Cybersecurity Risks and Privacy Policies
VerifiedAdded on 2020/02/24
|14
|3028
|316
AI Summary
This assignment analyzes the growing threat of cybersecurity risks in businesses, particularly focusing on data breaches and consumer privacy. It examines the importance of implementing robust privacy policies to protect sensitive information and build trust with customers. The analysis delves into the positive impacts of privacy policies, including enhanced brand reputation, reduced legal liabilities, and improved customer relationships. Furthermore, it explores real-world examples of cybersecurity incidents and their consequences, highlighting the need for proactive risk management strategies.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

MANAGEMENT OF INFORMATION SECURITY: PRIVACY
POLICY
1
POLICY
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Executive summary
Security vulnerabilities are common these days and thus there is an immense need for
organizations to indulge into practices that can complement their security standards. In this study
the main idea of security vulnerability as well as relevant aspects associated with this concept
has been discussed. Main emphasis has been laid on privacy policies that are essential for
maintaining safety of information security. Theoritical frameworks associated with information
security system have been considered and possible reasons for increased security breaches have
also been discussed. Finally, recommendations have been provided and conclusion has been
drawn out.
2
Security vulnerabilities are common these days and thus there is an immense need for
organizations to indulge into practices that can complement their security standards. In this study
the main idea of security vulnerability as well as relevant aspects associated with this concept
has been discussed. Main emphasis has been laid on privacy policies that are essential for
maintaining safety of information security. Theoritical frameworks associated with information
security system have been considered and possible reasons for increased security breaches have
also been discussed. Finally, recommendations have been provided and conclusion has been
drawn out.
2

Table of contents
Introduction......................................................................................................................................4
Findings...........................................................................................................................................4
Security issues faced by business organization and measures adopted to tackle those...................4
Theoretical frameworks for security management..........................................................................6
Analysis...........................................................................................................................................8
Impact of security breach on business values..................................................................................8
Potentiality of proper privacy policies...........................................................................................10
Recommendations..........................................................................................................................10
Conclusion.....................................................................................................................................12
Reference list.................................................................................................................................13
Appendix........................................................................................................................................15
3
Introduction......................................................................................................................................4
Findings...........................................................................................................................................4
Security issues faced by business organization and measures adopted to tackle those...................4
Theoretical frameworks for security management..........................................................................6
Analysis...........................................................................................................................................8
Impact of security breach on business values..................................................................................8
Potentiality of proper privacy policies...........................................................................................10
Recommendations..........................................................................................................................10
Conclusion.....................................................................................................................................12
Reference list.................................................................................................................................13
Appendix........................................................................................................................................15
3

Introduction
In the current era, almost each and every business firm uses digital standards to maintain
company data, MIS records and customer as well as service records. In such type of digital
maintenance standards, security vulnerabilities are natural, as any information that goes online
poses a risk regarding theft or manipulation. Vulnerabilities can be of two types, with risk and
without risks. Potential company information that may affect company value can be considered
as vulnerability with risk, while information that does not affect any company operation, are
vulnerabilities without risks. Privacy policies for a business organization has been considered for
this study to discuss about issues as well as existing Australian privacy policies for those issues.
Finally recommendations have been provided and conclusion has been drawn out from the same.
Findings
Security issues faced by business organization and measures adopted to tackle
those
With emerging trend of digitalized world, issues regarding security breach and leakage of
information have also increased. From 2015 to present number of cyber security incidents have
increased considerably. Rate of phishing increased to about 31%, ransomware to 15%,
unauthorized disclosure of information to 36% and denial of service to about 4% (Allen &
Peloza, 2015, p. 640).
4
In the current era, almost each and every business firm uses digital standards to maintain
company data, MIS records and customer as well as service records. In such type of digital
maintenance standards, security vulnerabilities are natural, as any information that goes online
poses a risk regarding theft or manipulation. Vulnerabilities can be of two types, with risk and
without risks. Potential company information that may affect company value can be considered
as vulnerability with risk, while information that does not affect any company operation, are
vulnerabilities without risks. Privacy policies for a business organization has been considered for
this study to discuss about issues as well as existing Australian privacy policies for those issues.
Finally recommendations have been provided and conclusion has been drawn out from the same.
Findings
Security issues faced by business organization and measures adopted to tackle
those
With emerging trend of digitalized world, issues regarding security breach and leakage of
information have also increased. From 2015 to present number of cyber security incidents have
increased considerably. Rate of phishing increased to about 31%, ransomware to 15%,
unauthorized disclosure of information to 36% and denial of service to about 4% (Allen &
Peloza, 2015, p. 640).
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Figure 1: Rise of security breaches
(Source: Allen & Peloza, 2015, p. 641)
Several companies have been victims of theft of information and customers have been part of
denial of service and unauthorized disclosure.
In 2016, several social media platforms and online service providers faced security breach issues.
For example, in 2016, many yahoo accounts got hacked which led Yahoo owners to warn users
for theft of information. Concerned people of Yahoo came to know about such phishing
incidents when several people reported about email spam and hack of bank accounts. On
December 2016, Yahoo updated and enforced security guidelines for strict maintenance of
customers’ account (news.com.au, 2017).
On March 2016, Snapchat experienced biggest security breach and ethical dilemma ever. Ethical
dilemma came into limelight when an internal employee admitted to have disclosed unauthorized
information to an outsider. Information regarding valuable data was leaked which led to hacking
of customer accounts that in turn led to exposure of several video as well as image files online.
Almost 121 million accounts were hacked worldwide and almost 100,000 video as well as image
file was exposed online (nbcnews.com, 2017).
As a result of this incident, Snapchat CEO Evan Spiegel posted an apology on social media
websites and informed about a bug that led to this massive breach of data security. This company
went into legal troubles and went on to install strict security protocols like secure socket layer,
transport layer security, secure HTTP and secure Email (Almorsy et al. 2016, p. 5).
Pretty Good Privacy (PHP) privacy standard, a public-key cryptosystem is a popular protocol
nowadays for business ventures which delve into digital practices mostly (Altuhhov et al. 2013,
p.110). This system helps to indicate authenticity of digital signature, codes and user accounts
which helps to prevent malwares in a system.
Security breaches are not only observed in digital platforms but also in physical ones. For
example in 2016, Woolworth faced massive privacy threats when it found out the existence of
whistle blowers within the company. Before Anzac day, their internal plans for Anzac day offers
got leaked and this led to the failure of the entire plan (news.com.au, 2017).
Privacy policies needed to operate a safe business
5
(Source: Allen & Peloza, 2015, p. 641)
Several companies have been victims of theft of information and customers have been part of
denial of service and unauthorized disclosure.
In 2016, several social media platforms and online service providers faced security breach issues.
For example, in 2016, many yahoo accounts got hacked which led Yahoo owners to warn users
for theft of information. Concerned people of Yahoo came to know about such phishing
incidents when several people reported about email spam and hack of bank accounts. On
December 2016, Yahoo updated and enforced security guidelines for strict maintenance of
customers’ account (news.com.au, 2017).
On March 2016, Snapchat experienced biggest security breach and ethical dilemma ever. Ethical
dilemma came into limelight when an internal employee admitted to have disclosed unauthorized
information to an outsider. Information regarding valuable data was leaked which led to hacking
of customer accounts that in turn led to exposure of several video as well as image files online.
Almost 121 million accounts were hacked worldwide and almost 100,000 video as well as image
file was exposed online (nbcnews.com, 2017).
As a result of this incident, Snapchat CEO Evan Spiegel posted an apology on social media
websites and informed about a bug that led to this massive breach of data security. This company
went into legal troubles and went on to install strict security protocols like secure socket layer,
transport layer security, secure HTTP and secure Email (Almorsy et al. 2016, p. 5).
Pretty Good Privacy (PHP) privacy standard, a public-key cryptosystem is a popular protocol
nowadays for business ventures which delve into digital practices mostly (Altuhhov et al. 2013,
p.110). This system helps to indicate authenticity of digital signature, codes and user accounts
which helps to prevent malwares in a system.
Security breaches are not only observed in digital platforms but also in physical ones. For
example in 2016, Woolworth faced massive privacy threats when it found out the existence of
whistle blowers within the company. Before Anzac day, their internal plans for Anzac day offers
got leaked and this led to the failure of the entire plan (news.com.au, 2017).
Privacy policies needed to operate a safe business
5

As stated in the Australian Privacy Principles (APP), there are 13 basic principles that a business
can include in their policies. Most of the Australian public as well as private organizations that
have an annual income of more than $3000,000 are considered collectively as APP entities
which must abide by the regulations of Privacy Act 1988 (Andress & Winterfeld, 2013, p.50).
Some of the basic principles have been stated by Australian Privacy principle (2017);
Principle 1:
A business must familiarize itself with privacy policies as well as people associated with privacy
norms.
Principle 2:
A business must consider the design of privacy before setting up a business
Principle 3:
A business need to maintain integrity of data collected from common people and deal with them
in an open transparent manner
Principle 4:
If there is an involvement of platforms which may expose customer information, then these
platforms must provide an option of anonymity to the customers
Principle 5:
An APP covered entity must collect information from people that are necessary for a business.
A business venture must let people know about certain aspects of information that are being
collected from customers or common people.
Principle 6:
Companies must keep their privacy policies updated and also must let people know about
information that needs to be shared with third party members (Australian Privacy principle,
2017).
Principle 7:
Security principles must be imposed on company assets as well as working procedures,
especially security maintenance procedures that may help to cope up with security issues. Users’
privacy must be kept intact with the help of government principles
6
can include in their policies. Most of the Australian public as well as private organizations that
have an annual income of more than $3000,000 are considered collectively as APP entities
which must abide by the regulations of Privacy Act 1988 (Andress & Winterfeld, 2013, p.50).
Some of the basic principles have been stated by Australian Privacy principle (2017);
Principle 1:
A business must familiarize itself with privacy policies as well as people associated with privacy
norms.
Principle 2:
A business must consider the design of privacy before setting up a business
Principle 3:
A business need to maintain integrity of data collected from common people and deal with them
in an open transparent manner
Principle 4:
If there is an involvement of platforms which may expose customer information, then these
platforms must provide an option of anonymity to the customers
Principle 5:
An APP covered entity must collect information from people that are necessary for a business.
A business venture must let people know about certain aspects of information that are being
collected from customers or common people.
Principle 6:
Companies must keep their privacy policies updated and also must let people know about
information that needs to be shared with third party members (Australian Privacy principle,
2017).
Principle 7:
Security principles must be imposed on company assets as well as working procedures,
especially security maintenance procedures that may help to cope up with security issues. Users’
privacy must be kept intact with the help of government principles
6

Theoretical frameworks for security management
Most of the frameworks on security management have been drafted by the guidance from APP
principles, which is based on a common concept of imposing securities regarding availability of
information and maintenance of data.
Information security TRIAD
This TRIAD model is based on three basic aspects namely Availability, Integrity and
confidentiality of information. Confidentiality is the process in which restricts free access of
information, while integrity is the assurance that all information are trustworthy. Availability is
the process which ensures accessibility of information by authorized people (Baskerville et al.
2014, p. 148).
Figure 2: Information security TRIAD
(Source: Baskerville et al. 2014, p. 150)
Business ventures need to comply with these procedures for maintaining proper security
management.
Layered onion security model
Layered onion model or Defense in Depth (DiD) is a security assurance procedure, which
involve multiple security controls as well as Information Technology (IT) systems.
Outer layers generally contain firewalls, middle layers contain security controls and in centre
remains the data that needs to be protected (Biener et al. 2015, p. 152).
7
Most of the frameworks on security management have been drafted by the guidance from APP
principles, which is based on a common concept of imposing securities regarding availability of
information and maintenance of data.
Information security TRIAD
This TRIAD model is based on three basic aspects namely Availability, Integrity and
confidentiality of information. Confidentiality is the process in which restricts free access of
information, while integrity is the assurance that all information are trustworthy. Availability is
the process which ensures accessibility of information by authorized people (Baskerville et al.
2014, p. 148).
Figure 2: Information security TRIAD
(Source: Baskerville et al. 2014, p. 150)
Business ventures need to comply with these procedures for maintaining proper security
management.
Layered onion security model
Layered onion model or Defense in Depth (DiD) is a security assurance procedure, which
involve multiple security controls as well as Information Technology (IT) systems.
Outer layers generally contain firewalls, middle layers contain security controls and in centre
remains the data that needs to be protected (Biener et al. 2015, p. 152).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 3: Onion security model
(Source: Biener et al. 2015, p. 153)
Business dealings that involve digital platforms generally make use of this onion model to
mitigate risks regarding the breach of data. The steps typically include involvement of physical
security, network security, prevention of unauthorised access, guard information, detect malware
or bugs and mitigate risk by appropriate protocols.
Analysis
Breach of security involves potential risks as leak of confidential as well as customer data not
only affect reputation of companies but also affect the relationship between a company and its
potential stakeholders.
Impact of security breach on business values
In the recent years, due to increasing risks regarding security breach, impact has been detected in
six different categories. Reputation and brand damage accounts to 29%, loss of productivity up
to 21%, revenue losses up to 19%, forensics up to 12%, technical support of about 10% and
compliance regulatory measures 8% (Chang et al. 2014, p. 40).
8
(Source: Biener et al. 2015, p. 153)
Business dealings that involve digital platforms generally make use of this onion model to
mitigate risks regarding the breach of data. The steps typically include involvement of physical
security, network security, prevention of unauthorised access, guard information, detect malware
or bugs and mitigate risk by appropriate protocols.
Analysis
Breach of security involves potential risks as leak of confidential as well as customer data not
only affect reputation of companies but also affect the relationship between a company and its
potential stakeholders.
Impact of security breach on business values
In the recent years, due to increasing risks regarding security breach, impact has been detected in
six different categories. Reputation and brand damage accounts to 29%, loss of productivity up
to 21%, revenue losses up to 19%, forensics up to 12%, technical support of about 10% and
compliance regulatory measures 8% (Chang et al. 2014, p. 40).
8

Figure 4: Impact of security breach on six different areas
(Source: Chang et al. 2014, p. 41)
According to Corones & Davis (2017, p. 70), social media platforms lose millions of users
within a day due to security breaches. For example Snapchat lost 12 million users when its
security breach scandal came into limelight in 2016. Yahoo was found to lose its pace back in
2016 due to mass account hacking scandal. Woolworth failed to collect enough revenue on
Anzac day, rather Coles; a potential competitor of Woolworths emerged as a superior retail chain
(news.com.au, 2017).
Over the past 12 years, rate of security breaches has increased mainly due to involvement of
innovative technological methods. Some other relevant reasons that have been found in cases
associated with security breaches are stated by Seo & Kim (2015, p. 1580):
Technical failure
Failure of technologies is inevitable as minor bugs in the system can hamper an entire system.
Majority of companies imply complex technologies but does not stay aware of software involved
in the system.
No perimeter for protection
As per the guidelines of APP, a company needs to design its security standards before involving
any kind of operations, which most of the companies fail to apply (Wu et al. 2014, p. 6).
Lack of layered defense
Onion model suggests the use of security at each level of storing or processing information
which is helpful to safeguard valuable information from the attack of potential hackers. Mostly
companies ignore the importance of this system and end up becoming a victim of cyber attacks.
9
(Source: Chang et al. 2014, p. 41)
According to Corones & Davis (2017, p. 70), social media platforms lose millions of users
within a day due to security breaches. For example Snapchat lost 12 million users when its
security breach scandal came into limelight in 2016. Yahoo was found to lose its pace back in
2016 due to mass account hacking scandal. Woolworth failed to collect enough revenue on
Anzac day, rather Coles; a potential competitor of Woolworths emerged as a superior retail chain
(news.com.au, 2017).
Over the past 12 years, rate of security breaches has increased mainly due to involvement of
innovative technological methods. Some other relevant reasons that have been found in cases
associated with security breaches are stated by Seo & Kim (2015, p. 1580):
Technical failure
Failure of technologies is inevitable as minor bugs in the system can hamper an entire system.
Majority of companies imply complex technologies but does not stay aware of software involved
in the system.
No perimeter for protection
As per the guidelines of APP, a company needs to design its security standards before involving
any kind of operations, which most of the companies fail to apply (Wu et al. 2014, p. 6).
Lack of layered defense
Onion model suggests the use of security at each level of storing or processing information
which is helpful to safeguard valuable information from the attack of potential hackers. Mostly
companies ignore the importance of this system and end up becoming a victim of cyber attacks.
9

Lack of new tactics to safeguard information
Day by day with the involvement of complex ICT techniques old techniques get obsolete and
more vulnerable to security threats. It is thus an impeccable need for business ventures to update
technologies in a regular basis to mitigate risks in future.
Human failure
Sometimes threats exist within an organization which makes it necessary for organizations to
keep a track of internal employees. Whistleblowers not only breach privacy concerns but also
breach ethical codes and thus when internal whistleblowers expose internal company planning or
procedures, brand value and ethical dilemma both gets affected.
Potentiality of proper privacy policies
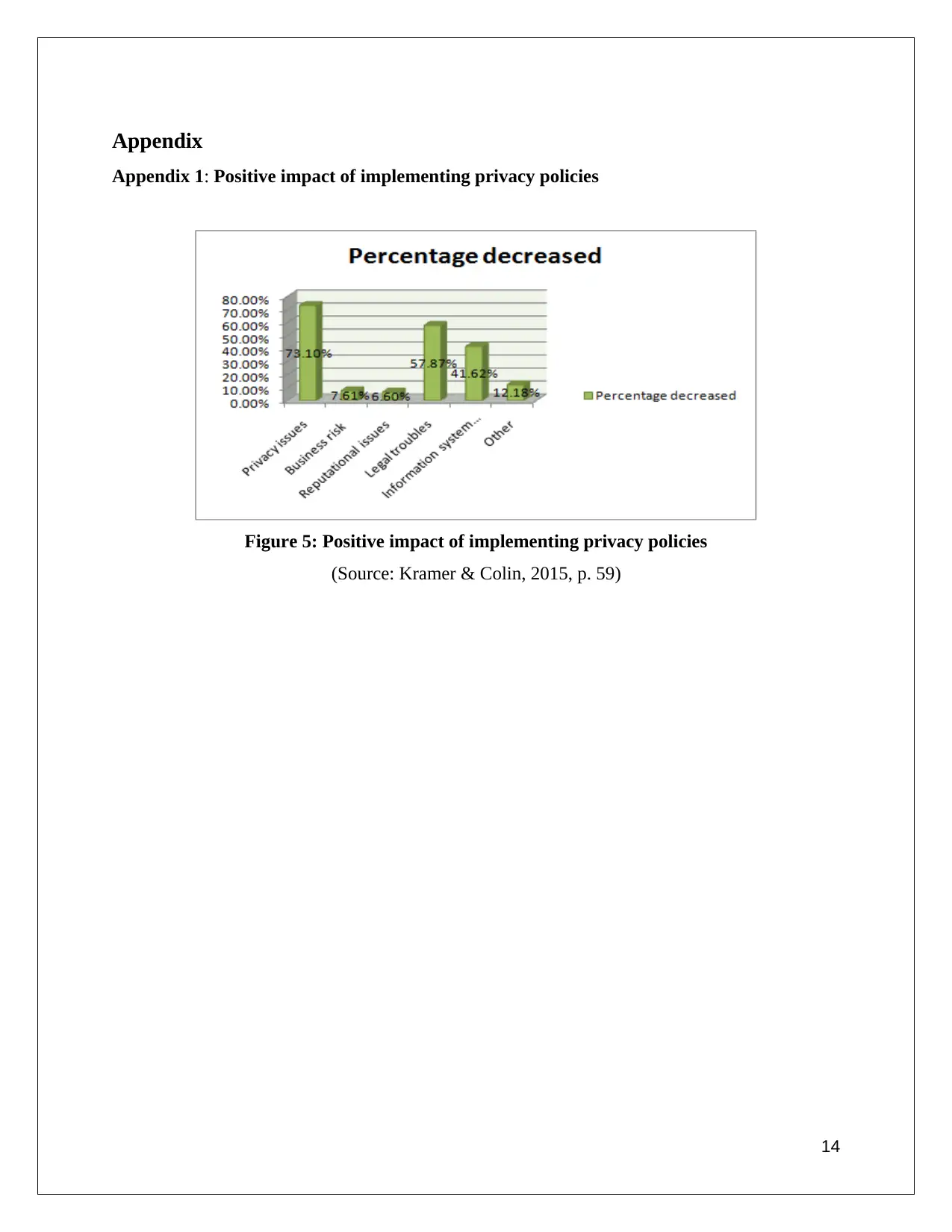
As Internet of Things (IoT) has become omnipresent, it is important to follow privacy policies as
it helps to avoid legal troubles. It has been shown by cyber risk federal regulations that
compliance of privacy policies with company standards lowers the risk of privacy issues by
73.10%, business risks by 7.61%, reputational issues by 6.60%, legal troubles by 57.87%,
information system issues by 41.62% and other minor risks by 12.18% (refer to appendix 1).
Most beneficial aspect of implementing privacy policies within an organization is the mitigation
of legal risks even if security issues occur. Governmental guidelines also open opportunities for
getting help in times of security issues. Moreover if APP guidelines are followed properly with
the adjudication of theoretical frameworks, then privacy issues and information system issues
also get reduced (Harris & Patten, 2014, p. 110).
Recommendations
Proper maintenance of security by abiding APP guidelines
Abiding each and every principle in APP is not necessary, but involvement of relevant principles
might help to avoid legal as well as ethical dilemmas.
Use of layered security system
Use of security standards in every level of storage as well as processing of data help to mitigate
data theft and manipulation at a considerable extent.
Privacy training to employees
Privacy training must be provided to employees in order to avoid operational and internal issues
(Corones & Davis, 2017, p. 70).
10
Day by day with the involvement of complex ICT techniques old techniques get obsolete and
more vulnerable to security threats. It is thus an impeccable need for business ventures to update
technologies in a regular basis to mitigate risks in future.
Human failure
Sometimes threats exist within an organization which makes it necessary for organizations to
keep a track of internal employees. Whistleblowers not only breach privacy concerns but also
breach ethical codes and thus when internal whistleblowers expose internal company planning or
procedures, brand value and ethical dilemma both gets affected.
Potentiality of proper privacy policies
As Internet of Things (IoT) has become omnipresent, it is important to follow privacy policies as
it helps to avoid legal troubles. It has been shown by cyber risk federal regulations that
compliance of privacy policies with company standards lowers the risk of privacy issues by
73.10%, business risks by 7.61%, reputational issues by 6.60%, legal troubles by 57.87%,
information system issues by 41.62% and other minor risks by 12.18% (refer to appendix 1).
Most beneficial aspect of implementing privacy policies within an organization is the mitigation
of legal risks even if security issues occur. Governmental guidelines also open opportunities for
getting help in times of security issues. Moreover if APP guidelines are followed properly with
the adjudication of theoretical frameworks, then privacy issues and information system issues
also get reduced (Harris & Patten, 2014, p. 110).
Recommendations
Proper maintenance of security by abiding APP guidelines
Abiding each and every principle in APP is not necessary, but involvement of relevant principles
might help to avoid legal as well as ethical dilemmas.
Use of layered security system
Use of security standards in every level of storage as well as processing of data help to mitigate
data theft and manipulation at a considerable extent.
Privacy training to employees
Privacy training must be provided to employees in order to avoid operational and internal issues
(Corones & Davis, 2017, p. 70).
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Conclusion
Vulnerability of information is very natural as well as inevitable in current scenario, where
technologies get new appearances in a day to day format. While there are technologies to protect
information, there are certain technical ways to break into security systems too. In order to be
precise, it is impossible to restrict security issues completely, but there are some legal guidelines
which can help to mitigate risks. It is therefore a mandate for companies to look into their
privacy standards properly and abide by APP guidelines to avoid legal or moral problems. In
future if companies devote their time to improve their security standards, security issues can be
prevented.
11
Vulnerability of information is very natural as well as inevitable in current scenario, where
technologies get new appearances in a day to day format. While there are technologies to protect
information, there are certain technical ways to break into security systems too. In order to be
precise, it is impossible to restrict security issues completely, but there are some legal guidelines
which can help to mitigate risks. It is therefore a mandate for companies to look into their
privacy standards properly and abide by APP guidelines to avoid legal or moral problems. In
future if companies devote their time to improve their security standards, security issues can be
prevented.
11

Reference list
Allen, A.M. & Peloza, J., 2015. ‘Someone to watch over me: The integration of privacy and
corporate social responsibility’. Business Horizons, vol. 58, no. 6, pp.635-642.
Almorsy, M., Grundy, J. & Müller, I., 2016. ‘An analysis of the cloud computing security
problem’. arXiv preprint arXiv:1609.01107. vol. 22, no. 1, pp.1-6
Altuhhov, O., Matulevičius, R. & Ahmed, N., 2013. ‘An extension of business process model
and notation for security risk management’. International Journal of Information System
Modeling and Design (IJISMD), vol. 4, no. 4, pp.93-113.
Andress, J. & Winterfeld, S., 2013. ‘Cyber warfare: techniques, tactics and tools for security
practitioners’. 3rd edn, Elsevier, Amsterdam.
Australian Privacy principle, 2017. Guide to developing an APP privacy policy| Office of the
Australian Information Commissioner - OAIC. Oaic.gov.au. Available at:
<https://www.oaic.gov.au/agencies-and-organisations/guides/guide-to-developing-an-app-
privacy-policy> [Accessed on 23 Aug. 2017].
Baskerville, R., Spagnoletti, P. & Kim, J., 2014. ‘Incident-centered information security:
Managing a strategic balance between prevention and response’. Information &
Management, vol. 51, no. 1, pp.138-151.
BAYLY, L., 2017. Snapchat Got Phished: Employee Bank Details, IDs, Compromised. NBC
News. Available at: <https://www.nbcnews.com/tech/tech-news/snapchat-hacked-again-
employee-bank-details-ids-phished-n527866> [Accessed on 23 Aug. 2017].
Biener, C., Eling, M. & Wirfs, J.H., 2015. ‘Insurability of cyber risk: An empirical analysis’. The
Geneva Papers on Risk and Insurance Issues and Practice, vol. 40, no.1, pp.131-158.
Chang, V., Kuo, Y.H. & Ramachandran, M., 2016. ‘Cloud computing adoption framework: A
security framework for business clouds’. Future Generation Computer Systems, vol. 57, no. 1,
pp.24-41.
Chung, F., 2017. Woolies let off the hook over Anzac breaches. NewsComAu. Available at:
<http://www.news.com.au/finance/business/retail/woolies-let-off-the-hook-over-anzac-day-
breaches/news-story/f6b74b1ce0139a7213cf6f83bfbb0c51> [Accessed on 23 Aug. 2017].
Corones, S. & Davis, J., 2017. ‘Protecting Consumer Privacy and Data Security: Regulatory
Challenges and Potential Future Directions’. Fed. L. Rev., vol. 45, no. 1, pp.65-75.
12
Allen, A.M. & Peloza, J., 2015. ‘Someone to watch over me: The integration of privacy and
corporate social responsibility’. Business Horizons, vol. 58, no. 6, pp.635-642.
Almorsy, M., Grundy, J. & Müller, I., 2016. ‘An analysis of the cloud computing security
problem’. arXiv preprint arXiv:1609.01107. vol. 22, no. 1, pp.1-6
Altuhhov, O., Matulevičius, R. & Ahmed, N., 2013. ‘An extension of business process model
and notation for security risk management’. International Journal of Information System
Modeling and Design (IJISMD), vol. 4, no. 4, pp.93-113.
Andress, J. & Winterfeld, S., 2013. ‘Cyber warfare: techniques, tactics and tools for security
practitioners’. 3rd edn, Elsevier, Amsterdam.
Australian Privacy principle, 2017. Guide to developing an APP privacy policy| Office of the
Australian Information Commissioner - OAIC. Oaic.gov.au. Available at:
<https://www.oaic.gov.au/agencies-and-organisations/guides/guide-to-developing-an-app-
privacy-policy> [Accessed on 23 Aug. 2017].
Baskerville, R., Spagnoletti, P. & Kim, J., 2014. ‘Incident-centered information security:
Managing a strategic balance between prevention and response’. Information &
Management, vol. 51, no. 1, pp.138-151.
BAYLY, L., 2017. Snapchat Got Phished: Employee Bank Details, IDs, Compromised. NBC
News. Available at: <https://www.nbcnews.com/tech/tech-news/snapchat-hacked-again-
employee-bank-details-ids-phished-n527866> [Accessed on 23 Aug. 2017].
Biener, C., Eling, M. & Wirfs, J.H., 2015. ‘Insurability of cyber risk: An empirical analysis’. The
Geneva Papers on Risk and Insurance Issues and Practice, vol. 40, no.1, pp.131-158.
Chang, V., Kuo, Y.H. & Ramachandran, M., 2016. ‘Cloud computing adoption framework: A
security framework for business clouds’. Future Generation Computer Systems, vol. 57, no. 1,
pp.24-41.
Chung, F., 2017. Woolies let off the hook over Anzac breaches. NewsComAu. Available at:
<http://www.news.com.au/finance/business/retail/woolies-let-off-the-hook-over-anzac-day-
breaches/news-story/f6b74b1ce0139a7213cf6f83bfbb0c51> [Accessed on 23 Aug. 2017].
Corones, S. & Davis, J., 2017. ‘Protecting Consumer Privacy and Data Security: Regulatory
Challenges and Potential Future Directions’. Fed. L. Rev., vol. 45, no. 1, pp.65-75.
12

Dawson, M., 2015. New threats and countermeasures in digital crime and cyber terrorism. 2nd
edn, IGI Global, New York.
Harris, M. & P. Patten, K., 2014. ‘Mobile device security considerations for small-and medium-
sized enterprise business mobility’. Information Management & Computer Security, vol. 22, no.
1, pp.97-114.
Kramer, H. & Colin Walter, I.S.G., 2015. ‘The Influence of Software Vulnerabilities on Business
Risks’. Technical Report, vol. 1, no. 1, pp. 5-60.
Michalos, A.C., 2017. ‘The impact of trust on business, international security and the quality of
life’. How Good Policies and Business Ethics Enhance Good Quality of Life, vol. 2, no. 3, pp.
127-153.
Privacy Policy, 2017. Privacy Policy. Standards.org.au. Available at:
<http://www.standards.org.au/Pages/privacy.aspx> [Accessed on 23 Aug. 2017].
Seo, D.J. & Kim, T.S., 2015. ‘Influence of Personal Information Security Vulnerabilities and
Perceived Usefulness on Bank CustomersWillingness to Stay’. The Journal of Korean Institute
of Communications and Information Sciences, vol. 40, no. 8, pp.1577-1587.
Wu, D.D., Chen, S.H. & Olson, D.L., 2014. ‘Business intelligence in risk management: Some
recent progresses’. Information Sciences, vol. 256, no. 12, pp.1-7.
13
edn, IGI Global, New York.
Harris, M. & P. Patten, K., 2014. ‘Mobile device security considerations for small-and medium-
sized enterprise business mobility’. Information Management & Computer Security, vol. 22, no.
1, pp.97-114.
Kramer, H. & Colin Walter, I.S.G., 2015. ‘The Influence of Software Vulnerabilities on Business
Risks’. Technical Report, vol. 1, no. 1, pp. 5-60.
Michalos, A.C., 2017. ‘The impact of trust on business, international security and the quality of
life’. How Good Policies and Business Ethics Enhance Good Quality of Life, vol. 2, no. 3, pp.
127-153.
Privacy Policy, 2017. Privacy Policy. Standards.org.au. Available at:
<http://www.standards.org.au/Pages/privacy.aspx> [Accessed on 23 Aug. 2017].
Seo, D.J. & Kim, T.S., 2015. ‘Influence of Personal Information Security Vulnerabilities and
Perceived Usefulness on Bank CustomersWillingness to Stay’. The Journal of Korean Institute
of Communications and Information Sciences, vol. 40, no. 8, pp.1577-1587.
Wu, D.D., Chen, S.H. & Olson, D.L., 2014. ‘Business intelligence in risk management: Some
recent progresses’. Information Sciences, vol. 256, no. 12, pp.1-7.
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Appendix
Appendix 1: Positive impact of implementing privacy policies
Figure 5: Positive impact of implementing privacy policies
(Source: Kramer & Colin, 2015, p. 59)
14
Appendix 1: Positive impact of implementing privacy policies
Figure 5: Positive impact of implementing privacy policies
(Source: Kramer & Colin, 2015, p. 59)
14
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



