Network Architecture for Seagull International Company
VerifiedAI Summary
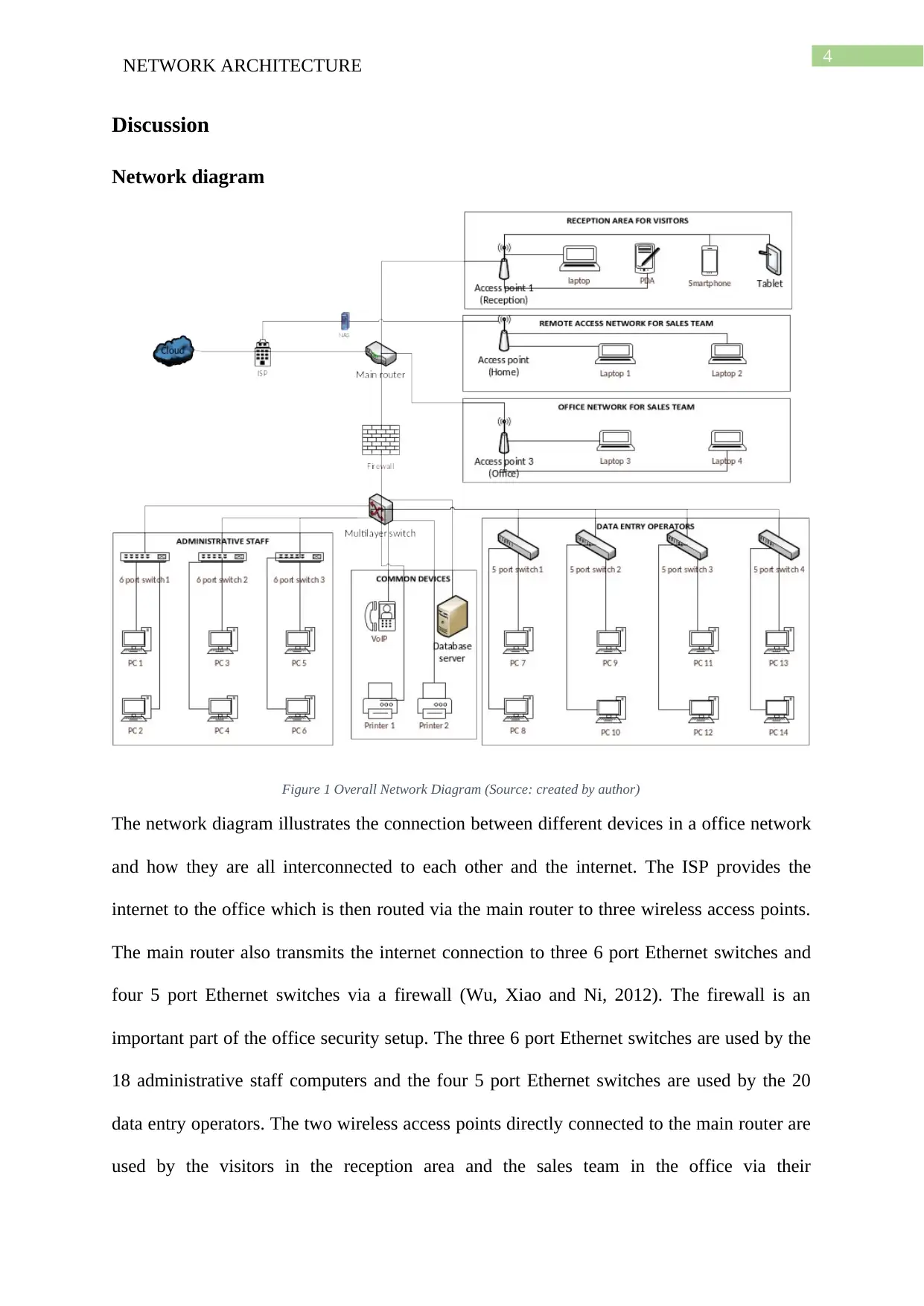
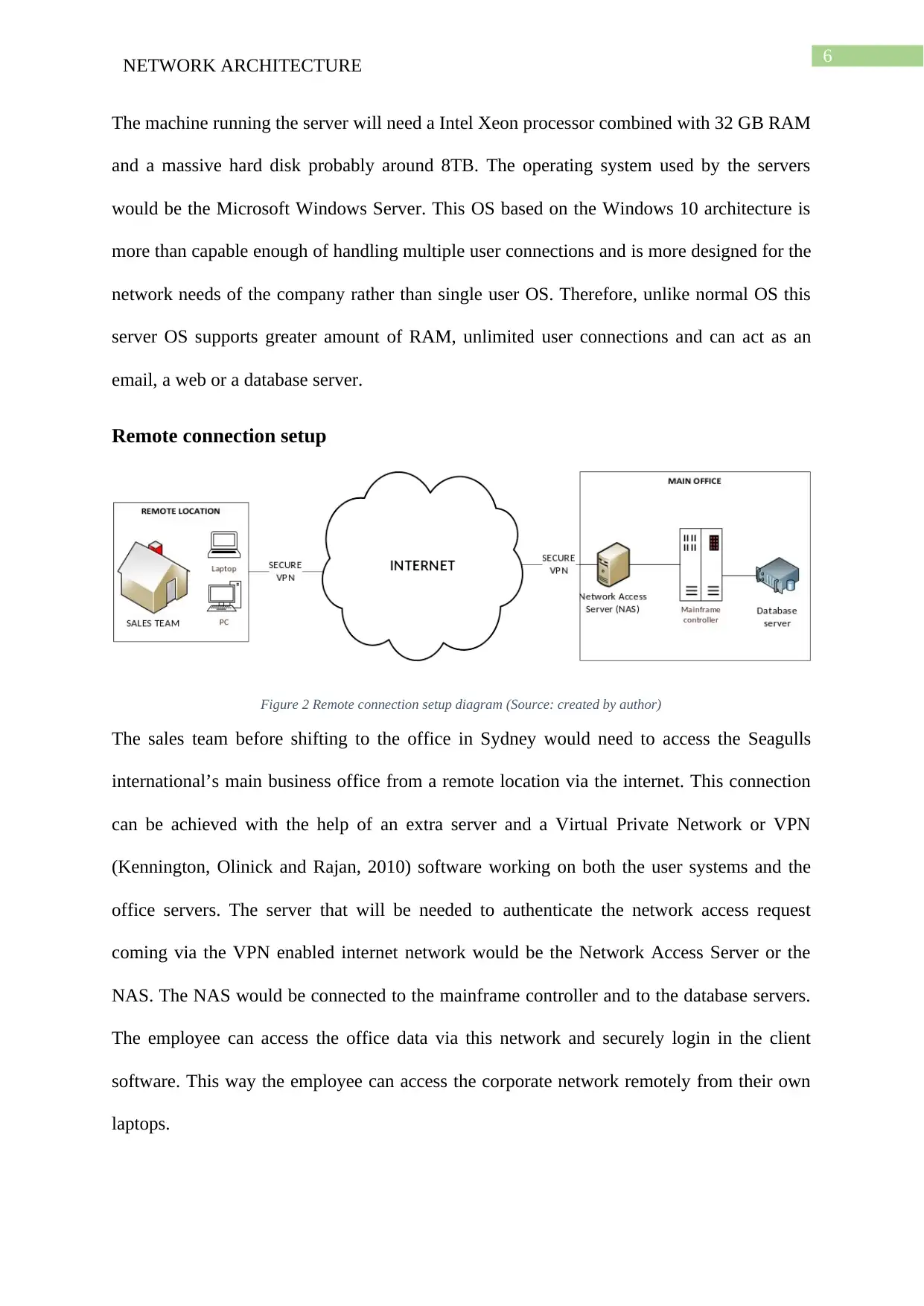
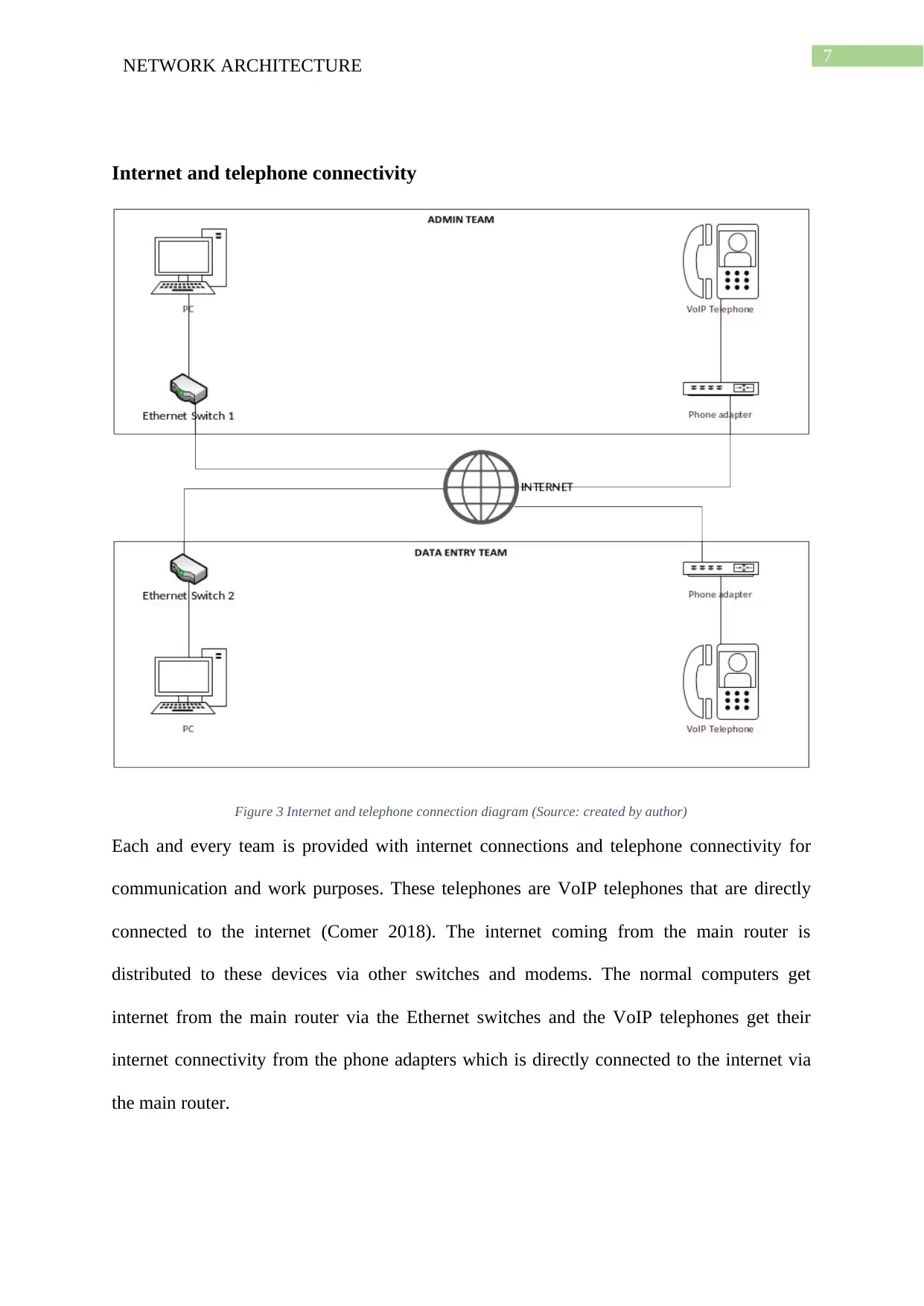
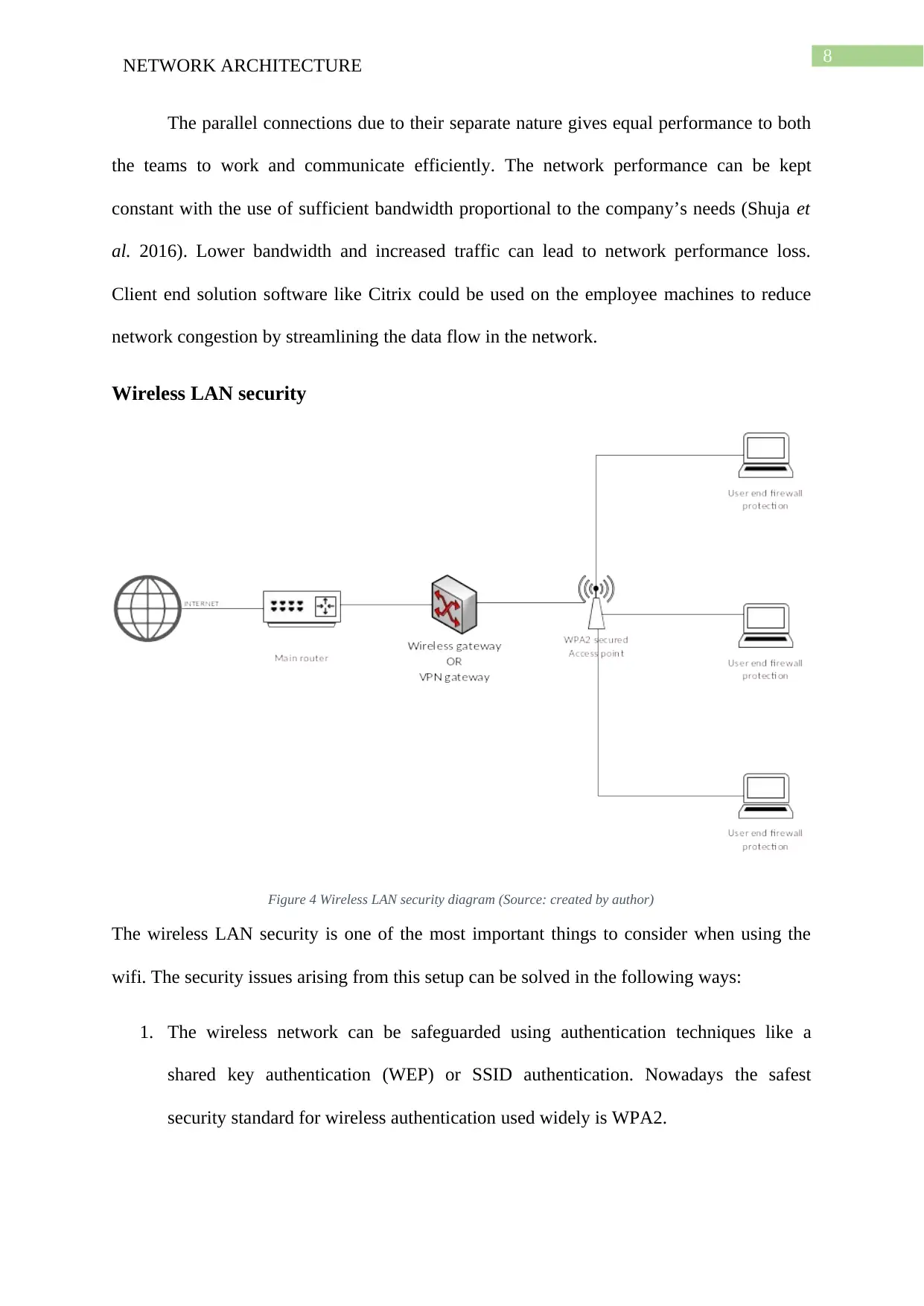
The report provides a detailed view of the network architecture of the Seagull International Company. It details the network setup along with the devices needed to create the network. This part is illustrated with a network diagram. The report also discusses the remote access of the network along with the wireless security solutions needed for secure communications. The report addresses the IP address allocation to network devices connected to the office network. It also demonstrates the setup of the internet and telephone connection between the admin and the data entry teams. The operating system needed for server and regular office systems have also been discussed in this report. The diagrams shown in this report have been created by the author using Microsoft Visio. The report concludes with an overall summary of the report.
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)