IT Networking and Communication: IPv4 Addressing, Subnetting, and Protocols
VerifiedAdded on 2022/10/31
|13
|2866
|214
AI Summary
This document provides an overview of IPv4 addressing, subnetting, and protocols used in IT networking and communication. It covers topics such as classful and classless addressing, subnet masks, network addresses, fragmentation, and different protocols like TCP/IP, DHCP, ARP, DNS, HTTP, FTP, ICMP, HTTPS, IGMP, NTP, UDP, TLS, TFTP, TCP, SSH, SNMP2/3, SMTP, SIP, RTP, and POP3. The document also compares and contrasts link-state and distance-vector routing methods.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: NETWORKING
0
Networking
IT NETWORKING AND COMMUNICATION
(Student Details: )
9/21/2019
0
Networking
IT NETWORKING AND COMMUNICATION
(Student Details: )
9/21/2019
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Management
1
IT NETWORKING AND COMMUNICATION
Answer 1
In IPv4, there are two types of addressing include classless and classful. In the context
of classful addressing, usually an IP address allocation methodology is used. This addressing
typically allocates IP addressed as per the pre-defined five major classes. It has been found
that classful addressing is less useful as well as less practical as compared to that of classless
addressing (Liu & Chen, 2009). On the other hand, in classless addressing an IP address used
for the allocation. Such allocation is usually designed for replacing classful addressing in
order to minimize the early exhaustion of different IP addresses. It has been observed that
classless addressing is much more useful and practical as compared to that of classful
addressing (Beard, Stallings, & Tahiliani, 2016).
Furthermore, in classful addressing of IPv4, both the host ID and network ID can be
changed on the basis of the classes. Contrary, within classless addressing, no boundary on
changes into host ID and network ID is found which is exactly opposite from classful
addressing (Gilchrist, 2019).
Answer 2
In this context, a block into class A typically owns an address that is too large for
every organization. It means that most of the addresses present in class A are wasted and
hence not used. In addition, a block within class C is possibly also small for almost any
organization. Additionally, class A subnet is having 24 bits worth of addressing that is
adequate for 17 million individual devices. In this way, most of the entities own a small
fraction of such number of devices, therefore such addresses are not utilised by the
companies (Stallings, Brown, Bauer, & Bhattacharjee, 2012).
Answer 3
A mask in IPv4 addressing is also known as a subnet mask which usually masks the
network portion of a system’s IP address. The subnet mask leaves the host part like the
machine identifier. It has been found that mask in IPv4 uses a similar format like an IPv4
1
IT NETWORKING AND COMMUNICATION
Answer 1
In IPv4, there are two types of addressing include classless and classful. In the context
of classful addressing, usually an IP address allocation methodology is used. This addressing
typically allocates IP addressed as per the pre-defined five major classes. It has been found
that classful addressing is less useful as well as less practical as compared to that of classless
addressing (Liu & Chen, 2009). On the other hand, in classless addressing an IP address used
for the allocation. Such allocation is usually designed for replacing classful addressing in
order to minimize the early exhaustion of different IP addresses. It has been observed that
classless addressing is much more useful and practical as compared to that of classful
addressing (Beard, Stallings, & Tahiliani, 2016).
Furthermore, in classful addressing of IPv4, both the host ID and network ID can be
changed on the basis of the classes. Contrary, within classless addressing, no boundary on
changes into host ID and network ID is found which is exactly opposite from classful
addressing (Gilchrist, 2019).
Answer 2
In this context, a block into class A typically owns an address that is too large for
every organization. It means that most of the addresses present in class A are wasted and
hence not used. In addition, a block within class C is possibly also small for almost any
organization. Additionally, class A subnet is having 24 bits worth of addressing that is
adequate for 17 million individual devices. In this way, most of the entities own a small
fraction of such number of devices, therefore such addresses are not utilised by the
companies (Stallings, Brown, Bauer, & Bhattacharjee, 2012).
Answer 3
A mask in IPv4 addressing is also known as a subnet mask which usually masks the
network portion of a system’s IP address. The subnet mask leaves the host part like the
machine identifier. It has been found that mask in IPv4 uses a similar format like an IPv4
Management
2
address. For instance, the 4 different sections of 1-3 numbers are separated by dots (Dillon,
Wu, & Chang, 2010).
In this context, a mask in IPv4 contains two parts from which one part recognizes the
network and on the other hand, the second part classifies the particular host or machine in the
network. In other words, it can be said that subnet masks (IPv4) generally used to identify the
wide range of IP addresses that make up a subnet, on a single network (Bi, Zeng, & Zhang,
2016).
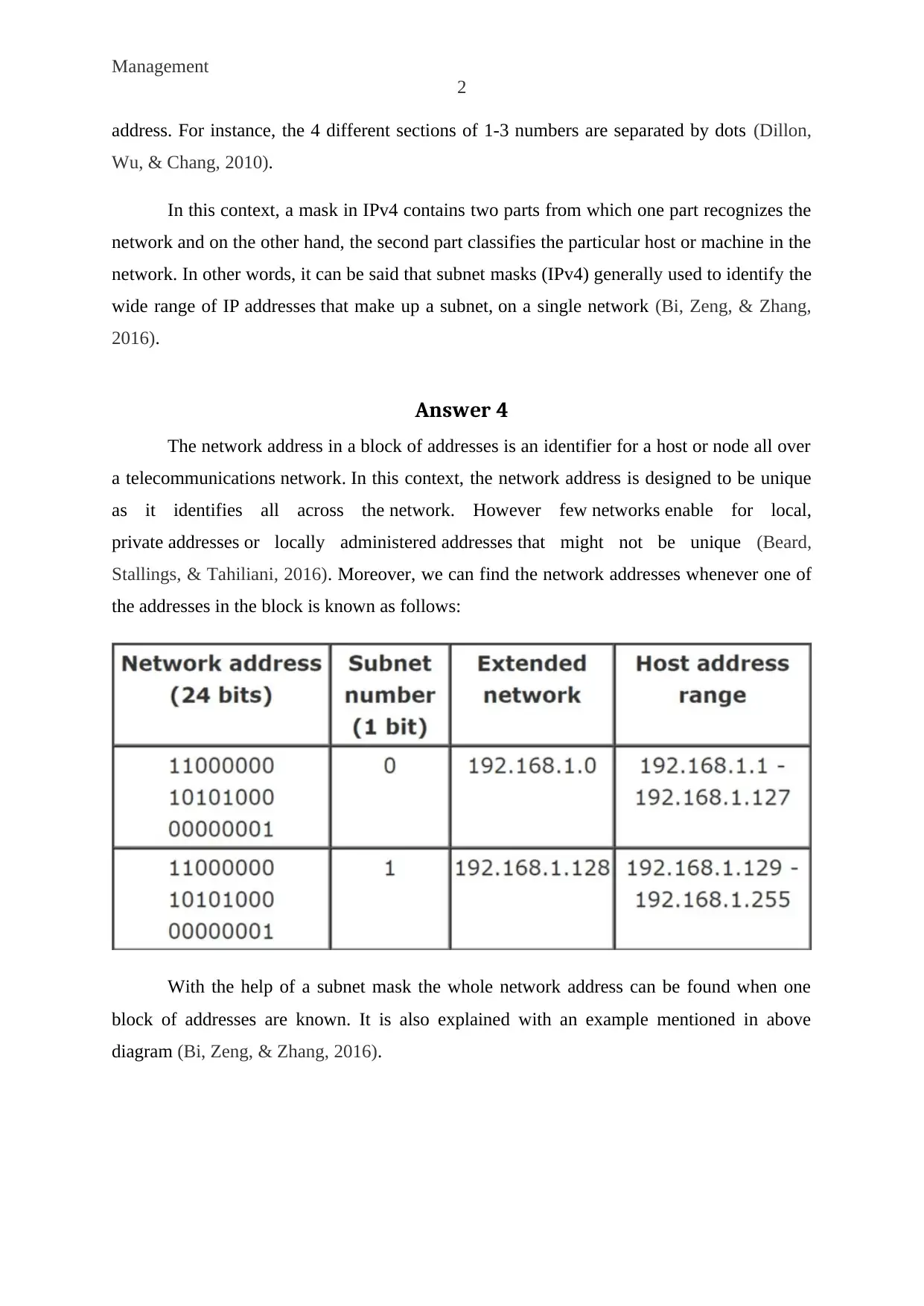
Answer 4
The network address in a block of addresses is an identifier for a host or node all over
a telecommunications network. In this context, the network address is designed to be unique
as it identifies all across the network. However few networks enable for local,
private addresses or locally administered addresses that might not be unique (Beard,
Stallings, & Tahiliani, 2016). Moreover, we can find the network addresses whenever one of
the addresses in the block is known as follows:
With the help of a subnet mask the whole network address can be found when one
block of addresses are known. It is also explained with an example mentioned in above
diagram (Bi, Zeng, & Zhang, 2016).
2
address. For instance, the 4 different sections of 1-3 numbers are separated by dots (Dillon,
Wu, & Chang, 2010).
In this context, a mask in IPv4 contains two parts from which one part recognizes the
network and on the other hand, the second part classifies the particular host or machine in the
network. In other words, it can be said that subnet masks (IPv4) generally used to identify the
wide range of IP addresses that make up a subnet, on a single network (Bi, Zeng, & Zhang,
2016).
Answer 4
The network address in a block of addresses is an identifier for a host or node all over
a telecommunications network. In this context, the network address is designed to be unique
as it identifies all across the network. However few networks enable for local,
private addresses or locally administered addresses that might not be unique (Beard,
Stallings, & Tahiliani, 2016). Moreover, we can find the network addresses whenever one of
the addresses in the block is known as follows:
With the help of a subnet mask the whole network address can be found when one
block of addresses are known. It is also explained with an example mentioned in above
diagram (Bi, Zeng, & Zhang, 2016).

Management
3
Answer 5
In order to define subnetting, it can be seen as the practice of separating a network
into 2 or more than 2 smaller networks. It has been found that subnetting hikes routing
efficiency. In addition to that, it also enhances the network security and thereby decreases the
whole size of broadcast domain (Tiwana & Konsynski, 2010). In general, the IP addresses are
segmented into classes include A, B, and C. In this context, default masks for these classes
are:
Subsequently, an individual may use the network from their classes A, B or C
networks as per their requirements. Here, when alteration is done by with the help of
subnetting then it is known as subnet mask. Moreover, subnetting enables one to create
multiple logical networks that already exist into a single class B, A or C network. Subnet
masks are created by subnetting process which can be illustrated like dividing house with
building walls into rooms of distinct sizes on the basis of the requirements (Stallings, Brown,
Bauer, & Bhattacharjee, 2012).
Answer 6
In general, NAT is used whenever the number of IP addresses is restricted. In other
words, whenever the host system is linked to the network with the help of a non-Ethernet
adapter then NAT is utilised (Liu & Chen, 2009). With the help of NAT, a virtual machine
can make use of several standard TCP/IP protocols for connecting to the other machines
across the exterior network. In the context of address depletion, NAT acts as a provisional
solution in order to circumvent the problem and thereby support IPv4 address
reusability. Moreover, whenever a host having a private IP address desires to communicate
with a server exterior their private network, then NAT uses the public IP address for address
depletion (De Toni, 2016).
3
Answer 5
In order to define subnetting, it can be seen as the practice of separating a network
into 2 or more than 2 smaller networks. It has been found that subnetting hikes routing
efficiency. In addition to that, it also enhances the network security and thereby decreases the
whole size of broadcast domain (Tiwana & Konsynski, 2010). In general, the IP addresses are
segmented into classes include A, B, and C. In this context, default masks for these classes
are:
Subsequently, an individual may use the network from their classes A, B or C
networks as per their requirements. Here, when alteration is done by with the help of
subnetting then it is known as subnet mask. Moreover, subnetting enables one to create
multiple logical networks that already exist into a single class B, A or C network. Subnet
masks are created by subnetting process which can be illustrated like dividing house with
building walls into rooms of distinct sizes on the basis of the requirements (Stallings, Brown,
Bauer, & Bhattacharjee, 2012).
Answer 6
In general, NAT is used whenever the number of IP addresses is restricted. In other
words, whenever the host system is linked to the network with the help of a non-Ethernet
adapter then NAT is utilised (Liu & Chen, 2009). With the help of NAT, a virtual machine
can make use of several standard TCP/IP protocols for connecting to the other machines
across the exterior network. In the context of address depletion, NAT acts as a provisional
solution in order to circumvent the problem and thereby support IPv4 address
reusability. Moreover, whenever a host having a private IP address desires to communicate
with a server exterior their private network, then NAT uses the public IP address for address
depletion (De Toni, 2016).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Management
4
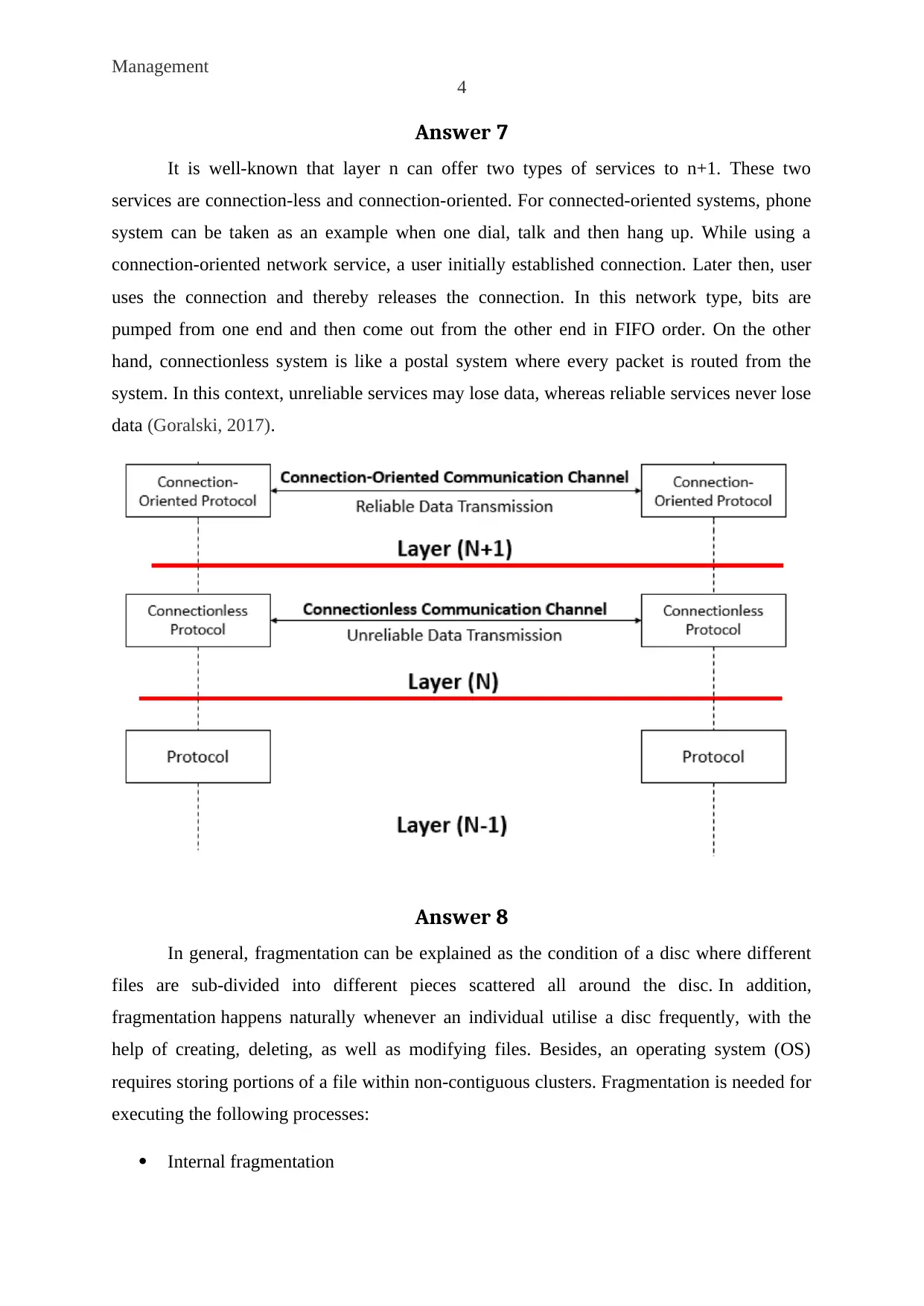
Answer 7
It is well-known that layer n can offer two types of services to n+1. These two
services are connection-less and connection-oriented. For connected-oriented systems, phone
system can be taken as an example when one dial, talk and then hang up. While using a
connection-oriented network service, a user initially established connection. Later then, user
uses the connection and thereby releases the connection. In this network type, bits are
pumped from one end and then come out from the other end in FIFO order. On the other
hand, connectionless system is like a postal system where every packet is routed from the
system. In this context, unreliable services may lose data, whereas reliable services never lose
data (Goralski, 2017).
Answer 8
In general, fragmentation can be explained as the condition of a disc where different
files are sub-divided into different pieces scattered all around the disc. In addition,
fragmentation happens naturally whenever an individual utilise a disc frequently, with the
help of creating, deleting, as well as modifying files. Besides, an operating system (OS)
requires storing portions of a file within non-contiguous clusters. Fragmentation is needed for
executing the following processes:
Internal fragmentation
4
Answer 7
It is well-known that layer n can offer two types of services to n+1. These two
services are connection-less and connection-oriented. For connected-oriented systems, phone
system can be taken as an example when one dial, talk and then hang up. While using a
connection-oriented network service, a user initially established connection. Later then, user
uses the connection and thereby releases the connection. In this network type, bits are
pumped from one end and then come out from the other end in FIFO order. On the other
hand, connectionless system is like a postal system where every packet is routed from the
system. In this context, unreliable services may lose data, whereas reliable services never lose
data (Goralski, 2017).
Answer 8
In general, fragmentation can be explained as the condition of a disc where different
files are sub-divided into different pieces scattered all around the disc. In addition,
fragmentation happens naturally whenever an individual utilise a disc frequently, with the
help of creating, deleting, as well as modifying files. Besides, an operating system (OS)
requires storing portions of a file within non-contiguous clusters. Fragmentation is needed for
executing the following processes:
Internal fragmentation

Management
5
External fragmentation
Data fragmentation (Bi, Zeng, & Zhang, 2016).
Answer 9
There are three key strategies that can be used while moving from IPv4 to IPv6. The
three strategies are as follows:
1. Dual-stack strategy: here both the IPv4 and IPv6 coexist within the similar networks
or devices
2. Tunnelling strategy: here encapsulation of the IPv6 network is done into IPv4 packets
3. Translation strategy: here NAT-PT translation is used
Tunnelling strategy Dual-stack strategy
This strategy is able to communicate with the
remotely available IPv6 network. Besides,
such strategy loads on the router without
supporting IPv6 within an ISP network.
However, some problems like fragmentation
and MTU size issue are associated with this
(Stallings, Brown, Bauer, & Bhattacharjee,
2012).
This strategy is easy-to-use which can
communicate with all hosts. The dual-stack
strategy uses two separate protocols that are
running over single machine which consumes
memory and CPU power (Vacca, 2012).
Answer 10
There are few common addresses mapping protocols which are typically used in
different scenarios, as follows:
TCP/IP protocol suite
DHCP
ARP
DNS
HTTP
FTP
ICMP
5
External fragmentation
Data fragmentation (Bi, Zeng, & Zhang, 2016).
Answer 9
There are three key strategies that can be used while moving from IPv4 to IPv6. The
three strategies are as follows:
1. Dual-stack strategy: here both the IPv4 and IPv6 coexist within the similar networks
or devices
2. Tunnelling strategy: here encapsulation of the IPv6 network is done into IPv4 packets
3. Translation strategy: here NAT-PT translation is used
Tunnelling strategy Dual-stack strategy
This strategy is able to communicate with the
remotely available IPv6 network. Besides,
such strategy loads on the router without
supporting IPv6 within an ISP network.
However, some problems like fragmentation
and MTU size issue are associated with this
(Stallings, Brown, Bauer, & Bhattacharjee,
2012).
This strategy is easy-to-use which can
communicate with all hosts. The dual-stack
strategy uses two separate protocols that are
running over single machine which consumes
memory and CPU power (Vacca, 2012).
Answer 10
There are few common addresses mapping protocols which are typically used in
different scenarios, as follows:
TCP/IP protocol suite
DHCP
ARP
DNS
HTTP
FTP
ICMP

Management
6
HTTPS
IGMP
NTP
UDP
TLS
TFTP
TCP
SSH
SNMP2/3
SMTP
SIP
RTP
POP3
IMAP4
Out of all aforementioned protocols, most common protocols are:
TCP/IP protocol is the set of communications protocols that are typically utilised for
the Internet as well as other similar networks.
The FTP protocol is a standard internet protocol that is used to transmit files amid
computers on the internet all across TCP/IP connections.
HTTP is used to access web content, which is now replaced by HTTPS.
HTTPS is a secure version of HTTP which is now usually utilised for accessing
website content.
TLS protocol is an updated version of the Secure Sockets Layer (SSL) (Stallings,
Brown, Bauer, & Bhattacharjee, 2012).
Answer 11
ICMP is the protocol which stands for Internet Control Message. It is an error-
reporting protocol in which network devices like routers utilise for generating error messages
towards the source IP address. In addition to that, ICMP forms as well as sends messages
towards the source IP address. The ICMP is used by the routers, hosts, intermediary devices
in order to convey error info or other updates to the rest hosts, intermediary devices and
routers as well (Comer, 2018).
6
HTTPS
IGMP
NTP
UDP
TLS
TFTP
TCP
SSH
SNMP2/3
SMTP
SIP
RTP
POP3
IMAP4
Out of all aforementioned protocols, most common protocols are:
TCP/IP protocol is the set of communications protocols that are typically utilised for
the Internet as well as other similar networks.
The FTP protocol is a standard internet protocol that is used to transmit files amid
computers on the internet all across TCP/IP connections.
HTTP is used to access web content, which is now replaced by HTTPS.
HTTPS is a secure version of HTTP which is now usually utilised for accessing
website content.
TLS protocol is an updated version of the Secure Sockets Layer (SSL) (Stallings,
Brown, Bauer, & Bhattacharjee, 2012).
Answer 11
ICMP is the protocol which stands for Internet Control Message. It is an error-
reporting protocol in which network devices like routers utilise for generating error messages
towards the source IP address. In addition to that, ICMP forms as well as sends messages
towards the source IP address. The ICMP is used by the routers, hosts, intermediary devices
in order to convey error info or other updates to the rest hosts, intermediary devices and
routers as well (Comer, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Management
7
Furthermore, ICMP is also utilised for executing DDoS (denial-of-service) attacks
with the help of directing an IP packet which is larger than the total number of bytes passed
by the IP protocols (Stallings, Brown, Bauer, & Bhattacharjee, 2012).
Answer 12
In general, an autonomous system (AS) can be seen as a collection of inter-connected
Internet Protocol (IP) routing prefixes. It usually happens under the control of single or more
network operators. In addition, the AS typically works under a common administrative
domain. It has been found that IGPs function in an AS while EGPs also inter-links different
Ass simultaneously (Tiwana & Konsynski, 2010).
Answer 13
The RIP (Routing Information Protocol), can be explained as a dynamic protocol
which is used to identify the best path or route from end-to-end. In other words, RIP finds a
path from source to destination all across a network with the help of using a routing count
algorithm. In this context, such algorithm is utilised to define the shortest path through the
source-to-destination that enables the data to be delivered at very high-speed within shortest
time. The purpose of RIP can be defined as offering the shortest as well as best-suited way
for data to take from node-to-node (Vacca, 2012).
Answer 14
In the context of RIP message, it is typically used by a router for requesting and
receiving routing info about an AS or for sharing knowledge periodically with their
neighbors. It has been found that RIP acts like a distance-vector-routing-protocol while using
7
Furthermore, ICMP is also utilised for executing DDoS (denial-of-service) attacks
with the help of directing an IP packet which is larger than the total number of bytes passed
by the IP protocols (Stallings, Brown, Bauer, & Bhattacharjee, 2012).
Answer 12
In general, an autonomous system (AS) can be seen as a collection of inter-connected
Internet Protocol (IP) routing prefixes. It usually happens under the control of single or more
network operators. In addition, the AS typically works under a common administrative
domain. It has been found that IGPs function in an AS while EGPs also inter-links different
Ass simultaneously (Tiwana & Konsynski, 2010).
Answer 13
The RIP (Routing Information Protocol), can be explained as a dynamic protocol
which is used to identify the best path or route from end-to-end. In other words, RIP finds a
path from source to destination all across a network with the help of using a routing count
algorithm. In this context, such algorithm is utilised to define the shortest path through the
source-to-destination that enables the data to be delivered at very high-speed within shortest
time. The purpose of RIP can be defined as offering the shortest as well as best-suited way
for data to take from node-to-node (Vacca, 2012).
Answer 14
In the context of RIP message, it is typically used by a router for requesting and
receiving routing info about an AS or for sharing knowledge periodically with their
neighbors. It has been found that RIP acts like a distance-vector-routing-protocol while using
Management
8
UDP packets in order to exchange info via port 520 (Goralski, 2017). Therefore, RIP
message:
Requests
Respond to requests (Dynerowicz & Mendes, 2017).
Start-up router and triggers update
Lastly, sends updates at regular intervals
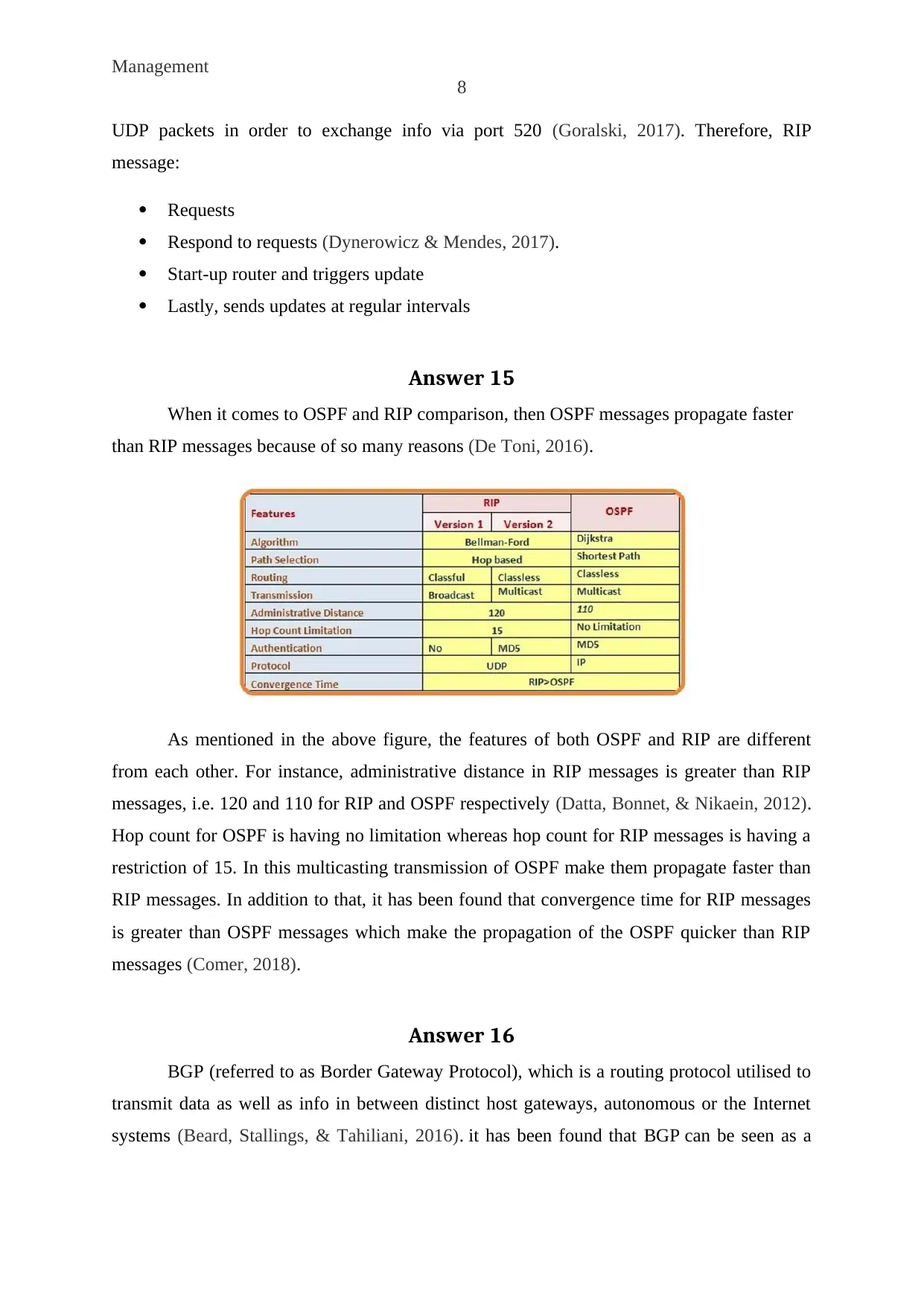
Answer 15
When it comes to OSPF and RIP comparison, then OSPF messages propagate faster
than RIP messages because of so many reasons (De Toni, 2016).
As mentioned in the above figure, the features of both OSPF and RIP are different
from each other. For instance, administrative distance in RIP messages is greater than RIP
messages, i.e. 120 and 110 for RIP and OSPF respectively (Datta, Bonnet, & Nikaein, 2012).
Hop count for OSPF is having no limitation whereas hop count for RIP messages is having a
restriction of 15. In this multicasting transmission of OSPF make them propagate faster than
RIP messages. In addition to that, it has been found that convergence time for RIP messages
is greater than OSPF messages which make the propagation of the OSPF quicker than RIP
messages (Comer, 2018).
Answer 16
BGP (referred to as Border Gateway Protocol), which is a routing protocol utilised to
transmit data as well as info in between distinct host gateways, autonomous or the Internet
systems (Beard, Stallings, & Tahiliani, 2016). it has been found that BGP can be seen as a
8
UDP packets in order to exchange info via port 520 (Goralski, 2017). Therefore, RIP
message:
Requests
Respond to requests (Dynerowicz & Mendes, 2017).
Start-up router and triggers update
Lastly, sends updates at regular intervals
Answer 15
When it comes to OSPF and RIP comparison, then OSPF messages propagate faster
than RIP messages because of so many reasons (De Toni, 2016).
As mentioned in the above figure, the features of both OSPF and RIP are different
from each other. For instance, administrative distance in RIP messages is greater than RIP
messages, i.e. 120 and 110 for RIP and OSPF respectively (Datta, Bonnet, & Nikaein, 2012).
Hop count for OSPF is having no limitation whereas hop count for RIP messages is having a
restriction of 15. In this multicasting transmission of OSPF make them propagate faster than
RIP messages. In addition to that, it has been found that convergence time for RIP messages
is greater than OSPF messages which make the propagation of the OSPF quicker than RIP
messages (Comer, 2018).
Answer 16
BGP (referred to as Border Gateway Protocol), which is a routing protocol utilised to
transmit data as well as info in between distinct host gateways, autonomous or the Internet
systems (Beard, Stallings, & Tahiliani, 2016). it has been found that BGP can be seen as a

Management
9
Path Vector Protocol (PVP), it upholds several paths towards different hosts, gateway routers,
networks and hence defines the routing decisions accordingly (Bi, Zeng, & Zhang, 2016).
Answer 17
The link-state and distance-vector routing methods can be compared and contrasted as
follows:
Link State Routing-Protocol
It is used to avoid the convergence as well as loop problems of Distance Vector
protocols
In this context, routers direct updates which advertise the state of the links.
Here, the cost is the metric which is used to calculate routes
Here, areas are usually utilised to determine which routers share updates with one
other
In this protocol, routers know the state of all possible links in their nearby field
Here, the routers utilise distinct tables for maintaining an understanding of the Link-
States
o Neighbour table - list of neighbour routers and the interface (Liu & Chen,
2009).
o Shortest-Path table – is the best route to every particular destination
o Topology table
Convergence is fast (Gilchrist, 2019).
It can utilise more RAM as well as CPU resources
Loops are usually averted
Distance-Vector-Routing-Protocols
For this protocol, distance is a major metric used to calculate routes
9
Path Vector Protocol (PVP), it upholds several paths towards different hosts, gateway routers,
networks and hence defines the routing decisions accordingly (Bi, Zeng, & Zhang, 2016).
Answer 17
The link-state and distance-vector routing methods can be compared and contrasted as
follows:
Link State Routing-Protocol
It is used to avoid the convergence as well as loop problems of Distance Vector
protocols
In this context, routers direct updates which advertise the state of the links.
Here, the cost is the metric which is used to calculate routes
Here, areas are usually utilised to determine which routers share updates with one
other
In this protocol, routers know the state of all possible links in their nearby field
Here, the routers utilise distinct tables for maintaining an understanding of the Link-
States
o Neighbour table - list of neighbour routers and the interface (Liu & Chen,
2009).
o Shortest-Path table – is the best route to every particular destination
o Topology table
Convergence is fast (Gilchrist, 2019).
It can utilise more RAM as well as CPU resources
Loops are usually averted
Distance-Vector-Routing-Protocols
For this protocol, distance is a major metric used to calculate routes
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Management
10
o IGRP uses bandwidth and delay
o RIP uses hop count (Gollmann, 2010).
This is slower to converge as it has to wait for the periodic updates
Distance-Vector Protocols are RIP, IGRP
More susceptible to loops (Dillon, Wu, & Chang, 2010).
Routers rely on neighbours for route information
10
o IGRP uses bandwidth and delay
o RIP uses hop count (Gollmann, 2010).
This is slower to converge as it has to wait for the periodic updates
Distance-Vector Protocols are RIP, IGRP
More susceptible to loops (Dillon, Wu, & Chang, 2010).
Routers rely on neighbours for route information

Management
11
References
Beard, C., Stallings, W., & Tahiliani, M. (2016). Wireless communication networks and
systems. UK: Pearson Education Limited.
Bi, S., Zeng, Y., & Zhang, R. (2016). Wireless powered communication networks: An
overview. IEEE Wireless Communications, 23(2), 10-18.
Comer, D. (2018). The Internet book: everything you need to know about computer
networking and how the Internet works. New York: Chapman and Hall/CRC.
Datta, S., Bonnet, C., & Nikaein, N. (2012). Android power management: Current and future
trends. Enabling Technologies for Smartphone and Internet of Things, 1, 48-53.
De Toni, A. (2016). The network evolution from extended enterprise to virtual enterprise. In
International Operations Management (pp. 74-95). UK: Routledge.
Dillon, T., Wu, C., & Chang, E. (2010). Cloud computing: issues and challenges. Advanced
Information Networking and Applications (AINA), 2010 24th IEEE International
Conference, IEEE, 27-33.
Dynerowicz, S., & Mendes, P. (2017). Named data networking in Opportunistic Networks.
Berlin: ICN.
Gilchrist, A. (2019). The well-connected community: A networking approach to community
development. UK: Policy Press.
Gollmann, D. (2010). Computer Security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), 544-554.
Goralski, W. (2017). The illustrated network: how TCP/IP works in a modern network.
London: Morgan Kaufmann.
Liu, C., & Chen, H. (2009). Network Attached Storage. U.S. Patent Application, 29(250),
435.
Stallings, W., Brown, L., Bauer, M., & Bhattacharjee, A. (2012). Computer security:
principles and practice. NJ: Pearson Education.
11
References
Beard, C., Stallings, W., & Tahiliani, M. (2016). Wireless communication networks and
systems. UK: Pearson Education Limited.
Bi, S., Zeng, Y., & Zhang, R. (2016). Wireless powered communication networks: An
overview. IEEE Wireless Communications, 23(2), 10-18.
Comer, D. (2018). The Internet book: everything you need to know about computer
networking and how the Internet works. New York: Chapman and Hall/CRC.
Datta, S., Bonnet, C., & Nikaein, N. (2012). Android power management: Current and future
trends. Enabling Technologies for Smartphone and Internet of Things, 1, 48-53.
De Toni, A. (2016). The network evolution from extended enterprise to virtual enterprise. In
International Operations Management (pp. 74-95). UK: Routledge.
Dillon, T., Wu, C., & Chang, E. (2010). Cloud computing: issues and challenges. Advanced
Information Networking and Applications (AINA), 2010 24th IEEE International
Conference, IEEE, 27-33.
Dynerowicz, S., & Mendes, P. (2017). Named data networking in Opportunistic Networks.
Berlin: ICN.
Gilchrist, A. (2019). The well-connected community: A networking approach to community
development. UK: Policy Press.
Gollmann, D. (2010). Computer Security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), 544-554.
Goralski, W. (2017). The illustrated network: how TCP/IP works in a modern network.
London: Morgan Kaufmann.
Liu, C., & Chen, H. (2009). Network Attached Storage. U.S. Patent Application, 29(250),
435.
Stallings, W., Brown, L., Bauer, M., & Bhattacharjee, A. (2012). Computer security:
principles and practice. NJ: Pearson Education.

Management
12
Tiwana, A., & Konsynski, B. (2010). Complementarities between organizational IT
architecture and governance structure. Information Systems Research, 21(2), 288-304.
Vacca, J. (2012). Computer and information security handbook. London: Newnes.
12
Tiwana, A., & Konsynski, B. (2010). Complementarities between organizational IT
architecture and governance structure. Information Systems Research, 21(2), 288-304.
Vacca, J. (2012). Computer and information security handbook. London: Newnes.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





