COMP9812: Mobile Operating Systems Security Comparison and Analysis
VerifiedAdded on 2023/06/04
|9
|2300
|438
Report
AI Summary
This report provides a detailed comparison of security features in mobile operating systems, focusing on Android, iOS, BlackBerry, and Windows. It examines access control options, encryption methods, and security architectures, highlighting the strengths and weaknesses of each OS. The report also discusses vulnerability management, application provenance, and built-in security standards. While BlackBerry is considered highly secure, followed by Apple's iOS, Android is noted for its open-source nature, which makes it more prone to malware. The report concludes that each operating system has its security issues and requires a selective approach to safeguard mobile access, recommending the use of Transport Layer Security for data protection. Desklib offers similar reports and study resources for students.

REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Security: Compare the security available in mobile operating systems and identify which is
most secure.
most secure.
Contents
Introduction......................................................................................................................................3
Comparison of the security available in mobile operating systems................................................3
Conclusion.......................................................................................................................................6
References........................................................................................................................................6
Appendices......................................................................................................................................7
Introduction......................................................................................................................................3
Comparison of the security available in mobile operating systems................................................3
Conclusion.......................................................................................................................................6
References........................................................................................................................................6
Appendices......................................................................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
In the early times, it has been seen that the mobile phones were only capable of sending and then
receiving the text messages for the communication purpose. With the growing technology and
the advancement in the present times, the mobile phones have become a major necessity of the
people. For these, the various mobile operating systems like Android, iOS, Windows, Sailfish,
Ubuntu etc. are available in different smart phones. The smartphones have been able to carry the
different features of the digital devices which is considered to be a common phone feature and
the smartphones along with tablets have been able to enter into this arena. The mobile operating
systems is considered to be the skeleton which helps in running and managing the programs in
the computer which is then loaded by booting a program (Enck et al., 2014). The system is a
base infrastructure which is for running on mobile devices and a software platform for
developers to create various programs or applications that are run and managed by mobile OS.
The mobile operating system is considered to be the base infrastructure software program which
is designed to run on mobile devices with software platform. Here, the developers are also able
to create different programs and the applications that are easy to run and be managed by the
mobile OS. It holds the different operating systems, where the Google Android and Apple IOS
has been growing strong with time and regular updates (Johnston et al., 2015).
Comparison of the security available in mobile operating
systems
There are different security measures which are important to be mapped for handling and
addressing the business risks. Some of them are:
a. Apple iOS: Considering the security issues, the mobile has access control options with
PIN, passcode and the fingerprints where the MDM configurable PIN or passcode
policies help in handling the encryption of the device with iPhone 3GS+. There is no SD
card encryption but removes the encryption keys with remote wiping.
b. Google Android: The access control options are for the PIN, passcode and the swipe
where the Face Lock is also applicable for it. Here, MDM configurable PIN or the
passcode policies are there with full device encryption that is for selecting the tables and
the phones for Android 3+ and Android 4+ (Succi et al., 2018). The OEM proprietary
In the early times, it has been seen that the mobile phones were only capable of sending and then
receiving the text messages for the communication purpose. With the growing technology and
the advancement in the present times, the mobile phones have become a major necessity of the
people. For these, the various mobile operating systems like Android, iOS, Windows, Sailfish,
Ubuntu etc. are available in different smart phones. The smartphones have been able to carry the
different features of the digital devices which is considered to be a common phone feature and
the smartphones along with tablets have been able to enter into this arena. The mobile operating
systems is considered to be the skeleton which helps in running and managing the programs in
the computer which is then loaded by booting a program (Enck et al., 2014). The system is a
base infrastructure which is for running on mobile devices and a software platform for
developers to create various programs or applications that are run and managed by mobile OS.
The mobile operating system is considered to be the base infrastructure software program which
is designed to run on mobile devices with software platform. Here, the developers are also able
to create different programs and the applications that are easy to run and be managed by the
mobile OS. It holds the different operating systems, where the Google Android and Apple IOS
has been growing strong with time and regular updates (Johnston et al., 2015).
Comparison of the security available in mobile operating
systems
There are different security measures which are important to be mapped for handling and
addressing the business risks. Some of them are:
a. Apple iOS: Considering the security issues, the mobile has access control options with
PIN, passcode and the fingerprints where the MDM configurable PIN or passcode
policies help in handling the encryption of the device with iPhone 3GS+. There is no SD
card encryption but removes the encryption keys with remote wiping.
b. Google Android: The access control options are for the PIN, passcode and the swipe
where the Face Lock is also applicable for it. Here, MDM configurable PIN or the
passcode policies are there with full device encryption that is for selecting the tables and
the phones for Android 3+ and Android 4+ (Succi et al., 2018). The OEM proprietary
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
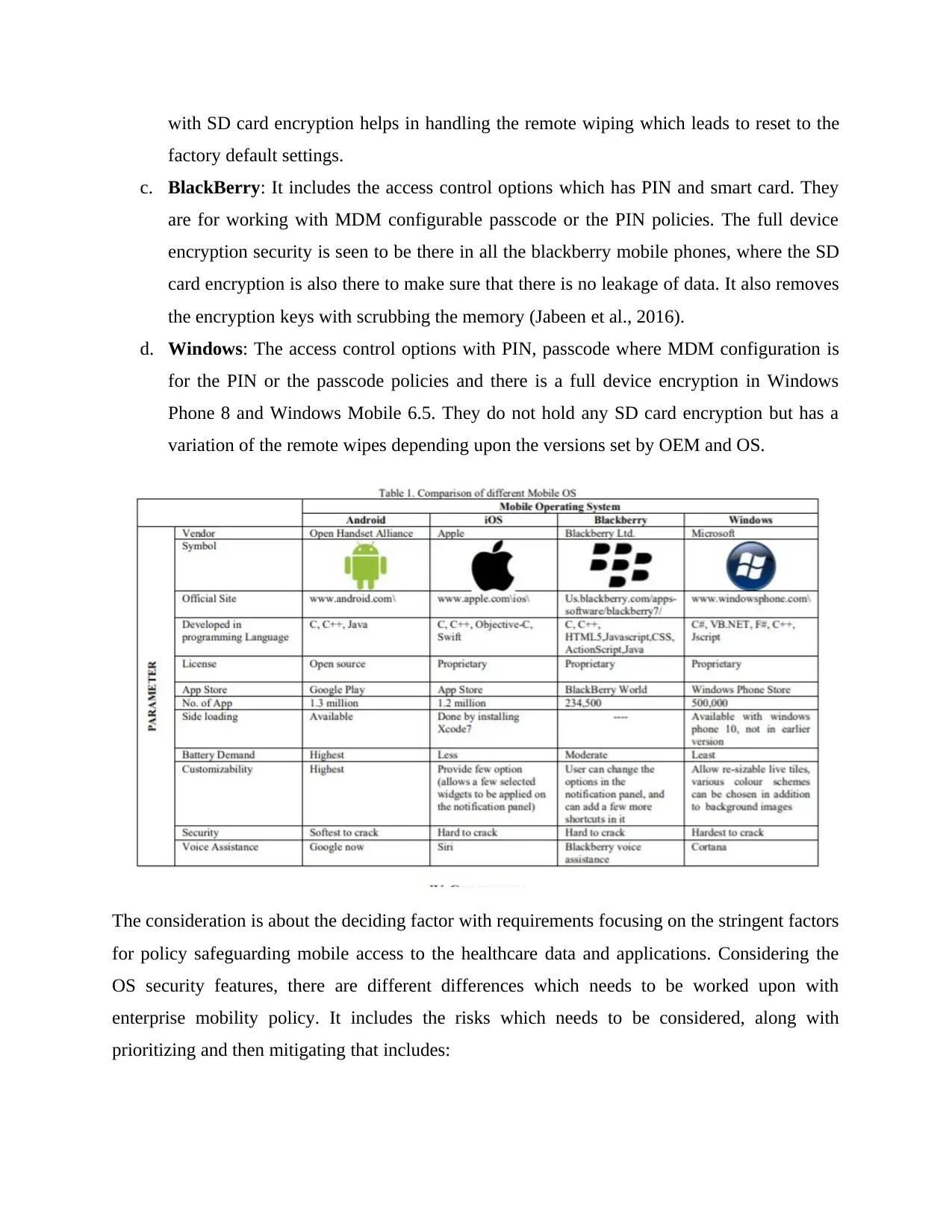
with SD card encryption helps in handling the remote wiping which leads to reset to the
factory default settings.
c. BlackBerry: It includes the access control options which has PIN and smart card. They
are for working with MDM configurable passcode or the PIN policies. The full device
encryption security is seen to be there in all the blackberry mobile phones, where the SD
card encryption is also there to make sure that there is no leakage of data. It also removes
the encryption keys with scrubbing the memory (Jabeen et al., 2016).
d. Windows: The access control options with PIN, passcode where MDM configuration is
for the PIN or the passcode policies and there is a full device encryption in Windows
Phone 8 and Windows Mobile 6.5. They do not hold any SD card encryption but has a
variation of the remote wipes depending upon the versions set by OEM and OS.
The consideration is about the deciding factor with requirements focusing on the stringent factors
for policy safeguarding mobile access to the healthcare data and applications. Considering the
OS security features, there are different differences which needs to be worked upon with
enterprise mobility policy. It includes the risks which needs to be considered, along with
prioritizing and then mitigating that includes:
factory default settings.
c. BlackBerry: It includes the access control options which has PIN and smart card. They
are for working with MDM configurable passcode or the PIN policies. The full device
encryption security is seen to be there in all the blackberry mobile phones, where the SD
card encryption is also there to make sure that there is no leakage of data. It also removes
the encryption keys with scrubbing the memory (Jabeen et al., 2016).
d. Windows: The access control options with PIN, passcode where MDM configuration is
for the PIN or the passcode policies and there is a full device encryption in Windows
Phone 8 and Windows Mobile 6.5. They do not hold any SD card encryption but has a
variation of the remote wipes depending upon the versions set by OEM and OS.
The consideration is about the deciding factor with requirements focusing on the stringent factors
for policy safeguarding mobile access to the healthcare data and applications. Considering the
OS security features, there are different differences which needs to be worked upon with
enterprise mobility policy. It includes the risks which needs to be considered, along with
prioritizing and then mitigating that includes:

a. The security architecture where mobile OSes tend to make use of sandboxing methods
with insulation of the applications from one to the other kernel. They are able to consider
the features of disabling that could be exploited through the mobile malware or there is a
leakage in the data like the shared or the removable storage (Sinha et al., 2016).
b. The permission modes with OSes requires that the users are able to grant the requested
permission for the applications with default permissions and the variations in prompting.
The users might need the help to monitor and then detect about the over-reaching
applications which tend to pose the risks more than the benefits.
c. The vulnerability management is set over-the-air OS updates which is considered to be
common and the updates are depending upon working on the models and the carrier
which is important for the enforcement of the minimized versions.
d. Application provenance is about how the vendors are able to handle the tight control of
the applications that can easily be installed. Here, the others notices that Google is able to
work on the reactive stances that leads to promoting the malware. The consideration is
about disabling the options that let the users promote the malware. The focus is on the
disabling of the options that lets the users to install the unsigned data applications from
the unofficial application stores. This directly leads to monitor the installation of
applications to properly detect and then remove the malware.
e. The built-in security standards are considered to be holding the major control, where
OSes works with the built-in basic security factors where the support settings tend to
vary. Hence, the verification is about how the device supporting mobile policy technical
requirements and defining mandatory optional settings for different kinds of devices.
It is seen that for the proper security setup, one can make use of the Transport Layer Security to
protect the data. The operating system malware resistance depends on public app store
provenance, where the users have the ability to install the apps sideloaded from a lesser
trustworthy sites and the permissions are granted for installing the apps. The example is that
Apple exerts a major control on iTunes App store and then prevent the users from any type of the
sideloading. Here, the public apps are not reviewed or signed by Apple (Feizollah et al., 2015).
Hence, the effective malware deterrent is then compared to Google Play Store Oversized with
allowing the Android malware to blossom. The malware does exploit a new vulnerability where
there are short patch flows which are found to be associated to the Apple and RIM manufactured
with insulation of the applications from one to the other kernel. They are able to consider
the features of disabling that could be exploited through the mobile malware or there is a
leakage in the data like the shared or the removable storage (Sinha et al., 2016).
b. The permission modes with OSes requires that the users are able to grant the requested
permission for the applications with default permissions and the variations in prompting.
The users might need the help to monitor and then detect about the over-reaching
applications which tend to pose the risks more than the benefits.
c. The vulnerability management is set over-the-air OS updates which is considered to be
common and the updates are depending upon working on the models and the carrier
which is important for the enforcement of the minimized versions.
d. Application provenance is about how the vendors are able to handle the tight control of
the applications that can easily be installed. Here, the others notices that Google is able to
work on the reactive stances that leads to promoting the malware. The consideration is
about disabling the options that let the users promote the malware. The focus is on the
disabling of the options that lets the users to install the unsigned data applications from
the unofficial application stores. This directly leads to monitor the installation of
applications to properly detect and then remove the malware.
e. The built-in security standards are considered to be holding the major control, where
OSes works with the built-in basic security factors where the support settings tend to
vary. Hence, the verification is about how the device supporting mobile policy technical
requirements and defining mandatory optional settings for different kinds of devices.
It is seen that for the proper security setup, one can make use of the Transport Layer Security to
protect the data. The operating system malware resistance depends on public app store
provenance, where the users have the ability to install the apps sideloaded from a lesser
trustworthy sites and the permissions are granted for installing the apps. The example is that
Apple exerts a major control on iTunes App store and then prevent the users from any type of the
sideloading. Here, the public apps are not reviewed or signed by Apple (Feizollah et al., 2015).
Hence, the effective malware deterrent is then compared to Google Play Store Oversized with
allowing the Android malware to blossom. The malware does exploit a new vulnerability where
there are short patch flows which are found to be associated to the Apple and RIM manufactured
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

devices that reduce the risks. The difficulty is to handle the security standards and then work
with the grade for the simple comparison of the mobile operating system security. BlackBerry
Phones are considered to be most secured devices which are then followed by Apple iPhones and
iPads. The latest versions of the mobile operating systems are able to support the encryption of
the latest file system that can protect the user and application data which has been stored on the
mobile devices. It is seen that the mobile devices require a proper selective approach with
avoiding the Windows Phone 7 & Android devices which are not able to support this policy
(Conroy et al., 2014).
All the operating systems have security issues at a certain level. If the malicious user has a
physical access to the different devices or attack which is made over the network, or through
email, then Android is considered to be easiest for the use with softest target. iPhone and then the
older versions of Blackberry are considered to be security focused which have different and
unique unlocking methods that make it very secure. Android is one of the open source that
introduces the malware issues and there are different bugs in the system as well. The android
users do not encounter any issue mainly they do not download anything apart from the Play
Store. Hence, Android is considered to be the least secured device mainly because it is open
source. The Apple phones have the security of devices with using Touch ID where the tight lapse
on the applications and the ability to push the updates out to the deices help in quick functioning.
This is a major advantage over Android, Windows and Blackberry.
Conclusion
The mobile operating systems has different features where the open source has a higher degree
of customization which is widespread with the use of Android OS. Along with this, there are
major peculiarities on how it is more prone to the bugs and the malware (Chen et al., 2016). The
iOS is considered to be the proprietary that helps in providing little options for the customization
process. Hence, there are launching of the updates on the addressing of security concerns which
is considered to be easy, comparatively. Blackberry and Microsoft phones are found to be bit
behind in the race mainly, but they are also coming up with the updates so resolve the existing
issues in the system.
with the grade for the simple comparison of the mobile operating system security. BlackBerry
Phones are considered to be most secured devices which are then followed by Apple iPhones and
iPads. The latest versions of the mobile operating systems are able to support the encryption of
the latest file system that can protect the user and application data which has been stored on the
mobile devices. It is seen that the mobile devices require a proper selective approach with
avoiding the Windows Phone 7 & Android devices which are not able to support this policy
(Conroy et al., 2014).
All the operating systems have security issues at a certain level. If the malicious user has a
physical access to the different devices or attack which is made over the network, or through
email, then Android is considered to be easiest for the use with softest target. iPhone and then the
older versions of Blackberry are considered to be security focused which have different and
unique unlocking methods that make it very secure. Android is one of the open source that
introduces the malware issues and there are different bugs in the system as well. The android
users do not encounter any issue mainly they do not download anything apart from the Play
Store. Hence, Android is considered to be the least secured device mainly because it is open
source. The Apple phones have the security of devices with using Touch ID where the tight lapse
on the applications and the ability to push the updates out to the deices help in quick functioning.
This is a major advantage over Android, Windows and Blackberry.
Conclusion
The mobile operating systems has different features where the open source has a higher degree
of customization which is widespread with the use of Android OS. Along with this, there are
major peculiarities on how it is more prone to the bugs and the malware (Chen et al., 2016). The
iOS is considered to be the proprietary that helps in providing little options for the customization
process. Hence, there are launching of the updates on the addressing of security concerns which
is considered to be easy, comparatively. Blackberry and Microsoft phones are found to be bit
behind in the race mainly, but they are also coming up with the updates so resolve the existing
issues in the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Awan, K.M., Waqar, M., Faseeh, M., Ullah, F. and Saleem, M.Q., 2017. Resource management
and security issues in mobile phone operating systems: A comparative analysis (No. e3344v1).
PeerJ Preprints.
Chen, M., Qian, Y., Mao, S., Tang, W. and Yang, X., 2016. Software-defined mobile networks
security. Mobile Networks and Applications, 21(5), pp.729-743.
Conroy, D.E., Yang, C.H. and Maher, J.P., 2014. Behavior change techniques in top-ranked
mobile apps for physical activity. American journal of preventive medicine, 46(6), pp.649-652.
Enck, W., Gilbert, P., Han, S., Tendulkar, V., Chun, B.G., Cox, L.P., Jung, J., McDaniel, P. and
Sheth, A.N., 2014. TaintDroid: an information-flow tracking system for realtime privacy
monitoring on smartphones. ACM Transactions on Computer Systems (TOCS), 32(2), p.5.
Feizollah, A., Anuar, N.B., Salleh, R. and Wahab, A.W.A., 2015. A review on feature selection
in mobile malware detection. Digital Investigation, 13, pp.22-37.
Jabeen, Q., Khan, F., Hayat, M.N., Khan, H., Jan, S.R. and Ullah, F., 2016. A Survey: Embedded
Systems Supporting By Different Operating Systems. arXiv preprint arXiv:1610.07899.
Johnston, M.J., King, D., Arora, S., Behar, N., Athanasiou, T., Sevdalis, N. and Darzi, A., 2015.
Smartphones let surgeons know WhatsApp: an analysis of communication in emergency surgical
teams. The American Journal of Surgery, 209(1), pp.45-51.
Sinha, A., Paul, N. and Devarajan, S., Zscaler Inc, 2016. Mobile device security, device
management, and policy enforcement in a cloud based system. U.S. Patent Application
15/154,328.
Succi, G. and Ivanov, V.V., 2018. Comparison of mobile operating systems based on models of
growth reliability of the software. Computer Research and Modeling, 10(3), pp.325-334.
Appendices
1. Awan et al., (2017) focuses on the security factors and the highlight which are related to
the IoS interfacing and the other mobile operating systems.
Awan, K.M., Waqar, M., Faseeh, M., Ullah, F. and Saleem, M.Q., 2017. Resource management
and security issues in mobile phone operating systems: A comparative analysis (No. e3344v1).
PeerJ Preprints.
Chen, M., Qian, Y., Mao, S., Tang, W. and Yang, X., 2016. Software-defined mobile networks
security. Mobile Networks and Applications, 21(5), pp.729-743.
Conroy, D.E., Yang, C.H. and Maher, J.P., 2014. Behavior change techniques in top-ranked
mobile apps for physical activity. American journal of preventive medicine, 46(6), pp.649-652.
Enck, W., Gilbert, P., Han, S., Tendulkar, V., Chun, B.G., Cox, L.P., Jung, J., McDaniel, P. and
Sheth, A.N., 2014. TaintDroid: an information-flow tracking system for realtime privacy
monitoring on smartphones. ACM Transactions on Computer Systems (TOCS), 32(2), p.5.
Feizollah, A., Anuar, N.B., Salleh, R. and Wahab, A.W.A., 2015. A review on feature selection
in mobile malware detection. Digital Investigation, 13, pp.22-37.
Jabeen, Q., Khan, F., Hayat, M.N., Khan, H., Jan, S.R. and Ullah, F., 2016. A Survey: Embedded
Systems Supporting By Different Operating Systems. arXiv preprint arXiv:1610.07899.
Johnston, M.J., King, D., Arora, S., Behar, N., Athanasiou, T., Sevdalis, N. and Darzi, A., 2015.
Smartphones let surgeons know WhatsApp: an analysis of communication in emergency surgical
teams. The American Journal of Surgery, 209(1), pp.45-51.
Sinha, A., Paul, N. and Devarajan, S., Zscaler Inc, 2016. Mobile device security, device
management, and policy enforcement in a cloud based system. U.S. Patent Application
15/154,328.
Succi, G. and Ivanov, V.V., 2018. Comparison of mobile operating systems based on models of
growth reliability of the software. Computer Research and Modeling, 10(3), pp.325-334.
Appendices
1. Awan et al., (2017) focuses on the security factors and the highlight which are related to
the IoS interfacing and the other mobile operating systems.

2. Chen et al., (2016) highlights about the software defined network where the mobile
applications are discussed and how the security is maintained in the operating systems.
3. Conroy et al., (2014) focus on the different changes of the mobile apps and how the
physical activity is depending upon the functioning of the mobile applications.
4. Enck et al., (2014) depends on the proper tracking of the information flow with handling
the privacy of the system and then monitoring the data in the smart phone devices.
5. Feizollah et al., (2015) highlghts about the features of the different problems of how it is
possible to detect the security issues and then help in rectify them.
6. Johnston et al., (2015) highlights about the use of the smartphone that lets a proper
conversation with the proper management of the devices to handle the teams in an
effective manner.
7. Sinha et al., (2016) is about working over the mobile device security and the management
of the device and the operating system. This is to make sure that the efficiency increases
with updates of software.
8. Succi et al., (2018) is about focusing on the comparison of the different models for a
better reliability and setup of the system software effectively.
applications are discussed and how the security is maintained in the operating systems.
3. Conroy et al., (2014) focus on the different changes of the mobile apps and how the
physical activity is depending upon the functioning of the mobile applications.
4. Enck et al., (2014) depends on the proper tracking of the information flow with handling
the privacy of the system and then monitoring the data in the smart phone devices.
5. Feizollah et al., (2015) highlghts about the features of the different problems of how it is
possible to detect the security issues and then help in rectify them.
6. Johnston et al., (2015) highlights about the use of the smartphone that lets a proper
conversation with the proper management of the devices to handle the teams in an
effective manner.
7. Sinha et al., (2016) is about working over the mobile device security and the management
of the device and the operating system. This is to make sure that the efficiency increases
with updates of software.
8. Succi et al., (2018) is about focusing on the comparison of the different models for a
better reliability and setup of the system software effectively.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





