Malware Virus: Types, Analysis, and Prevention
VerifiedAdded on 2023/01/17
|14
|3926
|1
AI Summary
This document provides an in-depth understanding of malware viruses, including their types, analysis methods, and prevention techniques. It explores the life cycle of malware and the significance of reverse engineering in testing malware. The document also discusses the impact of malware attacks and offers insights into protecting your system.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Malware Virus
Due Date: Tutorial, Week 6
Faculty: Science and Technology
Department: Computing & Technology
Module Code:
Academic Year: 2018/2019
Semester:
1
Due Date: Tutorial, Week 6
Faculty: Science and Technology
Department: Computing & Technology
Module Code:
Academic Year: 2018/2019
Semester:
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Content
1. Title Page
2. Table of Content
3. Executive Summary
4. Introduction
5. Methodology
5.1 Analysis
6. Implementation
6.1 Analysis of Malware Life cycle
6.2 Reverse Engineering Testbed
6.3 Static Analysis / Dynamic Analysis Tool
7. Summary / Recommendation
8. Reference
2
1. Title Page
2. Table of Content
3. Executive Summary
4. Introduction
5. Methodology
5.1 Analysis
6. Implementation
6.1 Analysis of Malware Life cycle
6.2 Reverse Engineering Testbed
6.3 Static Analysis / Dynamic Analysis Tool
7. Summary / Recommendation
8. Reference
2

Executive Summary
A computer program named as the virus affects the confidential data of a desktop by
infecting the stored files on it. A terminology virus is misunderstood by other kinds of
malware that affect the data stored on a computer. But two of the malware such as
adware and spy computer programs did not have its own generation ability. In a real
sense, a virus that infects information stored in the data from one pc to another in the
form of execution coding when the main computer is considered as the target. For
example, a user uses internet or CD, DVD, USB or a floppy disk in transferring data
from one pc to another that attracts virus from one computer to another.
When a user transfers the stored information from one pc to another then it will get
increases the chances of spreading the viruses to another desktop. This will get infect
the files shared from one server to another which increases the difficulty to access the
file. A computer virus is a very eye-catching term that attracts the attention of all the
users in knowing about this phrase that this consists of all the malware that does not
contain a re-generation feature. The term malware comprises of several viruses such
as viruses in the computer, worms, Trojan horses, rootkits, spyware and adware. All
these are a malicious program that affects the information in the computer as all these
are the unnecessary softwares spreads in the computers and infects its data.
Worms malware in the computer affects the security of a desktop as this will target
the weaknesses lies in the security of a computer which will directly spread to
different pcs by entering into its network lines. On another hand, Trojan horses
pretend as an unaffected malware but in reality, this carries the important files from
the computer and hides the malicious functions to infect the confidentiality of a
computer program (Niemelä, Hyppönen & Kangas, 2016). The difficulty for resource-
constrained IT departments gets increases in managing the multiple points by utilizing
the traditional endpoint security options.
Majority of the endpoint security protections options are not easy to put into action
and manage the same (Al-Saleh & Al-Huthaifi, 2017). Traditional endpoint
protections solutions utilize on a default allow mechanism which will allow a user to
3
A computer program named as the virus affects the confidential data of a desktop by
infecting the stored files on it. A terminology virus is misunderstood by other kinds of
malware that affect the data stored on a computer. But two of the malware such as
adware and spy computer programs did not have its own generation ability. In a real
sense, a virus that infects information stored in the data from one pc to another in the
form of execution coding when the main computer is considered as the target. For
example, a user uses internet or CD, DVD, USB or a floppy disk in transferring data
from one pc to another that attracts virus from one computer to another.
When a user transfers the stored information from one pc to another then it will get
increases the chances of spreading the viruses to another desktop. This will get infect
the files shared from one server to another which increases the difficulty to access the
file. A computer virus is a very eye-catching term that attracts the attention of all the
users in knowing about this phrase that this consists of all the malware that does not
contain a re-generation feature. The term malware comprises of several viruses such
as viruses in the computer, worms, Trojan horses, rootkits, spyware and adware. All
these are a malicious program that affects the information in the computer as all these
are the unnecessary softwares spreads in the computers and infects its data.
Worms malware in the computer affects the security of a desktop as this will target
the weaknesses lies in the security of a computer which will directly spread to
different pcs by entering into its network lines. On another hand, Trojan horses
pretend as an unaffected malware but in reality, this carries the important files from
the computer and hides the malicious functions to infect the confidentiality of a
computer program (Niemelä, Hyppönen & Kangas, 2016). The difficulty for resource-
constrained IT departments gets increases in managing the multiple points by utilizing
the traditional endpoint security options.
Majority of the endpoint security protections options are not easy to put into action
and manage the same (Al-Saleh & Al-Huthaifi, 2017). Traditional endpoint
protections solutions utilize on a default allow mechanism which will allow a user to
3

access the endpoint security systems to fights against the malware attacks on a
computer.
A unique solution that will spontaneously identify and overcome the unnecessary
software in the computer is referred to as Comodo Advanced Endpoint Protection.
This system will work secretly across all the endpoint security points without
affecting the end-user experience.
Introduction
Malware is any piece of software which is intended to cause harm to your system or
network. Malware is different from normal programs in a way that they most of them
can spread itself in the network, remain undetectable, cause changes/damage to the
infected system or network, persistence. They can bring down the machine's
performance to knees and can destroy the network. Consider the case when the
computer becomes infected and is no longer usable, the data inside becomes
unavailable these are some of the malware damage scenarios. Malware attacks can be
traced back to the time, even before the internet became widespread. Below are some
of the malware attacks in history:
Melissa: Melissa was created and released by David L. Smith in the year 1999.
It was a macro virus embedded inside a word file. The file was posed to
contain passwords for various websites which made the people curious to open
it and execute the macro. Once executed the macro would resend the virus to
first 50 people in the users address book. The virus was later tracked back to
the creator and Smith was sentenced to 10 years of prison time.
My Doom: My Doom was worm and not a virus. Hence it required no human
intervention to spread in the network. It was one of the fastest spreading email
worms in 2004. It was spread by spammers and contained a text. The malware
was initially supposed to be a variant of Mimail worm, but the theory was
rejected. It was named MyDoom basis the presence of the word doom in one
of the lines of the code. It affected companies like Google and Microsoft
causing damage in billions.
Stuxnet (2010): The destruction of a nuclear plant in Iran has occurred due to
the advanced malware system uses by a user named as Stuxnet. This had
entered the system through a USB stick and infected all the windows
machines; the code used a digital counterfeit certificate which helped to avoid
detection. Stuxnet travelled the network to check for control line systems
4
computer.
A unique solution that will spontaneously identify and overcome the unnecessary
software in the computer is referred to as Comodo Advanced Endpoint Protection.
This system will work secretly across all the endpoint security points without
affecting the end-user experience.
Introduction
Malware is any piece of software which is intended to cause harm to your system or
network. Malware is different from normal programs in a way that they most of them
can spread itself in the network, remain undetectable, cause changes/damage to the
infected system or network, persistence. They can bring down the machine's
performance to knees and can destroy the network. Consider the case when the
computer becomes infected and is no longer usable, the data inside becomes
unavailable these are some of the malware damage scenarios. Malware attacks can be
traced back to the time, even before the internet became widespread. Below are some
of the malware attacks in history:
Melissa: Melissa was created and released by David L. Smith in the year 1999.
It was a macro virus embedded inside a word file. The file was posed to
contain passwords for various websites which made the people curious to open
it and execute the macro. Once executed the macro would resend the virus to
first 50 people in the users address book. The virus was later tracked back to
the creator and Smith was sentenced to 10 years of prison time.
My Doom: My Doom was worm and not a virus. Hence it required no human
intervention to spread in the network. It was one of the fastest spreading email
worms in 2004. It was spread by spammers and contained a text. The malware
was initially supposed to be a variant of Mimail worm, but the theory was
rejected. It was named MyDoom basis the presence of the word doom in one
of the lines of the code. It affected companies like Google and Microsoft
causing damage in billions.
Stuxnet (2010): The destruction of a nuclear plant in Iran has occurred due to
the advanced malware system uses by a user named as Stuxnet. This had
entered the system through a USB stick and infected all the windows
machines; the code used a digital counterfeit certificate which helped to avoid
detection. Stuxnet travelled the network to check for control line systems
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

which controlled the nuclear centrifuges. This has affected zero-day
vulnerability in taking control of the centrifuges causing them to rotate at
uncontrollable speeds and thus destroying them.
Wannacry (2017): One of the biggest Ransomware attacks to date which
infected systems in more than 100 countries. Wannacry exploited an SMB
vulnerability which was already identified by Microsoft and patched in March
2017. Most of the systems were running an older version of the patch and
hence got affected. The way it was different from other malware is that it
spreads in the network without any user intervention and encrypt s the whole
system making it unusable unless the ransom is paid. It targeted the healthcare
industries and spread to other industries as well. A killing mechanism was
discovered by Marcus Hutchins, but the malware was updated and released
again bypassing that switch. This was a wakeup call for why IT security is
important and why we need to have an effective patch management system.
Types of Malware
Virus: A kind of malware which needs the support of a human to execute
this program.
o File viruses: This is a kind of virus that affects other files stored on
desktop and accessing the same when the affected file is opened on a
pc.
o Macro viruses: Viruses included in Excel files where VBS has used
creates difficulty in opening the current and other sheets.
o Master boot record viruses: The system gets useless when a user
commands the system to reboot the system.
o The form of Polymorphic viruses get changes suddenly to get caught
by a user.
o Stealth viruses: This virus will hide its own identity to be tracked
by a user in other legitimate files or services.
Trojan: In this virus, unwanted software files and other legal files coupled
with these files to install in a pc along with the malicious files.
o Remote Access Trojans: This will give access to all the hackers to
access the system’s information without the consent of its owner.
o Data Sending Trojans: Stealing of the information and leaks to the
hacker to affect confidentiality.
o Destructive Trojans: Damages the current files and all other files
stored on a pc.
5
vulnerability in taking control of the centrifuges causing them to rotate at
uncontrollable speeds and thus destroying them.
Wannacry (2017): One of the biggest Ransomware attacks to date which
infected systems in more than 100 countries. Wannacry exploited an SMB
vulnerability which was already identified by Microsoft and patched in March
2017. Most of the systems were running an older version of the patch and
hence got affected. The way it was different from other malware is that it
spreads in the network without any user intervention and encrypt s the whole
system making it unusable unless the ransom is paid. It targeted the healthcare
industries and spread to other industries as well. A killing mechanism was
discovered by Marcus Hutchins, but the malware was updated and released
again bypassing that switch. This was a wakeup call for why IT security is
important and why we need to have an effective patch management system.
Types of Malware
Virus: A kind of malware which needs the support of a human to execute
this program.
o File viruses: This is a kind of virus that affects other files stored on
desktop and accessing the same when the affected file is opened on a
pc.
o Macro viruses: Viruses included in Excel files where VBS has used
creates difficulty in opening the current and other sheets.
o Master boot record viruses: The system gets useless when a user
commands the system to reboot the system.
o The form of Polymorphic viruses get changes suddenly to get caught
by a user.
o Stealth viruses: This virus will hide its own identity to be tracked
by a user in other legitimate files or services.
Trojan: In this virus, unwanted software files and other legal files coupled
with these files to install in a pc along with the malicious files.
o Remote Access Trojans: This will give access to all the hackers to
access the system’s information without the consent of its owner.
o Data Sending Trojans: Stealing of the information and leaks to the
hacker to affect confidentiality.
o Destructive Trojans: Damages the current files and all other files
stored on a pc.
5

o Security software disabler Trojans: The firewall of a computer gets
useless with this the virus that forcibly allows all the malicious data
into the system.
Worm: It is a replica of other viruses that do not require the intervention
of a user in running the program.
Spam: Malicious content stored in the files of attached in emails which
will affect the inbox of the email account.
Ransomware: Decoding the data in which a user is asked to decrypt the
data and encrypt the entire system. This is in, turns, decreases the security of
the data stored in the system.
Rootkits: Difficult to track the data which is not easy to eradicate the
layout of the system.
Adware: It produces unwanted advertisements and web pages on the
system of a user.
Methodology
Static analysis: It performs the analysis of the software before its final execution is
termed as a static analysis. This approach conducted at the initial stage of the
execution period (Duprat, Lamiel, Kirchner, Correnson & Delmas, 2016). The flaws
in the memory of a computer can identify using the static analysis in the availability
of the source code of the computer program and this also determines the correctness
of models for a given system.
Other approaches covered under the static viruses are mention as below:
File fingerprinting
Extraction of hard-coded string
File format
Anti-Virus scanning
Packer detection
Disassembly
A. Signature-based detection technique: Another name of signature based the
detection technique is referred to as pattern matching or string or mask or
fingerprinting technique. Writers injected systematic bits of information into the
application that helps in identifying the malware contained in a program of a
computer. The malware detector will work in searching the previous signature codes
as this helps in detecting all the malicious content in the software.
6
useless with this the virus that forcibly allows all the malicious data
into the system.
Worm: It is a replica of other viruses that do not require the intervention
of a user in running the program.
Spam: Malicious content stored in the files of attached in emails which
will affect the inbox of the email account.
Ransomware: Decoding the data in which a user is asked to decrypt the
data and encrypt the entire system. This is in, turns, decreases the security of
the data stored in the system.
Rootkits: Difficult to track the data which is not easy to eradicate the
layout of the system.
Adware: It produces unwanted advertisements and web pages on the
system of a user.
Methodology
Static analysis: It performs the analysis of the software before its final execution is
termed as a static analysis. This approach conducted at the initial stage of the
execution period (Duprat, Lamiel, Kirchner, Correnson & Delmas, 2016). The flaws
in the memory of a computer can identify using the static analysis in the availability
of the source code of the computer program and this also determines the correctness
of models for a given system.
Other approaches covered under the static viruses are mention as below:
File fingerprinting
Extraction of hard-coded string
File format
Anti-Virus scanning
Packer detection
Disassembly
A. Signature-based detection technique: Another name of signature based the
detection technique is referred to as pattern matching or string or mask or
fingerprinting technique. Writers injected systematic bits of information into the
application that helps in identifying the malware contained in a program of a
computer. The malware detector will work in searching the previous signature codes
as this helps in detecting all the malicious content in the software.
6

B. Heuristic detection technique: This approach is also considered as a practice
technique that analyses the effect of the malware software in advance before its
occurrence. Many similarities lie between two of the approaches such as signature-
based technique and heuristic detection technique (Nieves & Romero, 2018). There is
a slight difference between both of these that in the signature-based approach a user
will search the malware manually which is done automatically in another approach.
Dynamic analysis: This analysis is also named as analysis of infected file during its
execution. The infected files are analysed in the simulated environment by using the
dynamic analysis process (Hansford and et.al., 2015). This utilises the virtual machine
concept in which the analysis will not conduct in a real environment but act like a real
one.
analysing the difference between defined points: The malware analyses for a
limited period and after that the chafes will be made in the system and again the
malware is analysed concerning the initial system state. In this approach, the
behaviour of malware is stated in the Comparison report.
Observing runtime-behaviour: Under this technique, the malware program,
introduces software to track the malicious activities in a system, of a user.
Hybrid analysis: This technique is a summation of statistical analysis and the
dynamic analysis to be called as a hybrid analysis. This consists of easy steps in a
systematic procedure in which a user will look for malware content lies in the system.
Implementation
The life cycle of Malware
This is a common statement that shows that higher the security of a system, higher
will be its quality. Due to the low security of a system, this will increases the cyber-
attack (Jaramillo, 2018). As per the cyber criminality, a cyber-attacker follows a
standard process in meeting its desired objectives. In analysing the process of
attaching it is important to enabling the defender to track the behaviour of extruder
entering the system by breaking its confidentiality. The security offering companies
describe various methods to show the prevention of the system through all these
attacks.
7
technique that analyses the effect of the malware software in advance before its
occurrence. Many similarities lie between two of the approaches such as signature-
based technique and heuristic detection technique (Nieves & Romero, 2018). There is
a slight difference between both of these that in the signature-based approach a user
will search the malware manually which is done automatically in another approach.
Dynamic analysis: This analysis is also named as analysis of infected file during its
execution. The infected files are analysed in the simulated environment by using the
dynamic analysis process (Hansford and et.al., 2015). This utilises the virtual machine
concept in which the analysis will not conduct in a real environment but act like a real
one.
analysing the difference between defined points: The malware analyses for a
limited period and after that the chafes will be made in the system and again the
malware is analysed concerning the initial system state. In this approach, the
behaviour of malware is stated in the Comparison report.
Observing runtime-behaviour: Under this technique, the malware program,
introduces software to track the malicious activities in a system, of a user.
Hybrid analysis: This technique is a summation of statistical analysis and the
dynamic analysis to be called as a hybrid analysis. This consists of easy steps in a
systematic procedure in which a user will look for malware content lies in the system.
Implementation
The life cycle of Malware
This is a common statement that shows that higher the security of a system, higher
will be its quality. Due to the low security of a system, this will increases the cyber-
attack (Jaramillo, 2018). As per the cyber criminality, a cyber-attacker follows a
standard process in meeting its desired objectives. In analysing the process of
attaching it is important to enabling the defender to track the behaviour of extruder
entering the system by breaking its confidentiality. The security offering companies
describe various methods to show the prevention of the system through all these
attacks.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Phase 1: Reconnaissance
The term reconnaissance is taken from a military vocabulary that
showcases and the process of conducting strategic observations on a
target territory (Prince, Goodman, Cowper, Chappelle & Thompson, 2018).
Extruders into the system will search for the information and then select
their target. Passive reconnaissance shows the gathering of information
through open sources like social media and on another hand; Active
reconnaissance describes the interaction of an attacker with the
resources of an entity.
Phase 2: Weaponization
The weaponization phase under which a hacker will pick the standard
operation named as modus operandi in building the entire package. This
will contains malicious content in the form of code or malicious files. The
main weapon consists of this head such as DDoS, botnets and malware.
Phase 3: Delivery
In the delivery phase, the infected files will get delivered by an
attacker in the stage of infection. An attacker will disturb the
functioning of a user by regulating the server of a user to get access by
the owner.
Phase 4: Exploitation
8
The term reconnaissance is taken from a military vocabulary that
showcases and the process of conducting strategic observations on a
target territory (Prince, Goodman, Cowper, Chappelle & Thompson, 2018).
Extruders into the system will search for the information and then select
their target. Passive reconnaissance shows the gathering of information
through open sources like social media and on another hand; Active
reconnaissance describes the interaction of an attacker with the
resources of an entity.
Phase 2: Weaponization
The weaponization phase under which a hacker will pick the standard
operation named as modus operandi in building the entire package. This
will contains malicious content in the form of code or malicious files. The
main weapon consists of this head such as DDoS, botnets and malware.
Phase 3: Delivery
In the delivery phase, the infected files will get delivered by an
attacker in the stage of infection. An attacker will disturb the
functioning of a user by regulating the server of a user to get access by
the owner.
Phase 4: Exploitation
8

Appropriate execution will not assure about its successful attack that is
the reason, this weapon is used to track the functioning of an attacker
(Srivastava and et. al., 2018). Using this weapon, an attacker will need to
control the code execution into the system. In the stage of the
exploitation, an attacker will explore the technical and human
weaknesses.
Phase 5: Installation
In this stage, the malware files are installed into the system f a user
which attracts the malware attacks by an extruder. In this, the tracker
will install a virus named as Trojan horses.
Phase 6: Command and Control
Under this stage, an attacker will take the full possession of the system
in order to access the application to work on it.
Some malware can operate independently. We can also expect AI-powered malware
shortly.
Phase 7: Actions on objectives: The attacks of a hacker achieve its different
parameters such as monetary, ideological, data related before planning its attack. In
the last stage of the analysis, a hacker will accomplishes its desired missions such as
ransom ware, breaking the login credentials and damaging of the system.
Reverse engineering malware test bed:
This will involves disassembling which is also referred as decompiling a software
program in a computer of a user. Under this process of a computer, the binary
instructions are converted into code mnemonics. This code mnemonics is consider as
a high level constructs which is mostly uses by all the engineers in building the
program by including the coding in creating a system. The impact of the coding will
9
the reason, this weapon is used to track the functioning of an attacker
(Srivastava and et. al., 2018). Using this weapon, an attacker will need to
control the code execution into the system. In the stage of the
exploitation, an attacker will explore the technical and human
weaknesses.
Phase 5: Installation
In this stage, the malware files are installed into the system f a user
which attracts the malware attacks by an extruder. In this, the tracker
will install a virus named as Trojan horses.
Phase 6: Command and Control
Under this stage, an attacker will take the full possession of the system
in order to access the application to work on it.
Some malware can operate independently. We can also expect AI-powered malware
shortly.
Phase 7: Actions on objectives: The attacks of a hacker achieve its different
parameters such as monetary, ideological, data related before planning its attack. In
the last stage of the analysis, a hacker will accomplishes its desired missions such as
ransom ware, breaking the login credentials and damaging of the system.
Reverse engineering malware test bed:
This will involves disassembling which is also referred as decompiling a software
program in a computer of a user. Under this process of a computer, the binary
instructions are converted into code mnemonics. This code mnemonics is consider as
a high level constructs which is mostly uses by all the engineers in building the
program by including the coding in creating a system. The impact of the coding will
9

directly affects the entire system and the overall computer programs when an engineer
builds this program.
An engineer will create the final solution after getting more detailed information
about the resolutions that solves the problems. The solutions introduces by engineers
will help in mitigating all the malicious contents for all the computer programs. The
Reverse engineers will explore the hints in revealing the final computer program
which are infected by malware viruses.
Disassemblers - This will help in generating assembly codes for the computer
programs and decompile is another term utilizes for transforming binary instructions
into effective codes but these are not available for building plan.
Debuggers This is used in modifying the data collected by a user in meeting its
functions to execute its work plans. This will also help all the engineers in regulating
the matters of this program to run and test it. This allows for more insight into what
the program is doing and how it is impacting a system or network.
PE Viewers- This is of different kids such as CFF explorer and PE explorer used in
extracting the useful data from the standard document.
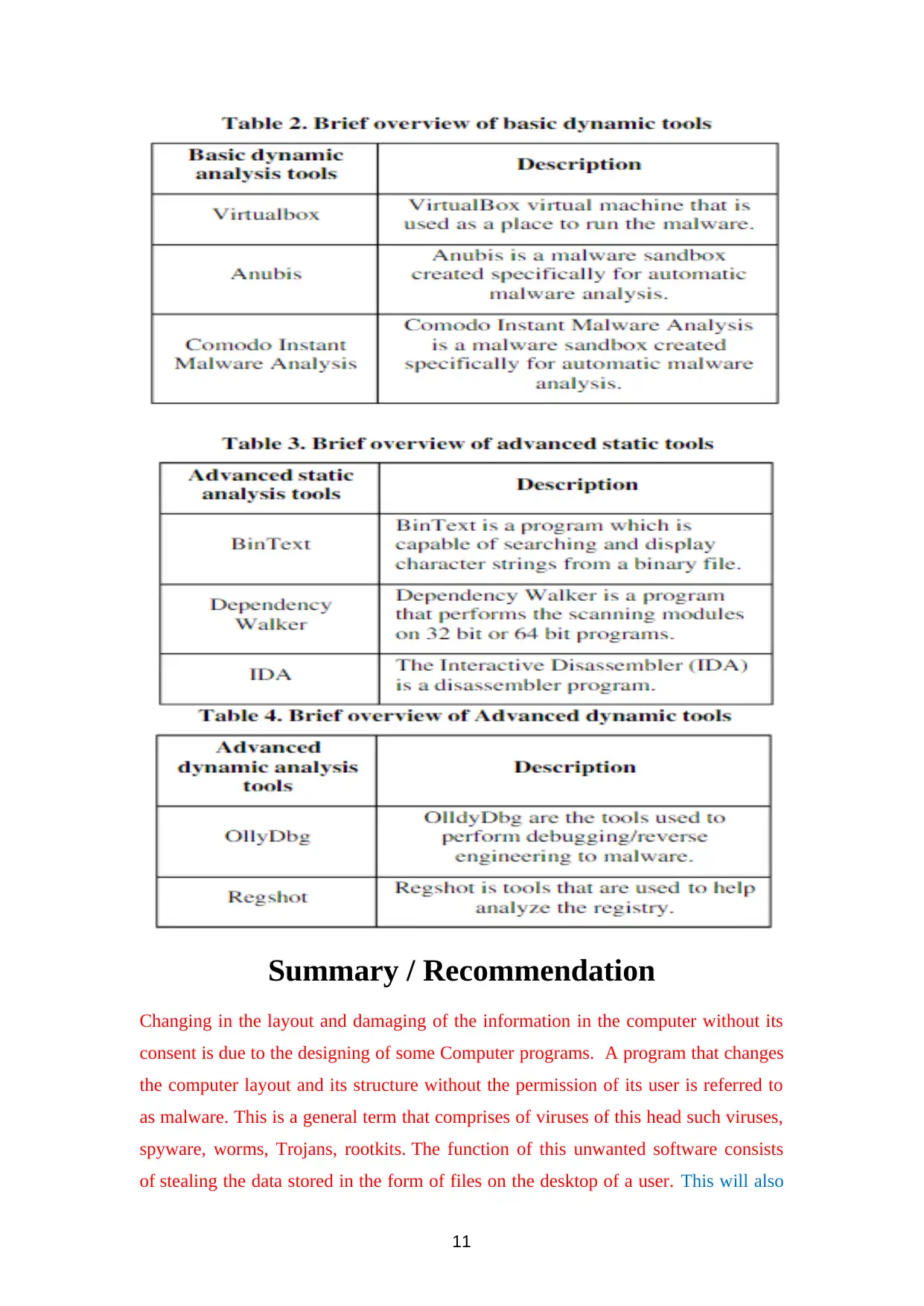
Analysis Tools:
10
builds this program.
An engineer will create the final solution after getting more detailed information
about the resolutions that solves the problems. The solutions introduces by engineers
will help in mitigating all the malicious contents for all the computer programs. The
Reverse engineers will explore the hints in revealing the final computer program
which are infected by malware viruses.
Disassemblers - This will help in generating assembly codes for the computer
programs and decompile is another term utilizes for transforming binary instructions
into effective codes but these are not available for building plan.
Debuggers This is used in modifying the data collected by a user in meeting its
functions to execute its work plans. This will also help all the engineers in regulating
the matters of this program to run and test it. This allows for more insight into what
the program is doing and how it is impacting a system or network.
PE Viewers- This is of different kids such as CFF explorer and PE explorer used in
extracting the useful data from the standard document.
Analysis Tools:
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Summary / Recommendation
Changing in the layout and damaging of the information in the computer without its
consent is due to the designing of some Computer programs. A program that changes
the computer layout and its structure without the permission of its user is referred to
as malware. This is a general term that comprises of viruses of this head such viruses,
spyware, worms, Trojans, rootkits. The function of this unwanted software consists
of stealing the data stored in the form of files on the desktop of a user. This will also
11
Changing in the layout and damaging of the information in the computer without its
consent is due to the designing of some Computer programs. A program that changes
the computer layout and its structure without the permission of its user is referred to
as malware. This is a general term that comprises of viruses of this head such viruses,
spyware, worms, Trojans, rootkits. The function of this unwanted software consists
of stealing the data stored in the form of files on the desktop of a user. This will also
11

includes the data encryption and changing the data by affecting the sensitive
information without the permission of a user. Aim of a user in dealing with all these
malware is to safeguard the malware from infecting other files into the system by
disabling the defender system.
As per the latest threat released by apt in relation to the malware and its behaviour on
the external environment, some of the suggestion mention below to deal with the
issues of malware. The suggestion given to an entity in protecting its built
infrastructure by getting affected from adversities:
1. To create a risk assessment plan for all the identified threats as the aim of this is to
search about the characteristics of a cyber-attacks which will affect the entire system
of a user.
2. The screening of the emails attachments and downloaded files to check the
malicious content in it as approx. 35% of malware content enters into corporate
networks.
3. Using application mechanism by a user which will allow trustworthy applications
to operate after taking ICS vendor's approval. In this manner, this application will
allow in protecting against the malware to run the overall program. The program code
running and injection into a form of legal applications and operating systems tests
using the analysis. The suggestion is predicted to generate effective results in the form
ICS networks after the considering the changes before its implementation.
4. It is essential to regulating the access for network connections of outside parties by
enlisting its IPT addresses into the server.
In restricting the entry of incoming malware connections in a target network by
performing the configurations to block an unwanted network belongs to the computers
system.
This will helps in building a trend for the foreign network connections by keeping
track about its time period and the amount of data supplied through this connection.
Data packets capture from the outgoing connections in assessing the encrypted data
sent to the outside network. This is a kind of a cyber-attack that contains malware or
malicious software performs activities on the computer of a user whose data is
12
information without the permission of a user. Aim of a user in dealing with all these
malware is to safeguard the malware from infecting other files into the system by
disabling the defender system.
As per the latest threat released by apt in relation to the malware and its behaviour on
the external environment, some of the suggestion mention below to deal with the
issues of malware. The suggestion given to an entity in protecting its built
infrastructure by getting affected from adversities:
1. To create a risk assessment plan for all the identified threats as the aim of this is to
search about the characteristics of a cyber-attacks which will affect the entire system
of a user.
2. The screening of the emails attachments and downloaded files to check the
malicious content in it as approx. 35% of malware content enters into corporate
networks.
3. Using application mechanism by a user which will allow trustworthy applications
to operate after taking ICS vendor's approval. In this manner, this application will
allow in protecting against the malware to run the overall program. The program code
running and injection into a form of legal applications and operating systems tests
using the analysis. The suggestion is predicted to generate effective results in the form
ICS networks after the considering the changes before its implementation.
4. It is essential to regulating the access for network connections of outside parties by
enlisting its IPT addresses into the server.
In restricting the entry of incoming malware connections in a target network by
performing the configurations to block an unwanted network belongs to the computers
system.
This will helps in building a trend for the foreign network connections by keeping
track about its time period and the amount of data supplied through this connection.
Data packets capture from the outgoing connections in assessing the encrypted data
sent to the outside network. This is a kind of a cyber-attack that contains malware or
malicious software performs activities on the computer of a user whose data is
12

affected due to the attack. Currently, people use various terms such as malware,
spyware, and ransom ware which are other names of the virus.
A term biological viruses is a virus that is injected in the human cell such as DNA or
RNA used to affect the health if a human being by replicating the cells in human
being. The host cells will create several copies of the cell in bursting the body parts of
a human being.
Reference
[1] Nowf, M. J. (2009). Online Shopping Adoption Among Women in Saudi Arabia (Doctoral
dissertation, Universiti Utara Malaysia).
[2] Mosharraf, S. I. M. (2011). ANALYSIS, DESIGN AND IMPLEMENTATION OF PRODUCT-
BASED BUSINESS MANAGEMENT WITH INTEGRATED ECommerce SUPPORT(Doctoral
dissertation, UNIVERSITY OF DHAKA).
[3] Mosharraf, S. I. M. (2011). ANALYSIS, DESIGN AND IMPLEMENTATION OF PRODUCT-
BASED BUSINESS MANAGEMENT WITH INTEGRATED ECommerce SUPPORT(Doctoral
dissertation, UNIVERSITY OF DHAKA).
[4] Molenaar, C. (2016). Why customers would rather have a smartphone than a car:
Relationship retailing as an opportunity. Routledge.
[5] Amit, R., & Zott, C. (2001). Value creation in e‐business. Strategic management
journal, 22(6‐7), 493-520.
[6] Nuzzolo, A., & Comi, A. (2015). E-shopping and urban goods flow modelling. Urban freight
and Behavior change (URBE 2015), Roma (Italia).
[7]Niemelä, J., Hyppönen, M., & Kangas, S. (2016). U.S. Patent No. 9,501,644. Washington,
DC: U.S. Patent and Trademark Office.
[8] Duprat, S., Lamiel, V. M., Kirchner, F., Correnson, L., & Delmas, D. (2016, January).
Spreading Static Analysis with Frama-C in Industrial Contexts. In 8th European Congress on
Embedded Real Time Software and Systems (ERTS 2016).
[9] Hansford, B. G., Peng, Y., Jiang, Y., Vannier, M. W., Antic, T., Thomas, S., ... & Oto, A.
(2015). Dynamic contrast-enhanced MR imaging curve-type analysis: is it helpful in the
differentiation of prostate cancer from healthy peripheral zone?. Radiology. 275(2).448-457.
[10] Nieves, J. L., & Romero, J. (2018). Heuristic analysis influence of saliency in the color
diversity of natural images. Color Research & Application. 43(5). 713-725.
[11] Al-Saleh, M. I., & Al-Huthaifi, R. K. (2017). On Improving Antivirus Scanning Engines:
Memory On-Access Scanner. JCS.13(8).290-300.
[12] Jaramillo, L. E. S. (2018, June). Detecting malware capabilities with FOSS: Lessons
learned through a real-life incident. In 2018 13th Iberian Conference on Information Systems
and Technologies (CISTI) (pp. 1-6). IEEE.
[13] Prince, L., Goodman, T., Cowper, S., Chappelle, W., & Thompson, W.
(2018). Occupational Health Screening of the 70th Intelligence, Surveillance, and
13
spyware, and ransom ware which are other names of the virus.
A term biological viruses is a virus that is injected in the human cell such as DNA or
RNA used to affect the health if a human being by replicating the cells in human
being. The host cells will create several copies of the cell in bursting the body parts of
a human being.
Reference
[1] Nowf, M. J. (2009). Online Shopping Adoption Among Women in Saudi Arabia (Doctoral
dissertation, Universiti Utara Malaysia).
[2] Mosharraf, S. I. M. (2011). ANALYSIS, DESIGN AND IMPLEMENTATION OF PRODUCT-
BASED BUSINESS MANAGEMENT WITH INTEGRATED ECommerce SUPPORT(Doctoral
dissertation, UNIVERSITY OF DHAKA).
[3] Mosharraf, S. I. M. (2011). ANALYSIS, DESIGN AND IMPLEMENTATION OF PRODUCT-
BASED BUSINESS MANAGEMENT WITH INTEGRATED ECommerce SUPPORT(Doctoral
dissertation, UNIVERSITY OF DHAKA).
[4] Molenaar, C. (2016). Why customers would rather have a smartphone than a car:
Relationship retailing as an opportunity. Routledge.
[5] Amit, R., & Zott, C. (2001). Value creation in e‐business. Strategic management
journal, 22(6‐7), 493-520.
[6] Nuzzolo, A., & Comi, A. (2015). E-shopping and urban goods flow modelling. Urban freight
and Behavior change (URBE 2015), Roma (Italia).
[7]Niemelä, J., Hyppönen, M., & Kangas, S. (2016). U.S. Patent No. 9,501,644. Washington,
DC: U.S. Patent and Trademark Office.
[8] Duprat, S., Lamiel, V. M., Kirchner, F., Correnson, L., & Delmas, D. (2016, January).
Spreading Static Analysis with Frama-C in Industrial Contexts. In 8th European Congress on
Embedded Real Time Software and Systems (ERTS 2016).
[9] Hansford, B. G., Peng, Y., Jiang, Y., Vannier, M. W., Antic, T., Thomas, S., ... & Oto, A.
(2015). Dynamic contrast-enhanced MR imaging curve-type analysis: is it helpful in the
differentiation of prostate cancer from healthy peripheral zone?. Radiology. 275(2).448-457.
[10] Nieves, J. L., & Romero, J. (2018). Heuristic analysis influence of saliency in the color
diversity of natural images. Color Research & Application. 43(5). 713-725.
[11] Al-Saleh, M. I., & Al-Huthaifi, R. K. (2017). On Improving Antivirus Scanning Engines:
Memory On-Access Scanner. JCS.13(8).290-300.
[12] Jaramillo, L. E. S. (2018, June). Detecting malware capabilities with FOSS: Lessons
learned through a real-life incident. In 2018 13th Iberian Conference on Information Systems
and Technologies (CISTI) (pp. 1-6). IEEE.
[13] Prince, L., Goodman, T., Cowper, S., Chappelle, W., & Thompson, W.
(2018). Occupational Health Screening of the 70th Intelligence, Surveillance, and
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Reconnaissance Wing: Intelligence Operators Compared with Non-Combatant Support
Personnel (No. AFRL-SA-WP-TR-2018-0009). USAFSAM/FHOH Wright-Patterson AFB
United States.
[14] Srivastava, A., Gupta, A. K., Sarkar, S., Lal, R. K., Yadav, A., Gupta, P., & Chanotiya, C.
S. (2018). Genetic and chemotypic variability in basil (Ocimum basilicum L.) germplasm
towards future exploitation. Industrial crops and products. 112. 815-820.
14
Personnel (No. AFRL-SA-WP-TR-2018-0009). USAFSAM/FHOH Wright-Patterson AFB
United States.
[14] Srivastava, A., Gupta, A. K., Sarkar, S., Lal, R. K., Yadav, A., Gupta, P., & Chanotiya, C.
S. (2018). Genetic and chemotypic variability in basil (Ocimum basilicum L.) germplasm
towards future exploitation. Industrial crops and products. 112. 815-820.
14
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





