SIT202 Computer Networks: TCP/IP, Ethernet, and Protocol Analysis
VerifiedAdded on 2023/06/10
|11
|2467
|424
Report
AI Summary
This report provides a detailed analysis of computer networks, focusing on TCP/IP and Ethernet protocols. It explores data communication, encapsulation processes at each layer of the OSI model, and peer layer communication. The report discusses the functionality of switches, MAC address tables, and network layer addressing. It also covers Point-to-Point Protocol (PPP), Link Control Protocol (LCP), Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), and Network Control Program (NCP). Furthermore, the report discusses mobile telephony, bandpass channels, and collision scenarios in network switches. Desklib offers additional resources, including past papers and solved assignments, for students studying computer networks.

Running head: NETWORK AND COMMUNICATIONS 1
Network and Communications
Name of Student
Institution Affiliation
Network and Communications
Name of Student
Institution Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK AND COMMUNICATION 2
Question 1 (1)
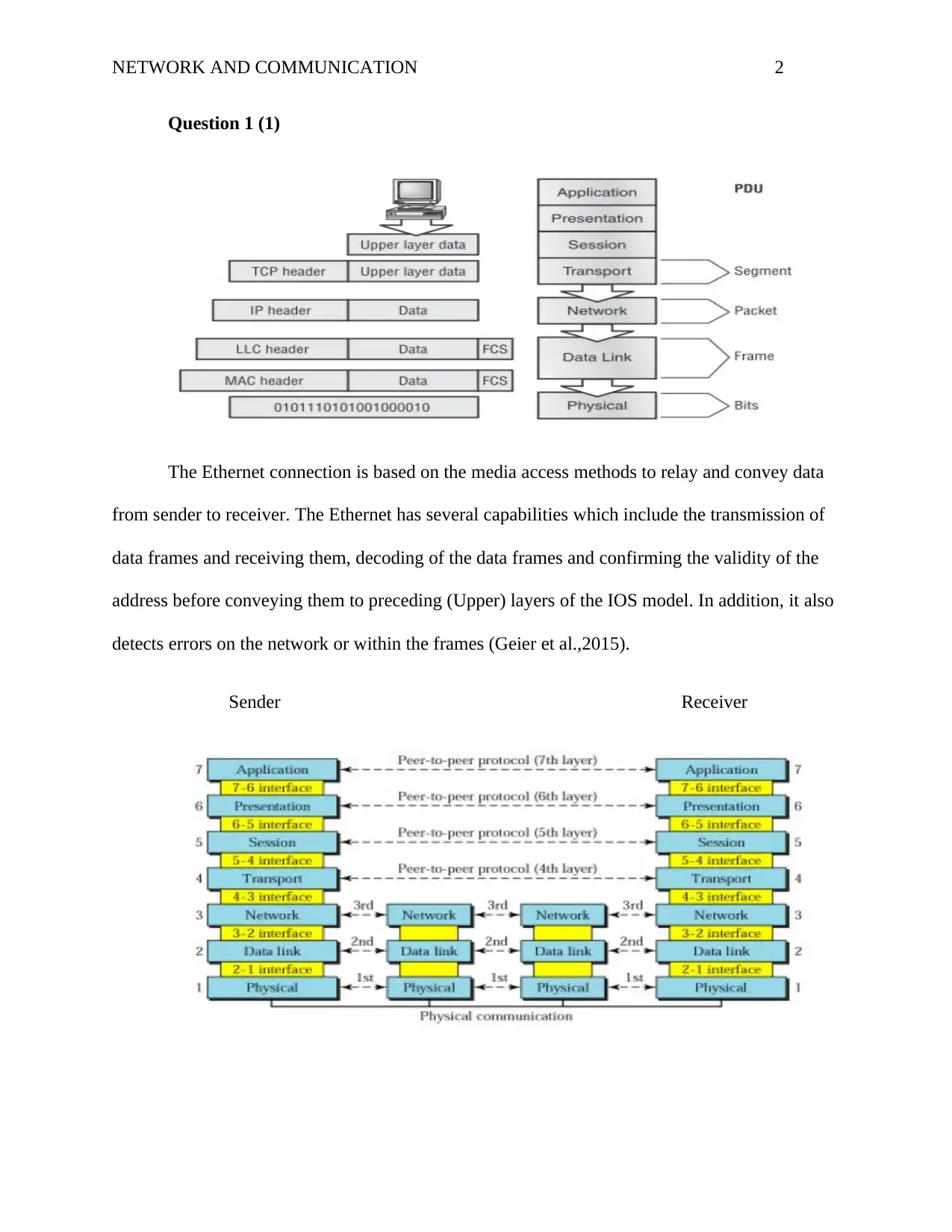
The Ethernet connection is based on the media access methods to relay and convey data
from sender to receiver. The Ethernet has several capabilities which include the transmission of
data frames and receiving them, decoding of the data frames and confirming the validity of the
address before conveying them to preceding (Upper) layers of the IOS model. In addition, it also
detects errors on the network or within the frames (Geier et al.,2015).
Sender Receiver
Question 1 (1)
The Ethernet connection is based on the media access methods to relay and convey data
from sender to receiver. The Ethernet has several capabilities which include the transmission of
data frames and receiving them, decoding of the data frames and confirming the validity of the
address before conveying them to preceding (Upper) layers of the IOS model. In addition, it also
detects errors on the network or within the frames (Geier et al.,2015).
Sender Receiver

NETWORK AND COMMUNICATION 3
Data moves down through the layer on the sender computer through the Ethernet cables
to the receiver. The application support layer enhances permits communication by the receiver
and the unrelated software systems. The transport layer ensures the transmission is appropriate
while the network layer is concerned with moving data across the devices. Each layer in the
sender receives information from the layer above it, adds its own information and passes the
whole package to the layer below it. When it reaches the physical layer, it is transformed into an
electromagnetic signal and convey through the physical link.
For the data to travel from one layer to the other, each layer must communicate to its peer
on the other end, during this peer-to-peer process the protocols of the two layers communicate to
one another; the source must communicate to its peer in the next layer, the destination layer. The
layers exchange information known as Protocol Data Communication (PDU). The dependency
function of each layer is aided by the service layer below it. To make the service a success, the
lower layer uses encapsulation to put the PDU from the upper layer to its data field. It then adds
the necessary headers the layers need to perform its function. As the data move, additional
headers are added. They are grouped into segments.
The layers use their own layer protocols to communicate with their peer layer in the other
end. Each layer’s protocol communicates to one another using protocol data units (PDUs),
between peer layers. The peer-layer protocol communication is attained by using the function
provision of the layers beneath it. The transport layer will insure that data is kept segmented
from one another. The Transport Control Protocol/ Internet Protocol commonly known as by its
abbreviations (TCP/IP) has four layers namely Application, Transport, Internet and Network
Access Layer which perform different functions to in aiding the data communication processes.
Data moves down through the layer on the sender computer through the Ethernet cables
to the receiver. The application support layer enhances permits communication by the receiver
and the unrelated software systems. The transport layer ensures the transmission is appropriate
while the network layer is concerned with moving data across the devices. Each layer in the
sender receives information from the layer above it, adds its own information and passes the
whole package to the layer below it. When it reaches the physical layer, it is transformed into an
electromagnetic signal and convey through the physical link.
For the data to travel from one layer to the other, each layer must communicate to its peer
on the other end, during this peer-to-peer process the protocols of the two layers communicate to
one another; the source must communicate to its peer in the next layer, the destination layer. The
layers exchange information known as Protocol Data Communication (PDU). The dependency
function of each layer is aided by the service layer below it. To make the service a success, the
lower layer uses encapsulation to put the PDU from the upper layer to its data field. It then adds
the necessary headers the layers need to perform its function. As the data move, additional
headers are added. They are grouped into segments.
The layers use their own layer protocols to communicate with their peer layer in the other
end. Each layer’s protocol communicates to one another using protocol data units (PDUs),
between peer layers. The peer-layer protocol communication is attained by using the function
provision of the layers beneath it. The transport layer will insure that data is kept segmented
from one another. The Transport Control Protocol/ Internet Protocol commonly known as by its
abbreviations (TCP/IP) has four layers namely Application, Transport, Internet and Network
Access Layer which perform different functions to in aiding the data communication processes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND COMMUNICATION 4
In encapsulation, PDUs are created by each protocol which entails the data and the
header that is to be transmitted. These data become the Service Data Unit (SDU) of the layer
below it. From the diagram above, the uppermost layer,7, PDU has a layer 7 header and
application data. When it is conveyed to 6 it becomes 6 SDU. The 6 layer attachés the data at the
beginning of L6H to give rise to layer 6 PDU which is later on passed to layer number 5. The
encapsulation process continues up to layer number 2 which initiate layer 2PDU, it transformed
into bits and forwarded to layer number 1
Question 1 (2)
The receiver will synchronize with the digital signals until it's done and receives the
whole frame. Once complete, it will pass it to the Data link layer which is above it. The data link
will check if there is an error in the data through the Cyclic Redundancy Check (CRC). The data
link layer will remove any information that was initially put any the remote system's data link
layer thus moving to Network layer to form packets. The IP address is checked in the Network
layer, then strips off from packets and passes the rest to the Transport layer to form segments.
In encapsulation, PDUs are created by each protocol which entails the data and the
header that is to be transmitted. These data become the Service Data Unit (SDU) of the layer
below it. From the diagram above, the uppermost layer,7, PDU has a layer 7 header and
application data. When it is conveyed to 6 it becomes 6 SDU. The 6 layer attachés the data at the
beginning of L6H to give rise to layer 6 PDU which is later on passed to layer number 5. The
encapsulation process continues up to layer number 2 which initiate layer 2PDU, it transformed
into bits and forwarded to layer number 1
Question 1 (2)
The receiver will synchronize with the digital signals until it's done and receives the
whole frame. Once complete, it will pass it to the Data link layer which is above it. The data link
will check if there is an error in the data through the Cyclic Redundancy Check (CRC). The data
link layer will remove any information that was initially put any the remote system's data link
layer thus moving to Network layer to form packets. The IP address is checked in the Network
layer, then strips off from packets and passes the rest to the Transport layer to form segments.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK AND COMMUNICATION 5
The transport layer processes the segment and rebuilds the stream. Thus the process of
encapsulation is reversed from the Layer 2, 2PDU back to layer 6.
Question 2
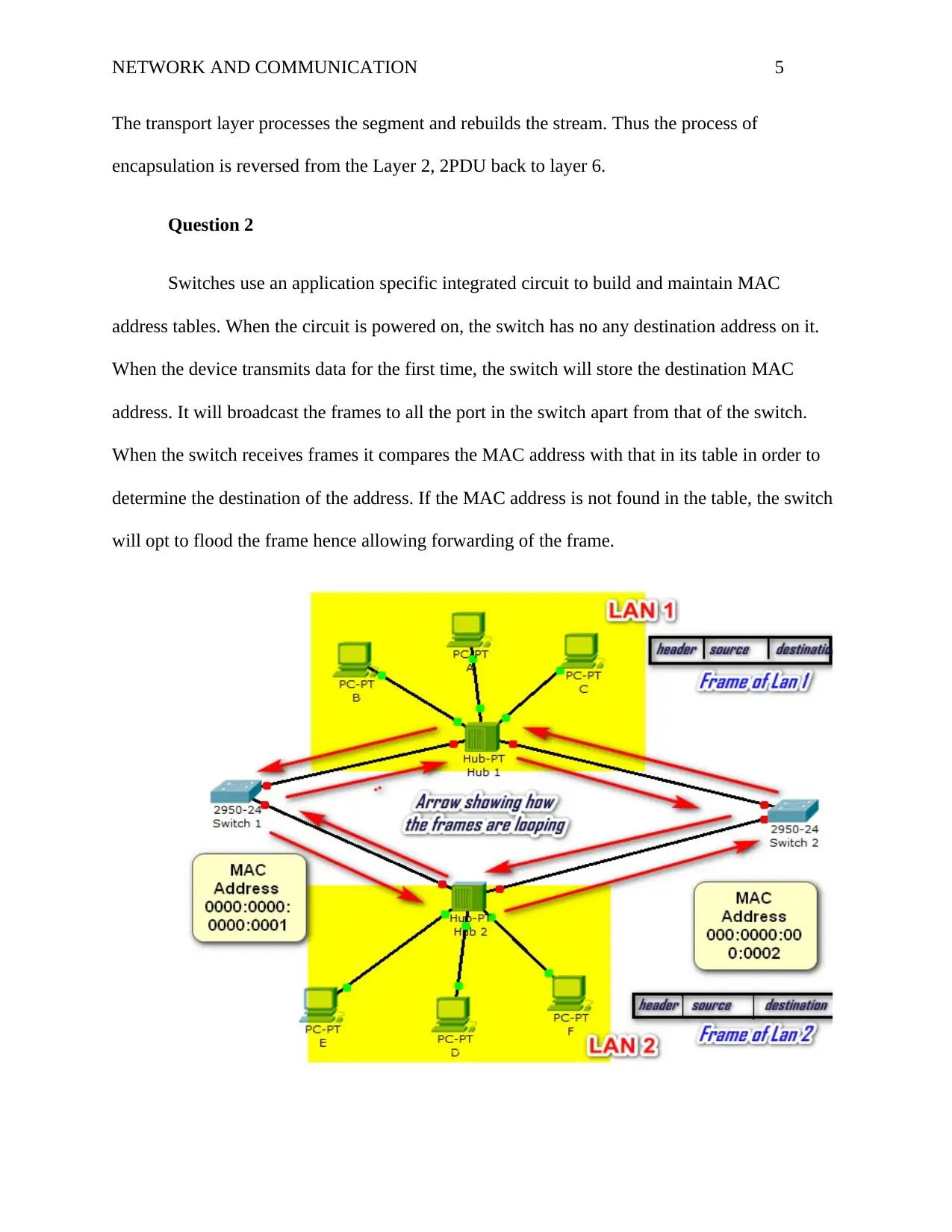
Switches use an application specific integrated circuit to build and maintain MAC
address tables. When the circuit is powered on, the switch has no any destination address on it.
When the device transmits data for the first time, the switch will store the destination MAC
address. It will broadcast the frames to all the port in the switch apart from that of the switch.
When the switch receives frames it compares the MAC address with that in its table in order to
determine the destination of the address. If the MAC address is not found in the table, the switch
will opt to flood the frame hence allowing forwarding of the frame.
The transport layer processes the segment and rebuilds the stream. Thus the process of
encapsulation is reversed from the Layer 2, 2PDU back to layer 6.
Question 2
Switches use an application specific integrated circuit to build and maintain MAC
address tables. When the circuit is powered on, the switch has no any destination address on it.
When the device transmits data for the first time, the switch will store the destination MAC
address. It will broadcast the frames to all the port in the switch apart from that of the switch.
When the switch receives frames it compares the MAC address with that in its table in order to
determine the destination of the address. If the MAC address is not found in the table, the switch
will opt to flood the frame hence allowing forwarding of the frame.

NETWORK AND COMMUNICATION 6
When host F on LAN 2 sends the frame to host A on LAN 1, Hub 2 will receive the
frame at the interface of the hub where it connects to F. It's obvious it will not find the MAC
address of A in LAN1 in its filter table. It will flood the frame to all the ports apart from that of
the source thus the same copy of the frames will be received in both switch 1 and switch 2 which
in turn will do the same: i.e. flooding the frame to all its port apart from that of the source in
search of the MAC address of A. This will result to increase in copies of the frame in the
network since the frames will keep circulating in the network. Eventually, the network will
completely break down as a result of unnecessary broadcast storm chewing the network
bandwidth.
Question 3
At the sender node, Alice encapsulates the packets for transmission on the ongoing link.
At the intermediate node, the frame is decapsulated and forwarded to the network layer which
then determines the routing. The link type involves in this transmission include the point-to-point
between two devices dedicated link and broadcast. Data Link Control (DLC) and Media Access
Control (MAC) are also used as sublayers. The network layer address stores the IP address of the
device which is unique across all nodes in all interconnected networks and is the source
destination. The link address locally identifies the device and stores address of the destination
source.
Alice node has the IP datagram to Bob's node, though in moving the frame the link
address is used to move to the next address. The Address Resolution Protocol is used to deduce if
the destination is local or remote. Once the destination of Bob has been identified as remote, the
ARP is used to determine the default gateway which is the router which in turn is responsible in
When host F on LAN 2 sends the frame to host A on LAN 1, Hub 2 will receive the
frame at the interface of the hub where it connects to F. It's obvious it will not find the MAC
address of A in LAN1 in its filter table. It will flood the frame to all the ports apart from that of
the source thus the same copy of the frames will be received in both switch 1 and switch 2 which
in turn will do the same: i.e. flooding the frame to all its port apart from that of the source in
search of the MAC address of A. This will result to increase in copies of the frame in the
network since the frames will keep circulating in the network. Eventually, the network will
completely break down as a result of unnecessary broadcast storm chewing the network
bandwidth.
Question 3
At the sender node, Alice encapsulates the packets for transmission on the ongoing link.
At the intermediate node, the frame is decapsulated and forwarded to the network layer which
then determines the routing. The link type involves in this transmission include the point-to-point
between two devices dedicated link and broadcast. Data Link Control (DLC) and Media Access
Control (MAC) are also used as sublayers. The network layer address stores the IP address of the
device which is unique across all nodes in all interconnected networks and is the source
destination. The link address locally identifies the device and stores address of the destination
source.
Alice node has the IP datagram to Bob's node, though in moving the frame the link
address is used to move to the next address. The Address Resolution Protocol is used to deduce if
the destination is local or remote. Once the destination of Bob has been identified as remote, the
ARP is used to determine the default gateway which is the router which in turn is responsible in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND COMMUNICATION 7
forwarding to Bob's node via data link layer. Router R1 and Router R2 communicate via point to
point connection. Alice IP (ARP Alice)requests for Bob's MAC address, the ARP at Alice
creates an ARP packet an forward it to the link of Alice. Data link of Alice makes a frame, which
is basically the packets in the data link, as shown in the frame link 1 and broadcasts the frame to
frame in link 2. In the frame link 3, ARP at Bob makes packet reply ARP sends it data link layer
including the Bob's MAC address. Bob's data link checks the type fields which denote ARP
protocol and decapsulates the frame.
Question 4 (1)
Point-To-Point-Protocol is considered very secure in respect to WAN. It has the
capabilities of being hidden from view; it has a way to encapsulate datagram multiprotocol
datagrams.
Question 4 (2)
The Link Control Protocol (LCP) is a core fundamental protocol that aid in the Point-to-
point communication in a network. It is used to create and establish logical links between the two
points; the source and the destination of the data. It is also responsible in Point-to-Point links for
complete operations for suit protocols inside the data-link layer of the OSI. It uses a set of frames
to control, manage and terminate the point-to-point links. It establishes and configures the
verification peer identification through the link configuration. It maintains the link by estimating
packets size and eliminates any configuration error. It also terminates the connection of the link
when the available resources exceed the requirement.
The Password Authentication Protocol (PAP) is used for access granting of devices
connected in point-to-point network. It is an authentication protocol that is primarily used in
forwarding to Bob's node via data link layer. Router R1 and Router R2 communicate via point to
point connection. Alice IP (ARP Alice)requests for Bob's MAC address, the ARP at Alice
creates an ARP packet an forward it to the link of Alice. Data link of Alice makes a frame, which
is basically the packets in the data link, as shown in the frame link 1 and broadcasts the frame to
frame in link 2. In the frame link 3, ARP at Bob makes packet reply ARP sends it data link layer
including the Bob's MAC address. Bob's data link checks the type fields which denote ARP
protocol and decapsulates the frame.
Question 4 (1)
Point-To-Point-Protocol is considered very secure in respect to WAN. It has the
capabilities of being hidden from view; it has a way to encapsulate datagram multiprotocol
datagrams.
Question 4 (2)
The Link Control Protocol (LCP) is a core fundamental protocol that aid in the Point-to-
point communication in a network. It is used to create and establish logical links between the two
points; the source and the destination of the data. It is also responsible in Point-to-Point links for
complete operations for suit protocols inside the data-link layer of the OSI. It uses a set of frames
to control, manage and terminate the point-to-point links. It establishes and configures the
verification peer identification through the link configuration. It maintains the link by estimating
packets size and eliminates any configuration error. It also terminates the connection of the link
when the available resources exceed the requirement.
The Password Authentication Protocol (PAP) is used for access granting of devices
connected in point-to-point network. It is an authentication protocol that is primarily used in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND COMMUNICATION 8
validating the users by supporting three types of authentications of varying security levels. PAP
makes this complete by using network server to request password from the clients’ device and
share the retrieved password to the relevant server without encrypting the password. It’s often
considered as least secure.
The Challenge-Handshake Authentication Protocol (CHAP) is used in authenticating
network hosts to point-to-point networks. It provides a secure connection since it provides
protection against playback attacks through a variable change value. In requests passwords in
network sever access which sends password a unique message to the clients device, the client
device will then encrypt the message and send it back to the access server, the authentic is
successful when the user’s response match.
The Network Control Program (NCP) is used to request for extra configurations and
facilities for the network in point-to-point networks. It makes possible for the devices connected
in point-to-point network to communicate, access remote devices and share/transmit files
between the devices. It provides the middle layer which aid computer network protocol suit in
running host computers. It uses the simplex protocol which utilizes the two ports (the UDP and
TCP port numbers) to establish two connections of the point-to-point devices, for two way
communication.
The Internet Protocol Control Protocol (IPCP) is used establishing, configuring and
managing Internet Protocols (IP) in devices connected in point-to-point network. It configures
the IP address by enabling and disabling the modules of the internet protocol on both ends of the
point-to-point network. The IPCP packets are transmitted when the PPP reaches the network
layer protocol phase. Each device in the point to point network sends its own configuration
validating the users by supporting three types of authentications of varying security levels. PAP
makes this complete by using network server to request password from the clients’ device and
share the retrieved password to the relevant server without encrypting the password. It’s often
considered as least secure.
The Challenge-Handshake Authentication Protocol (CHAP) is used in authenticating
network hosts to point-to-point networks. It provides a secure connection since it provides
protection against playback attacks through a variable change value. In requests passwords in
network sever access which sends password a unique message to the clients device, the client
device will then encrypt the message and send it back to the access server, the authentic is
successful when the user’s response match.
The Network Control Program (NCP) is used to request for extra configurations and
facilities for the network in point-to-point networks. It makes possible for the devices connected
in point-to-point network to communicate, access remote devices and share/transmit files
between the devices. It provides the middle layer which aid computer network protocol suit in
running host computers. It uses the simplex protocol which utilizes the two ports (the UDP and
TCP port numbers) to establish two connections of the point-to-point devices, for two way
communication.
The Internet Protocol Control Protocol (IPCP) is used establishing, configuring and
managing Internet Protocols (IP) in devices connected in point-to-point network. It configures
the IP address by enabling and disabling the modules of the internet protocol on both ends of the
point-to-point network. The IPCP packets are transmitted when the PPP reaches the network
layer protocol phase. Each device in the point to point network sends its own configuration

NETWORK AND COMMUNICATION 9
requests since the direction of PPP connection and Transport Control Protocol/ Internet Protocol
(TCP/IP) option are not dependable to each other’s (Sarkar et al.,2016).
Question 5(1).
Mobile telephony entails communication phone services which allow one to be mobile
rather than fixed in one position. Cellar phones connect to base transceiver stations. Due to the
effect of some unavoidable negative factors such as the attenuation, there is need to modulate
digital signals before transmitting them. This is because the frequency of the baseband e.g. that
of your voice is so weak that it cannot withstand the extent of transmission (i.e. distance to
cover), hence the heightening of the frequency to the order of MHz disguised in the bosom of the
carrier until it gets to its destination then demodulated. When transmission distance increases the
signal tends to lose, so carrier signal is added along with the message signal to strengthen the
original message signal.
Question 5 (2)
A bandpass is a channel whose resultant bandwidth does not start form 0. The data is
transmitted in form of amplitude modulated signals; the stream of data is modulated while
switching the amplitude and frequency in together with the incoming data (Al-Fuqaha et al.,
2015). The bandpass signals are analyzed by equivalent envelope representation. The signal
received is later on filtered with a bandwidth filter of equal bandwidth signal which entails
converting narrowband noise from the white noise. The received signal complexity
representation will be observed by the receiver for some time and make appropriate equivalently
for binary data. At the receiver, the data is then reconverted to its initial state i.e. from analog to
digital.
requests since the direction of PPP connection and Transport Control Protocol/ Internet Protocol
(TCP/IP) option are not dependable to each other’s (Sarkar et al.,2016).
Question 5(1).
Mobile telephony entails communication phone services which allow one to be mobile
rather than fixed in one position. Cellar phones connect to base transceiver stations. Due to the
effect of some unavoidable negative factors such as the attenuation, there is need to modulate
digital signals before transmitting them. This is because the frequency of the baseband e.g. that
of your voice is so weak that it cannot withstand the extent of transmission (i.e. distance to
cover), hence the heightening of the frequency to the order of MHz disguised in the bosom of the
carrier until it gets to its destination then demodulated. When transmission distance increases the
signal tends to lose, so carrier signal is added along with the message signal to strengthen the
original message signal.
Question 5 (2)
A bandpass is a channel whose resultant bandwidth does not start form 0. The data is
transmitted in form of amplitude modulated signals; the stream of data is modulated while
switching the amplitude and frequency in together with the incoming data (Al-Fuqaha et al.,
2015). The bandpass signals are analyzed by equivalent envelope representation. The signal
received is later on filtered with a bandwidth filter of equal bandwidth signal which entails
converting narrowband noise from the white noise. The received signal complexity
representation will be observed by the receiver for some time and make appropriate equivalently
for binary data. At the receiver, the data is then reconverted to its initial state i.e. from analog to
digital.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK AND COMMUNICATION 10
Question 6
We have a total of 8 collisions:
A switch cause one collision per pair devices so we will have collisions between pc-5 and
switch 1, p-6 and switch 3, switch 1 and switch 2, switch 2 and switch 3, switch 2 and router thus
making a total of 5 collisions based on the switch.
Devices that are connected to a hub have one resultant collision, thus in our diagram, we
will have collision one collision as a result of pc-1, pc-2, hub 4, hub 5 and hub 3. The second
collision involving a hub is between hub 2 and pc-3 while the last collision involving a hub is
between pc-4 and hub 1.
Bridge forward and filters incoming frames, it determines the destination address of the
frame. It has the capability of storing Ethernet frames in memory thus preventing collisions from
happening. Thus, no collision will be around the bridge.
Question 6
We have a total of 8 collisions:
A switch cause one collision per pair devices so we will have collisions between pc-5 and
switch 1, p-6 and switch 3, switch 1 and switch 2, switch 2 and switch 3, switch 2 and router thus
making a total of 5 collisions based on the switch.
Devices that are connected to a hub have one resultant collision, thus in our diagram, we
will have collision one collision as a result of pc-1, pc-2, hub 4, hub 5 and hub 3. The second
collision involving a hub is between hub 2 and pc-3 while the last collision involving a hub is
between pc-4 and hub 1.
Bridge forward and filters incoming frames, it determines the destination address of the
frame. It has the capability of storing Ethernet frames in memory thus preventing collisions from
happening. Thus, no collision will be around the bridge.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK AND COMMUNICATION 11
References
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., & Ayyash, M. (2015). Internet of
things: A survey on enabling technologies, protocols, and applications. IEEE
Communications Surveys & Tutorials, 17(4), 2347-2376.
Geier, J. (2015). Designing and Deploying 802.11 Wireless Networks: A Practical Guide to
Implementing 802.11 n and 802.11 ac Wireless Networks For Enterprise-Based
Applications. Cisco Press.
Sarkar, S. K., Basavaraju, T. G., & Puttamadappa, C. (2016). Ad hoc mobile wireless
networks:principles, protocols, and applications. CRC Press.
References
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., & Ayyash, M. (2015). Internet of
things: A survey on enabling technologies, protocols, and applications. IEEE
Communications Surveys & Tutorials, 17(4), 2347-2376.
Geier, J. (2015). Designing and Deploying 802.11 Wireless Networks: A Practical Guide to
Implementing 802.11 n and 802.11 ac Wireless Networks For Enterprise-Based
Applications. Cisco Press.
Sarkar, S. K., Basavaraju, T. G., & Puttamadappa, C. (2016). Ad hoc mobile wireless
networks:principles, protocols, and applications. CRC Press.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





