Threat and Risk Assessment for MyLicense Portal Data Security
VerifiedAdded on 2023/06/06
|11
|2635
|488
Report
AI Summary
This report presents a comprehensive threat and risk assessment for the MyLicense portal, focusing on data security and privacy. It examines potential threats to Personally Identifiable Information (PII), including security breaches, cyber terrorism, and vulnerabilities in Wi-Fi connections. The assessment categorizes threats by likelihood, impact, and priority, proposing preventive actions like contingency plans, security protocols, and encryption measures. The report addresses issues such as the security of vendor infrastructure, authentication of data centers, and the need for timely patches and updates. It also explores privacy threats, including confidentiality, integrity, availability, and non-repudiation. The analysis covers the severity of risks related to employee data and emphasizes the importance of training, legal compliance, and the implementation of robust security measures to protect sensitive information and maintain system integrity. The report concludes with a list of references to support the findings.

THREAT AND RISK ASSESSMENT
According to the Australian State Government initiatives the role of the department of the
administrative services is to deliver numbers of services to the other departments through
taking information from their own data centers. The set of operational services offered by the
department of administrative services holds payroll, personnel management, contract
management, human resource management, contract as well as tendering management etc. As
per the current age of policy and regulations developed by the government it is defined that,
the DAS is focused to move their existing services to the shared service approaches. The set
of services offered collectively by the DAS needs to centralize their services. Apart from this,
the DAS also needs to centralize their service approach all for the whole of government
(WofG). The clients who will adopt services from the DAS must migrate all the information
to the newly updates data server for higher range of security. As it is the responsibility of the
database administrator to keep the confidential data protected from the rest of the unwanted
and unauthenticated users. Only the department and agencies of the government are allowed
to access information from the server and none of the external users are capable to access
data from the server. According to the very first policy of the Government cloud technology
and mechanism the different services that are decided to be implemented by the DAS include
the following:
HR and Personal Management SaaS suite SaaS suite for the human Resource
management and personal management as well
SaaS suite for the contractor management
Payroll solution developed for the AWS COTS
SharePoint platform based on PaaS intranet WofG
The newly designed single web based portal which is known as MyLicense needs to
centralize all their application in details and other information as well. The renewed license
or the client agencies will be stored in the single web portal. For the license application as
well as for the renewal of the virtual license this specific strategy for is required. Not only
this but also, identical workflow is also allows by this application. In order to gain better view
for the license of the citizens as well s better summation between the information they
possess, MyLicense expects to give some of the new opportunities. All the citizens will be
encouraged to keep themselves registered to the MyLicense. It will help to create the digital
According to the Australian State Government initiatives the role of the department of the
administrative services is to deliver numbers of services to the other departments through
taking information from their own data centers. The set of operational services offered by the
department of administrative services holds payroll, personnel management, contract
management, human resource management, contract as well as tendering management etc. As
per the current age of policy and regulations developed by the government it is defined that,
the DAS is focused to move their existing services to the shared service approaches. The set
of services offered collectively by the DAS needs to centralize their services. Apart from this,
the DAS also needs to centralize their service approach all for the whole of government
(WofG). The clients who will adopt services from the DAS must migrate all the information
to the newly updates data server for higher range of security. As it is the responsibility of the
database administrator to keep the confidential data protected from the rest of the unwanted
and unauthenticated users. Only the department and agencies of the government are allowed
to access information from the server and none of the external users are capable to access
data from the server. According to the very first policy of the Government cloud technology
and mechanism the different services that are decided to be implemented by the DAS include
the following:
HR and Personal Management SaaS suite SaaS suite for the human Resource
management and personal management as well
SaaS suite for the contractor management
Payroll solution developed for the AWS COTS
SharePoint platform based on PaaS intranet WofG
The newly designed single web based portal which is known as MyLicense needs to
centralize all their application in details and other information as well. The renewed license
or the client agencies will be stored in the single web portal. For the license application as
well as for the renewal of the virtual license this specific strategy for is required. Not only
this but also, identical workflow is also allows by this application. In order to gain better view
for the license of the citizens as well s better summation between the information they
possess, MyLicense expects to give some of the new opportunities. All the citizens will be
encouraged to keep themselves registered to the MyLicense. It will help to create the digital
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
identified for each of the citizens. In order to view the data relate to license different
information are required. For the development of the privacy and personal data different
protection strategies are to be implemented.
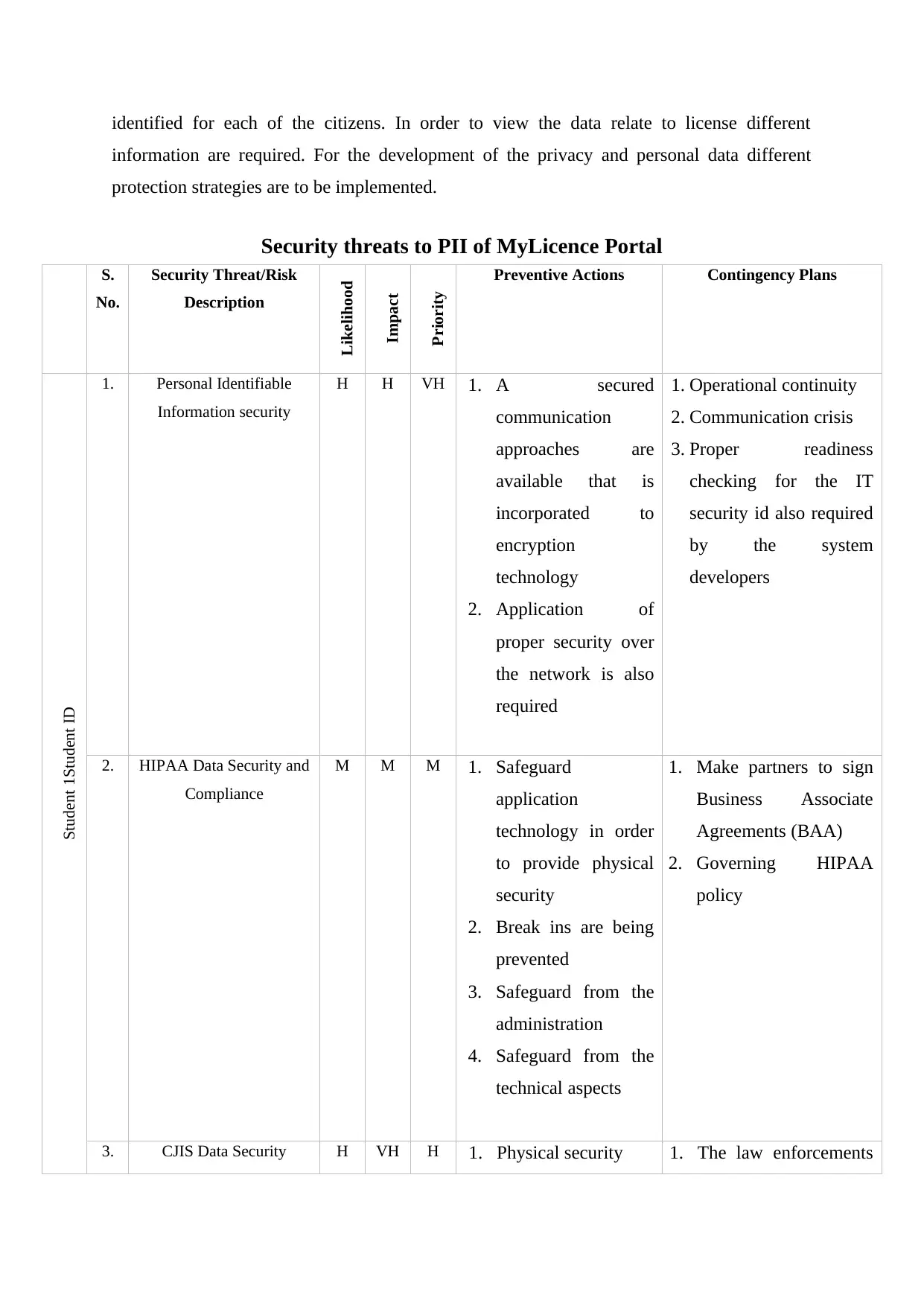
Security threats to PII of MyLicence Portal
S.
No.
Security Threat/Risk
Description
Likelihood
Impact
Priority Preventive Actions Contingency Plans
Student 1Student ID
1. Personal Identifiable
Information security
H H VH 1. A secured
communication
approaches are
available that is
incorporated to
encryption
technology
2. Application of
proper security over
the network is also
required
1. Operational continuity
2. Communication crisis
3. Proper readiness
checking for the IT
security id also required
by the system
developers
2. HIPAA Data Security and
Compliance
M M M 1. Safeguard
application
technology in order
to provide physical
security
2. Break ins are being
prevented
3. Safeguard from the
administration
4. Safeguard from the
technical aspects
1. Make partners to sign
Business Associate
Agreements (BAA)
2. Governing HIPAA
policy
3. CJIS Data Security H VH H 1. Physical security 1. The law enforcements
information are required. For the development of the privacy and personal data different
protection strategies are to be implemented.
Security threats to PII of MyLicence Portal
S.
No.
Security Threat/Risk
Description
Likelihood
Impact
Priority Preventive Actions Contingency Plans
Student 1Student ID
1. Personal Identifiable
Information security
H H VH 1. A secured
communication
approaches are
available that is
incorporated to
encryption
technology
2. Application of
proper security over
the network is also
required
1. Operational continuity
2. Communication crisis
3. Proper readiness
checking for the IT
security id also required
by the system
developers
2. HIPAA Data Security and
Compliance
M M M 1. Safeguard
application
technology in order
to provide physical
security
2. Break ins are being
prevented
3. Safeguard from the
administration
4. Safeguard from the
technical aspects
1. Make partners to sign
Business Associate
Agreements (BAA)
2. Governing HIPAA
policy
3. CJIS Data Security H VH H 1. Physical security 1. The law enforcements

2. Preventing
information access
by unauthorized
users
3. Authentication based
in multiple factors
4. Usability of data
security is needed
5. High level security I
terms of encryption
is required
should not be
perceived to be
impaired.
2. In case any additional
services are required,
they will be called
upon.
4. Data Security H H H 1. Requirements for the
encryption
technology and other
specifications.
2. Prevention policy
should be
implemented based
on data safety
1. For the cyberspace
operations ready forces
are to be maintained.
2. Risks are to be
migrated to proper data
5. Cyber Terrorism VH H H 1. Around vendor
premises security
approaches are
needed
2. Security power
system are to be
maximized
1. Maintenance and
planning of proper
cyber options to
control conflict.
2. Shared threats are to be
determined and
international stability
and security should be
increased.
Student 2 Student ID 6. Rogue Security Software L H L 1. Security loss
checking
2. Usage of the HTTP.
1. Impact analysis for the
businesses
2. Policy development for
the CP
7. Redirecting the DNS H M L 1. With the usage of the 1. Active directory
information access
by unauthorized
users
3. Authentication based
in multiple factors
4. Usability of data
security is needed
5. High level security I
terms of encryption
is required
should not be
perceived to be
impaired.
2. In case any additional
services are required,
they will be called
upon.
4. Data Security H H H 1. Requirements for the
encryption
technology and other
specifications.
2. Prevention policy
should be
implemented based
on data safety
1. For the cyberspace
operations ready forces
are to be maintained.
2. Risks are to be
migrated to proper data
5. Cyber Terrorism VH H H 1. Around vendor
premises security
approaches are
needed
2. Security power
system are to be
maximized
1. Maintenance and
planning of proper
cyber options to
control conflict.
2. Shared threats are to be
determined and
international stability
and security should be
increased.
Student 2 Student ID 6. Rogue Security Software L H L 1. Security loss
checking
2. Usage of the HTTP.
1. Impact analysis for the
businesses
2. Policy development for
the CP
7. Redirecting the DNS H M L 1. With the usage of the 1. Active directory
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

malicious domains
monitoring and
controlling are
required.
operations should be
managed.
2. Detect and Defend
potential attacks on
active directory.
8. Ransomware threats H VH VH 1. In depth approach for
defence are to be
adopted
2. Public file access are
needed to be
restricted all over
1. Data backup and
disaster recovery are
necessary
2. Business continuity
should have to be
implemented
9. Threats upon Zero Day L M L 1. Maximum rate of
protection is needed
that is possible
through application
firewall
2. Launch only those
applications that are
essential.
3. Holes in OS and
other applications are
fixed.
4. Chose Host Intrusion
Protection System
(HIPS) Anti-virus
protection.
1. In order to respond to
the crisis capacities
are to be established.
Threats are to be
integrated for all the
cases
10. Vulnerabilities with the
Wi-Fi connection
H M M 1. Portals are not be
accessed by public
wi fi connection
2. License process
should be avoided for
wi fi
1. For continuous
operation contingency
planning is required
monitoring and
controlling are
required.
operations should be
managed.
2. Detect and Defend
potential attacks on
active directory.
8. Ransomware threats H VH VH 1. In depth approach for
defence are to be
adopted
2. Public file access are
needed to be
restricted all over
1. Data backup and
disaster recovery are
necessary
2. Business continuity
should have to be
implemented
9. Threats upon Zero Day L M L 1. Maximum rate of
protection is needed
that is possible
through application
firewall
2. Launch only those
applications that are
essential.
3. Holes in OS and
other applications are
fixed.
4. Chose Host Intrusion
Protection System
(HIPS) Anti-virus
protection.
1. In order to respond to
the crisis capacities
are to be established.
Threats are to be
integrated for all the
cases
10. Vulnerabilities with the
Wi-Fi connection
H M M 1. Portals are not be
accessed by public
wi fi connection
2. License process
should be avoided for
wi fi
1. For continuous
operation contingency
planning is required
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Where,
Likelihood - VL: Very Low, L: Low, M: Medium, H: High, VH: Very High
Impact - VL: Very Low, L: Low, M: Medium, H: High, VH: Very High
Priority - VL: Very Low, L: Low, M: Medium, H: High, VH: Very High
Issues
1. DAS will contain integrated repositories of all the client agencies that maintain the
personal information of their clients. Any problem to the physical infrastructure of the
vendor may harm underlying agencies’ client data.
2. The vendor requires to maintain proper security of their data centres and other storage
infrastructure as they may be prone to viruses and malware that can be injected to the
incoming license files.
3. The authentication of the DAS datacentres can be hacked for leaking potential PII.
4. The vendor as well as DAS should not miss patches and updates for maintaining
utmost security of their databases.
5. The user or DAS computer systems may get infected with viruses that may harm the
central repositories.
Likelihood - VL: Very Low, L: Low, M: Medium, H: High, VH: Very High
Impact - VL: Very Low, L: Low, M: Medium, H: High, VH: Very High
Priority - VL: Very Low, L: Low, M: Medium, H: High, VH: Very High
Issues
1. DAS will contain integrated repositories of all the client agencies that maintain the
personal information of their clients. Any problem to the physical infrastructure of the
vendor may harm underlying agencies’ client data.
2. The vendor requires to maintain proper security of their data centres and other storage
infrastructure as they may be prone to viruses and malware that can be injected to the
incoming license files.
3. The authentication of the DAS datacentres can be hacked for leaking potential PII.
4. The vendor as well as DAS should not miss patches and updates for maintaining
utmost security of their databases.
5. The user or DAS computer systems may get infected with viruses that may harm the
central repositories.
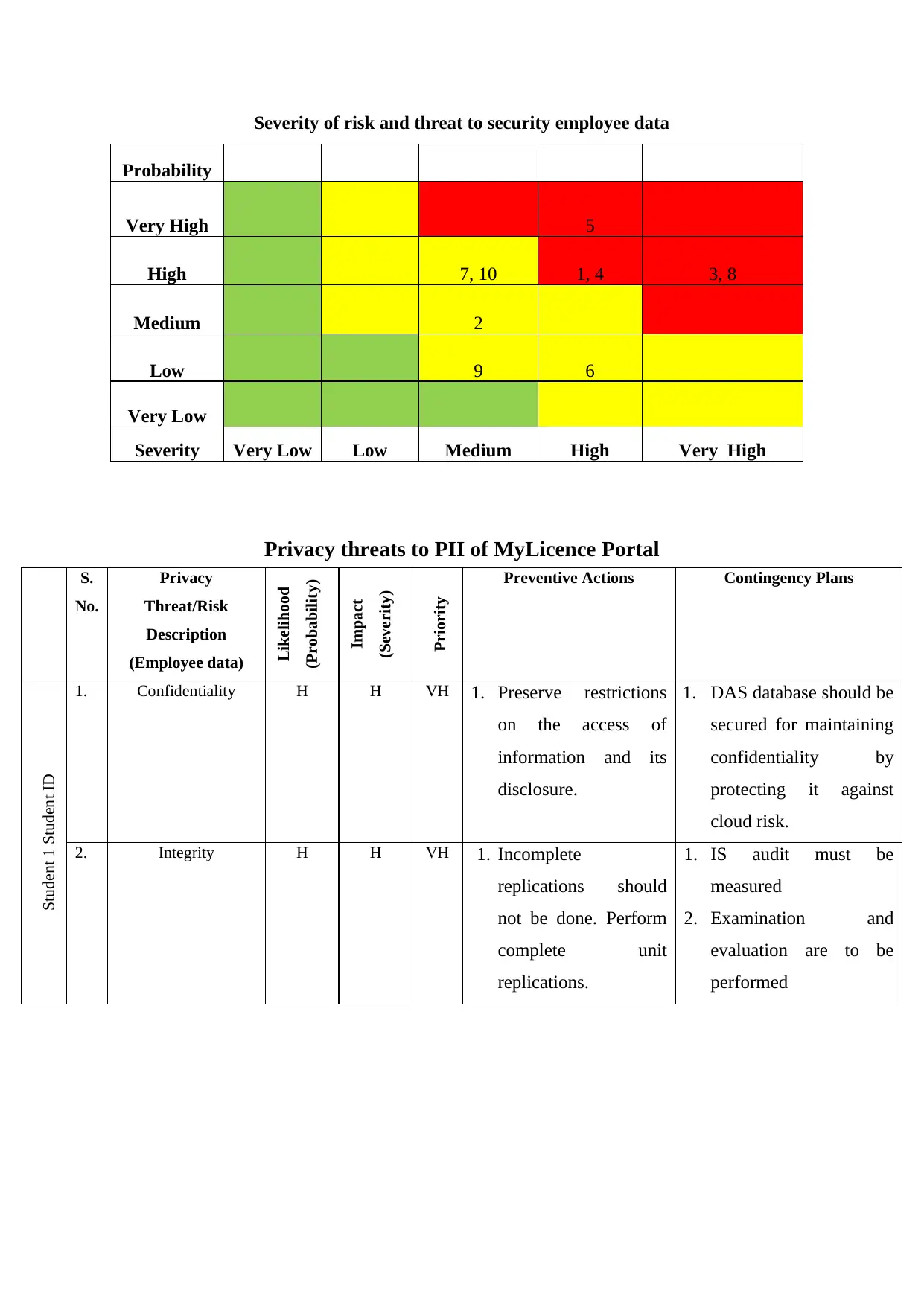
Severity of risk and threat to security employee data
Probability
Very High 5
High 7, 10 1, 4 3, 8
Medium 2
Low 9 6
Very Low
Severity Very Low Low Medium High Very High
Privacy threats to PII of MyLicence Portal
S.
No.
Privacy
Threat/Risk
Description
(Employee data)
Likelihood
(Probability)
Impact
(Severity)
Priority Preventive Actions Contingency Plans
Student 1 Student ID
1. Confidentiality H H VH 1. Preserve restrictions
on the access of
information and its
disclosure.
1. DAS database should be
secured for maintaining
confidentiality by
protecting it against
cloud risk.
2. Integrity H H VH 1. Incomplete
replications should
not be done. Perform
complete unit
replications.
1. IS audit must be
measured
2. Examination and
evaluation are to be
performed
Probability
Very High 5
High 7, 10 1, 4 3, 8
Medium 2
Low 9 6
Very Low
Severity Very Low Low Medium High Very High
Privacy threats to PII of MyLicence Portal
S.
No.
Privacy
Threat/Risk
Description
(Employee data)
Likelihood
(Probability)
Impact
(Severity)
Priority Preventive Actions Contingency Plans
Student 1 Student ID
1. Confidentiality H H VH 1. Preserve restrictions
on the access of
information and its
disclosure.
1. DAS database should be
secured for maintaining
confidentiality by
protecting it against
cloud risk.
2. Integrity H H VH 1. Incomplete
replications should
not be done. Perform
complete unit
replications.
1. IS audit must be
measured
2. Examination and
evaluation are to be
performed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
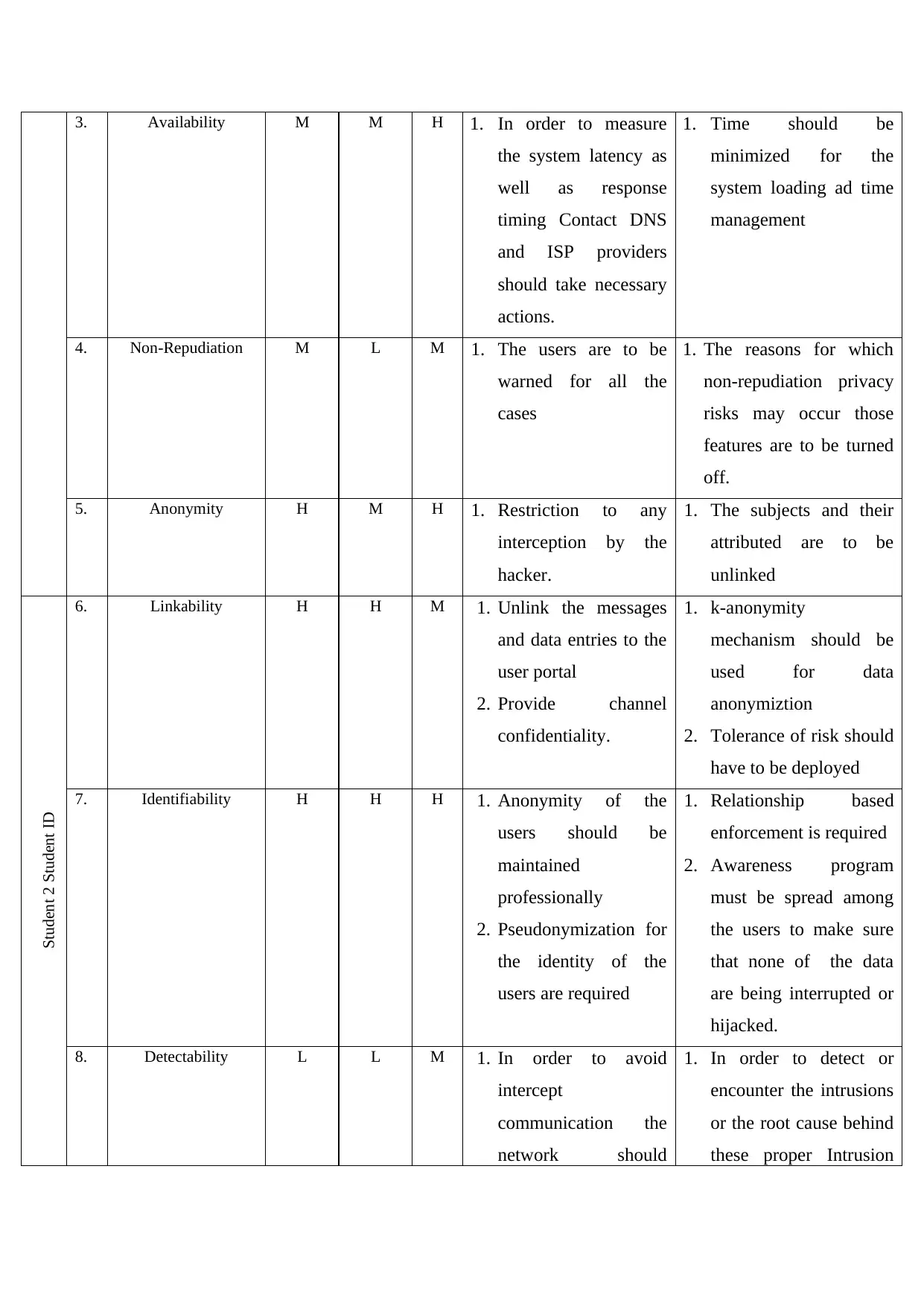
3. Availability M M H 1. In order to measure
the system latency as
well as response
timing Contact DNS
and ISP providers
should take necessary
actions.
1. Time should be
minimized for the
system loading ad time
management
4. Non-Repudiation M L M 1. The users are to be
warned for all the
cases
1. The reasons for which
non-repudiation privacy
risks may occur those
features are to be turned
off.
5. Anonymity H M H 1. Restriction to any
interception by the
hacker.
1. The subjects and their
attributed are to be
unlinked
Student 2 Student ID
6. Linkability H H M 1. Unlink the messages
and data entries to the
user portal
2. Provide channel
confidentiality.
1. k-anonymity
mechanism should be
used for data
anonymiztion
2. Tolerance of risk should
have to be deployed
7. Identifiability H H H 1. Anonymity of the
users should be
maintained
professionally
2. Pseudonymization for
the identity of the
users are required
1. Relationship based
enforcement is required
2. Awareness program
must be spread among
the users to make sure
that none of the data
are being interrupted or
hijacked.
8. Detectability L L M 1. In order to avoid
intercept
communication the
network should
1. In order to detect or
encounter the intrusions
or the root cause behind
these proper Intrusion
the system latency as
well as response
timing Contact DNS
and ISP providers
should take necessary
actions.
1. Time should be
minimized for the
system loading ad time
management
4. Non-Repudiation M L M 1. The users are to be
warned for all the
cases
1. The reasons for which
non-repudiation privacy
risks may occur those
features are to be turned
off.
5. Anonymity H M H 1. Restriction to any
interception by the
hacker.
1. The subjects and their
attributed are to be
unlinked
Student 2 Student ID
6. Linkability H H M 1. Unlink the messages
and data entries to the
user portal
2. Provide channel
confidentiality.
1. k-anonymity
mechanism should be
used for data
anonymiztion
2. Tolerance of risk should
have to be deployed
7. Identifiability H H H 1. Anonymity of the
users should be
maintained
professionally
2. Pseudonymization for
the identity of the
users are required
1. Relationship based
enforcement is required
2. Awareness program
must be spread among
the users to make sure
that none of the data
are being interrupted or
hijacked.
8. Detectability L L M 1. In order to avoid
intercept
communication the
network should
1. In order to detect or
encounter the intrusions
or the root cause behind
these proper Intrusion
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
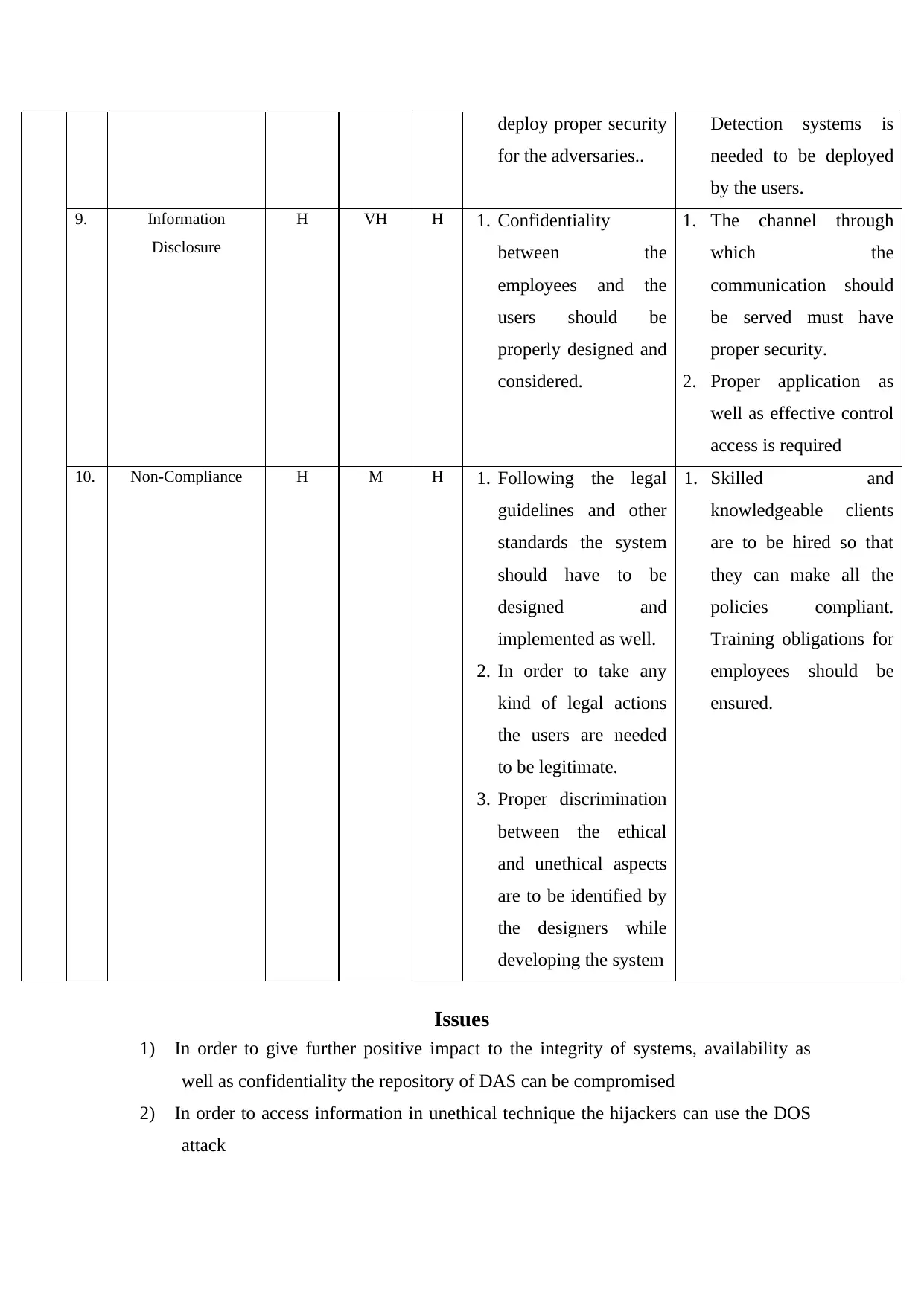
deploy proper security
for the adversaries..
Detection systems is
needed to be deployed
by the users.
9. Information
Disclosure
H VH H 1. Confidentiality
between the
employees and the
users should be
properly designed and
considered.
1. The channel through
which the
communication should
be served must have
proper security.
2. Proper application as
well as effective control
access is required
10. Non-Compliance H M H 1. Following the legal
guidelines and other
standards the system
should have to be
designed and
implemented as well.
2. In order to take any
kind of legal actions
the users are needed
to be legitimate.
3. Proper discrimination
between the ethical
and unethical aspects
are to be identified by
the designers while
developing the system
1. Skilled and
knowledgeable clients
are to be hired so that
they can make all the
policies compliant.
Training obligations for
employees should be
ensured.
Issues
1) In order to give further positive impact to the integrity of systems, availability as
well as confidentiality the repository of DAS can be compromised
2) In order to access information in unethical technique the hijackers can use the DOS
attack
for the adversaries..
Detection systems is
needed to be deployed
by the users.
9. Information
Disclosure
H VH H 1. Confidentiality
between the
employees and the
users should be
properly designed and
considered.
1. The channel through
which the
communication should
be served must have
proper security.
2. Proper application as
well as effective control
access is required
10. Non-Compliance H M H 1. Following the legal
guidelines and other
standards the system
should have to be
designed and
implemented as well.
2. In order to take any
kind of legal actions
the users are needed
to be legitimate.
3. Proper discrimination
between the ethical
and unethical aspects
are to be identified by
the designers while
developing the system
1. Skilled and
knowledgeable clients
are to be hired so that
they can make all the
policies compliant.
Training obligations for
employees should be
ensured.
Issues
1) In order to give further positive impact to the integrity of systems, availability as
well as confidentiality the repository of DAS can be compromised
2) In order to access information in unethical technique the hijackers can use the DOS
attack
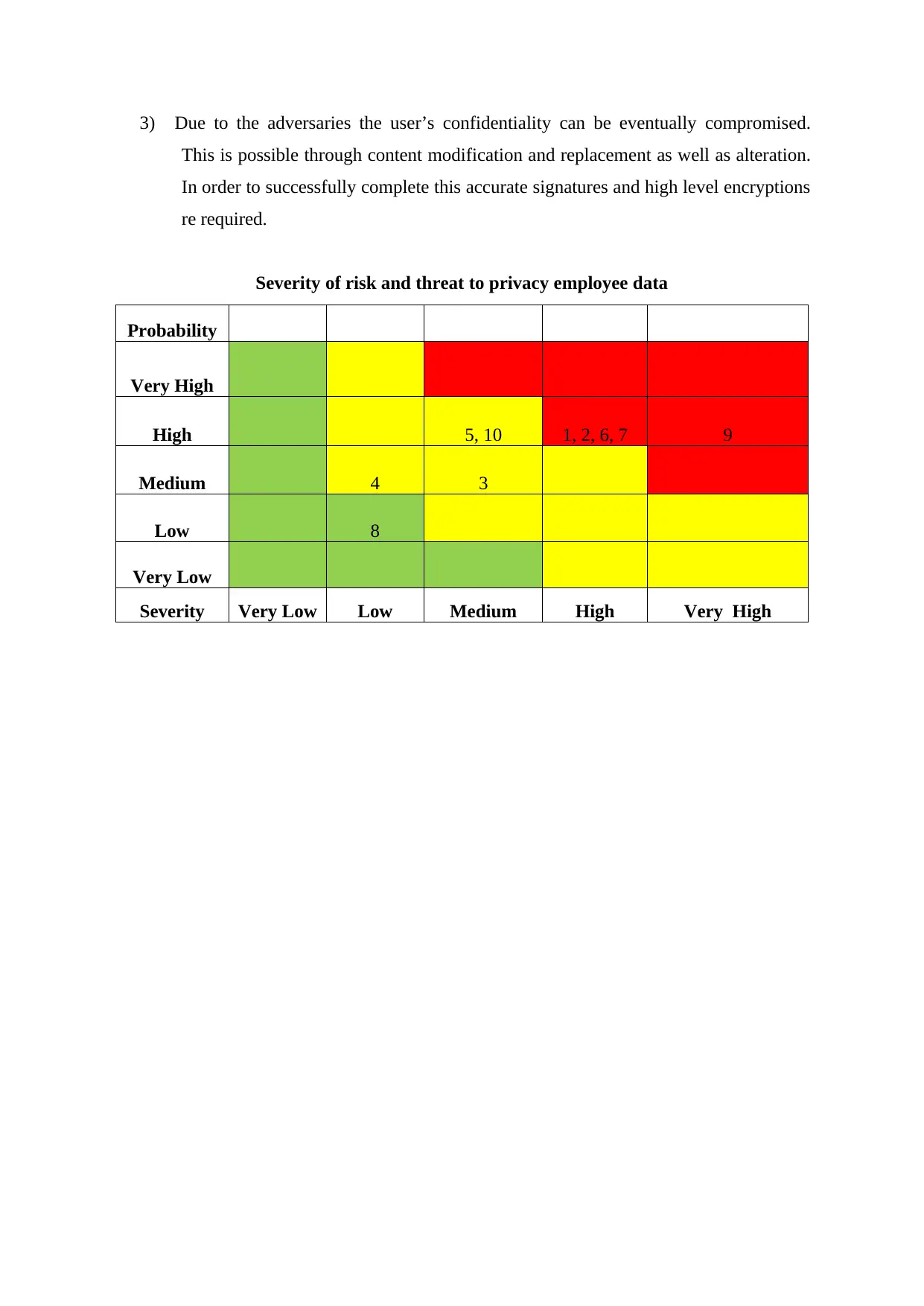
3) Due to the adversaries the user’s confidentiality can be eventually compromised.
This is possible through content modification and replacement as well as alteration.
In order to successfully complete this accurate signatures and high level encryptions
re required.
Severity of risk and threat to privacy employee data
Probability
Very High
High 5, 10 1, 2, 6, 7 9
Medium 4 3
Low 8
Very Low
Severity Very Low Low Medium High Very High
This is possible through content modification and replacement as well as alteration.
In order to successfully complete this accurate signatures and high level encryptions
re required.
Severity of risk and threat to privacy employee data
Probability
Very High
High 5, 10 1, 2, 6, 7 9
Medium 4 3
Low 8
Very Low
Severity Very Low Low Medium High Very High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Abomhara, M., & Køien, G. M. (2015). Cyber security and the internet of things:
vulnerabilities, threats, intruders and attacks. Journal of Cyber Security, 4(1), 65-88.
da Silva Costa, L., Alencar, Á. P., Neto, P. J. N., dos Santos, M. D. S. V., da Silva, C. G. L.,
Pinheiro, S. D. F. L., ... & Reis, A. O. A. (2015). Risk factors for suicide in bipolar
disorder: a systematic review. Journal of affective disorders, 170, 237-254.
Deng, Y. (2015). A threat assessment model under uncertain environment. Mathematical
Problems in Engineering, 2015.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
Hutle, M., Hansch, G., & Fitzgerald, W. (2015). D2. 2 Threat and Risk Assessment
Methodology. Tunneling and Underground Space Technology, 24(3), 269-277.
Jing, X., Hu, H., Yang, H., Au, M. H., Li, S., Xiong, N., ... & Vasilakos, A. V. (2017). A
quantitative risk assessment model involving frequency and threat degree under line-
of-business services for infrastructure of emerging sensor networks. Sensors, 17(3),
642.
Johnson, C., Badger, L., Waltermire, D., Snyder, J., & Skorupka, C. (2016). Guide to cyber
threat information sharing. NIST special publication, 800, 150.
Juliadotter, N. V., & Choo, K. K. R. (2015). Cloud attack and risk assessment
taxonomy. IEEE Cloud Computing, (1), 14-20.
Kazim, M., & Zhu, S. Y. (2015). A survey on top security threats in cloud
computing. International Journal of Advanced Computer Science and Applications
(IJACSA).
Lessler, J., Chaisson, L. H., Kucirka, L. M., Bi, Q., Grantz, K., Salje, H., ... & Cummings, D.
A. (2016). Assessing the global threat from Zika virus. Science, 353(6300), aaf8160.
Lippmann, R. P., & Riordan, J. F. (2016). Threat-based risk assessment for enterprise
networks. Lincoln Laboratory Journal, 22(1), 33-45.
Abomhara, M., & Køien, G. M. (2015). Cyber security and the internet of things:
vulnerabilities, threats, intruders and attacks. Journal of Cyber Security, 4(1), 65-88.
da Silva Costa, L., Alencar, Á. P., Neto, P. J. N., dos Santos, M. D. S. V., da Silva, C. G. L.,
Pinheiro, S. D. F. L., ... & Reis, A. O. A. (2015). Risk factors for suicide in bipolar
disorder: a systematic review. Journal of affective disorders, 170, 237-254.
Deng, Y. (2015). A threat assessment model under uncertain environment. Mathematical
Problems in Engineering, 2015.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the
security concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
Hutle, M., Hansch, G., & Fitzgerald, W. (2015). D2. 2 Threat and Risk Assessment
Methodology. Tunneling and Underground Space Technology, 24(3), 269-277.
Jing, X., Hu, H., Yang, H., Au, M. H., Li, S., Xiong, N., ... & Vasilakos, A. V. (2017). A
quantitative risk assessment model involving frequency and threat degree under line-
of-business services for infrastructure of emerging sensor networks. Sensors, 17(3),
642.
Johnson, C., Badger, L., Waltermire, D., Snyder, J., & Skorupka, C. (2016). Guide to cyber
threat information sharing. NIST special publication, 800, 150.
Juliadotter, N. V., & Choo, K. K. R. (2015). Cloud attack and risk assessment
taxonomy. IEEE Cloud Computing, (1), 14-20.
Kazim, M., & Zhu, S. Y. (2015). A survey on top security threats in cloud
computing. International Journal of Advanced Computer Science and Applications
(IJACSA).
Lessler, J., Chaisson, L. H., Kucirka, L. M., Bi, Q., Grantz, K., Salje, H., ... & Cummings, D.
A. (2016). Assessing the global threat from Zika virus. Science, 353(6300), aaf8160.
Lippmann, R. P., & Riordan, J. F. (2016). Threat-based risk assessment for enterprise
networks. Lincoln Laboratory Journal, 22(1), 33-45.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Macher, G., Armengaud, E., Brenner, E., & Kreiner, C. (2016). Threat and risk assessment
methodologies in the automotive domain. Procedia computer science, 83, 1288-1294.
Paek, S. H., Park, I. S., Lee, E. Y., Yun, J. B., Sohn, K. W., & Choi, S. J. (2014). U.S. Patent
No. 8,800,037. Washington, DC: U.S. Patent and Trademark Office.
Runge, C. A., Tulloch, A., Hammill, E., Possingham, H. P., & Fuller, R. A. (2015).
Geographic range size and extinction risk assessment in nomadic
species. Conservation Biology, 29(3), 865-876.
Shameli-Sendi, A., Aghababaei-Barzegar, R., & Cheriet, M. (2016). Taxonomy of
information security risk assessment (ISRA). Computers & security, 57, 14-30.
Tuna, G., Kogias, D. G., Gungor, V. C., Gezer, C., Taşkın, E., & Ayday, E. (2017). A survey
on information security threats and solutions for Machine to Machine (M2M)
communications. Journal of Parallel and Distributed Computing, 109, 142-154.
methodologies in the automotive domain. Procedia computer science, 83, 1288-1294.
Paek, S. H., Park, I. S., Lee, E. Y., Yun, J. B., Sohn, K. W., & Choi, S. J. (2014). U.S. Patent
No. 8,800,037. Washington, DC: U.S. Patent and Trademark Office.
Runge, C. A., Tulloch, A., Hammill, E., Possingham, H. P., & Fuller, R. A. (2015).
Geographic range size and extinction risk assessment in nomadic
species. Conservation Biology, 29(3), 865-876.
Shameli-Sendi, A., Aghababaei-Barzegar, R., & Cheriet, M. (2016). Taxonomy of
information security risk assessment (ISRA). Computers & security, 57, 14-30.
Tuna, G., Kogias, D. G., Gungor, V. C., Gezer, C., Taşkın, E., & Ayday, E. (2017). A survey
on information security threats and solutions for Machine to Machine (M2M)
communications. Journal of Parallel and Distributed Computing, 109, 142-154.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





