Communication Systems Assignment: Modulation, Error Detection, WLAN
VerifiedAdded on 2023/06/03
|17
|2315
|81
Homework Assignment
AI Summary
This document provides a comprehensive solution to a communication systems assignment. It begins by detailing various analog modulation techniques, including ASK, FSK, PSK, DPSK, and multilevel ASK and PSK, converting a binary data sequence into analog waveforms. The solution then computes frequency assignments for a 16-level FSK system. Further, it includes drawings of analog and frequency modulation waveforms. The assignment also covers the creation of a 16 QAM constellation diagram and provides a detailed explanation of the error detection process using Cyclic Redundancy Check (CRC), including computations for a given message and pattern. The solution extends to the analysis of Direct Sequence Spread Spectrum (DSSS) signal transmission and compares the differences between infrastructure and ad-hoc modes in WLAN, including comparative illustrations. Finally, the document explains the preference for hexagonal shapes in cellular communication.

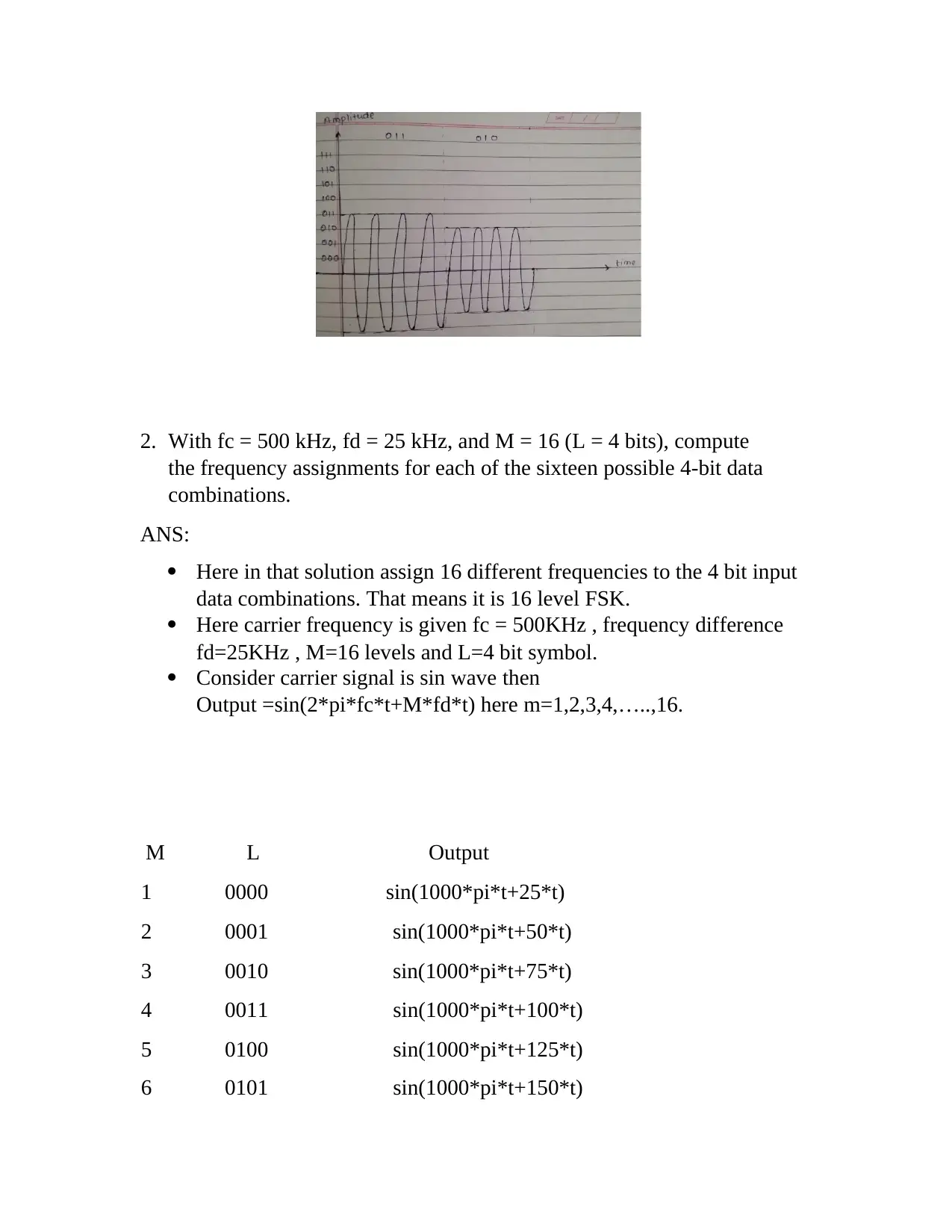
1. Convert the binary data “011010” into analog waveforms using following
modulation techniques:
a. Two level Amplitude Shift Keying
b. Two level Frequency Shift Keying
c. Two level Phase Shift Keying
d. Differential Phase shift keying
e. Four level Amplitude Shift Keying
f. Four level Phase Shift Keying
g. Eight level Amplitude Shift Keying
ANS:
a. Two level Amplitude Shift Keying
Amplitude Shift Keying is the simplest type of digital
CW modulation.
The ASK modulator is nothing but a multiplier followed by band
pass filter.
This multiplier multiply the NRZ digital signal and the sinusoidal
carrier to produce the ASK signal as its output.
Two level ASK means Binary ASK. Due to the multiplication the
ASK output will present only a binary 1 is to be transmitted.
ASK output corresponding to binary 0 is zero.
modulation techniques:
a. Two level Amplitude Shift Keying
b. Two level Frequency Shift Keying
c. Two level Phase Shift Keying
d. Differential Phase shift keying
e. Four level Amplitude Shift Keying
f. Four level Phase Shift Keying
g. Eight level Amplitude Shift Keying
ANS:
a. Two level Amplitude Shift Keying
Amplitude Shift Keying is the simplest type of digital
CW modulation.
The ASK modulator is nothing but a multiplier followed by band
pass filter.
This multiplier multiply the NRZ digital signal and the sinusoidal
carrier to produce the ASK signal as its output.
Two level ASK means Binary ASK. Due to the multiplication the
ASK output will present only a binary 1 is to be transmitted.
ASK output corresponding to binary 0 is zero.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

b. Two level Frequency Shift Keying
In FSK frequency of the carrier signal varies according to the
digital input signal but there is no change in the amplitude and
phase of the carrier.
Two level FSK called as Binary FSK. The output of a FSK
modulated wave is high in frequency for a binary 1 input and is
low in frequency for a binary 0 input.
c. Two level Phase Shift Keying
Binary PSK is the most efficient of the three modulation methods,
i.e ASK, FSK, PSK. Therefore it is used for high bit rate.
In BPSK phase of the sinusoidal carrier changes according to
the data bit to be transmitted.
In BPSK carrier phase is changed between 0 degree and 180
degree by the bipolar digital signal.
d. Differential Phase shift keying
In FSK frequency of the carrier signal varies according to the
digital input signal but there is no change in the amplitude and
phase of the carrier.
Two level FSK called as Binary FSK. The output of a FSK
modulated wave is high in frequency for a binary 1 input and is
low in frequency for a binary 0 input.
c. Two level Phase Shift Keying
Binary PSK is the most efficient of the three modulation methods,
i.e ASK, FSK, PSK. Therefore it is used for high bit rate.
In BPSK phase of the sinusoidal carrier changes according to
the data bit to be transmitted.
In BPSK carrier phase is changed between 0 degree and 180
degree by the bipolar digital signal.
d. Differential Phase shift keying

DPSK combines two basic operations
1) The differential encoding and
2) Phase shift keying
DPSK will eliminate the ambiguity about whether the received
data was inverted or not.
DPSK does not require the synchronous carrier at the demodulator
at the detection.
e. Four level Amplitude Shift Keying
In four level Amplitude Shift Keying amplitude of carrier signal
changes in four levels according to the input digital signal which
is divide in 2 bit symbols.
Here binary input is 011010 ,so divide this in 2 bit symbol like this
01 10 10
For 00, 01, 10, 11 inputs 4 different amplitude carrier signal will
get at the output.
1) The differential encoding and
2) Phase shift keying
DPSK will eliminate the ambiguity about whether the received
data was inverted or not.
DPSK does not require the synchronous carrier at the demodulator
at the detection.
e. Four level Amplitude Shift Keying
In four level Amplitude Shift Keying amplitude of carrier signal
changes in four levels according to the input digital signal which
is divide in 2 bit symbols.
Here binary input is 011010 ,so divide this in 2 bit symbol like this
01 10 10
For 00, 01, 10, 11 inputs 4 different amplitude carrier signal will
get at the output.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

f. Four level Phase Shift Keying
In Four level PSK carrier changes in 4 phases
(0,90,180,270 degrees) according to the 2 bit(symbol) input
digital signal.
For 00, 01, 10, 11 input signal phases are 0, 90, 180, 270 degree
respectively.
g. Eight level Amplitude Shift Keying
In eight level ASK amplitude of carrier signal changes in eight
level according to the binary input signal which is 3bit symbol.
Here binary input is 011010 ,so divide it into 3 bit symbol like this
011 010
For 000 , 001, 010, 011, 100, 101, 110, 111 these eight binary
input signal 8 different amplitude assigned.
In Four level PSK carrier changes in 4 phases
(0,90,180,270 degrees) according to the 2 bit(symbol) input
digital signal.
For 00, 01, 10, 11 input signal phases are 0, 90, 180, 270 degree
respectively.
g. Eight level Amplitude Shift Keying
In eight level ASK amplitude of carrier signal changes in eight
level according to the binary input signal which is 3bit symbol.
Here binary input is 011010 ,so divide it into 3 bit symbol like this
011 010
For 000 , 001, 010, 011, 100, 101, 110, 111 these eight binary
input signal 8 different amplitude assigned.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2. With fc = 500 kHz, fd = 25 kHz, and M = 16 (L = 4 bits), compute
the frequency assignments for each of the sixteen possible 4-bit data
combinations.
ANS:
Here in that solution assign 16 different frequencies to the 4 bit input
data combinations. That means it is 16 level FSK.
Here carrier frequency is given fc = 500KHz , frequency difference
fd=25KHz , M=16 levels and L=4 bit symbol.
Consider carrier signal is sin wave then
Output =sin(2*pi*fc*t+M*fd*t) here m=1,2,3,4,…..,16.
M L Output
1 0000 sin(1000*pi*t+25*t)
2 0001 sin(1000*pi*t+50*t)
3 0010 sin(1000*pi*t+75*t)
4 0011 sin(1000*pi*t+100*t)
5 0100 sin(1000*pi*t+125*t)
6 0101 sin(1000*pi*t+150*t)
the frequency assignments for each of the sixteen possible 4-bit data
combinations.
ANS:
Here in that solution assign 16 different frequencies to the 4 bit input
data combinations. That means it is 16 level FSK.
Here carrier frequency is given fc = 500KHz , frequency difference
fd=25KHz , M=16 levels and L=4 bit symbol.
Consider carrier signal is sin wave then
Output =sin(2*pi*fc*t+M*fd*t) here m=1,2,3,4,…..,16.
M L Output
1 0000 sin(1000*pi*t+25*t)
2 0001 sin(1000*pi*t+50*t)
3 0010 sin(1000*pi*t+75*t)
4 0011 sin(1000*pi*t+100*t)
5 0100 sin(1000*pi*t+125*t)
6 0101 sin(1000*pi*t+150*t)

7 0110 sin(1000*pi*t+175*t)
8 0111 sin(1000*pi*t+200*t)
9 1000 sin(1000*pi*t+225*t)
10 1001 sin(1000*pi*t+250*t)
11 1010 sin(1000*pi*t+275*t)
12 1011 sin(1000*pi*t+300*t)
13 1100 sin(1000*pi*t+325*t)
14 1101 sin(1000*pi*t+350*t)
15 1110 sin(1000*pi*t+375*t)
16 1111 sin(1000*pi*t+400*t)
3. Draw the approximate Analog Modulation and Frequency
Modulation waveforms in complete steps for the following signal:
ANS:
In Analog communication there are two type of modulation Ampitude and
Angle modulation .In angle modulation there are two types Frequency
and Phase modulation.
If the amplitude of the carrier wave is varied accordance with the
instantaneous amplitude of the modulating signal then this modulation
called Amplitude modulation.
If the frequency of the carrier wave is varied accordance with the
instantaneous value of the modulating signal then this modulation
called Amplitude modulation.
8 0111 sin(1000*pi*t+200*t)
9 1000 sin(1000*pi*t+225*t)
10 1001 sin(1000*pi*t+250*t)
11 1010 sin(1000*pi*t+275*t)
12 1011 sin(1000*pi*t+300*t)
13 1100 sin(1000*pi*t+325*t)
14 1101 sin(1000*pi*t+350*t)
15 1110 sin(1000*pi*t+375*t)
16 1111 sin(1000*pi*t+400*t)
3. Draw the approximate Analog Modulation and Frequency
Modulation waveforms in complete steps for the following signal:
ANS:
In Analog communication there are two type of modulation Ampitude and
Angle modulation .In angle modulation there are two types Frequency
and Phase modulation.
If the amplitude of the carrier wave is varied accordance with the
instantaneous amplitude of the modulating signal then this modulation
called Amplitude modulation.
If the frequency of the carrier wave is varied accordance with the
instantaneous value of the modulating signal then this modulation
called Amplitude modulation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4. Draw the 16 QAM Constellation Diagram having two different
amplitude levels and eight different phase levels.
Quadrature Amplitude Modulation utilizes both amplitude and phase
components to provide a form of modulation .
The constellation diagram shows all the possible symbols that can
be transmitted by the system as a collection of points.
amplitude levels and eight different phase levels.
Quadrature Amplitude Modulation utilizes both amplitude and phase
components to provide a form of modulation .
The constellation diagram shows all the possible symbols that can
be transmitted by the system as a collection of points.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
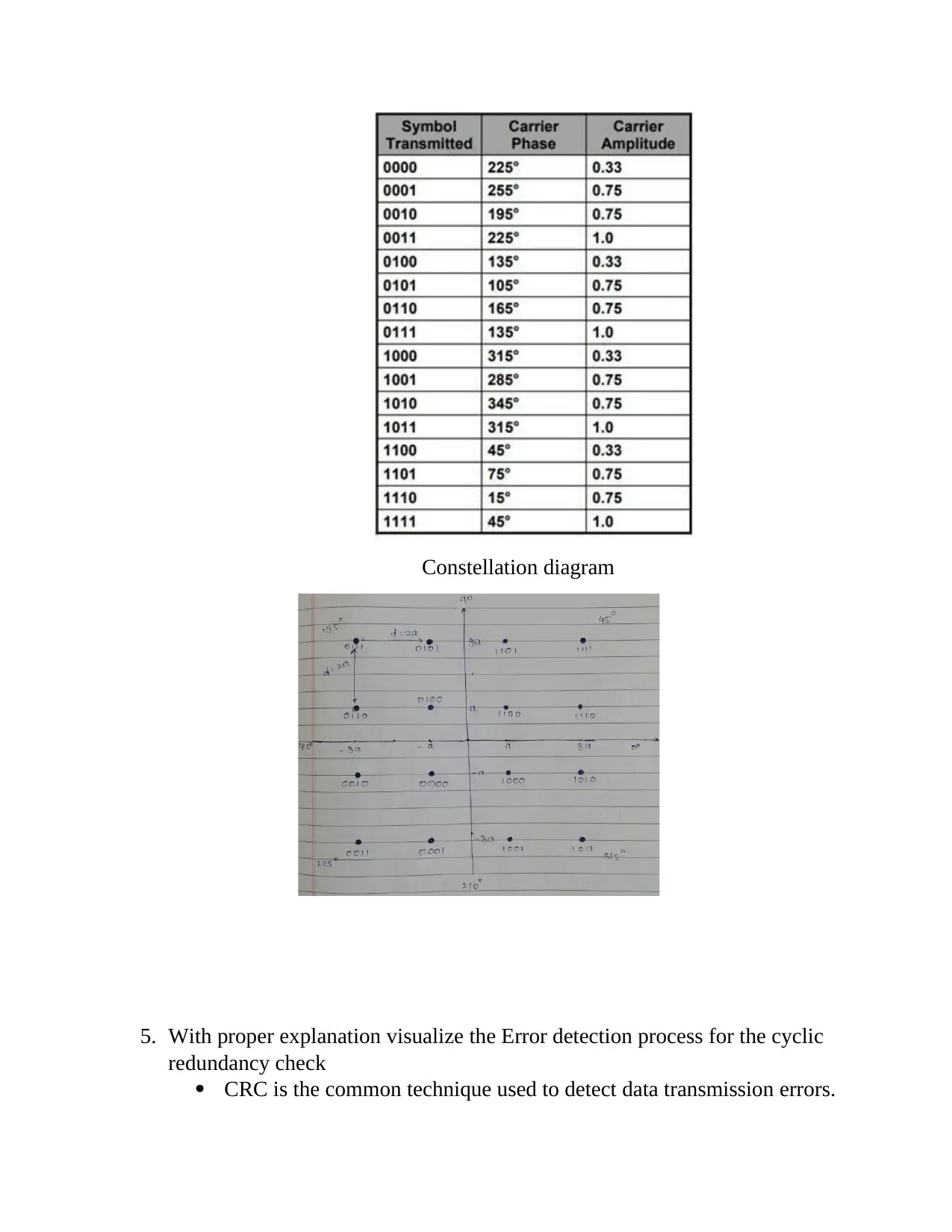
Constellation diagram
5. With proper explanation visualize the Error detection process for the cyclic
redundancy check
CRC is the common technique used to detect data transmission errors.
5. With proper explanation visualize the Error detection process for the cyclic
redundancy check
CRC is the common technique used to detect data transmission errors.

Binary division is the basis of the system.
As per the Sender Side
generator G(x) polynomial is present to the sender.
Appending of (n-1) zero bits with the data
is performed by the sender. N represents
no. of bits that are present in generator
Appending of dividend is performed as per the data present along generator G(x)
by means of modulo 2 division (arithmetic).
Remainder that will be present i.e. (n-1) bits are the CRC.
Combination from Data bits along with the CRC bits which
indicates Codeword = Data bits + CRC bits
Example
It can be assumed that –
(a) 10110 is the data.
(b) 1101 is the code generator. (polynomial also holds the
understanding of the polynomial : x^3+x^2+1)
Calculation of CRC Bits:
Processing of calculating CRC taking into consideration
for the bits that are used as per the gathered data.
As per the above code, generator is considered to be1101.
So, there has been a total 4 bits. Hence appending of 000
with the data can be made.
Cyclic redundancy check is performed as follows:
101 is the CRC. The receiver receives 10110101 from the sender.
As per the Sender Side
generator G(x) polynomial is present to the sender.
Appending of (n-1) zero bits with the data
is performed by the sender. N represents
no. of bits that are present in generator
Appending of dividend is performed as per the data present along generator G(x)
by means of modulo 2 division (arithmetic).
Remainder that will be present i.e. (n-1) bits are the CRC.
Combination from Data bits along with the CRC bits which
indicates Codeword = Data bits + CRC bits
Example
It can be assumed that –
(a) 10110 is the data.
(b) 1101 is the code generator. (polynomial also holds the
understanding of the polynomial : x^3+x^2+1)
Calculation of CRC Bits:
Processing of calculating CRC taking into consideration
for the bits that are used as per the gathered data.
As per the above code, generator is considered to be1101.
So, there has been a total 4 bits. Hence appending of 000
with the data can be made.
Cyclic redundancy check is performed as follows:
101 is the CRC. The receiver receives 10110101 from the sender.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

At Receiver Side
Generator is same for the receiver G(x).
Data is divided with the generator (data + CRC).
Data is accurately received if the remainder is 0
Otherwise error is detected.
Assume the received message is 10110110.
Calculation of CRC Bits:
No addition of padding bits is performed and hence calculation is performed as per
the commencing of the entirely received code.
Generator is same for the receiver G(x).
Data is divided with the generator (data + CRC).
Data is accurately received if the remainder is 0
Otherwise error is detected.
Assume the received message is 10110110.
Calculation of CRC Bits:
No addition of padding bits is performed and hence calculation is performed as per
the commencing of the entirely received code.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Differentially projected CRC bits are calculated. Hence an error is detected.
6. Compute the frame check sequence for the following information: Message
= 10111100, Pattern = 11011 .
ANS:
Most common algorithm for frame check sequence is
Cyclic Redundancy Check algorithm.
So here we are using CRC algorithm , Here data is 10111100.
code generator is 11011.
In the above code, code generator is 11011. So, there is total 5
bits. So, we will append 0000 with the data.
6. Compute the frame check sequence for the following information: Message
= 10111100, Pattern = 11011 .
ANS:
Most common algorithm for frame check sequence is
Cyclic Redundancy Check algorithm.
So here we are using CRC algorithm , Here data is 10111100.
code generator is 11011.
In the above code, code generator is 11011. So, there is total 5
bits. So, we will append 0000 with the data.

Cyclic redundancy check is 0010. Thus, the sender sends 101111000010 to
the receiver
7. Compare the differences of TCP and OSI protocols for wired and
wireless LANs using diagrams.
Ans:
OSI(Open System Interconnection)
OSI is considered to be a protocol independent and generic standard that
acts as per the communication gateway in between the platform of end
users and the network. Follows vertical approach & There are 7 layers
present in the OSI.
TCP/IP(Transmission Control Protocol / Internet Protocol)
TCP/IP model has been reliant on the standard protocols as per the usage of
the platform of features that are developed by Internet. There are a total of 4
layers.
the receiver
7. Compare the differences of TCP and OSI protocols for wired and
wireless LANs using diagrams.
Ans:
OSI(Open System Interconnection)
OSI is considered to be a protocol independent and generic standard that
acts as per the communication gateway in between the platform of end
users and the network. Follows vertical approach & There are 7 layers
present in the OSI.
TCP/IP(Transmission Control Protocol / Internet Protocol)
TCP/IP model has been reliant on the standard protocols as per the usage of
the platform of features that are developed by Internet. There are a total of 4
layers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





