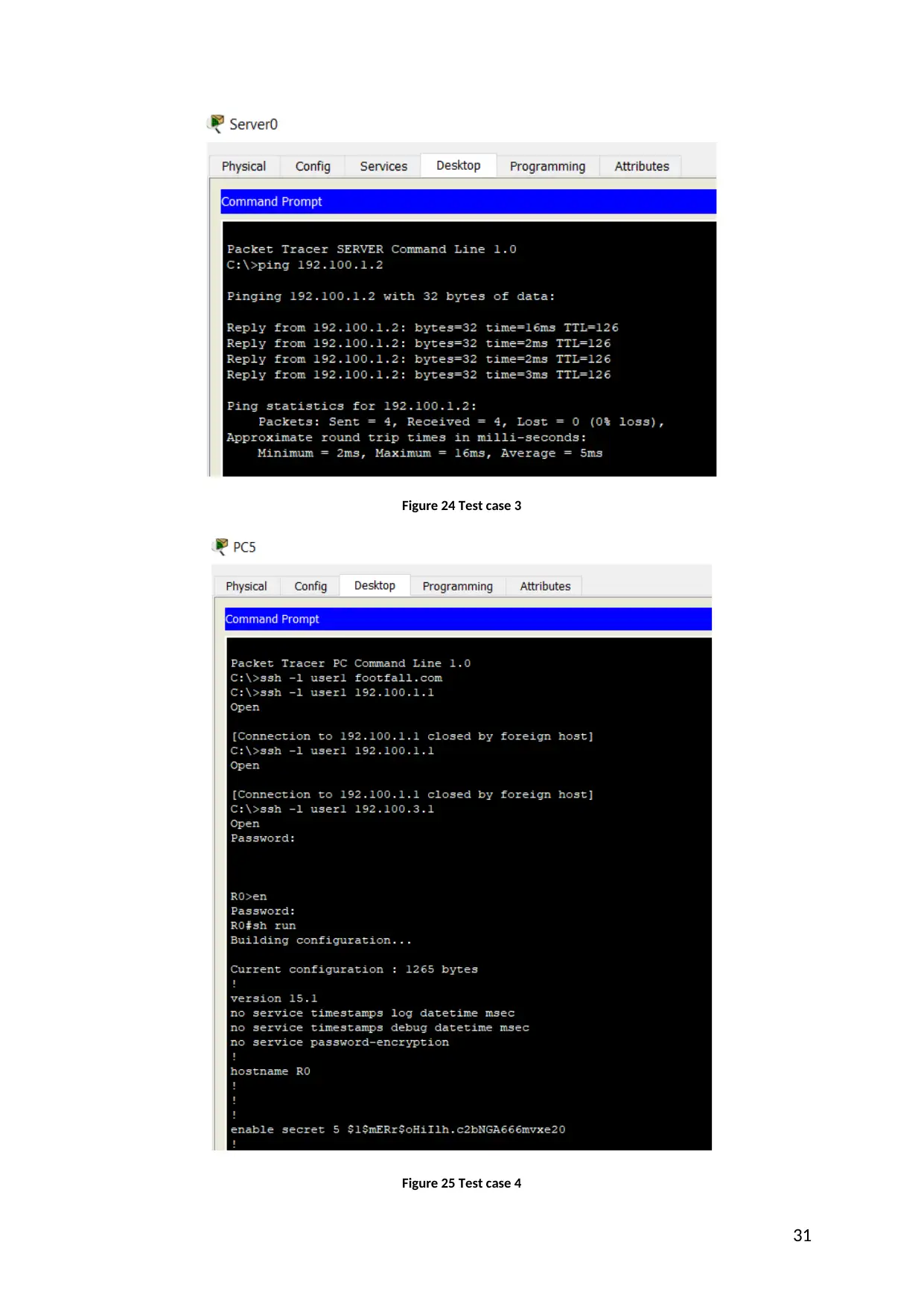
Figure 24 Test case 3
Figure 25 Test case 4
31
Figure 25 Test case 4
31

Figure 26 Test case 5
M2. Select/ design and apply appropriate methods/ techniques.
The appropriate design is selected and designed as in task 3.1 and a secured methodology is
applied for the security purpose and appropriate designing is done to fulfill the “Footfall
field marketing Ltd” an Organization.
M3. Present and communicate appropriate findings.
Various LAN components used in the network are;
1. Routers
It is a hardware component used in the network for connecting number of devices and PC’s
together either by cable or wireless. The router is used to transfer data packets among the
networks. One Routers is used to transfer data packets to other routers in the network.
2. Switch
It is another hardware component used for network creation. The switches provide the
ability to communicate to the network devices. Switches are utilized for information sharing
a purpose.
32
M2. Select/ design and apply appropriate methods/ techniques.
The appropriate design is selected and designed as in task 3.1 and a secured methodology is
applied for the security purpose and appropriate designing is done to fulfill the “Footfall
field marketing Ltd” an Organization.
M3. Present and communicate appropriate findings.
Various LAN components used in the network are;
1. Routers
It is a hardware component used in the network for connecting number of devices and PC’s
together either by cable or wireless. The router is used to transfer data packets among the
networks. One Routers is used to transfer data packets to other routers in the network.
2. Switch
It is another hardware component used for network creation. The switches provide the
ability to communicate to the network devices. Switches are utilized for information sharing
a purpose.
32

3. PC
Computers that are personal to the user. It is used for different purposes. In the network, it
is connected to the switch and is used to transfer and receive information packets from
other PC’s in the network.
4. Server
It is the computer program used for various services on different systems in the network.
For the communication system on the client side will send the server a request for the
service and the server reads the request made by the client and responds it. The server is
used for managing different devices, resources and services in the network (Hughes, 2017).
D2. Take responsibility for managing and organizing activities.
I have taken the responsibilities for managing the activities and have designed the network
accordingly to manage and organize the activities.
D3. Demonstrate convergent, lateral and creative thinking.
For implementing this project I have chosen the Cisco packet tracer for making the project it
is the best tool for implementing the network project as it has all the functionalities like
Router, switch, cables, DHCP setting and more.
For the LAN network, testing techniques are used, which is utilized as a part of “footfall field
marketing Ltd”. It is valuable to discover distinctive bugs and blunder in the framework.
Shortcoming and quality of the system can be dictated by utilizing the testing techniques. In
this segment, I am depicting the testing techniques for the LAN network.
The “footfall field marketing Ltd” is utilizing a different area and the server where area name
is “www.footfall.com” for evaluating whether the URL is operational or not. For this, it is
needed to check the program by inserting “www.footfall.com” in the area where URL needs
to be entering. By inserting this in URL it is observed that “footfall field marketing”
organization URL is working appropriately.
33
Computers that are personal to the user. It is used for different purposes. In the network, it
is connected to the switch and is used to transfer and receive information packets from
other PC’s in the network.
4. Server
It is the computer program used for various services on different systems in the network.
For the communication system on the client side will send the server a request for the
service and the server reads the request made by the client and responds it. The server is
used for managing different devices, resources and services in the network (Hughes, 2017).
D2. Take responsibility for managing and organizing activities.
I have taken the responsibilities for managing the activities and have designed the network
accordingly to manage and organize the activities.
D3. Demonstrate convergent, lateral and creative thinking.
For implementing this project I have chosen the Cisco packet tracer for making the project it
is the best tool for implementing the network project as it has all the functionalities like
Router, switch, cables, DHCP setting and more.
For the LAN network, testing techniques are used, which is utilized as a part of “footfall field
marketing Ltd”. It is valuable to discover distinctive bugs and blunder in the framework.
Shortcoming and quality of the system can be dictated by utilizing the testing techniques. In
this segment, I am depicting the testing techniques for the LAN network.
The “footfall field marketing Ltd” is utilizing a different area and the server where area name
is “www.footfall.com” for evaluating whether the URL is operational or not. For this, it is
needed to check the program by inserting “www.footfall.com” in the area where URL needs
to be entering. By inserting this in URL it is observed that “footfall field marketing”
organization URL is working appropriately.
33
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

LO4. Be able to manage LAN infrastructures
A.C 4.1 critically discusses how this LAN infrastructure will be monitored and
managed (via troubleshooting)
Troubleshooting can be defined as clearing and differentiate the issues in the LAN for
increasing performance. For achieving the end goals the LAN issues are troubleshot, the LAN
monitoring is the basic to recognize the issues in LAN. It can be done by managing system
computer.
Troubleshooting of LAN is frequently done. It can be uncertain and can include determining
of a replicate IP on the system, organized system applications wrongly, low performance of
the devices, issues in cabling, damaged switches, and LAN card, spyware and infections
attacks, more load on the system servers with the application program.
The Local area network has problems that are been produced due to several reasons
discussed above. It’s the responsibility of Network administrator that they should be aware
of the infrastructure of LAN, hardware and software components used in network, privacy
and policy rights of the user and the network configuration. To achieve this administrator
can make a list of resources and components like a number of the switch, hub, router,
workstations, software installed used for LAN (Wilkins, 2011).
Troubleshooting is done by following strategies for resolving issues occurred in LAN network
daily;
1. The plugging of the system is checked that is, to make sure that all the system are
hardly plugged at both nodes that is one at LAN card and other at Hub.
2. Evaluation of IP address is done that the IP address is of the same class or not and
the subnet cover is related or not in LAN network.
3. The gateway address is checked for the machines connected to confirm that address
is accurate or not.
4. For connectivity evaluation, PING command is used.
5. Firewall settings are evaluated and verified that the hindrance in traffic is not caused
by a firewall.
6. If a midway server and opposing network issues than it is needed to verify the
settings of the intermediate server at user’s machine.
34
A.C 4.1 critically discusses how this LAN infrastructure will be monitored and
managed (via troubleshooting)
Troubleshooting can be defined as clearing and differentiate the issues in the LAN for
increasing performance. For achieving the end goals the LAN issues are troubleshot, the LAN
monitoring is the basic to recognize the issues in LAN. It can be done by managing system
computer.
Troubleshooting of LAN is frequently done. It can be uncertain and can include determining
of a replicate IP on the system, organized system applications wrongly, low performance of
the devices, issues in cabling, damaged switches, and LAN card, spyware and infections
attacks, more load on the system servers with the application program.
The Local area network has problems that are been produced due to several reasons
discussed above. It’s the responsibility of Network administrator that they should be aware
of the infrastructure of LAN, hardware and software components used in network, privacy
and policy rights of the user and the network configuration. To achieve this administrator
can make a list of resources and components like a number of the switch, hub, router,
workstations, software installed used for LAN (Wilkins, 2011).
Troubleshooting is done by following strategies for resolving issues occurred in LAN network
daily;
1. The plugging of the system is checked that is, to make sure that all the system are
hardly plugged at both nodes that is one at LAN card and other at Hub.
2. Evaluation of IP address is done that the IP address is of the same class or not and
the subnet cover is related or not in LAN network.
3. The gateway address is checked for the machines connected to confirm that address
is accurate or not.
4. For connectivity evaluation, PING command is used.
5. Firewall settings are evaluated and verified that the hindrance in traffic is not caused
by a firewall.
6. If a midway server and opposing network issues than it is needed to verify the
settings of the intermediate server at user’s machine.
34

A.C 4.2 Resolve LAN issues to improve security, reliability, and performance.
Now in this project, I have discussed dependability, security, and execution issue
arrangement which happened in the association LAN organize (Rao, Rai, and Narain, 2017).
Settling issues with the security:
Issues in LAN security is organize which settled through antivirus, approval, and credible
processing in the LAN network. I myself have actualized LAN system arranges as following:
• I myself have introduced the antivirus most recent form on the system. Much of the
time channel and spyware framework are utilized for LAN servers and systems.
• Proxy server checks application present on the LAN arranges which made security
strings in the system.
• The client utilized approval, validation, and passwords encryption that keeps the
framework secure.
• Logging framework empowers the LAN framework and separates devices.
• I have also included the firewall for organizing the LAN.
Settling the execution and Dependability Issues
Execution and dependability are significant issues of the LAN network organize which is
settled through LAN card, subnets, and gadget. I have also clarified the way toward settling
the execution and unwavering quality Issues that are;
• The switch is utilized as a part of the system since it filtered the framework rate.
• LAN organize gadget expands RAM.
• Network tool cleared their program history, treats and superfluous documents in the
system for the determination the execution and Consistency Issues.
• In LAN organize, independently masterminded the entryway machine, intermediary
and file server, and print server. These all are stacked on every system server.
• LAN arranges utilized the change to the system composed as opposed to a center
point.
35
Now in this project, I have discussed dependability, security, and execution issue
arrangement which happened in the association LAN organize (Rao, Rai, and Narain, 2017).
Settling issues with the security:
Issues in LAN security is organize which settled through antivirus, approval, and credible
processing in the LAN network. I myself have actualized LAN system arranges as following:
• I myself have introduced the antivirus most recent form on the system. Much of the
time channel and spyware framework are utilized for LAN servers and systems.
• Proxy server checks application present on the LAN arranges which made security
strings in the system.
• The client utilized approval, validation, and passwords encryption that keeps the
framework secure.
• Logging framework empowers the LAN framework and separates devices.
• I have also included the firewall for organizing the LAN.
Settling the execution and Dependability Issues
Execution and dependability are significant issues of the LAN network organize which is
settled through LAN card, subnets, and gadget. I have also clarified the way toward settling
the execution and unwavering quality Issues that are;
• The switch is utilized as a part of the system since it filtered the framework rate.
• LAN organize gadget expands RAM.
• Network tool cleared their program history, treats and superfluous documents in the
system for the determination the execution and Consistency Issues.
• In LAN organize, independently masterminded the entryway machine, intermediary
and file server, and print server. These all are stacked on every system server.
• LAN arranges utilized the change to the system composed as opposed to a center
point.
35

• The local network card is introduced to build the system speed up to 100 Mbps
(Remoteutilities, 2017).
Decrease the activity on the system:
The activity is mindful to diminish the information broadcast rate above the system and it’s
capable to decrease the execution of the system. The system activity is a development of
the information parcel starting with one side then onto the side next to it. So to build the
execution we have to decrease the movement from the system by utilizing the activity
examination instruments. It is utilized to examine the entire system movement and lessen
the activity to build the information transmission rate.
Verification process:
The verification forms are imperative and helpful for the system. The verification procedure
is utilized to confirm the distinctive client before getting the information or data from the
system. The confirmation procedure should be possible by utilizing client’s username and
client’s password. The primary favorable position of this procedure is that lone approved
client can get to the information and the unapproved client can't get to the information
Secure reinforcement:
Reinforcements are utilized to make another duplicate of the first record. The client can get
to the duplicate of the first document in basic condition. Distinctive store gadgets are
needed for the reinforcement of the first document.
Throughput increment:
The implementation of the system can be expanded by enhancing the throughput is to build
throughput we have to quantify the aggregate sum of the information communication over
the system in the particular time period.
36
(Remoteutilities, 2017).
Decrease the activity on the system:
The activity is mindful to diminish the information broadcast rate above the system and it’s
capable to decrease the execution of the system. The system activity is a development of
the information parcel starting with one side then onto the side next to it. So to build the
execution we have to decrease the movement from the system by utilizing the activity
examination instruments. It is utilized to examine the entire system movement and lessen
the activity to build the information transmission rate.
Verification process:
The verification forms are imperative and helpful for the system. The verification procedure
is utilized to confirm the distinctive client before getting the information or data from the
system. The confirmation procedure should be possible by utilizing client’s username and
client’s password. The primary favorable position of this procedure is that lone approved
client can get to the information and the unapproved client can't get to the information
Secure reinforcement:
Reinforcements are utilized to make another duplicate of the first record. The client can get
to the duplicate of the first document in basic condition. Distinctive store gadgets are
needed for the reinforcement of the first document.
Throughput increment:
The implementation of the system can be expanded by enhancing the throughput is to build
throughput we have to quantify the aggregate sum of the information communication over
the system in the particular time period.
36
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

A.C 4.3 critically evaluates the performance of a LAN.
The keep up the usefulness of the LAN network we have to assess the execution of the LAN
network. There are diverse approaches to demonstrate the execution of the Local zone
organizes. This segment is depicting how to assess the execution of the LAN network. There
are a few focuses are given which is utilized to quantify the execution of the system.
I have assessed the execution of local network within the checking and Troubleshooting
procedure that supports to improve unwavering quality, security, and execution of the
system.
For the most extreme execution, I have tested switch port as well as its speed.
Some issues are expected on the system so they have to utilize right checking
instruments that perceived the framework which produces issues or mistakes in the
local network.
LAN design must be tested for the system which might cause error or fault in the
system.
Local network has some applications which keep running on the system. So it is
needed to check settings for the application security that perceived the error and
mistake in the system so they influence the LAN execution.
In a local network, every switch contained directing board which is an assistance to
choose best steering way. Steering Path might be influenced the LAN arrange
execution. LAN execution corrupts if various time picked the wrong way in the
system.
LAN contains reinforcement frameworks which influence the system working. In the
event that the system reinforcement framework isn't working easily at that point,
there is information synchronization issue in the system.
SNMP stream is used in the local network for the distinguished switch issue which
might be measurements and long-haul issue in the system gadget. It influences the
LAN to arrange exhibitions.
The round excursion time needs to be introduced as a measure of time because
affirmation moves starting with one end then onto the next end.
For sending information and data between the customers, the server is needed to be
installed. For the inertness of the system, the finest indicator is time. The
37
The keep up the usefulness of the LAN network we have to assess the execution of the LAN
network. There are diverse approaches to demonstrate the execution of the Local zone
organizes. This segment is depicting how to assess the execution of the LAN network. There
are a few focuses are given which is utilized to quantify the execution of the system.
I have assessed the execution of local network within the checking and Troubleshooting
procedure that supports to improve unwavering quality, security, and execution of the
system.
For the most extreme execution, I have tested switch port as well as its speed.
Some issues are expected on the system so they have to utilize right checking
instruments that perceived the framework which produces issues or mistakes in the
local network.
LAN design must be tested for the system which might cause error or fault in the
system.
Local network has some applications which keep running on the system. So it is
needed to check settings for the application security that perceived the error and
mistake in the system so they influence the LAN execution.
In a local network, every switch contained directing board which is an assistance to
choose best steering way. Steering Path might be influenced the LAN arrange
execution. LAN execution corrupts if various time picked the wrong way in the
system.
LAN contains reinforcement frameworks which influence the system working. In the
event that the system reinforcement framework isn't working easily at that point,
there is information synchronization issue in the system.
SNMP stream is used in the local network for the distinguished switch issue which
might be measurements and long-haul issue in the system gadget. It influences the
LAN to arrange exhibitions.
The round excursion time needs to be introduced as a measure of time because
affirmation moves starting with one end then onto the next end.
For sending information and data between the customers, the server is needed to be
installed. For the inertness of the system, the finest indicator is time. The
37

information parcel is taken care of through the structure and server customer. The
time must be lessened for the association foundation amongst customer and server.
To distinguish the parcels has reached the destination or not, an application requires
the damage packet identifier in the system. This issue can diminish the entire
execution of the system. On the off chance that the affirmation is setting aside an
excessive amount of opportunity to achieve the goal point it will get affected by the
system transmission.
In the event that the information is lost while communication then the source needs
to send parcel again and sometimes this process may cost high investment to resend
the information.
The rate of retransferring the parcel (that is from sender to the receiver) makes
issues in the system as more the rate of retransferring execution time for the system
will decrease.
The output of the system must have expanded the execution of the system. If the
server is reacting rapidly to the customer asks in the event then the execution of the
system will be expanded consequently.
The information exchange rate from sender to receiver expands the execution of the
system. Information exchange rate is additionally the main consideration for the
execution of the system.
The server handling time is necessary for the system. on the off chance that the
handling time of the server isn't great then the execution of the system will be
lessened so preparing time ought to be great (Lewis, 2008).
D1. Use critical reflection to evaluate own work and justify the valid conclusion.
To build up the appropriate LAN network for an organization "footfall field advertising Ltd". I
myself have utilized distinctive equipment parts and diverse programming segment. Diverse
system innovations are given in this area to comprehend the significance of a business
system. Distinctive procedures are strategies are given in this answer to building the
execution and safety of the system. Miscellaneous LAN network issues are given in this
project which is valuable to enhance the system. I myself have effectively composed the
LAN network framework as indicated by the “footfall field marketing Ltd”. I myself have
executed the system for an alternate branch of the “footfall field marketing Ltd”. In an
38
time must be lessened for the association foundation amongst customer and server.
To distinguish the parcels has reached the destination or not, an application requires
the damage packet identifier in the system. This issue can diminish the entire
execution of the system. On the off chance that the affirmation is setting aside an
excessive amount of opportunity to achieve the goal point it will get affected by the
system transmission.
In the event that the information is lost while communication then the source needs
to send parcel again and sometimes this process may cost high investment to resend
the information.
The rate of retransferring the parcel (that is from sender to the receiver) makes
issues in the system as more the rate of retransferring execution time for the system
will decrease.
The output of the system must have expanded the execution of the system. If the
server is reacting rapidly to the customer asks in the event then the execution of the
system will be expanded consequently.
The information exchange rate from sender to receiver expands the execution of the
system. Information exchange rate is additionally the main consideration for the
execution of the system.
The server handling time is necessary for the system. on the off chance that the
handling time of the server isn't great then the execution of the system will be
lessened so preparing time ought to be great (Lewis, 2008).
D1. Use critical reflection to evaluate own work and justify the valid conclusion.
To build up the appropriate LAN network for an organization "footfall field advertising Ltd". I
myself have utilized distinctive equipment parts and diverse programming segment. Diverse
system innovations are given in this area to comprehend the significance of a business
system. Distinctive procedures are strategies are given in this answer to building the
execution and safety of the system. Miscellaneous LAN network issues are given in this
project which is valuable to enhance the system. I myself have effectively composed the
LAN network framework as indicated by the “footfall field marketing Ltd”. I myself have
executed the system for an alternate branch of the “footfall field marketing Ltd”. In an
38

organization, each floor has 5 different units and each level is linked with one another. By
utilizing this system, the staff of IT sector can access the PC arrangement of all offices. For
finding and evaluating the faults I myself have utilized the testing procedure however it is
found that no mistakes are there and the system effectively passed.
39
utilizing this system, the staff of IT sector can access the PC arrangement of all offices. For
finding and evaluating the faults I myself have utilized the testing procedure however it is
found that no mistakes are there and the system effectively passed.
39
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Conclusion
In this project, I myself have actualized the LAN arrange on the “Cisco Packet Tracer” device
for the “Footfall Field Marketing Ltd” association. “Cisco Packet Tracer” is programming that
is utilized associating and including the diverse sort organize gadget. LAN system of
association settled unwavering quality; organize security and execution issue and offers
communication amongst workplaces and their areas of expertise in the same building on
different floors.
In this project report, I clarified LAN arrange, their sort and innovations which are valuable
for “Footfall Field Marketing Ltd” association. At that point, the recommendation was made
by me for LAN arrangement as per association prerequisite and assess of LAN gadget.
Further, the actualized LAN coordinates with security gauges and tested the functioning of
LAN arrangements. At last, I worked on the investigating procedure to perceive the
dependability, security, and execution issue and after that settled in the system. I have
additionally clarified LAN organize execution.
40
In this project, I myself have actualized the LAN arrange on the “Cisco Packet Tracer” device
for the “Footfall Field Marketing Ltd” association. “Cisco Packet Tracer” is programming that
is utilized associating and including the diverse sort organize gadget. LAN system of
association settled unwavering quality; organize security and execution issue and offers
communication amongst workplaces and their areas of expertise in the same building on
different floors.
In this project report, I clarified LAN arrange, their sort and innovations which are valuable
for “Footfall Field Marketing Ltd” association. At that point, the recommendation was made
by me for LAN arrangement as per association prerequisite and assess of LAN gadget.
Further, the actualized LAN coordinates with security gauges and tested the functioning of
LAN arrangements. At last, I worked on the investigating procedure to perceive the
dependability, security, and execution issue and after that settled in the system. I have
additionally clarified LAN organize execution.
40

References
Au, E., 2016. Exciting projects for PHY and MAC layers of IEEE 802.11
[standards]. IEEE Vehicular Technology Magazine, 11(2), pp.79-81.
Balazinska, M. and Castro, P., 2003, May. Characterizing mobility and network usage
in a corporate wireless local-area network. In Proceedings of the 1st international
conference on Mobile systems, applications and services (pp. 303-316). ACM.
Balchunas, A. (2014). Ether channel. [online] Routeralley. Available at:
http://www.routeralley.com/guides/etherchannel.pdf [Accessed 26 Mar. 2018].
black-box (2017). Layer 2/3/4-Switches. [online] Black-box. Available at:
https://www.black-box.de/en-de/page/21079/Resources/Technical-Resources/
Technology-Overview/Layer-2/3/4-Switches [Accessed 26 Mar. 2018].
BusinessDictionary (2017). What is streaming media?. [online] BusinessDictionary.
Available at: http://www.businessdictionary.com/definition/streaming-media.html
[Accessed 26 Mar. 2018].
Cisco (2006). Hot Standby Router Protocol Features and Functionality. [online] Cisco.
Available at: https://www.cisco.com/c/en/us/support/docs/ip/hot-standby-router-
protocol-hsrp/9234-hsrpguidetoc.html [Accessed 26 Mar. 2018].
Cisco (2008). Implementing Quality of Service. [online] Cisco. Available at:
https://www.cisco.com/c/en/us/support/docs/quality-of-service-qos/qos-packet-
marking/13747-wantqos.html [Accessed 26 Mar. 2018].
Cohen, E.G., Qualcomm Inc, 2015. Spanning tree protocol for hybrid networks. U.S.
Patent 9,160,564.
Dialogic (2017). What is Differentiated Services Code Point (DSCP)?. [online] Dialogic.
Available at: https://www.dialogic.com/glossary/differentiated-services-code-point-
dscp [Accessed 26 Mar. 2018].
Gnanasekaran, S.K., Zhang, C., Chung, D.J.Y.P., Lakshmanan, S. and Kollu, B., Brocade
Communications Systems Inc, 2014. Virtual and logical inter-switch links. U.S. Patent
8,831,013.
41
Au, E., 2016. Exciting projects for PHY and MAC layers of IEEE 802.11
[standards]. IEEE Vehicular Technology Magazine, 11(2), pp.79-81.
Balazinska, M. and Castro, P., 2003, May. Characterizing mobility and network usage
in a corporate wireless local-area network. In Proceedings of the 1st international
conference on Mobile systems, applications and services (pp. 303-316). ACM.
Balchunas, A. (2014). Ether channel. [online] Routeralley. Available at:
http://www.routeralley.com/guides/etherchannel.pdf [Accessed 26 Mar. 2018].
black-box (2017). Layer 2/3/4-Switches. [online] Black-box. Available at:
https://www.black-box.de/en-de/page/21079/Resources/Technical-Resources/
Technology-Overview/Layer-2/3/4-Switches [Accessed 26 Mar. 2018].
BusinessDictionary (2017). What is streaming media?. [online] BusinessDictionary.
Available at: http://www.businessdictionary.com/definition/streaming-media.html
[Accessed 26 Mar. 2018].
Cisco (2006). Hot Standby Router Protocol Features and Functionality. [online] Cisco.
Available at: https://www.cisco.com/c/en/us/support/docs/ip/hot-standby-router-
protocol-hsrp/9234-hsrpguidetoc.html [Accessed 26 Mar. 2018].
Cisco (2008). Implementing Quality of Service. [online] Cisco. Available at:
https://www.cisco.com/c/en/us/support/docs/quality-of-service-qos/qos-packet-
marking/13747-wantqos.html [Accessed 26 Mar. 2018].
Cohen, E.G., Qualcomm Inc, 2015. Spanning tree protocol for hybrid networks. U.S.
Patent 9,160,564.
Dialogic (2017). What is Differentiated Services Code Point (DSCP)?. [online] Dialogic.
Available at: https://www.dialogic.com/glossary/differentiated-services-code-point-
dscp [Accessed 26 Mar. 2018].
Gnanasekaran, S.K., Zhang, C., Chung, D.J.Y.P., Lakshmanan, S. and Kollu, B., Brocade
Communications Systems Inc, 2014. Virtual and logical inter-switch links. U.S. Patent
8,831,013.
41

Hughes, A. (2017). Six Required Components of a LAN. [online]
Yourbusiness.azcentral.com. Available at: https://yourbusiness.azcentral.com/six-
required-components-lan-8409.html [Accessed 26 Mar. 2018].
Ibm (2017). IBM Knowledge Center. [online] Ibm. Available at:
https://www.ibm.com/support/knowledgecenter/en/STCMML8/com.ibm.storage.ts
3500.doc/opg_3584_apdhcp.html [Accessed 26 Mar. 2018].
Lewis, P. (2008). 19 Factors Affecting Wireless LAN Performance. [online] IT Pro
Portal. Available at: https://www.itproportal.com/2008/04/22/19-factors-affecting-
wireless-lan-performance/ [Accessed 26 Mar. 2018].
Mahalingam, M., Dutt, D., Duda, K., Agarwal, P., Kreeger, L., Sridhar, T., Bursell, M.
and Wright, C., 2014. Virtual extensible local area network (VXLAN): A framework for
overlaying virtualized layer 2 networks over layer 3 networks (No. RFC 7348).
Mitchell, B. (2017). Exploring Computer Network Topologies Like Bus, Ring and Star.
[online] Lifewire. Available at: https://www.lifewire.com/computer-network-
topology-817884 [Accessed 26 Mar. 2018].
NetFlow Analyzer (2012). Understanding IP Precedence, TOS & DSCP -
ManageEngine Blog. [online] ManageEngine Blog. Available at:
https://blogs.manageengine.com/network/netflowanalyzer/2012/04/24/
understanding-ip-precedence-tos-dscp.html [Accessed 26 Mar. 2018].
Omnisecu (2014). IEEE 802.1Q VLAN Tagging. [online] Omnisecu. Available at:
http://www.omnisecu.com/cisco-certified-network-associate-ccna/ieee-802.1q-vlan-
tagging.php [Accessed 26 Mar. 2018].
orbitco (2015). What is VLAN Trunking Protocol - VTP ?. [online] orbit-computer-
solutions. Available at: http://www.orbit-computer-solutions.com/vlan-trunking-
protocol-vtp-2/ [Accessed 25 Mar. 2018].
Rao, J.D.P., Rai, S. and Narain, B., 2017. A study of Network Attacks and Features of
Secure Protocols. Research Journal of Engineering and Technology, 8(1), p.4.
Remoteutilities (2017). Common Network Problems and their Solutions | Remote
Utilities. [online] Remoteutilities. Available at:
https://www.remoteutilities.com/about/blog/Remote_Utilities/Common_Network_
Problems_and_their_Solutions/ [Accessed 26 Mar. 2018].
42
Yourbusiness.azcentral.com. Available at: https://yourbusiness.azcentral.com/six-
required-components-lan-8409.html [Accessed 26 Mar. 2018].
Ibm (2017). IBM Knowledge Center. [online] Ibm. Available at:
https://www.ibm.com/support/knowledgecenter/en/STCMML8/com.ibm.storage.ts
3500.doc/opg_3584_apdhcp.html [Accessed 26 Mar. 2018].
Lewis, P. (2008). 19 Factors Affecting Wireless LAN Performance. [online] IT Pro
Portal. Available at: https://www.itproportal.com/2008/04/22/19-factors-affecting-
wireless-lan-performance/ [Accessed 26 Mar. 2018].
Mahalingam, M., Dutt, D., Duda, K., Agarwal, P., Kreeger, L., Sridhar, T., Bursell, M.
and Wright, C., 2014. Virtual extensible local area network (VXLAN): A framework for
overlaying virtualized layer 2 networks over layer 3 networks (No. RFC 7348).
Mitchell, B. (2017). Exploring Computer Network Topologies Like Bus, Ring and Star.
[online] Lifewire. Available at: https://www.lifewire.com/computer-network-
topology-817884 [Accessed 26 Mar. 2018].
NetFlow Analyzer (2012). Understanding IP Precedence, TOS & DSCP -
ManageEngine Blog. [online] ManageEngine Blog. Available at:
https://blogs.manageengine.com/network/netflowanalyzer/2012/04/24/
understanding-ip-precedence-tos-dscp.html [Accessed 26 Mar. 2018].
Omnisecu (2014). IEEE 802.1Q VLAN Tagging. [online] Omnisecu. Available at:
http://www.omnisecu.com/cisco-certified-network-associate-ccna/ieee-802.1q-vlan-
tagging.php [Accessed 26 Mar. 2018].
orbitco (2015). What is VLAN Trunking Protocol - VTP ?. [online] orbit-computer-
solutions. Available at: http://www.orbit-computer-solutions.com/vlan-trunking-
protocol-vtp-2/ [Accessed 25 Mar. 2018].
Rao, J.D.P., Rai, S. and Narain, B., 2017. A study of Network Attacks and Features of
Secure Protocols. Research Journal of Engineering and Technology, 8(1), p.4.
Remoteutilities (2017). Common Network Problems and their Solutions | Remote
Utilities. [online] Remoteutilities. Available at:
https://www.remoteutilities.com/about/blog/Remote_Utilities/Common_Network_
Problems_and_their_Solutions/ [Accessed 26 Mar. 2018].
42
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Savvius (2017). VoIP. [online] Savvius. Available at:
https://www.savvius.com/networking-glossary/voip/ [Accessed 26 Mar. 2018].
Sqa (2010). Network Interface Card (NIC). [online] Sqa. Available at:
https://www.sqa.org.uk/e-learning/HardOSEss04CD/page_43.htm [Accessed 26 Mar.
2018].
Sum, C.S., Zhou, M.T., Lu, L., Kojima, F. and Harada, H., 2014, April. Performance and
coexistence analysis of multiple ieee 802 wpan/wlan/wran systems operating in tv
white space. In Dynamic Spectrum Access Networks (DYSPAN), 2014 IEEE
International Symposium on (pp. 145-148). IEEE.
Total Computer Solutions (2017). Local Area Network (LAN) Security | Total
Computer Solutions. [online] Total Computer Solutions. Available at:
https://www.tcsusa.com/services/tbd-security/tbd-local-area-network-lan-security/
[Accessed 26 Mar. 2018].
Udutha, S.C. and Rapeti, M., Cisco Technology Inc, 2015. Preventing leaks among
private virtual local area network ports due to configuration changes in a headless
mode. U.S. Patent 8,989,188.
Wilkins, S. (2011). Top 10 Basic Network Troubleshooting Tools Every IT Pro Should
Know. [online] Pluralsight. Available at:
https://www.pluralsight.com/blog/it-ops/network-troubleshooting-tools [Accessed
26 Mar. 2018].
Wilkins, S. (2012). Switchport Security Configuration. [online] Pluralsight. Available
at: https://www.pluralsight.com/blog/it-ops/switchport-security-configuration
[Accessed 26 Mar. 2018].
43
https://www.savvius.com/networking-glossary/voip/ [Accessed 26 Mar. 2018].
Sqa (2010). Network Interface Card (NIC). [online] Sqa. Available at:
https://www.sqa.org.uk/e-learning/HardOSEss04CD/page_43.htm [Accessed 26 Mar.
2018].
Sum, C.S., Zhou, M.T., Lu, L., Kojima, F. and Harada, H., 2014, April. Performance and
coexistence analysis of multiple ieee 802 wpan/wlan/wran systems operating in tv
white space. In Dynamic Spectrum Access Networks (DYSPAN), 2014 IEEE
International Symposium on (pp. 145-148). IEEE.
Total Computer Solutions (2017). Local Area Network (LAN) Security | Total
Computer Solutions. [online] Total Computer Solutions. Available at:
https://www.tcsusa.com/services/tbd-security/tbd-local-area-network-lan-security/
[Accessed 26 Mar. 2018].
Udutha, S.C. and Rapeti, M., Cisco Technology Inc, 2015. Preventing leaks among
private virtual local area network ports due to configuration changes in a headless
mode. U.S. Patent 8,989,188.
Wilkins, S. (2011). Top 10 Basic Network Troubleshooting Tools Every IT Pro Should
Know. [online] Pluralsight. Available at:
https://www.pluralsight.com/blog/it-ops/network-troubleshooting-tools [Accessed
26 Mar. 2018].
Wilkins, S. (2012). Switchport Security Configuration. [online] Pluralsight. Available
at: https://www.pluralsight.com/blog/it-ops/switchport-security-configuration
[Accessed 26 Mar. 2018].
43
1 out of 44
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





