UMUC Network Security Solution
VerifiedAdded on 2019/10/01
|7
|2152
|141
Report
AI Summary
The University of Maryland University College (UMUC) network security plan aims to protect its resources from physical and cyber threats. To achieve this, the university has implemented a Demilitarized Zone (DMZ) using Cisco packet filtering firewalls to segregate internal and external links to servers. Physical security measures include locking systems, custodians, and low-profile areas for building setup. Anti-social engineering attacks are prevented through strong authentication systems and password management policies. Anti-malware software packages detect and remove malware in real-time. The university also employs the https protocol for secure access to internal and external network resources.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
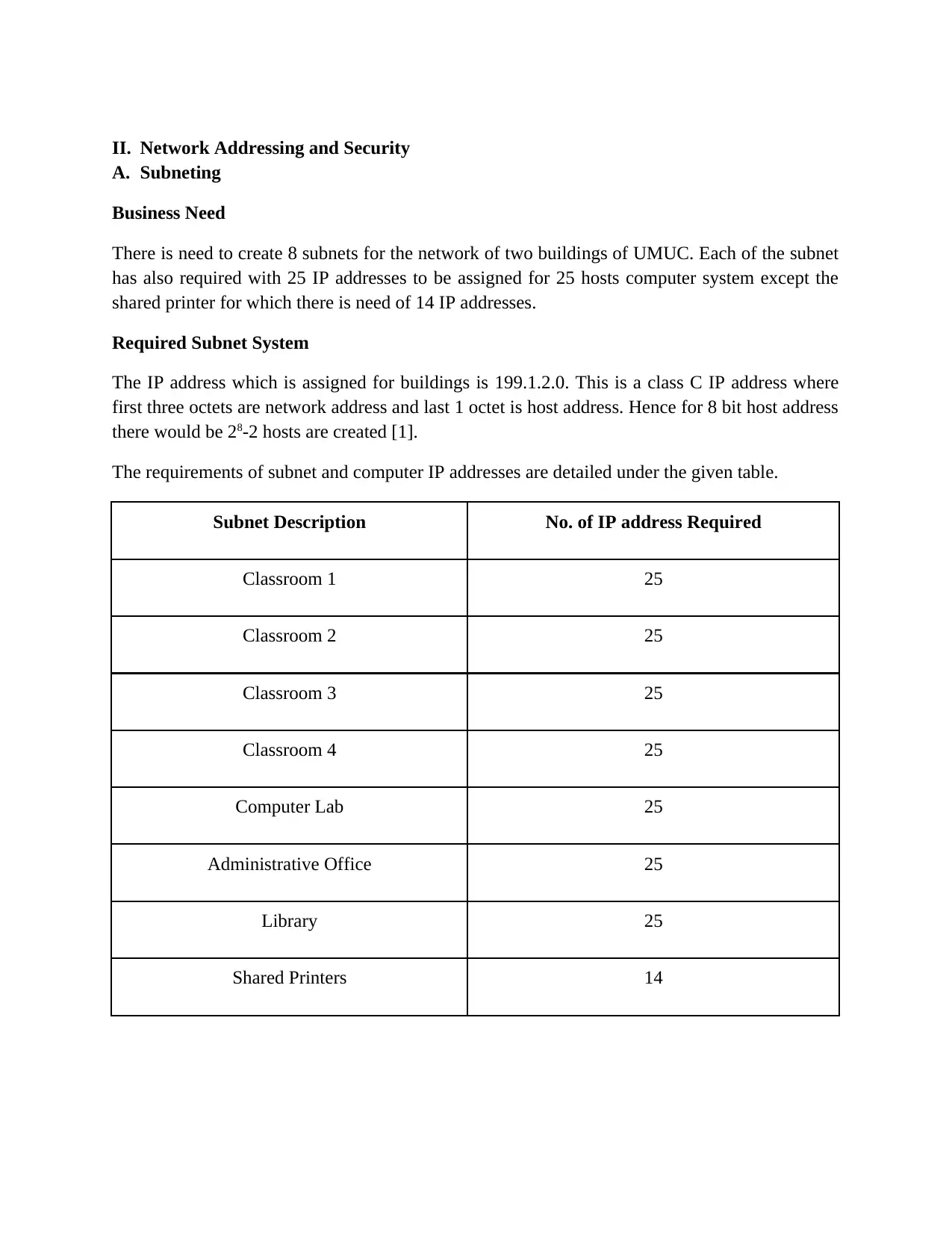
II. Network Addressing and Security
A. Subneting
Business Need
There is need to create 8 subnets for the network of two buildings of UMUC. Each of the subnet
has also required with 25 IP addresses to be assigned for 25 hosts computer system except the
shared printer for which there is need of 14 IP addresses.
Required Subnet System
The IP address which is assigned for buildings is 199.1.2.0. This is a class C IP address where
first three octets are network address and last 1 octet is host address. Hence for 8 bit host address
there would be 28-2 hosts are created [1].
The requirements of subnet and computer IP addresses are detailed under the given table.
Subnet Description No. of IP address Required
Classroom 1 25
Classroom 2 25
Classroom 3 25
Classroom 4 25
Computer Lab 25
Administrative Office 25
Library 25
Shared Printers 14
A. Subneting
Business Need
There is need to create 8 subnets for the network of two buildings of UMUC. Each of the subnet
has also required with 25 IP addresses to be assigned for 25 hosts computer system except the
shared printer for which there is need of 14 IP addresses.
Required Subnet System
The IP address which is assigned for buildings is 199.1.2.0. This is a class C IP address where
first three octets are network address and last 1 octet is host address. Hence for 8 bit host address
there would be 28-2 hosts are created [1].
The requirements of subnet and computer IP addresses are detailed under the given table.
Subnet Description No. of IP address Required
Classroom 1 25
Classroom 2 25
Classroom 3 25
Classroom 4 25
Computer Lab 25
Administrative Office 25
Library 25
Shared Printers 14
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
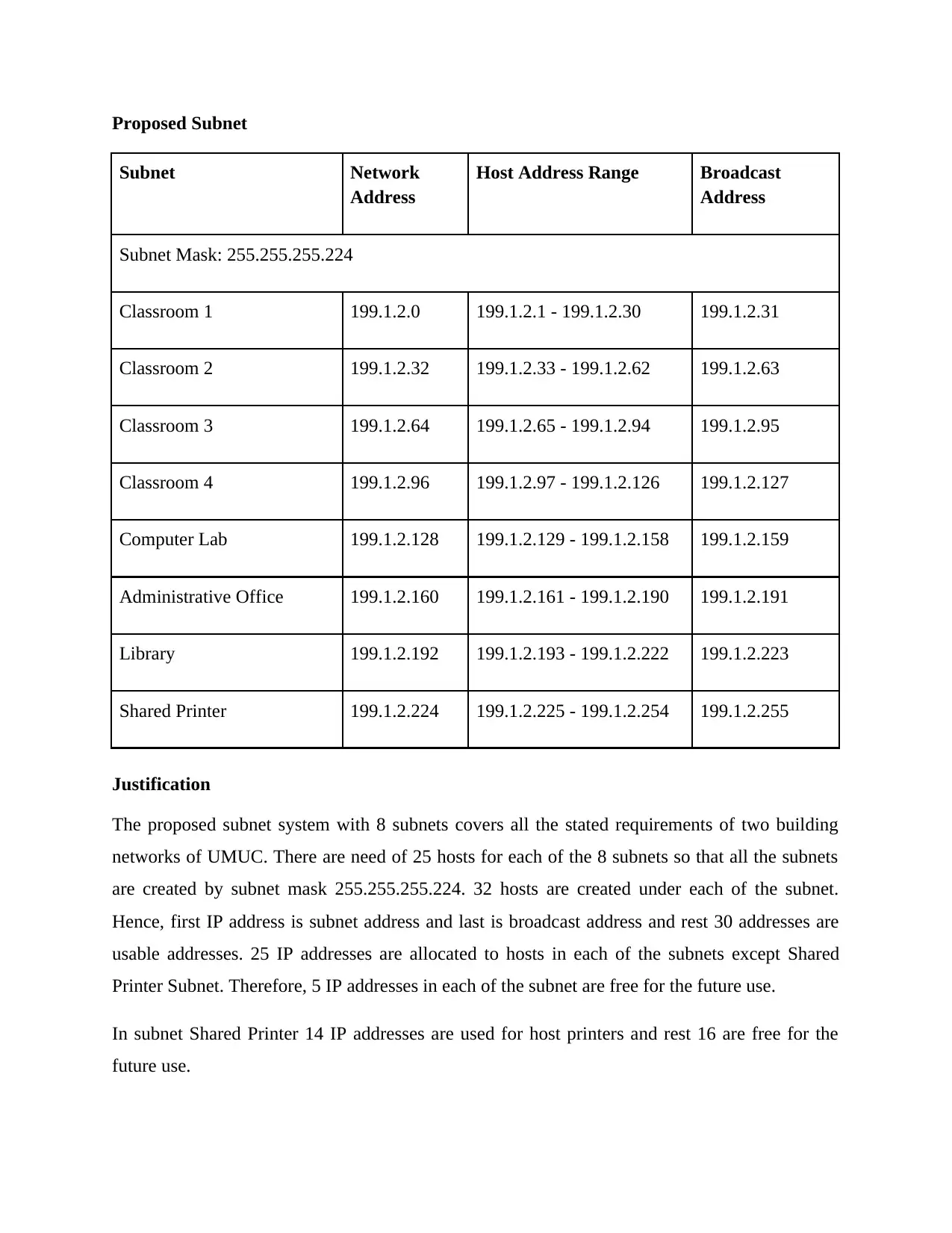
Proposed Subnet
Subnet Network
Address
Host Address Range Broadcast
Address
Subnet Mask: 255.255.255.224
Classroom 1 199.1.2.0 199.1.2.1 - 199.1.2.30 199.1.2.31
Classroom 2 199.1.2.32 199.1.2.33 - 199.1.2.62 199.1.2.63
Classroom 3 199.1.2.64 199.1.2.65 - 199.1.2.94 199.1.2.95
Classroom 4 199.1.2.96 199.1.2.97 - 199.1.2.126 199.1.2.127
Computer Lab 199.1.2.128 199.1.2.129 - 199.1.2.158 199.1.2.159
Administrative Office 199.1.2.160 199.1.2.161 - 199.1.2.190 199.1.2.191
Library 199.1.2.192 199.1.2.193 - 199.1.2.222 199.1.2.223
Shared Printer 199.1.2.224 199.1.2.225 - 199.1.2.254 199.1.2.255
Justification
The proposed subnet system with 8 subnets covers all the stated requirements of two building
networks of UMUC. There are need of 25 hosts for each of the 8 subnets so that all the subnets
are created by subnet mask 255.255.255.224. 32 hosts are created under each of the subnet.
Hence, first IP address is subnet address and last is broadcast address and rest 30 addresses are
usable addresses. 25 IP addresses are allocated to hosts in each of the subnets except Shared
Printer Subnet. Therefore, 5 IP addresses in each of the subnet are free for the future use.
In subnet Shared Printer 14 IP addresses are used for host printers and rest 16 are free for the
future use.
Subnet Network
Address
Host Address Range Broadcast
Address
Subnet Mask: 255.255.255.224
Classroom 1 199.1.2.0 199.1.2.1 - 199.1.2.30 199.1.2.31
Classroom 2 199.1.2.32 199.1.2.33 - 199.1.2.62 199.1.2.63
Classroom 3 199.1.2.64 199.1.2.65 - 199.1.2.94 199.1.2.95
Classroom 4 199.1.2.96 199.1.2.97 - 199.1.2.126 199.1.2.127
Computer Lab 199.1.2.128 199.1.2.129 - 199.1.2.158 199.1.2.159
Administrative Office 199.1.2.160 199.1.2.161 - 199.1.2.190 199.1.2.191
Library 199.1.2.192 199.1.2.193 - 199.1.2.222 199.1.2.223
Shared Printer 199.1.2.224 199.1.2.225 - 199.1.2.254 199.1.2.255
Justification
The proposed subnet system with 8 subnets covers all the stated requirements of two building
networks of UMUC. There are need of 25 hosts for each of the 8 subnets so that all the subnets
are created by subnet mask 255.255.255.224. 32 hosts are created under each of the subnet.
Hence, first IP address is subnet address and last is broadcast address and rest 30 addresses are
usable addresses. 25 IP addresses are allocated to hosts in each of the subnets except Shared
Printer Subnet. Therefore, 5 IP addresses in each of the subnet are free for the future use.
In subnet Shared Printer 14 IP addresses are used for host printers and rest 16 are free for the
future use.
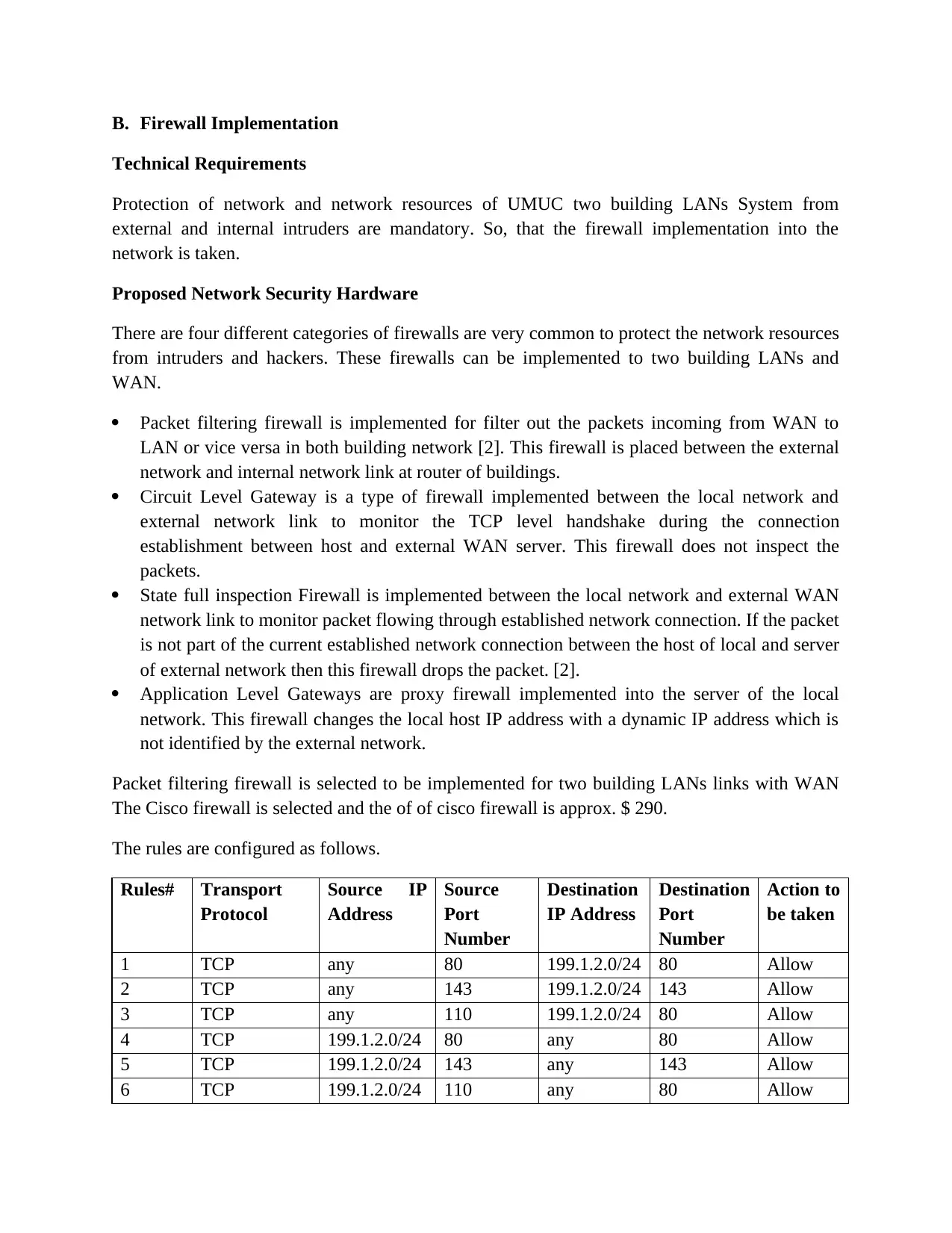
B. Firewall Implementation
Technical Requirements
Protection of network and network resources of UMUC two building LANs System from
external and internal intruders are mandatory. So, that the firewall implementation into the
network is taken.
Proposed Network Security Hardware
There are four different categories of firewalls are very common to protect the network resources
from intruders and hackers. These firewalls can be implemented to two building LANs and
WAN.
Packet filtering firewall is implemented for filter out the packets incoming from WAN to
LAN or vice versa in both building network [2]. This firewall is placed between the external
network and internal network link at router of buildings.
Circuit Level Gateway is a type of firewall implemented between the local network and
external network link to monitor the TCP level handshake during the connection
establishment between host and external WAN server. This firewall does not inspect the
packets.
State full inspection Firewall is implemented between the local network and external WAN
network link to monitor packet flowing through established network connection. If the packet
is not part of the current established network connection between the host of local and server
of external network then this firewall drops the packet. [2].
Application Level Gateways are proxy firewall implemented into the server of the local
network. This firewall changes the local host IP address with a dynamic IP address which is
not identified by the external network.
Packet filtering firewall is selected to be implemented for two building LANs links with WAN
The Cisco firewall is selected and the of of cisco firewall is approx. $ 290.
The rules are configured as follows.
Rules# Transport
Protocol
Source IP
Address
Source
Port
Number
Destination
IP Address
Destination
Port
Number
Action to
be taken
1 TCP any 80 199.1.2.0/24 80 Allow
2 TCP any 143 199.1.2.0/24 143 Allow
3 TCP any 110 199.1.2.0/24 80 Allow
4 TCP 199.1.2.0/24 80 any 80 Allow
5 TCP 199.1.2.0/24 143 any 143 Allow
6 TCP 199.1.2.0/24 110 any 80 Allow
Technical Requirements
Protection of network and network resources of UMUC two building LANs System from
external and internal intruders are mandatory. So, that the firewall implementation into the
network is taken.
Proposed Network Security Hardware
There are four different categories of firewalls are very common to protect the network resources
from intruders and hackers. These firewalls can be implemented to two building LANs and
WAN.
Packet filtering firewall is implemented for filter out the packets incoming from WAN to
LAN or vice versa in both building network [2]. This firewall is placed between the external
network and internal network link at router of buildings.
Circuit Level Gateway is a type of firewall implemented between the local network and
external network link to monitor the TCP level handshake during the connection
establishment between host and external WAN server. This firewall does not inspect the
packets.
State full inspection Firewall is implemented between the local network and external WAN
network link to monitor packet flowing through established network connection. If the packet
is not part of the current established network connection between the host of local and server
of external network then this firewall drops the packet. [2].
Application Level Gateways are proxy firewall implemented into the server of the local
network. This firewall changes the local host IP address with a dynamic IP address which is
not identified by the external network.
Packet filtering firewall is selected to be implemented for two building LANs links with WAN
The Cisco firewall is selected and the of of cisco firewall is approx. $ 290.
The rules are configured as follows.
Rules# Transport
Protocol
Source IP
Address
Source
Port
Number
Destination
IP Address
Destination
Port
Number
Action to
be taken
1 TCP any 80 199.1.2.0/24 80 Allow
2 TCP any 143 199.1.2.0/24 143 Allow
3 TCP any 110 199.1.2.0/24 80 Allow
4 TCP 199.1.2.0/24 80 any 80 Allow
5 TCP 199.1.2.0/24 143 any 143 Allow
6 TCP 199.1.2.0/24 110 any 80 Allow

Justification
Cisco Packet Filtering firewall is intelligent firewall and also compatible with Cisco Router for
filtering the incoming and outgoing traffics of the network of two buildings of UMUC. This
firewall filters all the packets either incoming from WAN to LAN and LAN to WAN. The major
benefit to implement packet filtering firewall from Cisco Model is that it is easily configured,
Easily managed and rules are implemented.
The rules for the firewall is important and rule generation and implementation are very ease with
Cisco packet filtering firewall. This firewall protects the network from intruder either from
internal or external network.
C. Intrusion Detection System/Intrusion Protection System
Technical Requirement
Network monitoring of network of two buildings of UMUC from intruders is required. Therefore
IDPS (Intrusion Detection and Prevention System is implemented with LAN of UMUC
buildings.
Proposed Network Security Hardware
The proposed IDPS is selected as NGIPS for buildings network security from intruders. This
prevents the building LANs from various categories of attacks such as Denial of Service Attack,
Man in Middle Attack etc [3]. Cisco Next Generation Intrusion Prevention System (NGIPS) is
selected to be implemented to protect the network resources from hackers, attackers and any
other categories of intruders. Cost of this IDPS is approximately $ 450.
Justification
Intrusion detection and Prevention System (IDPS) and is a network defense system that secures
the building LANs from Attackers and Hackers. NGIPS provides the real time contextual
awareness to the network administration staff to prevent the intruder to enter into the network.
When intruder has made entry the constant warning or alert message are displayed on the
monitoring window to the network administration staff. The deployment of this IPS is very
simple as all other devices are selected from Cisco so it is more compatible IPS for the university
building LAN. The monitoring and management of network security with NGIPS is simple
interface where there is single monitoring system with a desktop system is required. The
monitoring workstation provides the ongoing with network and produces alarm when the abuse
with network is detected.
D. DMZ Implementation
Technical Requirement
Cisco Packet Filtering firewall is intelligent firewall and also compatible with Cisco Router for
filtering the incoming and outgoing traffics of the network of two buildings of UMUC. This
firewall filters all the packets either incoming from WAN to LAN and LAN to WAN. The major
benefit to implement packet filtering firewall from Cisco Model is that it is easily configured,
Easily managed and rules are implemented.
The rules for the firewall is important and rule generation and implementation are very ease with
Cisco packet filtering firewall. This firewall protects the network from intruder either from
internal or external network.
C. Intrusion Detection System/Intrusion Protection System
Technical Requirement
Network monitoring of network of two buildings of UMUC from intruders is required. Therefore
IDPS (Intrusion Detection and Prevention System is implemented with LAN of UMUC
buildings.
Proposed Network Security Hardware
The proposed IDPS is selected as NGIPS for buildings network security from intruders. This
prevents the building LANs from various categories of attacks such as Denial of Service Attack,
Man in Middle Attack etc [3]. Cisco Next Generation Intrusion Prevention System (NGIPS) is
selected to be implemented to protect the network resources from hackers, attackers and any
other categories of intruders. Cost of this IDPS is approximately $ 450.
Justification
Intrusion detection and Prevention System (IDPS) and is a network defense system that secures
the building LANs from Attackers and Hackers. NGIPS provides the real time contextual
awareness to the network administration staff to prevent the intruder to enter into the network.
When intruder has made entry the constant warning or alert message are displayed on the
monitoring window to the network administration staff. The deployment of this IPS is very
simple as all other devices are selected from Cisco so it is more compatible IPS for the university
building LAN. The monitoring and management of network security with NGIPS is simple
interface where there is single monitoring system with a desktop system is required. The
monitoring workstation provides the ongoing with network and produces alarm when the abuse
with network is detected.
D. DMZ Implementation
Technical Requirement
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Some of the resources of network such as servers of LANs of two buildings of UMUC requires
very high security. Demilitarized zone provides very high security to servers of the LANs of two
buildings of UMUC.
Proposed DMZ
DMZ is implemented by configuring the firewall. The rules for all the Subnet group users having
the selected range of IP addresses of the system of LAN are required to be configured with DMZ
to allow or deny the access to the resources of server [4]. DMZ implementation is also
implemented by using the Cisco packet filtering firewalls. All internal and external links to the
servers are created demilitarized Zone.
Justification
Network of two buildings are also connected to Internet or WAN through the help of router.
Internal desktop workstations of various classrooms, lab, library and others are also connected to
the server via Cisco switches. The subnet has the group of users. to provides accessibility
security DMZ provides the high level of security to protect the server resources of the LAN.
Therefore, Cisco Firewalls are taken to be implemented over server to provide high level of
security for internal and external users.
E. Physical Security Measure
Technical Requirements
The network and associated hardware and other resources require the security from theft, damage
due to individual intention or any accidental causes. Natural Disasters are another major physical
security issue for the network. So, that physical security measures are required to be
implemented.
Proposed Network Security Hardware
The network security from physical causes is provided through the locking system to prevent the
theft of network and computing devices. A proper custodian is deployed to protect the devices
from theft under the locking system. The theft of devices may cause the loss and unauthorized
disclosure of information of the university or individual identity of faculty, staffs and students. A
regular cost is involved which should be paid by the university to employee who becomes
custodian of information system and network devices of university.
Justification
To protect the network hardware and information resources of the network of two buildings are
required from physical sources of damage. The risks associated with intentional and accidental
damage require to be identified and a proper security measures with defined policy must be
implemented with network. The anti theft mechanisms such custodian, locking system, selection
very high security. Demilitarized zone provides very high security to servers of the LANs of two
buildings of UMUC.
Proposed DMZ
DMZ is implemented by configuring the firewall. The rules for all the Subnet group users having
the selected range of IP addresses of the system of LAN are required to be configured with DMZ
to allow or deny the access to the resources of server [4]. DMZ implementation is also
implemented by using the Cisco packet filtering firewalls. All internal and external links to the
servers are created demilitarized Zone.
Justification
Network of two buildings are also connected to Internet or WAN through the help of router.
Internal desktop workstations of various classrooms, lab, library and others are also connected to
the server via Cisco switches. The subnet has the group of users. to provides accessibility
security DMZ provides the high level of security to protect the server resources of the LAN.
Therefore, Cisco Firewalls are taken to be implemented over server to provide high level of
security for internal and external users.
E. Physical Security Measure
Technical Requirements
The network and associated hardware and other resources require the security from theft, damage
due to individual intention or any accidental causes. Natural Disasters are another major physical
security issue for the network. So, that physical security measures are required to be
implemented.
Proposed Network Security Hardware
The network security from physical causes is provided through the locking system to prevent the
theft of network and computing devices. A proper custodian is deployed to protect the devices
from theft under the locking system. The theft of devices may cause the loss and unauthorized
disclosure of information of the university or individual identity of faculty, staffs and students. A
regular cost is involved which should be paid by the university to employee who becomes
custodian of information system and network devices of university.
Justification
To protect the network hardware and information resources of the network of two buildings are
required from physical sources of damage. The risks associated with intentional and accidental
damage require to be identified and a proper security measures with defined policy must be
implemented with network. The anti theft mechanisms such custodian, locking system, selection

of low profile area where fire, flood and earthquake occurs frequently for building setup must be
evaluated first. These all measures secure the UMUC buildings network and its resources
effectively.
F. Additional Network Security Measures
Technical Requirements
There is need to protect the network by implementing the mechanism and tools from security
system. The network resources are required to be protected from social engineering attacks,
malware programs and hackers.
Proposed Network Security System
Phishing is common social engineering attack where the attackers employ the users personal
information to get or reveal the confidential information such as credentials or password of
account [5]. A suitable program must be deployed for all the users to prevent the disclosure of
personal information to other users. Hiding the personal information to not be public prevents the
social engineering attack.
An anti-Malware software package is required to be deployed on the servers of the university
building. This anti-malware package detects the malware which is launched by students or any
one else from the network and removed automatically in real time. Therefore, the system related
with any user such as faculty or student is protected from malware. The cost of antimalware and
antivirus security package is approx. $350 for all the computing system including server.
The security protocol to access the internal and external network resources is https. This is
knows secured hypertext transfer protocol. This protocol is activated through the secured socket
layer and all the communication is provided through secured Internet protocol such as IPSec.
Justification
The social engineering attack is prevented by employing the strong authentication system. A
password management policy is best for protecting the information and network resources from
social engineering attacks such as fishing etc. The anti malware and antivirus software package.
These packages have intelligent defense mechanism to find out the malware and malicious code.
Once it finds the malicious code then it automatically removes them. IPSec protocol is secured
version of Internet protocol that encrypts the packet data. Once the packet data is encrypted it
becomes impossible to find the meaning of packet data even the packet is hacked during the
communication.
G. Network and Cloud Based Storage
Explicit condition of UMUC which is not liable as for any problem caused by use of users
personal devices stated by a form filling procedures at the time of device MAC address
evaluated first. These all measures secure the UMUC buildings network and its resources
effectively.
F. Additional Network Security Measures
Technical Requirements
There is need to protect the network by implementing the mechanism and tools from security
system. The network resources are required to be protected from social engineering attacks,
malware programs and hackers.
Proposed Network Security System
Phishing is common social engineering attack where the attackers employ the users personal
information to get or reveal the confidential information such as credentials or password of
account [5]. A suitable program must be deployed for all the users to prevent the disclosure of
personal information to other users. Hiding the personal information to not be public prevents the
social engineering attack.
An anti-Malware software package is required to be deployed on the servers of the university
building. This anti-malware package detects the malware which is launched by students or any
one else from the network and removed automatically in real time. Therefore, the system related
with any user such as faculty or student is protected from malware. The cost of antimalware and
antivirus security package is approx. $350 for all the computing system including server.
The security protocol to access the internal and external network resources is https. This is
knows secured hypertext transfer protocol. This protocol is activated through the secured socket
layer and all the communication is provided through secured Internet protocol such as IPSec.
Justification
The social engineering attack is prevented by employing the strong authentication system. A
password management policy is best for protecting the information and network resources from
social engineering attacks such as fishing etc. The anti malware and antivirus software package.
These packages have intelligent defense mechanism to find out the malware and malicious code.
Once it finds the malicious code then it automatically removes them. IPSec protocol is secured
version of Internet protocol that encrypts the packet data. Once the packet data is encrypted it
becomes impossible to find the meaning of packet data even the packet is hacked during the
communication.
G. Network and Cloud Based Storage
Explicit condition of UMUC which is not liable as for any problem caused by use of users
personal devices stated by a form filling procedures at the time of device MAC address

registration. Without MAC registration of user computing devices the access of LAN is not
granted. Access of LAN and WAN resources through wired and wireless network of the
university building is granted after MAC registration into server database. The form should have
explicitly a written all the terms and condition of use of the personal computing devices at
university building premise. The form must be signed by the users with mentioned MAC address
of their devices.
References
[1] G. Held, The ABCs of IP addressing. Boca Raton, Fla.: Auerbach Publications, 2002.
[2] "Firewall for ‘always on’ connections", Computer Fraud & Security, vol. 2000, no. 12, p. 5,
2000.
[3] J. Chenoweth, "Information Security Policies, Procedures, and Standards: Guidelines for
Effective Information Security Management", Journal of Information Privacy and Security, vol.
1, no. 1, pp. 43-44, 2005.
[4] I. Dubrawsky and C. Baumrucker, Designing and building enterprise DMZs. Rockland, MA:
Syngress, 2006.
[5] F. Mouton, L. Leenen and H. Venter, "Social engineering attack examples, templates and
scenarios", Computers & Security, vol. 59, pp. 186-209, 2016.
granted. Access of LAN and WAN resources through wired and wireless network of the
university building is granted after MAC registration into server database. The form should have
explicitly a written all the terms and condition of use of the personal computing devices at
university building premise. The form must be signed by the users with mentioned MAC address
of their devices.
References
[1] G. Held, The ABCs of IP addressing. Boca Raton, Fla.: Auerbach Publications, 2002.
[2] "Firewall for ‘always on’ connections", Computer Fraud & Security, vol. 2000, no. 12, p. 5,
2000.
[3] J. Chenoweth, "Information Security Policies, Procedures, and Standards: Guidelines for
Effective Information Security Management", Journal of Information Privacy and Security, vol.
1, no. 1, pp. 43-44, 2005.
[4] I. Dubrawsky and C. Baumrucker, Designing and building enterprise DMZs. Rockland, MA:
Syngress, 2006.
[5] F. Mouton, L. Leenen and H. Venter, "Social engineering attack examples, templates and
scenarios", Computers & Security, vol. 59, pp. 186-209, 2016.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





