Identification of MFA Factors and Impact on User-Centric Security
VerifiedAdded on 2023/04/26
|10
|2117
|489
Project
AI Summary
This research proposal explores the factors and impact of multi-factor authentication (MFA) in improving user-centric security. The introduction highlights the challenges in user-centered security, emphasizing the role of authentication in a digitized world. It then discusses the evolution and adoption of MFA, including single-factor and two-factor authentication, and its benefits for user interaction and system reliability. The literature review covers usability engineering techniques and challenges in user-centered security. The project management section outlines the use of an agile methodology and SPSS software for data analysis, involving surveys and interviews with employees and managers from three organizations. The research design includes a descriptive design and a positivism philosophy. Risk analysis identifies potential project risks, and a timeline details the project activities. Ethical considerations, including data confidentiality and informed consent, are also addressed. The proposal concludes with a comprehensive list of references.

Running head: RESEARCH PROPOSAL
Research Proposal
Name of Student-
Name of University-
Author’s Note-
Research Proposal
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RESEARCH PROPOSAL
Title- Identification of the factors and impact of multifactor authentication in improving
the user centric security
Introduction
The User-centered security is identified as one of the main challenge in the field of
information security and in information assurance (Choi et al. 2017). User-centered security has
now become a sub-domain of Human Computer Interface research and the research involved
with security. This user centered security has also influenced the lifecycle of product
development.
User-centered security mainly refers to the security models, systems, software and the
mechanism that considers usability as the main goal. In developing world of technology,
digitization is one of the aspects that is included in the modern society. Digitization helps to
maintain the security that are involved in processes and it is known as authentication (Giffin,
Skufca and Lao 2015). For implementing user centered security, authentication is the only
process that works successfully. Authentication mainly covers various areas that includes hyper
connected world including right management access, communication, as well as online
payments.
Cyberspace authentication is considered as process, which helps to verify the user
identity before accessing the system, resources, as well as network to the internet services. The
password that is used by the user is known as form of authentication that is considered as the
primary way of identifying users (Ogbanufe and Kim 2018). The passwords is to be convenient
that requires very little memory space as well as passwords that are needed to be typed that are
applied. All professionals of computer and the security professionals must use passwords that are
Title- Identification of the factors and impact of multifactor authentication in improving
the user centric security
Introduction
The User-centered security is identified as one of the main challenge in the field of
information security and in information assurance (Choi et al. 2017). User-centered security has
now become a sub-domain of Human Computer Interface research and the research involved
with security. This user centered security has also influenced the lifecycle of product
development.
User-centered security mainly refers to the security models, systems, software and the
mechanism that considers usability as the main goal. In developing world of technology,
digitization is one of the aspects that is included in the modern society. Digitization helps to
maintain the security that are involved in processes and it is known as authentication (Giffin,
Skufca and Lao 2015). For implementing user centered security, authentication is the only
process that works successfully. Authentication mainly covers various areas that includes hyper
connected world including right management access, communication, as well as online
payments.
Cyberspace authentication is considered as process, which helps to verify the user
identity before accessing the system, resources, as well as network to the internet services. The
password that is used by the user is known as form of authentication that is considered as the
primary way of identifying users (Ogbanufe and Kim 2018). The passwords is to be convenient
that requires very little memory space as well as passwords that are needed to be typed that are
applied. All professionals of computer and the security professionals must use passwords that are

2RESEARCH PROPOSAL
strong and the passwords should be weak from of authentication. The weak passwords are
possible to be hacked when the authentication process will be carried out.
This particular paper consists of evolution and the adoption of all User-centered security
system that consists MFA (Multi factor Authentication). The challenges that are faced while
adopting the User-centered security. One main way of user centered security that is explained in
this paper is Multi factor authentication. This papers explains MFA that has two type of
authentication, SFA (Single Factor Authentication) as well as 2FA (Two Factor Authentication).
The Multi-factor authentication is used for humans that have established interaction with all the
devices. The Multi factor authentication helps in fast interaction, makes the authentication
reliable, and helps in creating a user friendly system while accessing the system.
Literature Review
With the application of the usability to the secured systems, the most important approach
that synthesizes the usability engineering and the secured systems is applying all established
procedures that enhances the usability for developing secured systems and secure the systems
that already exists (Kumari et al. 2017). Techniques that helps to enhance the software usability
has a wide context range and also has wide sophistication. One of the technique is contextual
design. This mainly uses detailed study of the work habits of potential users and the needs that is
required for determining the goals of the initial products. The second technique is the Discount
usability testing that involves testing the user with paper mock-ups of low technology for getting
rapid feedback on the concepts of early design. In the lab testing, a particular is sked to perform
by the users with software as well as the reactions of the users and the problems that are faced by
them are monitored. Usability testing is done through contextual inquiry tested on deployed
product.
strong and the passwords should be weak from of authentication. The weak passwords are
possible to be hacked when the authentication process will be carried out.
This particular paper consists of evolution and the adoption of all User-centered security
system that consists MFA (Multi factor Authentication). The challenges that are faced while
adopting the User-centered security. One main way of user centered security that is explained in
this paper is Multi factor authentication. This papers explains MFA that has two type of
authentication, SFA (Single Factor Authentication) as well as 2FA (Two Factor Authentication).
The Multi-factor authentication is used for humans that have established interaction with all the
devices. The Multi factor authentication helps in fast interaction, makes the authentication
reliable, and helps in creating a user friendly system while accessing the system.
Literature Review
With the application of the usability to the secured systems, the most important approach
that synthesizes the usability engineering and the secured systems is applying all established
procedures that enhances the usability for developing secured systems and secure the systems
that already exists (Kumari et al. 2017). Techniques that helps to enhance the software usability
has a wide context range and also has wide sophistication. One of the technique is contextual
design. This mainly uses detailed study of the work habits of potential users and the needs that is
required for determining the goals of the initial products. The second technique is the Discount
usability testing that involves testing the user with paper mock-ups of low technology for getting
rapid feedback on the concepts of early design. In the lab testing, a particular is sked to perform
by the users with software as well as the reactions of the users and the problems that are faced by
them are monitored. Usability testing is done through contextual inquiry tested on deployed
product.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RESEARCH PROPOSAL
The Problem of User-Centered Security
Liu et al. (2016) stated that the most important and main challenge that is faced in user-
centered security is maintaining the relationship between the users and the security mechanisms.
This is an important factor since the development of security among the systems. The method of
interaction with the security mechanism is users applying the concept of security in context they
understood. The main challenge faced was to make model of security as a consistent tool along
with the security model used by the user. This might reduce all undesirable errors in the system.
One of the user-centered security that is commonly used is multi factor authentication that is
explained in the following section.
Multiple factor of Authentication
Feng et al. (2018) stated that MFA (Multi-factor authentication) is used to describe
authentication scheme that are basically that are used by the end users to present two proof for
the mechanism of authentication.
According to Giffin, Skufca and Lao (2015) MFA (Multi-factor Authentication) is
another type that can be used for carrying out login access. After the process of logging, a user
actually requires two-factor authentication, which is used to prove different identity in various
ways. The two-way authentication mainly includes a unique username and a unique password.
Various different authentication processes mainly includes the passcodes of SMS, the tokens,
and the notifications tokens. The factors associated with MFA are:
The knowledge factors are the most common factor involved in authentication. The
authentication mechanism is to be known by the user.
The Problem of User-Centered Security
Liu et al. (2016) stated that the most important and main challenge that is faced in user-
centered security is maintaining the relationship between the users and the security mechanisms.
This is an important factor since the development of security among the systems. The method of
interaction with the security mechanism is users applying the concept of security in context they
understood. The main challenge faced was to make model of security as a consistent tool along
with the security model used by the user. This might reduce all undesirable errors in the system.
One of the user-centered security that is commonly used is multi factor authentication that is
explained in the following section.
Multiple factor of Authentication
Feng et al. (2018) stated that MFA (Multi-factor authentication) is used to describe
authentication scheme that are basically that are used by the end users to present two proof for
the mechanism of authentication.
According to Giffin, Skufca and Lao (2015) MFA (Multi-factor Authentication) is
another type that can be used for carrying out login access. After the process of logging, a user
actually requires two-factor authentication, which is used to prove different identity in various
ways. The two-way authentication mainly includes a unique username and a unique password.
Various different authentication processes mainly includes the passcodes of SMS, the tokens,
and the notifications tokens. The factors associated with MFA are:
The knowledge factors are the most common factor involved in authentication. The
authentication mechanism is to be known by the user.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RESEARCH PROPOSAL
The possession factor are also used by the user that are involved in the process (Anakath,
Rajakumar and Ambika 2017). The authentication type that is used as the possession
factor are used from ages before. The authentication type mainly includes lock and key
authentication. If the key is correct, then the lock will also be correct.
The inherence factors are associated with a person. For example, the inherence
authentication includes biometrics (Odelu, Das and Goswami 2015). The most common
techniques of biometric is the fingerprint technique includes the retina scanner, facial
recognition, and the voice recognition.
Project Management
The methodology of project management that will be addressed in this research paper is
the agile method of project management. Projects that are involved in agile methodology are
based on iterative as well as incremental development where the software is mainly delivered in
a continuous and rapid manner.
The tool that are used for addressing this research paper research methodology is the
SPSS software method of data analysis. To study the Multi-factor authentication adoption in the
people, three organizations will be considered for carrying out the research study. The employees
of the organizations and the managers of the organization will be included as the respondents for
carrying out the survey. The sample size that will be considered to carry out the data analysis is
100 employees from all three organizations and 2 managers from each of the organizations. The
interview that will be carried out will be face to face interview with the managers.
For analyzing the utilization of Multi-Factor authentication from the perspective of user
and from the perspective of technology, the analyst will mainly use an analysis process in
The possession factor are also used by the user that are involved in the process (Anakath,
Rajakumar and Ambika 2017). The authentication type that is used as the possession
factor are used from ages before. The authentication type mainly includes lock and key
authentication. If the key is correct, then the lock will also be correct.
The inherence factors are associated with a person. For example, the inherence
authentication includes biometrics (Odelu, Das and Goswami 2015). The most common
techniques of biometric is the fingerprint technique includes the retina scanner, facial
recognition, and the voice recognition.
Project Management
The methodology of project management that will be addressed in this research paper is
the agile method of project management. Projects that are involved in agile methodology are
based on iterative as well as incremental development where the software is mainly delivered in
a continuous and rapid manner.
The tool that are used for addressing this research paper research methodology is the
SPSS software method of data analysis. To study the Multi-factor authentication adoption in the
people, three organizations will be considered for carrying out the research study. The employees
of the organizations and the managers of the organization will be included as the respondents for
carrying out the survey. The sample size that will be considered to carry out the data analysis is
100 employees from all three organizations and 2 managers from each of the organizations. The
interview that will be carried out will be face to face interview with the managers.
For analyzing the utilization of Multi-Factor authentication from the perspective of user
and from the perspective of technology, the analyst will mainly use an analysis process in
5RESEARCH PROPOSAL
detailed with the detailed technique for carrying out research methodology. The analyst will also
use the deductive approach of research. The design of research that will be used by the analyst is
the descriptive design of the research. The research philosophy that will be used by the analyst to
carry out this research paper is positivism philosophy. The process of data collection that the
analyst will use in the research analysis is primary method of collecting data. Both quantitative
as well as qualitative method of primary data collection method is used for carrying out the
research paper.
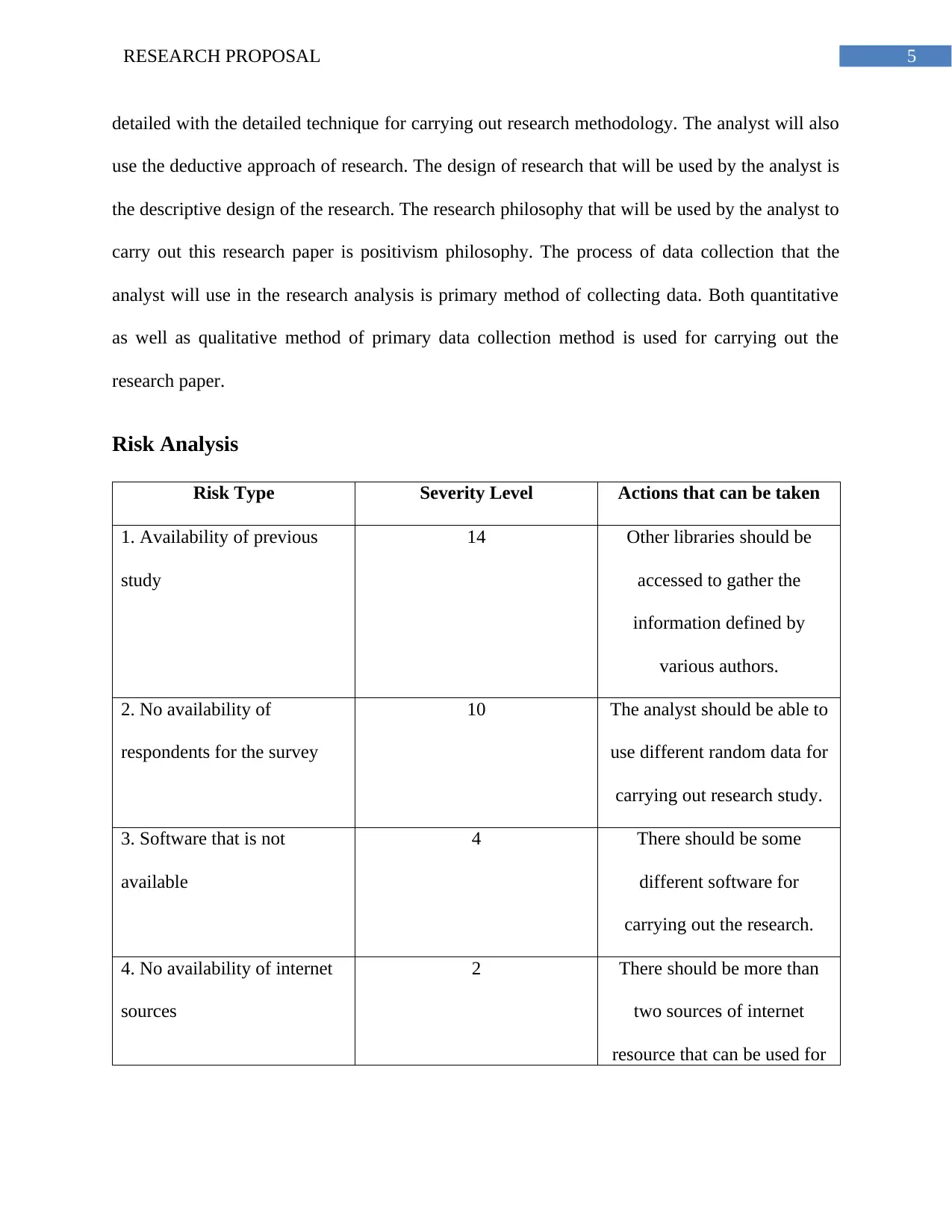
Risk Analysis
Risk Type Severity Level Actions that can be taken
1. Availability of previous
study
14 Other libraries should be
accessed to gather the
information defined by
various authors.
2. No availability of
respondents for the survey
10 The analyst should be able to
use different random data for
carrying out research study.
3. Software that is not
available
4 There should be some
different software for
carrying out the research.
4. No availability of internet
sources
2 There should be more than
two sources of internet
resource that can be used for
detailed with the detailed technique for carrying out research methodology. The analyst will also
use the deductive approach of research. The design of research that will be used by the analyst is
the descriptive design of the research. The research philosophy that will be used by the analyst to
carry out this research paper is positivism philosophy. The process of data collection that the
analyst will use in the research analysis is primary method of collecting data. Both quantitative
as well as qualitative method of primary data collection method is used for carrying out the
research paper.
Risk Analysis
Risk Type Severity Level Actions that can be taken
1. Availability of previous
study
14 Other libraries should be
accessed to gather the
information defined by
various authors.
2. No availability of
respondents for the survey
10 The analyst should be able to
use different random data for
carrying out research study.
3. Software that is not
available
4 There should be some
different software for
carrying out the research.
4. No availability of internet
sources
2 There should be more than
two sources of internet
resource that can be used for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6RESEARCH PROPOSAL
the research study.
Table 1: Risk that is identified for the project
Note: The level of severity increases from 1 and above from very low risk to very high
risk.
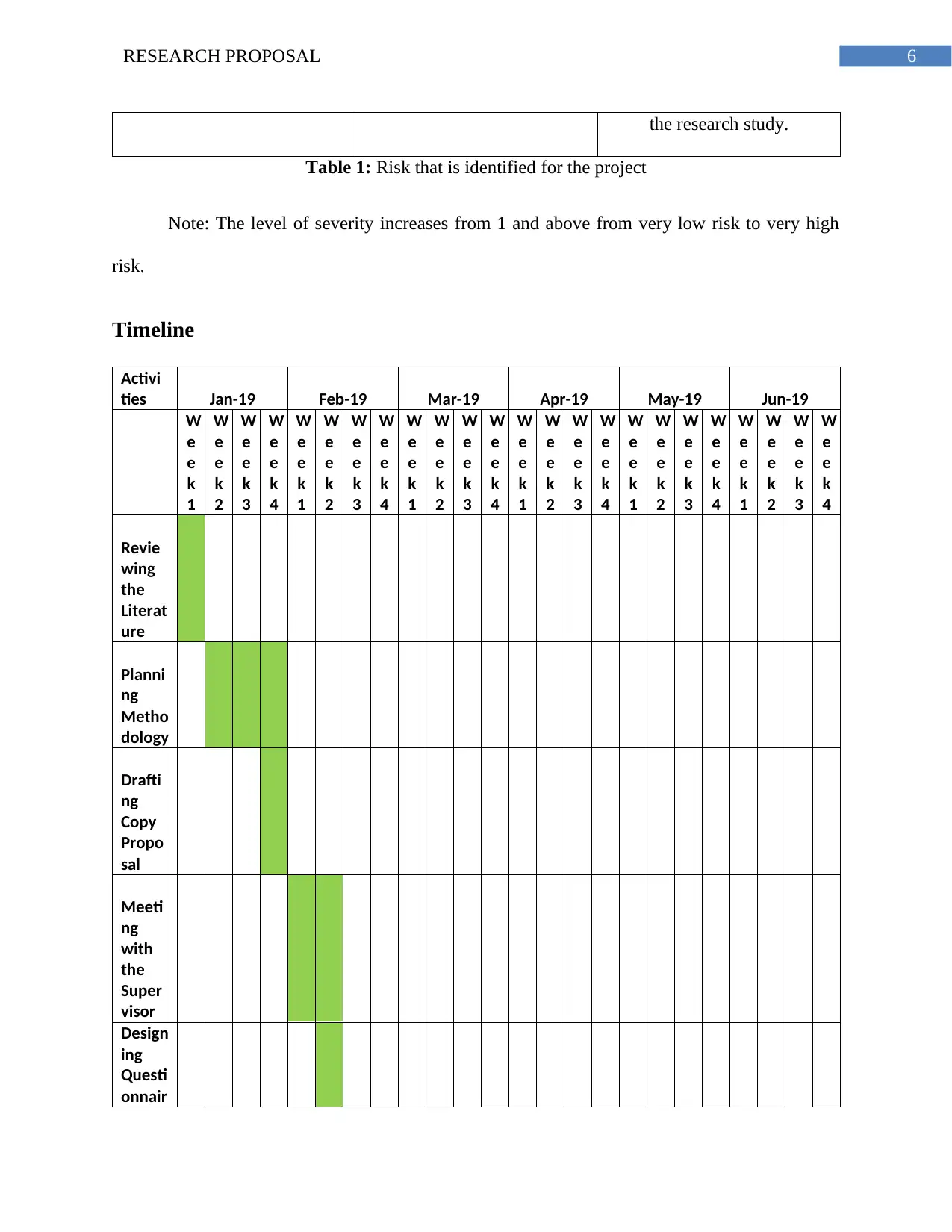
Timeline
Activi
ties Jan-19 Feb-19 Mar-19 Apr-19 May-19 Jun-19
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
Revie
wing
the
Literat
ure
Planni
ng
Metho
dology
Drafti
ng
Copy
Propo
sal
Meeti
ng
with
the
Super
visor
Design
ing
Questi
onnair
the research study.
Table 1: Risk that is identified for the project
Note: The level of severity increases from 1 and above from very low risk to very high
risk.
Timeline
Activi
ties Jan-19 Feb-19 Mar-19 Apr-19 May-19 Jun-19
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
W
e
e
k
1
W
e
e
k
2
W
e
e
k
3
W
e
e
k
4
Revie
wing
the
Literat
ure
Planni
ng
Metho
dology
Drafti
ng
Copy
Propo
sal
Meeti
ng
with
the
Super
visor
Design
ing
Questi
onnair
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7RESEARCH PROPOSAL
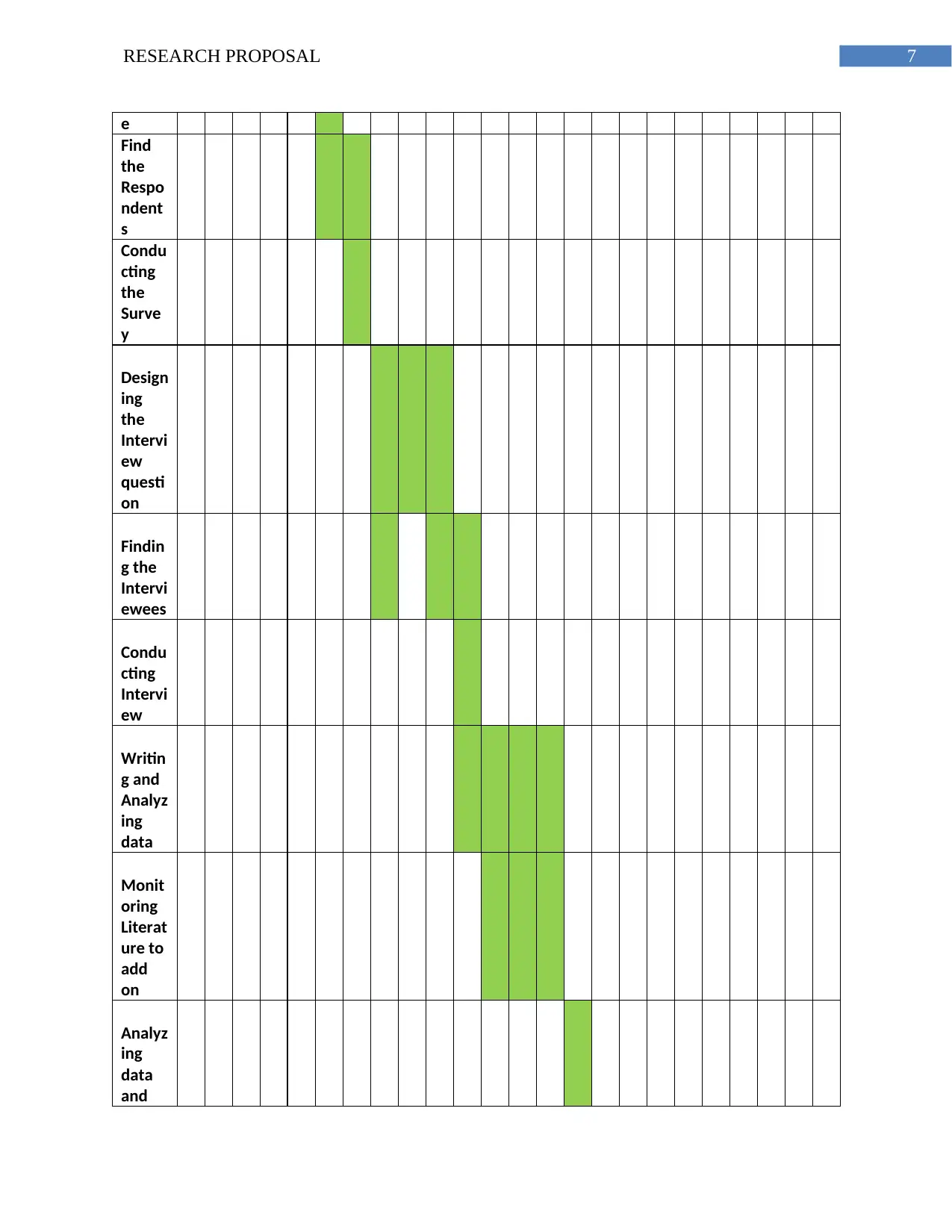
e
Find
the
Respo
ndent
s
Condu
cting
the
Surve
y
Design
ing
the
Intervi
ew
questi
on
Findin
g the
Intervi
ewees
Condu
cting
Intervi
ew
Writin
g and
Analyz
ing
data
Monit
oring
Literat
ure to
add
on
Analyz
ing
data
and
e
Find
the
Respo
ndent
s
Condu
cting
the
Surve
y
Design
ing
the
Intervi
ew
questi
on
Findin
g the
Intervi
ewees
Condu
cting
Intervi
ew
Writin
g and
Analyz
ing
data
Monit
oring
Literat
ure to
add
on
Analyz
ing
data
and
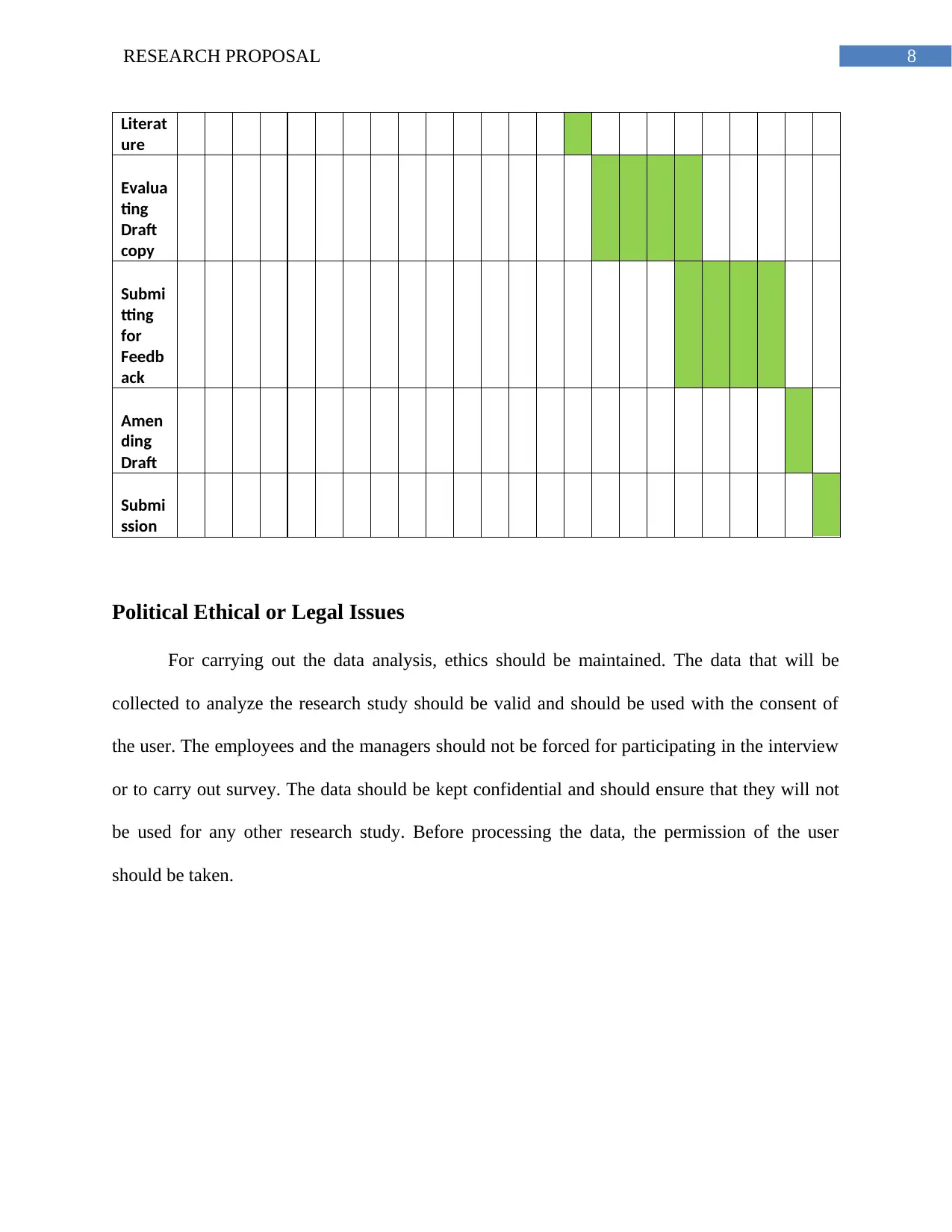
8RESEARCH PROPOSAL
Literat
ure
Evalua
ting
Draft
copy
Submi
tting
for
Feedb
ack
Amen
ding
Draft
Submi
ssion
Political Ethical or Legal Issues
For carrying out the data analysis, ethics should be maintained. The data that will be
collected to analyze the research study should be valid and should be used with the consent of
the user. The employees and the managers should not be forced for participating in the interview
or to carry out survey. The data should be kept confidential and should ensure that they will not
be used for any other research study. Before processing the data, the permission of the user
should be taken.
Literat
ure
Evalua
ting
Draft
copy
Submi
tting
for
Feedb
ack
Amen
ding
Draft
Submi
ssion
Political Ethical or Legal Issues
For carrying out the data analysis, ethics should be maintained. The data that will be
collected to analyze the research study should be valid and should be used with the consent of
the user. The employees and the managers should not be forced for participating in the interview
or to carry out survey. The data should be kept confidential and should ensure that they will not
be used for any other research study. Before processing the data, the permission of the user
should be taken.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RESEARCH PROPOSAL
References
Anakath, A.S., Rajakumar, S. and Ambika, S., 2017. Privacy preserving multi factor
authentication using trust management. Cluster Computing, pp.1-7.
Choi, Y., Lee, Y., Moon, J. and Won, D., 2017. Security enhanced multi-factor biometric
authentication scheme using bio-hash function. PloS one, 12(5), p.e0176250.
Feng, Q., He, D., Zeadally, S. and Wang, H., 2018. Anonymous biometrics-based authentication
scheme with key distribution for mobile multi-server environment. Future Generation Computer
Systems, 84, pp.239-251.
Giffin, A., Skufca, J.D. and Lao, P.A., 2015, January. Using Bayes factors for multi-factor,
biometric authentication. In AIP Conference Proceedings (Vol. 1641, No. 1, pp. 611-615). AIP.
Kumari, S., Li, X., Wu, F., Das, A.K., Choo, K.K.R. and Shen, J., 2017. Design of a provably
secure biometrics-based multi-cloud-server authentication scheme. Future Generation Computer
Systems, 68, pp.320-330.
Liu, Y., Zhong, Q., Chang, L., Xia, Z., He, D. and Cheng, C., 2016. A secure data backup
scheme using multi-factor authentication. IET Information Security, 11(5), pp.250-255.
Odelu, V., Das, A.K. and Goswami, A., 2015. A secure biometrics-based multi-server
authentication protocol using smart cards. IEEE Transactions on Information Forensics and
Security, 10(9), pp.1953-1966.
Ogbanufe, O. and Kim, D.J., 2018. Comparing fingerprint-based biometrics authentication
versus traditional authentication methods for e-payment. Decision Support Systems, 106, pp.1-
14.
References
Anakath, A.S., Rajakumar, S. and Ambika, S., 2017. Privacy preserving multi factor
authentication using trust management. Cluster Computing, pp.1-7.
Choi, Y., Lee, Y., Moon, J. and Won, D., 2017. Security enhanced multi-factor biometric
authentication scheme using bio-hash function. PloS one, 12(5), p.e0176250.
Feng, Q., He, D., Zeadally, S. and Wang, H., 2018. Anonymous biometrics-based authentication
scheme with key distribution for mobile multi-server environment. Future Generation Computer
Systems, 84, pp.239-251.
Giffin, A., Skufca, J.D. and Lao, P.A., 2015, January. Using Bayes factors for multi-factor,
biometric authentication. In AIP Conference Proceedings (Vol. 1641, No. 1, pp. 611-615). AIP.
Kumari, S., Li, X., Wu, F., Das, A.K., Choo, K.K.R. and Shen, J., 2017. Design of a provably
secure biometrics-based multi-cloud-server authentication scheme. Future Generation Computer
Systems, 68, pp.320-330.
Liu, Y., Zhong, Q., Chang, L., Xia, Z., He, D. and Cheng, C., 2016. A secure data backup
scheme using multi-factor authentication. IET Information Security, 11(5), pp.250-255.
Odelu, V., Das, A.K. and Goswami, A., 2015. A secure biometrics-based multi-server
authentication protocol using smart cards. IEEE Transactions on Information Forensics and
Security, 10(9), pp.1953-1966.
Ogbanufe, O. and Kim, D.J., 2018. Comparing fingerprint-based biometrics authentication
versus traditional authentication methods for e-payment. Decision Support Systems, 106, pp.1-
14.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





