Mobile Security and Privacy: A Hybrid Methodology Approach
VerifiedAdded on 2024/06/04
|15
|2801
|107
AI Summary
This research investigates the risks associated with mobile security and privacy, focusing on data hacking and the impact of mobile applications on user behavior. It employs a hybrid methodology, combining qualitative and quantitative approaches, to analyze the challenges and propose solutions for enhancing mobile security and protecting user privacy. The research explores existing methodologies, identifies their strengths and limitations, and justifies the use of a hybrid approach for a comprehensive understanding of the research problem.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

NIT6130 - ASS 3
1
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
1.1 1. State your research problems and re-organize your collected literatures..........................2
1.1.1 a. Prepare a statement on your research problem............................................................2
1.1.2 b. Try to structure the problem into a set of smaller sub-problems if possible...............2
1.1.3 c. Organize the collected literature according to the sub-problems defined...................3
1.1.4 d. Record your work using the table below.....................................................................4
1.2 Determine the types of methodology (qualitative or quantitative)........................................5
1.2.1 a. Compare and contrast the features of qualitative and quantitative methodologies.....5
1.2.2 b. Decide what type of methodology you plan to apply in your project and justify your
decision.....................................................................................................................................6
1.3 Review of the Existing Methodologies..................................................................................7
1.3.1 Selected Sub-Problem.....................................................................................................7
1.3.2 Analysis of the Selected Methodologies.........................................................................7
1.3.3 Relevance of the Research Problem................................................................................9
1.3.4 Summary of the Reviewed Methodologies.....................................................................9
1.4 Proposed Methodology........................................................................................................10
1.4.1 Identification and Justification......................................................................................10
1.4.2 Benefits and Limitations...............................................................................................10
1.4.3 Framework and Explanation.........................................................................................10
References......................................................................................................................................11
2
1.1 1. State your research problems and re-organize your collected literatures..........................2
1.1.1 a. Prepare a statement on your research problem............................................................2
1.1.2 b. Try to structure the problem into a set of smaller sub-problems if possible...............2
1.1.3 c. Organize the collected literature according to the sub-problems defined...................3
1.1.4 d. Record your work using the table below.....................................................................4
1.2 Determine the types of methodology (qualitative or quantitative)........................................5
1.2.1 a. Compare and contrast the features of qualitative and quantitative methodologies.....5
1.2.2 b. Decide what type of methodology you plan to apply in your project and justify your
decision.....................................................................................................................................6
1.3 Review of the Existing Methodologies..................................................................................7
1.3.1 Selected Sub-Problem.....................................................................................................7
1.3.2 Analysis of the Selected Methodologies.........................................................................7
1.3.3 Relevance of the Research Problem................................................................................9
1.3.4 Summary of the Reviewed Methodologies.....................................................................9
1.4 Proposed Methodology........................................................................................................10
1.4.1 Identification and Justification......................................................................................10
1.4.2 Benefits and Limitations...............................................................................................10
1.4.3 Framework and Explanation.........................................................................................10
References......................................................................................................................................11
2

1.1 1. State your research problems and re-organize your collected literatures
1.1.1 a. Prepare a statement on your research problem
The research is done to identify the risk of the mobile security and privacy. This research is
conducted for the implementation of the new and innovative technologies related to the
automobile industry (Wimbock, 2018). The research problem is related to the mobile hacking
and the privacy issues. This research is conducted to evaluate the common forms of the attacks
on the mobile function, which affects the work of the individual as well as of the organisation.
These kinds of attack changes the data present in the mobile and sometime data send to another
mobile or to other computer system. The main reason of this research is to solve problem which
affect the mobile function and the privacy related to the user. This research has some problems
which are required to be solving in this research. Every person has the different kind of problems
and they need to be solving on time.
1.1.2 b. Try to structure the problem into a set of smaller sub-problems if possible
There are the various problems in this research. The problems are designing the appropriate app,
this is the major problem of the mobile security and privacy. The sub problem of this problem is
lack of collaboration of different apps, designing issues, and correlation of different data
(Schäfer, 2018).The problem of this research is of data hacking. This is another issue related to
this research. The sub problem of the problem is this leak the information of the user and
sometimes the information is delivered to the other mobile user or to another computer system.
All these problems are the main reason of this research. Along with these problems the other
problems also exists and that are people awareness regarding the mobile technology and the
different improvements of the technology. Awareness regarding the health monitoring apps and
various changes of the behavior which is also the major issue of mobile technology.. This
research helps to provide the different objectives of the research and how to remove these
problems with the help of the users of the mobile technology.
3
1.1.1 a. Prepare a statement on your research problem
The research is done to identify the risk of the mobile security and privacy. This research is
conducted for the implementation of the new and innovative technologies related to the
automobile industry (Wimbock, 2018). The research problem is related to the mobile hacking
and the privacy issues. This research is conducted to evaluate the common forms of the attacks
on the mobile function, which affects the work of the individual as well as of the organisation.
These kinds of attack changes the data present in the mobile and sometime data send to another
mobile or to other computer system. The main reason of this research is to solve problem which
affect the mobile function and the privacy related to the user. This research has some problems
which are required to be solving in this research. Every person has the different kind of problems
and they need to be solving on time.
1.1.2 b. Try to structure the problem into a set of smaller sub-problems if possible
There are the various problems in this research. The problems are designing the appropriate app,
this is the major problem of the mobile security and privacy. The sub problem of this problem is
lack of collaboration of different apps, designing issues, and correlation of different data
(Schäfer, 2018).The problem of this research is of data hacking. This is another issue related to
this research. The sub problem of the problem is this leak the information of the user and
sometimes the information is delivered to the other mobile user or to another computer system.
All these problems are the main reason of this research. Along with these problems the other
problems also exists and that are people awareness regarding the mobile technology and the
different improvements of the technology. Awareness regarding the health monitoring apps and
various changes of the behavior which is also the major issue of mobile technology.. This
research helps to provide the different objectives of the research and how to remove these
problems with the help of the users of the mobile technology.
3

c. Organize the collected literature according to the sub-problems defined
According to the Schnall, Bakken et al. (2015), the mobile technology is widely used by the
different people. This is the major used device now adays. As this is widely used technology so
the protection is very required to maintain the security of the mobile and the privacy of
individual as well as of the organization(Schnall, Bakken et al. 2015). To protect the user from
any kind of the security problem different health and the monitoring apps are used and protect
the interest of the users. These apps help to remove the difficulties related to the health and the
workplace(Biswas, 2018). To remove the all kind of the problems different apps are designed
and proper implementation of these apps are required to be maintained to reach the target set
goal of this research.
4
According to the Schnall, Bakken et al. (2015), the mobile technology is widely used by the
different people. This is the major used device now adays. As this is widely used technology so
the protection is very required to maintain the security of the mobile and the privacy of
individual as well as of the organization(Schnall, Bakken et al. 2015). To protect the user from
any kind of the security problem different health and the monitoring apps are used and protect
the interest of the users. These apps help to remove the difficulties related to the health and the
workplace(Biswas, 2018). To remove the all kind of the problems different apps are designed
and proper implementation of these apps are required to be maintained to reach the target set
goal of this research.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
1.1.3 d. Record your work using the table below
Research problem Subproblem Collected Literature
Problem 1 - Data hacking Subproblem 1 - Leak the
personal problems of the
users.
Mobile health technology is
recently very useful
technology by users.
Qualitative methods are used
to improve the healthcare of
the mobile users. According
toSchnall, Bakken et al.
(2015), the personal
information of the user is a
hack and deliver to the other
user of mobile
technology(Schnall, Bakken
et al. 2015).
Subproblem 2 - not safe to
maintain all the information
on the mobile phone.
With the changes in the new
technology people use more
and more of mobile
technology, which creates the
more problems to the user
(Aggarwal, 2018).
Problem 2 - mobile apps and
behavior changes
Subproblem 1- use of the
mobile app and sustain
behavior.
To evaluate this kind of
research quantitative
methodology is used to
remove this problem (Press,
2018). Mobile phones are
mainly used by the people,
for these proper apps are
required to be the plan and
made for the benefit of the
5
Research problem Subproblem Collected Literature
Problem 1 - Data hacking Subproblem 1 - Leak the
personal problems of the
users.
Mobile health technology is
recently very useful
technology by users.
Qualitative methods are used
to improve the healthcare of
the mobile users. According
toSchnall, Bakken et al.
(2015), the personal
information of the user is a
hack and deliver to the other
user of mobile
technology(Schnall, Bakken
et al. 2015).
Subproblem 2 - not safe to
maintain all the information
on the mobile phone.
With the changes in the new
technology people use more
and more of mobile
technology, which creates the
more problems to the user
(Aggarwal, 2018).
Problem 2 - mobile apps and
behavior changes
Subproblem 1- use of the
mobile app and sustain
behavior.
To evaluate this kind of
research quantitative
methodology is used to
remove this problem (Press,
2018). Mobile phones are
mainly used by the people,
for these proper apps are
required to be the plan and
made for the benefit of the
5

user.
6
6

1.2 Determine the types of methodology (qualitative or quantitative)
1.2.1 a. Compare and contrast the features of qualitative and quantitative methodologies
Qualitative methodology is related to the non-numerical problems. This methodology is related
to the meaning, definitions, characteristics and symbols and description of the things. The source
of qualitative methods is the interview, focus groups, secondary data, and observation. The
qualitative methodology provides the many choices for techniques generation and to remove the
problem of the research.
Quantitative methodology is the methodology which provides the systematic observation
through statistical, mathematical and computational technology. This type of methodology is
planned to develop the understanding regarding the mathematical models, theories and different
hypotheses, which helps in achieving the objective of the research. Qualitative research is related
to the mathematical equation and the various measurement techniques of finding the problem. A
different source of the quantitative methodology is surveys, observations, and secondary data.
Qualitative methodology Quantitative methodology
This is related to the statistical methods. This methodology is related to the non-
statistical methods.
This helps to find the more complex problem. This is simple as compared to the qualitative
methodology.
It also uses the insider viewpoint related to
the research problem.
This mainly focuses on the actual view of the
world member.
Both this terms are a compliment to each other and both have the important value at the time of
conducting research (Biswas, 2018). Qualitative research is mainly used to analyze the testing
theory whereas quantitative research focuses on the mathematical theory. Both these methods are
very helpful in conducting the research. These are related to each other.
7
1.2.1 a. Compare and contrast the features of qualitative and quantitative methodologies
Qualitative methodology is related to the non-numerical problems. This methodology is related
to the meaning, definitions, characteristics and symbols and description of the things. The source
of qualitative methods is the interview, focus groups, secondary data, and observation. The
qualitative methodology provides the many choices for techniques generation and to remove the
problem of the research.
Quantitative methodology is the methodology which provides the systematic observation
through statistical, mathematical and computational technology. This type of methodology is
planned to develop the understanding regarding the mathematical models, theories and different
hypotheses, which helps in achieving the objective of the research. Qualitative research is related
to the mathematical equation and the various measurement techniques of finding the problem. A
different source of the quantitative methodology is surveys, observations, and secondary data.
Qualitative methodology Quantitative methodology
This is related to the statistical methods. This methodology is related to the non-
statistical methods.
This helps to find the more complex problem. This is simple as compared to the qualitative
methodology.
It also uses the insider viewpoint related to
the research problem.
This mainly focuses on the actual view of the
world member.
Both this terms are a compliment to each other and both have the important value at the time of
conducting research (Biswas, 2018). Qualitative research is mainly used to analyze the testing
theory whereas quantitative research focuses on the mathematical theory. Both these methods are
very helpful in conducting the research. These are related to each other.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8

1.2.2 b. Decide what type of methodology you plan to apply in your project and justify your
decision
While conducting this research a hybrid methodology is used to solve the problem of the
research. Hybrid research methodology is the combination of both qualitative and quantitative
methodology. As this is the combination of both the research methodology this gave the better
result to the research problems. This methodology is used because in mobile technology both the
qualitative and quantitative researchers are required. As there are different problems which re
required being analyses in the proper manner so that the decisions are made properly and the
purpose of the research will be achieved at the end of the research (Schäfer, 2018). Research on
the mobile security and privacy is not limited to survey or observation, but the deep analysis is
required to check and evaluation of the mobile apps and know about the expectations about the
customers and their desires. This is the very effective method of research as reducing the time
and cost of conducting the research. This helps to make the research successful and remove the
problems of the research
9
decision
While conducting this research a hybrid methodology is used to solve the problem of the
research. Hybrid research methodology is the combination of both qualitative and quantitative
methodology. As this is the combination of both the research methodology this gave the better
result to the research problems. This methodology is used because in mobile technology both the
qualitative and quantitative researchers are required. As there are different problems which re
required being analyses in the proper manner so that the decisions are made properly and the
purpose of the research will be achieved at the end of the research (Schäfer, 2018). Research on
the mobile security and privacy is not limited to survey or observation, but the deep analysis is
required to check and evaluation of the mobile apps and know about the expectations about the
customers and their desires. This is the very effective method of research as reducing the time
and cost of conducting the research. This helps to make the research successful and remove the
problems of the research
9

1.3 Review of the Existing Methodologies
1.3.1 Selected Sub-Problem
The research problem is framed by the researcher, he choose the problem of data hacking that
has two problems that is it leaks the problems of the users and secondly the information is not
safe in the cell phones.
1.3.2 Analysis of the Selected Methodologies
Literature 1: Data hacking
The researcher use the Hybrid methodology as hybrid is considered as the best part that adds the
qualitative and quantitative methodology. It is not pure in quantitative form or qualitative
methodology. If the researcher needs more information or data then he can use the qualitative
method and then convert data in quantitative form. For the research problem, a researcher has to
maintain and develop the better products that help to follow the same method and encourage the
other applications. It is also necessary to sustain with that applications so that life can be
changed. For this, they have to check the needs and want of the employees and how they use
their cell phones and provide their opinions. In this report, the researcher emphasis on the system
of data hacking that how data can hacked. If data can be hacked then what are the problems that
can be faced by the different users (Sim, et. al., 2018).
In case of data hacking the user did not save any important information in cell phones as by
saving, there is no chance of guarantee that it is safe. The information can be leaked by any
source so this all creates the trouble for the users.
Literature 2: Mobile applications and behavior changes
It can be analyses that the behavior change targets the specific risk and that has to establish their
effectiveness that reduces the development of diseases. It also evaluates that the more number of
consumers are using the cell phones and that is increasing day by day. There is positive impact of
mobile in our daily life, by using the mobile applications the life of users will be easier as they
10
1.3.1 Selected Sub-Problem
The research problem is framed by the researcher, he choose the problem of data hacking that
has two problems that is it leaks the problems of the users and secondly the information is not
safe in the cell phones.
1.3.2 Analysis of the Selected Methodologies
Literature 1: Data hacking
The researcher use the Hybrid methodology as hybrid is considered as the best part that adds the
qualitative and quantitative methodology. It is not pure in quantitative form or qualitative
methodology. If the researcher needs more information or data then he can use the qualitative
method and then convert data in quantitative form. For the research problem, a researcher has to
maintain and develop the better products that help to follow the same method and encourage the
other applications. It is also necessary to sustain with that applications so that life can be
changed. For this, they have to check the needs and want of the employees and how they use
their cell phones and provide their opinions. In this report, the researcher emphasis on the system
of data hacking that how data can hacked. If data can be hacked then what are the problems that
can be faced by the different users (Sim, et. al., 2018).
In case of data hacking the user did not save any important information in cell phones as by
saving, there is no chance of guarantee that it is safe. The information can be leaked by any
source so this all creates the trouble for the users.
Literature 2: Mobile applications and behavior changes
It can be analyses that the behavior change targets the specific risk and that has to establish their
effectiveness that reduces the development of diseases. It also evaluates that the more number of
consumers are using the cell phones and that is increasing day by day. There is positive impact of
mobile in our daily life, by using the mobile applications the life of users will be easier as they
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
can order anything from the mobile, the users can do online shopping. It takes less time as the
users do not go anywhere to purchase the thing. It also incurs fewer costs and that will be easy
for them.
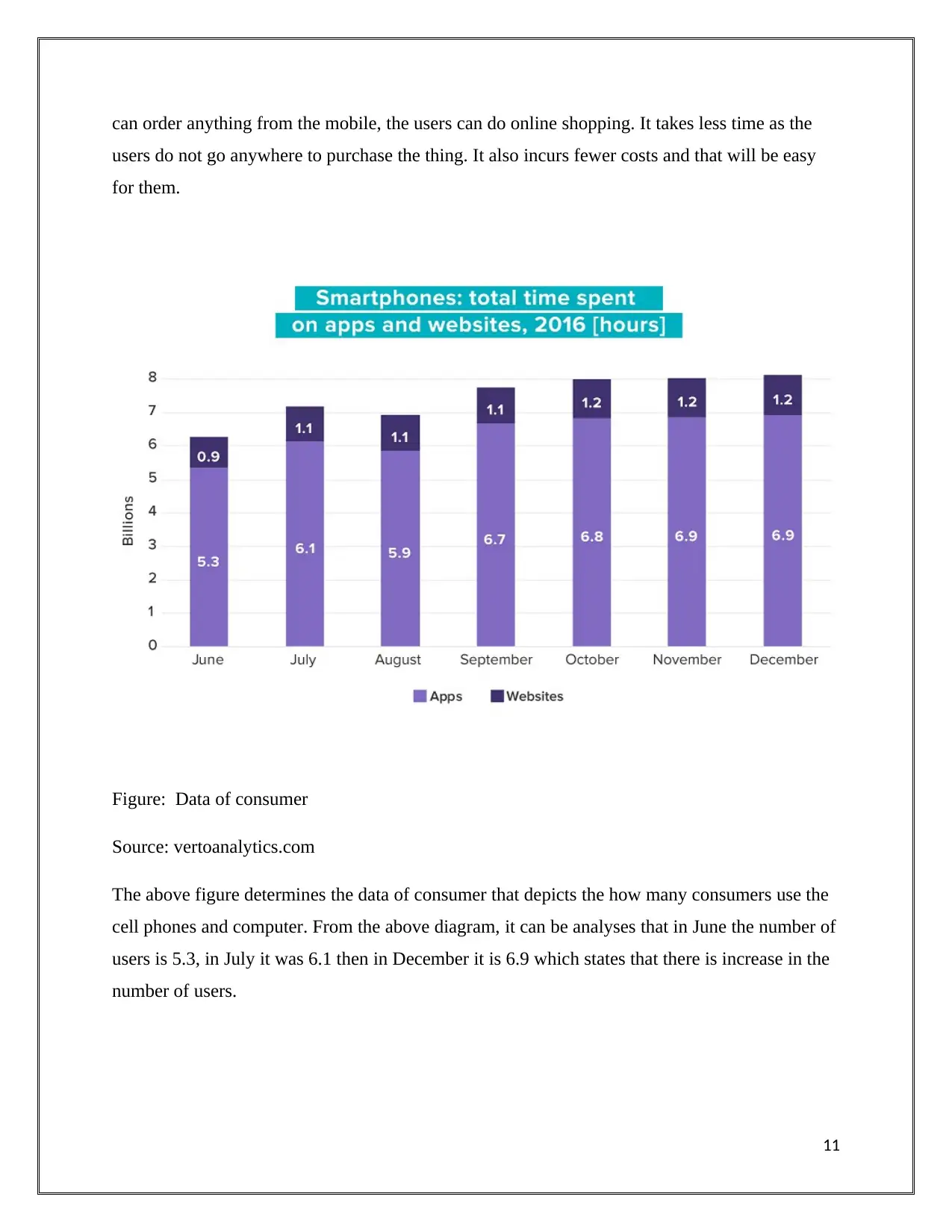
Figure: Data of consumer
Source: vertoanalytics.com
The above figure determines the data of consumer that depicts the how many consumers use the
cell phones and computer. From the above diagram, it can be analyses that in June the number of
users is 5.3, in July it was 6.1 then in December it is 6.9 which states that there is increase in the
number of users.
11
users do not go anywhere to purchase the thing. It also incurs fewer costs and that will be easy
for them.
Figure: Data of consumer
Source: vertoanalytics.com
The above figure determines the data of consumer that depicts the how many consumers use the
cell phones and computer. From the above diagram, it can be analyses that in June the number of
users is 5.3, in July it was 6.1 then in December it is 6.9 which states that there is increase in the
number of users.
11
1.3.3 Relevance of the Research Problem
Literature 1 depicts the study of data hacking that includes the problem of leak of information
and it is insecure to save all the information in the cell phones. As if the data can be hacked then
the hacker can receives the personal information of the users.
Literature 2 is based on the mobile applications and behavior change. The above analyses depict
the number of consumers who use cell phones and what are its impacts and benefits. It also
evaluates the different applications that can be used in the mobile.
1.3.4 Summary of the Reviewed Methodologies
Relevance of methodologies
Literature Research
Problem
Methodology Your sub-
problem
Relevance
Literature 1 Data hacking Quantitative There is
insecurity of
information.
Strongly
Relevant
Literature 2 Mobile
applications
and behavior
change
Quantitative The
applications are
widely used by
the number of
users.
Strongly
Relevant
12
Literature 1 depicts the study of data hacking that includes the problem of leak of information
and it is insecure to save all the information in the cell phones. As if the data can be hacked then
the hacker can receives the personal information of the users.
Literature 2 is based on the mobile applications and behavior change. The above analyses depict
the number of consumers who use cell phones and what are its impacts and benefits. It also
evaluates the different applications that can be used in the mobile.
1.3.4 Summary of the Reviewed Methodologies
Relevance of methodologies
Literature Research
Problem
Methodology Your sub-
problem
Relevance
Literature 1 Data hacking Quantitative There is
insecurity of
information.
Strongly
Relevant
Literature 2 Mobile
applications
and behavior
change
Quantitative The
applications are
widely used by
the number of
users.
Strongly
Relevant
12

1.4 Proposed Methodology
In this research, the researcher uses the different type of methodology that is the mixture of other
methodologies. In this research the section 1.4 topic is divided in to three section, section 1.4.1
depicts the methodology that can be used by the researcher. 1.4.2 States the limitations and
benefits of the methodology. 1.4.3 develops the frameworks and procedures of the methodology.
1.4.1 Identification and Justification
As it has stated by the researcher that hybrid methodology is used as this type of methodology
includes all other methodology, it is not limited to the quantitative and qualitative methods. It is
suggested that to use only one type of methods. I have to analyses the data and statistics in
relation to the research problems. From the data, the researcher can analyses the situation and
provide the recommendations to the users in relation to the research problem (Gogtay, 2018).
1.4.2 Benefits and Limitations
Benefits:
With the mobile applications, the users can connect easily with one another.
It also helps in sending and receiving information.
It can be considered as the reliable source that provides the data.
It can be used in the process of data analysis and testing.
Limitations:
It can be estimated that different users have different perceptions.
The solutions can be in vague process.
The designing of the applications can be a difficult and there can be chances of error
mistake.
It takes more time and cost to find the users.
13
In this research, the researcher uses the different type of methodology that is the mixture of other
methodologies. In this research the section 1.4 topic is divided in to three section, section 1.4.1
depicts the methodology that can be used by the researcher. 1.4.2 States the limitations and
benefits of the methodology. 1.4.3 develops the frameworks and procedures of the methodology.
1.4.1 Identification and Justification
As it has stated by the researcher that hybrid methodology is used as this type of methodology
includes all other methodology, it is not limited to the quantitative and qualitative methods. It is
suggested that to use only one type of methods. I have to analyses the data and statistics in
relation to the research problems. From the data, the researcher can analyses the situation and
provide the recommendations to the users in relation to the research problem (Gogtay, 2018).
1.4.2 Benefits and Limitations
Benefits:
With the mobile applications, the users can connect easily with one another.
It also helps in sending and receiving information.
It can be considered as the reliable source that provides the data.
It can be used in the process of data analysis and testing.
Limitations:
It can be estimated that different users have different perceptions.
The solutions can be in vague process.
The designing of the applications can be a difficult and there can be chances of error
mistake.
It takes more time and cost to find the users.
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.4.3 Framework and Explanation
In the above research, the researcher develops the study which includes the different tasks. In
task it identifies the problem of research that what are the problems and what are the sub
problems and their analyses. It also provides the methodology that can be used by the researcher
with their methodology and then relate with the research problem. Lastly proposed methodology
is framed which determines the justification and identification with their limitations and benefits.
In this research, the data is collected and the diagram depicts the number of users who use the
mobile phones and websites (Ledford. & Gast, 2018).
14
In the above research, the researcher develops the study which includes the different tasks. In
task it identifies the problem of research that what are the problems and what are the sub
problems and their analyses. It also provides the methodology that can be used by the researcher
with their methodology and then relate with the research problem. Lastly proposed methodology
is framed which determines the justification and identification with their limitations and benefits.
In this research, the data is collected and the diagram depicts the number of users who use the
mobile phones and websites (Ledford. & Gast, 2018).
14

References
Aggarwal, S. K. (2018). A review of the mass spectrometric studies of americium:
Present status and future perspective. Mass spectrometry reviews, 37(1), 43-56.
Biswas, S. (2018). U.S. Patent Application No. 15/790,864.
Gobo, G. (2018). Qualitative research across boundaries: indigenisation, glocalization or
creolization?.
Gogtay, N. J. (2018). Research methodology workshops: A small step towards practice of evidence-based
medicine. Perspectives in Clinical Research, 9(2), 59.
Ledford, J. R., & Gast, D. L. (2018). Single case research methodology: Applications in special education
and behavioral sciences. Routledge.
Press, A. L. (2018). Toward a qualitative methodology of audience study: Using
ethnography to study the popular culture audience. In The audience and its
landscape (pp. 113-130). Routledge.
Schäfer, F. (2018). U.S. Patent Application No. 15/542,577.
Schnall, R., Bakken, S., Rojas, M., Travers, J., & Carballo-Dieguez, A. (2015). mHealth
technology as a persuasive tool for treatment, care, and management of persons living
with HIV. AIDS and Behavior, 19(2), 81-89.
Sim, J., Saunders, B., Waterfield, J., & Kingstone, T. (2018). Can sample size in qualitative research be
determined a priori?. International Journal of Social Research Methodology, 1-16.
Wimbock, U. (2018). U.S. Patent No. 9,930,069. Washington, DC: U.S. Patent and
Trademark Office.
15
Aggarwal, S. K. (2018). A review of the mass spectrometric studies of americium:
Present status and future perspective. Mass spectrometry reviews, 37(1), 43-56.
Biswas, S. (2018). U.S. Patent Application No. 15/790,864.
Gobo, G. (2018). Qualitative research across boundaries: indigenisation, glocalization or
creolization?.
Gogtay, N. J. (2018). Research methodology workshops: A small step towards practice of evidence-based
medicine. Perspectives in Clinical Research, 9(2), 59.
Ledford, J. R., & Gast, D. L. (2018). Single case research methodology: Applications in special education
and behavioral sciences. Routledge.
Press, A. L. (2018). Toward a qualitative methodology of audience study: Using
ethnography to study the popular culture audience. In The audience and its
landscape (pp. 113-130). Routledge.
Schäfer, F. (2018). U.S. Patent Application No. 15/542,577.
Schnall, R., Bakken, S., Rojas, M., Travers, J., & Carballo-Dieguez, A. (2015). mHealth
technology as a persuasive tool for treatment, care, and management of persons living
with HIV. AIDS and Behavior, 19(2), 81-89.
Sim, J., Saunders, B., Waterfield, J., & Kingstone, T. (2018). Can sample size in qualitative research be
determined a priori?. International Journal of Social Research Methodology, 1-16.
Wimbock, U. (2018). U.S. Patent No. 9,930,069. Washington, DC: U.S. Patent and
Trademark Office.
15
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





