MOD002602 - Cloud Computing Security Procedures - Anglia Ruskin Univ
VerifiedAdded on 2023/04/21
|22
|8040
|172
Project
AI Summary
This project proposal for MOD002602 Computing Research Methodologies at Anglia Ruskin University investigates security procedures for data protection in cloud computing. The research aims to identify security techniques to prevent unauthorized data access, explore major security challenges, and recommend effective handling strategies. The proposal outlines the use of systematic literature review, surveys, and interviews as research methods, involving cloud experts to gather insights. It details the skills, resources, and ethical considerations necessary for the project, including data collection, processing, and visualization methods. The expected beneficiaries include organizations and academic institutions seeking to strengthen their cloud security measures. The proposal also addresses potential risks, such as volunteer compliance and software errors, and includes a review of relevant literature to support the research.

MOD002602 Computing Research Methodologies, 2018/9
Major Project Proposal for the Degree
Of
BEng (Hons) Computer Science
[SID Number]
Submission Date: May 3rd 2019
School of Computing and Information Science,
Faculty of Science and Engineering,
Anglia Ruskin University,
East Road, Cambridge CB1 1PT
1
Major Project Proposal for the Degree
Of
BEng (Hons) Computer Science
[SID Number]
Submission Date: May 3rd 2019
School of Computing and Information Science,
Faculty of Science and Engineering,
Anglia Ruskin University,
East Road, Cambridge CB1 1PT
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
MOD002602 Computing Research Methodologies, 2018/9
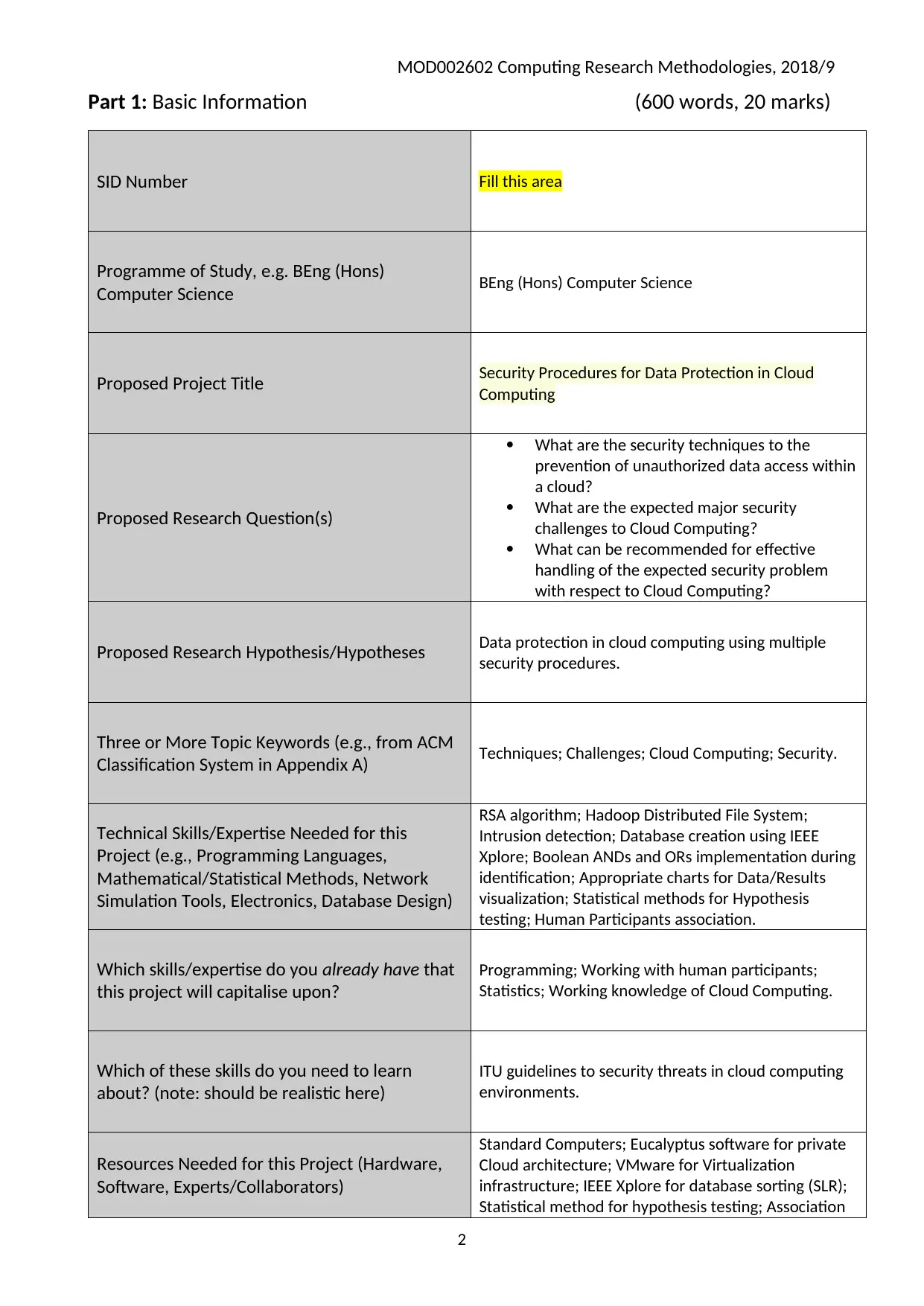
Part 1: Basic Information (600 words, 20 marks)
SID Number Fill this area
Programme of Study, e.g. BEng (Hons)
Computer Science BEng (Hons) Computer Science
Proposed Project Title Security Procedures for Data Protection in Cloud
Computing
Proposed Research Question(s)
What are the security techniques to the
prevention of unauthorized data access within
a cloud?
What are the expected major security
challenges to Cloud Computing?
What can be recommended for effective
handling of the expected security problem
with respect to Cloud Computing?
Proposed Research Hypothesis/Hypotheses Data protection in cloud computing using multiple
security procedures.
Three or More Topic Keywords (e.g., from ACM
Classification System in Appendix A) Techniques; Challenges; Cloud Computing; Security.
Technical Skills/Expertise Needed for this
Project (e.g., Programming Languages,
Mathematical/Statistical Methods, Network
Simulation Tools, Electronics, Database Design)
RSA algorithm; Hadoop Distributed File System;
Intrusion detection; Database creation using IEEE
Xplore; Boolean ANDs and ORs implementation during
identification; Appropriate charts for Data/Results
visualization; Statistical methods for Hypothesis
testing; Human Participants association.
Which skills/expertise do you already have that
this project will capitalise upon?
Programming; Working with human participants;
Statistics; Working knowledge of Cloud Computing.
Which of these skills do you need to learn
about? (note: should be realistic here)
ITU guidelines to security threats in cloud computing
environments.
Resources Needed for this Project (Hardware,
Software, Experts/Collaborators)
Standard Computers; Eucalyptus software for private
Cloud architecture; VMware for Virtualization
infrastructure; IEEE Xplore for database sorting (SLR);
Statistical method for hypothesis testing; Association
2
Part 1: Basic Information (600 words, 20 marks)
SID Number Fill this area
Programme of Study, e.g. BEng (Hons)
Computer Science BEng (Hons) Computer Science
Proposed Project Title Security Procedures for Data Protection in Cloud
Computing
Proposed Research Question(s)
What are the security techniques to the
prevention of unauthorized data access within
a cloud?
What are the expected major security
challenges to Cloud Computing?
What can be recommended for effective
handling of the expected security problem
with respect to Cloud Computing?
Proposed Research Hypothesis/Hypotheses Data protection in cloud computing using multiple
security procedures.
Three or More Topic Keywords (e.g., from ACM
Classification System in Appendix A) Techniques; Challenges; Cloud Computing; Security.
Technical Skills/Expertise Needed for this
Project (e.g., Programming Languages,
Mathematical/Statistical Methods, Network
Simulation Tools, Electronics, Database Design)
RSA algorithm; Hadoop Distributed File System;
Intrusion detection; Database creation using IEEE
Xplore; Boolean ANDs and ORs implementation during
identification; Appropriate charts for Data/Results
visualization; Statistical methods for Hypothesis
testing; Human Participants association.
Which skills/expertise do you already have that
this project will capitalise upon?
Programming; Working with human participants;
Statistics; Working knowledge of Cloud Computing.
Which of these skills do you need to learn
about? (note: should be realistic here)
ITU guidelines to security threats in cloud computing
environments.
Resources Needed for this Project (Hardware,
Software, Experts/Collaborators)
Standard Computers; Eucalyptus software for private
Cloud architecture; VMware for Virtualization
infrastructure; IEEE Xplore for database sorting (SLR);
Statistical method for hypothesis testing; Association
2
MOD002602 Computing Research Methodologies, 2018/9
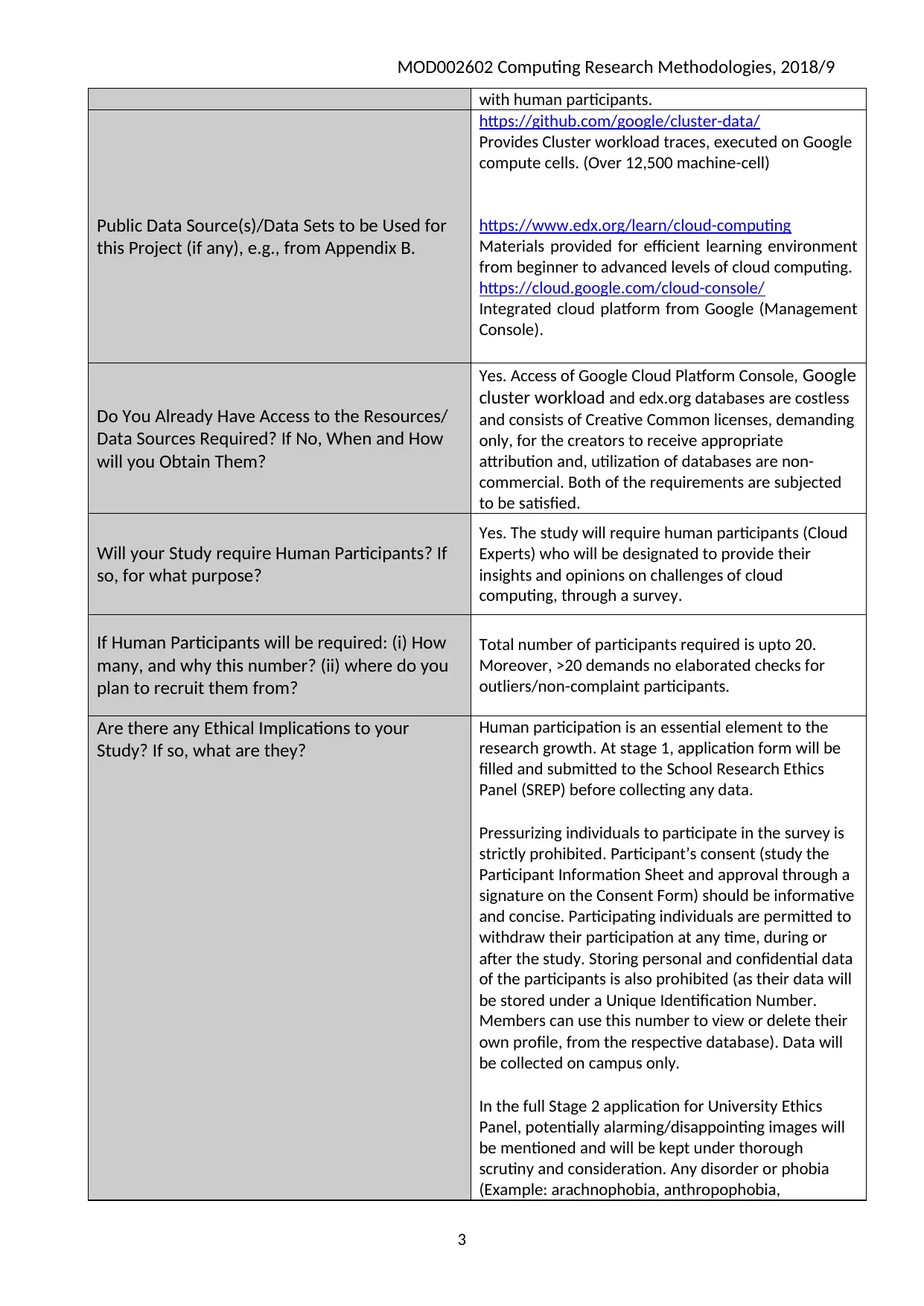
with human participants.
Public Data Source(s)/Data Sets to be Used for
this Project (if any), e.g., from Appendix B.
https://github.com/google/cluster-data/
Provides Cluster workload traces, executed on Google
compute cells. (Over 12,500 machine-cell)
https://www.edx.org/learn/cloud-computing
Materials provided for efficient learning environment
from beginner to advanced levels of cloud computing.
https://cloud.google.com/cloud-console/
Integrated cloud platform from Google (Management
Console).
Do You Already Have Access to the Resources/
Data Sources Required? If No, When and How
will you Obtain Them?
Yes. Access of Google Cloud Platform Console, Google
cluster workload and edx.org databases are costless
and consists of Creative Common licenses, demanding
only, for the creators to receive appropriate
attribution and, utilization of databases are non-
commercial. Both of the requirements are subjected
to be satisfied.
Will your Study require Human Participants? If
so, for what purpose?
Yes. The study will require human participants (Cloud
Experts) who will be designated to provide their
insights and opinions on challenges of cloud
computing, through a survey.
If Human Participants will be required: (i) How
many, and why this number? (ii) where do you
plan to recruit them from?
Total number of participants required is upto 20.
Moreover, >20 demands no elaborated checks for
outliers/non-complaint participants.
Are there any Ethical Implications to your
Study? If so, what are they?
Human participation is an essential element to the
research growth. At stage 1, application form will be
filled and submitted to the School Research Ethics
Panel (SREP) before collecting any data.
Pressurizing individuals to participate in the survey is
strictly prohibited. Participant’s consent (study the
Participant Information Sheet and approval through a
signature on the Consent Form) should be informative
and concise. Participating individuals are permitted to
withdraw their participation at any time, during or
after the study. Storing personal and confidential data
of the participants is also prohibited (as their data will
be stored under a Unique Identification Number.
Members can use this number to view or delete their
own profile, from the respective database). Data will
be collected on campus only.
In the full Stage 2 application for University Ethics
Panel, potentially alarming/disappointing images will
be mentioned and will be kept under thorough
scrutiny and consideration. Any disorder or phobia
(Example: arachnophobia, anthropophobia,
3
with human participants.
Public Data Source(s)/Data Sets to be Used for
this Project (if any), e.g., from Appendix B.
https://github.com/google/cluster-data/
Provides Cluster workload traces, executed on Google
compute cells. (Over 12,500 machine-cell)
https://www.edx.org/learn/cloud-computing
Materials provided for efficient learning environment
from beginner to advanced levels of cloud computing.
https://cloud.google.com/cloud-console/
Integrated cloud platform from Google (Management
Console).
Do You Already Have Access to the Resources/
Data Sources Required? If No, When and How
will you Obtain Them?
Yes. Access of Google Cloud Platform Console, Google
cluster workload and edx.org databases are costless
and consists of Creative Common licenses, demanding
only, for the creators to receive appropriate
attribution and, utilization of databases are non-
commercial. Both of the requirements are subjected
to be satisfied.
Will your Study require Human Participants? If
so, for what purpose?
Yes. The study will require human participants (Cloud
Experts) who will be designated to provide their
insights and opinions on challenges of cloud
computing, through a survey.
If Human Participants will be required: (i) How
many, and why this number? (ii) where do you
plan to recruit them from?
Total number of participants required is upto 20.
Moreover, >20 demands no elaborated checks for
outliers/non-complaint participants.
Are there any Ethical Implications to your
Study? If so, what are they?
Human participation is an essential element to the
research growth. At stage 1, application form will be
filled and submitted to the School Research Ethics
Panel (SREP) before collecting any data.
Pressurizing individuals to participate in the survey is
strictly prohibited. Participant’s consent (study the
Participant Information Sheet and approval through a
signature on the Consent Form) should be informative
and concise. Participating individuals are permitted to
withdraw their participation at any time, during or
after the study. Storing personal and confidential data
of the participants is also prohibited (as their data will
be stored under a Unique Identification Number.
Members can use this number to view or delete their
own profile, from the respective database). Data will
be collected on campus only.
In the full Stage 2 application for University Ethics
Panel, potentially alarming/disappointing images will
be mentioned and will be kept under thorough
scrutiny and consideration. Any disorder or phobia
(Example: arachnophobia, anthropophobia,
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
MOD002602 Computing Research Methodologies, 2018/9
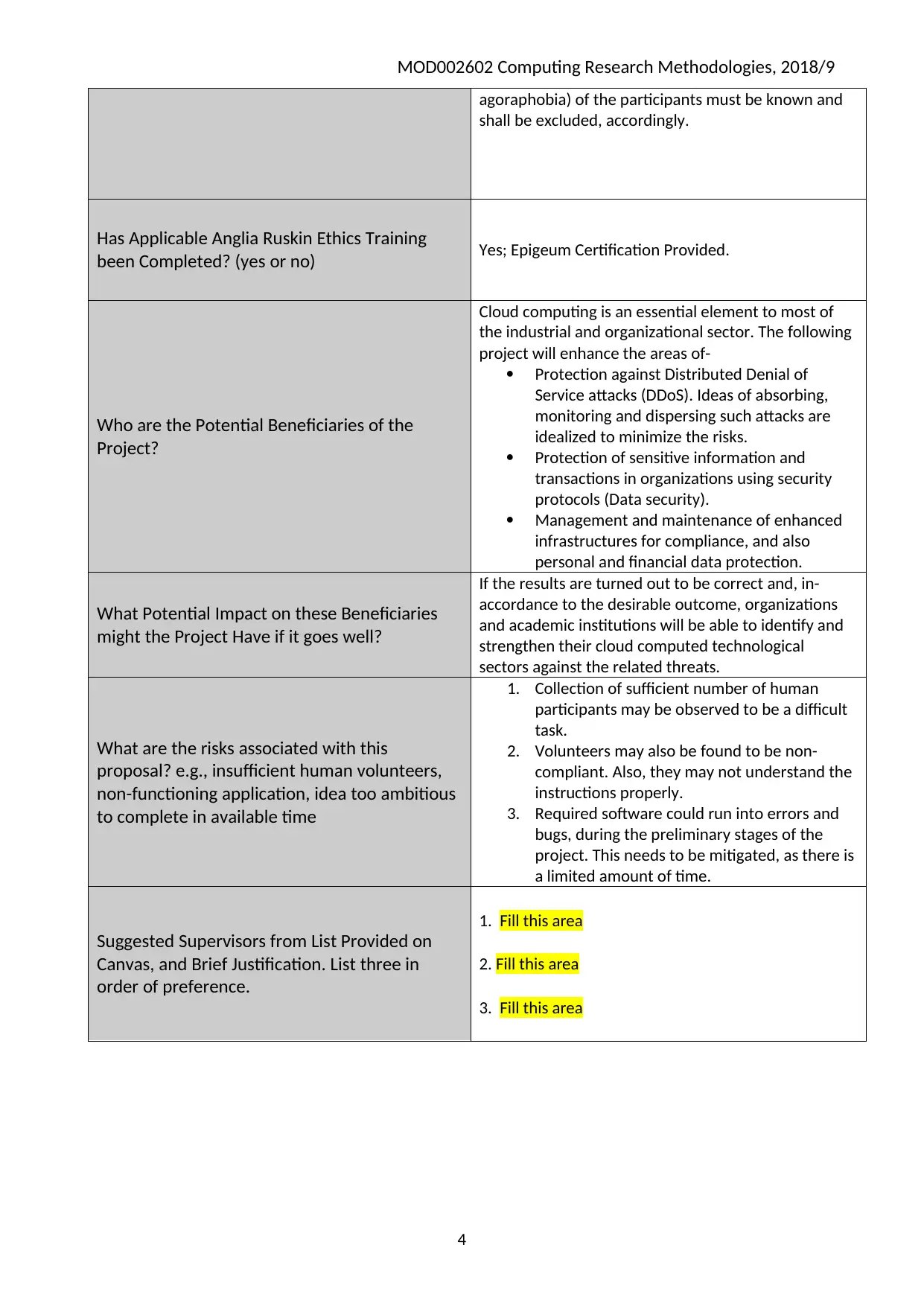
agoraphobia) of the participants must be known and
shall be excluded, accordingly.
Has Applicable Anglia Ruskin Ethics Training
been Completed? (yes or no) Yes; Epigeum Certification Provided.
Who are the Potential Beneficiaries of the
Project?
Cloud computing is an essential element to most of
the industrial and organizational sector. The following
project will enhance the areas of-
Protection against Distributed Denial of
Service attacks (DDoS). Ideas of absorbing,
monitoring and dispersing such attacks are
idealized to minimize the risks.
Protection of sensitive information and
transactions in organizations using security
protocols (Data security).
Management and maintenance of enhanced
infrastructures for compliance, and also
personal and financial data protection.
What Potential Impact on these Beneficiaries
might the Project Have if it goes well?
If the results are turned out to be correct and, in-
accordance to the desirable outcome, organizations
and academic institutions will be able to identify and
strengthen their cloud computed technological
sectors against the related threats.
What are the risks associated with this
proposal? e.g., insufficient human volunteers,
non-functioning application, idea too ambitious
to complete in available time
1. Collection of sufficient number of human
participants may be observed to be a difficult
task.
2. Volunteers may also be found to be non-
compliant. Also, they may not understand the
instructions properly.
3. Required software could run into errors and
bugs, during the preliminary stages of the
project. This needs to be mitigated, as there is
a limited amount of time.
Suggested Supervisors from List Provided on
Canvas, and Brief Justification. List three in
order of preference.
1. Fill this area
2. Fill this area
3. Fill this area
4
agoraphobia) of the participants must be known and
shall be excluded, accordingly.
Has Applicable Anglia Ruskin Ethics Training
been Completed? (yes or no) Yes; Epigeum Certification Provided.
Who are the Potential Beneficiaries of the
Project?
Cloud computing is an essential element to most of
the industrial and organizational sector. The following
project will enhance the areas of-
Protection against Distributed Denial of
Service attacks (DDoS). Ideas of absorbing,
monitoring and dispersing such attacks are
idealized to minimize the risks.
Protection of sensitive information and
transactions in organizations using security
protocols (Data security).
Management and maintenance of enhanced
infrastructures for compliance, and also
personal and financial data protection.
What Potential Impact on these Beneficiaries
might the Project Have if it goes well?
If the results are turned out to be correct and, in-
accordance to the desirable outcome, organizations
and academic institutions will be able to identify and
strengthen their cloud computed technological
sectors against the related threats.
What are the risks associated with this
proposal? e.g., insufficient human volunteers,
non-functioning application, idea too ambitious
to complete in available time
1. Collection of sufficient number of human
participants may be observed to be a difficult
task.
2. Volunteers may also be found to be non-
compliant. Also, they may not understand the
instructions properly.
3. Required software could run into errors and
bugs, during the preliminary stages of the
project. This needs to be mitigated, as there is
a limited amount of time.
Suggested Supervisors from List Provided on
Canvas, and Brief Justification. List three in
order of preference.
1. Fill this area
2. Fill this area
3. Fill this area
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MOD002602 Computing Research Methodologies, 2018/9
Part 2: Outline Methods (750 words, 25 marks)
Outline of Methods to be used for Data
Collection/Processing
(≈250 words)
For the following project, Systematic Literature Review
is appointed as the primary research method, whereas
interviews and surveys are considered to be the
secondary research method.
System Literature Review is the process of
identification, evaluation and interpretation of all
available research studies, relevant to specific research
topic, question or interest phenomenon.1 The review is
conducted with respect to a predefined search strategy.
SLR is generally undertaken for summarizing the
existing evidence, spotting the gaps in the present
research and, contributing it to the framework of the
new research activities.2 For the following research
work, systematic and guideline-based process by
kitchenham3, has been adopted. The review is
conducted in three phases: Planning (Identification of
the need and developing a review protocol); Conducting
(Selection of quality assessment, data extraction,
primary studies and data synthesis); Reporting
(Reporting of the results and documentations).
The secondary research method is Survey. In this
quantitative research type, respondents (experts) will
be selected under minimum experience criteria
between 1 to 31 years in Cloud Computing and, will be
provided a standardized questionnaire. Electronic
survey is undertaken for the respective research
method analysis. Participants will be offered
questionnaire via electronic mails.
Also, for the interviews, narrative and comparative
analysis will be conducted. Narrative method will
synthesize of non-quantitative method, appointing to
the extracted information that would be tabulated for
easy review. Framework of the method will consist of
the development of a theory, preliminary synthesis,
exploring relationships in data and assess to the
robustness of synthesis. For the Comparative analysis,
the relation and dissimilarities of the study’s contexts
will be evaluated.
1 O.P. Brereton, B.A. Kitchenham, D. Turner Budgen, M. Khalil, Lessons from applying the systematic literature review
process within the software engineering domain, Journal of Systems and Software 80 (4) (2017) 571–583.
2 M. Jørgensen, K. Moløkken-Østvold How large are software cost overruns? A review of the 1994 CHAOS report
Information and Software Technology, 48 (2016), pp. 297-301
3 L.M. Pickard, B.A. Kitchenham, P. Jones, Combining empirical results in software engineering, Information and
Software Technology 40 (14) (2015) 811–821.
5
Part 2: Outline Methods (750 words, 25 marks)
Outline of Methods to be used for Data
Collection/Processing
(≈250 words)
For the following project, Systematic Literature Review
is appointed as the primary research method, whereas
interviews and surveys are considered to be the
secondary research method.
System Literature Review is the process of
identification, evaluation and interpretation of all
available research studies, relevant to specific research
topic, question or interest phenomenon.1 The review is
conducted with respect to a predefined search strategy.
SLR is generally undertaken for summarizing the
existing evidence, spotting the gaps in the present
research and, contributing it to the framework of the
new research activities.2 For the following research
work, systematic and guideline-based process by
kitchenham3, has been adopted. The review is
conducted in three phases: Planning (Identification of
the need and developing a review protocol); Conducting
(Selection of quality assessment, data extraction,
primary studies and data synthesis); Reporting
(Reporting of the results and documentations).
The secondary research method is Survey. In this
quantitative research type, respondents (experts) will
be selected under minimum experience criteria
between 1 to 31 years in Cloud Computing and, will be
provided a standardized questionnaire. Electronic
survey is undertaken for the respective research
method analysis. Participants will be offered
questionnaire via electronic mails.
Also, for the interviews, narrative and comparative
analysis will be conducted. Narrative method will
synthesize of non-quantitative method, appointing to
the extracted information that would be tabulated for
easy review. Framework of the method will consist of
the development of a theory, preliminary synthesis,
exploring relationships in data and assess to the
robustness of synthesis. For the Comparative analysis,
the relation and dissimilarities of the study’s contexts
will be evaluated.
1 O.P. Brereton, B.A. Kitchenham, D. Turner Budgen, M. Khalil, Lessons from applying the systematic literature review
process within the software engineering domain, Journal of Systems and Software 80 (4) (2017) 571–583.
2 M. Jørgensen, K. Moløkken-Østvold How large are software cost overruns? A review of the 1994 CHAOS report
Information and Software Technology, 48 (2016), pp. 297-301
3 L.M. Pickard, B.A. Kitchenham, P. Jones, Combining empirical results in software engineering, Information and
Software Technology 40 (14) (2015) 811–821.
5
MOD002602 Computing Research Methodologies, 2018/9
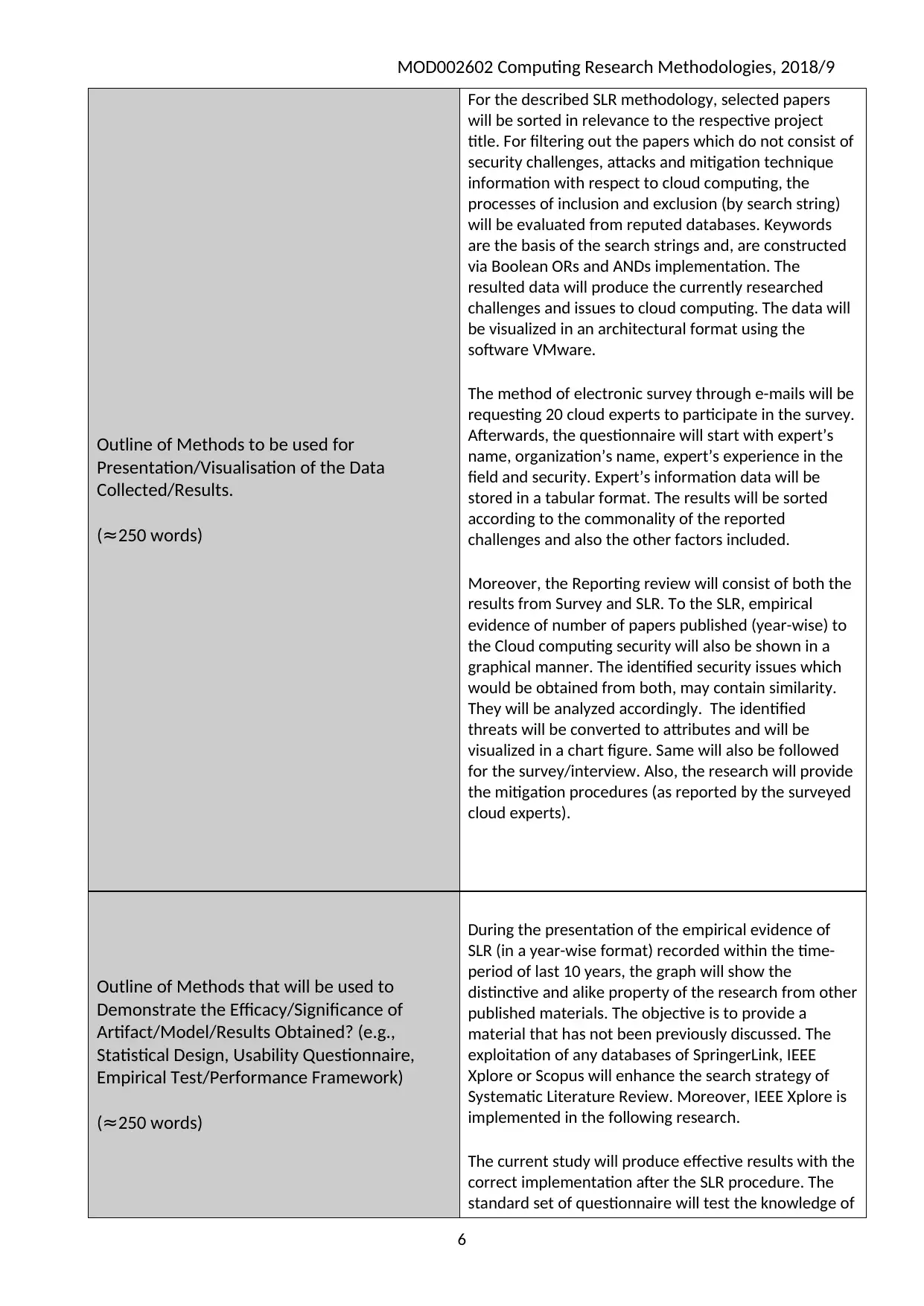
Outline of Methods to be used for
Presentation/Visualisation of the Data
Collected/Results.
(≈250 words)
For the described SLR methodology, selected papers
will be sorted in relevance to the respective project
title. For filtering out the papers which do not consist of
security challenges, attacks and mitigation technique
information with respect to cloud computing, the
processes of inclusion and exclusion (by search string)
will be evaluated from reputed databases. Keywords
are the basis of the search strings and, are constructed
via Boolean ORs and ANDs implementation. The
resulted data will produce the currently researched
challenges and issues to cloud computing. The data will
be visualized in an architectural format using the
software VMware.
The method of electronic survey through e-mails will be
requesting 20 cloud experts to participate in the survey.
Afterwards, the questionnaire will start with expert’s
name, organization’s name, expert’s experience in the
field and security. Expert’s information data will be
stored in a tabular format. The results will be sorted
according to the commonality of the reported
challenges and also the other factors included.
Moreover, the Reporting review will consist of both the
results from Survey and SLR. To the SLR, empirical
evidence of number of papers published (year-wise) to
the Cloud computing security will also be shown in a
graphical manner. The identified security issues which
would be obtained from both, may contain similarity.
They will be analyzed accordingly. The identified
threats will be converted to attributes and will be
visualized in a chart figure. Same will also be followed
for the survey/interview. Also, the research will provide
the mitigation procedures (as reported by the surveyed
cloud experts).
Outline of Methods that will be used to
Demonstrate the Efficacy/Significance of
Artifact/Model/Results Obtained? (e.g.,
Statistical Design, Usability Questionnaire,
Empirical Test/Performance Framework)
(≈250 words)
During the presentation of the empirical evidence of
SLR (in a year-wise format) recorded within the time-
period of last 10 years, the graph will show the
distinctive and alike property of the research from other
published materials. The objective is to provide a
material that has not been previously discussed. The
exploitation of any databases of SpringerLink, IEEE
Xplore or Scopus will enhance the search strategy of
Systematic Literature Review. Moreover, IEEE Xplore is
implemented in the following research.
The current study will produce effective results with the
correct implementation after the SLR procedure. The
standard set of questionnaire will test the knowledge of
6
Outline of Methods to be used for
Presentation/Visualisation of the Data
Collected/Results.
(≈250 words)
For the described SLR methodology, selected papers
will be sorted in relevance to the respective project
title. For filtering out the papers which do not consist of
security challenges, attacks and mitigation technique
information with respect to cloud computing, the
processes of inclusion and exclusion (by search string)
will be evaluated from reputed databases. Keywords
are the basis of the search strings and, are constructed
via Boolean ORs and ANDs implementation. The
resulted data will produce the currently researched
challenges and issues to cloud computing. The data will
be visualized in an architectural format using the
software VMware.
The method of electronic survey through e-mails will be
requesting 20 cloud experts to participate in the survey.
Afterwards, the questionnaire will start with expert’s
name, organization’s name, expert’s experience in the
field and security. Expert’s information data will be
stored in a tabular format. The results will be sorted
according to the commonality of the reported
challenges and also the other factors included.
Moreover, the Reporting review will consist of both the
results from Survey and SLR. To the SLR, empirical
evidence of number of papers published (year-wise) to
the Cloud computing security will also be shown in a
graphical manner. The identified security issues which
would be obtained from both, may contain similarity.
They will be analyzed accordingly. The identified
threats will be converted to attributes and will be
visualized in a chart figure. Same will also be followed
for the survey/interview. Also, the research will provide
the mitigation procedures (as reported by the surveyed
cloud experts).
Outline of Methods that will be used to
Demonstrate the Efficacy/Significance of
Artifact/Model/Results Obtained? (e.g.,
Statistical Design, Usability Questionnaire,
Empirical Test/Performance Framework)
(≈250 words)
During the presentation of the empirical evidence of
SLR (in a year-wise format) recorded within the time-
period of last 10 years, the graph will show the
distinctive and alike property of the research from other
published materials. The objective is to provide a
material that has not been previously discussed. The
exploitation of any databases of SpringerLink, IEEE
Xplore or Scopus will enhance the search strategy of
Systematic Literature Review. Moreover, IEEE Xplore is
implemented in the following research.
The current study will produce effective results with the
correct implementation after the SLR procedure. The
standard set of questionnaire will test the knowledge of
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

MOD002602 Computing Research Methodologies, 2018/9
the cloud experts. Accordingly, the suitable candidates
will be chosen. The participants will also be kept under
partial supervision to report as expected. Each response
will be stored in a separate data-field (distinctly
allocated ‘Unique Identification Number’).
Further, suggestions from the appointed 20 experts will
be summarized to mitigate future challenges with
respect to the vulnerabilities in Cloud Computing. The
effective use of RSA algorithm, API access control and
more methods are included in the minimization.
Part 3: Detailed Review of Examples of Relevant Literature (750 words, 25 marks)
Next, using http://scholar.google.com, enter the keywords you identified above, along with words
from your proposed title, to find ONE journal article and ONE conference article that are
somewhat similar to your research idea. Record the details of these articles in the tables below. If
you only find journal articles, then replicate and complete the journal article table twice. Likewise
if you only find conference articles, replicate and complete that table twice. For now, books,
websites, and company materials/white papers will not qualify as appropriate literature.
Guidance:
1. The journal must be registered in http://scimagojr.com (which uses SCOPUS). If it is not, then it
is not a reputable source, and you should select a different journal. If the journal hosting the
article you selected is in the third or fourth quartile, treat it very skeptically. Likewise, if the
conference hosting the conference article you have selected is not registered with
http://conferencerankings.com (or similar), or if the conference is ranked poorly, choose a
different article (ideally) or treat the article with a great deal of skepticism.
2. The full PDF of the journal/conference articles you select must be accessible to you, so that
you can read it thoroughly and begin writing your summary.
3. The article should normally be relatively recent, as computer science can change rapidly. We’ll
say within the last 10 years, unless you have a compelling reason for using a seminal/early
study. The paper should have a method and present results, and not be just a review.
4. In selecting conferences, be wary that many (most) conferences are not selective in what
articles they accept, and do not review the articles submitted to them properly. This makes the
7
the cloud experts. Accordingly, the suitable candidates
will be chosen. The participants will also be kept under
partial supervision to report as expected. Each response
will be stored in a separate data-field (distinctly
allocated ‘Unique Identification Number’).
Further, suggestions from the appointed 20 experts will
be summarized to mitigate future challenges with
respect to the vulnerabilities in Cloud Computing. The
effective use of RSA algorithm, API access control and
more methods are included in the minimization.
Part 3: Detailed Review of Examples of Relevant Literature (750 words, 25 marks)
Next, using http://scholar.google.com, enter the keywords you identified above, along with words
from your proposed title, to find ONE journal article and ONE conference article that are
somewhat similar to your research idea. Record the details of these articles in the tables below. If
you only find journal articles, then replicate and complete the journal article table twice. Likewise
if you only find conference articles, replicate and complete that table twice. For now, books,
websites, and company materials/white papers will not qualify as appropriate literature.
Guidance:
1. The journal must be registered in http://scimagojr.com (which uses SCOPUS). If it is not, then it
is not a reputable source, and you should select a different journal. If the journal hosting the
article you selected is in the third or fourth quartile, treat it very skeptically. Likewise, if the
conference hosting the conference article you have selected is not registered with
http://conferencerankings.com (or similar), or if the conference is ranked poorly, choose a
different article (ideally) or treat the article with a great deal of skepticism.
2. The full PDF of the journal/conference articles you select must be accessible to you, so that
you can read it thoroughly and begin writing your summary.
3. The article should normally be relatively recent, as computer science can change rapidly. We’ll
say within the last 10 years, unless you have a compelling reason for using a seminal/early
study. The paper should have a method and present results, and not be just a review.
4. In selecting conferences, be wary that many (most) conferences are not selective in what
articles they accept, and do not review the articles submitted to them properly. This makes the
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MOD002602 Computing Research Methodologies, 2018/9
articles they publish poor quality and unreliable. Searching for a conference with a good
quality sponsor, like the IEEE or ACM, is one way of filtering out the swamp of poor quality
conference articles.
5. If you cannot locate all the information for the boxes below, then it may be that you have not
found an appropriate source. If you are sure this information is nowhere to be found, continue
looking for a different article.
6. Write your summary/review in the third person, using complete sentence. Just write about
what the paper does – avoid writing about your own (worthless) opinions – stick to the facts
about what you have in front of you and just summarize what the paper does.
8
articles they publish poor quality and unreliable. Searching for a conference with a good
quality sponsor, like the IEEE or ACM, is one way of filtering out the swamp of poor quality
conference articles.
5. If you cannot locate all the information for the boxes below, then it may be that you have not
found an appropriate source. If you are sure this information is nowhere to be found, continue
looking for a different article.
6. Write your summary/review in the third person, using complete sentence. Just write about
what the paper does – avoid writing about your own (worthless) opinions – stick to the facts
about what you have in front of you and just summarize what the paper does.
8
MOD002602 Computing Research Methodologies, 2018/9
(a) Detailed Review of ONE Journal Article
Article Title Toward Secure and Dependable Storage Services in Cloud
Computing
Journal Title IEEE Transactions on Services Computing
Year Published 2014
Volume 5
Issue 2
Page Range (Start-End) 220-232
DOI 10.1109/tsc.2011.24
Journal Quartile(s) on
www.scimagojr.com
Q1 (Computer Networks and Communication); Q1 (Computer
Science Applications); Q1 (Hardware and Architecture); Q1
(Information Systems and Management)
Number of Citations on
www.scholar.google.com 691
Summary of Article (Research
Question Asked/Hypothesis
Tested, Method Used, Results,
Discussion)
≈ 375 words
In this article, a flexible and efficient distributed storage
authentication scheme has been proposed to assure availability
and correctiveness to the cloud users’ during dynamically explicit
data support. Erasure codes are implemented in file distribution
system for managing redundancies and ensuring dependability of
data against the Byzantine servers4; here, storage servers fail in
arbitrary ways. Our system is efficient to react to detection of
data correction and guarantees concurrent data error localization
that is, misbehaving server’s identification. Further, for balance
between data dynamics and error’s volatility (resilience),
algebraic property of a computed token and erasure-
programmed data are explored. Third-part auditing is supported
for worry-less cloud storage services usage and also safe
delegation of tasks integrity checking. The contribution of the
paper is to recorded to meet the following objectives:
While, the predecessors only provide storage status’s
results in binary format across the distributed
systems/servers. The following project achieves an
integrated storage corrected insurance and identification
of defected and deviated server(s).
The new scheme allows secure and potent dynamic
operations to the blocks of data, which includes: delete,
update and append.
The results of the experiment discusses the efficiency of
4 C. Wang, Q. Wang, K. Ren, and W. Lou, “Ensuring data storage security in cloud computing,” in Proc. of IWQoS’09,
July 2013, pp. 1–9.
9
(a) Detailed Review of ONE Journal Article
Article Title Toward Secure and Dependable Storage Services in Cloud
Computing
Journal Title IEEE Transactions on Services Computing
Year Published 2014
Volume 5
Issue 2
Page Range (Start-End) 220-232
DOI 10.1109/tsc.2011.24
Journal Quartile(s) on
www.scimagojr.com
Q1 (Computer Networks and Communication); Q1 (Computer
Science Applications); Q1 (Hardware and Architecture); Q1
(Information Systems and Management)
Number of Citations on
www.scholar.google.com 691
Summary of Article (Research
Question Asked/Hypothesis
Tested, Method Used, Results,
Discussion)
≈ 375 words
In this article, a flexible and efficient distributed storage
authentication scheme has been proposed to assure availability
and correctiveness to the cloud users’ during dynamically explicit
data support. Erasure codes are implemented in file distribution
system for managing redundancies and ensuring dependability of
data against the Byzantine servers4; here, storage servers fail in
arbitrary ways. Our system is efficient to react to detection of
data correction and guarantees concurrent data error localization
that is, misbehaving server’s identification. Further, for balance
between data dynamics and error’s volatility (resilience),
algebraic property of a computed token and erasure-
programmed data are explored. Third-part auditing is supported
for worry-less cloud storage services usage and also safe
delegation of tasks integrity checking. The contribution of the
paper is to recorded to meet the following objectives:
While, the predecessors only provide storage status’s
results in binary format across the distributed
systems/servers. The following project achieves an
integrated storage corrected insurance and identification
of defected and deviated server(s).
The new scheme allows secure and potent dynamic
operations to the blocks of data, which includes: delete,
update and append.
The results of the experiment discusses the efficiency of
4 C. Wang, Q. Wang, K. Ren, and W. Lou, “Ensuring data storage security in cloud computing,” in Proc. of IWQoS’09,
July 2013, pp. 1–9.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
MOD002602 Computing Research Methodologies, 2018/9
the proposal scheme. Security analysis’s extensiveness
shows the resiliency against the failure of Byzantine
systems, malicious attacks to modification and also,
server attack.
During the next sections, the paper introduces models with
respect to system (identified network entities being User, Cloud
Server and Third Part Auditor), adversary, design and notations.
Further, the recovery of storage errors or identification of
potential threats from external attacks are successfully detected
and addressed in the main scheme of ensuring storage of cloud
data to the users. The first part reviews the basic tool of the
coding theory, while the next section introduces a holomorphic
token (with respect to a universal hash function5). The whole
process of assuring cloud data storage has followed several
methods of preparation of file distribution, pre-computational
token challenges, error localization for eliminating errors in the
storage of the systems, error recovery and file retrieval and,
Third party auditing implementation and observations. All the
above mentioned steps are processed in the performance
evaluation. Lastly, in the design phase, dynamic data operations
has enhanced the update, delete and append operations,
expressed and represented in the algebraic functions.
Moreover, the paper investigated the data security problem to
cloud-distributed data storage system and, has proposed a highly
resilient, effective and flexible cloud storage servers and services.
The server colluding attacks are also identified and optimized to
the appropriate significance of the paper’s justification.
(b) Detailed Review of ONE Conference Article
Article Title Collaboration-Based Cloud Computing Security Management
Framework
Conference Title IEEE 4th International Conference on Cloud Computing
(CLOUD 2015)
Date Range of Conference 04-09 July 2015
Location of Conference Washington DC, United States
Page Range in Proceedings 364-371
DOI http://dx.doi.org/10.1109/CLOUD.2011.9
Conference Ranking on
http://www.conferenceranks.com/ B (ERA)
5 H. Shacham and B. Waters, “Compact proofs of retrievability,” in Proc. of Asiacrypt’08, volume 5350 of LNCS, 2012,
pp. 90–107
10
the proposal scheme. Security analysis’s extensiveness
shows the resiliency against the failure of Byzantine
systems, malicious attacks to modification and also,
server attack.
During the next sections, the paper introduces models with
respect to system (identified network entities being User, Cloud
Server and Third Part Auditor), adversary, design and notations.
Further, the recovery of storage errors or identification of
potential threats from external attacks are successfully detected
and addressed in the main scheme of ensuring storage of cloud
data to the users. The first part reviews the basic tool of the
coding theory, while the next section introduces a holomorphic
token (with respect to a universal hash function5). The whole
process of assuring cloud data storage has followed several
methods of preparation of file distribution, pre-computational
token challenges, error localization for eliminating errors in the
storage of the systems, error recovery and file retrieval and,
Third party auditing implementation and observations. All the
above mentioned steps are processed in the performance
evaluation. Lastly, in the design phase, dynamic data operations
has enhanced the update, delete and append operations,
expressed and represented in the algebraic functions.
Moreover, the paper investigated the data security problem to
cloud-distributed data storage system and, has proposed a highly
resilient, effective and flexible cloud storage servers and services.
The server colluding attacks are also identified and optimized to
the appropriate significance of the paper’s justification.
(b) Detailed Review of ONE Conference Article
Article Title Collaboration-Based Cloud Computing Security Management
Framework
Conference Title IEEE 4th International Conference on Cloud Computing
(CLOUD 2015)
Date Range of Conference 04-09 July 2015
Location of Conference Washington DC, United States
Page Range in Proceedings 364-371
DOI http://dx.doi.org/10.1109/CLOUD.2011.9
Conference Ranking on
http://www.conferenceranks.com/ B (ERA)
5 H. Shacham and B. Waters, “Compact proofs of retrievability,” in Proc. of Asiacrypt’08, volume 5350 of LNCS, 2012,
pp. 90–107
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

MOD002602 Computing Research Methodologies, 2018/9
Number of Citations on
www.scholar.google.com 202
Summary (Research Question
Asked/Hypothesis Tested, Method
Used, Results, Discussion)
≈ 375 words
In this paper, a flexible and efficient distributed storage
authentication scheme has been observed to be framed for
tackling losses with respect to trust and security in the cloud
environment. The execution is mostly enabled through the
extension of Security Management Process (SMP) in the
cloud hosted assets.6 The approach of the respective project
was to improve and support the collaborative strength
among the cloud stakeholders during the development of a
cloud secure and enforced network, comprising of all the
needs. Following issues were addressed in the following
approach:
What are the required security controls that can
mitigate the adopted service risks and also, who is
responsible for selecting such controls?
What are the required security protocols for
protecting the hosted cloud service, under the usage
of numerous tenants at a particular time?
What is the availability scope of the selected controls?
Which security metrics are needed for calculation of
cloud-hosted services security status?
The path is based on the alignment of FISMA standard where
the cloud model and cloud security are maintained to cover
the needs of the stakeholders. The alignment is covered
through the methods of Categorization of Service Security (to
all tenants) (the security is calculated to the likelihood and
exposure levels). Next step followed the ‘tailoring process to
security controls baseline’7 to create methods for mitigation
of risks, mainly by scoping (identification), compensating,
parameter setting of Security Controls. Then, the steps of
implementation and assessment of security controls are
evaluated, followed by the authorization of services and
effectiveness monitoring of the security controls. Formats of
the adopted standards of security are categorized in
Common Platform Enumeration (CPE)8, Common Weakness
Enumeration (CWE), Common Attack Pattern Enumeration
and Classification (CAPEC)9, Common Vulnerability and
Exposure (CVE)10 and Common Configuration Enumeration
(CCE)11. These are visualized in both class diagram and table
6 M. Menzel and C. Meinel, "SecureSOA Modelling Security Requirements for Service-Oriented Architectures," IEEE
International Conference on Services Computing, 2013
7 P. Saripalli and B. Walters, "QUIRC: A Quantitative Impact and Risk Assessment Framework for Cloud Security,", IEEE
8 S. Quinn, K. Scarfone, M. Barrett, and C. Johnson, NIST Special Publication 800-117, Guide to Adopting and Using the
Security Content Automation Protocol, July 2012. See http://csrc.nist.gov/publications/PubsSPs.html#800-117.
9 Barnum, S., 2012. Common attack pattern enumeration and classification (capec) schema description. Cigital Inc,
http://capec. mitre. org/documents/documentation/CAPEC_Schema_Descr iption_v1, 3.
10 G. Hoglund and G. McGraw. Exploiting Software: How to Break Code. Addison-Wesley, February 2014.
11 Mockapetris, P., "Domain Names – Implementation and Specification", RFC 1035, November 2013.
11
Number of Citations on
www.scholar.google.com 202
Summary (Research Question
Asked/Hypothesis Tested, Method
Used, Results, Discussion)
≈ 375 words
In this paper, a flexible and efficient distributed storage
authentication scheme has been observed to be framed for
tackling losses with respect to trust and security in the cloud
environment. The execution is mostly enabled through the
extension of Security Management Process (SMP) in the
cloud hosted assets.6 The approach of the respective project
was to improve and support the collaborative strength
among the cloud stakeholders during the development of a
cloud secure and enforced network, comprising of all the
needs. Following issues were addressed in the following
approach:
What are the required security controls that can
mitigate the adopted service risks and also, who is
responsible for selecting such controls?
What are the required security protocols for
protecting the hosted cloud service, under the usage
of numerous tenants at a particular time?
What is the availability scope of the selected controls?
Which security metrics are needed for calculation of
cloud-hosted services security status?
The path is based on the alignment of FISMA standard where
the cloud model and cloud security are maintained to cover
the needs of the stakeholders. The alignment is covered
through the methods of Categorization of Service Security (to
all tenants) (the security is calculated to the likelihood and
exposure levels). Next step followed the ‘tailoring process to
security controls baseline’7 to create methods for mitigation
of risks, mainly by scoping (identification), compensating,
parameter setting of Security Controls. Then, the steps of
implementation and assessment of security controls are
evaluated, followed by the authorization of services and
effectiveness monitoring of the security controls. Formats of
the adopted standards of security are categorized in
Common Platform Enumeration (CPE)8, Common Weakness
Enumeration (CWE), Common Attack Pattern Enumeration
and Classification (CAPEC)9, Common Vulnerability and
Exposure (CVE)10 and Common Configuration Enumeration
(CCE)11. These are visualized in both class diagram and table
6 M. Menzel and C. Meinel, "SecureSOA Modelling Security Requirements for Service-Oriented Architectures," IEEE
International Conference on Services Computing, 2013
7 P. Saripalli and B. Walters, "QUIRC: A Quantitative Impact and Risk Assessment Framework for Cloud Security,", IEEE
8 S. Quinn, K. Scarfone, M. Barrett, and C. Johnson, NIST Special Publication 800-117, Guide to Adopting and Using the
Security Content Automation Protocol, July 2012. See http://csrc.nist.gov/publications/PubsSPs.html#800-117.
9 Barnum, S., 2012. Common attack pattern enumeration and classification (capec) schema description. Cigital Inc,
http://capec. mitre. org/documents/documentation/CAPEC_Schema_Descr iption_v1, 3.
10 G. Hoglund and G. McGraw. Exploiting Software: How to Break Code. Addison-Wesley, February 2014.
11 Mockapetris, P., "Domain Names – Implementation and Specification", RFC 1035, November 2013.
11
MOD002602 Computing Research Methodologies, 2018/9
format. The lastly obtained framework architecture is
comprised of three layers:
Management layer
Enforcement layer
Feedback layer
The entire framework was used in a prototype model and
implemented in the following steps at the Auckland and
Swinburne’s cloud based ERP system. The whole recorded
observations and results are also demonstrated, according to
the recorded events.
Moreover, the whole comprehensive approach provided a
set of security management process and models has
provided descriptions on the platform services, stakeholders
security requirements; deployed cloud’s identified risks,
threats and mitigations; a security plan development tool and
a partially automated security plan. The whole framework is
efficient to cloud providers in management of the cloud
platforms by consumers for their management on cloud-
hosted devices and also, enabling outsourcing internal SMP
to the cloud.
Part 4: Literature Review (600 words, 20 marks)
An initial Literature Review of
published work.
Sources should adhere to
guidelines described in Part 3.
Review should compare the
approaches (methods) used in
each article, and their findings,
rather than just describing the
ten articles one at a time
sequentially.
Do not attribute weight to
speculative comments in
articles; stick to reviewing
methods and findings that are
backed up by evidence (i.e.,
the data collected/analysed in
the article).
Write about 10 sources.
≈ 600 words
1) Secure virtualization for cloud computing
This proposed paper is a novel architecture on ACPS (Advanced
Cloud Protection System) conducted on increasing the level of
security in cloud environment. Reaction of ACPS is recorded
under security breaches and security management layers.12 The
prototype of the respective model will be implemented on open
source solutions of: OpenECP and Eucalyptus. Aims: Shown
effectiveness of prototype testing against known attacks; ACPS
prototype’s performance evaluation under different workload.
Results show the resiliency against the attacks and the compared
overhead to be limited with respected to the provided
components.
2) Understanding the determinants of cloud computing
adoption
The paper investigates the affecting factors during cloud
computing adoption in firms to the high-tech industry. The
methodology is based on questionnaire-based survey for data
collection from 110 firms to a Taiwanese’s high-tech industry.
Respected hypothesis was tested and deprived under regressive
logistic analysis. The findings revealed the significant effect of
relative advantage, firm size, technology readiness, competitive
pressure, compatibility and more, to the adoption of cloud
computing.
3) Cloud Computing – The Business Perspective
This study generalizes the need of business in understanding the
12 P.T. Jaeger, J. Lin and J.M. Grimes, Cloud computing and information policy: computing in a policy cloud?. Journal of
Information Technology & Politics, 2008; 5 (3): 269-283.
12
format. The lastly obtained framework architecture is
comprised of three layers:
Management layer
Enforcement layer
Feedback layer
The entire framework was used in a prototype model and
implemented in the following steps at the Auckland and
Swinburne’s cloud based ERP system. The whole recorded
observations and results are also demonstrated, according to
the recorded events.
Moreover, the whole comprehensive approach provided a
set of security management process and models has
provided descriptions on the platform services, stakeholders
security requirements; deployed cloud’s identified risks,
threats and mitigations; a security plan development tool and
a partially automated security plan. The whole framework is
efficient to cloud providers in management of the cloud
platforms by consumers for their management on cloud-
hosted devices and also, enabling outsourcing internal SMP
to the cloud.
Part 4: Literature Review (600 words, 20 marks)
An initial Literature Review of
published work.
Sources should adhere to
guidelines described in Part 3.
Review should compare the
approaches (methods) used in
each article, and their findings,
rather than just describing the
ten articles one at a time
sequentially.
Do not attribute weight to
speculative comments in
articles; stick to reviewing
methods and findings that are
backed up by evidence (i.e.,
the data collected/analysed in
the article).
Write about 10 sources.
≈ 600 words
1) Secure virtualization for cloud computing
This proposed paper is a novel architecture on ACPS (Advanced
Cloud Protection System) conducted on increasing the level of
security in cloud environment. Reaction of ACPS is recorded
under security breaches and security management layers.12 The
prototype of the respective model will be implemented on open
source solutions of: OpenECP and Eucalyptus. Aims: Shown
effectiveness of prototype testing against known attacks; ACPS
prototype’s performance evaluation under different workload.
Results show the resiliency against the attacks and the compared
overhead to be limited with respected to the provided
components.
2) Understanding the determinants of cloud computing
adoption
The paper investigates the affecting factors during cloud
computing adoption in firms to the high-tech industry. The
methodology is based on questionnaire-based survey for data
collection from 110 firms to a Taiwanese’s high-tech industry.
Respected hypothesis was tested and deprived under regressive
logistic analysis. The findings revealed the significant effect of
relative advantage, firm size, technology readiness, competitive
pressure, compatibility and more, to the adoption of cloud
computing.
3) Cloud Computing – The Business Perspective
This study generalizes the need of business in understanding the
12 P.T. Jaeger, J. Lin and J.M. Grimes, Cloud computing and information policy: computing in a policy cloud?. Journal of
Information Technology & Politics, 2008; 5 (3): 269-283.
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
