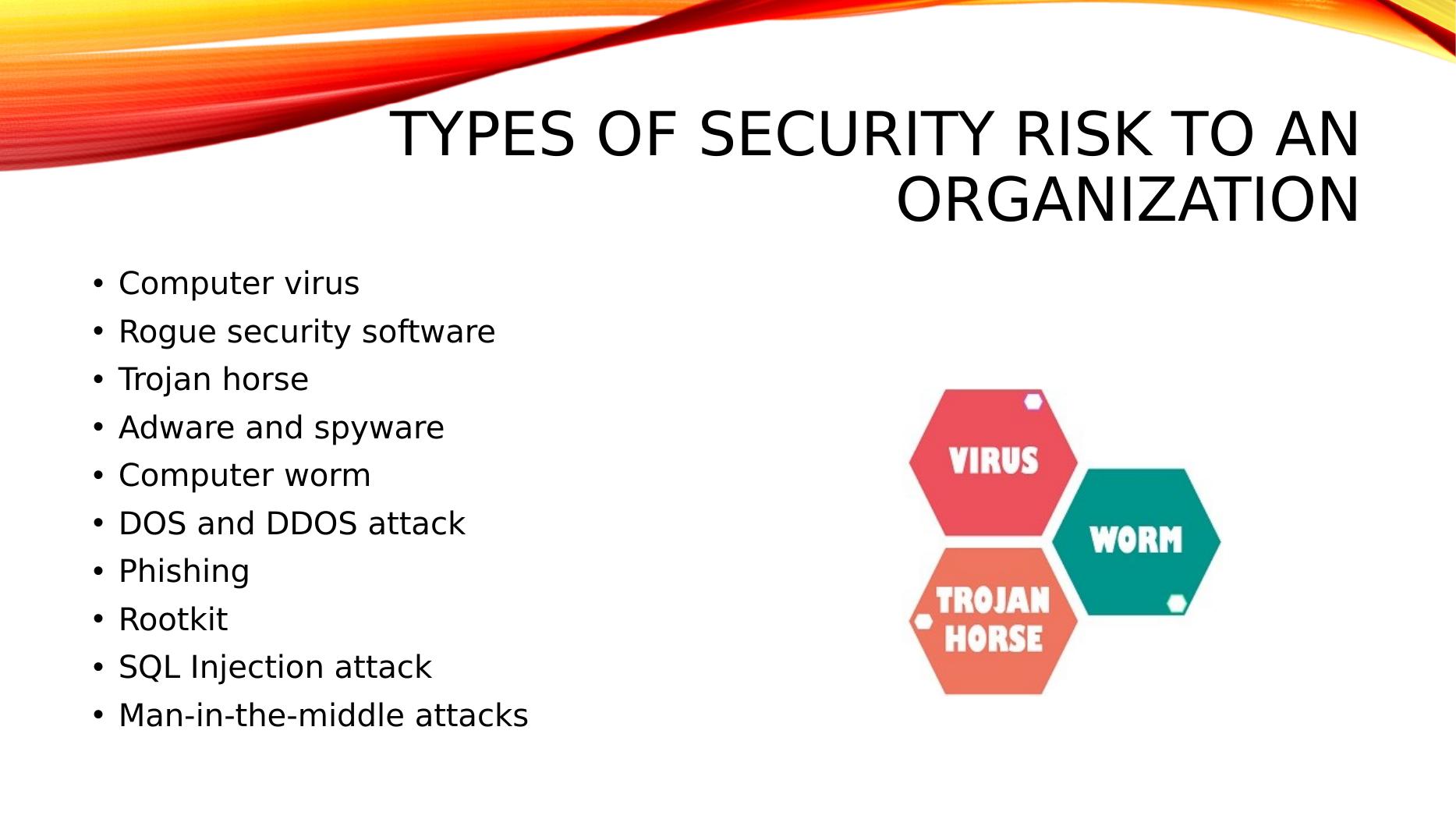
Assignment on Risks and Risk Management
Create an engaging presentation and guidebook on identifying and assessing IT security risks and organizational policies to protect business critical data and equipment.
11 Pages781 Words13 Views
Added on 2022-08-26
Assignment on Risks and Risk Management
Create an engaging presentation and guidebook on identifying and assessing IT security risks and organizational policies to protect business critical data and equipment.
Added on 2022-08-26
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
ICTNWK509 Design and Implement a Security Perimeter for ICT Networks
|11
|2802
|16
Network Security: Tools and Techniques for Protection
|4
|900
|214
Identified Vulnerabilities and Preventive Measures for Social and Operational Threats
|2
|642
|189
Malware Analysis Assignment PDF
|29
|6377
|378
Networking: Malicious Attacks, Social Engineering, Information Security Risks, Network Auditing, and Risk Assessment Management
|10
|3587
|73
Malware Virus: Types, Analysis, and Prevention
|14
|3926
|1