Creative Letting Ltd Network Implementation Report - Windows Server
VerifiedAdded on 2020/05/01
|25
|4326
|173
Report
AI Summary
This report outlines the network implementation strategy for Creative Letting Ltd, aiming to connect its Paris departments and provide internet access to employees. It details the selection of a suitable network topology and the procurement of necessary networking devices, including Cisco products. The network will be managed using Windows Server 2008, which will host DHCP, DNS, WINS, IIS, and other essential services. The report covers key aspects such as designing and implementing automatic IP addressing mechanisms, including routed and flat networks, dynamic IP addressing, and the functions and benefits of a DHCP server. It also addresses domain naming strategies, including installing DNS services, creating forward and reverse lookup zones, and integrating DHCP and DNS. Furthermore, the report discusses configuring and supporting routing and remote access, including troubleshooting, backup strategies, network health monitoring, and connectivity solutions. Network security is a major focus, with discussions on VPN configuration, security threats, Certificate Authority (CA), and IPsec implementation. The report concludes with an overview of the implemented network, its components, and its security considerations.

Creative Letting Ltd Network Implementation Report
Name
Institution
Date
Name
Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Chapter 1.....................................................................................................................................................4
Introduction.............................................................................................................................................4
Chapter 2.....................................................................................................................................................4
Implement Name Resolution Services.....................................................................................................4
2.1 Designing and implementing an automatic IP addressing mechanism.....................................4
2.1.0 Routed and Flat Networks..........................................................................................................4
2.1.1 IP Addressing Mechanism...........................................................................................................5
2.1.2 Dynamic IP addressing................................................................................................................5
2.1.3 Functions of a DHCP server.........................................................................................................7
2.1.4 Benefits of using a DHCP server..................................................................................................7
2.1.5 The DHCP DORA Process.............................................................................................................7
2.1.6 Installation of a DHCP server......................................................................................................7
2.1.7 Steps to installing the DHCP Relay agents..................................................................................8
2.2 Designing and implementing a domain naming strategy.................................................................10
2.2.1 Installing the DNS service.........................................................................................................10
2.2.2 Creating a forward lookup zone................................................................................................11
2.2.3 Creating a reverse lookup zone................................................................................................11
2.2.4 NetBIOS Name resolution.........................................................................................................12
2.2.5 Installing WINS..........................................................................................................................13
2.2.6 Adding static WINS records for non-WINS clients.....................................................................13
2.2.7 PUSH and PULL replication configuration.................................................................................13
2.2.8 Integration of DHCP and DNS in a network...............................................................................14
Chapter 3...................................................................................................................................................14
Configuring and Supporting Routing and Remote Access.....................................................................14
3.1 Troubleshooting, backup and fault tolerance strategy..................................................................14
3.1.1 Backup Strategy........................................................................................................................15
3.1.2 Backup strategy for DNS...........................................................................................................15
3.1.4 Backup strategy for DHCP.........................................................................................................15
3.2 Network health and monitoring analysis..........................................................................................15
Ipconfig..............................................................................................................................................16
Tracert...............................................................................................................................................17
Chapter 1.....................................................................................................................................................4
Introduction.............................................................................................................................................4
Chapter 2.....................................................................................................................................................4
Implement Name Resolution Services.....................................................................................................4
2.1 Designing and implementing an automatic IP addressing mechanism.....................................4
2.1.0 Routed and Flat Networks..........................................................................................................4
2.1.1 IP Addressing Mechanism...........................................................................................................5
2.1.2 Dynamic IP addressing................................................................................................................5
2.1.3 Functions of a DHCP server.........................................................................................................7
2.1.4 Benefits of using a DHCP server..................................................................................................7
2.1.5 The DHCP DORA Process.............................................................................................................7
2.1.6 Installation of a DHCP server......................................................................................................7
2.1.7 Steps to installing the DHCP Relay agents..................................................................................8
2.2 Designing and implementing a domain naming strategy.................................................................10
2.2.1 Installing the DNS service.........................................................................................................10
2.2.2 Creating a forward lookup zone................................................................................................11
2.2.3 Creating a reverse lookup zone................................................................................................11
2.2.4 NetBIOS Name resolution.........................................................................................................12
2.2.5 Installing WINS..........................................................................................................................13
2.2.6 Adding static WINS records for non-WINS clients.....................................................................13
2.2.7 PUSH and PULL replication configuration.................................................................................13
2.2.8 Integration of DHCP and DNS in a network...............................................................................14
Chapter 3...................................................................................................................................................14
Configuring and Supporting Routing and Remote Access.....................................................................14
3.1 Troubleshooting, backup and fault tolerance strategy..................................................................14
3.1.1 Backup Strategy........................................................................................................................15
3.1.2 Backup strategy for DNS...........................................................................................................15
3.1.4 Backup strategy for DHCP.........................................................................................................15
3.2 Network health and monitoring analysis..........................................................................................15
Ipconfig..............................................................................................................................................16
Tracert...............................................................................................................................................17

3
Telnet.................................................................................................................................................18
3.3 Connectivity Solutions.....................................................................................................................19
Chapter 4...................................................................................................................................................20
Configuring Network Security...............................................................................................................20
4.1 Networking design and implementation report for Remote Access.............................................20
4.1.0 Benefits of VPNS.......................................................................................................................20
4.1.1 RRAS configuration...................................................................................................................20
4.1.2 Configuring inbound and outbound VPN connections..............................................................21
4.1.2 Role of the RADIUS server........................................................................................................21
4.2 Security threats faced by modern computer networks...............................................................22
4.3 Certificate Authority (CA) and IPsec...........................................................................................22
4.3.1 Role of CA.................................................................................................................................22
4.3.2 Importance of digital certificates..............................................................................................23
4.3.3 IPsec..........................................................................................................................................23
Chapter 5...................................................................................................................................................24
Conclusion.............................................................................................................................................24
Bibliography...............................................................................................................................................25
Telnet.................................................................................................................................................18
3.3 Connectivity Solutions.....................................................................................................................19
Chapter 4...................................................................................................................................................20
Configuring Network Security...............................................................................................................20
4.1 Networking design and implementation report for Remote Access.............................................20
4.1.0 Benefits of VPNS.......................................................................................................................20
4.1.1 RRAS configuration...................................................................................................................20
4.1.2 Configuring inbound and outbound VPN connections..............................................................21
4.1.2 Role of the RADIUS server........................................................................................................21
4.2 Security threats faced by modern computer networks...............................................................22
4.3 Certificate Authority (CA) and IPsec...........................................................................................22
4.3.1 Role of CA.................................................................................................................................22
4.3.2 Importance of digital certificates..............................................................................................23
4.3.3 IPsec..........................................................................................................................................23
Chapter 5...................................................................................................................................................24
Conclusion.............................................................................................................................................24
Bibliography...............................................................................................................................................25
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Chapter 1
Introduction
Creative Letting Ltd. needs to implement a network which will connect all of its
departments in Paris and also provide internet connection to its employees. In order to
successfully achieve this, an appropriate network topology will be formulated and all required
networking devices must be procured i.e. from Cisco. The network will be managed on
Windows server 2008 which will host the DHCP server, DNS WINS, IIS and many other
services required in the network. The company must ensure implementation of networking
technologies that aim at keeping secure the network and the integrity of its data (Mori, 2016).
Chapter 2
Implement Name Resolution Services.
2.1 Designing and implementing an automatic IP addressing mechanism
2.1.0 Routed and Flat Networks
A routed network is a type of network that is mostly implemented when a bridged
network is not available because of hosting provider restrictions (Jia, 2015).
A flat network is a network where all stations are able to reach each other without
having to go via intermediary hardware devices such as a router. A flat network is one network
segment.
Differences: A flat network would allow any traffic to any workstation or server while
a routed network would not always allow traffic to any workstation or server.
Introduction
Creative Letting Ltd. needs to implement a network which will connect all of its
departments in Paris and also provide internet connection to its employees. In order to
successfully achieve this, an appropriate network topology will be formulated and all required
networking devices must be procured i.e. from Cisco. The network will be managed on
Windows server 2008 which will host the DHCP server, DNS WINS, IIS and many other
services required in the network. The company must ensure implementation of networking
technologies that aim at keeping secure the network and the integrity of its data (Mori, 2016).
Chapter 2
Implement Name Resolution Services.
2.1 Designing and implementing an automatic IP addressing mechanism
2.1.0 Routed and Flat Networks
A routed network is a type of network that is mostly implemented when a bridged
network is not available because of hosting provider restrictions (Jia, 2015).
A flat network is a network where all stations are able to reach each other without
having to go via intermediary hardware devices such as a router. A flat network is one network
segment.
Differences: A flat network would allow any traffic to any workstation or server while
a routed network would not always allow traffic to any workstation or server.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
A routed network is good because one will have better control of what users see and it
is easier to keep a good structure of the network especially when it is spread over 10 buildings.
2.1.1 IP Addressing Mechanism
A static IP addressing is a mechanism where hosts are given permanent IP address
which does not change even after the computer reboots.
A dynamic IP address is an IP address that is dynamically assigned to a computer and
every time the computer reboots, it is assigned a different IP address using the DHCP protocol.
The dynamic IP addressing mechanism is mostly recommended since it gives more
privacy and is cheaper and easier to set it up than static IP addressing.
2.1.2 Dynamic IP addressing
This is a class C network
IP address: 192.168.1.143
Subnet Mask: 255.255.255.0
Binary= 11111111.11111111.11111111.00000000
Number of subnet = 2^8 =256
Block size = 256-255 =1
Number of hosts per subnet = 2^8 =256-2=254
Therefore Subnet Address = 192.168.1.0
Broadcast Address: 192.168.1.255
Number of hosts in this network = 254
Address range = 192.168.1.1 to 192.168.1.254
A routed network is good because one will have better control of what users see and it
is easier to keep a good structure of the network especially when it is spread over 10 buildings.
2.1.1 IP Addressing Mechanism
A static IP addressing is a mechanism where hosts are given permanent IP address
which does not change even after the computer reboots.
A dynamic IP address is an IP address that is dynamically assigned to a computer and
every time the computer reboots, it is assigned a different IP address using the DHCP protocol.
The dynamic IP addressing mechanism is mostly recommended since it gives more
privacy and is cheaper and easier to set it up than static IP addressing.
2.1.2 Dynamic IP addressing
This is a class C network
IP address: 192.168.1.143
Subnet Mask: 255.255.255.0
Binary= 11111111.11111111.11111111.00000000
Number of subnet = 2^8 =256
Block size = 256-255 =1
Number of hosts per subnet = 2^8 =256-2=254
Therefore Subnet Address = 192.168.1.0
Broadcast Address: 192.168.1.255
Number of hosts in this network = 254
Address range = 192.168.1.1 to 192.168.1.254
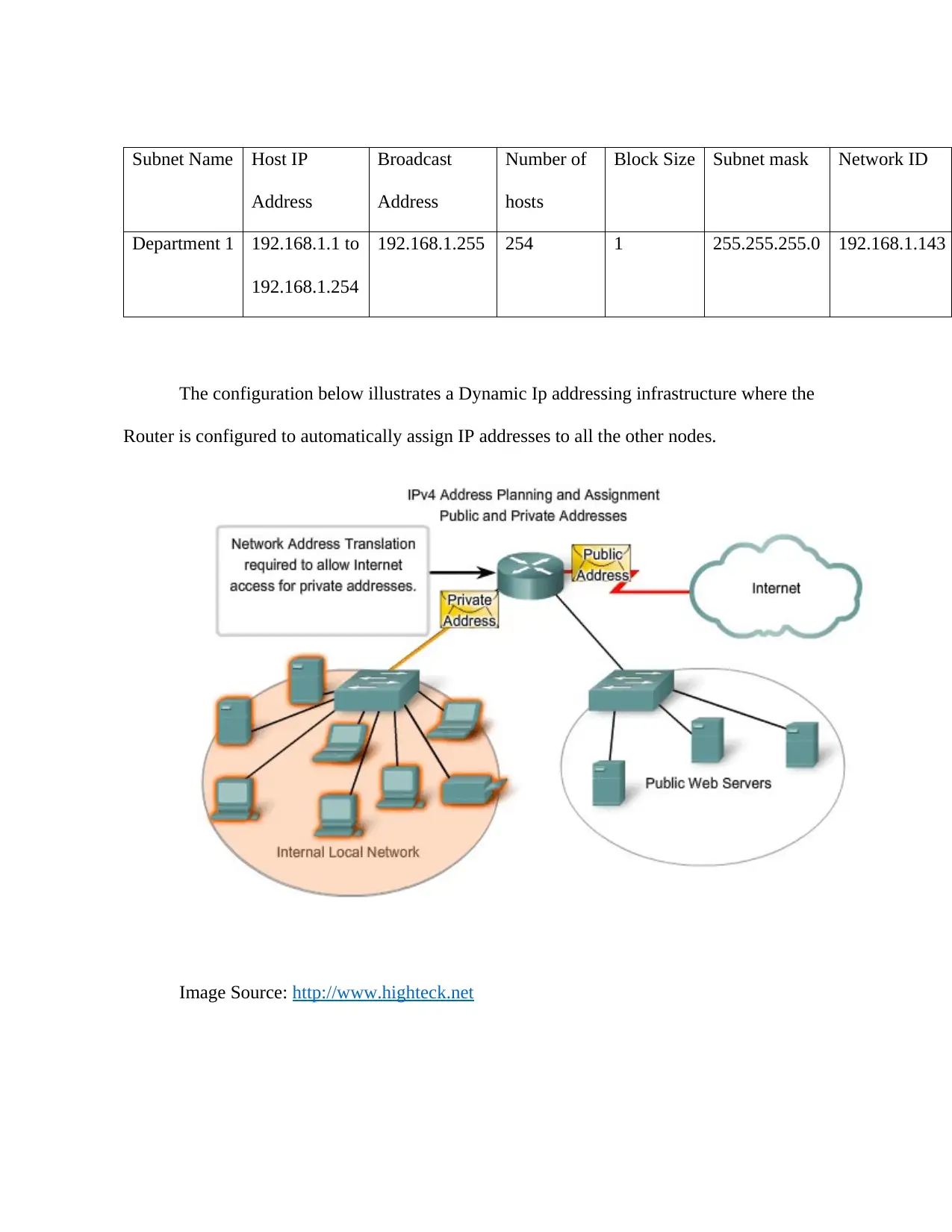
Subnet Name Host IP
Address
Broadcast
Address
Number of
hosts
Block Size Subnet mask Network ID
Department 1 192.168.1.1 to
192.168.1.254
192.168.1.255 254 1 255.255.255.0 192.168.1.143
The configuration below illustrates a Dynamic Ip addressing infrastructure where the
Router is configured to automatically assign IP addresses to all the other nodes.
Image Source: http://www.highteck.net
Address
Broadcast
Address
Number of
hosts
Block Size Subnet mask Network ID
Department 1 192.168.1.1 to
192.168.1.254
192.168.1.255 254 1 255.255.255.0 192.168.1.143
The configuration below illustrates a Dynamic Ip addressing infrastructure where the
Router is configured to automatically assign IP addresses to all the other nodes.
Image Source: http://www.highteck.net
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
2.1.3 Functions of a DHCP server.
Used to assign IP, DNS, and Gateway address to computers in a network dynamically.
DHCP stands for Dynamic Host Configuration Protocol.
2.1.4 Benefits of using a DHCP server.
Offers easier management of IP addresses.
Offers a centralized network client configuration.
Responds to requests from BOOTP clients.
Allows for network booting.
Supports very large networks by utilizing multithreading process of accepting client
requests simultaneously.
You can have multiple DHCP servers on the network while utilizing the DORA
principle.
2.1.5 The DHCP DORA Process
Discovery – the client broadcasts a message on the local network that it is connected to
in order to discover available DHCP servers.
Offer – An appropriately configured DHCP server gets requests from a client and then
it offers an address to it from a pool of available addresses.
Acknowledgement – The request is acknowledged by the server, and it informs the
client on the lease validity of the address and other information that is needed by the client.
2.1.6 Installation of a DHCP server.
A DHCP server can be set up on Windows Server 2008 and later. The server should be
correctly configured with a static IP address and you must know the network’s IP address
2.1.3 Functions of a DHCP server.
Used to assign IP, DNS, and Gateway address to computers in a network dynamically.
DHCP stands for Dynamic Host Configuration Protocol.
2.1.4 Benefits of using a DHCP server.
Offers easier management of IP addresses.
Offers a centralized network client configuration.
Responds to requests from BOOTP clients.
Allows for network booting.
Supports very large networks by utilizing multithreading process of accepting client
requests simultaneously.
You can have multiple DHCP servers on the network while utilizing the DORA
principle.
2.1.5 The DHCP DORA Process
Discovery – the client broadcasts a message on the local network that it is connected to
in order to discover available DHCP servers.
Offer – An appropriately configured DHCP server gets requests from a client and then
it offers an address to it from a pool of available addresses.
Acknowledgement – The request is acknowledged by the server, and it informs the
client on the lease validity of the address and other information that is needed by the client.
2.1.6 Installation of a DHCP server.
A DHCP server can be set up on Windows Server 2008 and later. The server should be
correctly configured with a static IP address and you must know the network’s IP address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
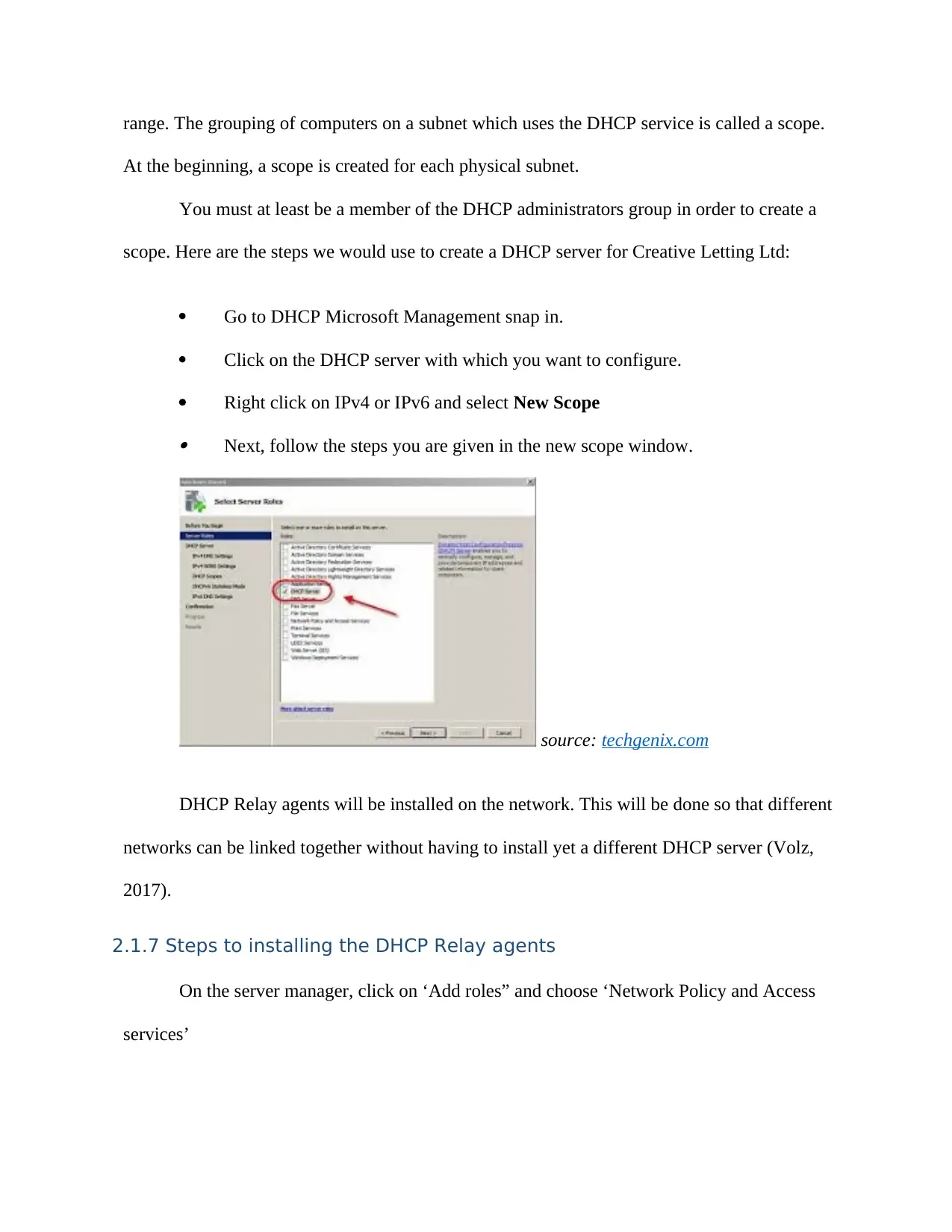
range. The grouping of computers on a subnet which uses the DHCP service is called a scope.
At the beginning, a scope is created for each physical subnet.
You must at least be a member of the DHCP administrators group in order to create a
scope. Here are the steps we would use to create a DHCP server for Creative Letting Ltd:
Go to DHCP Microsoft Management snap in.
Click on the DHCP server with which you want to configure.
Right click on IPv4 or IPv6 and select New Scope Next, follow the steps you are given in the new scope window.
source: techgenix.com
DHCP Relay agents will be installed on the network. This will be done so that different
networks can be linked together without having to install yet a different DHCP server (Volz,
2017).
2.1.7 Steps to installing the DHCP Relay agents
On the server manager, click on ‘Add roles” and choose ‘Network Policy and Access
services’
At the beginning, a scope is created for each physical subnet.
You must at least be a member of the DHCP administrators group in order to create a
scope. Here are the steps we would use to create a DHCP server for Creative Letting Ltd:
Go to DHCP Microsoft Management snap in.
Click on the DHCP server with which you want to configure.
Right click on IPv4 or IPv6 and select New Scope Next, follow the steps you are given in the new scope window.
source: techgenix.com
DHCP Relay agents will be installed on the network. This will be done so that different
networks can be linked together without having to install yet a different DHCP server (Volz,
2017).
2.1.7 Steps to installing the DHCP Relay agents
On the server manager, click on ‘Add roles” and choose ‘Network Policy and Access
services’

9
Choose Routing and remote access services and press next. Confirm Installation by
accepting the terms.
Go to start menu, admin tools and chose Routing and Remote Access. Go to the server
and right click on it and then choose the option to configure and enable routing remote access.
Yes, it will be important to have reserved IP addresses within our network range. These
reserved IP addresses will not be routed through the internet, they will be meant for devices
positioned behind the router or a proxy server. A pop up window will appear and you will tick
on LAN routing (if it is not ticked by default) and finish. At this step, Routing and remote
access service is active and we now need to install the DHCP Relay Agent Protocol. Go again
to admin tools, choose Routing ad remote access and expand the server name you want to
configure. On IPv4, expand again and right click on the general option and choose New
Routing Protocol. A pop up window is shown where you will select DHCP relay agent and
proceed. Now the DHCP relay agent will be added to the IPv4 option tree. Right click on it and
go to New Interface. On the new window, choose ‘internal’ and ok. Another window will pop p
where we give the number of relay agents the packets will go through from the PC and go to
‘ok’. Finally, a window for setting the destination address for DHCP pops up. Input the
destination address and click ‘ok’ (Volz, 2017).
Choose Routing and remote access services and press next. Confirm Installation by
accepting the terms.
Go to start menu, admin tools and chose Routing and Remote Access. Go to the server
and right click on it and then choose the option to configure and enable routing remote access.
Yes, it will be important to have reserved IP addresses within our network range. These
reserved IP addresses will not be routed through the internet, they will be meant for devices
positioned behind the router or a proxy server. A pop up window will appear and you will tick
on LAN routing (if it is not ticked by default) and finish. At this step, Routing and remote
access service is active and we now need to install the DHCP Relay Agent Protocol. Go again
to admin tools, choose Routing ad remote access and expand the server name you want to
configure. On IPv4, expand again and right click on the general option and choose New
Routing Protocol. A pop up window is shown where you will select DHCP relay agent and
proceed. Now the DHCP relay agent will be added to the IPv4 option tree. Right click on it and
go to New Interface. On the new window, choose ‘internal’ and ok. Another window will pop p
where we give the number of relay agents the packets will go through from the PC and go to
‘ok’. Finally, a window for setting the destination address for DHCP pops up. Input the
destination address and click ‘ok’ (Volz, 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
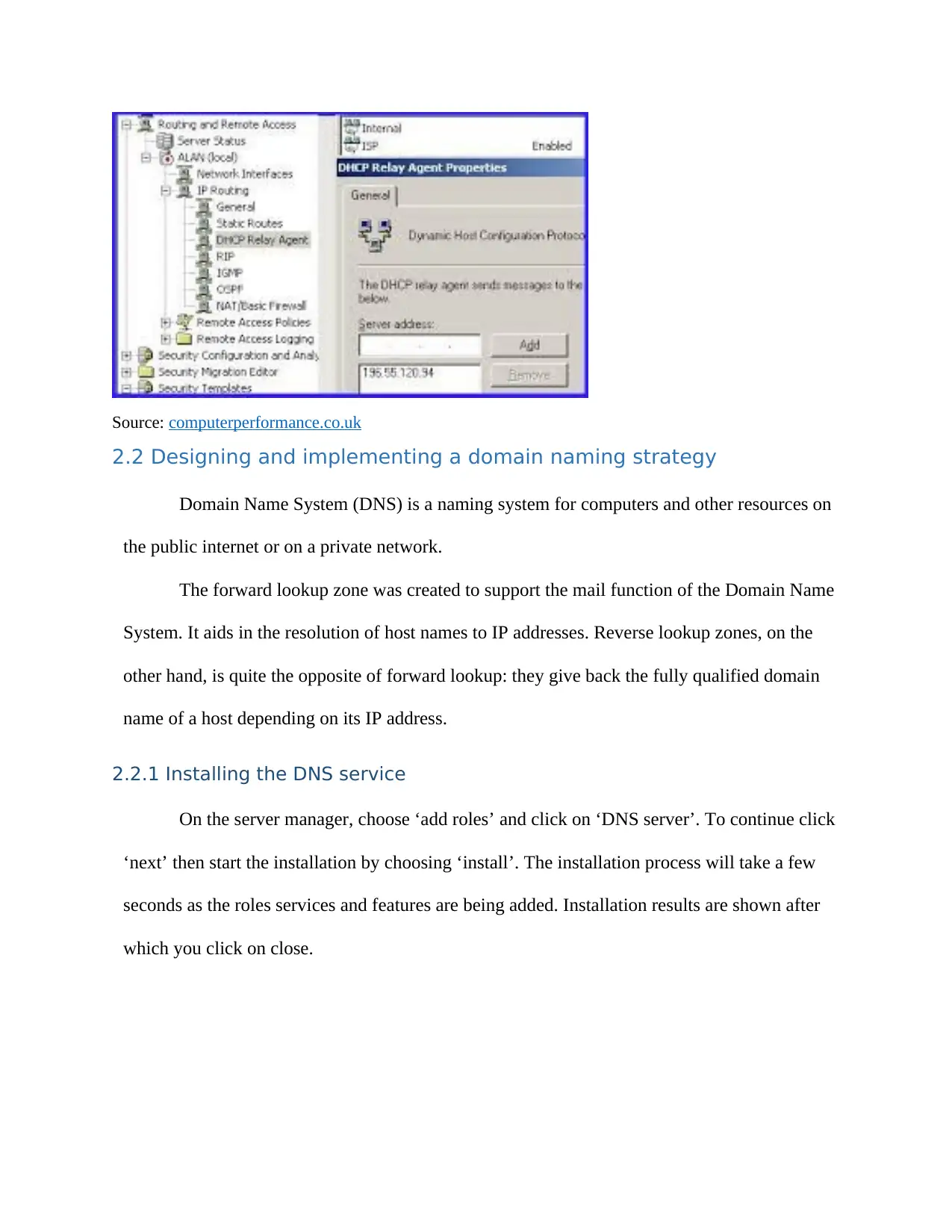
Source: computerperformance.co.uk
2.2 Designing and implementing a domain naming strategy
Domain Name System (DNS) is a naming system for computers and other resources on
the public internet or on a private network.
The forward lookup zone was created to support the mail function of the Domain Name
System. It aids in the resolution of host names to IP addresses. Reverse lookup zones, on the
other hand, is quite the opposite of forward lookup: they give back the fully qualified domain
name of a host depending on its IP address.
2.2.1 Installing the DNS service
On the server manager, choose ‘add roles’ and click on ‘DNS server’. To continue click
‘next’ then start the installation by choosing ‘install’. The installation process will take a few
seconds as the roles services and features are being added. Installation results are shown after
which you click on close.
2.2 Designing and implementing a domain naming strategy
Domain Name System (DNS) is a naming system for computers and other resources on
the public internet or on a private network.
The forward lookup zone was created to support the mail function of the Domain Name
System. It aids in the resolution of host names to IP addresses. Reverse lookup zones, on the
other hand, is quite the opposite of forward lookup: they give back the fully qualified domain
name of a host depending on its IP address.
2.2.1 Installing the DNS service
On the server manager, choose ‘add roles’ and click on ‘DNS server’. To continue click
‘next’ then start the installation by choosing ‘install’. The installation process will take a few
seconds as the roles services and features are being added. Installation results are shown after
which you click on close.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
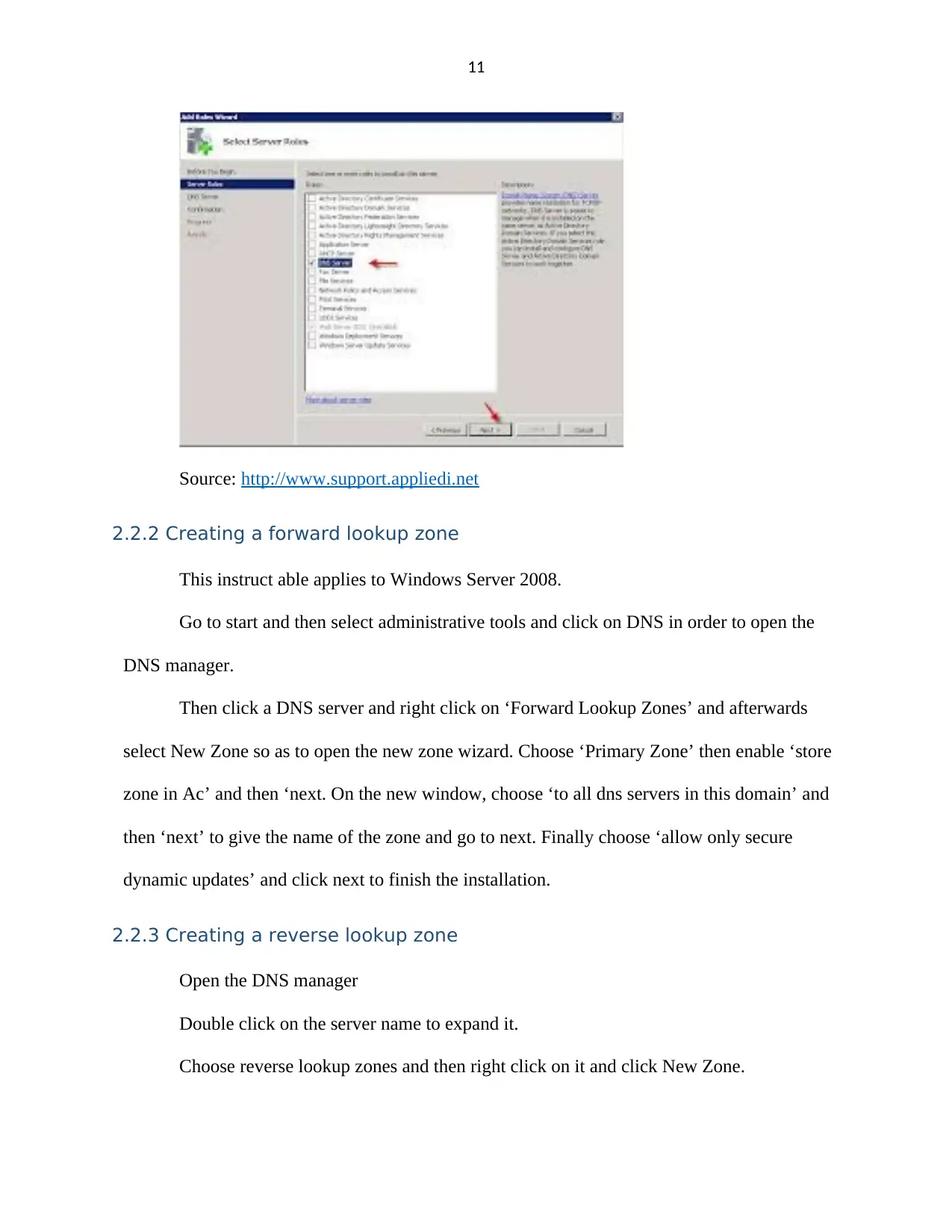
11
Source: http://www.support.appliedi.net
2.2.2 Creating a forward lookup zone
This instruct able applies to Windows Server 2008.
Go to start and then select administrative tools and click on DNS in order to open the
DNS manager.
Then click a DNS server and right click on ‘Forward Lookup Zones’ and afterwards
select New Zone so as to open the new zone wizard. Choose ‘Primary Zone’ then enable ‘store
zone in Ac’ and then ‘next. On the new window, choose ‘to all dns servers in this domain’ and
then ‘next’ to give the name of the zone and go to next. Finally choose ‘allow only secure
dynamic updates’ and click next to finish the installation.
2.2.3 Creating a reverse lookup zone
Open the DNS manager
Double click on the server name to expand it.
Choose reverse lookup zones and then right click on it and click New Zone.
Source: http://www.support.appliedi.net
2.2.2 Creating a forward lookup zone
This instruct able applies to Windows Server 2008.
Go to start and then select administrative tools and click on DNS in order to open the
DNS manager.
Then click a DNS server and right click on ‘Forward Lookup Zones’ and afterwards
select New Zone so as to open the new zone wizard. Choose ‘Primary Zone’ then enable ‘store
zone in Ac’ and then ‘next. On the new window, choose ‘to all dns servers in this domain’ and
then ‘next’ to give the name of the zone and go to next. Finally choose ‘allow only secure
dynamic updates’ and click next to finish the installation.
2.2.3 Creating a reverse lookup zone
Open the DNS manager
Double click on the server name to expand it.
Choose reverse lookup zones and then right click on it and click New Zone.
Use the New Zone wizard to step by step create a primary zone, secondary zone, and a
stub zone just as we did in the forward lookup zone above.
Finally, store the zone in Active Directory and select the dynamic updates you want to
enable.
Source: technet.microsoft.com
2.2.4 NetBIOS Name resolution
NetBIOS is able to broadcast names to all nodes that are listening nodes on the network.
Via the Windows Internet Service (WINS), a NetBIOS name is resolved to an IP address.
NetBIOS uses a User Datagram Protocol. When an operating system is installed, the NetBIOS
name will be assigned by the administrator.
Yes, I would Use NetBIOS name resolution because it uses existing TCP/IP protocols
such that it is able to be routed across the internet and other Wide Area Networks. This will
keep Creative Letting LTD always connected to the internet and can be scalable pretty easy.
Windows Internet Name Service (WINS) is the implementation of NetBIOS by
Microsoft. It is known the world over that just as DNS is to domain names, WINS is to
stub zone just as we did in the forward lookup zone above.
Finally, store the zone in Active Directory and select the dynamic updates you want to
enable.
Source: technet.microsoft.com
2.2.4 NetBIOS Name resolution
NetBIOS is able to broadcast names to all nodes that are listening nodes on the network.
Via the Windows Internet Service (WINS), a NetBIOS name is resolved to an IP address.
NetBIOS uses a User Datagram Protocol. When an operating system is installed, the NetBIOS
name will be assigned by the administrator.
Yes, I would Use NetBIOS name resolution because it uses existing TCP/IP protocols
such that it is able to be routed across the internet and other Wide Area Networks. This will
keep Creative Letting LTD always connected to the internet and can be scalable pretty easy.
Windows Internet Name Service (WINS) is the implementation of NetBIOS by
Microsoft. It is known the world over that just as DNS is to domain names, WINS is to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

